I WILL GIVE BRAINLIEST TO WHO ANSWERS FIRST AND CORRECTLY.
Pressing the Backspace key deletes the text to the ______ of the insertion point.
Answers
Answer:
The word you are looking for is "right"
Explanation:
Answer:
Pressing the Backspace key deletes the texts to the left of the insertion point.
Explanation:
Related Questions
7 (a) What is the function of the following combination of keys? CTRL + A i CTRL + Page Up v. CTRL + E vii. CTRL + F viii. CTRL + SHIFT HOME lain the role/use of the following features in a word processor (1) iv. CTRL+B CTRL + Home. vi. CTRL + Z (4 marks) Correct
Answers
Keyboard shortcuts are keys or key combinations that offer an alternative method of performing tasks that you would ordinarily perform with a mouse.
What is the function of shortcut key?Using shortcut keys in computer applications can help you navigate and carry out tasks more quickly and easily. Alt (on IBM-compatible computers), Command (on Apple computers), Ctrl, or Shift combined with another key is used to execute shortcut keys.The name "shortcut" comes from the fact that keyboard shortcuts are frequently used to speed up routine tasks by condensing input sequences to a few keystrokes. Most keyboard shortcuts require the user to press and hold a number of keys simultaneously or a series of keys one after another in order to distinguish them from regular keyboard input.Keyboard shortcuts are stringed-together keystrokes that let you complete a task fast. They are helpful and frequently excellent time savings.Given shortcuts :
CTRL + A = Select all document content.
CTRL + Page Up = Move to the previous sheet in the workbook.
CTRL + E = Aligns the line or selected text to the center of the screen.
CTRL + F = To find a word or words on a page.
CTRL + SHIFT HOME = highlights all text from the current position to the beginning of the text or page.
CTRL + Z = undo an action
Learn more about shortcut key refer to :
https://brainly.com/question/14447287
#SPJ1
How does visualizing help you better understand a poem?
Answers
explain why the computer is powerful working tool???
Answers
Answer:
here ya go
Explanation:
A computer is a powerful tool because it is able to perform the information processing cycle operations (input, process, output, and storage) with amazing speed, reliability, and accuracy; store huge amounts of data and information; and communicate with other computers.
Which of the following is NOT true about simple machines?
Group of answer choices
They can change the amount of force required.
They can reduce the amount of work that must be done.
They can change the distance over which a force is exerted.
They can change the direction in which a force is exerted.
Answers
Answer:
option A : they can change the amount of force required .
What actions can you take from the Go To tab? Check all that apply.
O moving to a specific page
O moving to a specific line
moving a file to a new folder
moving a specific number of pages ahead of the current position
moving to a new document
Answers
Moving to a specific page
Moving to a specific line
Moving a specific number of pages ahead of the current position
HOPE THAT HELP YOU!
Moving to a specific page and moving to a specific line as the moving a specific number of pages ahead of the current position.
When is the use of file?When you need to move a file from the document folder to the new folder you just created can be done by different methods and when you click right button of mouse there is a list pop up in which many options flashes you should choose either cut or copy from the list.
1)Choose 'cut' then paste it in the new folder. If you choose cut the file it will be removed from the document folder.
2)Choose 'copy' then paste it in the new folder. If you choose copy the file the file will remain in the document folder and also in the new folder.
An encrypted connection between user devices and one or more servers is established by a virtual private network (VPN), a service that provides Internet security. A VPN can safely link a user to the internal network of a business or to the Internet at large. Businesses frequently use a VPN to provide remote workers with access to internal software and data or to establish a single shared network among numerous office locations.
Therefore, Moving to a specific page and moving to a specific line as the moving a specific number of pages ahead of the current position.
Learn more about VPN on:
https://brainly.com/question/29432190
#SPJ2
a technological advancement that does not need direct line of sight to be read and that provides for low-cost tracking and security enhancements by using radio waves is called
Answers
RFID is a development in technology that uses radio waves to enable low-cost tracking and security improvements without requiring a clear line of sight.
How does RFID technology operate and what is it?Tags and readers are the two halves of the wireless system known as Radio Frequency Identification (RFID). The reader is an electronic gadget with one or more antennas that transmit radio waves and take in signals from RFID tags.
What is an RFID example?Fixed readers, which are installed in a specific location through which RFID tags pass. For instance, Amazon Go allows you to pay without visiting a cashier. The reader only needs to be in an RF zone for you to pass through to get the tag data. Mobile readers are portable, carry-anywhere reading devices.
