You have just connected a new USB device to your Windows system. You used the installation disc that came with the device to install the drivers needed to support the device. After installation, the system frequently crashes when you try to access the new device.
What should you do?
Answers
If the system frequently crashes when trying to access a newly installed USB device, you can try the following steps to troubleshoot the issue:
1) Uninstall and reinstall drivers: First, try uninstalling the drivers for the USB device and then reinstall them. Make sure to use the latest drivers provided by the manufacturer, as the ones on the installation disc may be outdated.
2) Update system drivers: Check for any pending driver updates for your Windows system. Sometimes outdated or incompatible drivers can cause issues with newly connected devices. Visit the manufacturer's website or use Windows Update to ensure your system has the latest drivers installed.
3) Test on a different USB port: Connect the USB device to a different USB port on your system. Sometimes, certain ports may have compatibility issues or hardware problems. Testing on a different port can help determine if the issue is port-specific.
4) Use a different USB cable: The USB cable provided with the device may be faulty or not compatible. Try using a different USB cable to connect the device and see if the crashes persist.
5) Check for conflicts with other devices: Ensure that there are no conflicts or compatibility issues with other connected devices. Disconnect other USB devices temporarily and see if the crashes still occur.
6) Check for firmware updates: Visit the manufacturer's website for the USB device and check if there are any firmware updates available. Updating the device's firmware can sometimes resolve compatibility issues.
7) Perform system updates: Make sure your Windows system is up to date with the latest updates and patches. Updates often include bug fixes and improvements that can help resolve compatibility issues.
8) Contact device manufacturer support: If the issue persists, it is recommended to reach out to the manufacturer's support team for further assistance. They may be able to provide specific troubleshooting steps or offer a solution for the problem.
Remember to back up your important data before attempting any major changes to your system.
Learn more about USB device here
https://brainly.com/question/31564724
#SPJ11
Related Questions
in a basic program with 3 IF statements, there will always be _________ END IIF's.
a)2
b)3
c)4
Answers
Answer:
c)4
Explanation:
Hope it could helps you
power steering belts should be checked for all of the following EXCEPT
Answers
You did not list the options.
1. At each step of its operation, the input to a Central Processing Unit is
a program.
an instruction.
main memory.
a control unit.
2. A byte in memory is identified by a unique number called its
3. In modern computer systems, a byte consists of ______________bits.
4. Which of the following is not true?
An algorithm allows ambiguity.
An algorithm, when carried out, must eventually stop.
An algorithm, can be carried out by a human being.
5. Replace the underlines with the words in parentheses that follow: The ____ solves the ____ of a
____ by expressing an ____ in a ____ to make a ____ that can run on a ____. ( algorithm,
computer, problems, program, programmer, programming language, user ) NOTE: do not just
put in the replacement words, put in the WHOLE sentence with the underlines replaced.
6. Which statement is NOT true:
Machine languages can be used to express algorithms.
Machine languages can be used to write programs that can run on any machine.
Machine language consists of zeros and ones.
Machine language is produced by compilers.
7. A compiler
maintains a collection of programs
tests a program's logic
translates source code into executable code
translates executable code to machine code
8. An error in a program that involves a violation of language rules will be detected at
_____________time.
9. Division by zero when the program is executing is an example of a ____________error.
10. The purpose of testing a program with different combinations of data is to expose run-time and
____________errors.
Answers
1. At each step of its operation, the input to a Central Processing Unit is an instruction.2. A byte in memory is identified by a unique number called its address.
3. In modern computer systems, a byte consists of eight bits.4. An algorithm allows ambiguity is the answer which is not true.5. The programmer solves the problems of a user by expressing an algorithm in a programming language to make a program that can run on a computer.6. Machine languages can be used to express algorithms is the statement which is NOT true.7. A compiler translates source code into executable code.8. An error in a program that involves a violation of language rules will be detected at compile time.9. Division by zero when the program is executing is an example of a run-time error.10. The purpose of testing a program with different combinations of data is to expose run-time and logic errors.
A Central Processing Unit (CPU) is a microprocessor unit responsible for executing the instructions of a computer program. An instruction is the input to the Central Processing Unit at each stage of its operation.A byte in memory is recognized by its address, which is a unique number. In modern computer systems, a byte is composed of eight bits.The statement which is not true is that an algorithm allows ambiguity. Ambiguity should be avoided in the development of algorithms.
