Write a recursive method called method3 that accepts an integer parameter and returns the integer reformed by repeating digits 1 and 2. For example, method3 (123456) will return 11223456 repeating only 1 and 2 and method3 (21) will return 2211. If the number is 0, return 0. You may assume that n is not negative
Answers
Answer:
Explanation:
The following is written in Java and creates only the method3 and returns a new method after doubling all of the 2's and 1's in the input.
public static int method3(int x) {
int finalValue = 0;
String number = String.valueOf(x);
for (int i = 0; i < number.length(); i++) {
if (number.charAt(i) == 1 || number.charAt(i) == 2) {
finalValue += Integer.valueOf(number.charAt(i));
finalValue += Integer.valueOf(number.charAt(i));
} else {
finalValue += Integer.valueOf(number.charAt(i));
}
}
return finalValue;
}
Related Questions
Where Can I Get Actual Microsoft AZ-900 Exam Questions?
Answers
Answer:
Pls check the site "examtopics"
U fill find ur questions there
which creative common license type allows others to use and build upon work non- commercially, provided that they credit the original author and maintain the same licensing.
Answers
Answer:
CC BY-NC-SA
Explanation:
BY ==> credit has to be given to original author
NC ==> non-commercial
SA ==>Share alike ; modified work should be reused under the original license
survey of 100 college students gave the following data: 8 owned a car (C) 20 owned a motorcycle (M) 48 owned a bicycle (B) 38 owned neither a car nor a motorcycle nor a bicycle No student who owned a car, owned a motorcycle 6 marks] How many students owned a bicycle and either a car or a motorcycle?
Answers
Where the above survey was made, the number of students who owned a bicycle and either a car or a motorcycle is 30.
What is the explanation for the above response?Let's denote the number of students who owned a car and a bicycle as C ∩ B, and the number of students who owned a motorcycle and a bicycle as M ∩ B. Then we have:
C = 8 (number of students who owned a car)
M = 20 (number of students who owned a motorcycle)
B = 48 (number of students who owned a bicycle)
C ∪ M ∪ B = 100 (number of students in the survey)
Neither C nor M nor B = 38
C ∩ M = 0 (no student who owned a car also owned a motorcycle)
We can use the formula:
C ∪ M ∪ B = C + M + B - (C ∩ M) - (M ∩ B) - (C ∩ B) + Neither
Plugging in the numbers we have:
100 = 8 + 20 + 48 - 0 - (M ∩ B) - (C ∩ B) + 38
Simplifying:
30 = (M ∩ B) + (C ∩ B)
Therefore, the number of students who owned a bicycle and either a car or a motorcycle is 30.
Learn more about survey at:
https://brainly.com/question/17373064
#SPJ1
Determine the total number of votes and the percentage of the total votes by each candidate. The sample output of your program is shown below. It incudes the winner of the election. Use methods from the System.out stream for your output.

Answers
The program that yeilds the above output is given as follows.
public class VoteCounter {
public static void main(String[] args) {
int candidate1Votes = 500;
int candidate2Votes = 300;
int candidate3Votes = 200;
int totalVotes = candidate1Votes + candidate2Votes + candidate3Votes;
double candidate1Percentage = (double) candidate1Votes / totalVotes * 100;
double candidate2Percentage = (double) candidate2Votes / totalVotes * 100;
double candidate3Percentage = (double) candidate3Votes / totalVotes * 100;
System.out.println("Total votes: " + totalVotes);
System.out.println("Candidate 1 votes: " + candidate1Votes + " (" + candidate1Percentage + "%)");
System.out.println("Candidate 2 votes: " + candidate2Votes + " (" + candidate2Percentage + "%)");
System.out.println("Candidate 3 votes: " + candidate3Votes + " (" + candidate3Percentage + "%)");
}
}How does this work?
In this program,we have three candidates, and the number of votes for each candidate is given.
