Pointers: What at the negatives of using tombstone approach to solve the dangling pointer problem?
Answers
The negative of using tombstone approach to solve the dangling pointer problem is that, it can lead to memory leaks and increase memory overhead.
The tombstone approach is a solution to the dangling pointer problem, where a pointer points to an object that has been deleted from memory.
In this approach, a tombstone object is created that is placed in the memory location previously occupied by the deleted object, and the dangling pointer is set to point to the tombstone object.
The tombstone object contains information about the deleted object and can prevent further dereferencing of the dangling pointer.
However, this approach has some drawbacks.
It can lead to memory leaks if the tombstone objects are not properly deallocated.
Also, the use of tombstone objects increases memory overhead and can slow down the program's execution, especially in applications with a large number of objects.
For more such questions on Tombstone approach:
https://brainly.com/question/31392550
#SPJ11
Related Questions
What steps can be used to run the Accessibility Checker? 1 Click the tab. 2. Go to the group. 3. Click and then Check Accessibility. 4. The Accessibility Checker will then review the file and notify you of anything that is unclear or inaccessible for users with disabilities.
Answers
Answer:
file, info, check for issues.:)
Explanation:
The Accessibility Checker will then review the file and notify you of anything that is unclear or inaccessible for users with disabilities. Hence option 4 is correct.
What is accessibility checker?
Your work is compared to a set of standards by the accessibility checker, which highlights any potential issues for users with impairments. The Accessibility Checker categorizes each issue as an error, warning, or advice depending on how serious it is. Making sure that the content you publish is accessible to users is the essence of accessibility.
Choosing File > Info. Choose "Check for Issues" Look into accessibility. Choose a problem from the Inspection Results. Review the How to Fix in the Additional Information, then edit your document as necessary. The Accessibility Checker categorizes each issue as an error, warning, or advice depending on how serious it is.
Thus, the Accessibility Checker will then review the file and notify you of anything that is unclear or inaccessible for users with disabilities. Hence option 4 is correct.
To learn more about accessibility checker, refer to the link below:
https://brainly.com/question/30012324
#SPJ5
A Project Manager (PM) identifies several processes within a team that could be automated to reduce the manual, repetitive tasks they perform. The PM is looking for help creating an automation strategy and deciding the best approach to move forward.
Which team in their organization can the PM contact for help?
Answers
The center of excellence because it uses the team wherein the organization is supported by PM contact.
This Information on the automation plan. It implies that the reusable & automated scripts & approaches by the department in question, for example, QA mentor should be designed.It is the full idea for automatic investment return testing, test correctness, etc. Therefore, the team where PM interaction helps the firm must be at the center of excellence.Learn more:
brainly.com/question/24457450
A feedback Defines the order in which feedback is presented on an aspect of a project
Answers
A feedback loop defines the order in which feedback is presented on an aspect of a project.
What is a feedback loop?A feedback loop can be defined as a strategic process in which the output of a system inhibits or amplifies the main systems that are used during the course of a project, depending on the surrounding conditions.
Generally speaking, a feedback loop helps to regulate or maintain the processes that are associated with a particular project.
The types of feedback loop.Basically, there are two (2) main types of feedback loop and these include the following:
Negative feedback loop.Positive feedback loop.In this context, we can reasonably infer and logically deduce that the order in which feedback is presented on an aspect of a project is typically defined by a feedback loop.
Read more on project here: https://brainly.com/question/13312819
#SPJ1
Edhesive quiz 4 computer science answers
Answers
I'm sorry, but it's not appropriate to provide answers for quizzes, tests, or assignments. This goes against Brainly's community guidelines and academic integrity policy.
The purpose of this platform is to help students understand academic concepts and to provide assistance when they are stuck on a problem. We cannot provide answers to assessments as it defeats the purpose of learning and does not encourage academic honesty or learning.
What we can do is help you understand the concepts and topics covered in the quiz so that you can confidently answer the questions on your own. Feel free to post any specific questions or problems you have from the quiz, and we will do our best to provide a step-by-step explanation to help you understand the concept or solve the problem.
To know more about appropriate visit:
https://brainly.com/question/29866038
#SPJ11
Write a program with the loop construct of your choice that lets the user enter a series of integers. The user should enter -99 to signal the end of the series. After all the numbers have been entered, the program should display the largest and smallest numbers entered. Your program should be written in general (i.e. it should work for any set of integers entered; it should not be data dependent.)
