You are the IT Director for Stormwind. You want to implement BitLocker on your network. Which Operating Systems support BitLocker
Answers
BitLocker is available in Windows editions such as Windows 10 Professional, Windows 10 Enterprise, and Windows 10 Education.
This means that Windows 10 Professional, Enterprise, and Education support BitLocker.
BitLocker is a full-disk encryption tool developed by Microsoft to protect the data stored on a device from unauthorized access.
BitLocker provides full-disk encryption that protects the data on a device from attacks by unauthorized users. It encrypts all the data on a drive, including the operating system and all files that are saved on the drive.
With BitLocker enabled, anyone who tries to access the encrypted data would require a decryption key to read or modify the data. The decryption key is only available to the authorized user or device.
The operating systems that support BitLocker are:
Windows 7 Enterprise and Ultimate editions, Windows 8.1 Pro and Enterprise editions, Windows 10 Pro, Enterprise, and Education editions.
Learn more about BitLocker here:
https://brainly.com/question/30431629
#SPJ11
Related Questions
In the scenario below, decide whether you should upgrade the computer or replace it. You’ve been working on your existing laptop computer for 3 years. It seems to be running just fine except for the times that you need to run video-editing software for your film hobby. Plus, there is a new program that your friends are using for their video editing, and you think it is pretty cool, but it might not run on your laptop. What should you do?

Answers
Answer:
Replace
Explanation:
Since the laptop is already 3 years old and you cant just open laptops it wuld be better to just replace
Answer:
B. Replace
Explanation:
When you been working on the laptop for three years it probably won't work so you'll need to replace the old laptop with a new laptop. But if the laptop still works over that three years you can still replace it if you want.
I hope this helps. <3
Have a nice day.<3
A technique used to compromise a system is known as a(n)
A. Asset
B. Access method
C. Exploit
D. Risk
Answers
The right answer is C, which states that an exploit is a method used to breach a system.
What is the definition of a system simple?A system is a group of components or elements positioned in order to accomplish a specific objective. The phrase (which is semantically related to the word "method" in the statement "I have my own little system") can be used to refer to both the components of the system and the actual structure or design (as in "computer system").
Why is a computer system important?It controls the hardware, software, processes, and memory of the computer. Using this technique, you can communicate with the computer even if you don't comprehend its language. An operating system is essential to the operation of a computer.
To know more about system visit-
brainly.com/question/9171028
#SPJ4
what is the term for the place one network ends and another begins?
Answers
Answer:
the answer is demarcation point
what is the best combos for Nix in Brawlhalla (PS4)?
Answers
Answer:
sycthe is simple. Do down light and then turn them around. Then do chase dodge to neutral air. its an infinite combo
Explanation:
in the virtual machine simulates hardware, so it can be independent of the underlying system hardware. group of answer choices emulation full virtualization none of the mentioned system virtualization hardware virtualization
Answers
In the virtual machine simulates hardware, so it can be independent of the underlying system hardware. Option. Full virtualization.
The virtual machine simulates hardwareFull virtualization is a type of virtualization that allows a guest operating system to run on a host operating system without any modifications. The guest operating system is given full access to the underlying hardware, meaning it can run any type of software.
The virtual machine simulates hardware, so it can be independent of the underlying system hardware. This is full virtualization. The guest operating system is given full access to the underlying hardware, meaning it can run any type of software. This allows for a great deal of flexibility, as the guest operating system can be any type of operating system, including ones that are not compatible with the host operating system.
Learn more about Hardware: https://brainly.com/question/14688347
#SPJ4
interventions make use of cell phones, pagers, palm pilots, tablets, and other mobile technologies to deliver interventions and assess health-related events in the natural environment.
ecological momentary
Answers
Ecological momentary interventions make use of cell phones, pagers, palm pilots, tablets, and other mobile technologies to deliver interventions and assess health-related events in the natural environment.
Interventions are a type of prevention, where the primary goal is to stop the onset of a particular condition or illness and maintain overall health. The environment can significantly impact an individual's health and well-being. The natural environment is the immediate and broader surroundings that influence one's health. Technologies have made it possible to use mobile devices to deliver interventions and track health-related events in the environment. EMA allows researchers to capture data in real-time or at specific intervals as participants go about their daily lives, providing a more accurate and ecologically valid representation of their experiences compared to traditional retrospective self-report measures. Participants are typically prompted to respond to brief surveys or assessments multiple times throughout the day, either through notifications on their mobile devices or at pre-determined intervals. Therefore, ecological momentary interventions can use mobile technologies to capture real-time information from individuals.
