Answers
Answer:
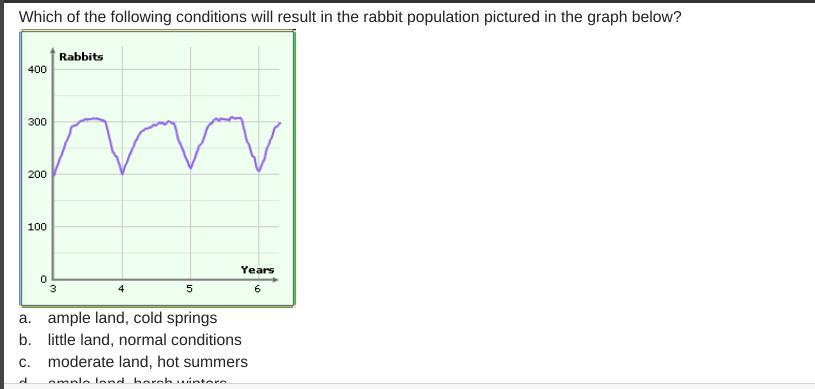
First one is A
Second one is B
Explanation:
Related Questions
In terms of computer hardware, where does the actual work of computing take place?
Answers
Answer: central processing unit
Explanation:
Which type of chart is used to chart progress over time?
Answers
Answer: Timeline
Explanation:
Write a python program to display the cube of a number upto given integer
Answers
Answer:
def display_cube(n):
for i in range(1, n+1):
print("Number is : {} and cube of the number is : {}".format(i, i**3))
# Test the function
display_cube(5)
Explanation:
This program defines a function display_cube(n) that takes an integer n as an argument and prints out the cube of the numbers from 1 to n. The range() function is used to generate a sequence of numbers from 1 to n, and the print() function is used to display the number and its cube. The ** operator is used to calculate the cube of a number. You can test the function by calling it and passing in an integer value as an argument.
how does the use of object serialization (using a binaryformatter) compare to simply writing our data to a text file?
Answers
BinaryWriter is used to write primitive types in binary to a stream and supports writing strings in a specific encoding. BinaryFromatter is responsible for serializing an entire object or graph of connected objects into binary format. So, I suppose you can say BinaryWriter is a much more elementary form of something like BinaryFormatter.
What is Object Serialization?
Object serialization is the most common method of converting an item into a stream of bytes in order to store or communicate the object to memory, a data set, or a document. Its primary goal is to save the condition of an article so that it can be reproduced when needed. Deserialization is the inverse cycle.
The item is serialized to a stream that contains the data that is serialized object. The stream may also contain information about the item's type, such as its version, culture, and get together name. The article can then be saved in an information base, a document, or memory.
Serialization allows the engineer to save the condition of an item and recreate it based on the situation, allowing for article stockpiling as well as information trade. An engineer can carry out tasks using serialization.
Use of Object Serialization:
Sending the item to a far off application by utilizing a web administration Passing an article starting with one space then onto the next Going an article through a firewall as a JSON or XML string Keeping up with security or client explicit data across applications The System.Runtime.Serialization namespace contains classes for paired and XML serialization and deserialization.To know more about Serialized Object, visit:https://brainly.com/question/15606999
#SPJ4
which camera is interchangeable
freeform
hybrid
DSLR
point and shoot
Answers
Answer:
DSLR
Explanation:
Double check my answer
PLZZZ HELPPPP
Which list can be sorted with a bubble sort?
(4, 5, 6, 7)
('dog', 'cat', 'fish')
['dog', 'cat', 'fish', 'bird']
[2, 5, 'dog', 'cat']
Answers
Answer:
dog cat fish bird
Explanation:
Answer:
dog cat fish bird
Explanation:
i got it right
What icon indicated video mode?
Av
Tv
The video camera icon
Answers
The video camera icon indicated video mode.
The video camera icon is a universally recognized symbol that indicates video mode on electronic devices such as cameras, smartphones, and video recorders. This icon usually appears on the interface of the device, usually on the screen or as a button that you can press, when you are in video mode, and it allows you to record videos.
AV and TV icons are related to audio-video and television, but they are not used specifically to indicate video mode. AV icon can be used for different purposes such as indicating the audio-video input/output of a device or indicating an audio-video format. The TV icon is used to indicate the television mode, which typically refers to the display mode of a device.
The range of an unsigned 6 bit binary number is
0-63
0-64
0-127
1-128
Answers
Answer:
6 bit = 2^6-1=64-1=63
from 0 to 63
When you use a BEFORE trigger to work with an UPDATE statement, you can use the ____________ keyword and a column name to refer to a value in the row before it is updated. Group of answer choices OLD NEW PREVIOUS SUBSEQUENT
Answers
When using a BEFORE trigger to work with an UPDATE statement, you can use the OLD keyword and a column name to refer to the value in the row before it is updated.