We calculate the total votes by summing up the votes for all candidates. Then,we calculate the percentage of votes for each candidate by dividing their votes by the total votes and multiplying by 100.
Finally,we use the System.out.println() method to display the total votes and the votes and percentages for each candidate.
Learn more about program:
https://brainly.com/question/23275071
#SPJ1
What are the two common places where files are saved?
O The Documents and The Hard Drive
O The Desktop and The Drawer
O The Desktop and the Documents folder
O The Files and The Desktop
Answers
How do you feel about cyber warfare as it applies to you, and individual? On Busniess?
Answers
Answer:
As an individual, I believe cyber warfare is a serious threat and I take steps to protect myself online. I use strong passwords, two-factor authentication, and other security measures to protect my data and accounts. On a business level, cyber warfare can be even more dangerous, as companies have more valuable data and a larger attack surface. Companies should invest in robust cybersecurity measures, such as firewalls, intrusion detection systems, and encryption, to protect their data and networks.
Explanation:
In C++
Write a simple program to test your Circle class. The program must call every member function at least once. The program can do anything of your choice.
Answers
Answer:
int main() {
Circle* pCircle = new Circle(5.0f, 2, 3);
pCircle->up();
pCircle->down();
pCircle->left();
pCircle->right();
cout << "X: " << pCircle->getx() << endl;
cout << "Y: " << pCircle->gety() << endl;
cout << "Radius: " << pCircle->getRadius() << endl;
pCircle->print();
pCircle->update_radius(4.0f);
if (pCircle->isUnit()) {
cout << "is unit" << endl;
}
pCircle->move_x(10);
pCircle->move_y(10);
}
Explanation:
something like that?
polymorphism enables you to write programs that process objects that share the same superclass as if they were all objects of the superclass
Answers
Programming can be made simpler by using polymorphism, which makes it possible to treat objects that share a superclass directly or indirectly as if they were all instances of the superclass.
What are the various types of polymorphism?In C++, polymorphism refers to when a single object or function behaves differently in various settings. Collate polymorphism and time polymorphism are the two types.
What is the process of polymorphism?In object-oriented programming, the term "polymorphism" refers to a design pattern where classes have various functionalities but share a same interface. The benefit of polymorphic is that because each class is used in the same way, the code employing them does not have to be aware of which class is being used.
To know more about polymorphism visit:
https://brainly.com/question/29850207
#SPJ4
The back panel is the best place for which of the following?
Question 3 options:
charts appropriate for the brochure
main title and purpose of brochure
contact information and maps
touching story about cause
Answers
Answer:
Imma contact info and maps
Explanation:
It's the most reasonable
Answer:
contact information and maps
which of the following is the most appropriate way to write css style for the font family property in html
Answers
Answer:
The answer is c your welcome
you want to ensure that a query recordset is read-only and cannot modify the underlying data tables it references. How can you do that?
Answers
To guarantee that a query's recordset cannot make any changes to the original data tables, the "read-only" attribute can be assigned to the query.
What is the effective method?An effective method to accomplish this is to utilize the "SELECT" statement along with the "FOR READ ONLY" condition. The instruction signifies to the database engine that the query's sole purpose is to retrieve data and not alter it.
The SQL Code
SELECT column1, column2, ...
FROM table1
WHERE condition
FOR READ ONLY;
Read more about SQL here:
https://brainly.com/question/25694408
#SPJ1
Hundreds of endpoints were not updated with the latest OS and patches. Identify an administrative control to remediate outdated operating systems and patches.
Answers
Implementing a regular patch management policy, with a schedule for updating all endpoints and enforcing compliance through configuration management or other tools.
What is patch management policy?Patch management rules are a set of standards that guarantee patching is managed, efficient, and secure. These instructions outline the actions and procedures to be followed when fixing bugs and vulnerabilities. There are several sorts of patches, such as security patches, hotfixes, and service packs.