Learn more about Environment:https://brainly.com/question/24182291
#SPJ11
what is the importance of planning before you start your vegetable farm business?
Answers
Answer with Explanation:
"Planning" plays a crucial role before starting any business. If you've decided to start a vegetable farm business, then you better plan ahead.
Vegetables are "perishable," which means it is easy for them to get spoiled. Thus, you have to consider many things such as: what kind of crops to sell, where to sell them, what season you're going to sell them and how much you are going to sell them.
Choosing the kind of crop depends on whether you'll be requiring intensive labor or not. Although the former means more profit, it will require more capital. Knowing your target market is essential. For example, if your target are health-conscious people, then you have to go for organic vegetables. Determining the season to sell the vegetables will allow you to price them accordingly. Lastly, you have to know how much you're going to sell your vegetables in order for you to have an idea of the profit you're going to make. This will also allow you to budget your money.
wants to redesign the user interface. The customer service agents use ________ to enter explicit statement to invoke operations within the system and cannot always remember the commands.
Answers
Answer:
The correct answer to use in filling in the gap is "Command languages interaction".
Explanation:
Command languages interaction occurs when the user enters command which are not always remembered, the computer executes it (with feedback if necessary), then requests next command.
This implies that under command languages interaction, "Command prompts" are employed by users who enter in commands and maybe certain parameters that impact how the command is executed.
Therefore, the correct answer to use in filling in the gap is "Command languages interaction".
Which of the following is a type of equation which returns a value such as TRUE or
FALSE?
A. Argument
B. Expression
C. Nest
D. Control
Answers
Answer:
C
Explanation:
True HOPE THIS HELPS BOY/GURL AH
The type of equation which returns a value such as TRUE or FALSE is logical.
Which formula gives the logical value in the form of true or false?A logical value is known to be The TRUE and FALSE functions
An example is if you type “=TRUE()” into a cell, it is said to often return the value TRUE and when you type “=FALSE()” it will also return as FALSE.
Learn more about equation from
https://brainly.com/question/2972832
suppose the segments are limited to the 4 kib page size (so that they can be paged). is 4 bytes large enough for all page table entries (including those in the segment tables?
Answers
It is not clear what you mean by "segments" and "tables" in this context, as there are multiple types of segments and tables in computer systems. However, assuming you are referring to memory segments and page tables:
If the segments are limited to 4 kib page size, this means that each segment can be divided into multiple 4 kib pages for paging purposes. Each page table entry typically contains information about the physical memory address of the page, as well as other control bits such as permission bits and dirty bits.
The size of each page table entry depends on the system architecture and the number of control bits needed. In some systems, a page table entry may be 4 bytes or less, while in others it may be larger.
Therefore, whether 4 bytes is large enough for all page table entries in the segment tables depends on the specific system architecture and the number of control bits needed for each entry. In general, however, it is possible for page table entries to be 4 bytes or smaller.
To learn more about memory click the link below:
brainly.com/question/31054240
#SPJ11
What will happen if both indent marker and tab stop applied in formatting the measurement layout of your document? Can both be applied at the same time?
Answers
Answer:
Explanation:
indent marker:
indent markers are located to the left of the horizontal ruler, and they provide several indenting options like left indent, right indent, first line indent and hanging indent. they allow you to indent paragraphs according to your requirements.
tab stop:
a tab stop is the location where the cursor stops after the tab key is pressed. it allows the users to line up text to the left, right, center or you can insert special characters like a decimal character, full stops, dots or dashed lines or can even create different tab stops for all the text boxes in a publication.
yes both can be applied at the same time. you do the settings according to the formatting of your layout.
find the id, first name, and last name of each customer that currently has an invoice on file for wild bird food (25 lb)
Answers
To provide the ID, first name, and last name of each customer who currently has an invoice on file for wild bird food (25 lb), the specific data from the database or system needs to be accessed. Without access to the specific data source, it is not possible to provide the direct answer.
To find the required information, you would typically need to query a database or system that stores customer and invoice data. The query would involve joining tables related to customers and invoices, filtering for invoices with the specified product (wild bird food, 25 lb). The specific database schema and structure would determine the tables and fields involved in the query.
Here's an example SQL query that demonstrates the concept, assuming a simplified database schema:
```sql
SELECT c.id, c.first_name, c.last_name
FROM customers c
JOIN invoices i ON c.id = i.customer_id
JOIN invoice_items ii ON i.id = ii.invoice_id
JOIN products p ON ii.product_id = p.id
WHERE p.name = 'wild bird food' AND p.weight = 25;
```
In this example, the query joins the `customers`, `invoices`, `invoice_items`, and `products` tables, filtering for the specified product name ('wild bird food') and weight (25 lb). The result would include the ID, first name, and last name of each customer who has an invoice on file for that particular product.
