Which two actions should be used to address users with visual impairments? Ensure that pages support screen-reader apps. Provide text descriptions for images.
Answers
The two actions that should be used to address users with visual impairments are:
Ensure that pages support screen-reader apps. Provide text descriptions for images.Explanation:
1.Ensuring that pages support screen-reader apps: Screen readers are software programs that read the content of a website out loud for users with visual impairments. To make a website accessible for screen readers, it's important to use semantic HTML markup and provide alternative text for non-text content. This enables screen readers to properly interpret and convey the meaning of the content to the user. Additionally, it's important to ensure that the website is keyboard navigable, as some visually impaired users may rely on keyboard navigation to browse the web.
2.Providing text descriptions for images: Users with visual impairments rely on alternative text descriptions to understand the content of images on a website. By providing a brief, accurate, and descriptive text alternative for each image, users with visual impairments can understand the context and meaning of the image. It's important to note that the text alternative should be concise and descriptive, but not overly verbose or repetitive. Additionally, the text alternative should be included in the HTML markup of the webpage, so that it can be read by screen readers and other assistive technologies.
To know more about HTML markup click here:
https://brainly.com/question/27750672
#SPJ11
Related Questions
Native language is better than the English language. Describe
Answers
Answer:
One’s native language is simply the one they learned naturally, that their parents spoke to them at home. English is just one of many languages that people on this planet speak.As you may find that communicating in your native language in your country is easier than in any other language. Research showed that Words spoken in your native language in which you learned everything in the first place, are directly correlated with you subconscious.
Native language:
It is the language that a person is exposed to since birth or even during the key period. In most situations, native language refers to the language which a person learns in young life because it is spoken in the family and/or it is the language of the area where the kid lives. Native language, first language, and arterial languages are other terms for a native language and a first language.English language:
In the West Germanic language group, English is an Indo-European tongue. Even as the worlds most frequently used and generally understood foreign language, modern English is widely used in computer coding, worldwide commerce, and higher education.Through work prospects to the ability to communicate with people from all around the world, speaking English allows you to expand your horizons. Each trip is made more exciting by knowing the local language. However, the English Language can also benefit the patient.Comparison between Native and English language:
The language that is spoken at home by parents was called a person's native language. People on this globe speak a different language, including American, which is only one of them.Depending on where you live, one may find it easier t converse in your native tongue than in any other language.The unconscious responds instantly to the words uttered in our original tongue, which is where you learned everything. Our national tongues are well known to us all. The native language can be understood by others, we are unable to communicate with others who do not speak our original language.According to my perspective, so because the English language is a common language that everyone can easily learn and understand, it is better than the native language.
Learn more:
brainly.com/question/2029237

The first screen you see when you open Word 2016 is called the __???
Answers
Answer:
the first screen You see when you open word 2016 is called Recent screen
Answer:
its screen saver
Explanation:
Why can’t my sister downloaded games on her tablet she has tablet fire 8 hd amazon...Plz help and her tablet is on Spanish she only has videos she used to have games but not anymore someone plz help her


Answers
Answer:
It basically says that she needs a parents approval to download and play these games. The tablet was probably restricted because of her young age. So your dad has to go in with his account or whatever he used to download or allow those games.
Hope it Helps:)
You are a visitor at a political convention with n delegates; each delegate is a member of exactly one political party. It is impossible to tell which political party any delegate belongs to; in particular, you will be summarily ejected from the convention if you ask anyone. However, you can determine whether any pair of delegates belong to the same party by introducing them to each other. Members of the same political party always greet each other with smiles and friendly handshakes, member of different parties always greet each other with angry stares and insults.
Suppose more than half of the delegates belong to the same political party. Design a divide and conquer algorithm that identifies all member of this majority party and analyze the running time of your algorithm.
(Clarification: If we represent those delegates with array A[1..n), we cannot get result of A[i]< A[j]? or A[i] > A[j]? But we can get the result of A[i] == A[j]? in constant time.)
Answers
To solve this problem using a divide and conquer algorithm, we can employ a modified version of the majority voting algorithm. Here's how the algorithm works:
If the array A has only one delegate, return it as the majority party.
Divide the array A into two halves: left and right.
Recursively apply the algorithm to both halves, obtaining the majority party for each half.
If the majority party in the left half is the same as the majority party in the right half, return it as the overall majority party.
If the left and right halves have different majority parties, count the occurrences of each party in the entire array A.
Return the party with the most occurrences as the overall majority party.