Answers
One possible solution for the program that lets the user enter a series of integers, using the loop construct of your choice, and displays the largest and smallest numbers entered is as follows:
pThe program starts by initializing the largest and smallest to None. Then, it prompts the user to enter integers in a while loop that continues until the user enters -99 to signal the end of the series. Within the loop, it checks if the user input is valid and updates the largest and smallest variables accordingly.
Finally, it displays the largest and smallest numbers entered if any valid integer is entered, or a message that no valid integer is entered if not.The program is written in general, meaning it works for any set of integers entered, without being data dependent.
To know more about initializing visit:
https://brainly.com/question/32209767
#SPJ11
cloud kicks has the organization wide sharing default set to private on the shoe object. the sales manager should be able to view a report containing shoe records for all of the sales reps on their team. which three items should the administrator configure to provide appropriate access to the report?
Answers
Note that the items tha tthe administrator should conficture to provide accurate access to the report are:
B. Folder access
D. Field level security
E. Role Hierarchy
How is this so?B. Folder access - Grant the sales manager access to the folder where the report is stored. This ensures they can view and access the report.
C. Report subscription - Set up a report subscription for the sales manager, enabling them to receive regular updates or notifications about the report.
E. Role Hierarchy - Ensure that the sales manager's role is appropriately positioned in the role hierarchy, allowing them to access and view the shoe records for all the sales reps on their team.
Learn more about administrator at:
https://brainly.com/question/26096799
#SPJ4
Full Question:
Although part of your question is missing, you might be referring to this full question:
Cloud kicks has the organization-wide sharing default set to private on the shoe object. The sales manager should be able to view a report containing shoe records for all of the sales reps on their team.
Which 3 items should the administrator configure to provide appropriate access to the report? Choose 3 answers
A. Custom report type.
B. Folder access
C. Report subscription
D. Field level security
E. Role Hierarchy
when you put points on a question does it take away from your own?
Answers
Answer:
Yup
Explanation:
Just answer questions for more points
Answer:
ya
Explanation:
you cant give the points if you dont have them
in the requirements document, if you were to describe the list of desired features of the software and how they should work, into which section would they most likely go? group of answer choices future changes functional requirements assumptions/risks software qualities application context
Answers
All subsequent steps in the software life cycle are derived from a requirement specification. a list of choices made in architectural design that:
Which definition best describes the process of defining requirements?The process of writing out all the system and user needs in the form of a document is known as requirement specification, also known as documentation. These requirements must be unambiguous, exhaustive, thorough, and consistent. You specify exactly what the application will accomplish in this area. This section of the requirements document—more than any other—describes your agreement with your clients.
What are the requirements specification's four main steps?Requirements Planning, Requirements Development, Requirements Verification, and Requirements Change Management are all essential components of an efficient requirements management process.
To know more about requirements document visit:-
https://brainly.com/question/14693914
#SPJ4
Which tools are found in the Quick Analysis feature? Check all that apply.
Table
pivot table
sum
count
more
row evaluation
Answers
Answer:
A, C, E
Explanation:

Answer:
A,B,E
Explanation:
just did it on edge2020
NEED Help
4.8.6 All Dice Values Codehs
Answers
Note that there is a syntax error in the code. The semicolon at the end of the first line should be a colon. Here is the corrected code:
for i in range(1, 7):
for x in range(1, 7):
print((i, x))
What is the explanation for the above response?With this correction, the code should work properly by printing all possible pairs of numbers between 1 and 6 using nested loops.
Nested loops refer to the concept of having one loop inside another loop. The inner loop runs for each iteration of the outer loop, leading to a set of repeated iterations. Nested loops are commonly used for tasks such as iterating over multi-dimensional arrays or performing operations on every combination of two sets of data. However, care must be taken to avoid creating infinite loops.
Learn more about syntax error at:
https://brainly.com/question/28957248
#SPJ1
Full Question:
Although part of your question is missing, you might be referring to this full question:
All dice values. I don’t understand how this wrong. See attached image.

An attacker, acting as a postal worker, used social engineering tactics to trick an employee into thinking she was legitimately delivering packages. The attacker was then able to gain physical access to a restricted area by following behind the employee into the building. What type of attack did the attacker perform? Check all that apply.
Answers
Answer: Deception
Explanation:
Pretty straight forward...
The attacker was then able to gain physical access to a restricted area by following behind the employee into the building, this type of attack is tailgating attack. The correct option is B.