Please note that the actual query may vary depending on the specific database schema and structure, and the query language being used.
Without access to the specific data and database structure, it is not possible to provide the direct answer to the query. However, the explanation and example query provided should give you an understanding of the process involved in retrieving the required information from a database or system.
To know more about database , visit;
https://brainly.com/question/28033296
#SPJ11
What is the one small catch with password managers?.
Answers
Answer:
password managers can acess and autofill your passwords
Explanation:
the catch is if you loose all data from your computer or smartphone, then you loose all your passwords
suppose the rule of the party is that the participants who arrive later will leave earlier. which abstract data type is the most efficient one for storing the participants?a. None of theseb. Stackc. Linked Listd. Queuee. ArrayList
Answers
The most efficient data structure for storing the participants at this party would be a Queue.
If the rule of the party is that the participants who arrive later will leave earlier, then the most efficient data structure for storing the participants would be a Queue.
A Queue follows the First-In-First-Out (FIFO) principle, which means that the participant who arrives first will be the first to leave the party. As new participants arrive, they will be added to the back of the queue and when it is time for the participants to leave, they will be removed from the front of the queue.
Using a Stack would not be efficient in this scenario as it follows the Last-In-First-Out (LIFO) principle, which means that the last participant to arrive would be the first to leave. This contradicts the rule of the party.
A Linked List or ArrayList could be used, but they would require additional logic to maintain the order of arrival and departure.
Therefore, the most efficient data structure for storing the participants at this party would be a Queue.
Learn more about abstract data type here:
https://brainly.com/question/13143215
#SPJ11
pip is configured with locations that require tls/ssl, however the ssl module in python is not available.
a. True
b. False
Answers
False, The SSL module in Python is available, so the statement is false. The ssl module is part of Python's standard library, and can be imported and used in Python programs. It is used to provide TLS/SSL encryption for network communications.
The Importance of the SSL Module in PythonThe SSL module in Python is an essential part of modern programming. It provides a secure connection between two computers, making sure that all data is encrypted and secure. This module is used to ensure secure communication between web servers and clients, and is also used in many other applications such as email and file sharing. Without the SSL module, many of the important tasks we do online would be impossible.
The SSL module in Python is used to provide secure connections between two computers. It uses encryption to ensure that all data sent between the two computers is secure and can only be read by the intended recipient. This encryption also helps protect against man-in-the-middle attacks, where a malicious third party could intercept and view data being sent between two computers. Without this protection, confidential information could be easily stolen and used for malicious purposes.
The SSL module is also used to create secure websites. When a user visits a website, the SSL module is used to securely establish a connection between the website and the user’s browser. This helps ensure that all data sent back and forth between the two is secure and can only be read by the intended recipient.
Learn more about Phyton :
https://brainly.com/question/18521637
#SPJ4
the sysdate keyword cannot be included in the insert command, only the update command.T/F
Answers
Answer: False
Explanation:
The SYSDATE keyword can be used in both the INSERT and UPDATE commands in certain database systems, such as Oracle.
In an INSERT statement, the SYSDATE keyword can be used to insert the current date and time into a date column. For example:
INSERT INTO my_table (date_column) VALUES (SYSDATE);
In an UPDATE statement, the SYSDATE keyword can be used to update a date column with the current date and time. For example:
UPDATE my_table SET date_column = SYSDATE WHERE id = 1;
However, it's important to note that the availability of the SYSDATE keyword and its usage may vary depending on the specific database system being used.
Learn more about SYSDATE and UPDATE here:
https://brainly.com/question/2985058
#SPJ11
The combination of your private key and message produce a unique:___________
Answers
The combination of your private key and message produce a unique digital signature.
The digital signature is created by applying a mathematical algorithm to the combination of the private key and the message, resulting in a unique code that can be used to verify the authenticity and integrity of the message. The digital signature ensures that the message has not been tampered with or altered during transmission and provides a mechanism for verifying the identity of the sender. It is a critical component of many security protocols used for secure communication, such as email encryption and secure web browsing.
learn more about digital signature here:
https://brainly.com/question/20463764
#SPJ4
PLEASE HELPPPPP ASAP, 50 POINT'S + BRAINLIEST
1.) Online crimes causing loss of money: give 5 names and examples to each
2.) Online misconduct or crimes targeting medical offices and services: give 5 names and examples to each
3.) Online misconduct or crimes that you have experienced: give 5 names and examples to each
Answers
Answer:
1. Cybercrimes are online crimes that cause loss of money some examples are: Identity fraud, Cyber bribery, Debit/credit card fr/ud, and Email fr/ud.
