write a python program that asks users to input a 6-digit integer. the program will then separate the integer into individual digits. print the digits out and separate them by the hyphen ( - ) character using string slicing
Answers
```python
# Prompt user for a 6-digit integer
num = input("Enter a 6-digit integer: ")
# Check if the input has exactly 6 digits
if len(num) == 6:
# Separate the digits using string slicing
digits = num[0] + '-' + num[1] + '-' + num[2] + '-' + num[3] + '-' + num[4] + '-' + num[5]
# Print the separated digits
print("Separated digits:", digits)
else:
print("Invalid input. Please enter a 6-digit integer.")
```
In this program, we use the `input()` function to capture the user's input as a string. We then check if the input has exactly 6 digits using the `len()` function. If it does, we separate the digits by concatenating them with hyphens in between. Finally, we print the separated digits using the `print()` function.
Note that this program assumes the user will provide a valid 6-digit integer as input. If the input may include non-digit characters or be of varying length, additional input validation or error handling should be implemented.
For more such questions on string, click on:
https://brainly.com/question/25324400
#SPJ8
Related Questions
what does a CPU use to temporarily store data
a) buffer
b) track
c) sector
d) cylinder
Answers
Answer:
a) buffer is the right answer
What is the output of the following code? Assume the Rectangle class exists and all the methods called below exist and work as expected.
ArrayList blah = new ArrayList ();
blah.add( new Rectangle(3,5) );
blah.add( new Rectangle(2,15) );
blah.add( new Rectangle(5,5) );
double x=0;
System.out.println(blah.size());
for(Rectangle s: blah) x+=s.area();
System.out.println(x);
Answers
Answer:
3
70.0
Explanation:
There will be 3 elements (Rectangle instances) in the list.
The sum of the areas x will contain 3*5 + 2*15 + 5*5 = 70 and will be printed as a double.
Which of the following is the keyword that should be listed after the hosts statement in the /etc/nsswitch.conf file so that the system will consult the /etc/hosts file to resolve a name to an IP address
Answers
The keyword that should be listed after the hosts statement in the file so that the system will consult the hosts file to resolve a name to an IP address is The files keyword.
What is an IP address?An IP address is known to be a kind of a special address that tells or detect a device that is known to be used on the internet or a local network.
Note that the IP stands for "Internet Protocol," and this is known to be a set or compositions of rules that is said to monitors the format of data sent through the use of the internet or local network
Hence, The files keyword is one that should be listed after the hosts statement in the file so that the system will consult the hosts file to resolve a name to an IP address.
Learn more about IP address from
https://brainly.com/question/24930846
#SPJ1
All _______ that store more than one piece of data
Answers
Answer:All data structure that store more than one piece of data
.
Explanation:
Please help me with my question

Answers
Answer:
1. Template
2. Name of the website
3. Signature of the instructor
.A method is invoked by
a)writing the name of the method followed by a colon and the name
of the calling object
b)writing the name of the calling object followed by a dot and a
list of values in parentheses
c)listing the name of the calling object and the name of the
method inside parentheses
d)writing the name of the calling object, followed by a dot,
followed by the name of the method and a list of values in parentheses
Answers
We can see here that a method is invoked by d) writing the name of the calling object, followed by a dot, followed by the name of the method and a list of values in parentheses.
What is methods?Methods can take parameters, which are variables that are passed into the method when it is called. The parameters are used to provide data to the method, or to receive data from the method. For example, the drive() method might take a parameter that specifies the speed at which the car should drive.
Methods can also return values, which are variables that are returned from the method when it is finished executing. The return value can be used by the code that called the method. For example, the drive() method might return the distance that the car has driven.
Learn more about code on https://brainly.com/question/26134656
#SPJ4
What is the name of an app that filters away internet connections from advertisers and trackers on your smartphone?
Answers
The app is called Disconnect Mobile. It is available for both Android and iOS devices.
The Benefits of Using Disconnect Mobile:An Essential Tool to Protect Your Privacy OnlineNowadays, with the rise of the internet and the digital age, it is becoming increasingly important to protect our online privacy. Advertisers and trackers are constantly looking for ways to access our data and use it for their own benefit. Fortunately, there is a solution to this problem: the Disconnect Mobile app.
