What is the main responsibility of the executive?
Answers
The President picks the leaders of all government agencies, including the Cabinet, in order to carry out and enforce the laws passed by Congress. The Vice President is also part of the Executive Branch.
What are the executive's primary duties? The President picks the leaders of all government agencies, including the Cabinet, in order to carry out and enforce the laws passed by Congress.The Vice President is a member of the Executive Branch and is prepared to take over as President if necessary.An executive manages operational activities for their company or organization and is typically in charge of developing policies and strategies to achieve organizational objectives.Executives frequently travel to conferences, meetings, and local, regional, national, and worldwide offices.Traveling executives frequently visit regional, local, national, and worldwide workplaces in addition to attending meetings and conferences.The executive branch is headed by the president, whose constitutional duties include acting as head of state, commander in chief of the armed forces, treaty negotiator, federal judge (including members of the Supreme Court), ambassador, and cabinet official.
To learn more about executive branch refer
https://brainly.com/question/20658746
#SPJ4
Related Questions
In the current situation, how do you access information as a student? How will you integrate the use of ICT in your daily life and your chosen track?
Answers
Answer:
Explanation:
As a computer science student information is accessed in every possible way. This can be through a local school lan network, mobile devices, e-mail, etc. All of these help information flow to and from various people and makes obtaining this information incredibly simple as a student. Especially in the field of computer science, I need to integrate as many ICT devices with me in my everyday life, to send emails, check calendar updates, research information on the web, check school reports, and even speak with clients.
Question 12 (1 point)
Generally, each pixel in an image creates 25 bytes of data.
True
False
Answers
Answer:
This is B: False
Explanation:
Each pixel of an image creates 24 bits, or 3 BYTES of data for color, and 1 byte for black and white.
PLEASE I REALLY NEED HELP
I have an hp laptop and it is FROZEN!! I cannot press x out of any of my tabs and the whole thing is frozen but I can pull up my settings and I can move my mouse. Shutting it off/down didn't work and it's still frozen please tell me what to do. also, will restarting it log me out of my whole account(s)? I NEED HELP PLEASEE
Answers
First try shutting down your computer for 5 minutes.
Turn it on if tabs are still open, try to right click it and press delete if you have that.
if you have none of your acounts try to make anew accounts the add a account to the new account you just made. still having peroblems, let me know?
Answer:
wait to it dies or hold the shut down button till it turns off
Explanation:
Rachel has set up a computer network. In this network, due to a device, the computers partake in the message transfer process. Which device is
this?
А. NIC
В. hub
C. modem
D. switch
E. bridge
Answers
Which types of computer hardware are internal?
Answers
Answer:
Here are some :) (sorry if there are too many)
Explanation:
RAM (Random Access Memory): It's a fast-access memory that is cleared when the computer is powered-down. RAM attaches directly to the motherboard, and is used to store programs that are currently running.
Video Card/GPU (Graphics Processing Unit): It's a specialized processor originally designed to accelerate graphics rendering.
Sound Card: USB sound "cards" are external devices that plug into the computer via USB.
Storage: SSD (Solid State Drive): It is a data storage device that uses solid-state memory to store persistent data.
HDD (Hard Disk Drive): It is a non-volatile storage device which stores digitally encoded data on rapidly rotating platters with magnetic surfaces. Just about every new computer comes with a hard disk these days unless it comes with a new solid-state drive.
CPU (Central Processing Unit/ sometimes just called a processor) It's a machine that can execute computer programs, and sometimes called the brain of the computer.
Motherboard: The motherboard is the body or mainframe of the computer, through which all other components interface. It is the central circuit board making up a complex electronic system.
Firmware: Firmware is loaded from the Read only memory (ROM) run from the Basic Input-Output System (BIOS). It is a computer program that is embedded in a hardware device, for example a microcontroller.
Power Supply: The power supply as its name might suggest is the device that supplies power to all the components in the computer.
CD-ROM Drive: There are two types of devices in a computer that use CDs: CD-ROM drive and a CD writer. The CD-ROM drive used for reading a CD. The CD writer drive can read and write a CD.
Floppy Disk: A floppy disk is a type of data storage that is composed of a disk of thin, flexible(“floppy”) magnetic storage medium encased in a square or rectangular plastic shell.