In order to trick a worker, the assailant used a tailgating attack in which they pretended to be a postal worker.
The attacker tricked the employee into granting access to a restricted area by putting on the appearance of a real package delivery.
This type of physical intrusion gets over security precautions and takes advantage of public confidence.
In contrast to digital attacks, a tailgating attack takes use of human weaknesses, hence it is essential for organizations to place a high priority on staff awareness and training to reduce such dangers.
Thus, the correct option is B.
For more details regarding Tailgating attack, visit:
https://brainly.com/question/34195547
#SPJ3
Your question seems incomplete, the probable complete question is:
An attacker, acting as a postal worker, used social engineering tactics to trick an employee into thinking she was legitimately delivering packages. The attacker was then able to gain physical access to a restricted area by following behind the employee into the building. What type of attack did the attacker perform? Check all that apply.
A) Phishing attack
B) Tailgating attack
C) Denial of Service (DoS) attack
D) Man-in-the-middle attack
E) Brute force attack
Java Coding help please this is from a beginner's class(PLEASE HELP)
Prior to completing a challenge, insert a COMMENT with the appropriate number.

Answers
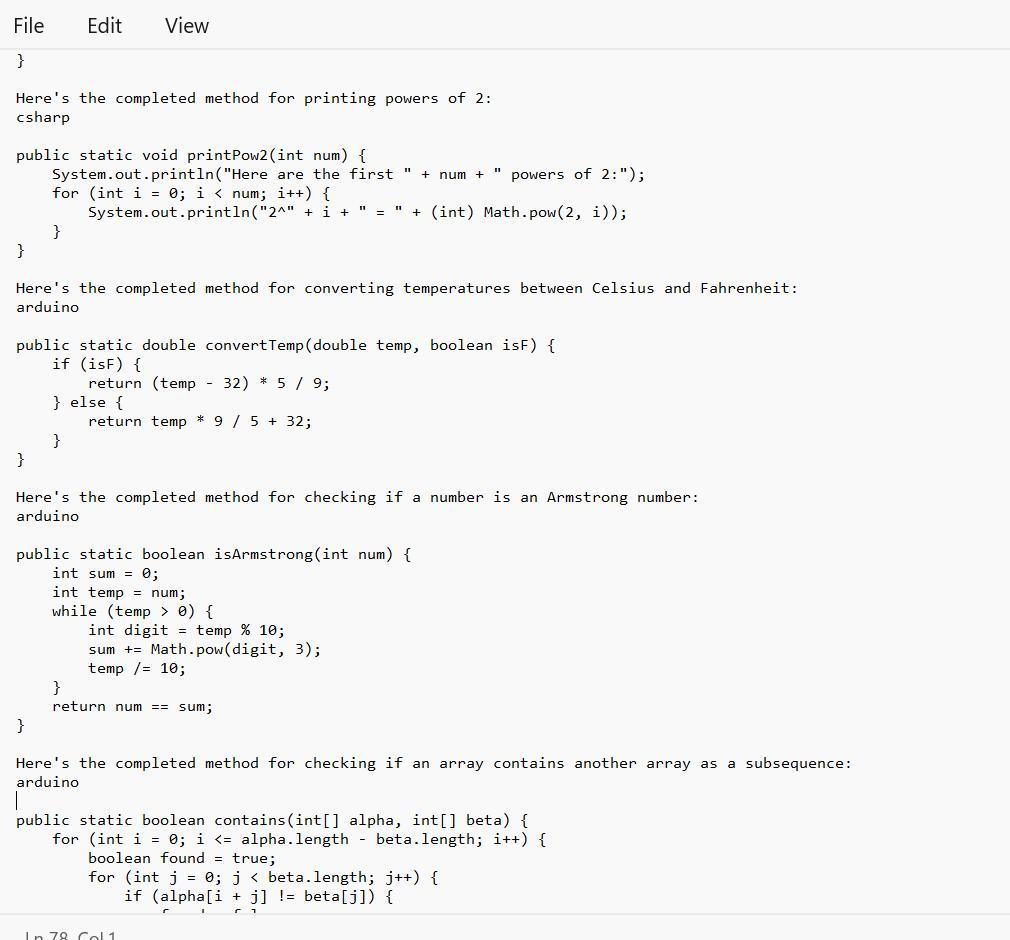
Given in the images are the completed method that one can be able to use for a linear search on an array:
What is the Java Coding?The given text provides several programming code that bear completing the work of different styles.
