Select the correct expression for (?) in the proof segment below: 1. (pVg) →r Hypothesis 2. 3. Click on the Correct Response A) -(pv q) T (?) Modus Tollens, 1, 2 B) P C) q D) -p V-q Hypothesis 4
Answers
Based on the given information, the correct expression for (?) in the proof segment is option B) P.
The Modus Tollens inference rule states that if we have a conditional statement of the form "p → q" and its negation "~q", then we can infer the negation of the antecedent "~p". In the proof segment, the hypothesis is given as "(p V q) → r" (step 1). To apply the Modus Tollens rule, we need the negation of "r" (step 2). From the available options, the only expression that represents the negation of "r" is option B) P.
Therefore, by applying the Modus Tollens rule using the hypothesis and the negation of the consequent, we can infer that the correct expression for (?) is option B) P.
To learn more about expression click here: brainly.com/question/28170201
#SPJ11
Related Questions
CORRECT ANSWER WILL BE MARK AS BRAINLIEST AND SPAM WILL BE REPORTED
What is the one major difference between ROM and RAM?
(dont want a copy paste answer from google if you are sure then only answer)
Answers
Answer:
ROM - Read Only Memory; Allows for the storage of files in a permanent state. Allowed to go back to Memory and get information from it at anytime and be able to work on it, at which point its turns to the RAM's job.
RAM - Random Access Memory; Allows for storage of files in a Temporary state. Files get cleared from RAM once file is closed or exited.
Fill in the missing word HTTPS module gives more...........to web sites.
Answers
HTTPS module gives more security to web sites.
What is the HTTPS module?The HTTPS piece gives more freedom to websites. It bears Hypertext Transfer Protocol Secure, and it is an enlargement of HTTP that encrypts the ideas.
So, The use of HTTPS is specifically main for websites that handle delicate facts, in the way that personal dossier, commercial undertakings, or login references. It still helps to authorize trust and believeableness accompanying consumers, as they can visualize a lock icon in the internet /web viewing software's address bar, displaying that the link is secure.
Learn more about HTTPS module from
https://brainly.com/question/27682740
#SPJ1
one more thing explain why this program would be better written using a function
look my previous q1
Answers
The key use is for mental chunking, to help you grasp what complex software does.
By naming a small function according to its outcome/overall purpose, you reduce the amount of stuff you need to mentally juggle.
It's one of the many tools available to divide and conquer complexity.
Same way as a TV is full of complex stuff, but you press on, and plug into the wall plus an aerial, hdmi and WiFi. You don't talk about how the inside works to make higher level discussions possible
Use dimensional analysis (the ""factor-label"" method) to solve the following problems
Answers
The factor-label approach, also known as dimensional analysis or unit conversions, is employed when converting between different units of measurement.
What is Factor label dimensional analysis?Because a number may be multiplied by one without changing its value, this technique works. Because it employs factors that are equivalent, it is known as the factor-label technique. a method of analysis that represents physical quantities in respect of their fundamental dimensions in the absence of enough data to create precise equations.
A technique for solving problems called dimensional analysis takes advantage of the notion that every number or phrase can be multiplied by one without changing its value. Dimensional analysis is the method of determining the dimensions of physical quantities in order to examine relationships between them.
To know more about dimensional analysis, visit:
https://brainly.com/question/13078117
#SPJ4
Select the correct answer.
How does a demilitarized zone (DMZ) work?
A.
by preventing a private network from sending malicious traffic to external networks
B.
by monitoring traffic on a private network to protect it from malicious traffic
C.
by interacting directly with external networks to protect a private network
D.
by interacting directly with a private network to ensure proper functioning of a firewall
E.
by monitoring traffic on external networks to prevent malicious traffic from reaching a private network
Answers
Answer:
The answer is C
Explanation:
Hope this helps :)
Which of the following statements is true regarding local area networks? SELECT 3 OPTIONS.
