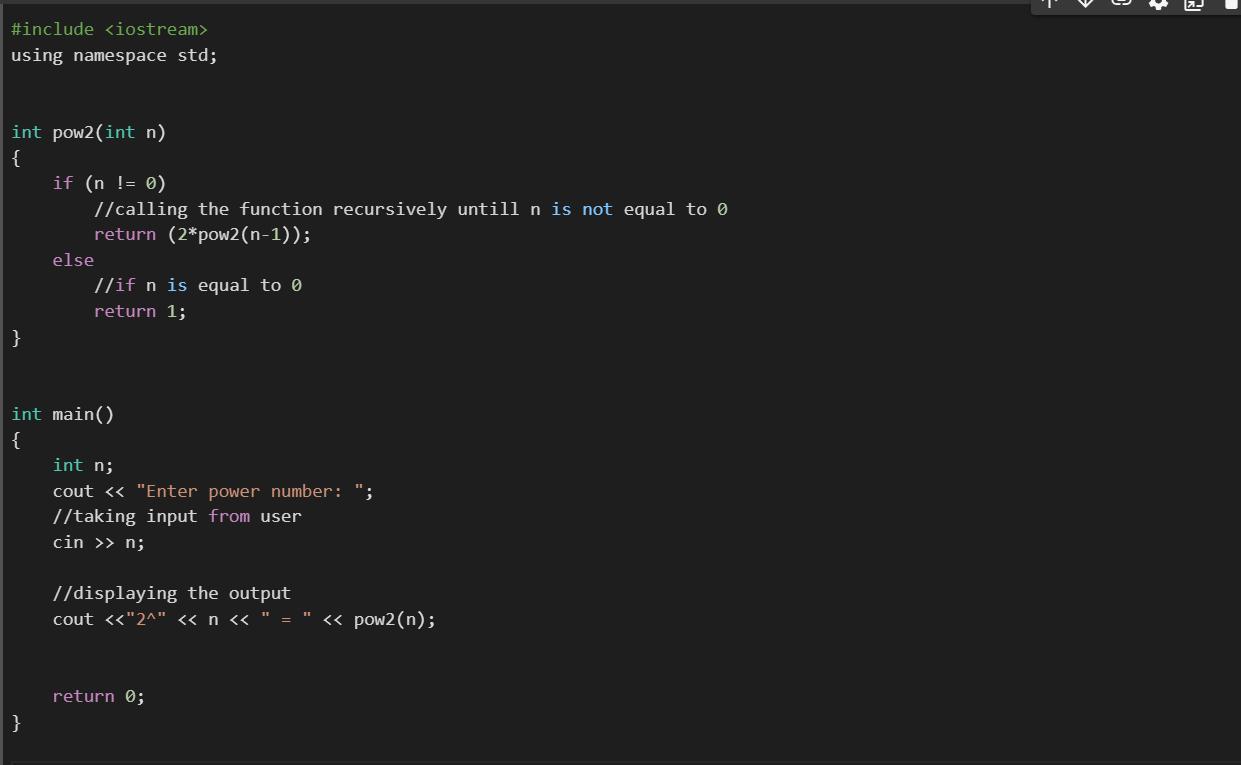
write a recursive function that receives as input an integer n and returns the answer 2n. you can assume n 0 int pow2(int n) {
Answers
Using the knowledge of computational language in C++ it is possible to write a code that write a recursive function that receives as input an integer n and returns the answer 2n.
Writting the code:#include <iostream>
using namespace std;
int pow2(int n)
{
if (n != 0)
//calling the function recursively untill n is not equal to 0
return (2*pow2(n-1));
else
//if n is equal to 0
return 1;
}
int main()
{
int n;
cout << "Enter power number: ";
//taking input from user
cin >> n;
//displaying the output
cout <<"2^" << n << " = " << pow2(n);
return 0;
}
See more about C++ at brainly.com/question/12974523
#SPJ1
Related Questions
Approximately how much bigger (how many more bytes) is a megabyte than a kilobyte?A. 1,000 timesB. 100,000 timesC. 1,000,000 timesD. 1,000,000,000 times
Answers
The correct option is C. A megabyte is approximately 1,000,000 times bigger (has 1,000,000 more bytes) than a kilobyte.
