The ______ module performs end-to-end encryption and obtains session keys on behalf of users. A. PKM B. RCM C. SSM D. CCM
Answers
The PKM (Public Key Management) module performs end-to-end encryption and obtains session keys on behalf of users.
End-to-end encryption ensures that the communication between two users is secure and private, by encrypting the data before it is sent and decrypting it only at the recipient's end.
The PKM module is responsible for generating and managing public and private keys for each user, authenticating users, and verifying the digital signatures of messages.
It also generates and distributes session keys for each communication session between two users, which are used to encrypt and decrypt the data exchanged during the session. The PKM module is an essential component of many communication systems, including email, instant messaging, and voice and video conferencing applications, as it provides a secure and reliable mechanism for protecting the privacy of user communications.
Learn more about End-to-end encryption here:
https://brainly.com/question/17017885
#SPJ11
Related Questions
Joe, a user, wants his desktop RAID configured to allow the fastest speed and the most storage capacity. His desktop has three hard drives. Which of the following RAID types should a technician configure to achieve this?
A. 0
B. 1
C. 5
D. 10
Answers
For Joe, the technician has to set up RAID 0. By dividing data into many copies, RAID 0, also known as the striped volume or stripe set, is set up to provide the highest performance and greatest storage space.
How does a RAID function?
Data is duplicated across two drives in the array using RAID 1 (mirrored disks), which offers complete redundancy. The identical data is always stored on both drives at the same time. As long as one disk remains, no data is lost.
Why could someone utilize RAID?
Redundant Array of Independent Disks, or RAID, is a technology that combines many hard disks to increase performance. RAID configuration might affect how quickly your computer operates.
To know more about RAID visit:
https://brainly.com/question/14669307
#SPJ4
What is the benefit of using MS Excel over the manual logbook?
Answers
Answer:
The advantages of Excel are wide and varied; here are the main advantages: Easy and effective comparisons: With the powerful analytical tools included within Microsoft Excel, you have the ability to analyze large amounts of data to discover trends and patterns that will influence decisions.
i am sorry if i give wrong ans i am only 13 years old and read at 7
how might b2b and b2c companies approach meeting customer needs differently
Answers
Businesses that cater to both B2B (business-to-business) and B2C (business-to-consumer) consumers frequently take a different approach to satisfying their demands because these customers have distinct needs.
What distinguishes B2B customers from B2C clients?What distinguishes B2B e-commerce from B2C e-commerce? Business to business is known as B2B, whereas business to consumer is known as B2C. B2B ecommerce makes use of online channels to market to other businesses. B2C e-commerce focuses on individual customers.
How do the purchasing processes for B2B and B2C differ?B2B: When purchasing a good or service involves business-related goals, the transaction requires a careful study, more thought, and continued support from the seller. Several business divisions are impacted by the choice. B2C: Typically, the sale is less logical
To know more about consumers visit:-
https://brainly.com/question/28671114
#SPJ1
Which function is used to remove all items from a particular dictionary?
i) len() ii) get() iii) keys() iv) None of
Answers
Answer:
The right answer is: Option 4: None of these.
Explanation:
A data structure in python is knows as a dictionary. It works like an array. Different functions can be used to perform different operations on the dictionary.
In the given options,
Option 1: len() function is used to return length of dictionary.
Option2: get() function is used with a key as argument to return the value present on the specific key
Option 3: keys() function is used to display all the keys of a dictionary in the form of a list
Hence,
The right answer is: Option 4: None of these.
Select the online reading comprehension tool that best fits the description. This tool lets users change text from one language to another. This tool helps users find definitions for difficult vocabulary. This tool allows users to listen to passages of text that they select. This tool helps users memorize vocabulary by giving them representations of words using pictures.
Answers
Answer:
This tool lets users change text from one language to another.
translation tool
This tool helps users find definitions for difficult vocabulary.
online dictionary
This tool allows users to listen to passages of text that they select.
text-to-speech tool
This tool helps users memorize vocabulary by giving them representations of words using pictures.
flash cards
Explanation:
just did the assignment on edg 2020
Answer:
Select the online reading comprehension tool that best fits the description.
