Which of the following is NOT considered file metadata?
a. filename
b. file creation date
c. file contents
d. file attributes
Answers
The one that is not considered file metadata is the filename. The correct option is a.
What is metadata?File metadata can be thought of as supplementary information about a file that is carried along with it and makes it easier to use and find. It's not the document or photo itself, but rather information about it, such as the file's name, thumbnail image, or creation date.
Metadata, also known as data that describes other data, is structured reference data that aid in the sorting and identification of attributes of the material it describes.
Therefore, the correct option is a. filename.
To learn more about metadata, refer to the link:
https://brainly.com/question/17286145
#SPJ1
Related Questions
When making routine transponder code changes, pilots should avoid inadvertent selection of which code?
Answers
When making routine transponder code changes, pilots should avoid inadvertent selection of code. 7700.
What are the transponder code that pilot should avoid?Under normal as well as non-emergency operations, it is very essential for pilot to make sure he avoid using the transponder codes of 7500, as well as 7600, and 7700.
Especially while switching codes, It is easy in switching by pilot to go to of these 3 codes on accident.
In this case, When making routine transponder code changes, pilots should avoid inadvertent selection of code. 7700.
Learn more about general emergency on:
https://brainly.com/question/14331925
#SPJ1
why do most operating systems let users make changes
Answers
By these changes you most likely are thinking of the term 'Over Clocking'
Over Clocking is used on most Operating Systems to bring the item your over clocking to the max.
Over Clocking; is mostly used for Crypto mining and gaming.
I need help please hurry!!!!!!! jay works in the it department. his main responsibility at work is to keep all equipment working. he needs to know what maintenance to perform and when. he should _____.
inventory all equipment
copy the user's manual and distribute it to all the employees
read the manuals
update the software in the office
establish the frequency of maintenance tasks
identify individuals to complete the tasks
set up auto reminders
list the maintenance tasks
create a log to document maintenance
Answers
Jay is employed with the it division. Maintaining the functionality of all equipment is his primary duty at work. He must understand what upkeep to execute and when to decide to perform maintenance.
He needs to decide how often to perform maintenance. The number of jobs that must be completed in a certain amount of time is referred to as maintenance frequency. Its periodicity can also vary based on the set time, from daily to weekly. Work equipment comprises a working platform, fall arrest devices, and any gear, computers, apparatus, tools, or installations used exclusively or mostly for work-related purposes. Task analysis examines how a task is carried out and includes a thorough description of both manual and mental processes, the lengths of the task and its elements, and task frequency.
Learn more about computers here
https://brainly.com/question/20414679
#SPJ4
Translate the following ASCII codes into strings of characters by interpreting each group of eight bits as an ASCII character.
a. x48656c6c6f21
b. x68454c4c4f21
c. x436f6d70757465727321
d. x4c432d32
Answers
The Translations are,
(a) Hello!(b) hELLO!(c) Computers!(d) LC-2What is ASCII codes?There are 128 characters in the 7-bit character system known as ASCII. It includes the letters and numerals from 0 to 9, as well as certain special characters and the upper and lower case English letters from A to Z. ASCII is the foundation for all character sets used in HTML, on the Internet, and in contemporary computers. American Standard Code for Information Interchange, also known as ASCII, is a character encoding standard for electronic communication. Text is represented by ASCII codes in computers, telecommunications systems, and other hardware. The lowercase alphabet has an ASCII value between 97 and 122. Additionally, the capital alphabet has an ASCII value between 65 and 90.The Translations are,
(a) Hello!(b) hELLO!(c) Computers!(d) LC-2To learn more about ASCII codes refer to:
https://brainly.com/question/28480297
#SPJ4
write a function is unique that accepts a dictionary from strings to strings as a parameter and returns true if no two keys map to the same value
Answers
When you have a Python dictionary and a function that you want to use on it, you can utilize this technique.
The function's name is the value of a new element that you add to the dict. When you're ready to use the function, you call it indirectly by using the dict element rather than the function's actual name.
def is_sub_dict(dict1, dict2):
one = dict1.keys()
two = dict2.keys()
for x in one:
if x in two:
if dict1[x] == dict2[x]:
pass
else:
return False
else:
return False
return True
Learn more about function here-
https://brainly.com/question/28939774
#SPJ4
You hide three worksheets in a workbook and need to unhide them. How can you accomplish this?.
Answers
Answer:
Nevermind, I didn't get that this was for a computer.