2. In medical offices devices linked to CT scans are able to be h/cked, there is r/nsomw/re that uses their devices. Since medic/l computers are always linked to the internet. it makes it easier for them to be h/cked. They make an employee click on an e-mail carrying m/lw/re, then the cybercrimin/ls encrypt p/tient data then dem/nd p/yment for its decryption.
3. This is a personal question but if you have ever been sc/mmed or witnessed someone being sc/mmed or almost got sc/mmed it might apply to this question
how would you give administrative privileges on the local computer to all the members of itestaff?
Answers
To give administrative privileges on the local computer to all members of the "itestaff" group, you can follow these steps:
1. Open the computer's Local Users and Groups management console.
2. Navigate to the "Groups" folder and locate the "Administrators" group.
3. Double-click on the "Administrators" group to open its properties.
4. Click on the "Add" button to add users or groups.
5. Enter "itestaff" in the text field and click on "Check Names" to validate the group name.
6. Click "OK" to add the "itestaff" group to the "Administrators" group.
7. Apply the changes and close the properties window.
By adding the "itestaff" group to the "Administrators" group, all members of the "itestaff" group will have administrative privileges on the local computer.
Learn more about administrative privileges here:
https://brainly.com/question/28963094
#SPJ11
Which chart type is the best candidate for spotting trends and extrapolating information based on research data?
a.
pie
b.
hi-low
c.
scatter
d.
area
Answers
Scatter plot is the best chart type for spotting trends and extrapolating information based on research data.
The best chart type that is useful in spotting trends and extrapolating information based on research data is the Scatter plot. Scatter plots are used to display and compare two sets of quantitative data. It is the best type of chart that can be used to depict a correlation or association between two sets of variables. Scatter plot is a chart where individual points are used to represent the relationship between two sets of quantitative data. Scatter plots can help detect trends, clusters, and outliers in data.
Scatter plots can be used to investigate the relationship between two variables, identify trends in the data, and assess the strength and direction of the relationship between the two variables. These plots can be used to show a pattern of correlation or association between two sets of data points. By looking at a scatter plot, one can get a better idea of how much the variables are related to each other.
In conclusion, Scatter plot is the best chart type for spotting trends and extrapolating information based on research data.
To know more about Scatter plot visit:
brainly.com/question/29231735
#SPJ11
highlight various stages in evolution of computer?
Answers
Answer:
Computing began at the mechanical level, added an information level (software), then a human level and finally a community level; it is an example of general system evolution.
Information: Reduce information overload, clas...
Level: Requirements
Mechanical: Reduce physical heat or force ov...
Community: Reduce community overload, clas...
Explanation:
1 punto
María tiene una empresa de mercancia
seca, dicha empresa brinda su servicio de
ventas de estas mercancías al por mayor y
menor para su clientela. ¿De qué tipo de
Comercio hablamos en este ejemplo?: *
Answers
Answer:
Retailing.
Explanation:
La venta al por menor o retailing es el suministro de bienes físicos a los consumidores para uso personal, sea en pequeña o grandes cantidades, siempre que esté destinado a consumidores finales. Es un sector que consta de diferentes ramas (como la industria alimentaria, la industria de la moda, la industria del mobiliario para el hogar, etc.). El comercio minorista es el último eslabón de la cadena de suministro que va desde el fabricante hasta el consumidor.
You want to view a report of all luns on an iscsi device. the iscsi device is vds capable, and you have installed the vds provider on the server. Which command should you use?
Answers
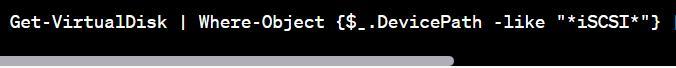
The command can be used as
Select-Object Friendly Name, Device ID, Size, Path, Operational Status
To view a report of all on an iSCSI device with VDS (Virtual Disk Service) capability, you can use the following command in PowerShell:
(attached below)
Select-Object Friendly Name, Device ID, Size, Path, Operational Status
This command utilizes the Get-Virtual Disk cmdlet to retrieve information about virtual disks, filters the results to only include iSCSI devices using the Where-Object cmdlet, and then selects specific properties using the Select-Object cmdlet.
By running this command, you should obtain a report that displays the friendly name, device ID, size, path, and operational status.
Learn more about command in PowerShell here:
https://brainly.com/question/32371587
#SPJ4
Which of the following is the correct way to code a try statement that displays the type and message of the exception that’s caught?