This tool lets users change text from one language to another.
✔ translation tool
This tool helps users find definitions for difficult vocabulary.
✔ online dictionary
This tool allows users to listen to passages of text that they select.
✔ text-to-speech tool
This tool helps users memorize vocabulary by giving them representations of words using pictures.
✔ flash cards
Explanation:
Which type of database program is Microsoft Access 2016?
O knowledge
O local data
O relational
O flat-file
Answers
Answer:
O relational
Explanation:
If I'm wrong I'm so so sorry! But form my research it keeps saying its relational.
If I'm right please give me brainliest I really need it to level up so please help me!
If you don't know how to give brainliest there should be a crown underneath my answer you just have to click it.
Thank you and have a wonderful night,morning,afternoon/day! :D
Answer:
Which type of database program is Microsoft Access 2016?
relational
Explanation:
Which best describes how an operating system works with the BIOS? It instructs the BIOS to complete a task. It allows user interaction with the BIOS. It translates instructions for the BIOS. It provides power to the BIOS.\
Answers
Answer:It translates instructions for the BIOS.
Explanation:just took the test :)
Answer:
C. It translates instructions for the BIOS.
Explanation:
edge 2020
What are some positive ways to build your online reputation? (Choose all that apply)
Build a brand for yourself.
Constantly promote a product you're selling.
Avoid revealing personal fights and problems.
Pay for views and likes on your content.
Answers
Answer:my best answer is to be nice and use manners
Explanation:
chhincvjucnvbeojnvjbbnjovnvbbnvjbcnojnv definitly dont do that
Caroline is collaborating with several writers who are creating multiple documents. There is a single list of content that must be eventually covered by all the documents, and Caroline needs a way to “flag” which writer is covering which content; all writers will be looking at the exact same online version of the list. Describe how Caroline could quickly use colors in Word to show which content goes with which writer; be specific about which Word tool she should use and how that tool operates.
Answers
A Word document can be shared with multiple users by selecting the File menu at the top ribbon and then select Share from the drop down menu
Several writers can work together on Microsoft Word by using the co-authoring, sharing, and co-editing features in MS Word
In order to co-author the content list, Caroline, should
1. Create the content list document
2. Click on Share icon on the top right corner of the document
3. Ensure to save the document in OneDrive
4. Input the email addresses of the other writers who are working on the list
5. Enter a message to the writers to add the title of the content they are working on in the list
When the other writers open the link to the document sent to them in the email they receive, and they open the document in a web browser, by selecting Edit Document > Edit in Browser
The presence of a writer and their real time changes to the content list document, showing the content they are working on are shown by colored flags that has the author (writer) name next to the content they are working on
Learn more about collaboration in Word here:
https://brainly.com/question/1877453
Absolute cell adressing
Answers
When copying a formula from one cell to another in Excel, an absolute reference is a cell reference where the column and row coordinates remain constant.
What is excel?Users of Microsoft Excel may format, arrange, and compute data in a spreadsheet.
Data analysts and other users can make information easier to view as data is added or changed by organising data using software like Excel.
Cell references come in two flavours: absolute and relative. When copied and filled into other cells, relative and absolute references behave in different ways.
A formula's relative references are altered when it is copied to another cell. Contrarily, regardless of where they are duplicated, absolute references hold true.
When a specific cell reference needs to be constant, an absolute cell reference can be used. Formulas, charts, functions, and other instructions frequently use references to cells in their syntax.
Thus, this can be concluded regarding absolute cell addressing.
For more details regarding absolute cell addressing, visit:
https://brainly.com/question/30443246
#SPJ1
HELP ME PLZ
A computer system has 16 GB of RAM and 8 MB of cache which is faster than
RAM
Explain why the computer system does not have 16 GB of cache.
