Write code to complete doublePennies()'s base case. Sample output for below program with inputs 1 and 10: Number of pennies after 10 days: 1024
Answers
In python:
def doublePenny(starting_penny, days):
i = 0
while i < days:
starting_penny = starting_penny * 2
i += 1
return starting_penny
We can test this function with the following code:
print(doublePenny(1,10)). The output will be 1024
I hope this helps!
Related Questions
answer this what is my favorite thing to do?
Answers
Answer:
Waste people's time with bad questions
Please help my career is a veterinarian!
4. What path could you take in high school to help prepare you for this career? For example: AP
courses, career and technical education, etc. Which is most appropriate and why?
5. What post-secondary routes (education after high school) could also help you to prepare for
this career? Explain or describe.

Answers
Answer:
1. Search for internships at local businesses or organizations. Choose part-time jobs that allow you to gain experience and help you build skills in your chosen career. Participate in extracurricular activities and take advantage of leadership opportunities. Join clubs that relate to your chosen field.
2. Schooling after high school that includes programs at technical and trade schools, community colleges, and four-year colleges.
Identify two stages of processing instructions
Answers
Answer:
1. Fetch instruction from memory.
2. Decode the instruction.
Lawn Mowing(Use the posted CarRental.py as an example to code this program.)The lawn-mowing season lasts 20 weeks. The weekly fee for mowing a lot as the following: To pay the bill, the customer can have three options: pay once, twice, or 20 times for the season. If the customer pays for once, the fee for the season is simply the seasonal total. If the customer requests two payments, each payment is half the seasonal fee plus a $5 service charge. If the customer requests 20 separate payments, add a $3 service charge per week. Write a Python main() function that reads the lot size and payment number option from the user, the program should print the amount per payment and the total payment as the sample output shown below. Note that, for now, you should assume that the lot size input will always be a positive number, and the payment option input is 1, 2, or 20. Sample outputs:Lot SizeWeekly FeeLess than 400 Sq. Ft $25400 Sq. Ft –Less than 600 Sq. Ft$35600 Sq. Ft and above
Answers
Answer:
The price of a Lawn Mowing Professional can vary depending on your area. ... On average, lawn mowing and trimming costs $50, with prices ... much you will pay to hire a professional to mow your lawn, this article ... In one example of average pricing for fertilization and weed control, ... Once a week, $206.
Explanation:
3.13 LAB: Poem (HTML)
Create a webpage that displays the poem below.
Use 2 paragraph tags for the stanzas and
tags where necessary to keep the correct formatting.
• Use a 3rd paragraph for the author and date, and enclose the author and date in a tag.
I'm Nobody! Who are you?
Are you
Nobody - Too?
Then there's a pair of us!
Don't tell! They'd banish us - you know!
How dreary to be Somebody!
How public like a
To tell one's name
To an admiring Bog!
Frog -
the livelong June -
By Emily Dickinson (1891)

Answers
Answer:
<!DOCTYPE html>
<html>
<head>
<title>Emily Dickinson Poem</title>
</head>
<body>
<p>I'm Nobody! Who are you?<br>
Are you<br>
Nobody - Too?<br>
Then there's a pair of us!<br>
Don't tell! They'd banish us - you know!</p>
<p>How dreary to be Somebody!<br>
How public like a<br>
Frog -<br>
To tell one's name<br>
To an admiring Bog!</p>
<p>By <em>Emily Dickinson</em> (1891)</p>
</body>
</html>
A vendor conducting a pilot program with your organization contacts you for
organizational data to use in a prototype. How should you respond?
Answers
Since the vendor is conducting a pilot program with your organization contacts you for organizational data to use in a prototype, The way that you can respond is to Refer the vendor to the right personnel.
What is an example of a reference vendor?A report outlining the payment history between a company customer and its supplier or vendor is known as a supplier reference (or trade reference). It helps a supplier to evaluate your creditworthiness and determine whether you're a trustworthy customer before extending credit to you.