What are some other units of digital information storage commonly used besides kilobytes and megabytes?A kilobyte (KB) is a unit of digital information storage that is equal to 1,024 bytes. A megabyte (MB), on the other hand, is a unit of digital information storage that is equal to 1,000,000 bytes. Therefore, a megabyte is approximately 1,000,000 times bigger than a kilobyte.
This is because the prefix "kilo" represents a multiplier of 1,024 (2^10) and the prefix "mega" represents a multiplier of 1,000,000 (10^6). In computing, these prefixes are commonly used to represent different units of digital information storage, such as kilobytes, megabytes, gigabytes, and so on. It's important to note that these units are not exact measurements, as there may be slight variations in the actual amount of storage capacity due to different measurement systems and algorithms used by different devices and software. However, in general, a megabyte is significantly larger than a kilobyte, and this difference is important to consider when dealing with large amounts of data.
To know about megabyte and kilobyte more visit:
https://brainly.com/question/3288094
#SPJ11
PLS HELP!!
In two to three paragraphs, come up with a way that you could incorporate the most technologically advanced gaming into your online education.
Make sure that your paper details clearly the type of game, how it will work, and how the student will progress through the action. Also include how the school or teacher will devise a grading system and the learning objectives of the game. Submit two to three paragraphs.
Answers
Incorporating cutting-edge gaming technology into web-based learning can foster an interactive and stimulating educational encounter. A clever method of attaining this goal is to incorporate immersive virtual reality (VR) games that are in sync with the topic being taught
What is the gaming about?Tech gaming can enhance online learning by engaging learners interactively. One way to do this is by using immersive VR games that relate to the subject being taught. In a history class, students can time-travel virtually to navigate events and interact with figures.
In this VR game, students complete quests using historical knowledge and critical thinking skills. They may solve historical artifact puzzles or make impactful decisions. Tasks reinforce learning objectives: cause/effect, primary sources, historical context.
Learn more about gaming from
https://brainly.com/question/28031867
#SPJ1
Mariella is trying to explain the concept of a variable to her sister who is new to programming. Which of the following analogies should Mariella use to help her sister understand?
A.
a car that uses gas
B.
a boy that walks his dog
C.
a box that holds mail
D.
a banana that is overripe
Answers
Mariella can help her sister understand the concept of a variable by equating it to a box that contains mail.
How can she do this?The same way a box can carry distinct mail types and permit amendments to their content, variables are also capable of accommodating diverse data types while permitting modification amidst program execution.
Option A (a car dependent on gas) could suffice in explaining dependencies or requirements; however, it fails when attempting to clarify the variable concept.
Option B (a boy walking his dog) does not relate to the variable definition.
Finally, Option D (an overripe banana) may be used to illustrate state and conditions but falls short when applied out of context as an explanation of the variable concept.
Read more about programs here:
https://brainly.com/question/1538272
#SPJ1
I need help please hurry!!!!!!! jay works in the it department. his main responsibility at work is to keep all equipment working. he needs to know what maintenance to perform and when. he should _____.
inventory all equipment
copy the user's manual and distribute it to all the employees
read the manuals
update the software in the office
establish the frequency of maintenance tasks
identify individuals to complete the tasks
set up auto reminders
list the maintenance tasks
create a log to document maintenance
Answers
Jay is employed with the it division. Maintaining the functionality of all equipment is his primary duty at work. He must understand what upkeep to execute and when to decide to perform maintenance.
He needs to decide how often to perform maintenance. The number of jobs that must be completed in a certain amount of time is referred to as maintenance frequency. Its periodicity can also vary based on the set time, from daily to weekly. Work equipment comprises a working platform, fall arrest devices, and any gear, computers, apparatus, tools, or installations used exclusively or mostly for work-related purposes. Task analysis examines how a task is carried out and includes a thorough description of both manual and mental processes, the lengths of the task and its elements, and task frequency.