To learn more about RFID technology visit:
brainly.com/question/17086920
#SPJ4
How would you define a cloud today?
as a non-factor
networking
server
any remote virtualized computing infrastructure
Answers
Answer:
The answer is "any remote virtualized computing infrastructure".
Explanation:
The term cloud is used as the symbol of the internet because cloud computing is some kind of internet computing, that offers various services for computers and phones in organizations via the internet.
The virtual network allows users to share numerous system resources throughout the network system.It allows you to access the optimal productivity by sharing the resources of a single physical computer on many virtual servers.can you defeat all 3 Daughters of Lerion at a 98 power level in AC Valhalla
Answers
Answer:
???????
Explanation:
Answer:
defeat what now...
Explanation:
What should be included in a publication or website after obtaining the right to use a graphic, text, or other item found on the Internet
Answers
Based on computer and media applications, the thing that should be included in a publication or website after obtaining the right to use a graphic, text, or other item found on the Internet is known as Reference
What is a Reference?Reference is the act or action of mentioning it alluding to something. Usually, reference to literary or artistic work is considered a source to the origin of the work.
References do not cover unauthorized access. However, when a right to use work like publication, text, graphics, etc., is given, it is expected that the individual should provide references to the sources.
Hence, in this case, it is concluded that the correct answer is "Reference."
Learn more about Reference here: https://brainly.com/question/6260792
do you have to be in hard mode in terraria to make the timeless traverler vanity set
Answers
After a group sets a project schedule, members should be prepared to
O make periodic adjustments on an as-needed basis.
make changes when some members fall behind.
drop other activities so they can complete their job on time.
complete a study-time survey to prove they can do the work.
Answers
After a group sets a project schedule, members should be prepared to complete a study-time survey to prove they can do the work.
What is a group project?A group project is a project in which more than one person work together. Group projects are given to improve the work, as various minds can bring out various implements for the project.
Thus, the correct option is D. complete a study-time survey to prove they can do the work.
Learn more about group project
https://brainly.com/question/14488746
#SPJ1
Answer:
A on edge
Explanation:
Q2. What does JSON stand for? Can you give an example of a JSON object. Q3. What is the purpose of a "projection" in a find query for MongoDB?
Answers
Answer:
Q2: JavaScript Object Notation
Q3: The $project function in MongoDB passes along the documents with only the specified fields to the next stage in the pipeline. ... The specification for $project command contain the inclusion of fields, the suppression of the _id field, the addition of new fields, and the resetting the values of existing fields.
Explanation:
Question 8 of 10
What does DOS stand for?
A. Disk override system
B. Disk only system
C. Disk opening system
D. Disk operating system
Answer: D
Answers
Answer:
Dis operating system
Explanation:
refers to the original operating system developed by Microsoft for IBM
Answer:
disk
Explanation:
You manage a network that has multiple internal subnets. You connect a workstation to the 192.168.1.0 subnet, which uses the default subnet mask. This workstation can communicate with some hosts on the private network, but not with other hosts. You run ipconfig/all and see the following:
Ethernet adapter Local Area Connection:
Connection SPecifi.c DNS Suffix . : mydomain.local
Description ....... : Broadcom network adapter
Physical Address................ : 00-AA-BB-CC-74-EE
DHCP Enabled.......NO
Autoconfiguration Enabled.... Yes
IPv4 Address...............: 192.168.1.1
Subnet Mask.................: 255.255.0.0
Default gateway..........: 192.168.1.1
DNS Servers.............: 192.168.1.20 192.168.1.27
Which of the following is the MOST likely to cause of the problem?
Answers
The correct answer is router. A router connects different networks and routes traffic between them. Every network connected by a router has a special identification number or address called a network number.
Arp. To see the MAC addresses connected to IP addresses that the local workstation has recently contacted, use the arp command. The subnet mask for APIPA is 255.255.0.0, and the IP address range is (169.254.0.1 to 169.254.255.254), with 65,534 valid IP addresses. The range 169.254. 0.0-169.254. 255.255 has been set aside by the Internet Assigned Numbers Authority (IANA) for Automatic Private IP Addressing. Since routable addresses are guaranteed not to clash with it, APIPA offers an address. Hubs link various computer networking components together. In that it amplifies signals that degrade after travelling across long distances on connected wires, a hub also performs the function of a repeater.
To learn more about router click the link below:
brainly.com/question/29768017
#SPJ4
or this question, you can assume you have access to a class called pet that stores all of the data that applies to a specific pet (name, type of animal, breed, health history, etc.). a pet store needs to create a map that stores the name of the pet (stored as a string) and the corresponding pet object. create a map that can store such data. you don't need to add anything it, just create and return a map to store the right data.