In this context, the "OLD" keyword represents the original values in the row before any modifications take place. This can be particularly useful when you need to compare or log the changes made during the update process. On the other hand, the "NEW" keyword is used to refer to the updated values in the row after the modifications have been applied.
This allows you to work with both the original and updated values within the trigger, enabling more control and flexibility in your database operations. To summarize, using the "OLD" keyword in a BEFORE trigger with an UPDATE statement allows you to reference the original value of a specific column before it is updated. This is helpful when tracking or comparing changes during the update process, and provides additional control when working with database modifications.
know more about database modifications here:
https://brainly.com/question/31567491
#SPJ11
What is the result when you run the following line of code after a prompt??
>>>print(3 + 11)
Answers
Answer:
The following output is 14
Explanation:
When you print something, python interprets it and spits it out to the console. In this case, python is just interpreting 3 + 11, which equals 14. Thus, making the answer 14.
hope i helped :D
Answer:
14
Explanation:
what is the use of numeric variable list any two numeric variable
Answers
Answer:
Numeric variables have data values that are recognized as numbers hence they can be sorted numerically or entered into arithmetic calculations.
Two types of numerical variables are: interval and ratio.
-An interval variable has values whose differences are interpretable but it does not have a true zero.
-A ratio variable is a variable with the features of interval variable and, additionally, whose any two values have meaningful ratio, making the operations of multiplication and division meaningful.
Explanation:
Exercise #3: Write a program that finds all students who score the highest and lowest average marks of the first two homework in CS (I). Your program should read the data from a file called " "
Answers
To find students with the highest and lowest average marks in the first two CS (I) homework, read data from a file, calculate averages, and print the corresponding student names using the provided Python code.
To write a program that finds all students who score the highest and lowest average marks of the first two homework in CS (I),
Read data from the file.First of all, the program should read data from a file. The file name is " ". Calculate the average of the first two homework for each student. Then the program should calculate the average of the first two homework for each student, and store it in a dictionary with the student's name as the key.Find the highest and lowest averages.After that, the program should find the highest and lowest averages and the corresponding student names.Print the names of the students who have the highest and lowest average marks.Finally, the program should print the names of the students who have the highest and lowest average marks.Below is the Python code that can be used to find the students who score the highest and lowest average marks of the first two homework in CS (I):
```python#open the filefile = open('filename', 'r')#initialize a dictionary to store the average of first two homework marks for each studentdata = {}#iterate through each line of the filefor line in file:#split the line into a list of valuesvalues = line.strip().split()#get the student's name and the first two homework marksname = values[0]marks = [int(x) for x in values[1:3]]#calculate the average of the first two homework marksaverage = sum(marks)/len(marks)#store the average in the dictionarydata[name] = average#find the highest and lowest averageshighest = max(data.values())lowest = min(data.values())#find the students with the highest and lowest averageshighest_students = [name for name, average in data.items() if average == highest]lowest_students = [name for name, average in data.items() if average == lowest]#print the names of the studentsprint('Students with highest average:', ', '.join(highest_students))print('Students with lowest average:', ', '.join(lowest_students))```
Note: Replace the 'filename' with the actual name of the file that contains the data.
Learn more about Python code: brainly.com/question/26497128
#SPJ11
write a program in python to open a udp socket between a client and a server, then use wireshark to monitor the packets sent.
Answers
Hi! I'd be happy to help you create a simple UDP client-server program in Python and guide you on how to monitor the packets using Wireshark.
First, create the server code (server.py):
```python
import socket
server_ip = '127.0.0.1'
server_port = 12345
server_socket = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
server_socket.bind((server_ip, server_port))
while True:
data, addr = server_socket.recvfrom(1024)
print("Received message:", data, "from:", addr)
```
Next, create the client code (client.py):
```python
import socket
server_ip = '127.0.0.1'
server_port = 12345
client_socket = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
message = "Hello, Server!"
client_socket.sendto(message.encode(), (server_ip, server_port))
```
Now, run the server.py script in one terminal and the client.py script in another terminal.
To monitor the packets using Wireshark:
1. Download and install Wireshark from https://www.wireshark.org/download.html
2. Open Wireshark and select your network interface (e.g., "Loopback" for local traffic)
3. In the "Filter" input field, type "udp.port == 12345" and press Enter
4. Run the client.py script again, and you should see the UDP packets between the client and the server in Wireshark.
Please note that you may need to adjust the IP addresses and port numbers according to your specific network configuration.
learn more about UDP client-server program here:
https://brainly.com/question/15014474
#SPJ11
Fast as possible, please

Answers
Which tab can be used to change the theme and background style of a presentation?

Answers
Answer:
Design IS the correct answer
Explanation:
what are some example of popular music for teenagers
Answers
Answer: Hip Hop, Rap, Alternative, Pop Rock
Explanation:
Answer:
Rod wave, Polo g, Lil Uzi Vert, Da baby, Bad bunny, Prince Royce, Cardi b, Nicki manaj, Drake, Miley cyrus, Marina, Trippe red, YNW melly, Lil peep, PARTYNEXTDOOR, Jeremih, Juice wrld, Pop smoke,
Explanation:
Thats what my older teenage cousins listens to.
