you must hold your limited learner permit (level 1) for ___________ prior to applying for a limited provisional license (level 2).
Answers
You must hold your limited learner permit (level 1) for a specific duration, usually 6 to 12 months (depending on your state's regulations), prior to applying for a limited provisional license (level 2). Make sure to check your local Department of Motor Vehicles (DMV) for the exact requirements in your area.
In some US states, there are graduated driver licensing (GDL) programs that require new drivers to pass through multiple stages before obtaining a full driver's license. These stages typically include a learner's permit and one or more levels of provisional licenses.
The duration of holding a limited learner permit (level 1) before applying for a limited provisional license (level 2) varies by state. However, in most states, new drivers must hold a limited learner permit for a certain period of time, typically 6 months to 1 year, before they can apply for a limited provisional license.
During the limited learner permit phase, new drivers are required to complete a certain number of hours of supervised driving practice, pass a driver's education course, and demonstrate safe driving skills. Once they have met the requirements and held the limited learner permit for the required time period, they can then apply for a limited provisional license.
The limited provisional license (level 2) typically allows new drivers to drive unsupervised during certain hours and under certain conditions, such as no driving at night, no passengers under a certain age, and no use of electronic devices while driving. After holding the limited provisional license for a certain period of time and meeting other requirements, such as no traffic violations or accidents, new drivers can then apply for a full driver's license.
Learn more about driving skills here:
https://brainly.com/question/30115103
#SPJ11
North Carolina, you must hold your limited learner permit (level 1) for at least 12 months prior to applying for a limited provisional license (level 2).
During this time, you will need to complete at least 60 hours of supervised driving practice, including 10 hours at night.
The limited learner permit is the first step in the graduated driver's license (GDL) system in North Carolina.
Individuals who are at least 15 years old to begin practicing driving with a licensed adult who is at least 21 years old and has held a driver's license for at least one year.
This permit allows individuals to drive only between 5 a.m. and 9 p.m. and only with the supervising adult in the front seat.
After holding the limited learner permit for at least 12 months, individuals who are at least 16 years old and have completed the required practice hours can apply for the limited provisional license (level 2).
This license allows individuals to drive unsupervised but with certain restrictions, such as a curfew between 9 p.m. and 5 a.m. and a limit of one passenger under the age of 21 who is not a member of the driver's immediate family.
It is important to note that the GDL system is designed to gradually introduce new drivers to the road and reduce their risk of crashes and injuries.
By requiring individuals to hold the limited learner permit for at least 12 months before applying for the limited provisional license, North Carolina is giving new drivers ample time to gain experience and confidence on the road before they begin driving independently.
For similar questions on Limited
https://brainly.com/question/9503055
#SPJ11
Related Questions
Describe the advantages and disadvantages of using cloud software compared to stand-alone software.
Answers
Answer:
Advantages of cloud software:
1. Cost effective: Cloud software generally has a lower upfront cost and can offer savings on maintenance and upgrade costs. Because of the shared infrastructure, cloud software providers are able to keep their costs down and pass savings to their customers.
2. Scalability: Cloud software is highly scalable and can be quickly scaled up or down depending on the needs of the user. This allows users to only pay for the resources they need and eliminates the need to purchase hardware and software that may not be used in the long term.
3. Mobility: Cloud software offers access from any device with an Internet connection. This means that users can work from anywhere and still be able to access their programs and data.
4. Increased collaboration: Cloud software allows multiple users to access, edit and share documents in real time. This increases productivity and the speed of collaboration.
Disadvantages of cloud software:
1. Security: While providers use sophisticated security measures, it is possible that hackers can gain access to data stored in the cloud.
2. Lack of control: Because you are relying on a third-party to host and manage your data, you lack direct control over the security and maintenance of your data. This can also lead to difficulties in deleting or transferring data.
3. Internet dependency: Cloud software requires an internet connection in order to access. This limits its use in places that don’t have a reliable connection or data speed.