This algorithm works because if the majority party exists, it must also be the majority party in at least one of the halves. By recursively dividing the array and comparing the majority parties in the subarrays, we can identify the overall majority party.
The running time of this algorithm can be analyzed as follows:
Let T(n) be the running time of the algorithm for an input size of n.
The base case, where n = 1, takes constant time, so T(1) = O(1).
Splitting the array into two halves takes O(1) time.
Recursively applying the algorithm to the left and right halves results in two recursive calls, each with input size n/2.
The time complexity of counting occurrences in step 5 is O(n).
The time complexity of comparing the majority parties in step 4 is also O(n).
Based on the above analysis, we can write the recurrence relation for the running time:
\(T(n) = 2T\left(\frac{n}{2}\right) + O(n)\)
By using the Master theorem (or other methods like the recursion tree method), we can determine that the overall running time of the algorithm is O(n log n).
Therefore, this divide and conquer algorithm can identify all members of the majority party in O(n log n) time.
To know more about conquer algorithm visit:
https://brainly.com/question/18720923
#SPJ11
When gathering information, which of the following tasks might you need to
performance
Answers
Answer:
Well you need to make sure your getting the proper information if it's from another person because some stuff isn't always true.
Explanation:
I hope this helps cause i really don't know at this point
How do you find a single number or name you want in a
large worksheet containing thousands of numbers and
names? Is it possible to replace a name or number with
some other name or number? How?
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
You can find a single number or name in a large worksheet containing thousands of numbers and names using the find and replacement feature in excel.
You can use Ctrl+F keyboard shortcut for finding and replacing features. When you press Ctrl+F, a dialog will get open, using this dialog, you can find the required number or name while entering in the search text box. Then, click on the Find button, if the worksheet matches the result, give you the matched result in the yellow highlighted color.
Also, you can use Ctrl+F to replace a name or number with some other name or number.
Alternatively, you can do this using the home tab, then find the option find and select under the editing group of commands.
Para que son importantes las tic [en la educacion?
Answers
Information and Communication Technologies (ICT) are very important tools in education. In this sense, ICT scan have a positive impact on teaching and student learning, as they allow the creation of new educational opportunities and experiences.
Below are some reasons why ICT is important in education:
Access to information: ICT sallow access to a wealth of information quickly and easily. Students can use the Internet to find educational resources, research materials and academic references to complement their training. Personalized learning: ICT sallow the creation of personalized and adaptive learning environments. Students can learn at their own pace and level, using digital tools that allow them to obtain immediate and personalized feedback on their performance. New ways of teaching: ICT allows the creation of new, more dynamic and interactive ways of teaching. Teachers can use digital tools such as videos, educational games, simulations and interactive activities to enrich students' learning experience. Fostering creativity and innovation: ICT can foster creativity and innovation in students, allowing them to create digital projects, multimedia presentations and other educational materials that allow them to express their ideas more effectively and visually.In conclusion, Acts are very important tools in education. They allow access to a wealth of information, the creation of personalized learning environments, the use of new ways of teaching and the promotion of creativity and innovation. It is important that teachers and students take full advantage of It to improve the quality of education and prepare for the digital world in which we live.
Lear More About Communication technologies
https://brainly.com/question/17998215
#SPJ11
When computer code encounters the word “if,” what does it do?
Answers
Answer:
It looks at the condition of the if() statement and determine whether the code inside its block should be run or not.
If the condition is true, run the code,
otherwise, skip that part of the code and continue.
Why is ROM used for in modern computers?
Answers
Answer:
Because ROM saves even after the computer is turned off
Explanation:
RAM doesnt function when the computer is off, ROM does.
Which tab is used to configure editing restrictions in Word 2016? Review References Security Developer
Answers
Answer:
Review Tab is the correct answer to the given question .
Explanation:
Giving the permission to file in word 2016
Click on the Review tab and select the restrict tab .Chose the option allow this type of editing .After that choose the option No changes .Pick the section of the document they want to authorize the adjustments.After that there are multiple option are seen select accordingly as user need and press ok button .Click on the start permission there is option is seen Start enforcement and press the button option start Enforcing Protection.After that feeding the password if the user need the password is in encrypt form then press encrypt option and click ok .If the user need to read the file
Click on the Review tab and select the restrict tab .After that choose the option "Stop Protection" .Giving the password you are feeding in the permission of file .Finally the user will edit the documentAnswer:
It's D developer!!!