A: traditionally used Ethernet cables to connect devices
B: can include wired and wireless connections
C: often used in homes and small businesses
D: uses satellite technology for connections
E: connects devices in a large geographic area
Answers
Answer:
A, B and C are correct
Explanation:
A : yes, they did use ethernet cables.
B : Lan networks connected via wires are called , "LAN" and LAN networks that connect to devices wirelessly are called, "WLAN" (Wireless Local Area Networks).
C : LAN networks are a type of network that is based in a small geographical area, therefore, it can be used in homes and small businesses.
Statements that can be considered to be true about local area networks in this question are;
A: traditionally used Ethernet cables to connect devices
B: can include wired and wireless connections
C: often used in homes and small businesses
Local area network can be regarded as is group of two or more connected computers which are positioned in a small geographic area, it could just a small building.This connection can be a wired connection, it can also be a wireless connection.Example if this network is Home networks ,another one is small business networks.
Therefore, option A,BC are all correct.
Learn more at:
https://brainly.com/question/22245838?referrer=searchResults
Can someone gift me V-Bucks? Please! If not, can u tell me how to get V-Bucks?
Answers
Explanation:
yeah sure are u boy or girl??
I do daily 5 gift card giveaway!!!..:)
Answer:
Explanation:
The only way I know is to buy V-bucks
Assignment 6: Animation for edhesive help please!!!!!!
Answers
I am here to offer guidance and support with your animation task! Please provide me with more information regarding what kind of assistance you require, including any specific animation program or coding language you're utilizing.
When it comes to creating animations, there are a variety of software tools and coding languages that can be utilized. Some popular animation software includes Adobe Animate, Toon Boom Harmony, and Blender. Adobe Animate is widely used for creating 2D animations, while Toon Boom Harmony is a popular choice for professional 2D and 3D animation projects. Blender is a free and open-source software that can be used to create 3D animations and visual effects.
In addition to software tools, there are also coding languages that can be used for animation, such as JavaScript, HTML5, and CSS3. JavaScript is used to create interactive animations for websites, while HTML5 and CSS3 can be used to create simple animations for websites and mobile applications.
Understanding which software or coding language you're using is crucial to providing relevant assistance for your animation project.
Learn more about animation here: https://brainly.com/question/22722118
#SPJ4
Which best describes most television in the 1940’s and 1950’s? A. 24 hour B. Cable C.black and white D. Color
Answers
the answer is C) black and white
Based on your prior knowledge, match each civilization to the region it occupied.

Answers
Answer: Inca- South America
Aztec - Meso America
Explanation:
Answer:Ladies and gents and all the nonbinary people out there, darlings the anwser is
Mesoamerica: Aztec
South America: Inca
Explanation:I just did it and got it right!
i'm sure u guys don't actually want an explanationLMFAOOO
virtual conections with science and technology. Explain , what are being revealed and what are being concealed
Answers
Some people believe that there is a spiritual connection between science and technology. They believe that science is a way of understanding the natural world, and that technology is a way of using that knowledge to improve the human condition. Others believe that science and technology are two separate disciplines, and that there is no spiritual connection between them.
What is technology?
Technology is the use of knowledge in a specific, repeatable manner to achieve useful aims. The outcome of such an effort may also be referred to as technology. Technology is widely used in daily life, as well as in the fields of science, industry, communication, and transportation. Society has changed as a result of numerous technological advances. The earliest known technology is indeed the stone tool, which was employed in the prehistoric past. This was followed by the use of fire, which helped fuel the Ice Age development of language and the expansion of the human brain. The Bronze Age wheel's development paved the way for longer journeys and the development of more sophisticated devices.
To learn more about technology
https://brainly.com/question/25110079
#SPJ13
When oversubscribing threads, not all threads are simultaneously executing.true or false
Answers
True. When oversubscribing threads, not all threads are simultaneously executing.