4. Cost: Although the initial cost is usually low, the costs can add up quickly if the user needs more resources or storage.
Overall, cloud software has many advantages compared to stand-alone software. The ability to access data from anywhere, the scalability, and the cost savings enjoyed by shared infrastructure can outweigh the risks associated with lack of control and internet dependence.
I need help with this thing called Switch Conditional Statements on OnlineGDB (Using just plain Java) I need code for the file Main.java and phonecalls.txt is the file that's supposed to give the data depending on what you put in it. (also, the code needs to be added from the base code, since the base code is required along with additional code to make it work, except for the questions marks, those are just markers for some of the code that needs to be there)


Answers
To read the contents of the phonecalls.txt file, a Scanner object is first created in this code and then a File object is created for the file. After that, each line of the file is read and divided into two pieces.
What Java software can read a.txt file?You can read files line by line by using FileReader to obtain the Buffered Reader. It is not a very effective method of reading a text file in Java because FileReader does not support encoding and only uses the system default encoding.
java.io.File, java.io.FileNotFoundException, and java.util.Scanner are imported.
try: File file = new File("phonecalls.txt"); Scanner scanner = new Scanner(file); public class Main public static void main(String[] args);
(Scanner.hasNextLine()) while String[] parts = line.split(" "); String[] line = scanner.nextLine();
double call; string callType = parts[0]
Double.parseDouble(parts[1]); Duration =
switch; double callRate = 0.0 (callType) Case "local": callRate = 0.05; break; Case "domestic": if (callDuration = 10.0): callRate = 0.10; else: callRate = 0.08;
if (callDuration = 5.0) then break; case "international" if callRate is equal to 0.25, otherwise callRate is equal to 0.20, and so on
To know more about code visit:-
https://brainly.com/question/17293834
#SPJ1
The study and practice of information storage and retrieval is called
Answers
how many consecutive actions or commands can you reverse using the undo feature?
Answers
Up to 100 consecutive actions or orders can be undone by clicking the arrow next to the Undo button.
Which Word offers an undo option that allows you to reverse the most recent instruction or action?One change must be undone. Choose the Undo option. Input Ctrl + Z. Your previous action was undone. For instance, undo would make a deleted item reappear if you changed your mind and decided to keep it after all.
How many undo operations can be made?Depending on the program you're using, you may only reverse something once. Many applications only permit one to five undo operations, however some systems permit many undo operations by repeatedly performing the undo operation.
To know more about Undo visit:-
https://brainly.com/question/6413908
#SPJ4
You are designing a simple calculator program for young children to use. Right now, if they do something that the program didn’t expect, a message appears that reads, “User input deemed invalid.” What changes could you make so that the message would be more suitable for this audience?
Answers
The change you could make to make the message more suitable for this audience would be to identify a suitable message so that the children understand that they made a mistake using the program. For example: You made a mistake, try again.
What is a user input?A user input is a term that refers to the action performed by a user of a digital system or a specific program. This message has been standardized to indicate to the user that he has made a mistake in pressing buttons or in handling a program.
How to modify the message?To modify the message we must edit the base font of the program so that the message that we want to appear on the screen is different. On the other hand, we must identify a message that is simple and direct so that the children understand that they made a mistake when using the program.
What message can we put for the children?The right message for children should clearly communicate to them what has happened without discouraging them. So a suitable example of a message would be:
You've made a mistake, try again.Learn more about user input in: https://brainly.com/question/8789964
#SPJ1
Choose all items that are true about the two example of HTML shown on the right.
Example 1 will display differently than example 2 in a web browser.
They are styled differently, but will look the same in a web browser.
Example 2 is easier to analyze and repair.
The styling in example 2 is required by modern web browsers.