Answers
Certainly! Here's an example of how you can create a map to store the name of a pet as a string and its corresponding `Pet` object:
```python
from typing import Dict
from pet import Pet
def create_pet_map() -> Dict[str, Pet]:
pet_map = {} # Create an empty dictionary to store the pet data
# Add pets to the map
pet1 = Pet("Max", "Dog", "Labrador Retriever", "No significant health issues")
pet_map["Max"] = pet1
pet2 = Pet("Charlie", "Cat", "Persian", "Allergies, requires special diet")
pet_map["Charlie"] = pet2
pet3 = Pet("Bella", "Dog", "Golden Retriever", "Up-to-date vaccinations, healthy")
pet_map["Bella"] = pet3
return pet_map
```
In this example, the `create_pet_map` function creates an empty dictionary called `pet_map`. It then creates several `Pet` objects with different properties and adds them to the map using the pet's name as the key.
Note that in the example above, I assume you have a class called `Pet` that represents a pet and stores relevant data about it. You would need to define the `Pet` class separately and provide the appropriate implementation for it based on your specific requirements.
Feel free to modify the code according to your needs and add more pets to the map.
Learn more about Pet here:
https://brainly.com/question/31293842
#SPJ11
One part of a development team has completed an algorithm. Why is it important to share it with others on the team? Choose all that apply. If it is easy to understand, no one will dispute what is included in the algorithm. It will give everyone else an opportunity to comment on the process described in the algorithm. It will serve as the starting point for all future activity. It communicates the consecutive instructions of the solution.
Answers
Answer: B,C,D
Explanation:
Answer:
the answer is B,C,D
Explanation:
what must you do when emailing pii or phi
Answers
When emailing personally identifiable information (PII) or protected health information (PHI), it is important to take steps to ensure the privacy and security of the data. Firstly, you should encrypt the email and any attachments containing PII or PHI to prevent unauthorized access.
Secondly, double-check that you are sending the email to the intended recipient(s) and not accidentally sharing sensitive information with the wrong person. Additionally, always use a secure email service and avoid using public Wi-Fi networks to send sensitive data. Finally, ensure that you have obtained proper consent from the individuals whose data you are sharing and that you are in compliance with any applicable laws or regulations regarding the handling of PII or PHI.
To learn more about data click here: brainly.com/question/29117029
#SPJ11
Edhesive 4.2 question 2 answers
Answers
Answer:
total=0
pet=input("what pet do you have? ")
while pet!= "rock":
total=total+1
print("you have a "+pet+" with a total of "+ str(total)+ " pet(s)")
pet=input("What pet do you have? ")
Explanation: Just copy and paste above again just copy and paste this will get you a 100 percent i made another account just to give yall edhesive answers if yall need help with any edhesive just comment below
explain how computer system is different from computer in 150 words
Answers
Answer:
To be distinguished from the physical or hardware components of a computer, programs are collectively referred to as software. A computer system, therefore, is a computer combined with peripheral equipment and software so that it can perform desired functions.
A computer is a device that does certain things (mostly very basic data manipulation and mathematical functions), just as a building is a device that does certain things (such as housing offices or apartments). What makes a computer special is that it does these things very very quickly. A computer system is a mechanism that incorporates multiple computers along with other things like data storage devices, networks, and data paths (ways to move data around among storage devices and computers), as well as software (rules for how to do things), procedures and processes and protocols and on and on. A computer system performs a rather complex function, just as a city is a system that involves multiple buildings along with roads, sewage treatment plants, water and electrical systems and many other things that enable it to perform a function considerably more complex than the function performed by a building.
A major advance in the field of computing was the advent of networking. Before that, computers had to be near each other in order to communicate with each other and computer systems typically existed in a relatively small physical location where all the computers were in the same place. If you see a movie released in the period from roughly 1950 to 1980, you will note that computers and computer systems were typically depicted as gigantic things located in a large room. With networking, a computer system might have computers in one place, remote access devices in another place, and other computers in other places. Thus a building might have computers and terminals and printers and what have you all over it, all capable of communicating with each other. The internet, which enables world wide networks, has made it possible to have computer systems that consist of thousands of computers (or more), located all over the globe.
a computer is like an engine whereas a computer system is like a vehicle (a car or truck or boat) that contains one or more engines and does something more complex than what the engine does. But the engine is the essential component that enables the vehicle to do what it does. a computer exists in a single place and does a primitive set of functions. A computer system combines a computer with many other things to perform a complex set of functions. It can also exist in a single place, but it may exist in many places at the same time.