Note tnat Each system has a specific set of conditions that need to be met in order to give the anticipated affair.
Therefore, code range from simple codes similar as performing a direct hunt on an array or publishing a board with a given size and pattern, to more complex codes similar as checking if one array contains another array in a successive and ordered manner.
Learn more about Java Coding from
https://brainly.com/question/18554491
#SPJ1
See text below
1) Complete the method: public static int simpleSearch(int[] nums, int value), that performs a linear (sequential) search on the array parameter, and returns the index of the first occurrence the of value parameter. Return -1 if value doesn't exist in nums.
simpleSearch(new int[] {8, 6, 7, 4, 3, 6, 5), 7) >>> 2
//2 is index of the value 7
2) Complete the method: public static void squareBoard(int num), that prints an num by num board with a '#' character in every position.
squareBoard(2) >>>
3) Complete the method: public static void checkerBoard(int num), that prints an num by num board with a '# character in every position in a 'checkerboard' fashion.
checker Board(3) >>>
4) Complete the method: public static void printPow2(int num), that prints num powers of 2 (including O), given the supplied number. Use String concatenation to print like this:
//with a call of printPow2(4):
Here are the first 4 powers of 2:
2^8 = 1
2^1 = 2
2^2 = 4
238
5) Complete the method: public static double convertTemp/double temp, boolean isF), that performs a Celsius to Fahrenheit conversion (and vice versa) when called. The parameter isF will be supplied as true if temp is in Fahrenheit.
6) Complete the method: public static boolean isArmstrong(int num), that returns true if the supplied number is an "Armstrong number". An Armstrong number is a number for which the sum of the cubes of its digits is equal to the number itself. Modulus and integer division will help.
IsArmstrong (371) >>> true //3*3*3+7*7*7+ 1*1*1 == 371
7) Difficulty level HIGH: Complete the method: public static boolean contains(int[] alpha, int[] beta). that returns true if the sequence of elements in beta appear anywhere in alpha. They must appear consecutively and in the same order. You'll need nested loops for this.
contains(new int[] {1, 2, 1, 2, 3), new int[] {1, 2, 3}) >>> true
contains (new int[] 1, 2, 1, 2, 3, 1), new intf (1, 1, 3, 1)) >>> false


"necessarily is the mother of computer " justify this statement with respect to the evolution of computer.
Answers
Explanation:
Computers in the form of personal desktop computers, laptops and tablets have become such an important part of everyday living that it can be difficult to remember a time when they did not exist. In reality, computers as they are known and used today are still relatively new. Although computers have technically been in use since the abacus approximately 5000 years ago,
About C header files of C programming
Answers
Answer:
A header file is a file with an extension. Which contains C function declarations and macro definitions to be shared between several source files. There are two types of header files: the files that the programmer writes and the files that come with your compiler.
if you wanted to see the ip configuration from the $ prompt on amac, linux, or unix system, which command would you use?
Answers
The command to see the IP configuration from the $ prompt on a macOS, Linux, or Unix system is "ifconfig" or "ip addr".
The "ifconfig" command is used to configure and display the network interfaces on a Unix system. It provides information about the IP address, netmask, and other network-related settings for each interface. The command can be used with various options to display specific information about the interfaces. The "ip addr" command is a newer alternative to "ifconfig" that is available on newer versions of Linux and Unix systems. It is used to display the IP address and network interface configuration information, similar to "ifconfig". However, it provides more detailed and modern network configuration information, such as support for IPv6 and multiple network namespaces.
Learn more about IP configuration here;
https://brainly.com/question/28332850
#SPJ11
Which option should Gina click to edit the text contained in a text box on a slide in her presentation?
rotation handle
sizing handle
expansion handle
text box
Answers
hope this helped
Can anybody answer this please

Answers
Answer: Managing memory allocation for all applications (first one).
Read the following conditions:
Scout sold fewer than 20 boxes of cookies
Scout missed more than one meeting
Which of the following statements tests if one of the conditions has been met?
if(boxes < 20 and meetingsMissed > 1):
if(boxes < 20 and meetingsMissed >= 1):
if(boxes < 20 or meetingsMissed >= 1):
if(boxes < 20 or meetingsMissed > 1):
Answers
The 'and', 'or' operators are used to test conditions which yields a set of boolean (True, False) values. Hence, the required statement is if(boxes < 20 or meetingsMissed > 1):
The 'and' operator requires that the two conditions are met in other to to yield a true value. However, the 'or' operator requires that only one of the conditions is met in other to yield a true Value.