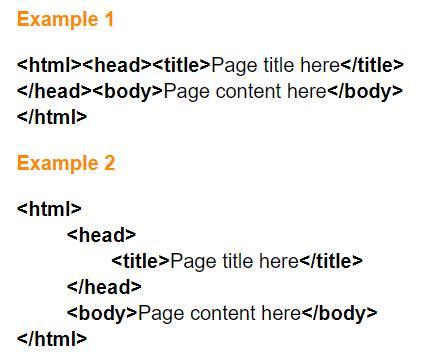
Answers
Answer:
2
Explanation:
Answer:
B and C
Explanation:
What does it mean to get optional from school? And is it like to have optional for school?
Answers
Answer:
"Getting optional" from the school typically means that a student can leave school early or not attend classes for a certain period. This can happen for various reasons, such as medical issues, personal circumstances, or disciplinary actions.
"Having optional" for school means that students have the choice to attend or not attend certain classes or activities. This is often offered to students who have already completed the required coursework or are excelling in their studies and would like to take more advanced or specialized classes.
Explanation:
What is the result of the following program? print(“10 + 2”) print(3 + 5) 12 8 10 + 2 3 + 5 12 3 + 5 10 + 2 8
Answers
Answer:
print(“10 + 2”) Will output "10 + 2" without the quotation marks. This is because the text to print is encapsulated in quotation marks, indicating a "string literal." This means, to put it simply, it will always print what you put there even if it's a math equation.
1. Word Module 2 SAM Textbook Project
2. Word Module 2 SAM Training
3. Word Module 2 SAM End of Module Project 1
4. Word Module 2 SAM End of Module Project 2
5. Word Module 2 SAM Project A
6. Word Module 2 SAM Project B
Answers
The raise To Power Module of the program's calling error can be found in the real and integer values of the argument variables.
String should be spelled Sting. The set Double Module instead of returning an integer, does such. Access to local variables declared in the Main module is restricted to that module only. The raise To Power Module of the program's calling argument variables' real and integer values can be used to pinpoint the issue. Although the arguments for the raise To Power Module (Real value and Integer power) have been defined. The integer power is represented as "1.5," and the real value is supplied as "2." A real number, on the other hand, is a number with a fractional part. thus, a number without a fraction is considered an integer. 1.5 is a real number, whereas 2 is an integer. The parameters' contents when invoking raise To Power.
Learn more about The raise To Power Module here:
https://brainly.com/question/14866595
#SPJ4
How to convert values in Delphi RAD STUDIOS
Answers
- To convert a string to an integer, you can use the StrToInt function. For example:
```
var
myString: string;
myInt: Integer;
begin
myString := '123';
myInt := StrToInt(myString);
// myInt now contains the integer value 123
end;
```
- To convert an integer to a string, you can use the IntToStr function. For example:
```
var
myInt: Integer;
myString: string;
begin
myInt := 123;
myString := IntToStr(myInt);
// myString now contains the string value '123'
end;
```
- To convert a string to a floating-point number, you can use the StrToFloat function. For example:
```
var
myString: string;
myFloat: Double;
begin
myString := '3.14';
myFloat := StrToFloat(myString);
// myFloat now contains the floating-point value 3.14
end;
```
- To convert a floating-point number to a string, you can use the FloatToStr function. For example:
```
var
myFloat: Double;
myString: string;
begin
myFloat := 3.14;
myString := FloatToStr(myFloat);
// myString now contains the string value '3.14'
end;
```
These are just a few examples of the many conversion functions and procedures available in Delphi RAD Studio. The specific function or procedure you need will depend on the type of data you're working with and the type of conversion you need to perform.
( I hope this was what you asked for! )
if you are creating a query using fields from two related tables, the join line identifies which fields establish a relationship between the tables. true false
Answers
It is true that when you are creating a query using fields from two related tables, the join line identifies which fields establish a relationship between the tables.