Explanation:
Pleeeeeeeeeeeeeeeeeeez mark me as brainliest i did this so hardly so plez i beg u and cry to mark me as brainliest and give a vote of full and give a thanks
Linear programming
Q.2) Consider the Linear problem: Min. Xo = 3x1 + 2x2 2 x1 + 3 x2= 12, (20 6 x1 +4x2 ≥24, XI≥0, X220 Use Graphical Solution method and find the values of X1, X2 and Xo at optimal solution.
Answers
The optimal solution is X1 = 2, X2 = 2, and Xo = 10.
Linear Programming:Linear programming is a branch of mathematical optimization that aims to find the optimal solution to a problem with linear constraints and a linear objective function. Linear programming problems can be solved using a variety of techniques, including the graphical method, the simplex method, and the interior-point method. In this problem, we will use the graphical method to find the optimal solution.
Graphical Method for Linear Programming:We can use the graphical method to solve a linear programming problem with two variables. The graphical method involves drawing the feasible region (the set of all feasible solutions to the problem) and then finding the optimal solution (the point that minimizes or maximizes the objective function) by examining the corner points of the feasible region.
To draw the feasible region, we need to plot the constraints and shade the region that satisfies all of the constraints. The optimal solution will always occur at one of the corner points of the feasible region. Once we have found the corner points, we can evaluate the objective function at each point and choose the one that minimizes or maximizes the function.
We can also use the graphical method to determine if the problem is infeasible (there is no feasible solution), unbounded (the optimal solution occurs at a point at infinity), or degenerate (there are multiple optimal solutions).Solution:Given the following linear problem:Min. Xo = 3x1 + 2x22 x1 + 3 x2 = 12,(20 6 x1 + 4x2 ≥ 24,X1 ≥ 0, X2 ≥ 0.To solve this problem, we need to plot the constraints and find the feasible region.
The first constraint, 2 x1 + 3 x2 = 12, is a straight line with intercepts (0, 4) and (6, 0). The second constraint, 6 x1 + 4 x2 ≥ 24, is also a straight line with intercepts (0, 6) and (4, 0). To find the feasible region, we need to shade the region that satisfies both constraints. The shaded region is shown below:
We can see that the feasible region is bounded and has four corner points: (0, 4), (2, 2), (4, 0), and (6, 0). To find the optimal solution, we need to evaluate the objective function at each corner point and choose the one that minimizes the function. The values of the objective function at each corner point are:Xo(0, 4) = 3(0) + 2(4) = 8Xo(2, 2) = 3(2) + 2(2) = 10Xo(4, 0) = 3(4) + 2(0) = 12Xo(6, 0) = 3(6) + 2(0) = 18
Therefore, the optimal solution is X1 = 2, X2 = 2, and Xo = 10.
Know more about Linear Programming here,
https://brainly.com/question/30763902
#SPJ11
What is the Multiple Source Test? (1 point) checking to make sure that information can be found in more than one place a fact checking software that tests information found on the Internet an amendment that states that all information must be in multiple locations a test that provides more than one answer possibility 2. Which of the following is a true statement? (1 point)
Answers
Answer:
there is no following options
Explanation:
Answer: The correct answer is checking to make sure that information can be found in more than one place
Explanation: Sources are defined as locations where information is stored and accessible. When researching and validating information on the Internet (or in print), it is common practice to test multiple sources to corroborate the same details (aka Multiple Source Testing).
Which is an aspect of structural-level design?
A.
flow
B.
radiosity
C.
perspective
D.
style
Answers
Answer:
flow
Explanation:
Flow is the obstacles the player will face if a player can't cross a broken bridge then the player will have to do certain side quests or wait until it is built and can be crossed. one the obstacle is gone the player can explore more parts of the world
also just learned this right now and finished.
Viruses that load from usb drives left connected to computers when computers are turned on are known as.
Answers
Answer:
Boost-Sector Viruses
Explanation:
The viruses of such types are known as boot sector viruses.
What is computer virus?A computer virus is a form of malware that accompanies another program (such as a document) and has the ability to multiply and propagate once it has been run on a machine.
When the drive's VBR is read, an infected floppy disk or USB drive connected to a computer will transfer, modify, or replace the preexisting boot code. The virus will load and start right away as part of the master boot record the following time a user attempts to boot their desktop.
Hence, the virus that can be loaded when computer is turned on is boot sector virus.