Explanation:
Took the test and got it right!!!!!!!
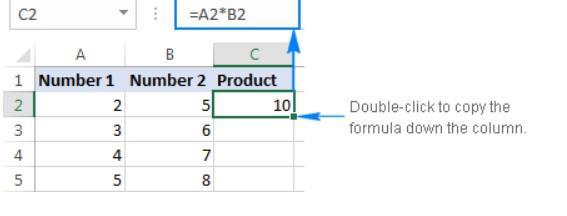
create a formula in the selected cell that multiplies the value in cell b2 of the current worksheet
Answers
To multiply two cells in Excel, use a multiplication formula like in the above example, but supply cell references instead of numbers. For example, to multiply the value in cell A2 by the value in B2, type this expression is A2*B2.
What do you under stand by Excel?
Microsoft's spreadsheet program Excel is a part of the Office family of products used for business purposes. Users can format, arrange, and compute data in a spreadsheet using Microsoft Excel.
To create formula in the selected cell follow these steps:
The PRODUCT function would be the quickest technique to multiply several cells or ranges.
Where number1, number2, etc. are numbers, cells or ranges that you want to multiply.
to multiply values in cells A2, B2 and C2, use this formula is PRODUCT(A2:C2)
To multiply the numbers in cells A2 through C2, and then multiply the result by 3, is PRODUCT(A2:C2,3)
Learn more about Excel click on this:
https://brainly.com/question/25863198
#SPJ4
Can you see who tries to access a password-protected file, but does not put in the password?
Answers
Yes/no
Explanation:
Depending on the person.
Yes, if your cousins,parents,etc have opened it.
No, if people like hackers have done it.
4.9 Code Practice: Question 1

Answers
total = 0
for x in range(3, 67, 3):
total += x
print(total)
I hope this helps!
The program sums all the values in a given range and assigns the total to the sum variable. The program is written in python 3 thus :
sum = 0
#initialize a sum variable, initialized as 0
for x in range(3, 67, 3):
#loop through the range taking a step of 3 after each iteration.
sum+= x
#add the iterated value to the sum variable after each iteration
print(sum)
#display the sum
A sample run of the program is attached
Learn more :https://brainly.com/question/14899725
Consider the following language: L= = {x € {a,b}*|x contains either aba or bab (or both)} example: ababaaa, babbbb, aaababababaaa, etc. Part(a) Give a NFA for L as a state transition diagram. Part(a) Give a DFA for L as a state transition diagram.
Answers
Part (a) - NFA for L as a state transition diagram:
The NFA for L can be constructed as follows:
- The initial state q0 has an ε-transition to state q1 and another ε-transition to state q4.
- From q1, there is a transition on symbol 'a' to state q2, and from q2, there is a transition on symbol 'b' to state q3.
- From q3, there is an ε-transition back to q1.
- From q4, there is a transition on symbol 'b' to state q5, and from q5, there is a transition on symbol 'a' to state q6.
- From q6, there is an ε-transition back to q4.
The final states are q3, q6, and any state that can be reached from either q3 or q6 by following ε-transitions.
Here is the state transition diagram for the NFA:
ε a ε
→q0 ---→q1 ---→q2 ---→q3←
| ↑ |
| | b
| ε |
↓ └────→
→q4 ---→q5 ---→q6 ---→q7←
ε b ε
Part (b) - DFA for L as a state transition diagram:
The DFA for L can be constructed using the subset construction method as follows:
- The initial state is the set {q0}.
- On symbol 'a', the set of reachable states is {q1, q4}. On symbol 'b', the set of reachable states is {q4}.
- On symbol 'a', the set of reachable states from {q1, q4} is {q2, q4}, and on symbol 'b', the set of reachable states is {q3, q4}.
- On symbol 'a', the set of reachable states from {q2, q4} is {q3, q4}, and on symbol 'b', the set of reachable states is {q3, q4}.
- On symbol 'a', the set of reachable states from {q3, q4} is {q3, q4}, and on symbol 'b', the set of reachable states is {q3, q5}.
- On symbol 'a', the set of reachable states from {q3, q5} is {q6}, and on symbol 'b', the set of reachable states is {q3, q4}.
- On symbol 'a', the set of reachable states from {q6} is {q3, q4, q7}, and on symbol 'b', the set of reachable states is {q3, q4}.
The final states are any set that contains q3 or q6.