The programmer solves the problems of a user by expressing an algorithm in a programming language to make a program that can run on a computer. The programmer accomplishes this by converting the algorithm to a sequence of computer instructions or code written in a specific programming language.A compiler translates source code into executable code, while an interpreter translates executable code to machine code.
Errors involving a violation of language rules will be discovered at compile time. Division by zero during program execution is an example of a runtime error. The purpose of testing a program with different data combinations is to expose runtime and logic errors.
To learn more about central processing unit :
https://brainly.com/question/21477287
#SPJ11
CHOOSE THE CORRECT CONTINUOUS TENSES( PRESENT CONTINUOUS,PAST CONTINUOUS AND FUTURE CONTINUOUS) : 1. I saw a snake while I ____________________ in the forest. am walking was walking will be walking will walk
Answers
Answer:
Explanation:
joe biden>
A credit card company receives numerous phone calls throughout the day from customers reporting fraud and billing disputes. Most of these callers are put "on hold" until a company operator is free to help them. The company has determined that the length of time a caller is on hold is normally distributed with a mean of 2.5 minutes and a standard deviation 0.5 minutes. If 1.5% of the callers are put on hold for longer than x minutes, what is the value of x? Use Excel, and round your answer to two decimal places.
Answers
Answer:
3.59 minutes
Explanation:
We solve this question using z score formula
Using Excel
Z-SCORE= (DataPoint-AVERAGE(DataSet))/STDEV(DataSet)
IN EXCEL,
AVERAGE, an excel function that calculates the Average of data set
STDEV.S: calculates the standard deviation while treating the data as a ‘sample’ of a population.
STDEV.P: This function calculates the standard deviation while treating the data as the entire population.
Z score formula = x - μ/σ
x = ?? μ = 2.5 minutes σ = 0.5 minutes
We are asked : If 1.5% of the callers are put on hold for longer than x minutes, what is the value of x?
Hence, Longer than = Greater than =
100 - 1.5%
= 100 - 0.015
= 0.985 ( 98.5%)
Using Excel we calculate = z score for 98.5 percentile
= 2.1701
Z score = x - μ/σ
2.1701 = x - 2.5/0.5
2.1701 × 0.5 = x - 2.5
1.08505 = x - 2.5
x = 1.08505 + 2.5
x = 3.58505
Approximately to 2 decimal places = 3.59 minutes
Therefore, 1.5% of the callers are put on hold for longer than 3.59 minutes.
Information that is sent across a network is divided into chunks called __________.
Answers
Answer:
Packets
Explanation:
the value that decides whether something falls into one category or another is called a ____
Answers
Dichotomous variables
Explanation:
A variable is any characteristics, number, or quantity that can be measured or counted. A variable may also be called a data item.
The value that decides whether something falls into one category or another is called a dichotomous variable.
What is dichotomous variable?A discrete dichotomous variable or a continuous dichotomous variable are additional terms for dichotomous variables.
Regular discrete variables and continuous variables are fairly comparable to the concept. When two dichotomous variables are continuous, there are options in between them, whereas when they are discrete, there is nothing between them.
The variable "Passing or Failing an Exam" is continuous and dichotomous. A test grade can be anywhere between 0% and 100%, with every conceivable percentage in between. You could pass with a 74%. 69% could result in failure.
Therefore, The value that decides whether something falls into one category or another is called a dichotomous variable.
To learn more about dichotomous variable, refer to the link:
https://brainly.com/question/22098213
#SPJ2
Como tomar captura en laptop?
Answers
Answer: En algunas laptops o PCs basta con presionar el botón Print Screen o Impr Pant, ubicado usualmente en la parte superior derecha del teclado. Se creará la carpeta de "capturas" automáticamente en Imágenes en PNG o JPG de tu ordenador. También puedes pulsar la tecla Windows junto a la tecla Impr Pant a la vez.
Explanation:
Answer:
para windows 10, encuentras el botón de windows, shift y s
Explanation:
Which type of modulation is used when human voice is moculated directly on a carrier wave? Selected Answer: b. Digital modulation
Answers
When human voice is directly modulated onto a carrier wave, analog modulation is used. (Option a)
Analog modulation is a method of encoding information, such as voice or music, onto a continuous carrier wave by varying its amplitude, frequency, or phase in proportion to the input signal.
In the case of human voice modulation, the variations in air pressure caused by the sound waves of the voice are converted into electrical signals, which are then used to modulate the carrier wave. This modulation process preserves the analog characteristics of the voice signal, including its continuous nature and the infinite range of values it can take.
