What is the best explanation for why it is important to identify sources in your research plan?

Answers
Answer:
Because it would be plagiarism if you didn't give credit plus if the viewer wants to get more information they can.
Answer:
it's B
Explanation:
Related Questions
Jose would like to have text with predefined styles that can flow around an image in a variety of shapes and sizes
Which object should he insert into his document?
WordArt
SmartArt
shapes
images
Answers
Answer:
A) WordArt
Explanation:
WordArt can be set to the predefined styles within Word and can be set to flow and wrap around images in word.
Answer:
Word art
Explanation:
Which statement is true regarding the Quick Access toolbar?
O It can be located at the top left-hand corner of the screen or below the ribbon.
O. It can contain functions that are also in the ribbon
O It can be modified to contain any function that you use frequently.
O All the above statements are true.
Answers
Answer: All the above statements are true
Answer:
D) All of the above
Explanation:
Y’all got your tickets for Spider-Man No Way Home? I do
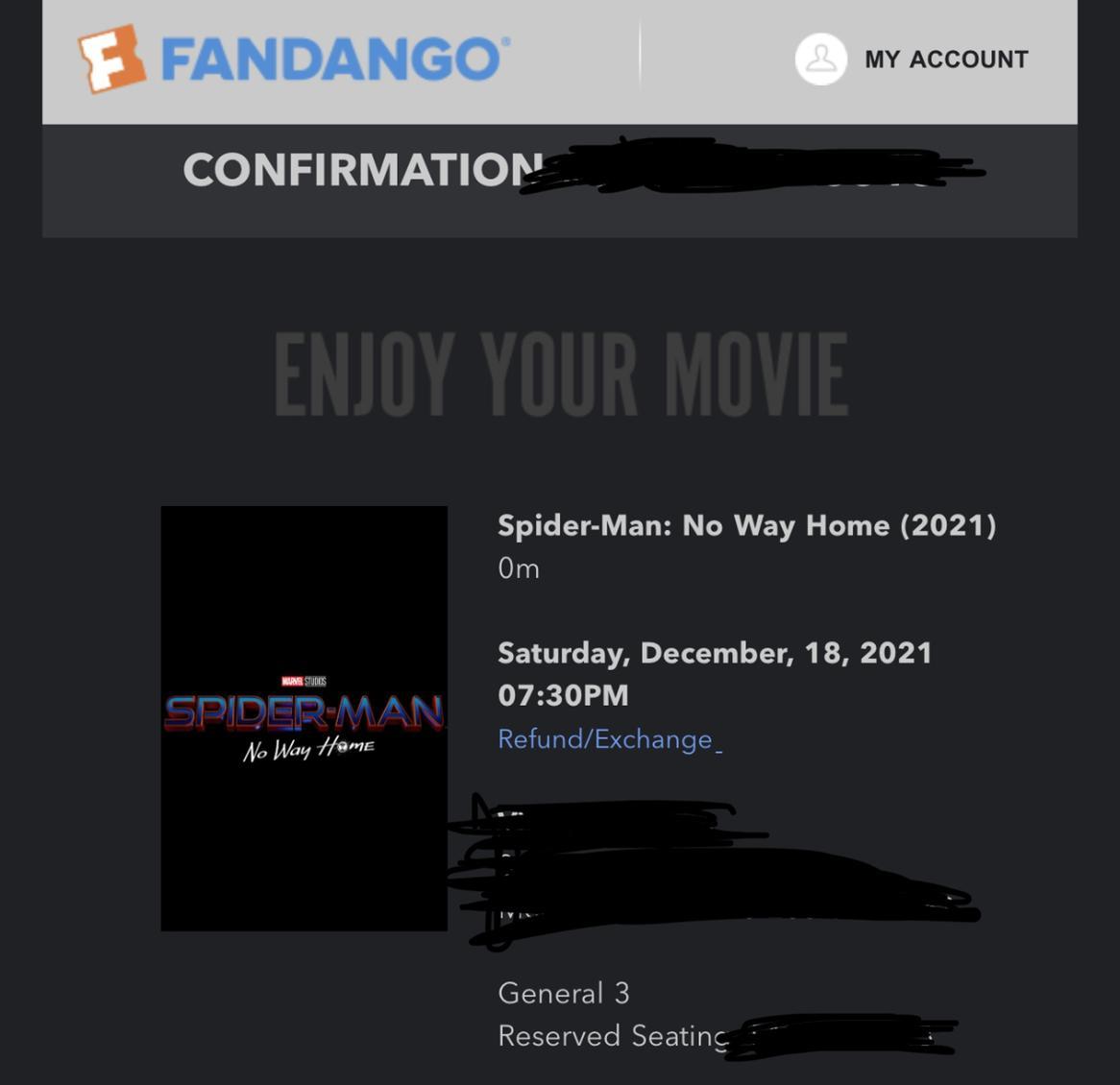
Answers
Answer:
IS IT THE NEW MARVEL MVOIE
Explanation:
how many rows of aliens are there usually at the start of a ‘space invaders’ game?