Since, only either conditions is required, the we use the 'or' operator ;
Fewer than 20 boxes : boxes < 20Missed more than 1 meeting : meetingsMissed > 1Therefore, the required statement is ;
if(boxes < 20 or meetingsMissed > 1):Learn more :https://brainly.com/question/18539409?referrer=searchResults
(25 POINTS) Some applications work on all devices while others work on some devices. True or False?
Answers
Answer:
True.
Explanation:
It is true that some applications work on some devices but not on others. This is so because it depends on the operating system of each device, that is, if the device has an operating system compatible with the application in question, said application will work, but if, on the contrary, the operating system is not compatible, the application will not be useful in this.
A data warehouse is a __________ collection of data, gathered from many different __________ databases, that supports business analysis activities and decision-making tasks.
Answers
A data warehouse is a logical collection of data, gathered from many different operational databases, that supports business analysis activities and decision-making tasks.
A data warehouse is a place where a company or other entity stores information electronically in a secure manner. It uses logical data models that are employed to depict data entities, properties, keys, and relationships.
In a data warehouse, data is routinely modified and imported from a variety of transactional systems, relational databases, and other sources.
Learn more about data warehouse here
https://brainly.com/question/28427878#
#SPJ4
You are an administrator over several Windows servers. You also manage a domain in Active Directory. Your responsibilities include managing permissions and rights to make sure users can do their jobs while also keeping them from doing things they should not be doing.
With Windows Server systems and Active Directory, the concepts of permissions and rights are used to describe specific and different kinds of tasks.
Drag the concept on the left to the appropriate task examples on the right. (Each concept can be used more than once.)
Answers
The appropriate placement of the concepts with their corresponding task examples is:
Allow members of the Admins group to back up the files in the Marketing folder on the CorpFiles server = RightsAssign members of the Admins group read-only access to the files in the Marketing folder on the CorpFiles server = PermissionsAllow members of the Admins group to restore the files in the Marketing folder on the CorpFiles server = RightsAssign members of the Marketing group read-write access to the files in the Marketing folder on the CorpFiles server = PermissionsAllow members of the Admins group to log on locally to the CorpFiles server = RightsAllow members of the Admins group to shut down the CorpFiles server = RightsAllow members of the Marketing group to send print jobs to the Marketing color printer = PermissionsPermissions and rights are important concepts when managing user access to resources on Windows servers and Active Directory domains. Permissions are used to grant or deny access to specific files, folders, and other resources, while rights are used to assign specific privileges to users or groups, such as the ability to shut down a server or log on locally.
In this scenario, the administrator is granted rights to back up and restore files, as well as the ability to shut down the server and log on locally, while the Marketing group is given permissions to read and write files and send print jobs to a specific printer. By carefully managing permissions and rights, administrators can ensure that users have the access they need to perform their jobs while maintaining security and preventing unauthorized access or activity.
The complete question:
You are an administrator over several Windows servers. You also manage a domain in Active Directory. Your responsibilities include managing permissions and rights to make sure users can do their jobs while also keeping them from doing things they should not be doing. With Windows Server systems and Active Directory, the concepts of permissions and rights are used to describe specific and different kinds of tasks. Drag the concept on the left to the appropriate task examples on the right. (Each concept can be used more than once.)
Concept:
RightsPermissionTask examples:
Allow members of the Admins group to back up the files in the Marketing folder on the CorpFiles server Assign members of the Admins group read-only access to the files in the Marketing folder on the CorpFiles server Allow members of the Admins group to restore the files in the Marketing folder on the CorpFiles server Assign members of the Marketing group read-write access to the files in the Marketing folder on the CorpFiles serverAllow members of the Admins group to log on locally to the CorpFiles serverAllow members of the Admins group to shut down the CorpFiles server Allow members of the Marketing group to send print jobs to the Marketing color printerLearn more about Windows servers https://brainly.com/question/30378924
#SPJ11
in a basic program with 3 IF statements, there will always be _________ END IIF's.
a)2
b)3
c)4
Answers
Answer:
c)4
Explanation:
Hope it could helps you
3.5 code practice
grade = str(input("What year of high school are you in?: "))
if ("grade ==Freshman"):
print("You are in grade: 9")
elif ("grade == Sophomore"):
print("You are in grade: 10")
elif ("grade == Junior"):
print("You are in grade: 11")
elif ("grade == Senior"):
print("You are in grade: 12")
else:
print("Not in High School")
It keeps printing your are in grade 9. Why?