Learn more about computers here
https://brainly.com/question/20414679
#SPJ4
what is the difference between internal and external network
Answers
An internal network, also known as a private network, is a network that is only accessible by devices within the same physical location, such as a home or office. These networks are typically protected by a firewall and are not directly accessible from the internet.
An external network, also known as a public network, is a network that is accessible by anyone with an internet connection, such as the internet itself.
What is the external network about?The external network networks are not protected by a firewall and are directly accessible from the internet.
In summary, internal network is a network which is protected and only accessible by devices within the same location, while external network is a network which is open to public and not protected by firewall, which is accessible by anyone with an internet connection.
Learn more about external network from
https://brainly.com/question/13139335
#SPJ1
_____are attempts by individuals to obtain confidential information from you by falsifying their identify. ... A. Phishing trips · B. Computer viruses
C. Spyware scams D. Phishing scams
Answers
The correct answer is D. Phishing scams. Phishing scams are attempts by individuals to obtain confidential information from you by falsifying their identity.
These scams typically involve sending fraudulent emails or creating fake websites that appear to be legitimate in order to trick individuals into providing sensitive information such as login credentials, credit card numbers, or social security numbers. It is important to be vigilant and cautious when receiving emails or browsing the internet to avoid falling victim to these types of scams. Always verify the authenticity of any requests for sensitive information before providing it, and use security software to protect your devices from potential threats.
Phishing scams are attempts by individuals to obtain confidential information from you by falsifying their identity. These scams typically involve deceptive emails or messages that appear to be from legitimate sources, encouraging you to reveal sensitive information like passwords or credit card numbers. To avoid falling victim to phishing scams, always be cautious when clicking on links or providing personal information online, and use security measures such as spam filters and firewalls to protect your devices.
To know more about Phishing scams visit:-
https://brainly.com/question/31216789
#SPJ11
based on a​ poll, ​% of internet users are more careful about personal information when using a public​ wi-fi hotspot. what is the probability that among randomly selected internet​ users, at least one is more careful about personal information when using a public​ wi-fi hotspot? how is the result affected by the additional information that the survey subjects volunteered to​ respond?
Answers
Based on Craik and Lockhart's levels of processing memory model, the following information about dogs can be arranged from the shallowest to the deepest encoding:
Physical Characteristics: This refers to surface-level information about the appearance of dogs, such as their size, color, or breed. It involves shallow processing as it focuses on perceptual features.Category Membership: Categorizing dogs as animals and classifying them as mammals would involve a slightly deeper level of processing compared to physical characteristics. It relates to understanding the broader category to which dogs belong.Semantic Information: This includes knowledge about dogs in terms of their behavior, traits, habits, or general characteristics. It involves a deeper level of processing as it requires understanding the meaning and concept of dogs.Personal Experiences and Emotional Connections: This level of processing involves encoding information about dogs based on personal experiences, emotions, and connections. It is the deepest level of processing as it connects the information to personal relevance and significance.
To know more about memory click the link below:
brainly.com/question/27116776
#SPJ11
The complete questions is :Question: Based On A Poll, 64% Of Internet Users Are More Careful About Personal Information When Using A Public Wi-Fi Hotspot. What Is The Probability That Among Four Randomly Selected Internet Users, At Least One Is More Careful About Personal Information When Using A Public Wi-Fi Hotspot? How Is The Result Affected By The Additional Information That The Survey
there are certain pieces of data that must be collected in order to meet promoting interoperability (meaningful use) requirements. which data element below does that?
Answers
To meet Promoting Interoperability (Meaningful Use) requirements, the following data elements must be collected:Immunization registry data syndromic surveillance dataReportable laboratory resultsPublic health surveillance dataClinical quality measures (CQMs)Patient-generated health data (PGHD)Health Information Exchange (HIE)The correct option is Clinical quality measures (CQMs).
Clinical quality measures (CQMs) are a subset of clinical data that is collected to demonstrate that appropriate care was provided to patients. These data elements must be collected to meet Promoting Interoperability (Meaningful Use) requirements.
Learn more about Clinical quality measures :https://brainly.com/question/29800937
#SPJ11
Which word should a programmer use to describe what should happen when the condition of an if statement is NOT met?