Analog modulation is commonly used in traditional analog communication systems, such as amplitude modulation (AM) or frequency modulation (FM), where the modulated carrier wave can be demodulated to retrieve the original voice signal accurately.
Therefore, when human voice is directly modulated onto a carrier wave, it is done using analog modulation techniques.
To learn more about analog click here
brainly.com/question/12948399
#SPJ11
Complete Question
Which type of modulation is used when human voice is moculated directly on a carrier wave? a. analog b. digital c. diffused d. directed
At a family reunion, your cousin takes a picture of both of you with her phone, orders a print of it, and mails it to you with a note apologizing for how weird it looks. You would use the word “bitmappy” instead of “weird” to describe the picture. Describe a situation that could have led to this problem. If you wanted to find information online that you could send to your cousin about how to avoid this problem, what are two or three keywords that you could use in your search?
Why is “less is more” such an important design principle, and why do so many people seem to want to violate this rule?
Answers
A bitmap is an image file format that can be used to create and store computer graphics. Weird means something strange or unusual.
What is the meaning of the phrase " less is more"?Sometimes keeping things simple is preferable to making them complex or advanced. Simplicity is better than extensive adornment. He should not use a word such as 'weird' and 'bitmap' in the search.
The idiom is used to convey the idea that sometimes having less of something—a lesser amount of it—can be preferable to having more of it. That a straightforward strategy frequently outperforms a complex one.
Therefore, A bitmap is an image file format that can be used to create and store computer graphics. Weird means something strange or unusual.
To learn more about, less is more, refer to the link:
https://brainly.com/question/20556896
#SPJ1
Project stem assignment 7 calendar, I’m so confused and need help please

Answers
The program based on the information will be written below.
How to write the codeThe program will be:
import datetime
# function takes the year as a parameter and returns a 1 if a year is a leap year and 0 if it is not
def leap_year(year):
if year % 4 == 0:
if year % 100 == 0 and year % 400 != 0:
return 0
else:
return 1
else:
return 0
# function accept the date as parameters and return how many days are in the given month
def number_of_days(date):
if date.month in [1, 3, 5, 7, 8, 10, 12]:
return 31
elif date.month in [4, 6, 9, 11]:
return 30
elif date.month == 2:
if leap_year(date.year) == 1:
return 29
else:
return 28
# function accept the date as parameters and calculate the number of days left in the year
def days_left(date):
mon = date.month
days = 0
while mon <= 12:
if mon == date.month:
days = days + number_of_days(datetime.date(date.year, mon, 1)) - date.day
else:
days = days + number_of_days(datetime.date(date.year, mon, 1))
# next month
mon += 1
return days
# ask the user to enter a day, month and year
print('Please enter a date')
day = int(input('Day:'))
mon = int(input('Month:'))
year = int(input('Year:'))
# create data variable
date = datetime.date(year, mon, day)
choise = '0'
while choise != '3':
while True:
# display menu
print('Menu:')
print('1) Calculate the number of days in the given month.')
print('2) Calculate the number of days left in the given year.')
print('3) Exit.')
# get the user choise
choise = input('>')
if choise == '1':
print('Number of days in the given month is', number_of_days(date))
elif choise == '2':
print('Number of days left in the given year is', days_left(date))
elif choise == '3':
break;
else:
print('Invalid input')
Learn more about program on:
https://brainly.com/question/26642771
#SPJ1
Discuss two business information systems that are used in two different sectors in a modern economy.
Answers
Explanation:
Two business information systems that are used in two different sectors in a modern economy are:
Transaction Processing System (TPS):
The Transaction Processing System (TPS) is a type of data system for capturing, storing, updating and recovering a company's data operations. Transaction systems often try to provide consistent response times to requests even if this is not as important as in real-time systems.
Management Information System (MIS)
MIS is the study of persons, technological systems and associations between them. Management Information Systems (MIS) Professionals at MIS allow businesses to profit maximally from staff, facilities and business process expenditure. MIS is a field of people with a focus on technological support.