Internal Storage: Internal storage is hardware that keeps data inside the computer for later use and remains persistent even when the computer has no power.
Disk Array Controller: A disk array controller is a device which manage the physical disk drives and presents them to the computer as logical units.
On some computers the speakers are internal as well. :)
If you wanted to find out whether an integer contained an even number of 1 bits, which status flag would be useful
Answers
Answer:
The correct answer will be "Parity".
Explanation:
Parity seems to be a methodology that tests when information is transferred or missing or overwritten when something is transferred between one storage location to another, and then it is communicated between processors or devices.It would be used whilst also contrasting the container as well as the aggregated parity to evaluate or dual inspect for inaccuracies.What are the steps to debugging?
Answers
Answer:
The basic steps in debugging are:
Recognize that a bug exists.
Isolate the source of the bug.
Identify the cause of the bug.
Determine a fix for the bug.
Apply the fix and test it.
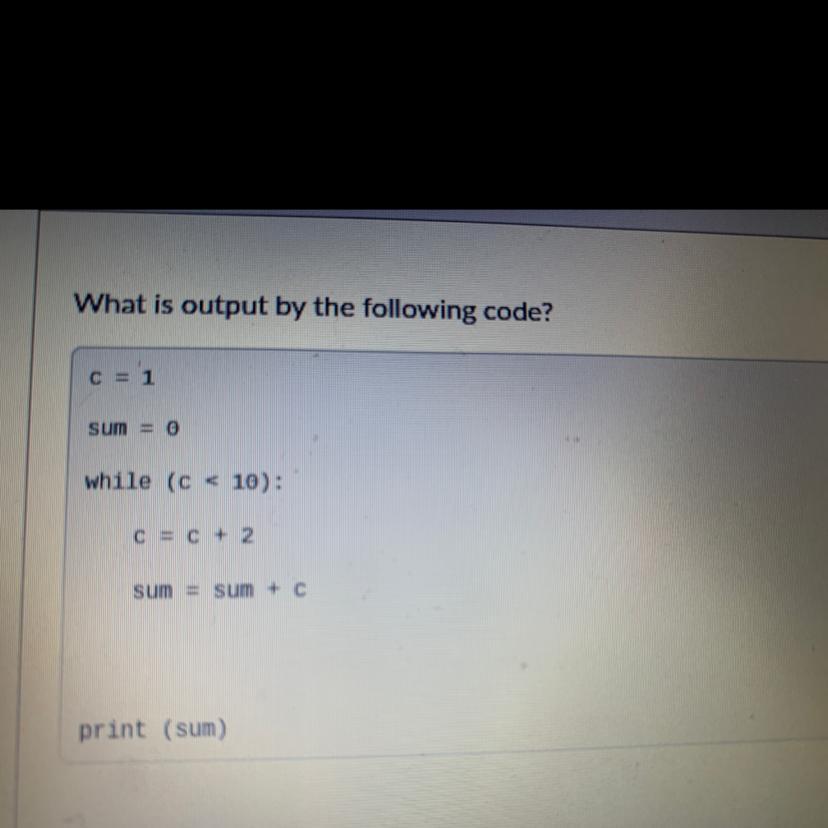
What is output by the following code?
C = 1
sum = 0
while (c 4 10):
C=C+2
sum = sum + c
print (sum)
Answers
Answer :
Sum = 3,8,15,24,35
Steps :
Initially, c = 1, so
while (c=1 < 10)
c= 1+2 =3
Sum = 0 + 3 = 3
while (c=3 < 10)
c= 3+2 =5
Sum = 3 + 5 = 8
while (c=5 < 10)
c= 5+2 =7
Sum = 8 + 7 = 15
while (c=7 < 10)
c= 7+2 =9
Sum = 15 + 9 = 24
while (c=9 < 10)
c= 9+2 =11
Sum = 24 + 11 = 35
Therefore, Sum = 3,8,15,24,35
You can learn more about while loop from the given link:
https://brainly.in/question/16569909
#SPJ13
In her role as an administrative professional, martina is learning about different types of business letters she might be asked to type. which is most likely to be requested by her manager? question 1 options: a. acceptance letterb. dear john letter c. happy birthday letter d. chain letter
Answers
Based on the given options, the most likely type of letter that Martina's manager will request her to type as an administrative professional is an acceptance letter.