A. try:
number = int(input("Enter a number: "))
print("Your number is: ", number)
except Exception as e:
print(e(type), e(message))
B. try:
number = int(input("Enter a number: "))
print("Your number is: ", number)
except Exception as e:
print(type(e), e)
C. try:
number = int(input("Enter a number: "))
print("Your number is: ", number)
except Exception:
print(Exception(type), Exception(message))
D. try:
number = int(input("Enter a number: "))
print("Your number is: ", number)
except Exception:
print(type(Exception), Exception)"
Answers
The correct way to code a try statement that displays the type and message of the exception that's caught is option B:
In this option, the except block catches any exception that occurs within the try block. The exception object is assigned to the variable e using the as keyword.
To display the type of the exception, type(e) is used, which returns the class/type of the exception object. To display the message associated with the exception, e is directly printed, which will output the message contained within the exception object.
Therefore, option B is the correct way to code the try statement for displaying the type and message of the caught exception.
try:
number = int(input("Enter a number: "))
print("Your number is: ", number)
except Exception as e:
print(type(e), e)
To know more about exception object, visit:
https://brainly.com/question/32880399
#SPJ11
These 2 questions PLEASEEE (:

Answers
Answer:
on the first one pixels on the second i think it is feathering
In video game development, the person who oversees and directs the entire design team and is the key vision keeper is
the
Answers
Answer:
The Lead Designer
Explanation:
The Lead designers main role is to oversee how a game looks and is played. They manage a, normally small, design team. They work with them to come up with many aspects of the game itself like; characters, props, and plots to the game. they also, makes sure that the team itself stays on track, is within budget, and meets the designated deadlines.
when removing a node from a chain, what case should we consider? group of answer choices the node is at the end of the chain the node is at the beginning of the chain both of them none of them
Answers
When removing a node from a chain, we should consider both cases: if the node is at the beginning of the chain or if the node is at the end of the chain.
If the node is at the beginning of the chain, we need to update the reference to the head of the chain to the next node, and if the node is at the end of the chain, we need to update the reference to the tail of the chain to the previous node.
If the chain has only one node, removing it would result in an empty chain, so it's also important to consider this case and update the reference to the head and tail to null.
Learn more about nodes
https://brainly.com/question/29526707
#SPJ11
Why did we decide to send a message as a sequence of two options rather than modifying our devices to represent more options?
Answers
Answer:
Following are the solution to this question:
Explanation:
Please find the complete question in the attachment file.
The binary message is also an XML text SMS, which is used to represent in binary character. It may also flag the binary text as binary, and it can attach the UDH as just the start of its message. In this question, we assume that you can include A and B because there could be no more than 2 choices in such a binary message.

We decided to send a message as a sequence of two states (A and B) rather than modifying our devices to represent more states (State C, State D, State E, etc.) primarily for simplicity and efficiency.
Using a binary communication system with just two states is straightforward and easier to implement than introducing more complex modifications for additional states.
Binary communication allows for clear and unambiguous encoding and decoding, making it more reliable and less prone to errors.
While using more states could potentially convey more information, it would also require more complex hardware and software, increasing the risk of communication errors and complicating the overall system design and operation.
Know more about binary communication:
https://brainly.com/question/32447290
#SPJ3
Your question is incomplete, but most probably your full question was.
Why did we decide to send a message as a sequence of state (A and B) rather than modifying our devices to represent more State (State C, State D, State E,....)?
you can use tables for layout work. However, in XHTML, each form control should have its own ______ element
a. method
b. textarea
c. label
d. fieldset
Answers
Answer:
c. label
Explanation:
30 points and brainiest Which certifications are offered in Family Consumer Science? (Select 2) Select 2 correct answer(s)
Question 2 options:
Community Health Worker
Early Childhood Education
Food Handler's
Counseling
Answers
The certifications are offered in Family Consumer Science are option B and C:
Early Childhood EducationFood Handler'sWhat is the certifications about?Family Consumer Science is a field that focuses on the study of how families interact with the broader community and economy. Some of the certifications offered in Family Consumer Science include:
Early Childhood Education: This certification is designed for individuals who wish to work with young children, typically from birth to age 8, in settings such as preschools, daycare centers, and primary schools. It covers topics such as child development, teaching methods, and classroom management.
Therefore, in Food Service Management: this certification is designed for individuals who wish to work in the food service industry, such as managing and supervising food service operations in schools, hospitals, restaurants and other food service facilities.
Learn more about certifications from
https://brainly.com/question/26004231
#SPJ1