Patch management is the process of updating software, drivers, and firmware to prevent vulnerabilities. Effective patch management also ensures that systems run at peak performance, increasing productivity.
Learn more about Path Management:
https://brainly.com/question/29744046
#SPJ1
Classify the following into online and offline storage
CD-ROM,Floppy disk,RAM,cache Memory,Registers
Answers
RAM and cache memory are examples of online storage as they provide direct and fast access to data. CD-ROM, floppy disk, and registers are examples of offline storage as they require external devices or are part of the processor's internal storage.
Online Storage:
1. RAM (Random Access Memory): RAM is a type of volatile memory that provides temporary storage for data and instructions while a computer is running. It is considered online storage because it is directly accessible by the computer's processor and allows for fast retrieval and modification of data.
2. Cache Memory: Cache memory is a small, high-speed memory located within the computer's processor or between the processor and the main memory. It is used to temporarily store frequently accessed data and instructions to speed up processing. Cache memory is considered online storage because it is directly connected to the processor and provides quick access to data.
Offline Storage:
1. CD-ROM (Compact Disc-Read-Only Memory): A CD-ROM is a type of optical disc that stores data and can only be read. It is considered offline storage because data is stored on the disc and requires a CD-ROM drive to read the information.
2. Floppy Disk: A floppy disk is a portable storage medium that uses magnetic storage to store data. It is considered offline storage because it requires a floppy disk drive to read and write data.
3. Registers: Registers are small, high-speed storage locations within the computer's processor. They hold data that is currently being used by the processor for arithmetic and logical operations. Registers are considered offline storage because they are part of the processor's internal storage and not directly accessible or removable.
for more questions on memory
https://brainly.com/question/28483224
#SPJ11
The world has entered the threshold of Big Data Control economy and many nations have formed a magnificent digital colony within. The digital firestorm has emerged and weaponization of Data has taken center stage! Nations that control Data today will ultimately control the future. True or false?
Answers
Perfrom traceroute of an ip address in Australia
Answers
How to perform a typical traceroute on an IP address using CMD command is given below:
The StepsIn case you're striving to perform a traceroute operation on an IP address, either using Windows or Mac computer systems, the following guidelines will provide assistance.
Windows users may select the Windows key and R simultaneously, enter "cmd," hit Enter. In comparison, users operating with the Mac OS should navigate through Finder by visiting Applications -> Utilities and double-clicking Terminal.
To get started with the procedure, insert the word "traceroute," and proceed by entering the specific IP address that you desire to locate. Even if searching for information on 203.0.113.1, simply input "traceroute 203.0.113.1." At this stage, submit and wait until the validation is done.
This method ascertains the path taken by packets across the network. It indicates the number of jumps made, along with their response time at every stage. One aspect to bear in mind is some routers/firewalls may block access thereby leading to incomplete outcomes.
Read more about Ip addresses here:
https://brainly.com/question/14219853
#SPJ1
What would game programmers do when decomposing a task in a modular program?
Answers
1. Identify the overall task or feature: Game programmers start by identifying the larger task or feature they want to implement, such as player movement, enemy AI, or collision detection.
2. Analyze the task: They analyze the task to understand its requirements, inputs, and desired outputs. This helps them determine the necessary functionality and behavior.
3. Identify subtasks or components: They identify the subtasks or components that make up the larger task. For example, in the case of player movement, this could involve input handling, character animation, physics simulation, and rendering.
4. Break down the subtasks further: Each subtask can be further decomposed into smaller, more specific functions or modules. For example, input handling might involve separate functions for keyboard input, mouse input, or touch input.
5. Define interfaces: They define clear interfaces between the modules, specifying how they interact and communicate with each other. This helps ensure modularity and maintainability of the code.
6. Implement and test modules: Game programmers then proceed to implement each module or function, focusing on their specific responsibilities. They can test and iterate on these smaller units of functionality independently.