An acceptance letter is typically used to formally accept a job offer or a business proposal. It is a professional correspondence that confirms the acceptance of an agreement or an offer made by another person or organization. It usually includes details such as the terms and conditions of the agreement, the start date, salary, and other important information related to the offer.
On the other hand, a "Dear John" letter is a type of letter that is typically used to end a romantic relationship, and a chain letter is a type of letter that is usually circulated to a large number of people to spread a message or a request. A happy birthday letter is a type of personal correspondence that is sent to friends or family members on their birthdays.
To learn more about acceptance letter visit;
https://brainly.com/question/15200765
#SPJ4
What is UNIX?
A program for writing documents
A graphical interface
An internet browser
An operating system
Answers
Answer:
UNIX is an operating system.
Pls help xD. In pseudocode or python code please. Will mark best answer brainliest. Thx

Answers
Answer:
I'm doing my best to send you my answer,
Explanation:
The coding will be below
which two functions can be performed with a next generation firewall but not with a legacy firewall?
Answers
Two functions that can be performed with a next-generation firewall (NGFW) but not with a legacy firewall are "deep packet inspection" and "application-level filtering."
Next-generation firewalls provide enhanced capabilities beyond traditional or legacy firewalls. They incorporate advanced technologies and features that enable more granular and context-aware control over network traffic.
1. Deep Packet Inspection (DPI): NGFWs can perform deep packet inspection, which involves analyzing the content of network packets at the application layer. This allows them to inspect not only the header information but also the payload of the packets. By understanding the actual application protocols and data within the packets, NGFWs can make more informed security decisions, detect and block specific types of malicious activities, and enforce more sophisticated security policies.
2. Application-level Filtering: NGFWs have the ability to identify and control networK traffic based on specific applications or application categories. They can identify the applications in use, regardless of the port or protocol being used. With application-level filtering, NGFWs provide more precise control over network traffic, allowing organizations to enforce policies that are based on applications rather than just IP addresses or ports. This enables better visibility into application usage, improves security by blocking unauthorized or high-risk applications, and allows for more effective bandwidth management.
In summary, next-generation firewalls offer capabilities such as deep packet inspection and application-level filtering that go beyond what legacy firewalls can provide. These functions enhance network security, improve policy control, and enable more effective management of network resources.
learn more about firewalls here; brainly.com/question/31753709
#SPJ11
If the evaluation of the first parameter of an Excel IFERROR function (shown in bold/underlined in the example below) does NOT return an error (e.g., #N/A), what value does the IFERROR function return?
=IFERROR( VLOOKUP(H15,D$11:F$19,3,FALSE), "Unknown" )
Question 3 options:
The value "FALSE"
The value of the first parameter
The value "TRUE"
The value of the second parameter
Answers
If the evaluation of the first parameter of an Excel IFERROR function does not return an error, the IFERROR function will return the value of the first parameter.
In the given example, if the VLOOKUP function in the first FERROR function successfully finds a match, the result of that VLOOKUP will be returned.
The IFERROR function is used to handle errors in Excel formulas by providing an alternative value or action when an error occurs. In this case, if the VLOOKUP function encounters an error, such as not finding a match, the IFERROR function will return "Unknown" as the second parameter. However, if the VLOOKUP function successfully retrieves a value without FERROR functionan error, that value will be returned by the IFERROR function.
Learn more about IFERROR function here:
https://brainly.com/question/31578339
#SPJ11
what are the advantages of using cloud computing? select all the answer that are true group of answer choicesinformation technology sandboxing capabilitiespowerful server capabilitiesincrease in productivitydata backup and storage of datacost effective
Answers
The advantages of using cloud computing include sandboxing capabilities, powerful server capabilities, increase in productivity, data backup and storage, and cost-effectiveness.
Sandboxing capabilities: Cloud computing offers the ability to create isolated environments for testing and development purposes, known as sandboxes. Sandboxing allows users to experiment with applications and software without affecting the production environment.
Powerful server capabilities: Cloud computing provides access to powerful server resources and infrastructure that may not be feasible to maintain on-premises. This enables users to leverage high-performance computing capabilities for demanding workloads and applications.