A.
iterative
B.
when
C.
else
D.
also
Answers
The word that should a programmer use to describe what should happen when the condition of an if statement is NOT met is option C. else.
Why are conditional statements used in programming?When a condition is true or false, a conditional statement instructs a program to take a certain action. If-then or if-then-else statements are frequently used to represent it. The preceding example is a block of code that employs a "if/then" conditional statement.
Therefore, the else statement is used, "to indicate what should happen when the condition of an if statement is not fulfilled," is the proper response since the otherwise statement is typically used when computations are still necessary when a condition in an if and else-if statement is not met.
Learn more about programmer from
https://brainly.com/question/22654163
#SPJ1
What important information is examined in the ethernet frame header by a layer 2 device in order to forward the data onward?.
Answers
An important information that is examined in the ethernet frame header by a layer 2 device in order to forward the data onward is option C: destination MAC address.
Is MAC address source or destination?The use of the addresses in the Datalink layer header, a Layer 2 switch locates the destination device in a Local Area Network (LAN) (where the data needs to be sent). The addresses put at the Datalink layer header are MAC addresses, as can be seen from the Datalink layer Frame structure.
The Layer 2 device, such as a switch, utilizes the destination MAC address to decide which port or interface to use to send the data on to the final destination.
The MAC ID of the device that transmitted the packet serves as the source, and the MAC ID of the device that is supposed to receive it serves as the destination.
Learn more about destination MAC address from
https://brainly.com/question/27911999
#SPJ1
What important information is examined in the Ethernet frame header by a Layer 2 device in order to forward the data onward?
source MAC address
source IP address
destination MAC address
Ethernet type
destination IP address
How is 69.50% is a C when 69% is a D?
Answers
Answer:
below
Explanation:
69.5% is probably the minimum amount needed to get a C while anything below that to a certain extent is a D. For example, a 59.5% - 69.49% might be a D.
Anyway, 69% is lower than 69%, so it make sense why it would be a D
First, simulate 10,000 bootstrap resamples of the average star ratings. For each bootstrap resample, calculate the resample mean and store the resampled means in an array called resample_star_ratings . Then, plot a histogram of the resampled means. resample_star_ratings = make_array ( ) for i in np. arange (10000) : resample = . . . resample_avg_rating = . .. resample_star_ratings = . .. # Do NOT change these lines. Table( ) . with_column( "Average Star Ratings of Reviews in Resamples", resample_star_ratings ) . hist ("Average Star Ratings of Reviews in Resamples", bins = np. arange(4, 5.01, 0.1))
Answers
The provided code snippet demonstrates how to perform a bootstrap resampling of average star ratings and plot a histogram of the resampled means.
The provided code snippet demonstrates how to perform a bootstrap resampling of average star ratings and plot a histogram of the resampled means.
1. The array `resample_star_ratings` is initialized to store the resampled means.
2. A loop iterates 10,000 times using `np.arange(10000)` to perform the bootstrap resampling process.
3. Within each iteration, the specific steps for resampling and calculating the resampled average rating are missing from the code snippet provided (`resample` and `resample_avg_rating`). These steps would involve randomly selecting samples from the original dataset with replacement and computing the mean of the resampled data.
4. After calculating the resampled average rating, it should be stored in the `resample_star_ratings` array using the appropriate method (e.g., `resample_star_ratings = np.append(resample_star_ratings, resample_avg_rating)`).
5. Finally, the histogram is plotted using `Table().with_column().hist()` function. The `hist()` function takes the column name containing the resampled means, specified as "Average Star Ratings of Reviews in Resamples". The `bins` parameter determines the bin range and spacing for the histogram, specified as `bins = np.arange(4, 5.01, 0.1)`.
Note: Since the specific code for resampling and calculating the resampled average rating is missing, the provided code snippet cannot be run as-is. You need to complete the missing parts to perform the bootstrap resampling and obtain accurate results.
