copy the pt4 worksheet to a new worksheet named pt5. delete the text in cell a1. remove the date and department fields from the pivottable. add a slicer for the department field and a timeline for the date field. use the slicer and the timeline to filter the pivottable to show the total sales amount for each manager for the kitchen and bath and plumbing departments for april 2015 through october 2015.
Answers
Copy pt4 to pt5, delete A1 text, remove date and dept fields, add slicer and timeline, filter by managers and departments.
How to filter a PivotTable using a slicer and timeline?Right-click on the "pt4" worksheet tab and select "Move or Copy".In the "Move or Copy" dialog box, select "Create a copy" and choose "pt5" as the new worksheet name. Click "OK".Click on cell A1 in the "pt5" worksheet and press the "Delete" key to remove the text.Click anywhere in the PivotTable in the "pt5" worksheet to display the "PivotTable Fields" pane.Uncheck the "Date" and "Department" fields in the "PivotTable Fields" pane to remove them from the PivotTable.Click anywhere in the PivotTable and go to the "PivotTable Analyze" tab in the ribbon.Click on the "Insert Slicer" button and select "Department" from the list of available fields. Click "OK".Click on the "Insert Timeline" button and select "Date" from the list of available fields. Choose "April 2015" as the start date and "October 2015" as the end date. Click "OK".Use the slicer to select the "Kitchen and Bath" and "Plumbing" departments.Use the timeline to select the period from April 2015 through October 2015.The PivotTable should now show the total sales amount for each manager for the selected departments and period.Learn more about worksheet
brainly.com/question/27708288
#SPJ11
Related Questions
you are the administrator for a large single-domain network. you have several windows server domain controllers and member servers. your 3,500 client computers are windows workstations. today, one of your users has called for help. it seems that his computer is reporting that a trust cannot be established between his windows computer and the domain controller. he is unable to log on to the domain. you examine the computer's account using active directory users and computers, and there is nothing obviously wrong. you need to allow this user to log on to the domain. what should you do? answer reset the computer account. rejoin the domain. reset the computer account and rejoin the domain. re-enable the computer account. re-enable the computer account and rejoin the domain.
Answers
In this scenario, the user is unable to log on to the domain due to the error message stating that a trust cannot be established between his computer and the domain controller.
1)As an administrator, the first step would be to examine the computer's account using Active Directory Users and Computers. If there is nothing obviously wrong with the account, the next step would be to reset the computer account.
2)Resetting the computer account will remove the trust relationship between the workstation and the domain controller, and will also disjoin the workstation from the domain. After resetting the computer account, the user can then rejoin the domain by logging in with an account that has administrative rights on the computer.
3)If resetting the computer account does not solve the issue, the next step would be to re-enable the computer account. This will allow the computer to communication with the domain controller and establish the trust relationship again. Once the computer account is enabled, the user can attempt to log in to the domain again.
4)In summary, to allow the user to log on to the domain, the administrator should reset the computer account and rejoin the domain. If this does not work, re-enabling the computer account should be the next step.
For more such question on communication
https://brainly.com/question/26152499
#SPJ11
import java.util.Scanner;
public class PigLatin {
public static void main(String args[]) {
Scanner console =new Scanner(System.in);
System.out.println("Please enter a word");
String phrase=console.nextLine();
System.out.println(eachWord(phrase));
}
public static String eachWord(String phrase) {
String help[]=phrase.split(" ");
for(int i=0; i
if (help[i].charAt(0) == 'a'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'e'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'i'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'o'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'u'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'A'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'E'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'I'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'O'){
return help[i] + "-ay";
}
if (help[i].charAt(0) == 'U'){
return help[i] + "-ay";
}
else {
return help[i].substring(1)+"-"+help[i].charAt(0)+"ay";
}
}
return "aoujbfgaiubsgasdfasd";
}
I need help with this Pig Latin Program. I want to split the string so each word can run through the method eachWord. I don't know how to revamp this!
Answers
Answer:b
Explanation:
I took quiz
Answer:
uuuuuuuuuuhhm
Explanation:
CODE!
Where do you stand on the controversial encryption issue? Should governments like the United States be allowed to have an escrowed key to all encrypted communications? Is unfettered encryption a good thing for cyberspace?
Answers
Where you stand on the controversial encryption issue depends on your point of view.