Explanation:
To unhide the worksheets in a workbook. Choose View > Unhide from the Ribbon. The PERSONAL XLSB workbook and the book are hidden. After selecting the worksheet to reveal it, click OK.
What is a worksheet?Created in Excel, a workbook is a spreadsheet programme file. One or more worksheets can be found in a workbook. Cells in a worksheet (sometimes referred to as a spreadsheet) can be used to enter and compute data. Columns and rows have been used to arrange the cells.
Choose the worksheets you want to conceal. How to choose a worksheet.Click Format > under Visibility > Hide & Unhide > Hide Sheet on the Home tab.The same procedures must be followed, except choose Unhide to reveal worksheets.Therefore, steps are written above for unhiding a workbook.
To learn more about the worksheet, refer to the link:
https://brainly.com/question/15843801
#SPJ2
middle of test help pls
Which of the following could be a possibility in the future?
A voice-activated computers
B computerized glasses
C holographic messages
D computerized watches
Answers
Answer:
I'm thinking d
Explanation:
i dont think we are advanced enough to do a,b, or c.
so imma say d
Answer:
all
Explanation:
Write a program to find the Perimeter and Semi- perimeter of a traingle.(Python)
Answers
This Python program takes user input of the sides of a triangle, calculates its perimeter and semi-perimeter, and displays the results. The code is mentioned below.
Here is a Python program to find the perimeter and semi-perimeter of a triangle:
# input the sides of the triangle
triangleSide1 = float(input("Put the first side's length: "))
triangleSide2 = float(input("Put the second side's length: "))
triangleSide3 = float(input("Put the third side's length: "))
# calculate the perimeter
perimeter = triangleSide1 + triangleSide2 + triangleSide3
# calculate the semi-perimeter
s = perimeter / 2
# print the results
print("Perimeter of the triangle = ", perimeter)
print("Semi-perimeter of the triangle = ", s)
In this program, we first take input from the user for the lengths of the sides of the triangle. We then calculate the perimeter by adding the lengths of all three sides. The semi-perimeter is then calculated by dividing the perimeter by 2.
Finally, the program prints the values of the perimeter and semi-perimeter.
This program prompts the user to enter the length of the three sides of a triangle, stores them as triangleSide1, triangleSide2, and triangleSide3, respectively. It then calculates the perimeter of the triangle by adding the lengths of all three sides, and stores the result in the variable perimeter.
The semi-perimeter of a triangle is half of its perimeter, so we calculate it by dividing the perimeter variable by 2 and storing the result in the variable s. Finally, the program prints out the values of the perimeter and s variables to display the results to the user.
Learn more about Python program here:
https://brainly.com/question/19792191
#SPJ4
To create a minimal Linux installation, for a bastion host for example, which mode should you install the operating system in?
Answers
Answer:
"Text" is the right approach. A further explanation is given below.
Explanation:
Visitors understand exactly unless the whole dashboard or window becomes black, you're throughout text format, demonstrating characters. Predominantly, a text-mode authentication display shows several other additional data about everything from the computer system you're continuing to operate on, this same signature including its device, and perhaps a encourage desperately looking for someone like you to sign this into Linux.how to convert bits to bytes
Answers
To convert bits to bytes, you need to divide the number of bits by 8. This is because there are 8 bits in a byte. For example, if you have 16 bits, you would divide 16 by 8 to get 2 bytes. Here is the formula:
Number of bytes = Number of bits / 8
So, if you want to convert 32 bits to bytes, you would do the following calculation:
32 bits / 8 = 4 bytes
Therefore, 32 bits is equal to 4 bytes.
We can say that 1 byte is 8 bits, therefore, 1 byte can represent 28 (256) different states.
For more information about bit and byte, visit:
https://brainly.com/question/28261277
#SPJ11
2. Think about an application (more than 150 lines of codes) to use
the join() method. It should be an interesting practical
application. The boring application will reduce your scores.
Answers
An interesting practical application of the join() method could be a messaging system where it is used to concatenate the sender's name and message content, allowing for a readable display of the chat history.
One interesting practical application of the join() method in Python could be a messaging system. Let's consider a scenario where multiple users send messages to a common chat room. Each message includes the sender's name and the content. To display the chat history in a readable format, the join() method can be used.
Here's a brief outline of the application:
1. Create a list to store the messages.
2. Implement a function to add messages to the list, taking the sender's name and message content as input.
3. Whenever a new message is received, call the add_message() function to append it to the list.
4. To display the chat history, iterate over the list of messages and use the join() method to concatenate the sender's name and message content with appropriate formatting.