Learn more about histogram:
https://brainly.com/question/25983327
#SPJ11
(a) Contruct instruction to load the 16-bit number 2036H in the register pair DE using LXI and MVI opcodes and explain the difference between the two instructions. (5 marks)
Answers
Here are the instructions to load the 16-bit number 2036H in the register pair DE using LXI and MVI opcodes and an explanation of the difference between the two instructions: Instruction using LXI opcode: LD DE, 2036HLXI instruction is used to load 16-bit data into a register pair.
LXI opcode is used to initialize the registers BC, DE, and HL with 16-bit data. The instruction has a format of LXI RP, data16. Here RP represents register pair (BC, DE, HL or SP) and data16 represents the 16-bit data.Instruction using MVI opcode:LD E, 36HLD D, 20HMVI instruction is used to load 8-bit data into a register. The instruction has a format of MVI R, data8. Here R represents the destination register and data8 represents the 8-bit data that will be loaded into the register.
The difference between the two instructions is that the LXI opcode is used to load 16-bit data into a register pair while the MVI opcode is used to load 8-bit data into a single register. Additionally, the LXI opcode requires two bytes of memory to store the 16-bit data while the MVI opcode only requires one byte of memory to store the 8-bit data.
To know more about 16-bit data visit:
https://brainly.com/question/31325908
#SPJ11
Ginny is about to rent a movie online and is trying to decide which resolution will give her the best viewing experience. She plans to watch the video on her laptop, which offers a display resolution of up to 1920 x 1080. Which video resolution should Ginny select
Answers
The resolution Ginny should select is FHD.
What is the video resolution?In technology, the term video resolution refers to the number of pixels per frame. This is important because the number of pixels affects how clear and detailed images are in the video. More common video resolutions are:
HD8K4K720 pHow to select the best resolution?The resolution you select for the video should match the resolution the display offers. In the case of Ginny, a 1920 x 1080 resolution matches an FHD or Full High Definition resolution that has exactly the same values, so this is the best resolution Ginny can choose.
Learn more about Full High Definition in: https://brainly.com/question/5641128
How might a company gain followers on Twitter?
Answers
what might be some challenges if you’re trying to design a product for someone
Answers
Answer:
failure
Explanation:
if someone dosnt like it
Which of the following is not one of the challenges posed by international networks, including the Internet? A. Quality of service B. Costs and tariffs C. Security D. Network management E. Differences in Internet protocols
Answers
Correct option is A. Quality of service,it is not one of the challenges posed by international networks, including the Internet.
How do international networks not pose a challenge in terms of quality of service?Quality of service (QoS) is not one of the challenges posed by international networks, including the Internet. QoS refers to the ability of a network to deliver reliable and predictable performance, such as low latency, high bandwidth, and minimal packet loss.
While QoS is important in many network environments, it is not typically considered a significant challenge in international networks.
On the other hand, challenges such as costs and tariffs, security, network management, and differences in Internet protocols are commonly encountered in international networks.
International networks often involve complex billing structures, regulatory frameworks, and varying pricing models, which can pose challenges in terms of cost management and tariff negotiations.
Security is a critical concern in international networks due to the diverse range of cyber threats and the need to protect sensitive data during transmission.
Network management becomes challenging due to the physical distance, diverse infrastructure, and varying technical standards across different countries.
Finally, differences in Internet protocols can hinder interoperability and require careful consideration when establishing connections between networks with varying protocols.
Learn more about Quality of service
brainly.com/question/15295852
#SPJ11
complete the following program, which displays the number of minutes in equivalent hours:minutes format.
Answers
Considering the available options, the route that would be used to forward a packet with a source IP address of 192.168.10.1 and a destination IP address of 10.1.1.1 is "O 10.1.1.0/24 [110/65] via 192.168.200.2, 00:01:20, Serial0/1/0"
What is Route in IP address?IP routing generally transmits packets from one network to another host on another remote network.
The process of IP routing involves evaluating routing tables to specify the following hop address of the packet that should be sent.
Therefore, Considering the available options, the route that would be used to forward a packet with a source IP address of 192.168.10.1 and a destination IP address of 10.1.1.1 is "O 10.1.1.0/24 [110/65] via 192.168.200.2, 00:01:20, Serial0/1/0"
Learn more about IP Routing here:
brainly.com/question/6991121
#SPJ1
a small group of travelers is meeting inside an ancient building, and the travelers need access to the internet using their mobile devices. however, the group is in an area where wi-fi internet is not available and cellular coverage is intermittent. one of the travelers has an unlimited cellular data plan and a strong consistent signal. which of the following methods would most likely be implemented to provide internet service to the group?