Some people believe that the government should have an escrowed key to all encrypted communications to prevent terrorism and other criminal activities. Others believe that unfettered encryption is a good thing for cyberspace and that the government should not be able to access private communications.
Encryption is a crucial part of cybersecurity and is used to protect sensitive information. It can also be used to prevent cyberattacks and data breaches. However, encryption can also be used by criminals to hide their activities and communications from law enforcement agencies and the government.
Encryption can make it difficult for the government to track down terrorists and other criminals. However, giving the government a backdoor to encrypted communications could also lead to abuse of power and violations of privacy rights.
Learn more about encryption at
https://brainly.com/question/31375565
#SPJ11
A well-structured relation contains minimal redundancy and allows users to manipulate the relation without errors or inconsistencies. True O False
Answers
The statement "A well-structured relation contains minimal redundancy and allows users to manipulate the relation without errors or inconsistencies" is TRUE.
Let's take a look at what this statement means.A relation is an essential aspect of the database, and its structure must be carefully designed to minimize data redundancy and maintain data integrity. In a well-structured relation, each attribute holds atomic values, meaning that it cannot be further subdivided or broken down into smaller parts.Redundancy in data can lead to anomalies, including insertion, deletion, and update anomalies. These anomalies can result in inconsistent and erroneous data when changes are made to the database structure or content.A well-structured relation must also adhere to the normalization rules, which help to eliminate redundant data. Normalization is a technique used to organize data in a database to minimize redundancy and dependency. A normalized relation is more flexible and allows users to manipulate the data without inconsistencies and errors. Hence, the given statement is true, and a well-structured relation contains minimal redundancy and allows users to manipulate the relation without errors or inconsistencies.
Learn more about data :
https://brainly.com/question/31680501
#SPJ11
Need help pleaseeee!!!!!

Answers
Answer:
Attenuation
Explanation:
This means the signal is getting weaker in long cables.
Which of the following ensures that data can be modified only by appropriate mechanisms? O A. integrity O B. confidentiality O C. redundancy O D. availability
Answers
Information integrity makes ensuring that only proper procedures may change the data.
Which of the following guarantees that people with permission may access data?Data accessibility refers to the ability of authorized people to access data. It offers reassurance that authorized users will always be able to access your system and data.
Is the integrity of a data unit guaranteed by a variety of mechanisms?Several techniques are used to ensure the integrity of a single data unit or stream of data units. Exchange of information with the aim of ensuring an entity's authenticity through authentication.
To know more about Information integrity visit:
https://brainly.com/question/30094382
#SPJ4
It's usually easier to change the design of a photo album slide show A.after you've created the presentation. B.before you've created the presentation. C.before you've planned out the presentation. D.after you've planned out the presentation but before creating it.
Answers
Answer:
A. after you've created the presentation.
Explanation:
A power point presentation is defined as a presentation program where one can create any presentation or design any layout like the photo album slide show to present it to others.
Once the album is created in the PowerPoint, it can be changed by going to the slide show and editing the content of the photo album of the slide show. Thus it is easier to make any changes in the design of the photo album slide show after the presentation have been created.
At one time, ibm was one of the largest manufacturers of personal computers. What was a product that ibm was well known for that came before computer?.
Answers
Answer:
A counting machine
Explanation:
IBM was well known for making a counting machine before they made computers
PPPLLLLSSS HELLLLP ME What kind of goal does Ariel set when he works to graduate from high school in four years?
short term
long term
normative
fantasy
Answers
Answer:
b. long term
Explanation:
The kind of goal that Ariel set when he works to graduate from high school in four years is long-term. The correct option is b.
What are goals?Your life objectives are all the things you hope to achieve. Your life objectives can have a long-lasting effect on you and are frequently quite important to you. They can be big, difficult objectives, or they can be smaller, more intimate objectives.
There are different types of goals like short-term and long-term goals. Short-term goals are made for a short time. Long-term goals are made for a long or large amount of time.
While some objectives might be more influential at one point in one's life, they might become less indispensable at a later one. Given the prevalence of positive psychology sensitization, it is now widely understood that happiness is one of, if not the most essential aim in life.
Therefore, the correct option is b. long term.
To learn more about goals, refer to the link:
https://brainly.com/question/6478420
#SPJ6
Choose the words that make the following sentence true.
Primary memory is (not volatile, volatile) and (not permanent, permanent).
Answers
Answer:
Primary memory is volatile and not permanent.