Disconnect Mobile is an app that filters away internet connections from advertisers and trackers on your smartphone. It is designed to give users the power to control their online privacy and protect their data from advertisers and trackers. Disconnect Mobile works by blocking and redirecting traffic from ads and trackers which allows users to browse the web without being tracked or targeted. This means that users can browse the web without worrying about their personal data or information being used without their consent.
Learn more about mobile app:
https://brainly.com/question/26052911
#SPJ4
FILL IN THE BLANK a _______ is a generic term used to denote any method for storing certificates and crls so that they can be retrieved by end entities.
Answers
A Certificate Repository is a generic term used to denote any method for storing certificates and CRLs so that they can be retrieved by end entities.
A Certificate Directory is a storage location where digital certificates and certificate revocation lists (CRLs) are stored for retrieval by end entities, which are typically computers or devices that require secure communication. The CD serves as a central repository for digital certificates and CRLs, which allows end entities to quickly and easily access the necessary information for secure communication. CDs are commonly used in public key infrastructure (PKI) systems, which provide a framework for secure communication over the internet.
You can learn more about Certificate Repository at
https://brainly.com/question/31718388
#SPJ11
First Person Who Answers Fast As Possible Will Be Marked As Brainiest
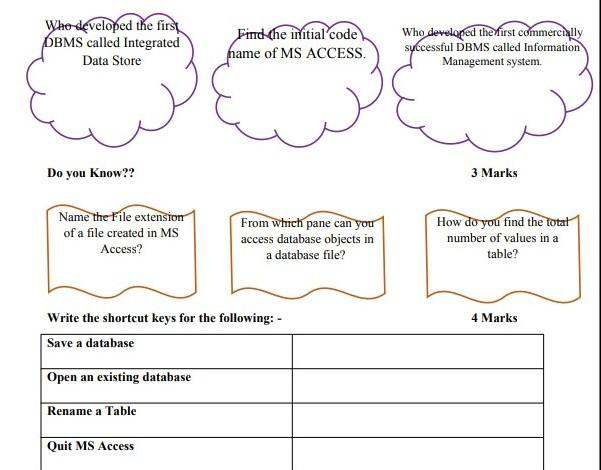
Answers
Answer:
Save a database object Ctrl+S or Shift+F12
Open an existing database Ctrl+O or Ctrl+F12
To quit MS Access ALT+F4
Explanation:
Many services are available via the Internet, and most are made possible by the TCP/IP suite of protocols.
Identify which protocol or Internet-based service is being used in each scenario.
VoIP Elijah uses his laptop to check his work voicemails.
IM Lise chats with her sales team about a new customer outreach initiative.
IRC Michele connects to the Internet at the airport for a few minutes to download any new email messages from work.
SMTP Rex sends an email to his boss updating her on the current status of a complaint from a customer.
POP Tim searches online for casual conversation about his new hobby flying drones.
Answers
VoIP (Voice over Internet Protocol) is used for checking voicemails over the internet, IM (Instant Messaging) is used for chatting with sales team, IRC is used to connect to the internet and download email messages, SMTP (Simple Mail Transfer Protocol) is used for sending emails and POP (Post Office Protocol) is used for searching online for casual conversation.
What are protocols?
Protocols are a set of rules and procedures that govern the communication between two or more devices or systems over a network. In computer networking, protocols define how data is transmitted, received, and processed between devices, and ensure that data is delivered reliably and securely.
There are many different protocols used in computer networking, each with its own specific purpose and function. For example, the Transmission Control Protocol (TCP) is a protocol used for reliable data transmission over the internet, while the Internet Protocol (IP) is used for routing and addressing data packets. Other protocols include HTTP (Hypertext Transfer Protocol) used for web browsing, SMTP (Simple Mail Transfer Protocol) used for email communication, and FTP (File Transfer Protocol) used for transferring files between devices.
Here are the protocols or Internet-based services being used in each scenario:
VoIP - Elijah uses his laptop to check his work voicemails.
IM - Lise chats with her sales team about a new customer outreach initiative.