Answers
The usual number of rows of aliens at the start of a 'Space Invaders' game is four.
In the classic 'Space Invaders' game, the player faces a formation of aliens descending from the top of the screen. The aliens are arranged in rows, and at the beginning of the game, there are typically four rows of aliens. Each row contains a different type of alien, and as the player progresses in the game, the aliens move faster and their formations become more challenging.
The four rows of aliens provide an initial level of difficulty for the player to overcome. As the player successfully eliminates the aliens, new waves of aliens appear, often with different movement patterns and increased speed. This progression adds to the excitement and challenge of the game.
know more about Space Invaders here:
https://brainly.com/question/10941943
#SPJ11
Jon wants to set up a trihomed DMZ. Which is the best method to do so? A. use dual firewalls B. use a single firewall with only two interfaces C. use a single three-legged firewall with three interfaces D. use dual firewalls with three interfaces
Answers
Answer:
The correct option is C) Use a single three-legged firewall with three interfaces
Explanation:
DMZ is an acronym for a demilitarized zone.
A DMZ network is one is situated between the internal network and the Internet. It is supported by an Internet Security and Acceleration (ISA) server.
The interfaces you'd get with the DMZ network are
A public network (Internet Protocol-IP) address with a public interfaceAn internal network interface with a private network (IP) address A DMZ interface with a public network (IP) addressUnlike the back-to-back DMZ settings, a trihomed DMZ is unable to use private IP addresses. To use the trihomed DMZ, public IP addresses are a must suitable requirement.
Cheers!
High Street stores are struggling to compete with online retailers. Discuss the advantages and disadvantages of each type of store, both to the individual shopper and to the community as a whole. How are some of the disadvantages of online shopping being overcome? Describe how this trend represents a cultural shift
Answers
Online retailers are companies that market their goods or services on digital channels like websites and mobile apps and then ship or digitally deliver them to clients.
Advantages of High Street Stores:
Tangible Experience: Before making a purchase, shoppers can view, touch, and try out things in high street stores. This enables clients to make wise judgements and guarantees that they receive the goods they desire.Shoppers can go shopping with friends or family and enjoy the experience of looking through and trying on clothing together in high street stores, making it a social pastime. As a result, there may be a sense of belonging and connection to the neighbourhood.Buying at high street retailers can assist support neighbourhood businesses, which can then help the local economy and help to create jobs in the neighbourhood.Disadvantages of High Street Stores:
Increased Prices: Compared to online shops, high street stores frequently have higher prices since running a physical store involves expenses like rent, utilities, and staffing.Restricted Variety: Compared to internet shops, high street stores may not offer as many things due to their limited area.Convenience: High street shops may not always be easy for customers to access, especially if they are distant from the customer's home or place of employment.Advantages of Online Retailers:
Reduced Prices: Due to decreased overhead costs, online shops frequently offer lower prices than high street stores.Large Selection: Compared to main street stores, online retailers have a far wider selection of products accessible, making it easier for clients to discover exactly what they need.Convenience: Internet buying is convenient since it allows customers to make purchases whenever they want, from the comfort of their homes.Disadvantages of Online Retailers:
Online shopping does not offer the same tangible experience as shopping in brick-and-mortar stores, so customers cannot view, touch, or try products before making a purchase.Loss of Social Experience: Because online shopping is frequently a solitary activity, clients are deprived of the social experience that comes with visiting high street establishments.Shipping and delivery times: Online shoppers frequently have to wait a few days or even weeks to receive their products due to shipping and delivery periods.Retailers now provide more lenient return policies, quicker shipment dates, and alternatives for free shipping to offset some of the drawbacks of online purchasing. In addition, some businesses are simulating the experience of trying on clothing or products by utilizing augmented reality and virtual try-on technologies.