Here is the state transition diagram for the DFA:
a b
→q0 ──→ q1,q4 ─→ q4
│ │
│ │
│ ↓
│ q3,q4
│ a │ b
↓ │ │ │
q2,q4 ──→ q3,q4 ←─┘
│ │ │
│ │ b │ a
│ ↓ ↓
└─ q3,q5 ← q6 ──→ q3,q4,q7
Know more about the state transition diagram click here:
https://brainly.com/question/13263832
#SPJ11
Kyra is teaching a photography class. She would like her students to share photos. She would also like the students to be able to review other students' photos and offer feedback. What technology should Kyra use?
a blog
a wiki
a domain
e-mail
Answers
Answer:
A blog.
Explanation:
A blog can be defined as an informative or discussion-based website that is updated regularly and published over the internet. The informations that are posted on a blog are usually done chronologically and it includes pictures, videos, music, movies, novels, etc.
In this scenario, Kyra is teaching a photography class. She would like her students to share photos, be able to review other students' photos and offer feedback.
Hence, the technology Kyra should use is a blog because it would avail the users (students) to post photos, make comments on blog posts and review items posted by others.
a computer program that copies itself into other software and can spread to other computer systems is called a software infestation. true false
Answers
Answer:False
Explanation:The software that copies itself is classified as malware
processes 0, 1, 2, 3 are executing concurrently. process 3 must execute after processes p0, p1, p2 finish their execution. there is no enforcement of order between the executions of process0, process1, process2. c) implement the required synchronization using minimum number of binary semaphores. give the initial value of each semaphore. d) implement the required synchronization using a minimum number of counting semaphore. give the initial value of each semaphore.
Answers
We can use 3 binary semaphores: semaphore S0, S1, and S2. S0, S1, and S2 are initially set to 1 and we can use 1 counting semaphore: semaphore C with an initial value of 3.
c) To implement the required synchronization using minimum number of binary semaphores, we can use 3 binary semaphores: semaphore S0, S1, and S2. S0, S1, and S2 are initially set to 1.
Process 0, 1, and 2 execute concurrently and signal semaphore S0, S1, and S2 respectively when they finish their execution. Process 3 waits on S0, S1, and S2 and only executes when all 3 semaphores have been signaled.
d) To implement the required synchronization using a minimum number of counting semaphores, we can use 1 counting semaphore: semaphore C with an initial value of 3.
Process 0, 1, and 2 execute concurrently and signal semaphore C when they finish their execution. Process 3 waits on semaphore C with a count value of 3 and only executes when the semaphore has been signaled 3 times.
Learn more about synchronization here:
https://brainly.com/question/15293990
#SPJ4
Case Project 2-1: The Differences Between IPv4 and IPv6 You are a network engineer for an IT consulting firm named F1IT. One of your clients, Beautivision, a chain of plastic surgery clinics with 80 locations nationwide, has asked you to prepare a proposal for implementing IPv6 in Beautivision’s corporate headquarters, its WAN network, and its clinic locations. In preparation, you need to create a one- to two-page memo that describes the main differences between IPv4 and IPv6. Write the memo to Mary Jane Newman, communications manager for Beautivision. When preparing the memo, keep in mind that Ms. Newman has some knowledge of information technology but is not an expert.
Answers
Answer:
Following are the difference to this question:
Explanation:
IPv4:
The \(IPv_4\) is uses the packet changed method, that is a Link Layer networks(like Ethernet). It has 4.3 billion addresses capacity. It uses the 32-bit logical device address, that written in decimal language. It is divided by 4 bytes E.g. 192.168.1.1
The host part and network part are 2 parts. For a network, the host part may vary, while for the entire subnet, the network part remains equal. The scheme of 232 addresses is available on application depends on security.
IPv6:
The IPv6 is used in the internet protocoland it is higher than IPv4. It can provide endless number Opf addresses, and use to solves the problem of IPv4 exhaustion and satisfies the demand for rising networking.
IPv4 Substitutor Built to meet more IP address requirements. In the Logical address of 128-bit Written hexadecimally and with colons divided, and the Space of 128 addresses are required. IPsec is an integrated security feature.
Design an email based on what you learned about email etiquette in this week’s lecture. Include all elements you think are appropriate for a professional email.
Answers
A professional email should include various elements to adhere to email etiquette. These elements consist of a clear and concise subject line, a formal greeting, a brief and focused message, proper grammar and punctuation, a professional closing, and appropriate attachments if necessary.