IRC - Michele connects to the Internet at the airport for a few minutes to download any new email messages from work.
SMTP - Rex sends an email to his boss updating her on the current status of a complaint from a customer.
POP - Tim searches online for casual conversation about his new hobby flying drones.
To know more about internet visit:
https://brainly.com/question/21565588
#SPJ1
Write code which takes a sentence as an input from the user and then prints the length of the first word in that sentence
Answers
Answer:
import java.util.*;
class StringProgram
{
public static void main(String s[])
{
Scanner sc = new Scanner(System.in);
System.out.print("Enter a Sentence: ");
String str= sc. nextInt();
// trim the white spaces at the beginning and at the end.
str = str.trim();
int c=0;
int i=0;
while(str.charAt(i++)!=' ')
++c;
System.out.println("Length of the first word in the sentence is: "+c);
}
}
Explanation:
A Program is an Algorithm – a set of directions for the computer to follow.
True
False
Answers
Answer:
True
Explanation:
(1) describe how you generally use your cellphone on a daily basis (including with whom do you communicate for what purpose with what frequency); (2) read the Supplementary Reading (click here: Does the Internet Make You More or Less Connected?), and discuss how YOUR cellphone use make YOU more or less connected.
Answers
Brainly wasn't letting me answer, so here's an attachment of the answer
can someone help me with this project im confused



Answers
u have to progrem a math algorithum
Determine what is printed by the following code.

Answers
Answer:
18
Explanation:
a will get the values 3,6,9,12,15 and 18.
sum will get the values 0,3,9,18,30 and 45. When it gets to 45, the loop will not be executed anymore.
At that point, a is 18.
What is the energy conversion and the law used in the given scenario?
Traditional power-generating stations do not store electrical energy. In such power stations, the original energy source spins a turbine which an electric generator. It converts [chemical, mechanical, or thermal] energy into electrical energy using a fundamental principle of physics called [Faraday's, Newton's, or Ohm's] law.
Answers
Answer:
The correct options are;
Mechanical
Faraday
Explanation:
The principle of working of electric generators is to convert kinetic energy, which is the energy present in the spinning turbine into electrical energy. Electricity is generated by the use of the electric generators has the largest share of all forms of electricity generated electricity and it is based on Faraday's law of of induction, which states that Emf = N×(ΔФ/Δt)
Where;
Emf = The induced voltage
ΔФ = Change in magnetic flux
Δt = Change in time.
Therefore, we have;
Traditional power-generating stations do not store electrical energy. In such power stations, the original energy source spins a turbine which an electric generator. It converts mechanical energy into electrical energy using a fundamental principle of physics called Faraday's law.
Answer:
The correct answer is Faraday's law.
Explanation:
I got it right on the Plato test.
Recommend a minimum of 3 relevant tips for people using computers at home, work or school or on their SmartPhone. (or manufacturing related tools)
Answers
The three relevant tips for individuals using computers at home, work, school, or on their smartphones are ensure regular data backup, practice strong cybersecurity habits, and maintain good ergonomics.
1)Ensure Regular Data Backup: It is crucial to regularly back up important data to prevent loss in case of hardware failure, accidental deletion, or malware attacks.
Utilize external hard drives, cloud storage solutions, or backup software to create redundant copies of essential files.
Automated backup systems can simplify this process and provide peace of mind.
2)Practice Strong Cybersecurity Habits: Protecting personal information and devices from cyber threats is essential.
Use strong, unique passwords for each online account, enable two-factor authentication when available, and regularly update software and operating systems to patch security vulnerabilities.
Be cautious while clicking on email attachments, downloading files, or visiting suspicious websites.
Utilize reputable antivirus and anti-malware software to protect against potential threats.
3)Maintain Good Ergonomics: Spending extended periods in front of a computer or smartphone can strain the body.
Practice good ergonomics by ensuring proper posture, positioning the monitor at eye level, using an ergonomic keyboard and mouse, and taking regular breaks to stretch and rest your eyes.
Adjust chair height, desk setup, and screen brightness to reduce the risk of musculoskeletal problems and eye strain.