To know more about computer virus click on,
https://brainly.com/question/29446269
#SPJ12
What methods do you use when researching a complicated or difficult subject? What tools are most useful to narrowing down and validating your research? Explain your answers.
Answers
please help me in this question

Answers
Answer:
Explanation:
i think operands
For questions 5-8, consider the following code:
def mystery(a = 2, b = 1, c = 3):
return 2 * a + b + 3 * c
What is the output for mystery(4, 3, 7)?
What is the output for mystery(5, 8)?
What is the output for mystery(1)?
What is the output for mystery()?
Answers
The output for mystery(4, 3, 7) is shown below. The output of the function mystery with the inputs (4, 3, 7) would be 2 * 4 + 3 + 3 * 7, which is equal to 8 + 3 + 21 or 32.
The value that the method numsInfo returned best fits which of the following?The index of the first element in the array whose value is identical to that of element at position n.
What exactly is the number mystery?The definition of a mystery number is a number that may be written as the sum of two other numbers, and those two numbers must be the opposites of one another.
To know more about output visit:-
https://brainly.com/question/18133242
#SPJ1
4.2 Code Practice: Question 1
Can someone help me write the code in python language?
Answers
Answer:
number = int(input("Enter a number: "))
sum = number
c = 1
while (sum<=100):
number = int(input("Enter a number: "))
sum = sum + number
c = c + 1
print("Sum: " + str(sum))
print("Numbers Entered: " + str(c))
Explanation:
Hope this helps lovely :)
which of the following statements about user personas is true? 1 point ux designers should avoid creating backstories for personas personas can help identify patterns of behavior in users. personas are modeled after the characteristics of the ux designer. a persona is a real user who provides real reviews on a product.
Answers
The statement "personas can help identify patterns of behavior in users" is true.
What is User personas?User personas are fictional characters created by UX designers to represent different types of users and their behaviors, goals, motivations, and pain points.
By creating user personas, UX designers can better understand their users' needs and design products that meet those needs. Personas are not modeled after the characteristics of the UX designer, and they do not have to be based on real users.
However, user research and feedback can be used to create more accurate and effective personas.
Read more about UX design here:
https://brainly.com/question/30736244
#SPJ1
Go to the Scenario PivotTable worksheet. Madhu wants to make the PivotTable easier to interpret. Remove the filter from the PivotTable. Use Total Revenue as the row label in cell B3, use Total Expenses as the row label in cell C3, and use Net Income as the row label in cell D3. Display the Revenue, Expenses, and Net Income values in the Currency number format with no decimal places. Display negative values in red, enclosed in parentheses. Resize columns B:D to their best fit using AutoFit.
Answers
Answer:
Click and drag the filter out of the "PivotTable Fields" so that is it empty IMG1. Change the row labels to what it tells you IMG2. Change the values as Currency format shown in the top right corner of IMG3. Select cells B4:D6 and press ctrl1 and match IMG4. Now double press the lines in between B&C, C&D, and D&E.

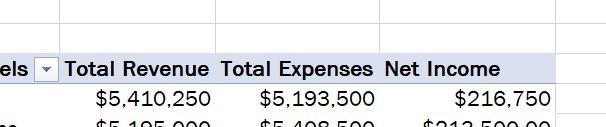


For ul elements nested within the nav element, set the list-style-type to none and set the line-height to 2em.
For all hypertext links in the document, set the font-color to ivory and set the text-decoration to none.
(CSS)
Answers
Using the knowledge in computational language in html it is possible to write a code that For ul elements nested within the nav element, set the list-style-type to none and set the line-height to 2em.
Writting the code:<!doctype html>
<html lang="en">
<head>
<!--
<meta charset="utf-8">
<title>Coding Challenge 2-2</title>
</head>
<body>
<header>
<h1>Sports Talk</h1>
</header>
<nav>
<h1>Top Ten Sports Websites</h1>
<ul>
</ul>
</nav>
<article>
<h1>Jenkins on Ice</h1>
<p>Retired NBA star Dennis Jenkins announced today that he has signed
a contract with Long Sleep to have his body frozen before death, to
be revived only when medical science has discovered a cure to the
aging process.</p>
always-entertaining Jenkins, 'I just want to return once they can give
me back my eternal youth.' [sic] Perhaps Jenkins is also hoping medical
science can cure his free-throw shooting - 47% and falling during his
last year in the league.</p>
<p>A reader tells us that Jenkins may not be aware that part of the
least-valuable asset.</p>
</article>
</body>
</html>
See more about html at brainly.com/question/15093505
#SPJ1