7. Integrate and test the modules: Finally, they integrate the modules together, ensuring they work harmoniously and produce the desired outcome. Thorough testing is conducted to verify that the overall task or feature functions correctly.
By decomposing tasks in this manner, game programmers can effectively manage the complexity of game development, promote code reusability, enhance collaboration, and facilitate the maintenance and future expansion of the game.
When decomposing a task in a modular program, game programmers follow a structured approach to break down the task into smaller, more manageable components.
This process is crucial for code organization, maintainability, and reusability. Here's an outline of what game programmers typically do:
1. Identify the task: The programmer begins by understanding the task at hand, whether it's implementing a specific game feature, optimizing performance, or fixing a bug.
2. Break it down: The task is broken down into smaller subtasks or functions that can be handled independently. Each subtask focuses on a specific aspect of the overall goal.
3. Determine dependencies: The programmer analyzes the dependencies between different subtasks and identifies any order or logical flow required.
4. Design modules: Modules are created for each subtask, encapsulating related code and functionality. These modules should have well-defined interfaces and be independent of each other to ensure reusability.
5. Implement and test: The programmer then implements the modules by writing the necessary code and tests their functionality to ensure they work correctly.
6. Integrate modules: Once individual modules are tested and verified, they are integrated into the larger game program, ensuring that they work together seamlessly.
By decomposing tasks into modules, game programmers promote code organization, readability, and ease of maintenance. It also enables parallel development by allowing different team members to work on separate modules simultaneously, fostering efficient collaboration.
For more such questions on programmers,click on
https://brainly.com/question/30130277
#SPJ8
Is it possible to compare 2 pre-packaged versions in cpi?
Answers
Yes, it is possible to compare two pre-packaged versions in the Consumer Price Index (CPI), but it can be challenging due to certain limitations of the index.
The CPI is designed to measure changes in the overall price level of a basket of goods and services consumed by households.
It focuses on broad categories and representative items within those categories, rather than specific versions of products.
When it comes to pre-packaged versions of products, there can be variations in size, quality, branding, and other attributes that may affect their prices differently.
These variations make direct comparisons complex within the framework of the CPI.
To compare two specific pre-packaged versions within the CPI, it would require detailed data on their specific characteristics and how they align with the representative item in the CPI basket.
This level of granularity may not be readily available in the public domain or within the CPI methodology.
For more questions on Consumer Price Index
https://brainly.com/question/8416975
#SPJ8
What is a copyright?
Answers
the exclusive legal right, given to an originator or an assignee to print, publish, perform, film, or record literary, artistic, or musical material, and to authorize others to do the same.
is co2+4h2--> ch4 + 2h2o a combustion
Answers
Answer:
No its not a combustion its a formation.
Explanation:
Select the correct answer from each drop-down menu.
How would you define the rule of thirds?
The rule of thirds is an important feature of
This rule suggests that you must
This is where you should place the
Reset
Next
portions of text or an image.
Answers
The rule of thirds is an important feature of composition in visual arts, such as photography, painting, and design.
This rule suggests that you must divide an image into nine equal parts by imagining two equally spaced horizontal lines and two equally spaced vertical lines. These lines create four intersection points, known as the power points or points of interest.
This rule emphasizes that you should place the key elements or points of interest in the image along these lines or at the intersection points. By doing so, the composition becomes more visually appealing and balanced. It adds dynamism and guides the viewer's eye through the image, creating a sense of harmony and interest.
The rule of thirds is based on the idea that placing the main subjects or focal points off-center creates a more visually pleasing and engaging composition compared to placing them at the center. It allows for more negative space and encourages the viewer to explore the entire image, rather than focusing solely on the center.
In photography, this rule can be applied to various elements, such as landscapes, portraits, and still life. For example, placing the horizon on one of the horizontal lines rather than in the center can create a more balanced and captivating composition. In portraits, aligning the subject's eyes or face along the vertical lines can enhance the overall visual impact.