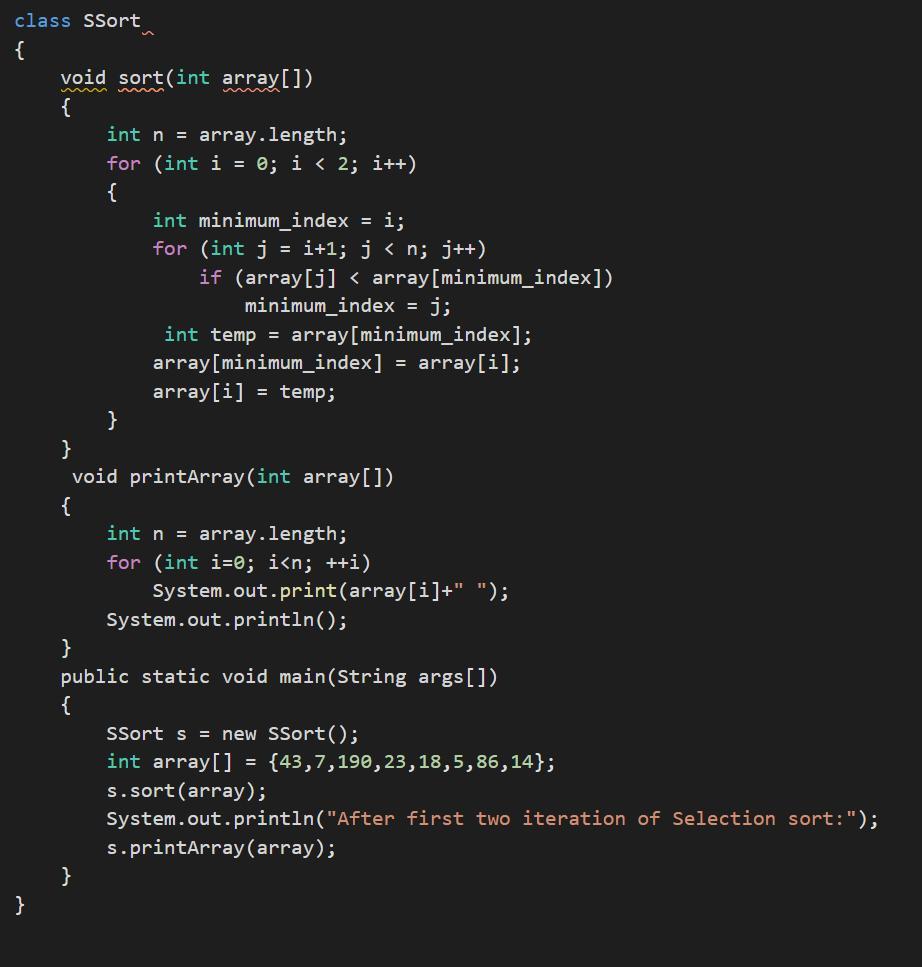
Show the contents of the array {43, 7, 190,23,18, 5,86,14} (sort in ascending order) after the first two iterations of Selection Sort. How many comparisons would be needed to sort an array containing 10 elements using Bubble sort in the worst case
Answers
Using the knowledge in computational language in JAVA it is possible to write a code that organizes the values in larger and smaller in arguments.
Writing the code in JAVA we have:class SSort
{
void sort(int array[])
{
int n = array.length;
for (int i = 0; i < 2; i++)
{
int minimum_index = i;
for (int j = i+1; j < n; j++)
if (array[j] < array[minimum_index])
minimum_index = j;
int temp = array[minimum_index];
array[minimum_index] = array[i];
array[i] = temp;
}
}
void printArray(int array[])
{
int n = array.length;
for (int i=0; i<n; ++i)
System.out.print(array[i]+" ");
System.out.println();
}
public static void main(String args[])
{
SSort s = new SSort();
int array[] = {43,7,190,23,18,5,86,14};
s.sort(array);
System.out.println("After first two iteration of Selection sort:");
s.printArray(array);
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

Crack the secret message: Crrp, Crrp, Crrp Zh’uh jrlqj wr wkh prrq. Li brx zdqw wr wdnh d wuls, Folpe derdug pb urfnhw vkls. (hint: the original letters were shifted,for example if it is shifted by 1 that means Z becomes A , A becomes B, etc. You need to know the number of shifts)
Answers
Answer:
Zoom, Zoom, Zoom We’re going to the moon. If you want to take a trip, Climb aboard my rocket ship.
Explanation:
I got it. This is a caesar cipher with 3 shifts.