Answers
Answer:
inorder to be close to the processor..the cache memory should be much smaller than the main memory...to increase processing speed.
difference between data bus and address bus and control bus
Answers
Answer: The address bus carries the information about the device with which the CPU is communicating and the data bus carries the actual data being processed, the control bus carries commands from the CPU and returns status signals from the devices.
can someone help me with this trace table - its computer science

Answers
TThe while loop keeps going until count is greater than or equal to 10.
count = 0, sum = 0
count = 2, sum =2
count = 4, sum = 6
count = 6, sum = 12
count = 8, sum = 20
count = 10, sum = 30
Now that count is equal to 10, it exits the while loop and the program ends. The values above complete your trace table.
ou want to configure the NTP daemon to receive time from pool.ntp.org. What entry should you place in the /etc/ntp.conf file?
Answers
Answer:
server pool.ntp.org
Explanation:
Select the two code fragments that are logically equivalent. if is_on_fire) : pass if door_is_open(): pass else: pass if is_on_fire(): pass elif door_is_open(): pass else: pass if is_on_fire): pass else: if door_is_open(): pass else: pass if is_on_fire(): pass else if door_is_open(): pass else: pass
Answers
Thus, Both of these code fragments check if `is_on_fire()` is true, and if so, they pass. If not, they then check if `door_is_open()` is true, and pass if it is. If neither condition is met, they pass as well are correct.
Based on your provided code fragments, the two logically equivalent code snippets are:
1.
```python
if is_on_fire():
pass
elif door_is_open():
pass
else:
pass
```
2.
```python
if is_on_fire():
pass
else:
if door_is_open():
pass
else:
pass
```
Both of these code fragments check if `is_on_fire()` is true, and if so, they pass. If not, they then check if `door_is_open()` is true, and pass if it is. If neither condition is met, they pass as well.
The difference between them is that the first one uses the `elif` keyword to combine the second condition and the `else` clause, while the second one uses a nested `if` statement within the `else` clause. However, they achieve the same logical outcome.
Know more about the logically equivalent code
https://brainly.com/question/13259334
#SPJ11
Have any of you guys had to deal with not seeing profile pictures or not being able to open PDFs on this website? Is it just me or an overall glitch of the Brainly system?
Answers
What are some ways to assess the credibility and accuracy of
an internet source?
A. Determine it’s purpose
B. Check the domain suffix
C. Make sure the author is credible
D. Make sure the site is up to date
Answers
Answer:
B, C, and D
Explanation:
All are ways to assess the credibility and accuracy.
The _____ contains lists of commands used to create presentations.
Outline view
Menu bar
Slide pane
Title bar
Answers
Answer:
The menu bar is correct
Explanation:
EDG2021
What is the keyboard shortcut to show formulas in a worksheet (as opposed to the value)? OCTRL+S OCTRL + Z CTRL- There is no shortcut for showing formulas
Answers
CTRL + (tilde) is a keyboard shortcut to show formulas instead of values in Excel spreadsheets. It can be found in the upper-left corner of most keyboards, below the Escape key or just left of the 1 key.
The keyboard shortcut to show formulas in a worksheet (as opposed to the value) is `CTRL + ~` (tilde).When working with Excel spreadsheets, you might want to display the formulas instead of the values in your cells. This could be done by using the "Show Formulas" button. But, if you're doing this frequently, it's easier to use a keyboard shortcut. To do this, press `CTRL + ~` (tilde) and it will show all of the formulas in your spreadsheet instead of the values.
The tilde symbol, ~, can be found in the upper-left corner of most keyboards. It is usually located below the Escape key or just left of the 1 key. It's worth noting that pressing the `CTRL + ~` (tilde) keyboard shortcut again will switch back to displaying the values.
To know more about Excel spreadsheets Visit:
https://brainly.com/question/10541795
#SPJ11
Under which accounting method are most income statement accounts translated at the average exchange rate for the period ?
A) current/concurrent method
B) monetary/nonmonetary methode
C)temporal method
D)All of the options
Answers
Under the accounting method where most income statement accounts are translated at the average exchange rate for the period, the correct option is D) All of the options.
