xm grafix, a graphics design company, has bought new design software. mason, the system administrator, wants to install the software on all the computers in the design department. however, not all the designers need the software. using the gpo, mason uses a deployment method that allows the users to install the program from the network when they need it. which of the following methods of deployment has mason most likely used in the given scenario?
Answers
Group Policy Objects (GPO) to make the software available from the network and allowing users to install it on-demand Mason has implemented a convenient and efficient deployment approach for the graphics design software at XM Grafix.
Mason the system administrator has used a deployment method that allows users to install the program from the network when they need it. Based on this information Mason most likely used a method called "On-Demand" or "Just-in-Time" deployment.
On-Demand deployment involves making the software available on a network location accessible to the users.
The software they can initiate the installation process themselves by accessing the network location and installing the program on their computer.
This method provides flexibility as it allows users to install the software when required without requiring the system administrator to manually install it on every computer in the design department.
Group Policy Objects (GPO) to make the software available from the network and allowing users to install it on-demand Mason has implemented a convenient and efficient deployment approach for the graphics design software at XM Grafix.
For similar questions on deployment
https://brainly.com/question/30363719
#SPJ11
Related Questions
An end-user has reported that a legitimate sender sent an unexpected email stating the user needed to urgently update the password account information to a vendor website. Once the user clicked on the URL in the email, the user was taken to a landing page to update the user's credentials. The user entered the credentials, despite noticing the URL was slightly misspelled. What happened in this situation
Answers
Group of answer choices.
A) The attacker has sniffed the user's packets on the user's local network and has captured the user's credentials in plain text.
B) The user is a victim of a pharming attack by using social engineering to trick the user into clicking a link that redirected their traffic to a spoof website.
C) The user is the victim of an impersonation attack, where the attacker used intimidation by coaxing the target and engaging with them by putting them at ease.
D) The user is a victim of a phishing scam, and the attacker spoofed or compromised the sender's email address and spoofed the website.
Answer:
D) The user is a victim of a phishing scam, and the attacker spoofed or compromised the sender's email address and spoofed the website.
Explanation:
Social engineering can be defined as an art of manipulating people, especially the vulnerable to divulge confidential information or performing actions that compromises their security.
Basically, it is a manipulative strategy or technique that involves the use of deceptive and malicious activities on unsuspecting victims in order to gain unauthorized access to their confidential or private information for fraud-related purposes. Some examples of social engineering attacks include quid pro quo, spear phishing, baiting, tailgating, water-holing, vishing, pretexting, phishing, etc.
Phishing is an attempt to obtain sensitive information such as usernames, passwords and credit card details or bank account details by disguising oneself as a trustworthy entity in an electronic communication usually over the internet.
Furthermore, phishing is a type of fraudulent or social engineering attack used to lure unsuspecting individuals to click on a link that looks like that of a genuine website and then taken to a fraudulent web site which asks for personal information.
This ultimately implies that, the user in this scenario is a victim of a phishing scam, and the attacker spoofed or compromised the sender's email address and spoofed the website to make it look like a credible, authentic and original one.
Answer:
D) The user is a victim of a phishing scam, and the attacker spoofed or compromised the sender's email address and spoofed the website.
how would you grant additional users access rights to your efs encrypted folders and data files?
Answers
To grant additional users access rights to your efs encrypted folders and data files steps are:
From the General tab, click Advanced.Click Details.Click Add.Click Find User.Select the user from list.Click OK to save your changes.What is the access?To give users access to your encrypted folders and files with EFS, follow these steps:
- Log in to the computer with admin privileges.- Find the folder or file you want to give access to. 1. Right-click and select "Properties".
Go to "General" tab and click "Advanced" button. Click "Details" under Encryption in Advanced Attributes. Then click "Add" in Encryption Details. In the window, enter the user or group name. Click "Advanced" to search. Click "Check Names" to verify username/group name. Select user/group, click "OK" to close window. In Encryption Details, select new user/group, check desired access level, then click OK to close. Click "OK" in Advanced Attributes and "Apply" & "OK" in Properties to save changes.
Learn more about access from
https://brainly.com/question/27961288
#SPJ4
miriam is a network administrator. she would like to use a wireless authentication technology similar to that found in hotels where users are redirected to a webpage when they connect to the network. what technology should she deploy?
Answers
The technology she should deploy is a captive portal.
What do you mean by technology?
