in a database table, a collection of related data fields which describe a single person or organization is called a _____. 1. bit 2. byte 3. file 4. record
Answers
In a database table, a collection of related data fields which describe a single person or organization is called a Record. Option 4
What is a database table?A table is a collection of linked data stored in a database in table format. It is made up of columns and rows. A table is a group of data components in relational and flat file databases that use a model of vertical columns and horizontal rows, with the cell being the unit where a row and column cross.
A database record is an object that may hold one or more values. Then, groups of records are saved in a table, which defines the data that each record can contain. There are several tables in a database, each with multiple records.
Learn more about database table:
https://brainly.com/question/22536427
#SPJ1
Related Questions
một số được gọi là thác đổ nếu phần tử biểu diễn thập phân của nó nhiều hơn một chữ số đồng thời theo chiều từ trái qua phải chữ số đứng trước lớn hơn chữ số đứng sau
dữ liệu vào tệp THACDO.INP gồm nhiều dòng,mỗi dòng chứa số nguyên N
kết quả ra tệp THACDO.OUT gồm nhiều dòng thông báo,mỗi dòng ghi "CO" nếu N là thác đổ và ngược lại thông báo "KHONG" nếu N không phải
Answers
this not a queston but a warning
if you see a tnyInk link DO NOT DOWNLOAD THE FILE IN IT they most likley contain malware and if you see that link in a comment report it please it will help. and also show this to your freinds or someone.
Answers
Simplify the Boolean expression (AB(C + BD) + AB]CD.
Answers
Explanation:
Simplify the Boolean expression (AB(C + BD) + AB]CD.
Explanation:
De Morgan’s Law: (AB)’=A’+B’
Distributive Law: A+BC=(A+B)(A+C)
Absorption Law: A(A+B)=A
Commutative Law: AB=BA
50 POINTS! PLEASE HELP!
________ is a VMware Network setting that does not put the virtual machine directly on the physical network of the computer.
Host Only
MAT
NAT
VNAT
Answers
Answer:
NAT
Explanation:
The Network Address Translation (NAT) is a Virtual Machine Software which allows organizations to make use of a single Internet Protocol by altering the private network addresses to a private one. It makes it possible to Map multiple network addresses to a public address thereby providing security. The NAT VMware allows a single device such as a router provide an information transfer interface between a private and public network. Hence, it does not use the physical network of the computer.
Answer:
NAT
Explanation:
I took the test :D Hope this helps!
Which windows tool shows currently running programs and can be used to end a process?.
Answers
Answer: Task manager
Explanation: It allows you to see applications, their processes and the resources they're using.
HELP!!!!!
Your colleague has made a suggested change to an important document you are both working on. You disagree with their suggested change. They will be reviewing the changes you make before the final version of the document is submitted to your boss. You both work remotely and are in radically different time zones. What is the best step to take next?
Answers
I need some help with a question! Thank ya'll for helping me!

Answers
Answer:
to create an industry standard for five main colors
Explanation:
your choice is correct. B and C are silly, distracting, incorrect answers. A is the only one that could also possibly be correct, but there is no real "universal definition of color", its more meant to reach an industry standard
write a method called max that accepts an array of integers as a parameter and returns the maximum value in the array. for example, if the array passed stores {12, 7, -1, 25, 3, 9}, your method should return 25. you may assume that the array contains at least one element. your method should not modify the elements of the array.
Answers
Method called max that accepts an array of integers as a parameter and returns the maximum value in the array:
public class max {
public static void main(String[] args) {
int[] myArray = {12, 7, -1, 25, 3, 9};
int max = myArray[0];
for (int i = 1; i < myArray.length; i++) {
if (myArray[i] > max) {
max = myArray[i];
}
}
System.out.println("The maximum value in the array is: " + max);
}
}
What is array?
A collection of items (values or variables) is referred to as an array in computer science. Each element is identifiable by at least one array index or key. An array is stored in a way that allows a mathematical formula to determine each element's position given its index tuple. A linear array, sometimes referred to as a one-dimensional array, is the most basic sort of data structure. Two-dimensional arrays are sometimes referred to as "matrices" since the theoretical concept of a matrix can be expressed as a two-dimensional grid. Although tuples instead of vectors it is the more mathematically accurate counterpart, the term "vector" is occasionally used in computers to reference to an array. In particular, lookup tables are frequently implemented as arrays, and the word "table" is occasionally used as a shorthand for array.