How to join table in database ?In order to maximize the database, database expert commonly separate the data on different table which is important to increase the program speed in reading database on large scale user. If the user want a data from more than one table, programmer will use join command to make the relation between the tables and they will done it as follow:
Identifies which field is unique where commonly is a primary key fieldMake the field that will contain the same value with the chosen field in process 1 at other table.Join the table by that both field to make a relationship the two. This action will be repeated if there is more than two table to join.Learn more about join table here
https://brainly.com/question/14094740
#SPJ4
If your query is 'michael kors women's handbags' and the Product Ad shows 'Womens Burlington handbags', What should be your rating? A) Bad B) Fair C) Good D) Excellent
Answers
How can i print an art triangle made up of asterisks using only one line of code. Using string concatenation (multiplication and addition and maybe parenthesis)?
Answers
#include <iostream>
int main(int argc, char* argv[]) {
//One line
std::cout << "\t\t*\t\t\n\t\t\b* *\t\t\b\n\t\t\b\b* *\t\t\b\b\n\t\t\b\b\b* *\t\t\b\b\b\n\t\t\b\b\b\b* *\t\t\b\b\b\b\n\t\t\b\b\b\b\b* * * * * *\t\t\b\b\b\b\b\n";
return 0;
}
Yes, it is possible with a single line and using escape sequences, but it is tedious and not recommended. Instead, you can use loops to write more readable and easy on the eyes code. We only used the cout method (C++). Good luck!

a server is configured for dynamic nat and has used all public ip addresses in the pool. what will the router do when another device wants to reach the outside network?
Answers
Port numbers are used by NAT overloading to identify each local host. Because of this, the method is also known as port address translation (PAT).
Therefore, the Standard Public IP address assigned to the NAT gateway will remain dedicated to it and cannot be used by another device unless you unassign or delete it. To convert a large number of unregistered IP addresses into a smaller number of registered ones, use dynamic NAT. With the aid of dynamic NAT, you are able to use a small number of registered addresses to connect to numerous hosts on the open Internet. After a certain amount of inactivity, the entry times out, and new translations can be made using the global IP address.
Learn more about addresses here-
https://brainly.com/question/16011753
#SPJ4
5 evaluation criteria
Answers
Answer:
relevance, efficiency, effectiveness, impact and sustainability.
Non- intentional errors caused by computer users such as erase or overwrite data or through viruses passed from secondary storage devices or the internet
Answers
Answer: I think yes
Explanation: because of national computer errors I do think that secondary storage devices should be needed.
I need help with 9.1

Answers
Answer:
x=circumfrence of circle im 29 boi
Explanation:
How can you tell that punch cards generally did not use the binary system to store data?
Answers
Punch cards generally did not use the binary system because they used a combination of holes punched in specific positions to represent data, not binary digits.
Punch cards generally did not use the binary system to store data because they relied on a combination of holes punched in specific positions on the card to represent different characters or values. The presence or absence of holes in predefined locations was used to encode information. In the binary system, data is represented using only two symbols or states, typically 0 and 1. However, punch cards had multiple possible hole positions, allowing for a larger number of potential combinations and characters to be represented. This suggests that punch cards used a different encoding scheme, often based on character sets or specific codes, rather than a binary representation.
Learn more about binary system here:
https://brainly.com/question/28222242
#SPJ11
T/F system restore points can only be created by windows automatically on a regular schedule.
Answers
It's true windows can build genuine system restore points automatically and on a regular basis.
What is Windows?
Windows is an operating system developed by Microsoft that is designed to run on desktop and laptop computers. It provides a graphical user interface (GUI) and supports multitasking. Windows allows users to interact with a computer and its programs by using graphical symbols and images instead of text-based commands. Windows comes pre-installed on most PCs, however, users can also purchase and install Windows on their own. Windows also provides a range of features such as the ability to install and uninstall programs, access the internet, and customize the settings.
To know more about Windows
https://brainly.com/question/27764853
#SPJ1
____ are arrays that have more than one dimension.
Answers
Multidimensional arrays are arrays that have more than one dimension.
What are Multidimensional arraysAn array is a data structure that stores a collection of elements of the same type. Typically, arrays have a single dimension, meaning they consist of a linear sequence of elements. For example, a one-dimensional array can be thought of as a list or a row of values.