When a programme produces more threads than the computer's available cores or processors, it is known as oversubscription. Due to the constrained resources, this may result in a situation where not all threads can run concurrently. As a result, the operating system must control the threads and plan their execution on the resources that are available. This may result in resource contention and context switching, which might have an adverse effect on programme performance and add delay. Therefore, when a programme oversubscribes threads, not all threads are guaranteed to be running concurrently.
learn more about processors here:
https://brainly.com/question/31199196
#SPJ11
define computer software
Answers
Answer:
It is any program on a computer that you cannot touch or clean by yourself. EX: Windows.
Have A Nice Day!
mary wants to send a message to sam in such a way that only sam can read it. which key should be used to encrypt the message? answer sam's public key mary's public key sam's private key mary's private key
Answers
Sam"s public key is the correct option. A type of encryption known as symmetric encryption uses a single secret key to both encrypt and decrypt digital data.
Symmetric cryptography is one type of encryption (also known as secret key cryptography or private key cryptography). Symmetric cryptography is best suited for bulk encryption because it is much faster than asymmetric cryptography. Symmetric cryptography uses a shared key between both parties (which is kept secret). Asymmetric encryption uses a pair of public key and a private key to encrypt and decrypt messages when communicating, as opposed to symmetric encryption, which uses a single key that must be shared among the individuals who need to receive the message.
Learn more about encryption here-
https://brainly.com/question/17017885
#SPJ4
Which is not an element of photography? a Cropping b Height c Directional Lighting d Framing
Answers
Answer: Cropping
Explanation:
the answer is "cropping" as this is done with editing, not while shooting.
Tell me 2-6 computer parts that are inside a computer.
Spam answers will not be accepted.
Answers
Answer:
Memory: enables a computer to store, at least temporarily, data and programs.
Mass storage device: allows a computer to permanently retain large amounts of data. Common mass storage devices include solid state drives (SSDs) or disk drives and tape drives.
Input device: usually a keyboard and mouse, the input device is the conduit through which data and instructions enter a computer.
Output device: a display screen, printer, or other device that lets you see what the computer has accomplished.
Central processing unit (CPU): the heart of the computer, this is the component that actually executes instructions.
Explanation:
Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
how can green computing be implemented in an organization? answer unselected by relocating certain divisions to different areas of the world, depending upon their computing power needs unselected by using virtualization to replace hundreds of individual servers with just a few powerful mainframe computers unselected by replacing energy-draining mainframes with more energy-efficient desktop machines unselected by taking old computers to the landfill and replacing them with just a few mainframes
Answers
Green computing can be implemented in an organization by using virtualization to replace hundreds of individual servers with just a few powerful mainframe computers.
Green computing, also known as green technology, can be defined as the use of computers and other computing devices and equipment in energy-efficient and eco-friendly ways. Organizations that use green computing methods often deploy energy-efficient central processing units (CPUs), peripherals, power systems, and servers. Organizations that use green computing methods also focus on reducing resource use and properly disposing of physical and electronic waste (e-waste).
Companies that use green computing strategies can include the following steps:
Remote work.Smart technology. Upgrade and rearrange the data center. Power down. Strategic scheduling. Display selection. Computer selection.Power management. Temperature check. E-waste.Alternative energy.Learn more about green computing here https://brainly.com/question/14491844
#SPJ4
In the TCP/IP stack, the ____ layer is concerned with physically moving electrons across a medium.
a. Internet c. Transport
b. Network d. Application
Answers
In the TCP/IP stack, the b.network layer is concerned with physically moving electrons across a medium.
The data link layer is responsible for encapsulating the data from the network layer into frames that can be transmitted over the physical medium. The network layer is the layer above the data link layer and is responsible for routing data packets between hosts over a network. It uses protocols such as IP to provide logical addressing, routing, and fragmentation of data packets.
Therefore, the network layer is not concerned with physically moving electrons across a medium, but rather with routing and delivering data packets between hosts in a network.
So the correct answer is b.network.
