the performance requirements for category 3 cables, connectors, basic links, and channels are specified at frequencies up to ? .
Answers
The performance requirements for category 3 cables, connectors, basic links, and channels are specified at frequencies up to 16 MHz.
Category 3 cables are typically used for voice and low-speed data communication applications. These cables have a maximum length of 100 meters and are often used in residential and small office settings. In order to ensure proper performance, category 3 cables must meet certain specifications. These include requirements for attenuation, crosstalk, and impedance.
Attenuation refers to the loss of signal strength as it travels through the cable. Crosstalk occurs when signals from one cable interfere with signals from another cable. Impedance is the measure of the resistance to the flow of current in the cable. Connectors, basic links, and channels must also meet specific performance requirements at frequencies up to 16 MHz. Connectors must have low insertion loss and high return loss, which helps to minimize signal degradation.
Basic links are made up of cable segments and connectors and must meet the same attenuation, crosstalk, and impedance requirements as the cable itself. Channels are composed of multiple basic links and must meet additional performance requirements related to crosstalk and other forms of signal interference.
know more about frequencies here:
https://brainly.com/question/29213586
#SPJ11
Related Questions
Discuss the Autonomous Robots and Additive Manufacturing contribution to Smart Systems. Why are these two technologies are important for the Smart Systems? Explain the technologies with an example.
Answers
Additive manufacturing, also known as 3D printing, revolutionizes traditional manufacturing methods by constructing objects layer by layer. It enables rapid prototyping, customization, and on-demand production. For instance, in a smart healthcare system, additive manufacturing can be employed to produce personalized medical implants, such as customized prosthetics or dental implants, based on patient-specific requirements, resulting in improved patient outcomes and reduced lead times. Both technologies contribute to the advancement of Smart Systems by optimizing processes, enhancing productivity, and enabling customization in various industries.
Please use python
6. Modify the eye () function to add an inner filled eyeball placed in a random location inside the eye.
Answers
The given task needs us to modify the `eye ()` function to add an inner filled eyeball placed in a random location inside the eye. We can accomplish this task by using the Python turtle library.
We have also added code inside the `eye ()` function to select a random location inside the eye and draw the inner eyeball using the function works by choosing a random x and y location within the bounds of the eye.
The random x and y location can be chosen using the `Randant` method of the `random` module. We have also defined a new variable `inferred` to represent the inner eyeball's radius as one-third of the given `rad` argument (which is the radius of the outer eyeball).Finally, we have called the `draw eyeball (col, rad)` function inside the `eye()` function to draw the inner eyeball in a random location inside the eye.
To know more about library. visit:
https://brainly.com/question/31622186
#SPJ11
Title the document Fuel Analysis. In this document, write a paragraph explaining your observations about the data you have entered and analyzed. Include any observations about when fuels are most expensive to purchase as well as when it is the least expensive to buy. Describe how you can use this information to help make your road trip budget.
Answers
Answer:
Fuel Analysis
Introduction:
In this document, we will analyze the data related to fuel prices and draw observations from the analysis. Our objective is to identify trends in fuel pricing and determine when fuels are most expensive and least expensive to purchase. By understanding these patterns, we can make informed decisions to help manage our road trip budget more effectively.
Observations:
Upon analyzing the data, we have observed certain patterns regarding fuel prices. Firstly, fuel prices tend to be higher during peak travel seasons and holidays when there is an increased demand for fuel. This surge in demand leads to higher prices due to limited supply. Additionally, fuel prices may also be affected by geopolitical factors, such as disruptions in oil production or natural disasters, which can cause temporary price fluctuations. It is important to consider these external factors when planning a road trip and budgeting for fuel expenses.
Furthermore, we have identified that fuel prices often exhibit regional variations. Prices may differ between urban and rural areas, as well as across different states or countries. Factors such as transportation costs, taxes, and regional supply and demand dynamics can influence these variations. It is advisable to research fuel prices along your planned route to anticipate potential cost fluctuations and make informed decisions.