You can determine whether you are prepared to undertake the project fully by running a pilot program. It might highlight unforeseen difficulties that must be resolved, providing you the chance to change and improve in a way that lessens the effects of those difficulties.
Hence, An organization can discover how a large-scale project might function in practice by conducting a small-scale, brief experiment known as a pilot program, also known as a feasibility study or experimental trial.
Learn more about pilot program from
https://brainly.com/question/28920126
#SPJ1
2. Between MAC, DAC, and RBAC, which would you recommend to someone starting up an
online retailing company who had to maintain customer records, track sales, etc., and had
a sizable staff of 20 or more employees? Why?
Answers
Answer: RBAC
Explanation:
I would recommend Role-Based Access Control (RBAC) to someone starting up an online retailing company who had to maintain customer records, track sales, and had a sizable staff of 20 or more employees. RBAC is an access control system that is based on the roles of users within an organization. It allows administrators to assign access privileges to users based on their roles within the company. This allows for a more secure and effective way to manage user access, as it is based on roles, rather than individual permissions. Additionally, RBAC provides a more granular level of control over access, allowing administrators to easily assign and manage access to specific resources and tasks. This makes it a good choice for a large organization with many users.
2.) Using Constants and Variables to create a Program (10 points)
You are going to write out a program below that will help calculate the total amount of money made per
week, based on a 5 day work week and making $8 per hour.
You will need to create (2) Constant variables
You will need to create (3) variables
Answers
Using Constants and Variables to create a Program is given below.
How to create the program# Establish constant values
DAYS_PER_WEEK = 5
HOURLY_WAGE = 8
# Introduce changeable parameters
hours_worked = 0
daily_earnings = 0
total_earnings = 0
# Ask user regarding hours labored each day
for day in range(1, DAYS_PER_WEEK + 1):
hours_worked = int(input(f"How many hours did you work on day {day}? "))
daily_earnings = hours_worked * HOURLY_WAGE
total_earnings += daily_earnings
# Display aggregate income for the week
print(f"You made a total of ${total_earnings} this week.")
Learn more about program on
https://brainly.com/question/26642771
#SPJ1
Can someone help me with the following logical circuit, perform two actions. FIRST, convert the circuit into a logical
statement. SECOND, create a truth table based on the circuit/statement. (20 pts. each for statement and
truth table.

Answers
Creation of Truth Table Based on the logical statement, we can create a truth table as shown below:
A B (not A) (not A) and B (not A) and B or A A or (not A) and B 0 0 1 0 1 0 0 1 0 0 1 0 1 1 0 1 1 0 1 1 1 0 1 1 0 1 1 0 1 1 1
The first two columns show the input values, the next column shows the output of the NOT gate, then the output of the AND gate, then the output of the OR gate and finally the output of the logical statement.
We can observe that the output of the logical statement is the same as the output of the OR gate.
Given the logical circuit, we are required to perform two actions on it. Firstly, convert the circuit into a logical statement. Secondly, create a truth table based on the circuit/statement. Let's understand how to do these actions one by one:Conversion of Circuit into Logical Statement.
The given circuit contains three components: NOT gate, AND gate and OR gate. Let's analyze the working of this circuit. The two input variables A and B are first passed through the NOT gate, which gives the opposite of the input signal.
Then the NOT gate output is passed through the AND gate along with the input variable B. The output of the AND gate is then passed through the OR gate along with the input variable A.We can create a logical statement based on this working as: (not A) and B or A. This can also be represented as A or (not A) and B. Either of these statements is correct and can be used to construct the truth table.
Creation of Truth Table Based on the logical statement, we can create a truth table as shown below:
A B (not A) (not A) and B (not A) and B or A A or (not A) and B 0 0 1 0 1 0 0 1 0 0 1 0 1 1 0 1 1 0 1 1 1 0 1 1 0 1 1 0 1 1 1
In the truth table, we have all possible combinations of input variables A and B and their corresponding outputs for each component of the circuit.