Increase in productivity: Cloud computing allows for easy collaboration and access to resources from anywhere with an internet connection. This enhances productivity by enabling teams to work together on projects in real-time, share documents, and access applications and data from any device.
Data backup and storage: Cloud computing offers reliable data backup and storage solutions. Data is stored in redundant servers, reducing the risk of data loss. It provides scalability and flexibility in managing storage needs, ensuring data availability and disaster recovery.
Cost-effective: Cloud computing eliminates the need for upfront investments in hardware and infrastructure. It operates on a pay-as-you-go model, allowing businesses to scale resources up or down as needed, thereby reducing capital expenditures. This cost-effective approach makes cloud computing accessible to businesses of all sizes.
To know more about cloud computing, visit:
brainly.com/question/30122755
#SPJ11
nonymizers allow a user toO obtain a new identity O send email and surf the Web anonymously O secretly spy on people visiting your Web site O randomly create a handle or avatar
Answers
Anonymously send emails and browse the web. All major browsers offer anonymous browsing options. To access Chrome's Incognito, use Ctrl+Shift+N (Opens in a new window).
Exists a browser that is entirely private?Tor. The Tor Browser connects to the Internet through an untraceable network of computers. Each computer only knows about the one before it as your connection is passed from one to the next.
Is it possible to conceal a website's IP?Yes. All of your internet traffic, not only that sent through your browser, is encrypted and your IP address is hidden when you use a VPN. When using open Wi-Fi networks, such as those found in public places, a VPN is extremely helpful. VPNs are regarded as crucial for internet safety since they offer a wealth of privacy advantages.
To know more about browsers visits :-
https://brainly.com/question/28504444
#SPJ4
Run a regression of Test scores (Testscr) on Teachers, Computers, percentage of English learners (el_pct), Average Income (avginc), and the percent qualifying for reduced-price lunch (meal_pct). a. If district avginc increases from $30,000$ to $40,000, how are test scores (Testscr) expected to change in the given school?
Answers
To estimate the expected change in test scores (Testscr) when the district average income (avginc) increases from $30,000 to $40,000, you would need the coefficient estimate for avginc from the regression model.
In a regression model, the coefficient estimate for avginc represents the expected change in test scores associated with a one-unit increase in average income, assuming all other variables are held constant.
So, if you have the coefficient estimate for avginc from the regression model, you can use it to calculate the expected change in test scores when avginc increases from $30,000 to $40,000.
For example, if the coefficient estimate for avginc is 0.05, it would mean that for every $1,000 increase in average income, test scores are expected to increase by 0.05 units (assuming all other variables are held constant).
To calculate the expected change in test scores when avginc increases from $30,000 to $40,000, you would calculate:
Change in test scores = Coefficient estimate for avginc * (New avginc - Old avginc)
Change in test scores = 0.05 * ($40,000 - $30,000)
Know more about regression:
https://brainly.com/question/32505018
Write the definition of a function tripleIt, which triples its argument but returns nothing so that it can be used as follows:
int x=5;
tripleIt(&x);
x is now equal to 15
Answers
The definition of a function tripleit, which triples its argument but returns nothing so that it can be used as follows: int x=5; tripleit(&x); /* x is now equal to 15 */ is given below:
The Functionvoid tripleIt ( int * x ) {
* x = * x * 3 ;
}
What this function does, is that it defines the function as an integer of x and then goes ahead to show the mathematical operation which occurs as a triple value which is x * 3 that gives the output as 15 as required by the question above.
Read more about functions in programming here:
https://brainly.com/question/13041454
#SPJ1
Describa la clasificación de los recursos educativos digitales abiertos. vea este video, para hacer eso
Answers
hola una pregunta dónde está el vídeo ?
hola una pregunta dónde está el vídeo ?
Why is it important for an app developer to work closely with the client and end users to understand what their users want and need?
Answers
if the app developer doesn't meet the clients needs within the app the client may be dissatisfied, and not use the app. The client could also spread the word that this app developer dosen't listen to their customers and this could jeopardize future clients wanting to work with the app developer.
what type of formula uses data from multiple worksheets
a. abstract formula
b. hyper formula
c. 3D formula
d. unbounded formula
Answers
Answer: I think its 3D formula
Explanation: ...