To learn more about array
https://brainly.com/question/28061186
#SPJ4
Suppose that in any given hour the traffic load generated by users on computers of a certain brand can be fast, medium or slow. Half of the computers that had a slow traffic load in the first hour, will have a slow traffic load in the second hour as well. Twenty five percent of the computers that had a slow traffic load in the first hour, will have a medium traffic load in the second hour. Twenty percent of the computers that had a medium traffic load in the first hour, will have a fast traffic load in the second hour, and also 20% of the computers that had a medium traffic load in the first hour, will have a slow traffic load in the second hour. Eighty percent of the computers that had a fast traffic load in the first hour, will have a fast traffic load in the second hour as well. Ten percent of the computers that had a fast traffic load in the first hour, will have a medium traffic load in the second hour. a) The number of states for this Markov chain is b) Find the state space S of this Markov chain. S={ c) The probability that the computers that had a fast traffic load in the first hour, will have a slow traffic load in the second hour is
Answers
a) Markov Chain StateA Markov chain state is a state that, at a certain moment in time, can be said to be in a Markov process. A Markov process is a stochastic model that is used to model systems where the next state of the system is solely dependent on the previous state of the system. Since the given situation has 3 possible states of fast, medium and slow, the number of states for this Markov chain is 3. Hence, the answer is 3.
b) State Space S of Markov ChainThe state space is the set of all possible states that can be visited in a Markov chain. In the given situation, the state space S of this Markov chain is S={F,M,S}. Therefore, the answer is S={F,M,S}.c) Probability requiredWe need to find the probability that the computers that had a fast traffic load in the first hour, will have a slow traffic load in the second hour. Given that 80 percent of the computers that had a fast traffic load in the first hour, will have a fast traffic load in the second hour as well and 20 percent of the computers that had a medium traffic load in the first hour, will have a slow traffic load in the second hour.
Therefore, the probability that the computers that had a fast traffic load in the first hour, will have a slow traffic load in the second hour is 0. Hence, the answer is 0.
Learn more about Markov chain here,
https://brainly.com/question/30465344
#SPJ11
New product ideas must fit into a company's mission statement and?
Answers
Answer:
Please give a better question :D
Explanation:
I don't understand your statement, below is a statement I wrote..?
_______
"The matching process of developing and maintaining a strategic fit between the organization's goals and capabilities and its changing marketing opportunities"
A _____ can be used to create and test prototypes, develop interfaces, and simulate factory layouts and assembly lines, without investing in physical equipment and layouts.
Answers
Answer:
The correct answer is "Cave automatic virtual environment ".
Explanation:
An interactive virtual setting composed of something like a VR chamber or space throughout the cube form wherein the projection displays represent the boundaries as well as flooring, is determined as Cave automatic virtual environment.This same client computer does have a Virtual reality headset as well as header projection but instead uses devices like walls etc.
In order to avoid slipping in the shop, your footwear should ___________.
Answers
Answer:
Be sticky or not slippery
Explanation:
Your company's data center has suffered a recent power outage, and corporate applications were unavailable for two days. You have been asked to craft a strategy to quickly continue operations in the event of another outage. What type of availability (HA/DR/FT) would you recommend and why?
Answers
Answer:
I would recommend HA.
Explanation:
HA stands for high availability. High availability is recommended because it has the power to be consistent or operational for a great amount of time. It is one of the features of a system whose objective is to make sure that operational performance is higher than it would be normally. Such a system works by having multiple components and checking regularly to see if each of the components are working fine, in a situation were it isn't, a component that is working well will be switched to.
According to training, phishing emails have caused what percentage of data breaches?
Answers
According to Verizon's 2021 DBIR, phishing accounts for about 25% of all data breaches, and human error accounts for 85% of all data breaches.
What exactly does "data breach" mean?
Any security lapse that results in the unintentional or intentional loss, alteration, disclosure, or access to personal data is referred to as a personal data breach.
Why is the risk of data breach?
Risks that are frequently encountered include identity theft, prejudice, and harm to the reputation of those whose data has been compromised.