The first two columns show the input values, the next column shows the output of the NOT gate, then the output of the AND gate, then the output of the OR gate and finally the output of the logical statement.
We can observe that the output of the logical statement is the same as the output of the OR gate.
For more such questions on Truth Table, click on:
https://brainly.com/question/13425324
#SPJ8
According to ACM and IEEE What are the most popular programming languages used in industry today
Answers
Python remains on top but is closely followed by C. Indeed, the combined popularity of C and the big C-like languages—C++ and C#—would outrank Python by some margin.
What is a programming language?A method of notation for creating computer programs is known as a programming language. The majority of formal programming languages are text-based, though they can also be graphical. They are a sort of programming language.
Large enterprises all across the world employ client-server applications, and Java is the programming language most often associated with their creation.
Learn more about programming language here:
https://brainly.com/question/16936315
#SPJ1
Mikolas is doing a research on U.S. visas for a school project. He has found conflicting information on two sites. The first site is travel.state.gov and the other is traveldocs.com. Which site should Mikolas trust more?
Traveldocs.com
Travel.state.gov
Answers
Answer:
Travel.State.Gov
Explanation:
This is a government website explaining visas which should be very well trusted. However, traveldocs.com could be made by any person who does or doesn't know what they're talking about.
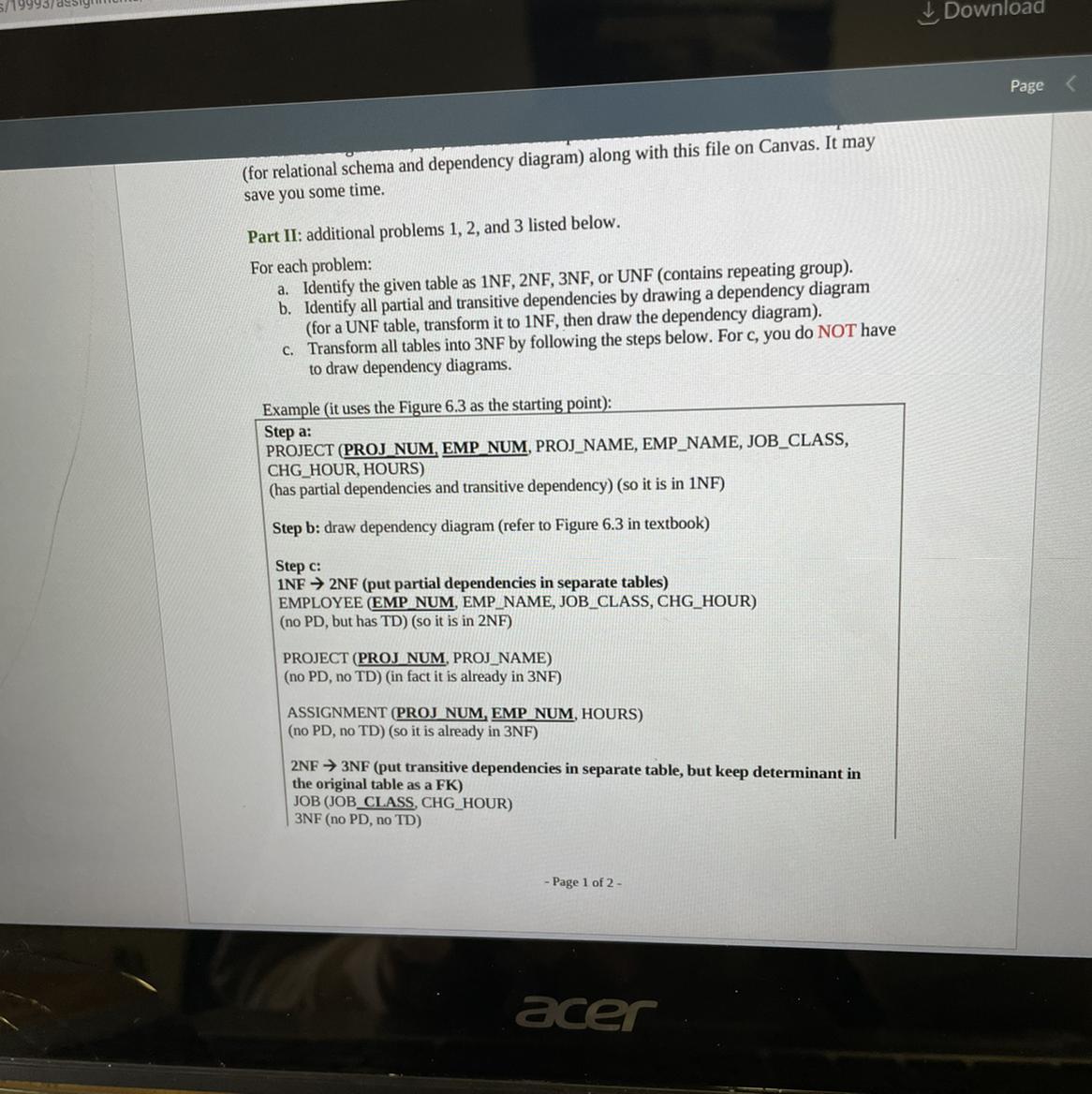
Part II: additional problems 1, 2, and 3 listed below.
For each problem:
a. Identify the given table as 1NF, 2NF, 3NF, or UNF (contains repeating group).
b. Identify all partial and transitive dependencies by drawing a dependency diagram
(for a UNF table, transform it to 1NF, then draw the dependency diagram).
c. Transform all tables into 3NF by following the steps below. For c, you do NOT have
to draw dependency diagrams.
1. STUDENT (STUDENT SSN, ST_NAME, MAJOR, ADVISOR NUM, ADV_NAME,
ADV OFFICE. ADV PHONE ST CREDITHRS, CLASS STANDING)
where:
STUDENT SSN
- All other attributes
ADVISOR NUM› ADV_NAME, ADV OFFICE, ADV PHONE
ST CREDIT HRS > CLASS STANDING
Note: XYZ > ORS means that XYZ determines ORS
You can also find this notation in figure 6.3 and definition of determination on page
62.
2. MOVIE (MOVIE NUM, MOVIE TITLE, STAR NUM, STAR NAME)
Sample data: (You can determine primary key based on the sample data.)
MOVIE NUM
MOVIE TITLE
STAR NUM
I STAR NAME
M001
The Mummy
S001
Brendan Fraser
S002
Rachel Weisz
M002
Crash
S001
Brendan Fraser
S003
Sandra Bullock
(You may notice one movie can feature many stars and one star can act in many movies.)
3. MOVIE (MOVIE NUM, MOVIE TITLE, DIRECTOR NUM, DIR NAME)
where:
MOVIE NUM
> MOVIE TITLE, DIRECTOR NUM, DIR NAME
DIRECTOR_NUM >
DIR NAME
Answers
The problem involves analyzing given tables and identifying their normal form, dependencies, and transforming them to 3NF if necessary.
What is the explanation for the above response?
1) a. UNF (contains a repeating group)
b.
STUDENT SSN > ST_NAME, MAJOR, ADVISOR NUM, ST CREDITHRS, CLASS STANDING
ADVISOR NUM > ADV_NAME, ADV OFFICE, ADV PHONE
STUDENT SSN is the primary key of the table.
c.
1NF:
STUDENT (STUDENT SSN, ST_NAME, MAJOR, ADVISOR NUM, ST CREDITHRS, CLASS STANDING)
ADVISOR (ADVISOR NUM, ADV_NAME, ADV OFFICE, ADV PHONE)
2)
a. 1NF
b.