The current/concurrent method considers both monetary and nonmonetary balance sheet items and translates income statement accounts at the average exchange rate for the period. This method takes into account the fluctuations in exchange rates throughout the period and provides a more accurate representation of the financial results in the reporting currency.
By using the average exchange rate, the impact of exchange rate fluctuations on income statement accounts is spread out over the period, reducing the impact of currency volatility on reported earnings.
Learn more about accounting method here: brainly.com/question/30512760
#SPJ11
Fiona wants to fix scratches and creases in an old photograph. Fiona should _____.
Answers
Answer:
Fiona should scan the photograph and use image-editing software to fix the image.
Explanation:
Answer:
Fiona should scan the photograph and use image-editing software to fix the image.
Explanation:
calculate how many 32-bit registers can be placed between 0xf10100 and 0xf10200 psychical address range if the address unit is 8 bits.
Answers
Given the physical address range and considering that the address unit is 8 bits, it can be calculated that 64 32-bit registers can be placed between the addresses 0xf10100 and 0xf10200.
First, note that the addresses given are in hexadecimal. The difference between 0xf10200 and 0xf10100 is 0x100, or 256 in decimal. Given that the address unit is 8 bits, each addressable unit corresponds to a byte. A 32-bit register comprises 4 bytes (since 1 byte = 8 bits). So, you divide the total number of addressable units (256 bytes) by the size of the register (4 bytes) to find the number of 32-bit registers that can be placed in that range. Doing the calculation, 256/4 equals 64, so you can fit 64 32-bit registers in the given physical address range.
Learn more about memory address calculation here:
https://brainly.com/question/32612621
#SPJ11
Drag each tile to the correct box.
Match the certification to its issuing agency.
Network+
CCENT
MCSA
CompTIA
Cisco
Microsoft
Answers
The match can be network+ - CompTIA, CCENT - Cisco, and MCSA - Microsoft.
A top provider of IT certifications, CompTIA, grants the Network+ credential. It supports the fundamental expertise and abilities needed for networking professionals.
Cisco Systems offers the CCENT (Cisco Certified Entry Networking Technician) certification. It acts as a springboard for anyone wishing to launch careers in networking. The core networking principles covered by CCENT include network architecture, routing, switching, and simple troubleshooting.
Microsoft offers the MCSA (Microsoft Certified Solutions Associate) credential. It certifies the technical abilities required to run and manage Microsoft technologies like Windows Server, SQL Server, and Azure.
Thus, this can be the match for the given scenario.
For more details regarding server, visit:
https://brainly.com/question/29888289
#SPJ1
Based on your prior knowledge, match each civilization to the region it occupied.

Answers
Answer: Inca- South America
Aztec - Meso America
Explanation:
Answer:Ladies and gents and all the nonbinary people out there, darlings the anwser is
Mesoamerica: Aztec
South America: Inca
Explanation:I just did it and got it right!
i'm sure u guys don't actually want an explanationLMFAOOO
Jorge says, “My smart phone is acting as a client when it checks e-mail over the Internet because it connects to a server, but it acts as a server when I'm making calls." Is Jorge correct, and if not, why not? Choose the best answer.
Jorge is correct about his smartphone acting as a client when it checks mail but incorrect about it acting as a server when calls are made.
Jorge is correct.
Jorge’s smartphone is always a client, even when it is off.
He is not correct because Jorge’s smartphone acts as a server when it checks e-mail.
Answers
Since Jorge says, “My smart phone is acting as a client when it checks e-mail over the Internet because it connects to a server, but it acts as a server when I'm making calls." Is option D: that Jorge is correct.
What exactly does "smart phone" mean?A smartphone is a portable electronic gadget that connects to the internet and cellular networks. Simon, the first smartphone ever made, was said to have been developed by IBM in 1994.
Note that the smartphone is a cell phone that offers more functionality than just making and receiving calls as well as texts.
Therefore, Since Jorge says, “My smart phone is acting as a client when it checks e-mail over the Internet because it connects to a server, but it acts as a server when I'm making calls." Is option D: that Jorge is correct.