You must determine what transpired in your case and determine whether it was due to a human error, a system error, an intentional or malevolent conduct, or something else else.
Learn more about data breach
brainly.com/question/4760534
#SPJ4
Phishing accounts for around 25% of all data breaches, and human mistake causes 85% of all data breaches, according to Verizon's 2021 DBIR.
A personal data breach is any security defect that permits the accidental or deliberate loss, alteration, disclosure, or access to personal data.
Identity theft, discrimination, and damage to the reputation of persons whose data has been compromised are risks that are commonly encountered.
Thus, you need to figure out what happened in your situation and decide whether it was brought on by a human error, a system error, malicious or intentional behavior, or something else.
For more details regarding phishing, visit:
https://brainly.com/question/24156548
#SPJ6
2. In many jurisdictions a small deposit is added to containers to encourage people to recycle them. In one particular jurisdiction, containers holding one litre or less have a $0.10 deposit, and containers holding more than one litre have a $0.25 deposit. Write a Python script that reads the number of containers of each size from the user. The script should compute and display the refund that will be received for returning those containers. Format the output so that it includes a dollar sign and displays exactly two decimal places.
Answers
Answer:
Here is the Python program:
small_container = int(input("Enter the number of small containers you recycled?"))
large_container = int(input("Enter the number of large containers you recycled?"))
refund = (small_container * 0.10) + (large_container * 0.25)
print("The total refund for returning the containers is $" + "{0:.2f}".format(float(refund)))
Explanation:
The program first prompts the user to enter the number of small containers. The input value is stored in an integer type variable small_container. The input is basically an integer value.
The program then prompts the user to enter the number of large containers. The input value is stored in an integer type variable large_container. The input is basically an integer value.
refund = (small_container * 0.10) + (large_container * 0.25) This statement computers the refund that will be recieved for returning the small and larger containers. The small containers holding one litre or less have a $0.10 deposit so the number of small containers is multiplied by 0.10. The large containers holding more than one litre have a $0.25 deposit so the number of large containers is multiplied by 0.25. Now both of these calculated deposits of containers of each side are added to return the refund that will be received for returning these containers. This whole computation is stored in refund variable.
print("The total refund for returning the containers is $" + "{0:.2f}".format(float(refund))) This print statement displays the refund in the format given in the question. The output includes a $ sign and displays exactly two decimal places by using {0:.2f} where .2f means 2 decimal places after the decimal point. Then the output is represented in floating point number using. format(float) is used to specify the output type as float to display a floating point refund value up to 2 decimal places.

The required code which calculates the amount of refund made by returning the containers written in python 3 goes thus :
small_size = eval(input('Enter number of 1L or less containers to be returned: '))
#prompts user to enter the number of small sized containers to be returned
big_size = eval(input('Enter number of containers greater than 1L to be returned: '))
#prompts user to enter the number of big size containers to be returned
small_refund = (small_size * 0.10)
#calculates the total refund on small sized containers
big_refund = (big_size * 0.25)
# calculates the total refund on big size containers
total_refund = float((small_refund + big_refund))
#calculates the Cummulative total refund
print('Your total refund is $' + '{0:.2f}'.format(total_refund))
#displays the total refund rounded to 2 decimal places.
Learn more :https://brainly.com/question/14353514

What is the first phase of game development?
OA
the concept phase
B.
the pre-production phase
O c.
the prototype phase
D.
the alpha phase
E.
the beta phase
Answers
Hello there! The answer is:
B. The Pre-Production Phase
When someone or a group of people are designing an app or game, they generally follow the rule of phases. Basically, if you don't know what this process is, sound effects, character designs, icons and the concept are discussed. This is the first phase of game development.