Technology is the application of knowledge to achieve practical goals in a predictable and repeatable manner. The term technology can also refer to the outcome of such an undertaking. Technology is widely used in medical, science, industry, communication, transportation, and everyday life. Physical objects such as utensils or machinery are examples of technologies, as are intangible instruments such as software. Many technological advances have resulted in societal shifts. The earliest known technology is the stone tool, which was employed in the prehistoric past, followed by fire use, which led to the development of the human brain and language throughout the Ice Age.
To learn more about technology
https://brainly.com/question/25110079
#SPJ4
Type the correct answer in the box spell all words correctly.
karl has designed an interactive stories website for kids. he has implemented an alphabetical format for browsing through the stories. which
structure will he use for easy navigation?
kart implements a
structure for users to advance through the chapters.
reset
nexus
Answers
Kart should implement a main navigation structure for users to advance through the chapters.
The types of navigation.
In Computer technology, there are three main types of navigation used on websites and these include the following:
Structural navigationUtility navigationAssociative navigationIn this scenario, Kart should implement a main navigation structure for users to advance through the chapters on this interactive stories website for kids.
Read more on website here: https://brainly.com/question/26324021
#SPJ1
!WILL GIVE BRAINLIEST!
Write a Python program that prompts the user for a word. If the word comes between the words apple
and pear alphabetically, print a message that tells the user that the word is valid, otherwise, tell
the user the word is out of range.
Answers
Answer:
word = input()
if word > "apple" and word < "pear":
print("Word is valid.")
else:
print("Word is out of range.")
Traditional hackers are motivated by ________.
A) thrill
B) validation of power
C) doing damage as a by-product
D) All of the above
Answers
Traditional hackers are motivated by all the above given parameters of the option - D
Traditional hackers can be motivated by various factors, including thrill, validation of power, and the desire to cause damage as a by-product. For some hackers, the thrill of exploring and overcoming technical challenges can be a motivating factor. They may derive excitement and satisfaction from successfully breaching security systems or discovering vulnerabilities.
Additionally, the validation of power can drive certain hackers, as gaining unauthorized access to systems can give them a sense of control and superiority. Some hackers may also aim to cause damage as a secondary objective, such as disrupting services, stealing sensitive information, or spreading malware. It's important to note that motivations can vary among hackers, and not all hackers have malicious intent. Some individuals may engage in hacking activities for ethical reasons, such as identifying vulnerabilities to help improve security systems.
To know more about hackers visit:
brainly.com/question/14672629
#SPJ11
Which of the following devices might be used to transmit electronic mail? *
1 point
(A) Printer
(B) Monitor
(C) Fax machine
(D) Smartphone
Answers
Why should even small-sized companies be vigilant about security?
Answers
Answer:businesses systems and data are constantly in danger from hackers,malware,rogue employees, system failure and much more
Explanation:
which of these is not part of the art director's job?
A. Hiring actors for a television commercial
B. Finding a new location for filming at the last minute.
C. Calming down a dissatisfied client.
D. Designing the color scheme for a print ad.
Answers
Answer:
C
Explanation:
When you instruct a computer or mobile device to run an application, the computer or mobile device answer its software, which means the application is copied from storage to memory?
Answers
I believe loads
not for sure what the question is
When both source and destination files need constant updating, use _____________.
A.) cropping
B.) embedding
C.) linking
D.) pasting
Answers
When both source and destination files need constant updating, use embedding or linking.
What is the destination file?The file is known to be one that is linked or said to be a form of embedded object that is often inserted into, or that data is saved to.
Note that the source file is one that has the information that is used to create the object and as such, when there is issues, one can use linking.
Learn more about destination files from
https://brainly.com/question/17019048
Can someone help me figure out why my else statment is not working?