5. Print the formatted chat history to the console or display it in a graphical user interface.
By utilizing the join() method, you can join the sender's name and message content into a single string, making it easier to present the chat history in a coherent manner.
This application not only demonstrates the practical usage of the join() method but also showcases its importance in creating a user-friendly messaging system.
Learn more about concatenate:
https://brainly.com/question/16185207
#SPJ11
What values are stored in the list numList? numberlist) for (10; 110; 1.) if (1X2 - 0) numList[1]. a. (1,2,3,4,5) b. (0,2,4,6,8) c. (2.4, 6, 8, 10) d. (1,3,5,7.9)
Answers
The values stored in the list numList are (10, 11, 12, 13, ..., 109, 110) as the for loop iterates from 10 to 110 with a step size of 1. The condition "if (1X2 - 0)" is not relevant in determining the values stored in the list.
Therefore, the answer is not any of the options provided.
The values stored in the list numList are given in the code snippet provided. Unfortunately, the code snippet you provided seems to be incomplete and contains errors. Please provide the complete, corrected code so I can accurately determine the values stored in numList and help you with your question.
to know more about numList here:
brainly.com/question/31130405
#SPJ11
Which of the following replacements for < MISSING STATEMENTS > will result in the list of highScores having all elements with values greater than or equal to 70?
IF (s >= 70)
{
APPEND(highScores, s)
}
IF (scores >= 70)
{
APPEND(highScores, scores)
}
IF (s >= 70)
{
APPEND(highScores, scores)
}
Answers
To have all the elements of the highScores with values greater than or equal to 70, we should use the code: IF (s >= 70){APPEND(highScores, s)}. Therefore, Option A is correct.
Option B is incorrect because "scores" is not defined. The variable declared was "s."Option C is also incorrect because we should only append the score when it is greater than or equal to 70, and not the variable "scores." So, the correct replacement is: IF (s >= 70){APPEND(highScores, s)}
The code snippet will ensure that only the score greater than or equal to 70 is appended to the highScore list.
For a program to append all scores greater than or equal to 70 to the highScore list, we can use a conditional statement. This is because we need to append a value to the highScore list if only it meets a particular condition.
In the given code snippets, we have three options, and we need to choose the option that will append only the scores greater than or equal to 70 to the highScore list.
In option A, if the score is greater than or equal to 70, the score will be appended to the highScore list.
For option B, we cannot use "scores" because the variable declared was "s." Therefore, option B is incorrect. For option C, if s is greater than or equal to 70, we will append "scores" instead of the score. This means that we will be appending another variable instead of the score, which is not what we want.
To summarize, we use a conditional statement to determine if a score meets a particular condition before appending it to the highScore list. In this case, the condition is that the score must be greater than or equal to 70. Therefore, the correct answer is option A.
Learn more about elements at: https://brainly.com/question/28565733
#SPJ11
beta measures the total risk of an individual security.
Answers
Beta measures the volatility or systematic risk of an individual security in relation to the overall market. It helps investors assess the risk associated with a security and make informed investment decisions.
Beta is a financial metric used to measure the volatility or systematic risk of an individual security in relation to the overall market. It provides insights into how much the price of a security tends to move in relation to the movement of the market as a whole.
Beta is calculated by comparing the historical price movements of the security to the historical price movements of a benchmark index, such as the S&P 500. A beta value of 1 indicates that the security tends to move in line with the market. A beta greater than 1 suggests that the security is more volatile than the market, meaning it tends to experience larger price swings. On the other hand, a beta less than 1 indicates that the security is less volatile than the market, implying smaller price fluctuations.
Investors use beta as a tool to assess the risk associated with a particular security. A higher beta implies higher risk, as the security is more sensitive to market movements. Conversely, a lower beta suggests lower risk, as the security is less affected by market fluctuations. It is important to note that beta only measures systematic risk, which is the risk that cannot be diversified away through portfolio diversification. It does not capture the idiosyncratic or company-specific risk.
Understanding beta helps investors make informed decisions about their investment portfolios. By considering the beta of a security, investors can assess its risk profile and determine how it fits within their overall investment strategy.
Learn more about Beta measures
https://brainly.com/question/10593001
#SPJ11
The statement given "beta measures the total risk of an individual security." is false because beta does not measure the total risk of an individual security, but rather it measures the systematic risk or volatility of a security in relation to the overall market.