Answers
The method that would most likely be implemented to provide internet service to the group is known as a Mobile hotspot.
What is the significance of mobile hotspots?The significance of a mobile hotspot is determined by the fact that it is a portable hotspot on your phone that lets you share your high-speed data to connect more devices to the internet in more places—all powered by our nationwide network.
According to the context of this question, the range of mobile hotspots may vary from 7-20 meters or sometimes more than that depending on the frequency level of the connection. It allows the mobile devices of other people to make connections with yours and enjoy high-speed data.
Therefore, the method that would most likely be implemented to provide internet service to the group is known as a Mobile hotspot.
To learn more about the Mobile hotspot, refer to the link:
https://brainly.com/question/15191618
#SPJ1
Why does a bus topology require a terminator
Answers
Answer:The purpose of the terminator is to absorb signals so that they do not reflect back down the line
Explanation:
The answer is-
B.) because otherwise the packets will bounce back and forth from end to end repeatedly
Bus topology can be regarded as a kind of topology for a Local Area Network, it is one that has it's nodes connected to a single cable(backbone) and any break in the so called backbone, there will be failure in the entire segment. However a Terminator is usually attached to the end-points of a bus network so that the signal is absorbed by the Terminator and as a result of this the signal will not reflect back down the line. If there is no Terminator there would be bouncing back and forth of packet in an endless loop.It should be noted that a bus topology require a terminator because otherwise the packets will bounce back and forth from end to end repeatedly
Write a function that takes the name of a file with a .csv extension (a comma-separated value file), and writes a new file that is equivalent (same name and same data) but with a .tsv extension (a tab-separated value file: like a CSV but with tabs instead of commas separating the elements of the file). Note: the character used to represent a tab is ‘\t’.
Answers
Answer:
import pandas as pd
def convert_to_tsv( csv_filename ):
df = pd.read_csv("csv_file")
df.to_csv("csv_filename.tsv", sep='\t')
Explanation:
The python program uses the pandas' module to read in the csv file in the function "convert_to_tsv". The file is saved as a tsv file with the pandas to_csv method and the " sep= '\t' " attribute.
Complete the code to finish this program to analyze the inventory for a store that sells purses and backpacks.
Each record is composed of the catalog number, the type of item, its color, the length, width, height, and the quantity in stock.
Sample rows of the file are bel[w.
234 purse,blue, 12,4,14,10
138,purse,red, 12.4.14,4
934, backpack, purple, 25,10,15,3
925, backpack,green 25,10,15,7
Answers
Answer:
import csv
fileIn = open("data/bags.txt","r")
countPurse = 0
textFile= csv.reader(fileIn)
for bag in textFile:
if bag[ 1 ] == 'purse':
countPurse = countPurse + int(bag[6])
fileIn.close()
print("Number of purses:",countPurse)
Explanation:
I hope this helps!
Using guarded equations, implement a function myInsert that behaves the same way as the insert function defined in Data. List package. The Data. List. Insert function takes an element and a list and inserts the element into the list at the first position where it is less than or equal to the next element. In particular, if the list is sorted before the call, the result will also be sorted.
myInsert : : Ord a â a â [a]â a[a]
a. Explain your nylnsert function definition.
b. Using nylnsert and foldr, implement insertion sort (named mySort).
nySort : : Ord a â a â [a]â a[a]
c. Explain how your nySort works when it is applied as below. Your explanation should be closely related to how foldr works.