In summary, the rule of thirds is a composition guideline that suggests dividing an image into nine equal parts and placing the key elements or points of interest along the lines or at the intersection points. It is a valuable technique used by visual artists to create visually pleasing and well-balanced compositions.
For more questions on visual arts,
https://brainly.com/question/30828226
#SPJ11
5. What are Excel cell references by default?
Relative references
Absolute references
Mixed references
Cell references must be assigned
Answers
Answer: relative references
Explanation:
By default, all cell references are RELATIVE REFERENCES. When copied across multiple cells, they change based on the relative position of rows and columns. For example, if you copy the formula =A1+B1 from row 1 to row 2, the formula will become =A2+B2.
The company is very strongly focused on power users over novice users, moderately focused on standard users over novice users, and moderately focused on power users over standard users. Use the AHP method to determine which feature to select.
Answers
Answer:
Explanation:
To use the AHP (Analytic Hierarchy Process) method, we need to follow these steps:
Step 1: Identify the Goal and Criteria
Goal: Select the feature to focus on
Criteria: Power users, standard users, and novice users
Step 2: Create a Hierarchy
Feature to focus on (Goal)
Power users
Standard users
Novice users
Step 3: Pairwise Comparisons
We need to compare the criteria to each other, using a scale from 1 to 9. The scale represents the importance of one criterion over another.
Power users are very strongly focused on over novice users: 9
Standard users are moderately focused on over novice users: 5
Power users are moderately focused on over standard users: 5
Step 4: Calculate Weights
Using the pairwise comparison results, we can calculate the weights of each criterion.
Power users: 0.707
Standard users: 0.224
Novice users: 0.069
Step 5: Evaluate Alternatives
We need to evaluate the alternatives based on each criterion.
Alternative 1: Feature A
Power users: 0.8
Standard users: 0.6
Novice users: 0.3
Alternative 2: Feature B
Power users: 0.9
Standard users: 0.5
Novice users: 0.2
Step 6: Calculate Scores
We need to calculate the score for each alternative by multiplying the weight of each criterion by its evaluation for the alternative.
Score for Alternative 1: 0.707 x 0.8 + 0.224 x 0.6 + 0.069 x 0.3 = 0.709
Score for Alternative 2: 0.707 x 0.9 + 0.224 x 0.5 + 0.069 x 0.2 = 0.776
Based on the AHP method, Alternative 2 (Feature B) has a higher score and should be selected.
Which four of the following are true about fair use?

Answers
D,C,B
Should be the correct answers. I'm not the best when it comes to copyright but I believe those are correct.
A folder has been shared with other users and set to read only. What does this mean for users?
Answers
Answer:
Its means that other people get to only read your folder. A. Users can only read the name of the shared folder. on edge.
Explanation:
when the tv was created (year)
Answers
Answer:
1927
Explanation:
Answer:
1971 is the year
Type (dog, cat, budgie, lizard, horse, etc.) Create a class that keeps track of the attributes above for pet records at the animal clinic. Decide what instance variables are needed and their data types. Make sure you use int, double, and String data types. Make the instance variables private. Write 2 constructors, one with no parameters and one with many parameters to initialize all the instance variables. Write accessor (get) methods for each of the instance variables. Write mutator (set) methods for each of the instance variables. In the main method of the Animal Clinic class, create 3 Pet objects by calling their constructors. Then call the accessor methods, mutator methods and toString() methods to test all of your methods.
Answers
Answer:
If you did the exercise with two Dog objects, it was a bit boring, right? After all, we have nothing to separate the dogs from each other and no way of knowing, without looking at the source code, which dog produced which bark.
In the previous article, I mentioned that when you create objects, you call a special method called a constructor. The constructor looks like the class name written as a method. For example, for a Dog class, the constructor would be called Dog().