Beta is a financial metric used in investment analysis to assess the sensitivity of a security's price movements in relation to the broader market. It quantifies the extent to which the price of a security tends to move in response to market fluctuations. A beta value greater than 1 indicates that the security is more volatile than the market, while a beta less than 1 suggests lower volatility.
However, beta alone does not capture the total risk of an individual security, as it does not account for unsystematic or idiosyncratic risks specific to the security itself, such as company-specific events or management decisions. To assess the total risk of an individual security, other measures such as standard deviation or variance may be used in conjunction with beta.
""
beta measures the total risk of an individual security.
true
false
""
You can learn more about financial metric at
https://brainly.com/question/28146445
#SPJ11
combine like terms to create an eqivalent expresion. -1/2(-3y+10)
Answers
Answer: Google doesn't have the answer.
Explanation:
I tried
Question 1 of 10
Which step happens first after a switch receives a message that includes a
MAC address?
OA. The switch receives a reply from the message's receiving device.
B. The switch sends the message to a random device on the
network.
OC. The switch looks up the receiving device's MAC address in a
switching table.
OD. The switch forwards the message to the port of the receiving
device.
SUBMIT
Answers
The step that happens first after a switch receives a message that includes a MAC address is that "The switch looks up the receiving device's MAC address in a switching table." (Option C)
What is a MAC Address?
A media access control (MAC) address is a one-of-a-kind identifier assigned to a network interface controller for use as a network address in intra-network communications. This is a widespread use in most IEEE 802 networking technologies, such as Ethernet, Wi-Fi, and Bluetooth.
What is a switch?
A network switch is a piece of networking gear that links devices on a computer network by receiving and forwarding data to the target device using packet switching.
Learn more about MAC Addresses:
https://brainly.com/question/24812654
#SPJ1
Which of the following signal processors would you use to stop unwanted background noise below a specific level in your file?
(a) compressor
(b) normalizer
(c) gate
(d) graphic EQ
Answers
To stop unwanted background noise below a specific level in your file, you should use: (c) gate
A gate is a signal processor that allows audio signals above a certain threshold to pass through while attenuating or silencing signals below that threshold. This helps eliminate unwanted background noise effectively.
The signal processor that you would use to stop unwanted background noise below a specific level in your file is gate. A gate is a device that allows the signal to pass through only if it is above a certain threshold. Anything below that threshold is muted or attenuated. A gate can be useful for removing low-level noise such as hum or hiss from an audio file. However, a gate cannot remove noise that is present at the same level as the desired signal, such as a siren or a cough during a speech. For that, you would need more advanced signal processors such as noise reduction or noise cancellation algorithms
to learn more about signal processor click here:
brainly.com/question/18687632
#SPJ11
Put these steps for managing your study time in chronological order. 1 set aside the same time each day 2 Identify the best time of day 3 Stick with it
Answers
Answer:
1 identify the best time of day 2 set aside the same time each day 3 stick with it
Answer:
1 identify the best time of day 2 set aside the same time each day 3 stick.
Explanation:
if you know hotboi let me know
You are creating a story map about Mexico. After configuring the web app template, you launch the app to test it. When the app opens, the map is zoomed to the whole world, instead of to Mexico. What actions will fix the problem
Answers
Hasan would like to use the Ruler command to help him with aligning a hand drawn object. Where in the Draw tab
should he go to find this command?
O Stencils group
O Tools group
O Pens group
Convert group
Answers
Since Hasan would like to use the Ruler command to help him with aligning a hand drawn object, the Draw tab that he should go to find this command is option C: Tools group.
What is the Draw tab?In Microsoft Office programs, the Draw tab is typically used for creating and manipulating shapes and other graphical elements.
The Tools group is one of the groups within the Draw tab, and it contains a variety of tools and commands that can be used to create and manipulate shapes and other elements.
Hence, the Ruler command is a tool that allows users to draw straight lines and measure distances between points on a drawing canvas.
Learn more about Draw tab from
brainly.com/question/14218463
#SPJ1
Answer: It is Stencils group, NOT c.
Explanation: right on edge22
Most case fans have standard _______________ connectors that are easy to plug in but can be forced to be connected the wrong way.
Answers
Answer:
Molex
Hope this Helps!
Configure Static Routes
Your branch office is connected to the main office and the internet through the SFO router. Both serial interfaces connecting the SFO router to the main office and the internet have been configured and are up. You need to configure static routes on the SFO router for each destination. Use the next hop address when assigning the static routes. Your ISP's address is 160.12.99.1. Use the show cdp neighbors detail command to discover the next hop address for the 10.0.0.0 network.