Utilizing the Information:
The observations from this fuel analysis can be highly valuable in budgeting for a road trip. By understanding when fuels are most expensive to purchase, such as during peak travel seasons, we can plan our journey accordingly. This may involve adjusting the timing of our trip to avoid periods of high fuel prices or choosing routes that pass through areas with relatively lower fuel costs. Additionally, being aware of regional variations allows us to make strategic decisions, such as refueling in areas where fuel prices are comparatively lower.
To optimize our road trip budget, we can leverage various resources to stay informed about fuel prices. Online platforms, mobile applications, or even local gas stations can provide real-time information on fuel prices along our route. Additionally, joining loyalty programs or utilizing fuel price comparison websites can help us identify cost-effective options for refueling.
In conclusion, analyzing the data and observing fuel pricing trends enables us to make informed decisions and effectively manage our road trip budget. By considering factors such as peak travel seasons, regional variations, and external influences on fuel prices, we can plan our journey strategically and minimize fuel expenses. This proactive approach will ensure a more enjoyable and financially sound road trip experience.
After analyzing the data on fuel prices, several observations can be made. Firstly, fuel prices tend to be more expensive during peak travel seasons, such as summer or holiday periods, and during times of high demand, such as during major events or natural disasters. Additionally, fuel prices tend to be higher in urban areas compared to rural areas due to higher demand and operating costs.
On the other hand, fuel prices are generally lower during the winter months when there is less demand for travel and during times of economic recession when demand for fuel decreases. Furthermore, fuel prices may be lower in areas where there is more competition among fuel providers.
Knowing when and where fuel prices are likely to be higher or lower can be helpful in planning a road trip budget. By researching fuel prices along your planned route and considering the time of year, you can estimate the amount of money you will need to spend on fuel and adjust your travel plans accordingly. Additionally, you may be able to save money by filling up at gas stations in areas with lower fuel prices or by using fuel rewards programs offered by some providers.
Which of the following devices converts computer output into displayed images?
a. printer
b. monitor
c. modem
d. processor
e. hard-disk drive
Answers
A monitor, also known as a display or screen, is the device that converts computer output into displayed images. It receives data from the processor and displays the information as visual content.
So, the correct answer is B.
Monitors come in various types, such as CRT, LCD, and LED. Unlike printers, which produce physical copies, monitors provide a real-time view of digital content.
Modems and hard-disk drives are not involved in the conversion of computer output into displayed images, as modems are responsible for data transmission and hard-disk drives store digital information.
Hence, the answer of the question is B.
Learn more about output devices at
https://brainly.com/question/13014449
#SPJ11
, , ,g d,t ,dt m,dt ymtd
Answers
Answer:ummm me confused
Explanation:
which kind of system software tells the computer how to communicate with peripherals, such as a printer or scanner?
Answers
The kind of system software that tells the computer how to communicate with peripherals, such as a printer or scanner, is known as "device driver."
A device driver is a set of computer programs or software files that run specific devices or gadgets to perform their designed functions while connected to the computer system.
A device driver is a form of software file that ensures hardware device functions as designed.
Several types of device drivers include:
BIOS;Motherboard Drivers;Hardware Drivers;Virtual Device Drivers.Hence, in this case, it is concluded that the correct answer is Device Driver.
Learn more here: https://brainly.com/question/19473613
Match each type of short- and long-term investment to its attribute. long-term bonds stocks US Treasury bonds mature after 12 months and may be issued by corporations or government entities arrowRight a type of loan to the US government that has minimal risk arrowRight can be held for years, typically for future growth potential arrowRight
Answers
Hope this Helps :)
Corporate or governmental bodies may issue bonds that have a 12-month maturity — enduring bonds, a low-risk loan to the US government is provided via US Treasury Bonds, can be held for years, usually for possible future growth — stocks.
What is a low-risk loan?No security is needed from the borrowers to obtain these loans. Additionally, the loan money may be utilized for any private purpose, including debt relief, house improvements, car purchases, trips, and weddings.
A loan that is considered to carry a larger risk of defaulting than other, more conventional loans is called a high-risk loan. One or more reasons may be to blame for the higher default risk when evaluating a loan request.
The loans that are most likely to be accepted for include payday loans, auto title loans, loans from pawn shops, and personal installment loans. These are all short-term emergency cash assistance options for those with bad credit.
Thus, Corporate or governmental bodies may issue bonds.