A cultural shift in how people shop and consume goods can be seen in the move towards internet shopping. Due to the ease, greater product availability, and lower pricing of online shopping, conventional high street retailers have seen a decline in business. With a greater focus on online marketing and e-commerce platforms, this cultural shift has also affected how shops market and sell products.
To know more about Internet,
https://brainly.com/question/21565588
#SPJ4
eeeeeeeeeeeeeeeeeeeeeeeeeeeereeeeeeeeeeeeeeeee
Answers
Answer:
okay
Explanation:
.............
the first webpage of a website is called
Answers
Answer:
A home page or The World Wide Web project
Explanation:..
Yo, my Lenovo laptop keeps showing this screen but I can't sign in, can someone help me?
Answers
Which address typ e is automatically created by defaukt on a host interface when no ras are received?
Answers
Answer:
Which address type is automatically created by default on a host interface when no RAs are received? global unicast address
Explanation:
Write a function named buildArray that builds an array by appending a given number of random two-digit integers (10-99). It should accept two parameters — the first parameter is the array, and the second is an integer for how many random values to add, which should be input by the user.
Answers
Answer:
The function in C++ is as follows:
void buildArray(int arr[], int n){
srand(time(NULL));
for(int i = 0;i<n;i++){
arr[i] = rand() % 99 + 10; }
for(int i = 0;i<n;i++){
cout<<arr[i]<<" ";
}
}
Explanation:
This defines the function
void buildArray(int arr[], int n){
This klets the program generate different random numbers
srand(time(NULL));
This iterates from 0 to n - 1 (n represents the length of the array)
for(int i = 0;i<n;i++){
This generates random 2 digit integer into the array
arr[i] = rand() % 99 + 10; }
This iterates through the array and print the array elements
for(int i = 0;i<n;i++){
cout<<arr[i]<<" ";
}
}
See attachment for complete program that includes the main
Which of the following usage will always be cost-free even after your account's Free Tier has expired? (Select TWO.)
A. One million API calls/month on Amazon API Gateway
B. 10 GB of data retrevals from Amazon Glavier per month
C. 500 MB/month of free storage on the Amazon Elastic Container Registry (ECR)
D. 10 custom monitoring metrics and 10 alarms on Amazon CloudWatch
Answers
The two options that will always be cost-free even after your account's Free Tier has expired are: "500 MB/month of free storage on the Amazon Elastic Container Registry (ECR)" and "10 custom monitoring metrics and 10 alarms on Amazon CloudWatch". Therefore the correct answer is options C and D.
Even after your account's Free Tier has expired, the usage mentioned in options C and D will continue to be cost-free. Option C provides 500 MB/month of free storage on the Amazon Elastic Container Registry (ECR), which remains free beyond the Free Tier.
Option D allows for 10 custom monitoring metrics and 10 alarms on Amazon CloudWatch, which also continue to be free even after the Free Tier expires.
Therefore options C and D are the correct answer.
To learn more about cost: https://brainly.com/question/28147009
#SPJ11
jack has a computer at home that he uses to access the internet, store and edit personal photos, and create and edit documents. recently, he has come to realize that in order to keep the computer performing at its best, he needs to carry out regular system maintenance on the computer. jack can use the program to locate and delete temporary files, such as installation files, web browsing history, and files in the recycle bin. a. windows registry b. disk defragmenter c. windows disk cleanup d. temporary files
Answers
The option Jack can use to locate and delete temporary files is c. Windows Disk Cleanup. By using Disk Cleanup, users can recover valuable storage space on their hard drive, improve system performance, and free up space for new files and data.