----------------------------------------------------------------------------------------------------------------------------
print("\tBank of The Funny Money Bunny Farm\n")
print("Client\t\tDeposits\tWithdrawals\tBalance\t\tNotes:")
print("__________________________________________________________________________________________________________________________")
names = ['Judith', 'Jimmie', 'Johnny', 'Joseph', 'Jeffry', 'Buddie', 'Charlie', 'Maxine', 'Jannis', 'Bodine']
deposists = [255.23, 525.55, 323.21, 651.48, 507.11, 101.11, 253.36, 323.22, 611.45, 252.91]
withdrawals = [255.76, 128.65, 156.22, 175.33, 390.12, 255.41, 128.22, 156.23, 728.98, 251.43]
balance = []
notes = []
for i in range(len(names)):
balance.appened(deposits[i] - withdrawals[i])
if(balance < 0):
print((names[i] + ", you are overdrawn. Your account balance is " + "$%.2f"%(balance[i]))
else:
print("" + names[i] + "\t\t" + "%.2f"%(deposits[i]) + "\t\t" + "%.2f"%(withdrawals[i]) + "\t\t" + "%.2f"%(balance[i]) + "\t\t" + notes[i])
print("__________________________________________________________________________________________________________________________")
print("\© Copyright 2021 Funny Bunny Money Productions")
#Main
print("\tBank of The Funny Money Bunny Farm\n")
account = int(input("How many new accounts are needed: "))
for i in range(account):
input("Enter the name of the client: ")
input("Enter the deposist of the client: ")
input("Enter the withdraral of the client: ")
Answers
Answer:
below is a version of your code that runs.
I'm not sure if it does what you expect it to do.

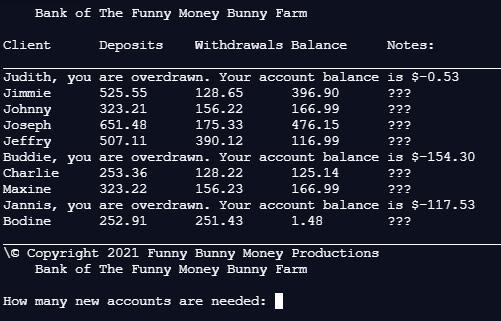
What are the missing parts to produce the following output?
0
2
4
• num in range(3):
print (num
Answers
The missing parts to produce the following output are as follows;
num = 0
while num < 5:
print(num)
num += 2
What is a print statement?In Computer programming, a print statement can be defined as a line of code that is used to send data to the print or println method of a programming system such as compiler, so as to output a given statement.
Additionally, methods are typically written and used by programmers to break down any complex problem into simple and manageable fragments (pieces) such as in modern programming languages, which comprises several predefined methods.
In this scenario, the output can be produced by using the following print statement written using a while loop;
num = 0
while num < 5:
print(num)
num += 2
Read more on print statement here: brainly.com/question/21631657
#SPJ1
Nicole wants to create a database to collect information about videos in her video rental store. She would like to use the database to look up movies by rating, actors, producer, and title. She would also like to retrieve the movies that are in stock. What fields should she have in her database?.
Answers
The fields that Nicole must have in her database is title, producer, actor, rating, and in stock.
What is field?Field is a set of data in database system with same data type. Field usually referred as a column or attribute but it also can hold another data like pictures, movie clips, etc.
Since, Nicole only want to look up movies by rating, actors, producer, title, and in stock movies. That all can be used as fields in her database with the appropriate data type for each field, also if Nicole want her also put more field for one category like actor 1, actor 2, actor 3, or rating 1, rating 2, rating 3.
Learn more about database here:
brainly.com/question/26096799
#SPJ4
11.6 Code Practice edhesive
Answers
Answer:
This is not exactly a copy paste but required code IS added to help
<html>
<body>
<a href=" [Insert the basic www wikipedia website link or else it won't work] ">
<img src=" [I don't believe it matters what image you link] "></a>
</body>
</html>
Mainly for the Edhesive users:
I received a 100% on Edhesive 11.6 Code Practice
The program for html code for the 11.6 code practice edhesive can be written in the described manner.
What is html element?HTML elements are a component of html documents. There are three kines of html elements viz, normal elements, raw text elements, void elements.
The html code for the 11.6 code practice edhesive can be written as,
<html>
<body>
<a href="https:/website-when-image-clicked.com">
<img src="https://some-random-image"></a>
</body>
</html>
Hence, the program for html code for the 11.6 code practice edhesive can be written in the described manner.
Learn more about the code practice edhesive here;
https://brainly.com/question/17770454
Which of the following statements about professional codes of conduct is true?
1.They are written in a software programming language.
2. They define salary levels for professions.
3. They define how professionals should make decisions about their professional behavior.
4. They are surveys taken by professionals to identify behavioral issues on the job.
Answers
Answer:
They define how professionals should make decisions about their professional behavior.
Explanation:
Answer: 3. They define how professionals should make decisions about their professional behavior.
Explanation: This is the correct answer on Edge 2021, just did the assignment. Hope this helps ^-^.