Learn more about smart phone from
https://brainly.com/question/28372521
#SPJ1
Jorge says, “My smart phone is acting as a client when it checks e-mail over the Internet because it connects to a server, but it acts as a server when I'm making calls." Is Jorge correct, and if not, why not? Choose the best answer.
He is not correct because Jorge’s smart phone acts as a server when it checks e-mail.
He is not correct because Jorge’s smart phone acts as a server when it checks e-mail.
Jorge’s smart phone is always a client, even when it is off.
Jorge’s smart phone is always a client, even when it is off.
Jorge is correct about his smart phone acting as a client when it checks mail but incorrect about it acting as a server when calls are made.
Jorge is correct about his smart phone acting as a client when it checks mail but incorrect about it acting as a server when calls are made.
Jorge is correct.
what are the first steps that you should take if you are unable to get onto the internet
Answers
If you are unable to get onto the internet, the first steps to take are: Check the connection: Ensure that your device is properly connected to the internet, either via Wi-Fi or a physical cable connection.
What are the other steps to take?The other steps to take are:
Restart your router - Try restarting your router or modem, as this can sometimes resolve connectivity issues.Disable and re-enable the network connection - Disable and re-enable the network connection on your device to see if this fixes the issue.Check the network settings - Ensure that your network settings are properly configured, including the network name, password, and IP address.Try a different device - Try accessing the internet using a different device to see if the issue is device-specific or network-related.Contact your service provider - If none of these steps work, contact your internet service provider for further assistance. They can diagnose the problem and provide you with the necessary support to get back online.Learn more about internet:
https://brainly.com/question/13570601
#SPJ1
a wired technology used to transmit data over telephone lines at 1.544 mbps is called?
Answers
Answer: A T1 line
Explanation:
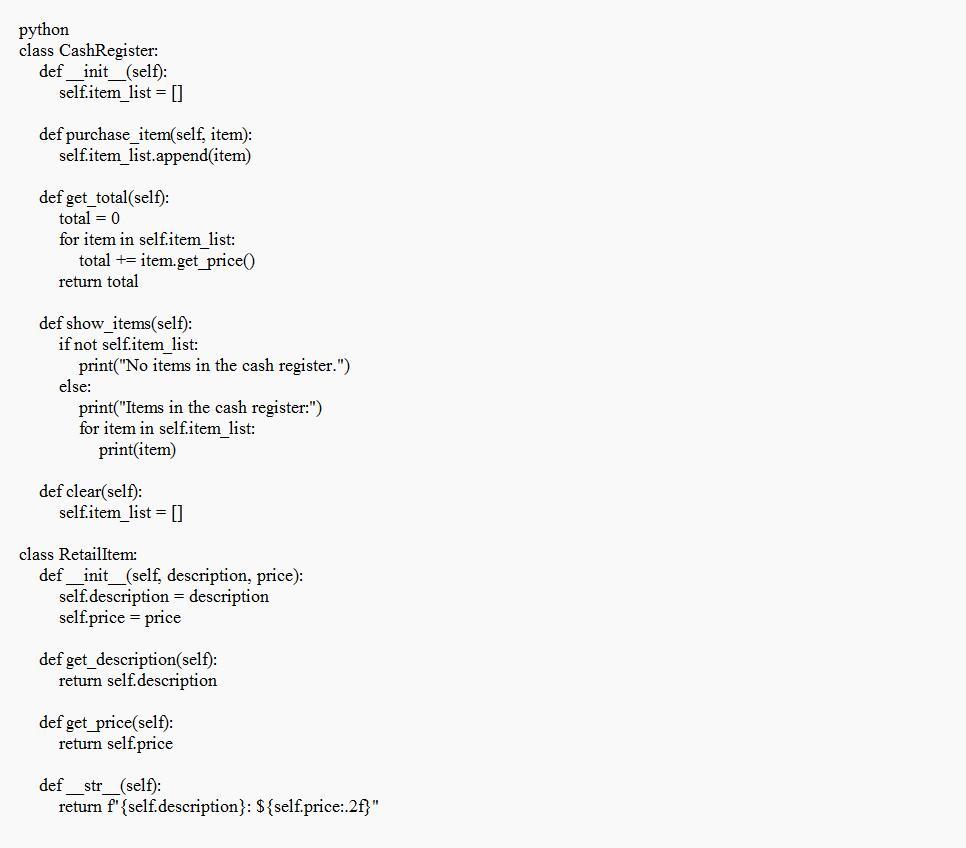
100 POINTS!!!! Write in python
10.8

Answers
A good example of the implementation of the Cash Register class that is known to have all the methods given in the question is attached below.