Disk Cleanup can be accessed from the Start menu or by running the "cleanmgr.exe" file from the command prompt. Windows Disk Cleanup is a built-in tool in the Microsoft Windows operating system that helps users free up space on their hard drive. The tool scans the hard drive for files and data that can be safely deleted and displays the results in a list for the user to review and select. Some of the types of files and data that can be deleted through Disk Cleanup include temporary internet files, system error memory dumps, and old Windows installation files.
Learn more about Windows Disk Cleanup: https://brainly.com/question/15054566
#SPJ4
Several key people were involved in programming-language development in the 1970s and 1980s.
Choose all that apply.
Bjarne Stroustrup released C++ programming language in the1980s.
John McCarthy developed LISP for artificial intelligence.
Bill Gates and Paul Allen released the first programming language for a personal computer.
Niklaus Wirth developed Pascal to teach programming.
Answers
Answer: 1,3,4
Explanation: These are correct answers
Several key people were involved in programming-language development in the 1970s and 1980s:
Bjarne Stroustrup released C++ programming language in the 1980s.
John McCarthy developed LISP for artificial intelligence.
Niklaus Wirth developed Pascal to teach programming.
Thus, options A, B and D are the correct options.
In the realm of programming-language development during the 1970s and 1980s, several notable figures left a lasting impact. Bjarne Stroustrup ushered in the 1980s by introducing the C++ programming language, an extension of C that brought object-oriented principles to the forefront. John McCarthy's contributions were marked by his creation of LISP, a language pivotal for artificial intelligence research and symbolic processing.
Meanwhile, Niklaus Wirth's innovation lay in Pascal, a language designed with pedagogy in mind, facilitating programming education. However, the claim of Bill Gates and Paul Allen released the first programming language for personal computers is inaccurate, as their pivotal role was in software and operating systems, not language development.
Thus, options A, B and D are the correct options.
Learn more about programming-language here:
https://brainly.com/question/32901513
#SPJ3
how was the background for the revolution of 2007 prepared
Answers
Answer:
Answer is in the attachment.
Hope this helps..
Which one of the following wireless transmission types requires a clear LOS to function?o Bluetootho NFCo IRo Wi-Fi
Answers
Infrared is the sort of wireless transmission that needs a clear LOS (line of sight) to work (IR). A clear channel must exist between the transmitter and receiver for infrared signals.
What kind of antenna, specifically across long distances, is used in a point-to-point link?Yagi antennas are useful for creating point-to-point links between buildings or in long, narrow spaces (for example, connecting to a distant point in a valley). They can also be utilised to increase a point-to-multipoint network's range.
What is the mobile Bluetooth range, measured in metres?The Bluetooth connection's range is roughly 30 feet (10 meters). However, depending on obstructions (people, metal, walls, etc.) or the electromagnetic environment, the maximum communication range may vary.
To know more about Bluetooth visit:-
https://brainly.com/question/13072419
#SPJ4
Which utility causes the computer to run slow? defragmentation utility OR compression utility?
Answers
Answer:
compression
Explanation:
Question 2 of 10
Priscilla wants to learn her grandmother's native language after seeing social
media highlighting her family's homeland. What type of impact is this?
A. Social and economic
B. Economic and personal
C. Personal and cultural
D. Ethical and personal

Answers
i thinkkkkkkkkkkkkkkkk D
Priscilla wants to learn her grandmother's native language after seeing social media highlighting her family's homeland. Thos is ype of impact is this D. Ethical and personal.
What is the cultural impact?Ethics are critical to people due to the fact they serve as (1) requirements of conduct for figuring out an accurate route of action, (2) pointers for decision-making and warfare resolution, and (3) impacts on worker motivation.
Changes that have an effect on people's surroundings (architecture, arts, customs, rituals etc.) because of influxes of travelers represent cultural impacts.