Help to draw in turtle. Python

Answers
Answer:
a basic piece of code:
from turtle import *
color('red', 'yellow')
begin_fill()
while True:
forward(200)
left(170)
if abs(pos()) < 1:
break
end_fill()
done()
Explanation:
What its doing is The TurtleScreen class defines graphics windows as a playground for the drawing turtles. Its constructor needs a tkinter.Canvas or a ScrolledCanvas as argument. It should be used when turtle is used as part of some application.
The function Screen() returns a singleton object of a TurtleScreen subclass. This function should be used when turtle is used as a standalone tool for doing graphics. As a singleton object, inheriting from its class is not possible.
All methods of TurtleScreen/Screen also exist as functions, i.e. as part of the procedure-oriented interface.
RawTurtle (alias: RawPen) defines Turtle objects which draw on a TurtleScreen. Its constructor needs a Canvas, ScrolledCanvas or TurtleScreen as argument, so the RawTurtle objects know where to draw.
Derived from RawTurtle is the subclass Turtle (alias: Pen), which draws on “the” Screen instance which is automatically created, if not already present.
All methods of RawTurtle/Turtle also exist as functions, i.e. part of the procedure-oriented interface.
What would we store the value of pi in?
A.) A variable
B.) Constant
IN PROGRAMMING
Answers
The value of pi can be saved in OPTION A.) A variable.
Can pi be stored in a variable?PI is known to be a constant, and one cannot set its value, It is said to be the final variable, meaning that you are not able to alter its value.
The computer system is one that is known to have different methods of programming and these methods of use different variables in their coding process.
Java saves the value of pi as a constant, and in regards to programming purposes, this is said to be enough.
Hence, The value of pi can be saved in OPTION A.) A variable.
Learn more about pi from
https://brainly.com/question/18270698
#SPJ1
What are some restrictions that should apply to sensitive and confidential data? check all that apply.
Answers
Some special protocol should be applied to sensitive and confidential data.
While dealing with sensitive and confidential data, some special protocols must be followed to ensure its safety. The data should be managed efficiently which requires diligent organization. Encrypted media devices must always be used for storage and as a further step the data itself can be encrypted as well. The data should have restricted access both by personnel and location. It should be backed up in a safe location.
You need to apply some special protocol or restriction to sensitive and confidential data in a way that:
Data must be stored on encyrpted media online that prevents cyber secuity issues. Data should always be protect from unauthorized access. Ensure and implement safegauards against data encryption and decryption from unauthorized access.The data should always be accessed with care, must never be shared with an unauthorized third party and should have a strong passcode. End- to – end encryption should be used for online transfers. Access to the data must only be available on-site and should be monitored and documented at all times.
Failure to properly safeguard sensitive and confidential data is a breach of trust which not only affects departments or projects integrity but also opens individuals and/or organizations up to legal liabilities.
You can learn more about confidential data at
https://brainly.com/question/27208943
#SPJ4
Ssrs what is the most optimal tool to use to organize reports in the report manager?
Answers
The most optimal tool to use for organizing reports in the SSRS (SQL Server Reporting Services) Report Manager is the "Folder" feature.
On the homepage, locate the "New Folder" button and click on it.Enter a name for the folder and click on "OK" to create it. Once the folder is created, you can drag and drop reports into it for better organization.
. To move a report to a specific folder, simply click and hold the report, then drag it into the desired folder.You can create subfolders within folders to further categorize your reports.To access a report within a folder, navigate to the folder and click on the report's name.In summary, using folders in the Report Manager allows you to effectively organize your reports for easy access and management.
To know more about use visit:
https://brainly.com/question/32193341
#SPJ11
CORRECT ANSWER WILL BE MARK AS BRAINLIEST AND SPAM WILL BE REPORTED
What is the one major difference between ROM and RAM?
(dont want a copy paste answer from google if you are sure then only answer)
Answers
Answer:
ROM - Read Only Memory; Allows for the storage of files in a permanent state. Allowed to go back to Memory and get information from it at anytime and be able to work on it, at which point its turns to the RAM's job.
RAM - Random Access Memory; Allows for storage of files in a Temporary state. Files get cleared from RAM once file is closed or exited.
Describe each of the principal factors risk factors in
information systems projects (20 marks)
Answers
The principal risk factors in information systems projects encompass various aspects such as project complexity, technology challenges, organizational factors, and external influences.
These factors contribute to the potential risks and uncertainties associated with the successful implementation of information systems projects.