MOVIE NUM > MOVIE TITLE
STAR NUM > STAR NAME
MOVIE NUM, STAR NUM is the primary key of the table.
c.
1NF:
MOVIE_STAR (MOVIE NUM, STAR NUM)
STAR (STAR NUM, STAR NAME)
MOVIE (MOVIE NUM, MOVIE TITLE)
3)
a. 3NF
b.
MOVIE NUM > MOVIE TITLE
DIRECTOR NUM > DIR NAME
MOVIE NUM is the primary key of the table.
c.
The given table is already in 3NF, so no transformation is needed.
Learn more about tables at:
https://brainly.com/question/3355185
#SPJ1
please help me social media marketing
Answers
53. A correct definition of Computer is_____
a. All of the options
b. Computer is a machine or device that can be programmed to perform arithmetical or logic operation sequences automatically
c. Computer understands only binary language which is written in the form of Os &, 1s
d. Computer is a programmable electronic device that stores, retrieves, and processes the data
Answers
Answer:
D
Explanation:
d. Computer is a programmable electronic device that stores, retrieves, and processes the data.
what is the data type name for integer?
Answers
Answer:
the data type name for integer is int
Hope This Helps!!!
Explanation:
the integer data type ( int ) is used to represent whole numbers that can be stored within 32-bits. The big integer data type ( bigint ) is used to represent whole numbers that are outside the range of the integer data type and can be stored within 64 bits.Barbarlee suspected and found a loophole in the university computer's security system that allowed her to access other students' records. She told the system administrator about the loophole, but continued to access others' records until the problem was corrected 2 weeks later. Was her actions unethical or not. Explain your position? What should be the suggested system administrators response to Barbarlee's actions? How should the university respond to this scenario?
Answers
Answer:
Explanation:
I can give you my opinion on the matter, not sure if this was taught to you or not so please take it with a grain of salt.
Her actions are highly unethical and even illegal to some extent. Especially in USA, FERPA prevents random people from accessing your educational records without your permission and there's hundreds of universities with their own rules/regulations on protecting students' privacy. The sys admin should have first recorded this event when she reported it and then actually went into the system to see if unwanted access has been done by any user(s). University should look at disciplinary actions since the person willingly accessed the system even after they reported the bug and also let ALL the university student/faculty/staff know of the problem and how they plan on fixing it.
This is only a summary, and this is my opinion. please expand in places where needed.
I found another answer in go.ogle:
I feel the actions of this person were unethical.
The student's action in searching for the loophole was neither definitively ethical nor unethical, as their motives are unclear.
The student's action in continuing to access records for two weeks was unethical, as this is a violation of privacy.
The system admin's failure to correct the problem could be considered unethical, but it is difficult to surmise, as there are not enough details.
What is the data type of the following variable?
name = "John Doe"
Answers
In computer programming, a variable is a storage location that holds a value or an identifier. A data type determines the type of data that can be stored in a variable. The data type of the following variable, name = "John Doe" is a string data type.
In programming, a string is a sequence of characters that is enclosed in quotes. The string data type can store any textual data such as names, words, or sentences.The string data type is used in programming languages such as Java, Python, C++, and many others. In Python, the string data type is denoted by enclosing the value in either single or double quotes.
For instance, "Hello World" and 'Hello World' are both strings.In conclusion, the data type of the variable name is string. When declaring variables in programming, it is important to assign them the correct data type, as it determines the operations that can be performed on them.
For more such questions on variable, click on:
https://brainly.com/question/28248724
#SPJ8
Help me with this digital Circuit please




Answers
A subset of electronics called digital circuits or digital electronics uses digital signals to carry out a variety of tasks and satisfy a range of needs.
Thus, These circuits receive input signals in digital form, which are expressed in binary form as 0s and 1s. Logical gates that carry out logical operations, including as AND, OR, NOT, NANAD, NOR, and XOR gates, are used in the construction of these circuits.