I hope I helped you!
which line of code will allow you to only load the localtime() method into active memory

Answers
Answer:
from time import localtime
Explanation:
have a lovely day :)
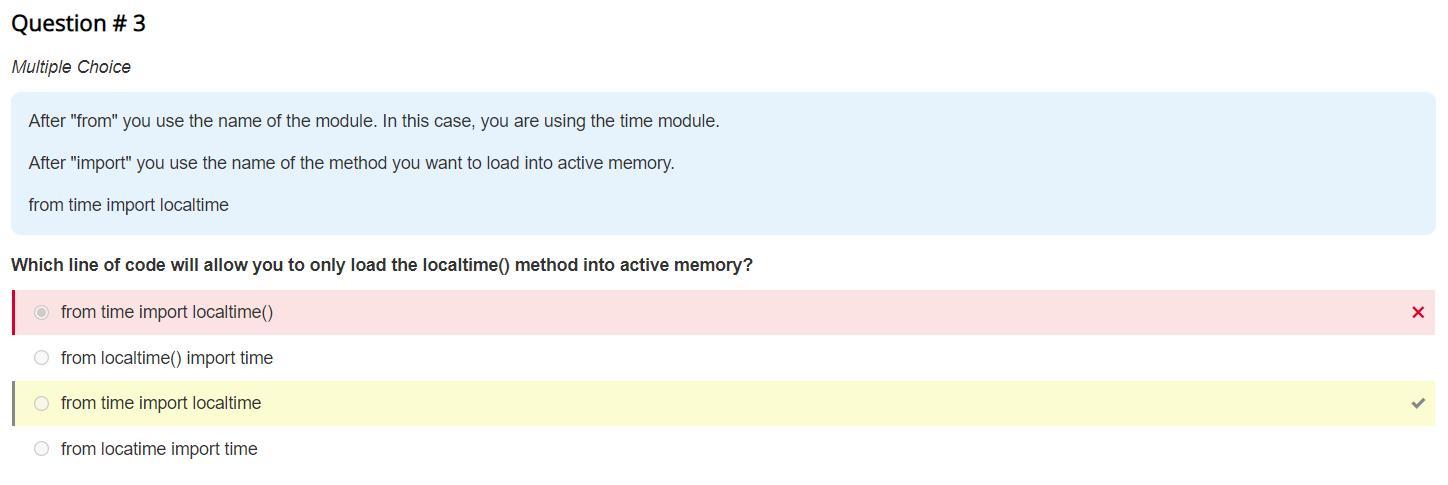
The line of code that will allow you to only load the localtime method into active memory is time.
The localtime function is simply known to be time in seconds as long as Epoch is targeted by timer into a broken-down time.
It is mostly written in local time. The function is known to be of timezone and any seasonal time adjustments. Local timezone information is used as though localtime() calls tzset().LocalTime cannot have a muted date-time object that shows a time, often viewed as hour-minute-second. Time is shown in nanosecond precision.
Learn more from
https://brainly.com/question/19639119
If you have questions about taxes, where can you go to get answers?
Options
A. Smart card
B. RFDI
C. Electronic pater display
D. Touch screen computer
Answers
Answer:
Explanation:
i was told to paste this to other comment sections sooo...HEY PLS DON'T JOIN THE ZOOM CALL OF A PERSON WHO'S ID IS 825 338 1513 (I'M NOT SAYING THE PASSWORD) HE IS A CHILD PREDATOR AND A PERV. HE HAS LOTS OF ACCOUNTS ON BRAINLY BUT HIS ZOOM NAME IS MYSTERIOUS MEN.. HE ASKS FOR GIRLS TO SHOW THEIR BODIES AND -------- PLEASE REPORT HIM IF YOU SEE A QUESTION LIKE THAT. WE NEED TO TAKE HIM DOWN!!! PLS COPY AND PASTE THIS TO OTHER COMMENT SECTIONS
Help please this is my last assignment of the year

Answers
Answer:
the answer is in the website that are there
will i3 pull 3220
and 6 GB of RAM windows 10 without lags?
Answers
It is to be noted that a Core i3 CPU (or processor) with 6GB of RAM running Windows 10 will most certainly be able to run without noticeable delays. However, the performance of the system will be determined by the exact tasks and apps that you will execute on it.
What is a Core i3 Processor?An i3 CPU is a low-end processor that will struggle to handle intense workloads or high-end games, but it should do simple activities like web surfing, word processing, and video playback without trouble. 6GB of RAM is also considered a little amount of memory; it may not be enough to run numerous apps at the same time, or to run heavy applications such as video editing software, but it should be plenty for simple activities.
It's crucial to remember that a computer's performance is influenced by numerous variables other than the CPU and RAM. Other elements, like as the storage drive, graphics card, and cooling system, can all contribute to the total system performance.