In this lab, your task is to:
Configure a static route to 10.0.0.0/8 network.
Configure a default route to the internet.
Save your changes to the startup-config file.
Answers
To configure a static route to the 10.0.0.0/8 network, and to configure a default route to the internet, and then save changes to the startup-config file, follow these steps:
Step 1: First, log in to the router and go to configuration mode by typing "configure terminal".
Step 2: Next, configure a static route to the 10.0.0.0/8 network by typing the following command: ip route 10.0.0.0 255.0.0.0 [next hop address]The next hop address can be found by using the show cdp neighbors detail command.
Step 3: Then, configure a default route to the internet by typing the following command: ip route 0.0.0.0 0.0.0.0 160.12.99.1. This command will forward all packets that do not match any of the existing routes to the next hop address 160.12.99.1, which is the ISP's address.
Step 4: Finally, save your changes to the startup-config file by typing the following command: copy running-config startup-config. This will save the current configuration as the startup-config file. The router will use this file when it boots up or if the configuration is reset.
Static routes are the most common type of routing used on small to medium-sized networks. A static route is a route that is manually configured by a network administrator, as opposed to one that is learned dynamically through a routing protocol. Static routes are typically used to specify a gateway of last resort or to route traffic to a specific destination.
Learn more about Static routes:
https://brainly.com/question/6783973
#SPJ11
____ is the value used by CISCO routers to decide between routes learned from different sources.
Answers
The value used by CISCO routers to decide between routes learned from different sources is called Administrative Distance (AD).
Administrative Distance is a measure of the trustworthiness of a routing protocol or source. It is a numerical value assigned by CISCO routers to various routing protocols, with lower values indicating higher trustworthiness. When a router receives multiple routes to a destination from different sources, it uses the Administrative Distance to choose which route to use for forwarding packets. For example, if a router receives a route to a destination from both OSPF (AD 110) and BGP (AD 20), it will choose the route learned from BGP as it has a lower AD and is considered more trustworthy. AD values can be changed by network administrators to prioritize certain routing protocols or sources over others.
learn more about CISCO routers here:
https://brainly.com/question/8986399
#SPJ11
The analysis of attempting to solve a problem with information systems is called ________.
Answers
The analysis of attempting to solve a problem with information systems is called systems analysis.
In the field of technology, system analysis can be described as studying and analyzing a system in order to solve any problems occurring in the information system. In simpler terms, systems analysis means analyzing and observing systems for troubleshooting.
The procedure of system analysis involved interpreting a problem, studying facts, and solving the problems.
The purpose behind system analysis is to improve a particular system. System analysis looks after that all components of an information system are working properly and hence can perform better.
To learn more about system analysis, click here:
https://brainly.com/question/24439065
#SPJ4
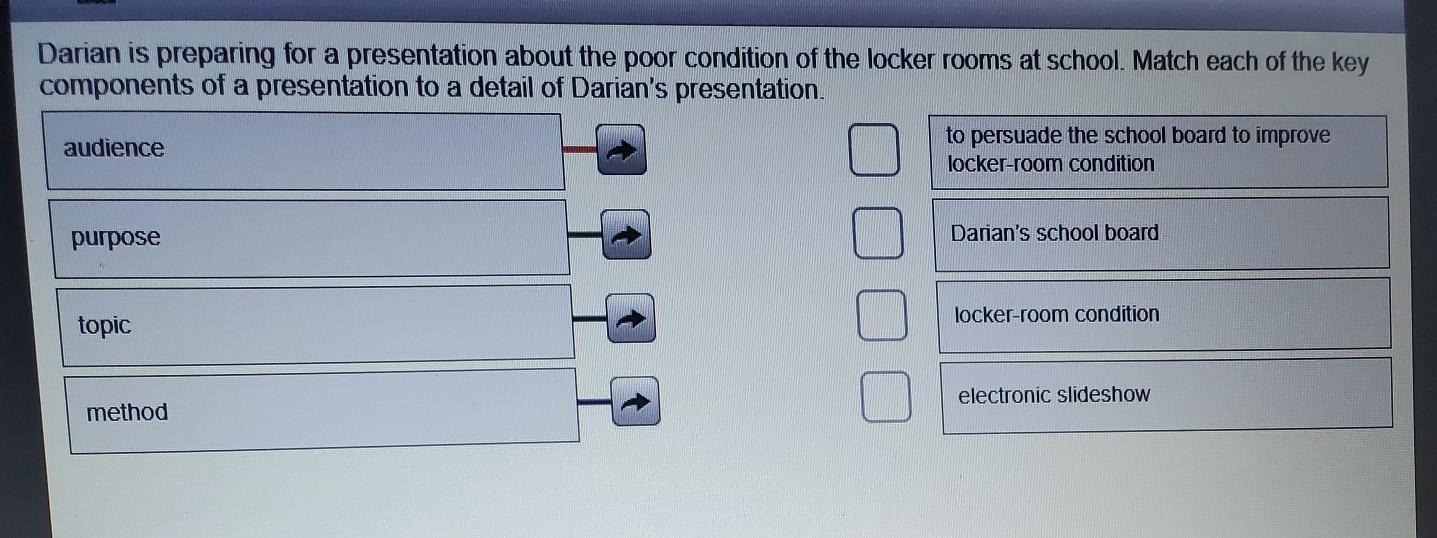
Darian is preparing for a presentation about the poor condition of the locker rooms at school. Match each of the key components of a presentation to a detail of Darian's presentation. audience to persuade the school board to improve locker-room condition purpose Darian's school board locker-room condition topic a electronic slideshow method can anyone
Answers