Learn more about network layer: https://brainly.com/question/30264898
#SPJ11
What is the primary objective of the HIPAA security Rule?
Answers
The primary objective of the HIPAA (Health Insurance Portability and Accountability Act) Security Rule is to protect the confidentiality, integrity, and availability of electronic protected health information (ePHI).
The HIPAA Security Rule sets standards for safeguarding sensitive health information in electronic form. Its main goal is to ensure that covered entities, such as healthcare providers, health plans, and healthcare clearinghouses, implement appropriate security measures to protect the privacy and security of individuals' health information. The Security Rule establishes specific administrative, physical, and technical safeguards that organizations must implement to secure ePHI against unauthorized access, use, and disclosure.
By adhering to the HIPAA Security Rule, covered entities are expected to implement comprehensive security programs, conduct regular risk assessments, develop policies and procedures, provide employee training, and employ security measures such as access controls, encryption, and audit controls. Ultimately, the Security Rule aims to enhance the overall security posture of the healthcare industry and safeguard individuals' sensitive health information in electronic form.
learn more about "Security":- https://brainly.com/question/28004913
#SPJ11
one security component that doubles as a network component
Answers
Answer:
is the sentence above the question?
Answer:
It is to enter the site and then it will protect you in terms of form and appearance, and so on as required
how are you going to give first aid to the farmer?
Enumerate the steps. 10 pnts
Answers
Ive seen this on another website I think its 1. Assess the situation. Assess the situation and check for any potential dangers to yourself, bystanders or the patient. 2. Plan for interventions. Get help: 3.Implement first aid. 4.Evaluate the situation.
Answer:
You get a first aid kit and give him bandages
Explanation:
Here are the multiplication facts for nine.
Nine, 18, 27, 36, 45, 54, 63, 72, 81, 90
print 3 numbers before asking a user to input an integer

Answers
Answer:
you can use an array to do this
Explanation:
(I've written this in java - I think it should work out):
Scanner input = new Scanner(System.in);
System.out.println("Enter an integer: ");
int userInt = input.nextInt();
int[] array = new int[userInt - 1];
for(int i = userInt-1; i < userInt; i--)
System.out.println(array[i]);
Write a function "get_wins" that takes the WSU game data and a team name as input, and it returns a list of tuples that includes the years and scores of each game WSU played and won against that team. For example, get_wins (wsu_games, 'UTAH') returns [(2018, (28, 24))] #WSU played 4 games with 'UTAH' but won only the 2018 game get_wins(wsu_games, 'STAN') returns [(2018, (41, 38)), (2019, (49, 22)), (2021, (34, 31))] #WSU played 3 games with 'STAN' and won all 3 games Your function definition should not use loops or recursion but use the Python map, reduce, and/or filter functions. You may define and call helper (or anonymous) functions, however your helper functions should not use loops or recursion. You cannot use all_games function you defined in problem 1. You will not get any points if your solution (or helper functions) uses a loop. If you are using reduce, make sure to import it from functools.
Answers
To write the "get_wins" function, you can use the filter function along with a lambda function. Here's a possible implementation:
```python
from functools import reduce
def get_wins(wsu_games, team_name):
# Filter the list of games by the given team name and if WSU won the game
filtered_games = filter(lambda game: game[1] == team_name and game[2][0] > game[2][1], wsu_games)
# Use a map function to create a list of tuples with the years and scores
result = list(map(lambda game: (game[0], game[2]), filtered_games))
return result
```
This function first filters the wsu_games list by checking if the second element (the team name) matches the input team_name and if WSU won the game (the first score is greater than the second). It then uses the map function to create a list of tuples containing the years (first element) and scores (third element) of the filtered games.