Learn mroe about processors:
https://brainly.com/question/28255343
#SPJ1
TASK 1. JUMBLE ME! Direction: Arrange the jumbled letters to form a word. 1. PEREAM 2. RRENT CU 3. METREMO H 4. TORSISER 5. TANCESISRE
Answers
The Rearrangement of the words are:
Ear mapRent cupMETREONSister orSister CaneWhat is arrangement of words?A sorting method is known to be the orders of entries that are based on each word or phrase found in a heading, e.g. spaces, etc.
The Rearrangement of the words are:
Ear mapRent cupMETREONSister orSister CaneLearn more about Arrangement from
https://brainly.com/question/984329
#SPJ1
Computer _ rely on up to date definitions?
A. Administrators
B. Malware Scan
C. Firmware updates
D. Storage Drivers
Answers
Answer: The correct answer is B. Malware Scan
Explanation:
The word "definition" only applies to antivirus and malware removal applications that scan for patterns using the definitions. The other choices do not use definitions. Firmware updates rely on images, storage drives use drivers and administrators are user privilege type.
(a) Create an evenly spaced vector of values from 1 to 20 in increments of 1. (b) Create a vector of values from zero to 2p in increments of p/10. (c) Create a vector containing 15 values, evenly spaced between 4 and 20. (Hint: Use the linspace command. If you can't remember the syntax, type help linspace.) (d) Create a table of conversions from feet to meters. Start the feet column at 0, increment it by 1, and end it at 10 feet. (Look up the conversion factor in a textbook or online.) (e) Create a table of conversions from radians to degrees. Start the radians column at 0 and increment by 0.1 pradian, up to p radians. (Look up the conversion factor in a textbook or online.) (f) Create a matrix aequal to [-1/3, 0, 1/3, 2/3], and use each of the built-in format options to display the results: format short (which is the default) format long format bank format shorte format long e format short eng format long eng format short g format long g format + format rat W
Answers
Use one of the built-in format choices to show the outcomes: brief format (which is the default) format long, format bank, format shorte, format long e, format short g, format long g, and format + rat W
a.)With step 1, the range 1:10 will produce a vector of numbers from 1 to 20.
command:
v1 = 1:20
b.) The range 0:pi/10:2*pi will produce a vector of numbers with a step of pi/10 from 0 to 2*pi.
command
v2 = 0:pi/10:2*pi
c.) The linspace(4,20,15) command will output a list of 15 values evenly spaced between 4 and 20.
command
the v3 = linspace (4,20,15)
d.) Make a column of numbers in the range of 0 to 10, representing the values of the feet. To translate these values to metres, multiply this vector by 0.3048.
command
feets = [0:10]';
feet *0.3048' times metres;
the table, t1 (feets,metres)
e) Make a column of numbers from 0 to pi with a step size of 0.1*pi. The corresponding degree values can be obtained by multiplying it by 180/pi.
command:
"radians" = [0:0.1*pi:pi];
degrees are determined by converting radians to radians*180 pi;
Table: t2 (radians,degrees)
Define the provided vector as m. To show the vector, use the disp() command after setting each format individually.
command:
m = [-1/3 0 1/3 2/3];
brief format
disp(m)
long format
disp(m)
bank format
disp(m)
short e format
disp(m)
style long e
disp(m)
format brief eng
disp(m)
long eng format
disp(m)
short format g
disp(m)
lengthy g format
disp(m)
style +
disp(m)
rat format
disp(m)
Learn more about long here:
https://brainly.com/question/11059729
#SPJ4
Which phrase best describes a countrys monetray base?
A. Only money that cannot be easily spent
B. Only currency and coins in circulation in the economy
C. All money invested in the stock market
D. All money in circulation throughout the economy
(Economics and Finance)
Please be quick I'm doing Apex
Answers
algorithm a solves problems by dividing them into five subproblems of half the size, recursively solving each subproblem, and then combining the solutions in linear time.
Answers
The algorithm you've described employs a divide-and-conquer approach, which tackles problems by breaking them down into smaller subproblems, recursively solving each one, and combining the results in a linear time. In this case, the algorithm divides the original problem into five subproblems, each half the size of the initial problem.