Project Complexity: Information systems projects can be inherently complex due to factors such as scope, scale, and the integration of multiple components. The complexity may arise from intricate business processes, diverse stakeholder requirements, or the need for extensive data management. Complex projects pose risks in terms of project management, resource allocation, and potential delays or cost overruns.
Technology Challenges: Information systems projects often involve implementing new technologies, software systems, or infrastructure. Technological risks include compatibility issues, scalability limitations, security vulnerabilities, and the need for specialized expertise. These challenges may impact the project timeline, functionality, and long-term viability of the system.
Organizational Factors: The success of an information systems project depends on organizational factors such as leadership, communication, and stakeholder engagement. Risks in this domain include lack of management support, insufficient user involvement, resistance to change, inadequate training, and poor project governance. Failure to address these factors can lead to user dissatisfaction, low adoption rates, and project failure.
External Influences: External factors, such as changes in regulatory requirements, market dynamics, or economic conditions, can introduce risks to information systems projects. These factors may necessitate modifications to project scope, increased compliance efforts, or adjustments to business strategies. Failure to anticipate and adapt to external influences can disrupt project timelines and impact the project's overall success.
Understanding and managing these principal risk factors is crucial for effective project planning, risk mitigation, and successful implementation of information systems projects. Proper risk assessment, contingency planning, stakeholder involvement, and ongoing monitoring are essential to minimize the impact of these risks and ensure project success.
Learn more about information systems here:
https://brainly.com/question/13081794
#SPJ11
Which of the following is not a method for opening Word software?
Answers
Answer:
right clicking on the desktop and clicking "view"
Answer:
veiw
Explanation:
Microsoft Windows, commonly referred to as Windows, is a group of several proprietary graphical operating system families, all of which are developed and marketed by Microsoft. Each family caters to a certain sector of the computing industry
Do you believe hackers are a necessary part of ensuring Internet safety and should they be rewarded for their efforts?
Answers
Answer:
The phrase 'Break the Law' means to fail to obey a law; to act contrary to a law. Derived from combining the words 'Hack' and 'Activism', hacktivism is the act of hacking, or breaking into a computer system, for politically or socially motivated purposes. The individual who performs an act of hacktivism is said to be a hacktivist. Which in all words saying should not be given a reward for breaking into something unless given the consent of the owners the owners may hire or ask them to help find a fault in there system but in other terms this should not happen.
you can use a in the clause if you need to specify column values or search conditions other than the one named in the update clause.
Answers
Yes, you can use the "AND" operator in the WHERE clause of an UPDATE statement to specify additional column values or search conditions.
This allows you to update multiple columns or narrow down the rows to be updated based on specific criteria.
For example, consider the following UPDATE statement:
UPDATE table_name
SET column1 = value1,
column2 = value2
WHERE column3 = value3 AND
column4 = value4;
In this statement, the WHERE clause includes additional search conditions (column3 = value3 and
column4 = value4) that need to be satisfied in order for the update to occur. This allows you to update specific rows that meet the specified criteria.
You can use the "AND" operator in the WHERE clause to specify column values or search conditions other than the ones named in the UPDATE clause, thus providing more flexibility in updating data.
To know more about clause, visit:
brainly.com/question/32672260
#SPJ11
What is your opinion on Electron Microscopes? Do you think it should continue and more money should be given towards developing the technology? Do you think it should be stopped? Why?
Answers
Answer:
Byeeeeee good luck :)
Explanation:
It is used to loosen or tighten slotted screws. * 1 point A. Hex Driver B. Torx Screwdriver C. Philips Head Screwdriver D. Flat Head Screwdriver
Answers
Answer:
D. Flat Head Screwdriver
Explanation:
Technology can be defined as a branch of knowledge which typically involves the process of applying, creating and managing practical or scientific knowledge to solve problems and improve human life. Technologies are applied to many fields in the world such as medicine, information technology, cybersecurity, engineering, environmental etc.
Basically, knowing how to use a technology simply means a scientist understands the appropriate method or technique to be used in the application of a technology such as when solving a problem. Also, knowing when to use a technology means to know the appropriate time to use a particular technology without it having any repercussion or adverse effect.
Generally, technology has impacted the world significantly and positively as it has helped to automate processes, increased efficiency and level of output with little or no human effort.
For example, a Flat Head Screwdriver can be defined as a type of screwdriver that is used to loosen or tighten slotted screws. A slotted screw has a single horizontal or vertical line on its head and is used for tightly holding two or more object together.