The special thing about constructors is that they are the path to any new object, so they are a great place to call code that initializes an object with default values. Further, the return value from a constructor method is always an object of the class itself, which is why we can assign the return value of the constructor to a variable of the type of class we create.
However, so far, we have not actually created a constructor at all, so how come we can still call that method?
In many languages, C# included, the language gives you a free and empty constructor without you having to do anything. It is implied that you want a constructor; otherwise there would be no way of using the class for anything, so the languages just assume that you have written one.
This invisible and free constructor is called the default constructor, and, in our example, it will look like this:
public Dog(){ }
Notice that this syntax is very similar to the Speak() method we created earlier, except that we do not explicitly return a value nor do we even declare the return type of the method. As I mentioned earlier, a constructor always returns an instance of the class to which it belongs.
In this case, that is the class Dog, and that is why when we write Dog myDog = new Dog(), we can assign the new object to a variable named myDog which is of type Dog.
So let’s add the default constructor to our Dog class. You can either copy the line above or, in Visual Studio, you can use a shortcut: type ctor and hit Tab twice. It should generate the default constructor for you.
The default constructor doesn’t actually give us anything new because it is now explicitly doing what was done implicitly before. However, it is a method, so we can now add content inside the brackets that will execute whenever we call this constructor. And because the constructor runs as the very first thing in an object’s construction, it is a perfect place to add initialization code.
For example, we could set the Name property of our objects to something by adding code such as this:
public Dog()
{
this.Name = "Snoopy";
}
This example will set the Name property of any new objects to “Snoopy”.
Of course, that’s not very useful because not all dogs are called “Snoopy”, so instead, let us change the method signature of the constructor so that it accepts a parameter.
The parentheses of methods aren’t just there to look pretty; they serve to contain parameters that we can use to pass values to a method. This function applies to all methods, not just constructors, but let’s do it for a constructor first.
Change the default constructor signature to this:
public Dog(string dogName)
This addition allows us to send a string parameter into the constructor, and that when we do, we can refer to that parameter by the name dogName.
Then, add the following line to the method block:
this.Name = dogName;
This line sets this object’s property Name to the parameter we sent into the constructor.
Note that when you change the constructor’s signature, you get a case of the red squigglies in your Program.cs file.When we add our own explicit constructors, C# and .NET will not implicitly create a default constructor for us. In our Program.cs file, we are still creating the Dog objects using the default parameter-less constructor, which now no longer exists.
To fix this problem, we need to add a parameter to our constructor call in Program.cs. We can, for example, update our object construction line as such:
Dog myDog = new Dog(“Snoopy”);
Doing so will remove the red squigglies and allow you to run the code again. If you leave or set your breakpoint after the last code line, you can look at the Locals panel and verify that your object’s Name property has indeed been? Got it?
The program that keeps track of the attributes above for pet records at the animal clinic is in explanation part.
What is programming?Making a set of instructions that instruct a computer how to carry out a task is the process of programming. Computer programming languages like JavaScript, Python, and C++ can all be used for programming.
The program can be:
public class Pet {
private String name;
private int age;
private double weight;
private String type;
private String breed;
public Pet() {
}
/**
* param name
* param age
* param weight
* param type
* param breed
*/
public Pet(String name, int age, double weight, String type, String breed) {
this.name = name;
this.age = age;
this.weight = weight;
this.type = type;
this.breed = breed;
}
/**
* return the name
*/
public String getName() {
return name;
}
/**
* param name
* the name to set
*/
public void setName(String name) {
this.name = name;
}
/**
* return the age
*/
public int getAge() {
return age;
}
/**
* param age
* the age to set
*/
public void setAge(int age) {
this.age = age;
}
/**
* return the weight
*/
public double getWeight() {
return weight;
}
/**
* param weight
* the weight to set
*/
public void setWeight(double weight) {
this.weight = weight;
}
/**
* return the type
*/
public String getType() {
return type;
}
/**
* param type
* the type to set
*/
public void setType(String type) {
this.type = type;
}
/**
* return the breed
*/
public String getBreed() {
return breed;
}
/**
* param breed
* the breed to set
*/
public void setBreed(String breed) {
this.breed = breed;
}
/*
* (non-Java)
*
*/
public String toString() {
return "Pet :: Name=" + name + ", age=" + age + ", weight=" + weight
+ ", type=" + type + ", breed=" + breed;
}
}
Thus, this is the program for the given scenario.