For more information about low-risk loan, click here:
https://brainly.com/question/16930597
#SPJ2
what was the first computer name brand
Answers
Answer: Electronic Controls Company and was founded in 1949 by J. Presper Eckert and John Mauchly.
hope this helps!
The first computer name brand was MITS and the computer was named The Altair.
Explanation:
Hope this help! Jesus loves you!
Have a great day!
Explain the expression below
volume = 3.14 * (radius ** 2) * height
Answers
Answer:
Explanation:
Cylinder base area:
A = π·R²
Cylinder volume:
V = π·R²·h
π = 3.14
R - Cylinder base radius
h - Cylinder height
which two functions can be performed with a next generation firewall but not with a legacy firewall?
Answers
Two functions that can be performed with a next-generation firewall (NGFW) but not with a legacy firewall are "deep packet inspection" and "application-level filtering."
Next-generation firewalls provide enhanced capabilities beyond traditional or legacy firewalls. They incorporate advanced technologies and features that enable more granular and context-aware control over network traffic.
1. Deep Packet Inspection (DPI): NGFWs can perform deep packet inspection, which involves analyzing the content of network packets at the application layer. This allows them to inspect not only the header information but also the payload of the packets. By understanding the actual application protocols and data within the packets, NGFWs can make more informed security decisions, detect and block specific types of malicious activities, and enforce more sophisticated security policies.
2. Application-level Filtering: NGFWs have the ability to identify and control networK traffic based on specific applications or application categories. They can identify the applications in use, regardless of the port or protocol being used. With application-level filtering, NGFWs provide more precise control over network traffic, allowing organizations to enforce policies that are based on applications rather than just IP addresses or ports. This enables better visibility into application usage, improves security by blocking unauthorized or high-risk applications, and allows for more effective bandwidth management.
In summary, next-generation firewalls offer capabilities such as deep packet inspection and application-level filtering that go beyond what legacy firewalls can provide. These functions enhance network security, improve policy control, and enable more effective management of network resources.
learn more about firewalls here; brainly.com/question/31753709
#SPJ11
What are the missing whole numbers on this number line? Enter your answers in the boxes. plz show work I'm I need answer 3rd grade

Answers
Which of the following best describes why an error occurs when the classes are compiled?

Answers
The error occurs when the classes are compiled is class Alpha does not have a defined constructor. The correct option is A.
What is compilation?Because a computer cannot directly grasp source code. It will only comprehend object-level programming. Even though source codes are in a human readable format, the system cannot comprehend them.
Compilation is the procedure used by computers to translate high-level programming languages into computer-understandable machine language. Compilers are the programmes that carry out this conversion.
When the classes are compiled, there is an error because class Alpha does not have a defined.
Thus, the correct option is A.
For more details regarding compilation, visit:
https://brainly.com/question/28232020
#SPJ1
A Windows 10 PC on the network is only able to connect to other resources, both public and private, by using IP addresses. What setting needs to be checked via the NIC (Network Interface Card) properties
Answers
The setting that needs to be checked via the NIC (Network Interface Card) properties on a Windows 10 PC in order to connect to other resources using IP addresses is the network adapter's IP configuration.
Specifically, the IP address, subnet mask, and default gateway should be checked to ensure they are correctly configured and match the settings of the network to which the PC is connected. NIC stands for "Network Interface Card." It is a hardware component that connects a computer to a network. It typically includes a connector for a cable, as well as the electronics necessary to transmit data over the network. NICs can be built into a computer's motherboard, or they can be added as a separate expansion card. They may also be built into other devices, such as routers and servers, to provide network connectivity.
Learn more about NIC, here https://brainly.com/question/30087617
#SPJ4
java, visual basic, python and c++ are examples of what type of programming language?
Answers
Marina requested a copy of her credit report in May 2019 and wants to request a second one in November 2019. What is true?
O She can; it is always free
She can, but she may have to pay for it
O She will not obtain it, a free copy can be requested every two years.
O She will not obtain it, the bureau sends it automatically once a year
Answers
Answer:
B. She can, but she may have to pay for it.
Explanation:
A credit report is a report that contains the credit history of an individual. A credit report is issued by Credit bureaus who have financial information of a person.