1) What number will be output by console.log?
var fizz;
var bop:
bop = 10;
fizz = 20:
bop = 100;
fizz= 200:
console.log (bop):
a 10
b) 100
c) 20
d) 200
e) None of the above
Answers
The number output by console.log will be 100. Option B.
The code provided initializes two variables, fizz and bop, assigns values to them, and then reassigns new values. The console.log statement is used to output the value of the bop variable.
Initially, bop is assigned a value of 10, and fizz is undefined due to the missing semicolons after their declarations. Then, bop is reassigned a value of 100, and fizz is reassigned a value of 200.
When the console.log(bop) statement is executed, it will output the current value of the bop variable, which is 100.
The output of console.log will display the current value of the variable that is passed as an argument. In this case, since bop is reassigned the value of 100 before the console.log statement, it will output 100. The previous values assigned to bop (10) and fizz (20 and 200) are overwritten, and only the current value of bop is printed.
It's worth noting that the code provided has syntax errors with the incorrect use of colons instead of semicolons to terminate statements. To fix this, semicolons should be used to separate statements.
Additionally, it is good practice to declare variables with proper syntax and avoid reusing variable names for different purposes, as it can lead to confusion and potential bugs in larger codebases. So Option B is correct.
For more question on output visit:
https://brainly.com/question/28498043
#SPJ8
Hey, can anyone please help me?

Answers
Answer:
i think the answer is b not sure tho
Explanation:
mb for being rly late lol hopefully this helps :)
The database documenter:
(a) lists the properties of selected objects in the database.
(b) suggests ways the database can be optimized.
(c) searches for rows of repeating data and suggests design changes to improve performance.
(d) is a wizard that provides step-by-step instructions on the creation of tables and forms.
Answers
By examining the detailed information provided by the Database Documenter, database developers can identify potential areas for optimization and design improvements.
The Database Documenter is a tool that primarily (a) lists the properties of selected objects in the database. This feature enables users to generate detailed reports on various database objects such as tables, queries, forms, and reports, providing important information on their structure, properties, and relationships. The Database Documenter does not directly suggest optimization methods (b), search for rows of repeating data (c), or provide step-by-step instructions for creating tables and forms (d). However, by examining the detailed information provided by the Database Documenter, database developers can identify potential areas for optimization and design improvements.
To know more about Database visit:
https://brainly.com/question/6447559
#SPJ11
URGENT! I know it has to be one of these answers, but I cannot tell the difference between them for the life of me. Help.

Answers
I don't see a difference. Otherwise, they both are correct.
You create a cookie by passing to the setcookie() function a required ____ argument and five optional arguments.namevalueexpirespath
Answers
You create a cookie by passing to the setcookie() function a required "name" argument and five optional arguments - "value", "expires", "path", "domain", and "secure".
Named parameters, named-parameter arguments, named arguments, or keyword arguments are all terms used in computer programming to describe a computer language's support for function calls that explicitly link each argument to a particular parameter parameter within the function call.
When using named arguments, you can match an argument to a parameter by its name rather than by its place in the parameter's value list. You can omit arguments for certain parameters by using optional arguments. With methods, indexers, builders, and delegates, both procedures are applicable.
The "name" argument is the only mandatory argument as it specifies the name of the cookie. The other arguments are optional and allow you to set additional properties such as the value of the cookie, when it should expire, which pages can access it, and whether it should only be sent over a secure connection.
To learn more about Named argument, click here:
https://brainly.com/question/27969907
#SPJ11
The required argument for creating a cookie using the setcookie() function is the "name" argument, which specifies the name of the cookie.
setcookie("myCookie", "cookieValue", time() + 3600, "/");
The five optional arguments that can be passed to the setcookie() function are:
"value": specifies the value of the cookie.
"expires": specifies the expiration time of the cookie. If not set, the cookie will expire when the user closes their browser.
"path": specifies the path on the server where the cookie will be available.
"domain": specifies the domain name for which the cookie will be available.
"secure": specifies whether the cookie can only be transmitted over a secure HTTPS connection.
Here is an example of how to create a cookie using the setcookie() function with some of the optional arguments:
setcookie("myCookie", "cookieValue", time() + 3600, "/");
In this example, the cookie name is "myCookie", the cookie value is "cookieValue", the cookie will expire in 1 hour (3600 seconds) from the current time, and it will be available on the root path of the server.
Learn more about HTTPS connection here,
https://brainly.com/question/30439999
#SPJ11