Read more about the Ethical and personal:
https://brainly.com/question/1031443
#SPJ2
Make the following code to be secure. #include <stdio. h> #include <stalib. h> int main () char *buffer; int index; char chi const char filename = "classExercise2c. txt"; FILE *fp; buffer = (char *) malloc ( sizeof (char) * 32 ) ; printf ("Type some text: ") ; index = 0; while ( (ch=getchar () ) ) f buffer [index] = ch; index++; if( ch == '\n') break; /* cap the string */ buffer [index] = '\0'; fp = fopen (filename, "w") ; fwrite (buffer, 1, index, fp) ; fclose (fp) ; printf ("8s created\n", filename) ; return (0) ;
Answers
By implementing these changes, you will ensure that the code is more secure and less prone to vulnerabilities. Remember to validate and sanitize user input in real-world scenarios to further enhance security.
To make the code secure, we need to address potential vulnerabilities and enhance the overall safety of the program. Here are the steps you can take to achieve that:
1. Include the necessary header files:
- Replace "#include " with "#include ".
- Replace "#include " with "#include ".
2. Declare variables properly:
- Declare "char ch" instead of "char chi" to store the user input character.
- Move the declaration of "char *buffer" and "int index" inside the main() function.
3. Initialize variables:
- Set "char ch" to 0 before the while loop.
- Initialize "index" to 0 before the while loop.
4. Validate user input:
- Check if "index" is within the range of 0 to 31 before storing the character in the buffer. This prevents buffer overflow.
- Add a condition inside the while loop to break if the user enters a newline character ('\n').
5. Free memory:
- After writing the buffer to the file and closing it, free the allocated memory by adding "free(buffer);" before "return (0);".
To know more about scenarios visit:
https://brainly.com/question/32621521
#SPJ11
Internet sites such as eBay make it easier for sellers and buyers to find one another and, by doing so,a. reduce the number of exchanges that occur.b. lower the value created by the goods and services available.c. increase transaction costs.d. reduce transactions costs.
Answers
The correct answer is (d) reduce transactions costs. Financial intermediaries lower transaction costs by "achieving economies of scale" and as transaction size increases, transaction fees per dollar of capital decrease.
Who was the Internet's founder?Vinton Cerf and Bob Kahn, two computer scientists, developed the modern Internet as a system and its communication protocols.
Who is the internet's owner?If you view the Internet as a single, unified thing, nobody truly owns it. The Despite the fact that the Internet is not their property, numerous organisations control its structure and functioning. There is no government or organisation that controls the Internet.
To know more about Internet visit:
https://brainly.com/question/21565588
#SPJ4
Why is it important to use sort and
filter to manage data in a spreadsheet?
Answers
It is important to use sort and filter to manage data in a spreadsheet because they allow for efficient organization, analysis, and retrieval of specific information from large datasets.
Sorting data in a spreadsheet enables the arrangement of data in a desired order based on selected criteria such as alphabetical, numerical, or chronological. This allows for easier identification of patterns, trends, or outliers within the dataset. Sorting helps in visualizing the data in a structured manner, making it more comprehensible and facilitating decision-making processes.
Filtering data allows users to selectively display or hide specific subsets of data based on defined criteria. By applying filters, users can focus on specific aspects of the dataset, such as specific values, ranges, or categories, and exclude irrelevant information. This helps in narrowing down the data and extracting meaningful insights, saving time and effort by eliminating the need to manually scan through large amounts of data.
Using sort and filter functions in spreadsheet management enhances data manipulation and analysis capabilities. These features enable users to explore and analyze data from different perspectives, identify relationships, identify and correct errors, and generate meaningful reports or summaries. Additionally, they support data integrity by allowing users to ensure consistency, accuracy, and relevance in their data analysis processes.
Learn more about spreadsheet
brainly.com/question/27729752
#SPJ11
What are the 2 types of Digital Imagery?
Answers
Answer:
vector or raster
Explanation:
Complete the question in Python for 100 points and brainliest.
The RetailItem class they discuss in the problem is right here in a separate screenshot.


Answers
An example implementation of the CashRegister class that incorporates the required methods is given below.