For more details regarding programming, visit:
https://brainly.com/question/11023419
#SPJ5
Choose the type of malware that best matches each description.
to be triggered
:infects a computer or system, and then replicates itself, but acts independently and does not need
: tricks the user into allowing access to the system or computer, by posing as a different type of file
infects a computer or system, and then replicates itself after being triggered by the host
Answers
Answer:
B - tricks the user into allowing access to the system or computer, by posing as a different type of file
Answer:
Worm: infects a computer or system, and then replicates itself, but acts independently and does not need to be triggered
Trojan horse: tricks the user into allowing access to the system or computer, by posing as a different type of file
Virus: infects a computer or system, and then replicates itself after being triggered by the host
Explanation:
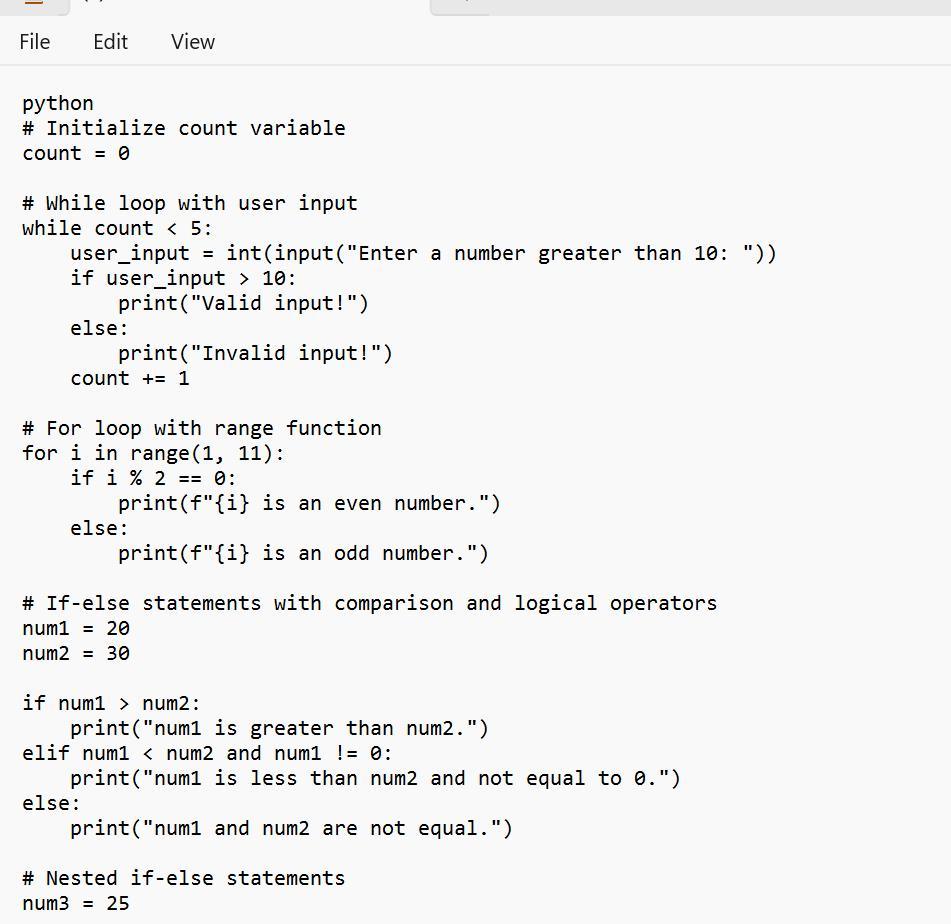
if-else AND if-elif-else
need at minimum two sets of if, one must contain elif
comparison operators
>, <, >=, <=, !=, ==
used at least three times
logical operator
and, or, not
used at least once
while loop AND for loop
both a while loop and a for loop must be used
while loop
based on user input
be sure to include / update your loop control variable
must include a count variable that counts how many times the while loop runs
for loop must include one version of the range function
range(x), range(x,y), or range(x,y,z)
comments
# this line describes the following code
comments are essential, make sure they are useful and informative (I do read them)
at least 40 lines of code
this includes appropriate whitespace and comments
python
Answers
Based on the image, one can see an example of Python code that is said to be able to meets the requirements that are given in the question:
What is the python?The code given is seen as a form of a Python script that tells more on the use of if-else as well as if-elif-else statements, also the use of comparison operators, logical operators, and others
Therefore, one need to know that the code is just a form of an example and it can or cannot not have a special functional purpose. It is one that is meant to tell more on the use of if-else, if-elif-else statements, etc.