Answer:
Primary memory refers to the memory that is accessed by the CPU and is not permanent.
It is volatile, since it is cleared out when the device is powered off.
Explanation:
Edge 2022

Where would you find the Create Table Dialog box ?
Answers
Hope it’s right
Best luck with your studying
Answer:
From the Insert command tab, in the Tables group, click Table. NOTES: The Create Table dialog box appears, displaying the selected cell range.
Explanation:
Write a pseudo code to calculate the area of rectangle
Answers
Answer:
Explanation:
Declare variables length and width
Input length and width
Calculate area by multiplying length and width
Print the area
Here's what the code would look like in a more detailed and structured format:
CalculateRectangleArea
1. Declare variables length, width, and area
2. Input length
3. Input width
4. Set area = length * width
5. Output area
END ALGORITHM
A successful attack on a network may adversely impact security in all the following ways EXCEPT:
- Loss of confidentiality
- Loss of integrity
- Loss of functionality
- Loss of availability
Answers
A successful attack on a network can adversely impact security in all the following ways, except for the c. loss of functionality. A loss of confidentiality occurs when unauthorized individuals gain access to sensitive information, such as personal or financial data.
This can lead to identity theft or financial fraud. A loss of integrity happens when unauthorized individuals alter or manipulate data, causing errors or inconsistencies in the information. This can lead to mistrust of the system and the data it contains. A loss of availability occurs when the network or system becomes unavailable, preventing users from accessing information or services. This can have serious consequences for businesses that rely on their networks to operate efficiently.
In contrast, a loss of functionality is not necessarily a direct result of a successful attack on a network. Instead, it refers to the failure of a system or network to perform its intended tasks or functions, regardless of whether or not an attack has occurred. While a loss of functionality can be a serious issue, it is not a direct consequence of a network attack and is therefore not included in the list of ways in which such an attack can impact security.
Learn more about financial fraud here-
https://brainly.com/question/30715266
#SPJ11
If you have a 3D printer please show me a vid of you making something because I'm interested in getting one. Ty! Also can someone show me how to put more points in a question that I ask on Brainly?
Answers
Explanation:
Too add more points on your brainly question(phone), type your question
Then, see on your top left, you can see the points. It will show 10,which means you have to lose 10 points which is the minimum points for one question. If you are generous to give more points, click on it the you can scroll till the maximum point which is 100..but each points you give will divide 2.
For example, you just loose 10 points for your question but I only got 5 points
Hope you understand this
I'm not sure with laptop
HAVE A GOOD DAY!
Where are methods listed in a UML class diagram showing three parts?
in the top third of the diagram
in the middle third of the diagram
in the bottom third of the diagram
anywhere in the diagram a lowercase m is shown
Answers
Answer:
the bottom third
Explanation:
Check out the exampe below.
swim() would be an example of a method.

PLEASEEE HELP HURRY

Answers
To start searching for a scholarly article on G. o. ogle Scholar, you should:
"Type the title of the article or keywords associated with it." (Option A)
What is the rationale for the above response?Here are the steps you can follow:
Go to Go. o. gle Scholar website In the search box, type the title of the article or relevant keywords associated with it.Click the "Search" button.Browse through the search results to find the article you are looking for.Click on the title of the article to view the abstract and other details.If the article is available for free, you can download or access it directly from the search results page. If not, you may need to purchase or access it through a library or other academic institution.Note that you can also use advanced search options and filters available on Go. ogle Scholar to narrow down your search results based on various criteria, such as publication date, author, and journal.
Learn more about G. o. ogle at:
https://brainly.com/question/28727776
#SPJ1
_______ make up the basic structure of a relational database with columns containing field data and rows containing record information.
Answers
Tables make up the basic structure of a relational database…
Which function in excel helps facilitate taking a random sample?
Answers
true or false? two hexadecimal digits can be stored in one byte.
Answers
The given statement is True. Two hexadecimal digits can be stored in one byte.
In computing, a byte is a unit of digital information that typically consists of 8 bits. Each bit can have two possible values: 0 or 1. Hexadecimal (base-16) is a numerical system commonly used in computing, which represents numbers using 16 different symbols (0-9 and A-F). Each hexadecimal digit corresponds to 4 bits. Since a byte consists of 8 bits, it can accommodate two hexadecimal digits.