How to explain the informationThe program will be:
class CashRegister:
def __init__(self):
self.items = []
def purchase_item(self, item):
self.items.append(item)
def get_total(self):
total = 0
for item in self.items:
total += item.get_price()
return total
def show_items(self):
if not self.items:
print("No items in the cash register.")
else:
print("Items in the cash register:")
for item in self.items:
print(item)
def clear(self):
self.items = []
Learn more about program on
https://brainly.com/question/26642771
#SPJ1
public class Main extends Exception { 2 3 public Main(){} 4- public Main(string str) { 5 super(str); } 7 int importantData = 5; 9 public static void main(String[] args) { Main t = new Main(); t.importantMethod(); 12 } 13 14 private void importantMethod(){ 15 if( importantData > 5) 16 throw new Main("Important data is invalid"); 17 else 18 System.out.println(importantData); 19 } } 20 }What is the output?
a. No Output
b. 5
c. Exception-Important Data is invalid
d. Compilation error
Answers
The second option is correct : b. 5. The code defines a class called "Main" that extends the "Exception" class. It has two constructors - one with no arguments and the other with a string argument, which it passes to the parent Exception class using the "super" keyword.
The output of the code would be "Exception-Important Data is invalid" (Option c). This is because the code defines a custom exception class "Main" which extends the built-in "Exception" class. The code also defines a private method "importantMethod()" which throws an exception if the "importantData" variable is greater than 5. In the "main" method, an instance of the "Main" class is created and its "importantMethod()" is called. Since the value of "importantData" is 5, the else block is executed and "5" is printed to the console. However, if the value of "importantData" was greater than 5, the if block would have executed and thrown a new instance of the "Main" exception with the message "Important data is invalid".
To know more about Exception visit :-
https://brainly.com/question/31678510
#SPJ11
what is the plan to make optimum usage of available spaces?
Answers
Answer:
dergragmentation or share to speed up procceces
800,000= 180,000(P/AD, i,5) + 75,000(P/F,i,5) I want to find interest rate (i)
Would you let me know how to calculate this using Excel?
Answers
here is how to compute the above using Excel.
How to calculate the aboveOpen a new Excel spreadsheet and enter the following values in the cells:
Cell A1: 800,000 (Total amount)
Cell A2: 180,000 (Payment at the end of each period)
Cell A3: 75,000 (Payment at the beginning of each period)
Cell A4: 5 (Number of periods)
In cell A5, enter an initial guess for the interest rate (i). For example, you can start with 0.1 (10%).
In cell B1, enter the formula =A2*PMT(A5,A4,0) to calculate the present value of the periodic payments at the end of each period.
In cell B2, enter the formula =A3*PMT(A5,A4-1,0) to calculate the present value of the periodic payments at the beginning of each period.
In cell B3, enter the formula =A1 - B1 - B2 to calculate the remaining balance.
In cell B4, enter the formula =RATE(A4, B2, B1) to calculate the interest rate.
Learn more about Excel Formula at:
https://brainly.com/question/29280920
#SPJ1
These 2 questions PLEASEEE (:

Answers
Answer:
on the first one pixels on the second i think it is feathering
a type of specialized suite that includes a variety of programs designed to make computing easier and safer.
Answers
A type of specialized suite that includes a variety of programs designed to make computing easier and safer is called computer security suite. It is a software program that provides security for different aspects of your computer.
It is designed to protect you from hackers, viruses, and malware. It typically includes antivirus, firewall, anti-spam, and anti-spyware software. Antivirus software is one of the most important components of a computer security suite. It is designed to protect your computer from viruses and other malicious software. A firewall is another important component of a computer security suite. It helps protect your computer from unauthorized access and blocks traffic from known malicious sources.
Anti-spam software is designed to block unwanted emails that may contain malware or phishing scams. Anti-spyware software is designed to detect and remove spyware from your computer. In conclusion, a computer security suite is an important software program that provides security for different aspects of your computer. It includes antivirus, firewall, anti-spam, and anti-spyware software.
Learn more about specialized suite: https://brainly.com/question/25849396
#SPJ11
A nested folder Can best be described as what?
Answers
Answer:
A nested folder can be described as a folder within a folder, or a subfolder.
!! please help !!
What is a nameable container used for organizing and storing data?

Answers
Answer:
Variable
Explanation:
Variable is a container for storing the data. In any programming language, a variable is used to store the data or the value that is used in the program for execution
Answer:
D. Varaible
Explanation: