Type of protocol used in network management systems for monitoring network-attached devices is called?
Answers
The type of protocol used in network management systems for monitoring network-attached devices is called the Simple Network Management Protocol (SNMP).
SNMP is a standard protocol used to manage and monitor network devices such as routers, switches, and servers. It allows network administrators to collect and organize information about these devices, as well as configure and control them remotely. SNMP operates on a client-server model, where network devices act as agents that send information (called SNMP traps or notifications) to a central management station.
The NMS uses SNMP to query the devices for specific information, such as their status, performance metrics, and configurations. SNMP uses a hierarchical structure called the Management Information Base (MIB) to organize and define the data that can be accessed and managed by the NMS.
To know more about SNMP visit:
https://brainly.com/question/33724548
#SPJ11
Related Questions
explain the basic operations of a computer system
Answers
Answer:
OPERATING ON INSTRUCTIONS GIVEN AND HOW IT IS GIVEN
the built-in object class . question 24 options: is the base class for most, but not all, classes defines multiple methods including tostring() and equals() is derived from class super defines tostring() and no additional methods
Answers
The base class for most classes, but not all, typically defines several methods, including toString() and equals(). It is derived from the superclass, which defines toString() and does not have any additional methods.
In object-oriented programming, a base class serves as a template or blueprint for other classes to inherit from. Most classes in a program usually derive from a common base class, although there may be exceptions. The base class often provides common functionality or attributes that are shared among its derived classes. One common practice in many programming languages is to include certain methods in the base class that are applicable to most derived classes. Two commonly included methods are toString() and equals(). The toString() method is responsible for providing a string representation of the object, which is useful for debugging or displaying the object's state. The equals() method is used to compare two objects for equality.
The base class, being the superclass, itself inherits from another class, known as the super. In this case, the superclass defines the toString() method but does not introduce any additional methods. Therefore, when the base class is derived from the superclass, it inherits the toString() method and does not have any extra methods of its own. It's important to note that the specifics may vary depending on the programming language and the design choices made in a particular system. However, the concept of a base class with common methods, derived from a superclass that provides the toString() method, is a common pattern in object-oriented programming.
To learn more about object-oriented programming, click here: brainly.com/question/28732193
#SPJ11
this is very simple i just need someone to type out this for me
Answers
Answer:
#27
2i , -2i, i, -i i^2 = -1
1(x - 2i)(x + 2i) 1(x-i)(x+i)
x^2 +2x-2x -4.2i x^2 -xi-xi -i
(x^2 + 4) x^4 + 1
x^2 +x^2 +11x
x^4 +5x^2 +4
+4+2+2+-1
*This was not simple for me
Find the total cost of a $125 coat purchased in Los Angeles County where the sales tax is 9%. Use the expression c + 0.09c
A
$11.25
B
$112.50
c
$126.25
0 $136.25
Answers
In ad hoc mode, devices can only communicate between themselves and cannot connect to another network.
True or false?
Answers
The statement is true: in ad hoc mode, devices can only communicate between themselves and cannot connect to another network. In ad hoc mode, devices can only communicate with each other and cannot connect to another network.
Ad hoc mode, also known as peer-to-peer mode or independent basic service set (IBSS) mode, is a wireless networking mode where devices can directly communicate with each other without the need for a central access point (AP). In ad hoc mode, devices form a temporary network and rely on each other to establish connections and share data.
In this mode, devices create a local network among themselves, often referred to as a "mesh network." Devices within the ad hoc network can communicate with each other by directly transmitting data between devices.
However, in ad hoc mode, devices do not have the capability to connect to another network, such as a traditional infrastructure network with an access point that connects to a wired network or the internet. Ad hoc mode is primarily designed for device-to-device communication within a limited range and is not intended for connecting to external networks.
Learn more about network here: https://brainly.com/question/30456221
#SPJ11
limitation of the 8-bit extended ASCII character set is that it can only represent up to 128 explain how can these limitations can be overcome?
Answers
Write an assembly program to find the largest item in an array and store it in a variable named MAXIMUM. Hint: Use both Jump and loop instructions to write the program. Logic: Assume that the first item of the array is the minimum and store it in variable MAXIMUM Write a loop. Inside the loop, compare the each array item with the minimum If the array item is less than the MAXIMUM, update MAXIMUM with that array item. . Data Array WORD 10, 2, 23, 45, 21, 11 MAXIMUM WORD
Answers
Use the knowledge of computational language in C++ to write the a code assembly program to find the largest item.
How to write a maximum function in C++?To make it simpler the code is described as:
#include<bitd/stdc++.h>
Using namespace std;
Int main(){
Int arr[10]={10, 2, 23, 45, 21, 11};
Int min=INT_MAX;
Int max=INT_MIN;
for(int i=0;i<10;i++)
If(min<arr[i])min=arr[i];
for(int j=0;j<10;j++)
if(max>arr[j])max=arr[j];
Cout<<max<<” “<<min<<endl;
return 0;
See more about C++ code at brainly.com/question/19705654

Say true or false
Computer is the main tool of ICT.
b. Cyber crimes play positive role for better use of ICT
Answers
a) true
b) false
Select the correct answer.
Nancy wants to buy a cooking stove that’s electrically insulated and resistant to heat. What material should she choose for the cooktop?
A.
composite
B.
polymer
C.
metal
D.
ceramic
E.
semiconductor
Answers
Answer:
E I think is the best answer
T/F. A function has only input parameters but can return multiple values.
Answers
The given statement "A function has only input parameters but can return multiple values" is true because a function can accept one or more input parameters and can return one or more output values.
In programming, a function is a self-contained block of code that performs a specific task and can be called or invoked by other parts of the program.
A function can have zero or more input parameters, which are values passed to the function for processing, and it can also return zero or more output values, which are the results of the function's processing.
So, it is possible for a function to have only input parameters but return multiple values. This is achieved by returning the values as a tuple or a list, which can be unpacked by the calling code. Overall, the flexibility of functions makes them a powerful tool for developers to create reusable and modular code.
For more questions like Function click the link below:
https://brainly.com/question/30011747
#SPJ11
There are many reasons to convert to the decimal numbering system. Select the best answer. When checking numeric values in computer memory, decimal makes sense because you use decimal numbering every day. When checking words in computer memory, decimal makes sense because you use decimal numbering every day. When comparing values in a computer program, decimal numbering makes sense because it is always shorter than hexadecimal. When checking words in computer memory, decimal numbering makes sense because it is easier than hexadecimal.
Answers
Answer:
first statement makes most sense.
Explanation:
When checking numeric values in computer memory, decimal makes sense because you use decimal numbering every day. --> sounds OK.
When checking words in computer memory, decimal makes sense because you use decimal numbering every day. --> doesn't make sense
When comparing values in a computer program, decimal numbering makes sense because it is always shorter than hexadecimal. --> Not true
When checking words in computer memory, decimal numbering makes sense because it is easier than hexadecimal. --> Hexadecimal would be easier when inspecting computer words, because you can easily see the byte alignment of the values.
Answer:
the first statement
Explanation:
got it right on edge
The ________ function concatenates the contents of one c-string with another c-string. strcopy strappend strcat stradd none of these
Answers
The strcat() function concatenates the contents of one c-string with another c-string.
The strcat() function concatenates string2 to string1 and ends the resulting string with the null character.
The strcat() function works on null-ended strings. The string arguments to the function should contain a null character (\0) that marks the end of the string.
How does strcat function works C++?
The strcat() function takes two statements: dest and src . This function appends a copy of the character string pointed to by src to the end of the string pointed to by dest. The null terminating character at the end of dest is replaced by the first character of src and the resultant character is also null-terminated.
To learn more about strcat() function , refer
https://brainly.com/question/15683939
#SPJ4
Web technologies like Flash, CSS, Java, and HTML often depend on APIs to accomplish what task?
Answers
In Programming, web technologies like the front end part e.g Flash, CSS, Java, and HTML depends on back end APIs for task like data persistence, sending and getting data e.g post and get request in summary perform CRUD(Create, read, update and delete) operations
The development of web application is basically divider into two
The front end, done basically with technologies like HTML CSS, JavaScriptBack end, this can be done using Python, C#, Java, or any suitable languageTh front end depends on the back end for sending and retrieving information
Learn more:
https://brainly.com/question/8391970
hw4a.3. floating point precision for a binary floating point system of the form , with an exponent range from to , what is the minimum for which the number can be represented exactly?
Answers
An exponent value of 127 reflects the actual zero, while the exponent is an 8-bit unsigned integer with a skewed range of 0 to 255. Since exponents of 127 (all 0s) and +128 (all 1s) are reserved for exceptional numbers, the exponent ranges from 126 to +127.
What is the exponential function's range?All real numbers comprise the exponential function's domain. Any real integers greater than zero fall inside the range.
How can I convert from 32-bit binary to decimal?In binary, what is 32? Binary 32 equals 100000. To convert 32 to binary, divide it by 2 in successive iterations until the quotient equals 0.
To know more about binary visit:-
https://brainly.com/question/19802955
#SPJ1
I’ll give Brainly if u answer all please
ASAP

Answers
Answer:
Answers are: 38, 135, 23, 209, 53 & 181 respectively
Explanation:
How do cell phones negatively affect students in the classroom?
Answers
Cell phones negatively affect students with a divert attention and have a detrimental effect on cognitive ability, reaction times, performance, and enjoyment of focused tasks.
What is cognitive ability?Any task, no matter how simple or difficult, requires cognitive abilities, which are brain-based skills. They are less concerned with actual knowledge and more with the processes by which we learn, remember, solve problems, and pay attention.
For instance, picking up the phone requires motor skills (lifting the receiver), language skills (talking and understanding language), perception (hearing the ring tone), decision-making (answering or not), and social skills.
Particular neuronal networks provide support for cognitive abilities or skills. For instance, the temporal lobes and some parts of the frontal lobes are primarily responsible for memory functions. Due to damaged neuronal regions and networks, people with traumatic brain injuries may have lower cognitive function.
Learn more about cognitive abilities
https://brainly.com/question/9741540
#SPJ4
In the market for reserves, if the federal funds rate is above the interest rate paid on excess reserves, then an open market ________ the supply of reserves, raising the federal funds interest rate, everything else held constant. sale decreases sale increases purchase decreases purchase increases
Answers
In the market for reserves, if the federal funds rate is above the interest rate paid on excess reserves, then an open market sale decreases the supply of reserves, raising the federal funds interest rate, everything else held constant.
When the federal funds rate is above the interest rate paid on excess reserves, it indicates that banks can earn a higher return by lending their excess reserves to other banks in the federal funds market. In this scenario, the central bank can conduct an open market sale, which involves selling government securities to banks. This sale reduces the reserves available to banks, decreasing the supply of reserves in the market.
Learn more about market here;
https://brainly.com/question/15483550
#SPJ11
A custom object Trainer_c has a lookup field to another custom object Gym___c.Which SOQL query will get the record for the Viridian City gym and it's trainers?A. SELECT Id, (SELECT Id FROM Trainer_c) FROM Gym_c WHERE Name - Viridian City Gym'B. SELECT ID FROM Trainer_c WHERE Gym__r.Name - Viridian City Gym'C. SELECT Id, (SELECT Id FROM Trainers) FROM Gym_C WHERE Name - Viridian City Gym'D. SELECT Id, (SELECT Id FROM Trainers) FROM Gym_C WHERE Name . Viridian City Gym'
Answers
SELECT ID FROM Trainer_c WHERE Gym__r. Name = 'Viridian City Gym'. In Salesforce, the relationship between two custom objects is represented by a lookup field.
This query retrieves the Id field from the Trainer_c object where the related Gym__c object's Name field is equal to "Viridian City Gym". In this case, the Trainer_c object has a lookup field to the Gym_c object, represented by the Gym__r notation in the query.
The query uses the WHERE clause to filter the results so that only trainers who are associated with the gym named "Viridian City Gym" are returned. The SELECT clause specifies which fields to retrieve, in this case only the Id field of the Trainer_c object.
Salesforce Object Query Language is known as SOQL. The database of your organization's can be read using SOQL. Syntactically, SOQL and SQL are comparable (Structured Query Language). A SOQL query can be created and run in Apex code or in the Query Editor of the Developer Console.
To know more about SOQL query visit: https://brainly.com/question/30138701
#SPJ4
4.11 lesson practice edhesive questions 4 and 5

Answers
Answer:
It may just be me but I can't see the picture
Explanation:
Answer:
4. Monte carlo simulations
I need the answer for number 5 please.
Explanation:
Help me!!
1.03!! need major help!!
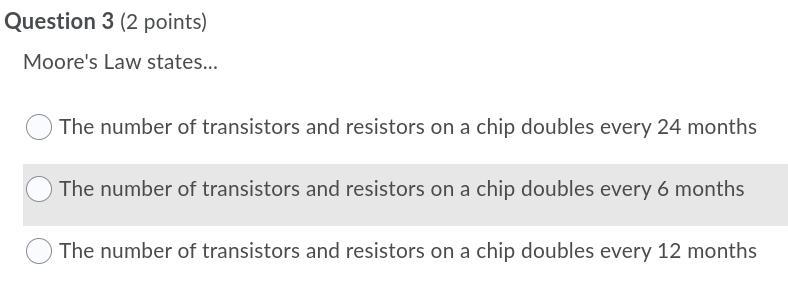
Answers
Answer: the answer is A
Explanation:
Moore's law, prediction made by American engineer Gordon Moore in 1965 that the number of transistors per silicon chip doubles every year. ... Moore observed that the number of transistors on a computer chip was doubling about every 18–24 months.
Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
a team of researchers wants to create a program to analyze the amount of pollution reported in roughly 3,000 counties across the united states. the program is intended to combine county data sets and then process the data. which of the following is most likely to be a challenge in creating the program? responses a computer program cannot combine data from different files. a computer program cannot combine data from different files. different counties may organize data in different ways. different counties may organize data in different ways. the number of counties is too large for the program to process. the number of counties is too large for the program to process. the total number of rows of data is too large for the program to process.
Answers
A team of researchers wants to create a program to analyze the amount of pollution reported in roughly 3,000 counties across the United States. The program is intended to combine county data sets and then process the data. The most likely to be a challenge in creating the program B. Different counties may organize data in different ways.
This can lead to inconsistencies in the format and structure of the data, making it difficult for the program to combine and process the data effectively. Although computer programs can combine data from different files (response A), the challenge lies in ensuring that the data is structured consistently so that it can be combined accurately.
This may require the researchers to preprocess the data, standardizing the format and structure across all county data sets. The number of counties (response C) and the total number of rows of data (response D) are unlikely to be challenges for the program, as modern computers and software can handle large amounts of data efficiently. The key issue here is ensuring that the data is organized in a way that the program can process and analyze it effectively, which may require additional work from the researchers to clean and restructure the data before processing. Therefore, the correct option is B.
Know more about Researchers here:
https://brainly.com/question/25257437
#SPJ11
what function do you need to call to ask the user of the program to enter text?
Answers
Answer:
raw_input() function
The function that one need to call to ask the user of the program to enter text is the readLine function. The correct option is a.
What are the functions of programming?Code units that are "self contained" and carry out a particular purpose are called functions. Typically, functions "take in," "process," and "return" data and results. Once a function has been written, it can be utilized countless times.
It is possible to "call" functions from within other functions. These coding building pieces are known as functions in programming. There are input and output in every programming function.
The function has instructions that are used to translate its input into output. It is comparable to a cow that consumes grass (the input), converts it into milk, and then is milked by a dairy farmer (the output).
Therefore, the correct option is a. readLine.
To learn more about functions, refer to the link:
https://brainly.com/question/29760009
#SPJ5
The question is incomplete. Your most probably complete question is given below:
readLine
readln
text
println
Match the terms with their explanations.

Answers
Answer:
Zoom helps move the object of view further or closer
White Balance tells the camera what each color should look like
Shutter controls how long light enters the camera
focus provides sharper images by way of a ring at the front of the lens
Explanation:
Took photography classes
How did technology advance during World War II- catapult computing int a new modern are?