For more questions on computers
https://brainly.com/question/24540334
#SPJ8
meaning of mesh topology
Answers
The meaning of mesh topology is that it is a type of networking that is made up of the fact that all its nodes do work together to share data amongst each other.
What is meant by mesh topology?Mesh topology is a kind of networking that is said to be where the full nodes do act in a form of a cooperation so that they can be able to share or distribute data among themselves.
Note that this topology was said to be first seen or developed in about an approximate of about 30+ years ago and it is one that is often used in military applications and now it is seen to be used in home automation, smart HVAC control, and others.
Hence, The meaning of mesh topology is that it is a type of networking that is made up of the fact that all its nodes do work together to share data amongst each other.
Learn more about mesh topology from
https://brainly.com/question/14879489
#SPJ1
For the CART model, if my three terminal node's deviation are
100,200,300. So can I know the deviation of the estimated model? If
yes, what's the value of deviation of the estimated model.
Answers
Yes, you can calculate the deviation of the estimated model for the CART model if the deviation of the three terminal nodes are 100, 200, and 300.
CART stands for Classification and Regression Trees and it is a machine learning technique used for classification and regression analysis of complex data by creating decision trees.
Decision trees are constructed by splitting a dataset into smaller subsets and repeating the process recursively until a termination condition is met
1:Deviation = 100Mean of the node = x1Standard deviation of the node = σ1Therefore,100 = ∑(xi - x1)² / n1where ∑(xi - x1)² is the sum of the squared deviations of the data points from the mean of the node and n1 is the number of data points in the node.
2:Deviation = 200Mean of the node = x2Standard deviation of the node = σ2100 = ∑(xi - x2)² / n2For terminal node
3:Deviation = 300Mean of the node = x3Standard deviation of the node = σ3100 = ∑(xi - x3)² / n3
Now, we can calculate the deviation of the estimated model as follows :d = (n1σ1² + n2σ2² + n3σ3²) / (n1 + n2 + n3)Substituting the values of n1, n2, n3, σ1, σ2, σ3, we get :d = (1(100²) + 1(200²) + 1(300²)) / (1 + 1 + 1)d = 166.67
Therefore, the deviation of the estimated model is 166.67.
To know more Deviation visit:
brainly.com/question/31835352
#SPJ11
which memory module has 240 pins and can support quad, triple, or dual channels?
Answers
When it comes to computer memory, there are various types of memory modules that are available in the market. One such memory module is the 240-pin module, which is commonly used in modern computer systems.
The memory module with 240 pins that can support quad, triple, or dual channels is called DDR3 SDRAM (Double Data Rate 3 Synchronous Dynamic Random-Access Memory). This type of memory module is commonly used in high-performance computing systems that require faster data transfer rates and larger memory capacity. DDR3 SDRAM is designed to work with Intel and AMD processors, and it is capable of running at speeds of up to 2133 MHz. This memory module has four notches on the bottom edge and 240 pins, which makes it compatible with motherboards that support DDR3 memory.
In summary, the memory module with 240 pins that can support quad, triple, or dual channels is DDR3 SDRAM. This type of memory module is widely used in modern computing systems and is designed to provide faster data transfer rates and larger memory capacity.
To learn more about computer memory, visit:
https://brainly.com/question/30273393
#SPJ11
Explain the simliparities or difference between a workbook , worksheet and spread sheet
Answers
Answer:
Spreadsheet vs Workbook. Summary: Difference Between Spreadsheet and Workbook is that Spreadsheet software allows users to organize data in rows and columns and perform calculations on the data. ... While Workbook is consider as whole file that can contain bundle of worksheets in it.
Explanation:
mark brainlyist
Why are Quick Parts useful in an Outlook message?
Spreadsheet data sources can be hyperlinked to an email message.
Stored text and graphics can be quickly inserted into an email message.
A gallery of shapes will open up, and you can quickly choose one to insert.
Highlighted parts of Word documents can be inserted into a message body.
Answers
Answer:
I hope the picture helped

Answer:
B. stored text and graphics can be quickly inserted into an email message
Explanation:
Edge 2021
Write a program that asks the user to enter the number of employees in an organization, the employees' names, and the number of hours they
Answers
A possible program that asks the user to enter the number of employees in an organization, the employees' names, and the number of hours they worked would involve using loops and arrays.