This format enables the circuit to change between states for exact output. The fundamental purpose of digital circuit systems is to address the shortcomings of analog systems, which are slower and may produce inaccurate output data.
On a single integrated circuit (IC), a number of logic gates are used to create a digital circuit. Any digital circuit's input consists of "0's" and "1's" in binary form. After processing raw digital data, a precise value is produced.
Thus, A subset of electronics called digital circuits or digital electronics uses digital signals to carry out a variety of tasks and satisfy a range of needs.
Learn more about Digital circuit, refer to the link:
https://brainly.com/question/24628790
#SPJ1
Little Italy Pizza charges $14.95 for a 12-inch diameter cheese pizza and $17.95 for a 14-inch diameter cheese pizza. Write the pseudocode for an algorithm that calculates and displays how much each of these earns the establishment per square inch of pizza sold. (Hint: You will need to first calculate how many square inches there are in each pizza.)
Answers
Answer:
Following are the pseudocode to this question:
Declare variables A1, A2, B1, B2, C1,C2
Initialize B1 to 14.95
Initialize B2 to 17.95
Calculate A1=3.14*12*12/4
Calculate A2=3.14*14*14/4
Calculate C1=B1/A1
Calculate C2=B2/A2
PRINT "12 inches pizza earns $"+C1+" PER square inch"
PRINT "14 inches pizza earns $"+C2+" PER square inch"
Explanation:
In the above-given code, six variable "A1, A2, B1, B2, C1, and C2" is declared, in which "B1 and B2" is used for initializing the given value, in the next step "A1, A2, C1, and C2" variable is declared that calculates and store its values and use the print method to print its stored value with the message.
1
Select the correct answer.

Answers
10.8 LAB: Inventory (linked lists: insert at the front of a list) Given main() in the Inventory class, define an insertAtFront() method in the InventoryNode class that inserts items at the front of a linked list (after the dummy head node). Ex. If the input is: 4 plates 100 spoons 200 cups 150 forks 200
the output is: 200 forks 150 cups 200 spoons 100 plates * Inventory.java does not need to be modified.
* All that needs to be done is to define an insertAtFront() method in InventoryNode.java that inserts a node at the front of the linked list, after the dummy head node.
*** Copying the code below to make it easier...
import java.util.Scanner;
public class Inventory {
public static void main (String[] args) {
Scanner scnr = new Scanner(System.in);
InventoryNode headNode;
InventoryNode currNode;
InventoryNode lastNode;
String item;
int numberOfItems;
int i;
// Front of nodes list
headNode = new InventoryNode();
lastNode = headNode;
int input = scnr.nextInt();
for(i = 0; i < input; i++ ) {
item = scnr.next();
numberOfItems = scnr.nextInt();
currNode = new InventoryNode(item, numberOfItems);
currNode.insertAtFront(headNode, currNode);
lastNode = currNode;
}
// Print linked list
currNode = headNode.getNext();
while (currNode != null) {
currNode.printNodeData();
currNode = currNode.getNext();
}
}
}
-----------------------------------------------------------------------------------------
public class InventoryNode {
private String item;
private int numberOfItems;
private InventoryNode nextNodeRef; // Reference to the next node
public InventoryNode() {
item = "";
numberOfItems = 0;
nextNodeRef = null;
}
// Constructor
public InventoryNode(String itemInit, int numberOfItemsInit) {
this.item = itemInit;
this.numberOfItems = numberOfItemsInit;
this.nextNodeRef = null;
}
// Constructor
public InventoryNode(String itemInit, int numberOfItemsInit, InventoryNode nextLoc) {
this.item = itemInit;
this.numberOfItems = numberOfItemsInit;
this.nextNodeRef = nextLoc;
}
// TODO: Define an insertAtFront() method that inserts a node at the
// front of the linked list (after the dummy head node)
// Get location pointed by nextNodeRef
public InventoryNode getNext() {
return this.nextNodeRef;
}
// Print node data
public void printNodeData() {
System.out.println(this.numberOfItems + " " + this.item);
}
}
Answers
The method that inserts an item in front of a linked list after a dummy head node is as shown below public void insert At Front(Inventory Node head Node, InventoryNode currNode) {currNode.nextNodeRef = headNode.nextNodeRef; headNode.nextNodeRef = currNode;}
The insertAtFront() method takes two arguments, headNode and currNode, which are the head node and the current node, respectively, to insert an item at the front of a linked list (after the dummy head node). Here, after initializing currNode and setting its properties, insertAtFront() is called and executed. This method works by reordering the pointers to nodes in a linked list to ensure that the item to be inserted is added after the dummy head node.