How are the waterfall and agile methods of software development similar?
Answers
The waterfall and agile methods of software development are similar in that they both aim to develop software in an organized and efficient manner. However, they differ in the approach they take to achieve this goal.
The waterfall method is a linear, sequential method of software development. It follows a defined process with distinct phases, such as requirements gathering, design, implementation, testing, and maintenance. Each phase must be completed before the next phase can begin, and changes to the software are not allowed once a phase is completed.
On the other hand, Agile method is an iterative and incremental approach to software development. It emphasizes on flexibility, collaboration, and customer satisfaction. Agile method encourages regular inspection and adaptation, allowing for changes and improvements to be made throughout the development process. Agile methodologies, such as Scrum and Kanban, follow an incremental approach, where the software is developed in small chunks called iterations or sprints.
Both Waterfall and Agile approach have their own advantages and disadvantages and are suitable for different types of projects and teams. It is important to choose a method that aligns with the specific needs and goals of the project and the team.
Enum name_tag { BLUEBERRY, BANANA, PINEAPPLE, WATERMELON }; typedef enum name_tag name_t; struct fruit_tag { name_t name; double size; }; typedef struct fruit_tag fruit_t; fruit_t getBigger(fruit_t f, double d) { f.Size += d; return f; } int main(void) { fruit_t myFruit; myFruit.Name = BANANA; myFruit.Size = 5.2; myFruit = getBigger(myFruit, 3.4); printf("This fruit is %.2f grams.\n", myFruit.Size); return 0; }
Answers
Answer:
The output of the given code is "This fruit is 8.60 grams".
Explanation:
In the given code there are some mistype errors, which is reduced in the attachment file, please find the attachment and its description as follows:
In the program, an enum keyword is used, that defines a "name_tag" datatype, which assigns other values, that are "BLUEBERRY, BANANA, PINEAPPLE, WATERMELON".In the next step, the typedef keyword is used, which creates the reference of the name_tag, and in the next step, a structure is declared, which defines the name as name_t and double variable size.By using typedef a method "getBigger" is declared that adds input value in reference f and returns its value.Inside the main method, the structure reference variable "myFruit" is created that assigns size value and name values, and in this reference variable, we call the method and print its return value.
Which three individuals were involved in creating programming languages?
A. Kathleen Booth
B. Charles Babbage
C. John G. Kemeny
D. Grace Hopper
Answers
The three individuals that were involved in creating programming languages are:
A. Kathleen Booth
C. John G. Kemeny
D. Grace Hopper
What is a software?A software can be defined as a set of executable instructions that is typically used to instruct a computer system on how to perform a specific task and proffer solutions to a particular problem.
What is programming?Programming can be defined as a process through which software developer and computer programmers write a set of instructions (codes) that instructs a software on how to perform a specific task on a computer system.
Based on historical information and records, we can infer and logically deduce that the three individuals that were involved in creating programming languages are:
Kathleen Booth John G. KemenyGrace HopperRead more on programming languages here: brainly.com/question/26497128
#SPJ1
Transferring data from a remote computer to a local computer is .....
Answers
The answer is uploading
what is the best resource to learn python?
Answers
Answer:
prolly a snake expert
Explanation:
they know snakes
How do I create a for loop in MATLAB?
Answers
There is one additional approach to retrieve array elements using the for loop. Here, we immediately add an array to the for loop so that the iterator variable can access its elements (i.e., I or j etc).
How is a for loop used?To repeat a certain block of code a predetermined number of times, use a "For" loop. We loop from 1 to that number, for instance, to verify each student's grade in the class. We utilize a "While" loop when it is unknown how many times something will happen.
In MATLAB, how do you repeat a function?action is repeated n times by the function repeat(action, n). The input arguments can be specified in any order. The action is repeated n times using the functions repeat(action,n) and repeat(n,action).
To learn more about iterator variable here:
https://brainly.com/question/12475735
#SPJ4
Adam is using the software development life cycle to create a new game. He made an outline of what functionality the game will require, determined how long it will take to create the game, and made a list of people who could help him with the graphics. What should Adam do next
Answers
Answer:
Write pseudocode and create a mock-up of how the game will work and look
Explanation:
Since in the question it is mentioned that Adam wants to develop a new game for this he made an outline with respect to game functions needed, time period, people who help him.
After that, he writes the pseudocode i.e a programming language and then develops a model i.e mock up that reflects the working of the game and its look so that he would get to know how much work is pending.