On the other hand, a multidimensional array extends the concept of arrays to have more than one dimension. It organizes elements in a tabular or matrix-like structure, where each element is accessed using multiple indices. The dimensions of a multidimensional array represent the number of indices required to access an element.
Read mroeo nMultidimensional arrays here brainly.com/question/23459333
#SPJ4
What is a layer, in the context of this lesson?
the ethernet word for a packet
a device for remembering something
a logical unit of a system
a computer’s most basic program
Answers
Answer:
A logical unit of a system.
Explanation:
i'm thinking your are talking about system layers such as the ISO? Layers help identify the order of how the whole system works.
A logical unit of a system is a layer, was the based on the lesson in the main motive. Thus, option (c) is correct.
What is layer?The layer refers to the layering method of breaking up the delivery of messages into discrete components and activities. Communication programs are frequently multi-tiered. Layers are useful because they allow you to add components to an image and work on them one at a time without permanently affecting the original image.
A logical unit is a device or software program that allows an end user (an application program, a terminal user, or an input/output mechanism) to connect to a network. A logical unit number is a one-of-a-kind identifier for a single or group of physical or virtual storage devices that execute.
As a result, the logical unit of a system is a layer, was the based on the lesson in the main motive. Therefore, option (c) is correct.
Learn more about on layer, here:
https://brainly.com/question/13490759
#SPJ5
which of the following is a true statement? network topology has no effect on the network performance. ethernet is a better lan than token ring network. a switch and a router provide the same functions. fiber distributed data interface (fddi) network is a ring-based token network. none of the above statements is true.
Answers
The true statement is: "None of the above statements is true."
Network topology can have a significant impact on network performance, depending on factors such as network size, traffic patterns, and fault tolerance requirements. Therefore, it is not true that network topology has no effect on network performance.
Ethernet and Token Ring are both LAN technologies with their own advantages and disadvantages. It is not accurate to say that one is universally better than the other.
A switch and a router perform different functions in a network. A switch forwards data at the data link layer (Layer 2), while a router forwards data at the network layer (Layer 3). While there may be some overlap in their functions, it is not true that a switch and a router provide the same functions.
FDDI is a ring-based network technology that uses tokens to control access to the network. However, it is not accurate to say that FDDI is a token ring network, as this term usually refers to a specific type of LAN technology.
Therefore, none of the given statements is true.
Learn more about topology link:
https://brainly.com/question/10536701
#SPJ11
TRUE/FALSE. After a suspect system is identified, a best practice is to leave the computer powered on until you can copy volatile data, such as the contents of RAM.
Answers
True, in order to properly collect and preserve volatile data, it is recommended to leave the computer powered on until the data can be copied.
This is typically done by a digital forensic examiner and can help to uncover important evidence in a criminal investigation. It is important to note that volatile data can be lost if the computer is powered off or rebooted, so it is crucial to act quickly and follow proper procedures.
Introduce the concept of digital forensics and the importance of preserving evidence. The second paragraph would discuss volatile data, emphasizing the need to maintain the system's power to preserve crucial information. Lastly, the third paragraph would elaborate on the best practices for handling suspect systems, including proper documentation and chain of custody.
To know more about computer visit:-
https://brainly.com/question/14588541
#SPJ11
which command rebuilds the boot sector for the active system partition?
Answers
The command that rebuilds the boot sector for the active system partition is "bootrec /fixboot". This command is useful in cases where the boot sector has been corrupted or damaged, preventing the computer from booting up properly.In order to use the "bootrec /fixboot" command,
follow these steps:1. Insert the Windows installation media and boot from it.2. Choose the language and other preferences, and click on the "Next" button.3. Click on the "Repair your computer" option at the bottom-left corner of the screen.4. Select the operating system you want to repair, and click on the "Next" button.5. Choose the "Command Prompt" option from the list of repair options.6. Type in the command "bootrec /fixboot" and press the Enter key.7. Wait for the command to complete, and then restart the computer. This should fix any issues with the boot sector and allow the computer to boot up normally again.