Credit bureaus issue one credit report for free every year. But if a person desires to issue a credit report more than once a year then he/she will have to pay a fee for it.
In the given scenario, Marina who has requested a copy of the credit report in May 2019, will have to pay a fee for a copy of the second credit report.
Therefore, option B is correct.
Give four advantages for ssd compared to hdd
Answers
Answer:
Explanation:
SSD is not affected by magnets
SSD is more reliable because it uses flash technology instead of platters and arms.
SSD has no moving parts so it has less chance of breaking down
SSD makes no noise because it has no moving parts.
Why do numA and numB have the same scope in the subtract function? def subtract(numA, numB): return numA - numB def divide(numC, numD): return numC / numD answer = subtract(24,6) print (answer)
Answers
Answer:
The output of the subtract method is "18".
Explanation:
In the above-given code, two methods "subtract and divide" is declared, that accepts two variable in its parameter, and method work with there respective names.
In this code, the subtract method accepts two-variable "numA and numB", within the same scope because it helps the method in proper functioning, and if the variable is no defined in the scope it will give an error.
Answer: 18
Explanation: got it right on edgen
Compare and contrast the advantages and disadvantages of the Windows, Apple, and Linux operating systems.
Answers
during a forensics investigation, you need to access a usb thumb drive that you found on the crime scene. before accessing the usb thumb drive, what must you do?
Answers
Before accessing the USB thumb drive, Enable write protection.
What is a USB thumb drive used for?A USB flash drive can be used to store crucial files and data backups, transport favorite settings or applications, perform diagnostics to diagnose computer problems, or boot an operating system. The drives are compatible with Microsoft Windows, Linux, MacOS, many varieties of Linux, and a variety of BIOS boot ROMs.Although the world of technology is always changing, flash drives remain popular. They're an easy approach to back up your data because of their modest size and portability.Because of its small size and design, a USB device is sometimes known as a thumb drive. Thumb drives are typically a few inches long, with width and depth measurements that are fractions of an inch.To learn more about USB refer,
https://brainly.com/question/27800037
#SPJ1
Some one help pls will mark brainless !!!!!
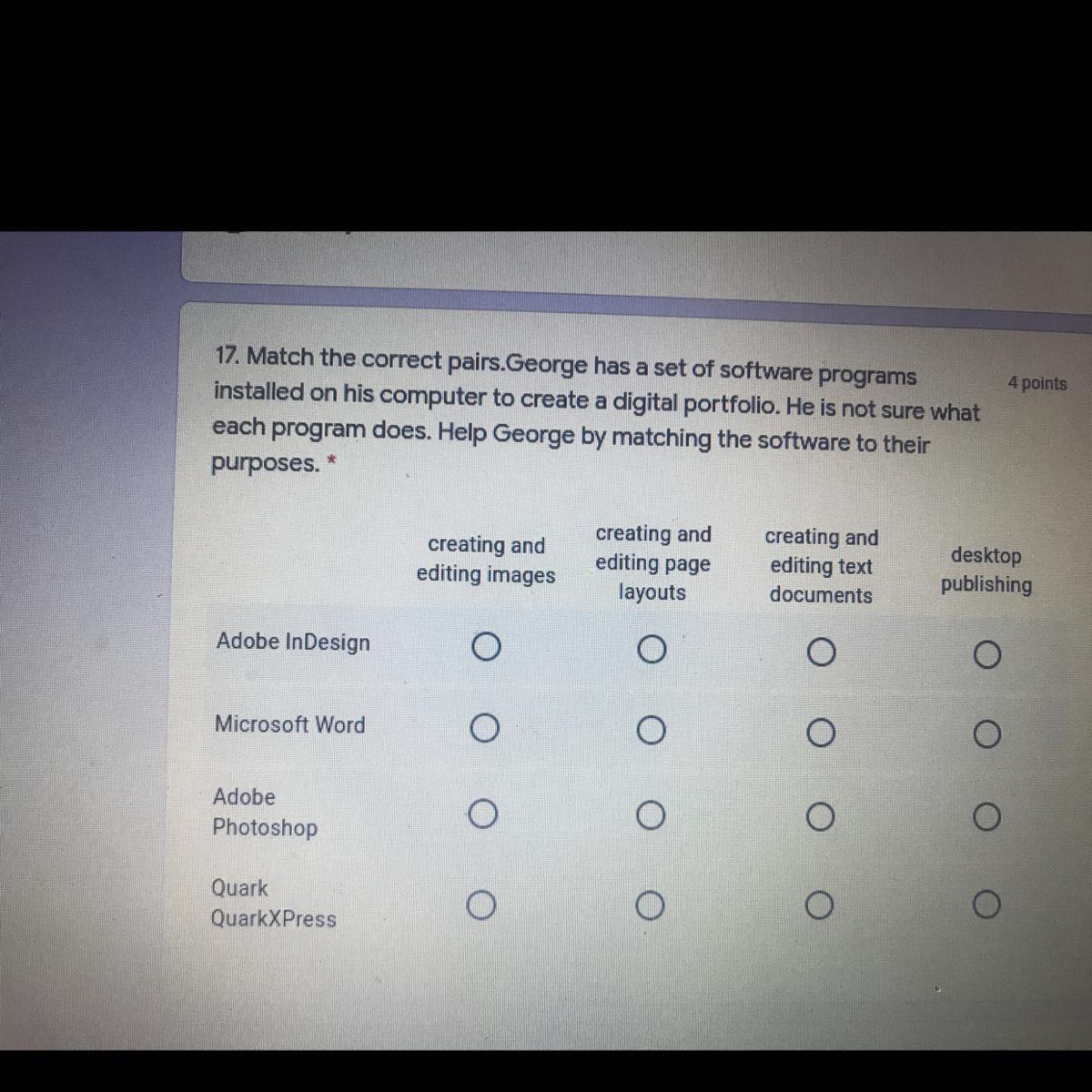
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
Electromagnetic fields flow in what way?
high voltage to low voltage
sender to receiver
high frequency to low frequency