To know more about Lambda Function, click here:
https://brainly.com/question/30904350
#SPJ11
If the primary voltage of a transformer is 230V and the primary coil is 80. Calculate the secondary voltage when the secondary turn is 160. *Ans 460 volts*
Answers
Answer:
\(V_{out} = 460\)
Explanation:
From your question, you already posted the answer
However, I'll give the steps to get the answer
Given
\(Primary\ Voltage = 230V\)
\(Primary\ Coil = 80\)
\(Secondary\ Coil = 160\)
Required
Secondary Voltage
The relationship between the primary voltage, secondary voltage, turns of primary coil and secondary coil is as follows;
\(\frac{V_{out}}{V_{in}} = \frac{N_{s}}{N_{p}}\)
Where
\(V_{in} = Primary\ Voltage = 230V\)
\(V_{out} = Secondary\ Voltage = ??\)
\(N_{p} = Primary\ Coil = 80\)
\(N_{s} = Secondary\ Coil = 160\)
Substitute these values in the formula above;
\(\frac{V_{out}}{V_{in}} = \frac{N_{s}}{N_{p}}\)
becomes
\(\frac{V_{out}}{230} = \frac{160}{80}\)
\(\frac{V_{out}}{230} = 2\)
Multiply both sides by 230
\(230 * \frac{V_{out}}{230} = 2 * 230\)
\(V_{out} = 2 * 230\)
\(V_{out} = 460\)
Hence, the secondary voltage is 460 Volts
Answer:
460 volts
Explanation: hope this helps :)
terrance is trying to explain industrial espionage to a group of new security techs. what is the ultimate goal of espionage?
Answers
The ultimate goal of industrial espionage is to acquire confidential information, trade secrets, competitive intelligence, and other forms of valuable data from businesses, organizations, and governments.
What is espionage?Espionage is the practice of spying or using covert means to gather information, usually involving the use of a government or organization to obtain confidential information from another government or organization. It is a very old practice, used by governments and organizations to obtain information on their adversaries and gain an advantage. Espionage can involve the use of intelligence, surveillance, interception of communication, and infiltration of an individual or organization. Espionage activities can be either legal or illegal depending on the circumstances. It is an important tool to gather information and protect a state or organization from its enemies. Espionage is also used for economic and industrial espionage, which is illegal in most countries.
To learn more about espionage
https://brainly.com/question/28143545
#SPJ4
Safety Rules Criss-Cross Puzzle
15
Across
2. Report all equipment
that is out of
to the
1. Observe all safety
3. Never use equipment without
6. Make sure to save and close all your
application.
7. Sit in the chair in an
9. Playing or running around the room is not
10. Never insert a
computer.
13. Cutting blades should be directed
teacher.
4. When using the
keep your
fingers away from the
area where the staples
come out.
5. No student will be
allowed to
a
machine until he has
been instructed in its
proper use.
8. Never eat or drink in
the
11. Never throw, toss or
pitch
to
another person.
12. When cut or injured
report to the
at once.
14. Avoid
backwards in chairs.
15. Keep your
Down
listed on the equipment.
off
other people and don't
talk to them while they
are operating a machine.
with the individual
position.
object in the outlets at the back of the
from the body.
Answers
hy does payments constitute such a large fraction of the FinTech industry? (b) Many FinTech firms have succeeded by providing financial services with superior user interfaces than the software provided by incumbents. Why has this strategy worked so well? (c) What factors would you consider when determining whether an area of FinTech is likely to tend towards uncompetitive market structures, such as monopoly or oligopoly?
Answers
(a) lengthy and complex processes for making payments (b) legacy systems and complex interfaces (c) regulatory requirements and substantial initial investment, can limit competition
(a) Payments constitute a significant portion of the FinTech industry due to several factors. First, traditional banking systems often involve lengthy and complex processes for making payments, leading to inefficiencies and higher costs. FinTech firms leverage technology and innovative solutions to streamline payment processes, providing faster, more secure, and convenient payment options to individuals and businesses. Additionally, the rise of e-commerce and digital transactions has increased the demand for digital payment solutions, creating a fertile ground for FinTech companies to cater to this growing market. The ability to offer competitive pricing, improved accessibility, and enhanced user experience has further fueled the growth of FinTech payment solutions.