nySort [3,1,4,2,5]
Answers
Sorting involves arranging a set of elements in a particular order (ascending or descending)
The insert functionThe insertion sort function written in Python, where comments are used to explain each line is as follows:
#This defines the function
def mySort(myList):
#This iterates through the list
for i in range(1, len(myList)):
#This gets the current element
currElem = myList[i]
#This gets the index of the previous element
j = i - 1
# This compares the adjacent elements, and rearrange them (if needed)
while j >= 0 and currElem < myList[j]:
myList[j + 1] = myList[j]
j = j - 1
# This places the current element after a smaller element
myList[j + 1] = currElem
Read more about sorting techniques at:
https://brainly.com/question/15263760
Make Your Own Flowchart
Answers
Answer:
https://encrypted-tbn0.gstatic.com/images?q=tbn:ANd9GcS5V59B3u23rfG-bXj8jNoV7rXfV62cyPnkcg&usqp=CAU
an example of a flow chart
Explanation:
can someone give me an window blur code in javascript like i mean full coding
Answers
Answer:
uh wha- what?!?!
Explanation:
no
find it urself
:P
jekqfjewil bored anyways
Which type of testing is used to test how well the system will perform with a workload?
Integration testing
performance testing
unit testing
acceptance testing
Answers
Answer:
Performance Testing
Explanation:
The Correct option is - Performance Testing
Reason -
INTEGRATION TESTING is a level of software testing where individual units / components are combined and tested as a group. The purpose of this level of testing is to expose faults in the interaction between integrated units.
PERFORMANCE TESTING is a testing measure that evaluates the speed, responsiveness and stability of a computer, network, software program or device under a workload.
UNIT TESTING is a type of software testing where individual units or components of a software are tested. The purpose is to validate that each unit of the software code performs as expected.
Acceptance testing, a testing technique performed to determine whether or not the software system has met the requirement specifications.
How do i cancel my subscription please help it doesnt say cancel anywhere todays the last day of my free trial help
Answers
Answer:
The answer is "turn off auto-renewal"
Explanation:
In the given question it is not defined, which type of subscription it is taking about. so, we assume, it is talking about software subscription and the cancellation of the software can be defined as follows:
The application base subscription provides a monthly or yearly service license scheme, which allows customers to purchase the cost per user. In general, users were also obligated to claim for there initial fee soon, which also enables it to use the software and by disabling the auto-renewal option we can cancel our subscription.What is the purpose of a Post Mortem Review? (5 points)
Answers
Answer:
The interpretation of the discussion is characterized throughout the explanation portion below.
Explanation:
A post-mortem investigation, as well widely recognized as the autopsy, has become a post-mortem assessment of that same body. This same goal of some kind of post-mortem should be to investigate what happened. Post-mortems have been performed by pathologists (Physicians specializing in considering the mechanisms as well as tends to cause including its illness).
a data analyst is working at a small tech startup. they’ve just completed an analysis project, which involved private company information about a new product launch. in order to keep the information safe, the analyst uses secure data-erasure software for the digital files and a shredder for the paper files. which stage of the data life cycle does this describe?
Answers
The stage of the data life cycle which the information provided describes is: destroy.
What is DBLC?DLC is an abbreviation for data life cycle and it can be defined as a strategic methodology that defines the sequence of stages that a given unit of data goes through from inception (collection) to its eventual deletion (destruction) at the end of its useful life.
In Computer technology, there are six (6) steps in a data life cycle and these include the following:
PlanCaptureManageAnalyzeArchiveDestroyBased on the information provided, we can reasonably infer and logically deduce that stage of the data life cycle which is being described is destroy because the analyst used a secure data-erasure software for the digital files and a shredder for the paper files.
Read more on data life cycle here: https://brainly.com/question/28039445
#SPJ4
in most large and medium-sized companies, a(n) within the it department is responsible for providing user support.
Answers
In most large and medium-sized companies, a help desk, or information center, within the IT department is responsible for providing user support.
What is information technology (IT)?Information technology (IT) can be defined as a field in computer science that typically deals with the use of computer systems to generate, process, store, retrieve, and exchange different types of electronic data and information over a secured network.
In most large and medium-sized business organizations (companies), a help desk or information center, within the Information technology (IT) department is saddled with the responsibility of providing user support to the members working there.
Learn more about information technology here: brainly.com/question/14426682
#SPJ1
Complete Question:
In most large and medium-sized companies, a help desk, or ____, within the IT department is responsible for providing user support.
A: resource center
B: portal
C: information center
D: technology center