In binary, the values from 0000 to 1111 represent the numbers 0 to 15. In hexadecimal, these values are represented by the digits 0 to F. Therefore, a byte can store any combination of two hexadecimal digits ranging from 00 to FF. This correspondence between hexadecimal and binary allows for more compact representation and easier conversion between different numeral systems when working with bytes in computer systems.
Learn more about byte here;
https://brainly.com/question/15750749
#SPJ11
What is the name of the national outreach project?
Answers
Answer:
FCCLA should be the answer.
Explanation:
Suppose a probe was sent to land on an airless moon. As the probe got close, the moon's gravity began pulling it straight down. The probe used its rockets to brake.
Unfortunately, a calculation error was made when the probe was designed. As the probe got close to the surface, the force of gravity became greater than the maximum force of its rockets.
Assuming the force of gravity was practically constant from that point on, describe the probe's vertical motion as it neared the moon's surface

Answers
The description of the probe's vertical motion as it neared the moon's surface is that . The Moon's surface gravity is said to be weaker due to the fact that it is far lower in terms of mass than Earth.
What are Space Probe?This is known to be a kind of unscrewed spacecraft sent from Earth and it is made to look out or explore objects in space.
Note that Space probes are a kind of robots that work well or by remote control.
Note that they do ]take pictures and gather data and thus The description of the probe's vertical motion as it neared the moon's surface is that . The Moon's surface gravity is said to be weaker due to the fact that it is far lower in terms of mass than Earth.
Learn more about probe from
https://brainly.com/question/2323914
#SPJ1
Explain the benefits of using an error event schema during an
ETL process.
Answers
Answer:
Explanation:
almost all databases like SQL, Oracle or data warehouses use ETL (Extract, Transform and Load) procedure to extract data from multiple sources, transform them and then load into their own databases.
use of error event schema during an ETL process is
undoubtedly the best option to do the complete procedure error free
it gives you guarantee to handle all the data lapses like data duplication, missing data values, invalid values etc. etc.
thus, to minimize the time and maximize the quality it is highly recommended to use error event schema during an ETL process.
b) State two factors that may cause interference of the WiFi signal for his network
Answers
Answer:
Ping
Mbps Speed (Download or Upload)
Brainliest Please.
Tell me if im right please!!
114. Flatten Binary Tree to Linked ListGiven a binary tree, flatten it to a linked list in-place.For example, given the following tree: 1 / \ 2 5 / \ \3 4 6look like: 1 -> 2 -> 3 -> 4 -> 5 -> 6
Answers
To flatten a binary tree to a linked list in-place, we can use a recursive approach.
We start by flattening the left and right subtrees of the current node, and then we move the flattened right subtree to the right of the flattened left subtree. Finally, we set the left child of the current node to null and the right child to the flattened subtree.
Here's an implementation in Python:
```
class Solution:
def flatten(self, root: TreeNode) -> None:
"""
Do not return anything, modify root in-place instead.
"""
if not root:
return
self.flatten(root.left)
self.flatten(root.right)
if root.left:
right_subtree = root.right
root.right = root.left
root.left = None
# Find the end of the flattened left subtree
end = root.right
while end.right:
end = end.right
# Append the flattened right subtree
end.right = right_subtree
```
In the example given, the binary tree would be flattened to the linked list: 1 -> 2 -> 3 -> 4 -> 5 -> 6.
To know more about linked list visit:
https://brainly.com/question/28938650
#SPJ11
You are the administrator of a server, and you have root privileges. The it manager has asked you to install the cups package to enable printing on the server. In this lab, your task is to complete the following: use dnf to install the cups package. After the installation is complete, print the sales document in /home/wadams
Answers
To install the cups package, type dnf install cups and press Enter at the prompt.
In order to confirm the installation, press Y and then Enter.
To print the sales document, enter lpr /home/wadams/sales and press Enter.
What is a cups package?
CUPS was created in 1997 by Michael R Sweet at Easy Software Products, with the first beta release on May 14, 1999. Soon after, Till Kamppeter began packaging CUPS for Mandrake Linux and developing the Foomatic CUPS drivers, which aided in the adoption of CUPS for printing on Linux. In 2002, Apple licensed CUPS for macOS, and in February 2007, Apple bought CUPS and hired Michael to continue its development as an open source project.
Michael left Apple in December 2019 to launch Lakeside Robotics. In September 2020, he collaborated with OpenPrinting developers to fork Apple CUPS in order to continue its development. Today, Apple CUPS is the CUPS version included with macOS® and iOS®, whereas OpenPrinting CUPS is the CUPS version being developed by OpenPrinting for all operating systems.