(b) FinTech firms have succeeded by providing financial services with superior user interfaces compared to incumbents for several reasons. Firstly, traditional financial institutions often have legacy systems and complex interfaces that can be challenging for users to navigate. FinTech companies capitalize on this opportunity by designing user-friendly interfaces that are intuitive, visually appealing, and provide a seamless user experience. By prioritizing simplicity, convenience, and accessibility, FinTech firms attract and retain customers who value efficiency and ease of use. Moreover, FinTech companies leverage technological advancements such as mobile applications and digital platforms, allowing users to access financial services anytime, anywhere, further enhancing the user experience.
(c) Several factors contribute to the likelihood of an area of FinTech tending towards uncompetitive market structures such as monopoly or oligopoly. Firstly, high barriers to entry, including regulatory requirements and substantial initial investment, can limit competition, allowing a few dominant players to establish market control. Additionally, network effects play a significant role, where the value of a FinTech service increases as more users adopt it, creating a competitive advantage for early entrants and making it challenging for new players to gain traction. Moreover, data access and control can also contribute to market concentration, as companies with vast amounts of user data can leverage it to improve their services and create barriers for potential competitors. Lastly, the presence of strong brand recognition and customer loyalty towards established FinTech firms can further solidify their market position, making it difficult for new entrants to gain market share.
To learn more about technology click here: brainly.com/question/9171028
#SPJ11
In how many ways can we select a chairperson, vice-chairperson, secretary, and treasurer from a group of 12 persons?
Answers
There are 11,880 ways to select a chairperson, vice-chairperson, secretary, and treasurer from a group of 12 persons.
What is permutation?The number of possible arrangements for a given set is calculated mathematically, and this process is known as permutation. Simply said, a permutation is a term that refers to the variety of possible arrangements or orders. The arrangement's order is important when using permutations.
We need to elect a chairperson, vice chairperson, secretary, and treasurer out of the 12 persons present. So, for a total of 12, we are choosing 4 people.
When we remove one person from these 12, we are left with 11 people. If we choose one more from the list of 11, that leaves us with 10. If we choose another person from the group of 10, that leaves nine.
12 \(*\) 11 \(*\)10 \(*\) 9 = 11880
These are all the various leadership arrangements that are conceivable.
The permutation approach is another way to resolve this.
nPr = (n - r) = n!
12!/(12 - 4)! = 12!/8! = 11880 ways
So, out of a group of 12, there are 11,880 options to choose the chairman, vice-chairperson, secretary, and treasurer.
To learn more about permutations refer to:
https://brainly.com/question/1216161
#SPJ4
Please! I need help matching this.
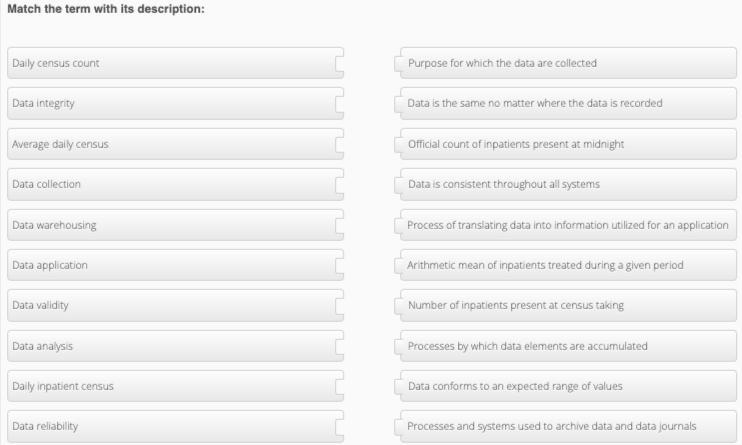
Answers
We can see here that matching the term with its description, we have:
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1