Learn more about python from
https://brainly.com/question/26497128
#SPJ1

3.16 (Gas Mileage) Drivers are concerned with the mileage obtained by their automobiles. One driver has kept track of several tankfuls of gasoline by recording miles driven and gallons used for each tankful. Develop a program that will input the miles driven and gallons used for each tankful. The program should calculate and display the miles per gallon obtained for each tankful. After processing all input information, the program should calculate and print the combined miles per gallon obtained for all tankfuls. Here is a sample input/output dialog:
Answers
Answer:
I am writing a C program.
#include <stdio.h> // for using input output functions
#include <stdbool.h> // for using a bool value as data type
int main() { // start of the main() function body
int count=0; //count the number of entries
double gallons, miles, MilesperGallon, combined_avg, sum; //declare variables
while(true) {// takes input gallons and miles value from user and computes avg miles per gallon
printf( "Enter the gallons used (-1 to stop): \n" ); //prompts user to enter value of gallons or enter -1 to stop
scanf( "%lf", &gallons );//reads the value of gallons from user
if ( gallons == -1 ) {// if user enters -1
combined_avg = sum / count; //displays the combined average by dividing total of miles per drives to no of entries
printf( "Combined miles per gallon for all tankfuls: %lf\n", combined_avg ); //displays overall average value
break;} //ends the loop
printf( "Enter the miles driven: \n" ); //if user does not enter -1 then prompts the user to enter value of miles
scanf( "%lf", &miles ); //read the value of miles from user
MilesperGallon = miles / gallons; //compute the miles per gallon
printf( "The miles per gallon for tankful: %lf\n", MilesperGallon ); //display the computed value of miles per gallon
sum += MilesperGallon; //adds all the computed miles per gallons values
count += 1; } } //counts number of tankfuls (input entries)
Explanation:
The program takes as input the miles driven and gallons used for each tankful. These values are stored in miles and gallons variables. The program calculates and displays the miles per gallon MilesperGallon obtained for each tankful by dividing the miles driven with the gallons used. The while loop continues to execute until the user enters -1. After user enters -1, the program calculates and prints the combined miles per gallon obtained for all tankful. At the computation of MilesperGallon for each tankful, the value of MilesperGallon are added and stored in sum variable. The count variable works as a counter which is incremented to 1 after each entry. For example if user enters values for miles and gallons and the program displays MilesperGallon then at the end of this iteration the value of count is incremented to 1. This value of incremented for each tankful and then these values are added. The program's output is attached.

Explain how data is represent in the computer system
Answers
Explanation:
Computers use binary - the digits 0 and 1 - to store data. A binary digit, or bit, is the smallest unit of data in computing. It is represented by a 0 or a 1. Binary numbers are made up of binary digits (bits), eg the binary number 1001.