What is the Cash Register class?Based on the given program, It initiates three RetailItem instances that signify distinctive products that are available for procurement. The CashRegister object is updated with additional items through the purchase_item function.
The CashRegister's stored items can be viewed through the show_items method, while the get_total method computes and gives back the overall cost. Eventually, the internal list of items within the CashRegister is cleared utilizing the transparent approach.
Learn more about Cash Register class from
https://brainly.com/question/31655783
#SPJ1
See text below
8.
This exercise assumes you have created the RetailItem class for Programming Exer- cise 5. Create a Cash Register class that can be used with the RetailItem class. The Cash Register class should be able to internally keep a list of RetailItem objects. The class should have the following methods:
. A method named purchase_item that accepts a RetailItem object as an argument. Each time the purchase_item method is called, the RetailItem object that is passed as an argument should be added to the list.
. A method named get_total that returns the total price of all the RetailItem objects stored in the Cash Register object's internal list.
⚫ A method named show_items that displays data about the RetailItem objects stored in the Cash Register object's internal list.
⚫ A method named clear that should clear the CashRegister object's internal list.
Demonstrate the Cash Register class in a program that allows the user to select several items for purchase. When the user is ready to check out, the program should display a list of all the items he or she has selected for purchase, as well as the total price.

were broken by us cryptanalysis and german encryption methods used in europe were deciphered by british intelligence. in both cases, these successful cryptanalytic attacks relied in part on a common method known as
Answers
During world war ii japanese encryption methods at midway island were broken by us cryptanalysis and german encryption methods used in europe were deciphered by british intelligence. in both cases, these successful cryptanalytic attacks relied in part on a common method known as frequency analysis.
Frequency analysis involves examining the frequency of letters, pairs of letters, or other patterns within encrypted messages to deduce the underlying plaintext. This technique is based on the premise that certain letters or patterns occur more frequently in a given language, allowing cryptanalysts to make educated guesses about the message's content. By comparing the observed frequencies to those expected in the language, analysts can potentially uncover the encryption scheme and decode the message.
The successful application of frequency analysis in both the Japanese and German cases greatly impacted the course of World War II. Breaking the Japanese encryption at Midway Island enabled the US to anticipate and counter enemy plans, leading to a decisive naval victory. Similarly, British intelligence's deciphering of German encryption, notably the Enigma machine, provided invaluable information for the Allies, ultimately contributing to the defeat of Nazi Germany.
In summary, frequency analysis was a vital method employed by both US and British intelligence in deciphering enemy encryption during World War II. This technique allowed for crucial breakthroughs, significantly shaping the war's outcome in favor of the Allies.
The Question was Incomplete, Find the full content below :
During world war ii japanese encryption methods at midway island were broken by us cryptanalysis and german encryption methods used in europe were deciphered by british intelligence. in both cases, these successful cryptanalytic attacks relied in part on a common method known as ____________
Know more about Frequency analysis here :
https://brainly.com/question/14957579
#SPJ11
Which transmission media is faster? Fibre Optic or Radio-waves? I want full explanation!
Answers
Answer:
Due to the direct line of sight,the data rate of radio links is higher than that of fiber optic connections. A radio link has a lower latency (less delay).In contrast ,fiber optic connections may achieve higher bandwidths