The divide-and-conquer strategy is advantageous as it simplifies complex problems by reducing them to more manageable components. The recursive nature of the algorithm allows it to address each subproblem individually, making the solution process more efficient.
The final step of the algorithm, combining the solutions in linear time, implies that the time complexity of this stage is proportional to the size of the input. This efficiency is crucial for the overall performance of the algorithm, as it allows for a quicker synthesis of the subproblem solutions.
In summary, the algorithm in question is an efficient problem-solving method that leverages the divide-and-conquer approach, dividing the main problem into five smaller subproblems, recursively solving them, and merging the solutions in linear time. This method streamlines the problem-solving process, making it a practical choice for tackling complex problems.
Learn more about algorithm here
https://brainly.com/question/29674035
#SPJ11
Give the steps involved in using Corel draw to make simple design of drawing the Nigerian flag
Answers
If you want to make a straightforward Nigerian flag design using CorelDRAW, adhere to the subsequent guidelines.
The Steps to DesignTo commence, launch CorelDRAW and generate a fresh file that meets your preferred size criteria.
Choose the Rectangle tool located in the toolbox and utilize it to create a rectangular shape that mirrors the flag's backdrop.
Reutilize the Rectangle tool to create a diminutive rectangle at the center, which represents the vertical white band.
Opt for the Circle tool and sketch a circle at the center of the white band that signifies the emblem.
"Assign the suitable shades to every component, wherein the two vertical stripes should be colored in green and the middle stripe and coat of arms must be coated in white."
Using appropriate tools and techniques, include any additional details, such as the emblem of the coat of arms or inscriptions, as needed.
Ensure to store the document in the preferred format, such as PNG or JPEG, and if necessary, extract it for future application.
Read more about graphics design here:
https://brainly.com/question/28807685
#SPJ1
TRUE OR FALSE (1 POINT EACH) 11. Most computers typically fall into one of three types of CPU organization: (1) general Register organization; (2) single accumulator organization;or (3) stack organization.
Answers
TRUE. Most computers typically fall into one of three types of CPU organization: general Register organization, single accumulator organization, or stack organization.
There are three main types of CPU organization that are commonly used in computer architecture:
General register organization: In this type of organization, the CPU has a set of general-purpose registers that can be used to hold data and perform arithmetic and logical operations. Each register has a unique identifier, and data can be moved between registers using load and store instructions.Single accumulator organization: In this type of organization, the CPU has a single accumulator register that is used as the primary location for arithmetic and logical operations. Data is loaded into the accumulator from memory or other registers, and the result of an operation is stored back into the accumulator.Stack organization: In this type of organization, the CPU uses a stack to store data and perform operations. Data is pushed onto the stack and popped off the stack as needed, and arithmetic and logical operations are performed on data that is on the top of the stack.Learn more about registers here:
https://brainly.com/question/16740765
#SPJ11
If you select one slice of pie in a pie chart, you have selected a ____
data series
data set
data point
data line
Answers
Answer:
a date point I think I don't really know
To reduce costs and the environmental impact of commuting, your company decides to close a number of offices and to provide support for staff to work from home. However, the senior management who introduce the policy are unaware that software is developed using Scrum. Explain how you could use technology to support Scrum in a distributed environment to make this possible. What problems are you likely to encounter using this approach
Answers
Answer:
The description including its query is provided throughout the section of the elaboration elsewhere here.
Explanation:
Coordination between teams is the main challenge that this new strategy can make. Agile creation is focused on the teamwork of cross-functional teams, where every other mission is identified and distinct teams are formed. All the departments collaborate and afterward work in stages until the completion of this research project.Unless the organization shuts several departments, contact with various teams and peers will be disrupted and contact differences with workers as well as the team would be established. The best approach will be to provide regular communication calls with multiple project managers such that each project stage is synchronized. In turn, this same project coordinator should always have numerous calls with his group members to even get construction progress.Glenda is searching airline schedules on HolApp, a mobile Web application. While browsing the application, a banner appears on the mobile screen showcasing offers and discounts on air tickets. The banner is best referred to as a(n) ________.
Answers
Answer:
online display advertisement
Explanation:
Q:
Glenda is searching airline schedules on HolApp, a mobile Web application. While browsing …
A. online display advertisement
B. contextual advertisement...
A:
A