When designing a professional email, it is important to consider email etiquette guidelines. Start with a clear and concise subject line that reflects the purpose of the email. Begin the email with a formal greeting, addressing the recipient by their appropriate title and name. Keep the body of the email focused and brief, using proper grammar and punctuation. Use a professional and polite tone throughout the message. Conclude the email with an appropriate closing, such as "Sincerely" or "Best regards," followed by your name and contact information. If there are any necessary attachments, ensure they are properly labeled and referenced in the email. By following these elements, your email will demonstrate professionalism and enhance effective communication.
To learn more about professional email click here : brainly.com/question/30760750
# SPJ11
Application Casse
The Mentorship Program at TVH
Group Thermote & Vanhalst (TVH) is a global organization that spe- cializes in constructing and repairing forklift trucks. The organization's expansion presents Paul Sanders, HR Director at TVH, with a tough prob- lem. It doesn't have a system to capture, store, and leverage employees' knowledge. There is a massive inflow of young people who lack techni- cal know-how, and specialized knowledge is lost when older employees leave the company. In order to deal with this problem, Paul Sanders introduced a mentorship program. This program helps older employees transmit their knowledge and know-how to younger employees. Paul re- alizes that the transition to the mentoring system has not gone smoothly when he gets a letter from Freddy Jacobs, one of his most respected employees. Freddy challenges him by saying, "Lately we are doing noth- ing but explaining work processes to the young guys. Our own work has to be put aside, and why? Moreover, the young guy at pre-packing has never seen a forklift truck in his life, but he started off in charge of three older people. We have worked together successfully for more than 30 years, and | hope that you will deal correctly with this situation."
After Paul read the letter, he frowned. Experienced workers were putting a lot of effort into teaching newcomers the tricks of the trade, but the older workers were now becoming upset because of the career opportunities given to the newcomers. Paul believes that an insufficient transfer of knowledge is at the heart of many issues at TVH. How can he optimize his system to manage knowledge efficiently?
Questions
8-18. If you were Paul Sanders, how would you deal with the issues raised in the letter?
8-19. What would make the mentoring program a success? How would you define success and failure?
8-20. Under what circumstances would you choose these training processes?
Answers
8-18. If I were Paul Sanders, I would deal with the issues raised in the letter by:Acknowledging the situation and how it affects older employees and the entire organization.
Have a dialogue with Freddy Jacobs and the older employees about their concerns and possible solutions to address them.Update the mentoring program by taking into account the views of the older employees. The mentoring program could be amended to include mentoring committees made up of experienced workers from the different departments.
The committees would work with the younger employees to provide hands-on training and support on the job.8-19. A successful mentoring program should provide a platform where experienced employees can transfer their knowledge and skills to younger employees. Success can be measured by employee performance, reduced errors, and fewer accidents. In contrast, failure would be when the program does not achieve its objectives or employees do not benefit from the program.8-20.
To know more about employees visit:
https://brainly.com/question/29331800
#SPJ11
how graphical representation of spreadsheet data can be helpful in business
Answers
Answer: Business graphs are visual aids used to analyze data. They can make comparing multiple sets of data much easier, as sometimes trends and relationships are easily identified on the chart or graph. They also help to show the audience the data in a way that is easy to understand and remember.
Explanation:
what is robotic technology
Answers
Answer:
according to britannica :
"Robotics, design, construction, and use of machines (robots) to perform tasks done traditionally by human beings. ... Robots are widely used in such industries as automobile manufacture to perform simple repetitive tasks, and in industries where work must be performed in environments hazardous to humans"
Explanation:
A hacker wants to gain illegal Elizabeth owns a Mac and is not careful about what websites she visits, what links she clicks on, or what she downloads. She says that it is impossible for Macs to get viruses because the operating system is sandboxed. Is she correct? A. Yes, it is impossible for a Mac to become infected with any malware. B. No, a Mac can get a virus and be affected just as bad as a PC. C. No, a Mac can get a virus but it is not susceptible to any other type of malware. D. No, a Mac can still get viruses, but the viruses cannot get to the heart of the machine. Reset Next to Elizabeth owns a Mac and is not careful about what websites she visits, what links she clicks on, or what she downloads. She says that it is impossible for Macs to get viruses because the operating system is sandboxed. Is she correct? A. Yes, it is impossible for a Mac to become infected with any malware. B. No, a Mac can get a virus and be affected just as bad as a PC. C. No, a Mac can get a virus but it is not susceptible to any other type of malware. D. No, a Mac can still get viruses, but the viruses cannot get to the heart of the machine. Reset Next passwords for a popular online website. Where should they direct their attack? A. a bank B. a server C. a removable USB drive D. a laptop
Answers
Since Elizabeth says that it is impossible for Macs to get viruses because the operating system is sandboxed. The response is D. No, a Mac can still get viruses, but the viruses cannot get to the heart of the machine.