north to south
Answers
Answer: North to South
Explanation:
Electromagnetic field is a field that's caused by moving electric charge. The direction of the electromagnetic field is from the north to the south pole. This direction can be deduced by holding the current carrying conductor in your left hand with the thumb extended pointing in the direction of the electron flow from negative to positive.
Even though electromagnetic fields cannot be seen with our eyes, they are presentcin our environment as they are produced through the build up of electric charges.
Answer:
high frequency to low frequency, or high voltage to low voltage.
Explanation:
All i know is north to south is wrong i got it wrong and had to do a retake on the quiz
A period in which unemployment is low, business produces many goods and services, and wages are good is called ______.
A. prosperity
B. productivity
C. personal income
D. business cycle
Answers
Answer:
A
Explanation:
Jordan just wrote a secret message program in Python that converts the number 7,095 to 1s and 0s. Which number system is Jordan converting to?
A Binary
B Decimal
C Digital
D Hexadecimal
Answers
Answer:
binary
Explanation:
bi-two numbers doesnt meet reqiurments automatically considered 0
Answer:
Binary
Explanation:
i took the test
What was one factor that led to more people seeking jobs in cities and factories?
do any of you gies know how to bet Arceus in legend Arceus
Answers
Answer:
The balance of Economic and political power shifted from agriculture to manufacturing, making industry and cities grow.
Suppose a slide contains three ovals and you want to evenly space the ovals horizontally across the slide. after you select the three ovals, which command would you use to accomplish this?
Answers
The slide's oval shapes can be uniformly spaced apart using the Align tool. Selecting the three ovals and then choosing "Align Horizontally" from the Align panel will accomplish this.
To evenly space three ovals horizontally across a slide in Microsoft PowerPoint, you can use the Align command. Here are the steps:
Select the three ovals that you want to align.
Go to the "Home" tab on the ribbon and click on the "Align" button in the "Arrange" section.
From the drop-down menu, select "Align Center." This will center all three ovals horizontally on the slide. Next, select "Distribute Horizontally." This will evenly space the ovals across the slide so that the same amount of space is between each oval. Finally, check to make sure that the ovals are aligned and spaced correctly. By using the Align and Distribute commands, you can easily and accurately arrange multiple objects on a slide. This can save time and ensure that your presentation looks professional and organized.