Note that the "bootrec /fixboot" command should only be used as a last resort, after trying other troubleshooting steps such as running a virus scan or repairing the Master Boot Record (MBR). It should also be used with caution, as an incorrect command or typo could cause further damage to the system.
To know more about command visit:
https://brainly.com/question/32329589
#SPJ11
The lifetime of a new 6S hard-drive follows a Uniform
distribution over the range of [1.5, 3.0 years]. A 6S hard-drive
has been used for 2 years and is still working. What is the
probability that it i
Answers
The given hard-drive has been used for 2 years and is still working. We are to find the probability that it is still working after 2 years. Let A denote the event that the hard-drive lasts beyond 2 years. Then we can write the probability of A as follows:P(A) = P(the lifetime of the hard-drive exceeds 2 years).By definition of Uniform distribution, the probability density function of the lifetime of the hard-drive is given by:
f(x) = 1/(b - a) if a ≤ x ≤ b; 0 otherwise.where a = 1.5 years and b = 3.0 years are the minimum and maximum possible lifetimes of the hard-drive, respectively. Since the probability density function is uniform, the probability of the hard-lifetime of a new 6S hard-drive follows a Uniform distribution over the range of [1.5, 3.0 years]. We are to find the probability that a 6S hard-drive, which has been used for 2 years and is still working, will continue to work beyond 2 years.Let X denote the lifetime of the hard-drive in years.
Then X follows the Uniform distribution with a = 1.5 and b = 3.0. Thus, the probability density function of X is given by:f(x) = 1/(b - a) if a ≤ x ≤ b; 0 otherwise.Substituting the given values, we get:f(x) = 1/(3.0 - 1.5) = 1/1.5 if 1.5 ≤ x ≤ 3.0; 0 the integral is taken over the interval [2, 3] (since we want to find the probability that the hard-drive lasts beyond 2 years). Hence,P(A) = ∫f(x) dx = ∫1/1.5 dx = x/1.5 between the limits x = 2 and x = 3= [3/1.5] - [2/1.5] = 2/3Thus, the probability that a 6S hard-drive, which has been used for 2 years and is still working, will continue to work beyond 2 years is 2/3.
To know more about Uniform distribution visit:
brainly.com/question/13941002
#SPJ11
How do you identify quality resources on the Internet? There are 4 correct answers. Select each answer.
Question 3 options:
Check the information for accuracy by looking for references or searching for the same information with another source.
Determine if the information seems to balance pros and cons. If it's difficult to tell the difference between facts and opinions, the website may not be research based.
Determine who wrote the information. Anyone can post to the internet.
Find out when the information was published or edited last. The facts could be out of date.
When you conduct an Internet search, observe where the website is in the list of search results. The websites listed first are the most reliable resources.
Answers
Answer:
Every option except option E.) is true. I hope this helps! :)
Miriam Is a network administrator. A few employees want to access sensitive Information stored on a backup device. She wants to give access
rights these employees. Which option will she use?
ОА.
remote desktop
ОВ.
monitoring service
Oc.
user accounts
OD.
print service
OE.
directory service

Answers
Answer:
C. user accounts
Explanation:
An access control can be defined as a security technique use for determining whether an individual has the minimum requirements or credentials to access or view resources on a computer by ensuring that they are who they claim to be.
Simply stated, access control is the process of verifying the identity of an individual or electronic device. Authentication work based on the principle (framework) of matching an incoming request from a user or electronic device to a set of uniquely defined credentials.
Basically, authentication and authorization is used in access control, to ensure a user is truly who he or she claims to be, as well as confirm that an electronic device is valid through the process of verification
Hence, an access control list primarily is composed of a set of permissions and operations associated with a NTFS file such as full control, read only, write, read and execute and modify.
Generally, access control list are defined for specific user accounts and may either be an administrator, standard user or guest account.