To define the insertAtFront() method in the InventoryNode class, you can add the following method inside the InventoryNode class.
Learn more about here:
https://brainly.com/question/30667459
#SPJ4
Which two keys are commonly used to move or insert data?
Select an answer.
Alt and Shift
Ctrl and Shift
Tab and Ctrl
Esc and Shift
Answers
Ctrl and Shift are the two keys that are commonly used to move or insert data. Hence option B is correct.
What is computer system?A computer system is defined as a digital electrical device that can be configured to carry out specific tasks as directed by computer programs. This blog post will focus on four basic computer hardware elements: input devices, processing devices, output devices, and memory devices.
Choose a cell or a range of cells. or mash Ctrl + X. Wherever you wish to relocate the data, choose a cell. or click Ctrl + V. In Excel, Ctrl Shift-Enter facilitates the conversion of the data into an array format with numerous data values.
Thus, Ctrl and Shift are the two keys that are commonly used to move or insert data. Hence option B is correct.
To learn more about computer system, refer to the link below:
https://brainly.com/question/17206337
#SPJ1
how do i get a instant win in 1v1 lol online
Answers
Answer:
you can practice a lot all the day to become a pro, and see videos of how to win ( in the game of the 1v1) and do it and well that
Explanation:
hope it helps
What are web servers used for?
O A. To store webpages
O B. To power computers
O C. To browse the internet
Answers
Answer:
a
Explanation:
A web server is software and hardware that uses HTTP (Hypertext Transfer Protocol) and other protocols to respond to client requests made over the World Wide Web. The main job of a web server is to display website content through storing, processing and delivering webpages to users.
1.The ___________ method adds a new element onto the end of the array.
A.add
B.input
C.append
D.len
2.A(n) ____________ is a variable that holds many pieces of data at the same time.
A.index
B.length
C.array
D.element
3.A(n) ____________ is a piece of data stored in an array.
A.element
B.length
C.array
D.index
4.Where does append add a new element?
A.To the end of an array.
B.To the beginning of an array.
C.To the middle of an array.
D.In alphabetical/numerical order.
5.Consider the following code that works on an array of integers:
for i in range(len(values)):
if (values[i] < 0):
values[i] = values [i] * -1
What does it do?
A.Changes all positives numbers to negatives.
B.Nothing, values in arrays must be positive.
C.Changes all negative numbers to positives.
D.Subtracts one from every value in the array.
6.Which of the following is NOT a reason to use arrays?
A.To quickly process large amounts of data.
B.Organize information.
C.To store data in programs.
D.To do number calculations.
7.Consider the following:
stuff = ["dog", "cat", "frog", "zebra", "bat", "pig", "mongoose"]
"frog" is ____________.
A.an index
B.an element
C.a list
D.a sum
8._____________ is storing a specific value in the array.
A.Indexing
B.Summing
C.Assigning
D.Iterating
9.Consider the following code:
stuff = ["dog", "cat", "frog", "zebra", "bat", "pig", "mongoose"]
print(stuff[3])
What is output?