Answers
The technological advance during World War II helped in bomb sightings, communication was stronger, and the discovery of penicillin saved the lives of many people.
What was World War II?World War II happened from 1939 to 1945, during this time much advancement in technology happened compared to World War I.
Effective Blitzkrieg operations relied on radio communications, which allowed commanders to plan the advance and throw the opponent off guard.
Therefore, the development of technology during World War II improved bomb spotting, communication, and the discovery of penicillin, which helped save countless lives.
To learn more about World War II, refer to the link:
https://brainly.com/question/27753772
#SPJ1
_____ returns the smallest integer greater than or equal to 7.3
Assume you have already entered the following line.
from math import
ceil(7.3)
floor(7.3)
larger(7.3)
round(7.3)
Answers
Answer:
Explanation:
Required
Which returns smallest integer greater than or equal to 7.3
i.e.
\(x \le 7.3\)
When executed, the result of each instruction is:
\(ceil(7.3) = 8\) -- This returns the smallest integer greater than 7.3
\(floor(7.3) = 7\) --- This returns the smallest integer less than 7.3
\(larger(7.3)\) --- there is no such thing as larger() in python
\(round(7.3) = 7\) --- This rounds 7.3 to the nearest integer
From the above result,
8 is the smallest integer greater than or equal to 7.3
i.e.
\(8 \ge 7.3\)
Hence:
\(ceil(7.3)\) is correct
Your customer said that the language used in your program was offensive. This is an aspect of
O accuracy
O efficiency
O usability
O propriety
Answers
Answer: USABILITY
Explanation:
Perhaps efficiency
Answer:
Propriety
Explanation:
Right on Edge
Question #2
Dropdown
Choose the correct term to complete the sentence.
In the _____ model, each computer in a network can act as a server for all the other computers, sharing files and access to devices.
A.) peer-to-peer
B.) host-server
C.) client-server
Answers
Answer - A: peer-to-peer
Explanation: Correct on my Edg 2020/2021 for my state.
In the client-server model, each computer can act as a server for other computers, facilitating file sharing and device access. Therefore, option C is correct.
The client-server model is a network architecture where computers, referred to as clients, make requests for services or resources from other computers, known as servers.
Clients initiate communication by sending requests, and servers respond by providing the requested services or resources. This model allows for distributed processing, where the workload is divided between clients and servers.
Servers are responsible for managing and providing services, such as file sharing, database access, or web hosting, while clients consume these services. The client-server model facilitates efficient sharing of resources and enables scalable and centralized control in networked environments.
Therefore, option C is correct.
Learn more about client-server model here:
https://brainly.com/question/32440221
#SPJ7
how might b2b and b2c companies approach meeting customer needs differently
Answers
Businesses that cater to both B2B (business-to-business) and B2C (business-to-consumer) consumers frequently take a different approach to satisfying their demands because these customers have distinct needs.
What distinguishes B2B customers from B2C clients?What distinguishes B2B e-commerce from B2C e-commerce? Business to business is known as B2B, whereas business to consumer is known as B2C. B2B ecommerce makes use of online channels to market to other businesses. B2C e-commerce focuses on individual customers.
How do the purchasing processes for B2B and B2C differ?B2B: When purchasing a good or service involves business-related goals, the transaction requires a careful study, more thought, and continued support from the seller. Several business divisions are impacted by the choice. B2C: Typically, the sale is less logical
To know more about consumers visit:-
https://brainly.com/question/28671114
#SPJ1
A computer network that is restricted to the organization it serves; an internal internet.t/f
Answers
A computer network that is restricted to the enterprise it serves is called an internal internet. Therefore, the statement given is a true statement.
An internal internet also referred to as an intranet is a local network that is only accessible to people within an enterprise. The internal internet is the most restricted network. It can be stated as the internal internet is a private network setup within an enterprise that is used to securely share organizational information and computing resources among its employees.
Therefore, it is concluded that the internal internet or intranet is the restricted computer network to be used by the enterprise only.
You can learn more about intranet/internal internet at
brainly.com/question/13139335
#SPJ4