In this scenario, Miriam a network administrator wants to give access rights to employees who are interested in accessing sensitive Information stored on a backup device. Thus, the option Miriam should use is user account.
Answer:
user accounts
Explanation:
Complete the expression so that user_points is assigned with 0 if user_items is greater than 25 (second branch). Otherwise, user_points is assigned with 10 (first branch).
user_level = int(input()) # Program will be tested with values: 15, 20, 25, 30, 35.
if ''' Your code goes here ''':
user_points = 10
else:
user_points = 0
print(user_points)
What is the answer for Python please
Answers
The required expression that completes the code in Python is
“if (user_level<= 25):”
The complete code is given below that assigns 10 to “user_points” in case “user_level” is less than and equal to 25, and assigns “user_points” 10 if the “user_level” is greater than 25.
user_level = int(input("Enter some values from 15,20,25,30,35 : " ))
# requires to input some value from 15, 20, 25, 30, 35
if (user_level<= 25):
user_points = 10
''' checks whether “user_level” is less than and equal to 25. If it is evaluated to true then control goes to its body where 10 is assigned to “user_points '''
else:
user_points = 0
''' in case “if conditions” is evaluated to false then else runs where 0 is assigned to “user_points” '''
print(user_points)
# prints user_points
You can learn more about if-else in python at
https://brainly.com/question/28032696
#SPJ4
Which of the following is not a type of external data? a) Demographics b) Household c) Socioeconomic d) Promotion History Q8 Does a data warehouse? a) Improve data access b) Slow data access c) Makes
Answers
The answer to the first question is "d) Promotion History" as it is not typically categorized as a type of external data. Regarding the second question, a data warehouse is designed to improve data access rather than slow it down
External data refers to information that is obtained from sources outside of an organization. It provides valuable insights into external factors that can influence business operations and decision-making. The options provided in the question are all types of external data, except for "d) Promotion History." While demographic data, household data, and socioeconomic data are commonly used to understand consumer behavior, market trends, and target audience characteristics, promotion history typically falls under internal data. Promotion history refers to the records and data related to past promotional activities, campaigns, and strategies employed by the organization itself.
Moving on to the second question, a data warehouse is a centralized repository that is specifically designed to improve data access. It is a large-scale storage system that integrates data from various sources, such as transactional databases, spreadsheets, and external data feeds. The purpose of a data warehouse is to provide a structured and optimized environment for data storage, organization, and retrieval. By consolidating data into a single location, a data warehouse facilitates efficient access to information for analysis, reporting, and decision-making. It eliminates the need to query multiple systems and allows for faster and more streamlined data retrieval and analysis processes. Therefore, the correct answer to the question is "a) Improve data access."
Learn more about external data here : brainly.com/question/32220630
#SPJ11
codes such as those offered by the spj, prsa, and rtnda are legally enforceable.
Answers
The codes of ethics provided by professional organizations such as the Society of Professional Journalists (SPJ), Public Relations Society of America (PRSA), and Radio Television Digital News Association (RTDNA) are not legally enforceable. These codes are voluntary guidelines that members of these organizations agree to abide by.
However, violating these codes could result in disciplinary action by the organization, including revocation of membership.The codes of ethics provided by these organizations serve as a standard for ethical conduct within their respective professions. They outline principles and best practices that aim to promote accuracy, fairness, and impartiality in journalism and public relations. These codes are intended to guide professionals in making ethical decisions and maintaining the trust of their audience and clients.While not legally enforceable, these codes may have some impact in legal proceedings. For example, if a journalist is accused of defamation, they may argue that they were abiding by the SPJ Code of Ethics in their reporting. This could potentially strengthen their defense in court.In summary, the codes of ethics provided by professional organizations such as SPJ, PRSA, and RTDNA are not legally enforceable. However, they serve as voluntary guidelines for ethical conduct and may have some influence in legal proceedings.
Learn more about codes here
https://brainly.com/question/29330362
#SPJ11