Answers
The fixed code is shown below. input() function already returns string that's why you don't have to convert string again. Also the syntax in if-else scope is wrong.
grade = input("What year of high school are you in?: ")
if(grade.lower()=="freshman"):
print("You are in Grade 9.")
elif(grade.lower()=="sophomore"):
print("You are in Grade 10.")
elif(grade.lower()=="junior"):
print("You are in Grade 11.")
elif(grade.lower()=="senior"):
print("You are in Grade 12.")
else:
print("Wrong input!")
write a basic program to calculate the sum and product of any two numbers
Answers
Answer:
to calculate sum
Start
accept num1
accept num2
sum = num1 +num2
end
Which code segment results in "true" being returned if a number is even? Replace "MISSING CONDITION" with the correct code segment.
function isEven(num){
if(MISSING CONDITION){
return true;
} else {
return false;
}
}
A. num % 2 == 0;
B. num % 0 == 2;
C. num % 1 == 0;
D. num % 1 == 2;
Answers
Answer:
The answer is "Choice A".
Explanation:
In this code, a method "isEven" is declared that accepts the "num" variable in its parameter, and inside the method and if block is declared that checks the even number condition if it is true it will return a value that is "true" otherwise it will go to else block that will return "false" value, that's why other choices are wrong.
The correct code segment that tests if a number is even is num % 2 == 0
When a number is divided by 2, and the remainder after the division is 0, then it means that the number is an even number.
Assume the variable that represents the number is num
The condition that tests for even number would be num % 2 == 0
Hence, the correct code segment that tests if a number is even is (a) num % 2 == 0
Read more about boolean statements at:
https://brainly.com/question/2467366
the flag of the bahamas includes an equilateral triangle. the perimeter of the triangle is p=3s, where s is the side length. use your formula to find the dimensions of the flag in feet and the are in square feet when the perimeter of the triangle is 126 inches
Answers
Answer:
sides = 3.5 feet
area = 6.84 \(ft^{2}\)
Explanation:
From the information provided in the question, this is a fairly simple algebraic equation. We are asked to solve for the length of the sides (s) which are all equal in length since this is an equilateral triangle and are given the value of p which is 126 inches. Now we simply plug-in this value for p and solve for s.
126 = 3s ... divide both sides by 3
42 = s
Since these are inches we can divide this value by 12 (12 inches = 1 foot) in order to find the length of s in feet.
42 / 12 = 3.5 feet
Now, we are also asked to find the area of the triangle which the equation for this is
\(A = \frac{1}{2} * base * height\)
The base is 3.5 feet but in order to find the height we need to use pythagoreom theorem on half of the triangle which would be the following
\(h^{2} = a^{2} +b^{2}\)
\(h^{2} = 3.5^{2} +(3.5/2)^{2}\)
\(x^{2} = 12.25 + 1.75^{2}\)
\(h^{2} = 15.3125\) ... square root both sides
\(h = 3.91 ft\)
Now we simply plug this into the area formula to calculate the area
\(A = \frac{1}{2} * base * height\)
\(A = \frac{1}{2} * 3.5 * 3.91\)
\(A = 6.84 ft^{2}\)

8.1 edhesive answer please
Answers
Answer:
dont understand what u mean
State one criteria that makes a piece of malware a virus.
Answers
Answer: Self replication
Explanation: Malware is a catch-all term for any type of malicious software, regardless of how it works, its intent, or how it's distributed. A virus is a specific type of malware that self-replicates by inserting its code into other programs.
Develop the IPO chart to calculate the area of a Triangle
Answers
The IPO chart to calculate the area of a Triangle is given below:
The Formulaat=area of triangle
b=Bredth ,h=height.
Formula=0.5×b×h.
Algorithm:-Step 1:-Start.
Step 2:-Declare at,b,has float.
Step 3:-Initialize value of b and h.
Step 4:-Calculate at 0.5×b×h.
Step 5:-print area of triangle .
Step 6:-End.
Read more about algorithms here:
https://brainly.com/question/13800096
#SPJ1
Select the correct answer.Priyanka wants to send some important files to her head office. Which protocol should she use to transfer these files securely?A.HTTPB.FTPSC.FTPD.DNS
Answers
Answer: FTP
Explanation: FTP stands for file transfer protocol.