To know more about Space ovals Please click on the given link.
https://brainly.com/question/30112524
#SPJ4
I want the objective for this experiment(active high
pass filter)and I neeed the description for this experiment and the
procedure and the conclusion
Answers
The objective of this experiment is to design and build an active high-pass filter and examine its response to a square wave input signal. The filter is built to allow high-frequency signals to pass through and attenuate low-frequency signals. It is also expected to have a gain of at least 1.
The components that will be used include a voltage source, operational amplifier (op-amp), resistors, and capacitors. Below are the description, procedure, and conclusion for this experiment.
Description: An active high-pass filter is a circuit that attenuates signals with frequencies lower than the cutoff frequency while allowing signals with frequencies above the cutoff frequency to pass through. The op-amp is used in this filter because of its ability to amplify the input signal. The circuit is designed to have a gain of at least 1 and a cutoff frequency of 1kHz.
Procedure: The circuit diagram is constructed using the op-amp, resistors, and capacitors as shown below. A 1kHz input square wave signal is applied to the circuit, and the output signal is recorded. The cutoff frequency of the filter is then calculated using the formula:
f = 1/ (2πRC),
where R is the resistance and C is the capacitance. The gain of the circuit is also measured using the formula:
A = Vo/Vi,
where Vo is the output voltage and Vi is the input voltage.Conclusion: The active high-pass filter was found to have a cutoff frequency of 1kHz and a gain of approximately 1.
The input signal was attenuated at frequencies below the cutoff frequency, while signals with frequencies above the cutoff frequency passed through. The circuit was successful in achieving its objective of allowing high-frequency signals to pass through while attenuating low-frequency signals.
To know more about design and build an active high-pass filter visit:
https://brainly.com/question/33228913
#SPJ11
what is the maximum forwarding throughput of switching fabric implemented via memory logic, if the memory bandwidth is such that a maximum of 3b packets per second can be written into or read from memory? explain your answer.
Answers
Switching fabrics are used to help devices communicate with one another in a network. Switching fabrics are responsible for the speed and reliability of a network, so understanding them is critical. When it comes to switching fabric implemented via memory logic, the maximum forwarding throughput can be calculated using a formula.
Max forwarding throughput = (number of memory reads + number of memory writes) x packet size.The number of memory reads and writes are based on the number of packets that need to be forwarded, and the packet size is based on the data being sent.If the memory bandwidth is such that a maximum of 3b packets per second can be written into or read from memory, we can calculate the maximum forwarding throughput as follows:
Max forwarding throughput = (3b + 3b) x packet size.If we assume a packet size of 64 bytes, the maximum forwarding throughput would be:Max forwarding throughput = (3b + 3b) x 64 bytes,Max forwarding throughput = 6b x 64 bytes,
Max forwarding throughput = 384b/second. The maximum forwarding throughput of switching fabric implemented via memory logic, if the memory bandwidth is such that a maximum of 3b packets per second can be written into or read from memory and assuming a packet size of 64 bytes is 384b/second.
To know more about network visit:
https://brainly.com/question/29350844
#SPJ11
________ is the type of security loss that involves computer criminals invading a computer system and replacing legitimate programs with their own unauthorized ones that shut down legitimate applications and substitute their own processing to spy, steal, and manipulate data.
Answers
Answer:
Usurpation
Explanation:
In context of CIBS-210 it is known as Usurpation
In our situation now a days in online class we are experiencing different problems such as internet
problems like internet connection low quality gadgets technical problems using laptops and computers set up as an ict student how can you solve these common learning problems based on the knowledge you gained in computer hardware servicing
Answers
Debugging is finding and fixing problems in an algorithm or program. True
or False.
False
True
Answers
Debugging is finding and fixing problems in an algorithm or program is True statement.
Debugging is indeed the process of finding and fixing problems, errors, or bugs in an algorithm or computer program.
When a program does not produce the expected output or behaves unexpectedly, programmers use debugging techniques to identify and resolve the issues.
This involves analyzing the code, checking for syntax errors, logical errors, and unexpected behavior, and making the necessary corrections to ensure the program functions correctly.
Thus, the given statement is True.
Learn more about Debugging here:
https://brainly.com/question/9433559
#SPJ6