To know more about OpenPrinting, visit: https://brainly.com/question/27962260
#SPJ4
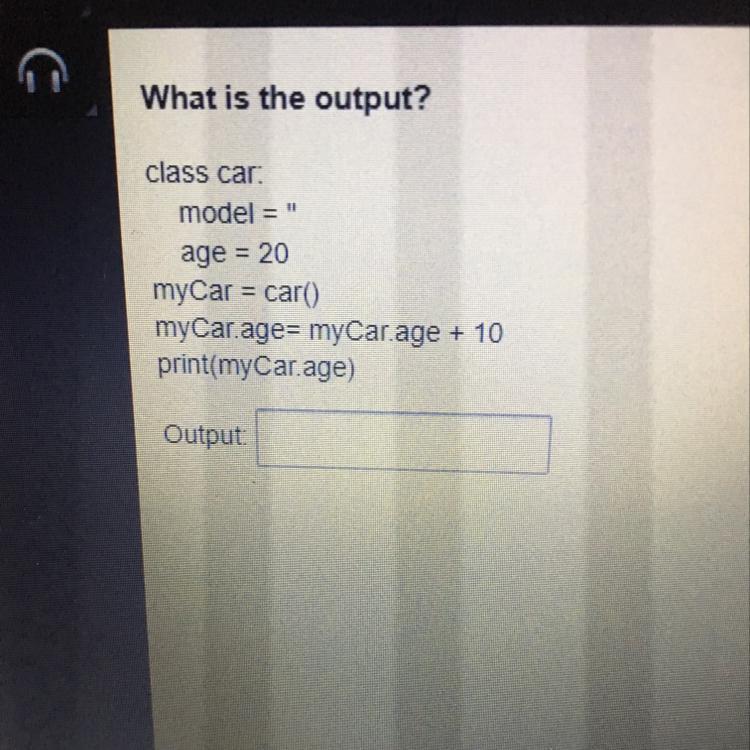
What is the output?
class car:
model = "
age = 20
myCar = car()
myCar.age= myCarage + 10
print(myCarage)
Output:
Answers
Answer:
Following are the modified code to this question:
class car:#defining a class car
model = ""#defining a class
age = 20#defining an integer variable that hold a value
myCar = car()#creating reference of class
myCar.age= myCar.age+ 10#Use reference to add value in age variable
print(myCar.age)#print age value
Output:
30
Explanation:
In the above code class care is defined, inside the car a string variable "model", and an integer variable "age" is defined that hold a value, in the next step, class reference myCar is defined, that used to add value in age variable an at the last we use print method to print age variable value.
what is main function of processing unit?
Answers
Answer:
to control the operation of all part of the computer.
hope it helps.
Answer:
to control the operations of the computer
Explanation:
hope it's help you have a great day keep smiling be happy stay safe ☺
Any aesthetic pomodoro timer apps you know? That are free* Something similar to pomofocus.io -> however I cannot download it as an app, just an extension ;(
Answers
Answer:
hi! i personally have never used a focus timer app but after looking for some, it seems like a great idea:) attached i have some apps i found!
Explanation:


How are computers located on a network
Answers
Answer:
When computers connect on the same network, it is called a local area network, or LAN.
Explanation:
The router is given the IP address for your connection to the Internet and then assigns local IP addresses to each device in your network.
Hope this can help you
carry out the binary multiplication 11011 times 1001 using only left bit shifts and addition. show your work.
Answers
The result of the binary multiplication 11011 times 1001 is 100111011.
To carry out the binary multiplication of 11011 times 1001 using only left bit shifts and addition, follow these steps:
Step 1: Write down the binary numbers, 11011 as the multiplicand and 1001 as the multiplier.
```
11011
x 1001
```
Step 2: Perform partial multiplications for each digit in the multiplier, shifting the multiplicand one position to the left for each subsequent digit:
```
11011 (1 × 11011)
00000 (0 × 11011, shifted one position to the left)
00000 (0 × 11011, shifted two positions to the left)
11011 (1 × 11011, shifted three positions to the left)
```
Step 3: Add all the partial products together:
```
11011
+00000
+00000
+11011
-------
100111011
```
You can learn more about binary multiplication at: brainly.com/question/31307857
#SPJ11