Help me please (⌒-⌒; )

Answers
Answer:
raise the prices
Explanation:
Hope this helped, Have a Great Day/Night!!
What are some of the unique benefits and challenges of flash drives as a way to store data?
Answers
Answer:
these are some benefits Increased Durability. Unlike traditional hard-disk drives, flash drives lack moving parts
Maximum Portability
Plenty of Storage Capacity
Fast Transfer Speeds
Compatibility with Many Devices
9.
Consider the following code:
x = 5 % 4
if (x == 1):
print (1)
elif (x 2):
print (2)
elif (x == 3):
print (3)
else:
print (4)
What is output?
Answers
Answer:
1
Explanation:
hope it helps you
please mark me as brainliest
Complete the sentence.
One way to increase the reliability of a hard disk drive is by making it part of ____
an optical array
a capacitator
a RAID
an analog ray
Answers
Answer: It is raid
Explanation:
Took the test for edge
what describes an ipv6 address of ::1? loopback broadcast public multicast see all questions back next question
Answers
An IPv6 address of ::1 is a loopback address.
IPv6 is the Internet Protocol version 6, a new version of IP that is based on IPv4. IPv6 addresses are 128 bits in length, and they are written in a hexadecimal form separated by colons.IPv6 addresses come in three forms: Unicast, Multicast, and Anycast.
A loopback address is a unique IP address that is utilized to check network software without having to use the network. As a result, no physical device is required to use it. A loopback address is also known as a virtual IP address.::1 is the loopback address in IPv6, which is similar to 127.0.0.1 in IPv4.
To know more about IPV6 Address of ::1; https://brainly.com/question/31103106
#SPJ11
write a paragraph about ICT in personal life?
Answers
Answer:
Information and communications technology (ICT) is an extensional term for information technology (IT) that stresses the role of unified communications[1] and the integration of telecommunications (telephone lines and wireless signals) and computers, as well as necessary enterprise software, middleware, storage and audiovisual systems, that enable users to access, store, transmit, and manipulate information.
Cry walker invested $7200 in the business .(use the make deposits window and check no 5555) quickbooks
Answers
To record Cry Walker's investment of $7200 in the business using QuickBooks, go to the "Make Deposits" window and enter check number 5555.
Open QuickBooks and navigate to the "Banking" menu.
Select "Make Deposits" to open the "Make Deposits" window.
Enter the relevant bank account where Cry Walker's investment will be deposited.
In the "Received From" field, enter Cry Walker's name or the name of the account representing the investment.
In the "From Account" column, select the appropriate equity account to record the investment.
Enter the amount of $7200 in the "Amount" field.
In the "Check #" field, input 5555 to designate the check number associated with this transaction.
Click "Save & Close" to record the investment in QuickBooks.
By following the steps outlined above in the QuickBooks "Make Deposits" window and entering check number 5555, Cry Walker's investment of $7200 can be accurately recorded in the system, ensuring proper tracking of the financial transactions related to the business.
Learn more about QuickBooks here:
brainly.com/question/27983902
#SPJ11
A social media site violates its terms of service by selling information about its users
to another company. This is an example of a violation of:
digital privacy.
digital encoding.
digital domain.
digital computation.
Answers
what does the first number in a zip code represent?
Answers
so.. the answer is “ The first digit in a ZIP code represents a defined group of U.S. states. “
hope this helps!!
What are 3 customizations that can be done using the header/footer section in the customize reports tray?.
Answers
The 3 customizations that can be done using the header/footer section in the customize reports tray are:
One can customize the data, and also sum up that is add or delete columns, and also add or delete information on the header/footer. What is the customizations about?In the case above, a person can also be able to personalize the font and style of the given report that they have.
Note that a lot of columns and filters differ for all kinds of report/group of reports and as such, The 3 customizations that can be done using the header/footer section in the customize reports tray are:
One can customize the data, and also sum up that is add or delete columns, and also add or delete information on the header/footer,Learn more about customizations from
https://brainly.com/question/3520848
#SPJ1
Answer:
change the header or footer alignment, show the logo, show or hide the report basis
Explanation:
so sorry about these "experts" that always spout random information