A.zebra
B.bat
C.frog
D.['dog', 'cat', 'frog', 'zebra', 'bat', 'pig', 'mongoose']
10.Consider the following code:
tests = [78, 86, 83, 89, 92, 91, 94, 67, 72, 95]
sum = 0
for i in range(_____):
sum = sum + tests[i]
print("Class average: " + str((sum/_____)))
What should go in the ____________ to make sure that the code correctly finds the average of the test scores?
A.sum
B.val(tests)
C.len(tests)
D.len(tests) - 1
Answers
Answer:
1. append
2. array
3. elament
4. To the end of an array.
5. Changes all negative numbers to positives.
6. To do number calculations.
7. an elament
8. Assigning
9. zebra
10. len(tests)
Explanation:
got 100% on the test
How do technologies such as virtual machines and containers help improve
operational efficient?
Answers
Answer:
Through the distribution of energy usage across various sites, virtual machines and containers help to improve operational efficiency. A single server can accommodate numerous applications, negating the need for additional servers and the resulting increase in hardware and energy consumption.
Hope this helps! :)
Which type of list is most approprite for giving instructions on how to build a bird
house?
Bucket List
Numbered List
Bulleted List
Marked check list
Answers
Use a bulleted list for unordered items; use a numbered list for ordered items.
What is bulleted list?A bulleted list is an unordered list of items where every item has a graphical bullet. The bullets may be characters of different fonts, as well as graphical icons.Bulleted lists help the author structure the text in a better way - provide a list of application components, list of usage scenarios, etc. When the order of elements is not important and you don't need to refer to a list element later in the text, it's good to use bulleted lists. They help avoid the perception of the elements order importance.When the order of elements is important (instruction steps, list of itemns ordered by importance), you can use a numbered list instead.To learn more about bulleted list refer to:
https://brainly.com/question/26707368
#SPJ1
Yall tryna play gta later? I play on ps4
Answers
Answer:
xbox tho
Explanation:
Answer:
Sure
Explanation:
How does a computer work?
Answers
Answer:
A computer is a Device that can run multiple applications at a time and access the internet where you can find online stores and more also used to make video calls and more.
Package Newton’s method for approximating square roots (Case Study: Approximating Square Roots) in a function named newton. This function expects the input number as an argument and returns the estimate of its square root. The program should also include a main function that allows the user to compute the square roots of inputs from the user and python's estimate of its square roots until the enter/return key is pressed.An example of the program input and output is shown below:Enter a positive number or enter/return to quit: 2 The program's estimate is 1.4142135623746899 Python's estimate is 1.4142135623730951 Enter a positive number or enter/return to quit: 4 The program's estimate is 2.0000000929222947 Python's estimate is 2.0 Enter a positive number or enter/return to quit: 9 The program's estimate is 3.000000001396984 Python's estimate is 3.0 Enter a positive number or enter/return to quit
Answers
The python program that calculates the volume and the square of the volume is as follows
radius = float(input("Radius: "))
volume = (4.0/3.0) * (22.0/7.0) * radius**3
sqrtVolume = volume**0.5
print(f'The volume is {volume} units cubed')
print(f'The square root of that number is {sqrtVolume}')
How to write the program?The complete program written in Python where comments are used to explain each line is as follows
This gets the radius
radius = float(input("Radius: "))
#This calculates the volume
volume = (4.0/3.0) * (22.0/7.0) * radius**3
#This calculates the square root of the volume
sqrtVolume = volume**0.5
#This prints the volume
print(f'The volume is {volume} units cubed')
#This prints the square root of the volume
print(f'The square root of that number is {sqrtVolume}')
Therefore, The python program that calculates the volume and the square of the volume is as follows
radius = float(input("Radius: "))
volume = (4.0/3.0) * (22.0/7.0) * radius**3
sqrtVolume = volume**0.5
Read more about python programs at
brainly.com/question/26497128
#SPJ2