Kourtney is searching for a software package that provides many resources for software developers all in one place. What should Kourtney search for?
Answers
The thing or factor that Kourtney need to search for is said to be an integrated development environment.
What is software package?This is known to be a composition or a set of related programs that is said to be made for a specific type of task such as word processing, sold and it is one that a user can be able to use as a single unit.
Since Kourtney is searching for a software package that provides many resources for software developers all in one place, an integrated development environment is the best option for her.
Learn more about software package from
https://brainly.com/question/1538272
#SPJ1
What is the difference between HIPS and anti virus?
Answers
HIPS (Host-based Intrusion Prevention System) and antivirus (AV) are both cybersecurity technologies that are designed to protect against various types of malware and cyber attacks.
Approach: HIPS works by monitoring and analyzing system behavior, looking for suspicious or unauthorized activities that may indicate a cyber attack. It can prevent attacks by blocking or alerting the system administrator to suspicious behavior. Antivirus, on the other hand, uses a signature-based approach to detect known malware and viruses based on their unique code patterns.Coverage: HIPS is designed to protect against a broader range of threats, including zero-day attacks and unknown threats that do not yet have a signature. Antivirus is more effective at detecting known threats but may not be as effective against new or unknown threats.Impact: HIPS can have a higher impact on system performance and may require more configuration and management than antivirus, which typically runs in the background with minimal user intervention.
To learn more about antivirus (AV) click the link below:
brainly.com/question/31785361
#SPJ11
n2care has one product, the medcottage, that is prefabricated and pre-equipped with medical equipment used by nursing homes. n2care is utilizing a(n) targeting strategy.
Answers
Based on the above, the n2care is utilizing a concentrated targeting strategy.
What is concentrated targeting strategy?The term Concentrated marketing is known to be a kind of a marketing strategy where the firm or a company is known to be based on one single target market group for all of their marketing goals or initiatives.
Note that Companies are said to make use concentrated marketing to tell more on how their products can be able to reach or meet the special needs of their niche audience.
Therefore, Based on the above, the n2care is utilizing a concentrated targeting strategy.
Learn more about targeting strategy from
https://brainly.com/question/17198359
#SPJ1
N2Care has one product, the MEDCottage, that is pre-fabricated and pre-equipped with medical equipment used by nursing homes. N2Care is utilizing a(n) _______ targeting strategy.
multisegment
undifferentiated
concentrated
mass marketing
How does educating and training users maintain a secure network environment?
Answers
Define the term editing
Answers
Answer:
editing is a word file mean making changes in the text contain is a file. or a word file is one of the most basic ms office word operation.
a company is renovating a new office space and is updating all cisco routers. the up-to-date internetwork operating system (ios) will provide the best protection from zero-day exploits. what other options could a network administrator configure for route security? (select all that apply.)
Answers
The options that could a network administrator configure for route security are options A and B:
Message authenticationBlock source routed packetsWhat serves as a message's authentication?The property that a message has not been altered while in transit and that the receiving party can confirm the message's source is known as message authentication or data origin authentication in the field of information security.
Therefore, A message authentication code (MAC) is a cryptographic checksum on data that employs a session key to identify unintentional as well as intentional data modifications. A MAC needs two inputs: a message and a secret key that can only be known by the message's sender and intended recipient.
Learn more about network administrator from
https://brainly.com/question/4264949
#SPJ1
See options below
Message authentication
Block source routed packets
Use 802.1p header.
Survey a site for signal strength
Windows Defender Credential Guard does not allow using saved credentials for RDP connections?
Answers
Go to the Computer Configuration > Administrative Templates > System > Device Guard > Enable Virtualization Based Security. In the Configure Credential Guard section, set the dropdown value to Disabled.
How can I allow RDP credentials to be saved?
Allows delegation of stored credentials for RDP connections via GPO. By default Windows allows the user to save the password for her RDP connection. To do this, the user must enter the RDP machine name and user name, and select the Allow saving credentials checkbox in the Remote Desktop Connection (mstsc.exe) client window.
Does RDP not allow saved credentials?
Go to Local Computer Policy > Computer Configuration > Administrative Templates > System > Credential Delegation. Change the policy named "Allow delegation of stored credentials with NTLM server authentication only" to active.
To know more about Credentials visit here:
https://brainly.com/question/30164649
#SPJ4