Below is an algorithm in pseudocode for a function that accepts an integer array as an argument and returns the total of the values in the array using a counted for loop.
Here is a sample code in Python:
num_employees = int(input("Enter the number of employees: "))
names = []
hours = []
for i in range(num_employees):
name = input("Enter the name of employee #" + str(i+1) + ": ")
names.append(name)
hour = int(input("Enter the number of hours worked by " + name + ": "))
hours.append(hour)
print("Employee hours:")
for i in range(num_employees):
print(names[i] + ": " + str(hours[i]))
This program starts by asking the user to input the number of employees, which is converted to an integer using the int() function. It then uses two empty lists, names and hours, to store the names and hours worked of each employee, respectively. The program then uses a for loop to iterate through the range of num_employees, prompting the user to enter the name and hours worked for each employee. The name is appended to the names list, while the hour is converted to an integer and appended to the hours list. Finally, the program uses another for loop to print the names and hours worked of each employee.
Learn more about loops and array in python code here
https://brainly.com/question/31512399
#SPJ11
Keith needs to import data into an Access database from a text file. Which option is the most common delimiter and easiest to work with?
Answers
Answer:tab
Explanation:
Cause I got it right
Answer:
The answer is a comma.
Explanation:
This is the correct answer because space and tab are not delimiters. Therefore it has to be either comma or semicolon and a semicolon is bigger and harder to navigate around. So this gives you the answer of a comma.
Defin major domains of AI??
koii h
Answers
Answer:
\(\sf\fbox\red{Answer:-}\)
The different domains of AI are Formal tasks, Mundane Tasks, and Expert Tasks.
\(\small\fbox{\blue{\underline{mαrk \; mє \; вrαínlíєѕt \; plєαѕє ♥}}}\)
marc is an investigator who discovers a piece of visible data. what did marc likely then see? group of answer choices any data stored in sectors or clusters a file dragged to the windows recycle bin a file being swapped in visible ram a string of sms text messages
Answers
Based on the given options, if Marc is an investigator who discovers a piece of visible data, he likely saw a file being swapped in visible RAM.
How can this process be explained?This refers to the process where data from the computer's memory is temporarily stored on the hard drive.
The other options, such as data stored in sectors or clusters, a file dragged to the Windows recycle bin, and a string of SMS text messages, do not necessarily indicate visible data that Marc would come across in his investigation.
Thus, the correct answer is a file being swapped in visible ram
Read more about file managers here:
https://brainly.com/question/13189758
#SPJ4
The CPU is often called the
of the computer.
Answers
Answer:
Explanation:
Tower?
Answer:
Its often called the brains of a computer.
Explanation:
These are single- celled microoganisms that can cause food poisoning
Answers
The single-celled microorganisms that can cause food poisoning are called bacteria. Bacteria are microscopic organisms that exist in various environments, including food. They can multiply rapidly under favorable conditions, such as improper food handling, inadequate cooking, or inadequate refrigeration.
Certain types of bacteria, such as Salmonella, Escherichia coli (E. coli), and Campylobacter, are commonly associated with foodborne illnesses. For example, Salmonella can be found in raw or undercooked eggs, poultry, meat, and unpasteurized milk. E. coli can be present in contaminated water or undercooked ground beef. Campylobacter can contaminate poultry, raw milk, and untreated water.
When consumed, these bacteria release toxins or cause infections in the gastrointestinal tract, leading to symptoms like nausea, vomiting, diarrhea, and abdominal pain. It is essential to practice proper food handling and preparation techniques, such as thorough cooking, avoiding cross-contamination, and refrigerating perishable foods promptly, to minimize the risk of food poisoning.
To know more about microorganisms visit :-
https://brainly.com/question/9004624
#SPJ11
What is the best gaming name you can come up with?
Answers
Of the four email features listed below, which is the most important?
Answers
Explanation:
You didn't list the four options. You just wrote the question. (I apologize if my sentence sounds rude, for it wasn't my intention)