Answer:
Purpose - To paurswade the board to change the conditions of the locker room
Topic - Locker room condition
Method - Electronic Slideshow
Audience - School Board
state the types of Data range
Answers
There about 5 types of data range. See them below.
What are the various types of data range?Numeric range: This is a range of values that can be expressed as a numerical value.
Boolean range: This is a range of values that can be either true or false. Boolean data types are commonly used for logical expressions and conditional statements.
Character range: This is a range of values that can be represented as a character or string of characters. Character data types are commonly used for text-based data.
Date/time range: This is a range of values that can be expressed as a date or time value. Date/time data types are commonly used for tracking events or scheduling tasks.
Enumeration range: This is a range of values that can be expressed as a predefined set of values.
Learn more about data range at:
https://brainly.com/question/20607770
#SPJ1
AYYOOOO CAN YOU HELP A GIRL OUUTT???
Fields are data items representing a single attribute of a record. Question 2 options: True False
Answers
Answer: The answer is true
How do you add a new comment to a document?
A. Choose the References tab, then New Comment.
B. Choose the Layout tab, then Insert Comment.
C. Choose the File tab, then New Comment.
D. Choose the Review tab, then New Comment.
Answers
Answer:
D. Choose the Review tab, then New Comment
Explanation:
It's quite easy to add comments to word documents.
From the list of given options, only option D satisfy the given question.
To add comments to a text, you simply highlight the text
Go to the review tab then select new comment.
Once you follow these simple steps, a new comment will be created in your word document.
The correct answer is D. Choose the Review tab, then New Comment.
If you go to the review tab in Microsoft Word, the center there is a group labeled Comments. There's a large button on the left-hand side in that group labeled New Comment.
Hope this helps :)
changes made to the ________ affect the overall totals on the summary worksheet.
Answers
Changes made to the individual cells or data points within a worksheet can have a significant impact on the overall totals on the summary worksheet.
This is because the summary worksheet is often constructed to aggregate and analyze data from multiple worksheets or sources, and any changes to the underlying data can ripple through to the final summary figures. For example, if a user updates the sales figures for a particular product line in a sales worksheet, this can impact the total sales figures for that product line in the summary worksheet. Similarly, changes made to formulas, calculations, or formatting within a worksheet can also affect the summary totals, depending on how the summary worksheet is constructed. It is important for users to carefully review and check the impact of any changes made to individual worksheets on the overall summary, to ensure accuracy and consistency in their reporting and analysis. This can often involve testing and validation of different scenarios or data inputs to identify any potential issues or errors before finalizing the summary worksheet.
Know more about individual cells here:
https://brainly.com/question/13253816
#SPJ11
Help me pls!!! last question
Tori needs to turn her Turtle to the left 90 pixels. Which line of code should Tori use?
tina(90)
tina.back(90)
tina.left(90)
tina.right(90)
Answers
Answer:
tina.left(90)
Explanation:
In code if you want your character to turn left you put "left" in your code and if you want your character to go right type "right" and so on and so on so your answer is tina.left(90)
Answer: Option C is the correct line of code Tori should use.
tina.left(90)
Explanation:
I took the test and got it correct, you can trust me.
, Hope this helps :)
Have a great day!!