The place that they should direct their attack is option B. a server.
What is Mac's server name?Go to Apple menu > System Settings, select General from the sidebar, and then select About from the right-hand menu on your Mac. The name of your Mac's computer can be found at the top of the About settings page (you might need to scroll down).
Malware can infect a Mac computer. Macs are susceptible to malware and viruses. Even while Mac infections are less frequent than PC malware, Mac machines aren't completely shielded from online dangers by the security mechanisms built into macOS.
Note that Sandboxing is widely used to analyze untested or untrusted code and is intended to stop dangers from entering the network. In order to prevent infection or damage to the host computer or operating system, sandboxing keeps the code confined to a test environment.
Learn more about viruses from
https://brainly.com/question/26128220
#SPJ1
How can presentation software be used in a business or professional setting? Choose all that apply.
Answers
Answer:
Presentations are commonly projected onto a whiteboard a large screen.
Slides can also be printed out onto clear acetate and used with a overhead projector (0HP) to project the contact onto a screen. If this method is used each acetate side usually has to be replaced my newly.
Presentations can also be set up to play through a large did you go display in reception areas of the hotels, schools, businesses etc.
Answer:
The answers are A, B, and C
Explanation:
to automate the ticket-purchasing process at movie theaters through a kiosk
to teach lessons to high school students
to deliver a sales presentation to clients
a collection of logic gates that transforms a set of binary inputs into a set of binary outputs
Answers
A collection of logic gates, also known as a digital circuit, is an interconnected assembly of gates that perform specific functions
These gates, including AND, OR, and NOT, are fundamental building blocks of digital systems, such as computers and calculators.
By processing a set of binary inputs (0s and 1s), the logic gates transform them into a set of binary outputs based on predefined rules. The output is generated by following the Boolean logic associated with each gate type.
Digital circuits can range from simple arrangements, like adders and encoders, to complex systems like microprocessors, all relying on the efficient manipulation of binary information to execute tasks and perform calculations.
Learn more about logic gates at
https://brainly.com/question/16662101
#SPJ11
most computers have temporary holding areas called __________.
Answers
Answer:
Random Access Memory (RAM)
what is a spreadsheet
Answers
which information is not included in a material safty data sheet?
Answers
Answer:
The MSDS lists the hazardous ingredients of a product, its physical and chemical characteristics (e.g. flammability, explosive properties), its effect on human health, the chemicals with which it can adversely react, handling precautions, the types of measures that can be used to control exposure, emergency
concept map of diabetes and obesity including interventions, goals
and subjective and objective data
Answers
This concept map provides an overview of the relationships between diabetes, obesity, interventions, goals, and subjective/objective data. It is important to note that the specific interventions, goals, and data may vary depending on individual patient characteristics and healthcare provider recommendations.
[Diabetes and Obesity Concept Map]
Interventions:
- Diet modification
- Regular physical activity
- Medication management
- Weight management programs
- Blood glucose monitoring
- Education on healthy lifestyle habits
- Behavioral therapy
- Support groups
Goals:
- Achieve and maintain a healthy body weight
- Control blood glucose levels within target range
- Reduce the risk of complications related to diabetes and obesity
- Improve overall physical fitness and cardiovascular health
- Enhance self-management skills and adherence to treatment plans
Subjective Data:
- Patient's self-reported symptoms (e.g., increased thirst, frequent urination, fatigue)
- Dietary habits and preferences
- Patient's knowledge and understanding of diabetes and obesity
- Perception of body image and self-esteem
- Patient's motivation and readiness for lifestyle changes
Objective Data:
- Body mass index (BMI)
- Blood glucose levels (fasting and postprandial)
- HbA1c levels (glycated hemoglobin)
- Waist circumference
- Blood pressure readings
- Lipid profile (cholesterol, triglycerides)
- Physical fitness assessment (e.g., exercise tolerance, cardiovascular endurance)
To know more about Map visit-
https://brainly.com/question/32667763
#SPJ11
hiiiiiiiiihwdawdfgthnythgrfergthyjuhgfd
Answers
Answer:
Your answer would be gas.
Explanation:
Steam is just water just evaporated.