Microsoft PowerPoint users may opt to use a variety of ____________________, which are animation-like effects displayed while moving from one slide to another. (transitions, hyperlinks, background images)
Answers
Answer:
transitions
Explanation:
Hope this helps!
What should be the primary concern when using machinery or project tools in class? (Choose the best answer.)
* 4 points
working to find a shortcut
A safe work environment for everyone.
working quickly
fun
Answers
Answer:
First number
Explanation:
bcoz it help us to find a shorcut our work then other methods.
The primary concern when using machinery or project tools in class should be "A safe work environment for everyone."
Safety is of utmost importance when operating machinery or tools, especially in an educational setting where students may have limited experience or training in handling such equipment.
The well-being of students and teachers should always be the top priority to prevent accidents, injuries, or damage to property.
Educators must ensure that students are properly trained on how to use the machinery or tools safely and follow all safety guidelines and protocols. It is crucial to provide adequate supervision, proper safety equipment, and clear instructions to minimize risks and create a secure learning environment.
To learn more about safe work environment;
https://brainly.com/question/29335222
#SPJ3
Name the nation that manufactures the most computer chips
globally. Describe the impact of the CHIPs Act, which Congress just
enacted, on the US computer sector.
Answers
The nation that manufactures the most computer chips globally is Taiwan. Taiwan is known for its advanced semiconductor industry, with companies like TSMC (Taiwan Semiconductor Manufacturing Company) being major players in the global chip market.
Now, let's discuss the impact of the CHIPs Act on the US computer sector. The CHIPs Act, which stands for Creating Helpful Incentives to Produce Semiconductors, was recently enacted by Congress in order to strengthen domestic semiconductor production in the United States.
The impact of the CHIPs Act on the US computer sector can be significant. By providing financial incentives and support to domestic chip manufacturers, the act aims to promote investment in new fabrication facilities, research and development, and workforce development in the United States.
To know more about manufactures visit:
https://brainly.com/question/29489393
#SPJ11
What is the purpose of formatting charts?
changes the data set used for creating the chart
changes the look and feel of the display
changes the values in the data set
changes the type of chart used
Intro
Don
Answers
Answer:
Changes the look and feel of the display
Explanation:
Because you don't change the data nor the values in the char
And it does not change the type of chart.
Which file attribute identifies the file as having been modified since the last backup?.
Answers
Archive File Definition
The meaning of the word Archive in the Online Computer Dictionary is used to make a copy of a backup file with the aim of protecting the original copy from damage.
How to Archive Files Into 1 File
If you want to send a large number of files, you can make the file into 1 archive file format with .zip, .tar, or .rar format first. This method is also quite easy and fast.
• First, make sure your computer has programs such as winzip, winrar. This program is needed to archive files.
• Second, you can select the file you want to archive, then right-click on the file. The example below shows 2 files to be archived
• The third step, you can directly select Add to “folder name.rar” to directly create archive files automatically. If you want to do some settings, it can be done by selecting the Add to archive option. The Add to archive option allows you to choose the save format of the file, divide or create the archive into several parts (part 1, part 2, etc.), to create a password. With the password, before the file can be extracted, it is necessary to enter the password first.
In addition to files, you can also archive folders directly along with the contents of the files in it. Keep in mind, how fast the process of archiving this file will depend on how many or large files to be archived.
Learn more about archive files athttps://brainly.com/question/15355917.
#SPJ4
a network interface card (nic) operates at the open systems interconnection (osi) model’s _____ layers.
Answers
A network interface card (NIC) operates at the Open Systems Interconnection (OSI) model's Physical layer (Layer 1) and Data Link layer (Layer 2).
At the Physical layer, the NIC is responsible for transmitting and receiving electrical, optical, or wireless signals that carry the actual data across the network medium, such as Ethernet cables or wireless connections.At the Data Link layer, the NIC handles tasks like framing data into packets, error detection and correction, and managing access to the network medium using protocols like Ethernet.It's important to note that the OSI model is a conceptual framework, and different network technologies may implement the OSI layers differently. However, the NIC's primary functions align with the Physical and Data Link layers of the OSI model.
To know more about network click the link below:
brainly.com/question/31713855
#SPJ11
What data type is this statement defined as in Python?
testAvg = 0.00;
A. integer
B. string
C. float
D. real
Answers
String because in python a succession of Unicode characters is called a string. Unicode was created to encompass all characters in all languages and bring encoding standardization.
What is python?Python is a programming language for creating websites and software, as well as automating processes and conducting data analysis.
Python is a general-purpose programming language, which means it can be used to develop a wide range of applications and isn't tailored to any particular problem.
Thus, option B is correct.
For more details about python, click here
https://brainly.com/question/13441316
#SPJ1
A customer bought a goods for Rs.9,000 after getting 10% discount. Calculate the marked price of the goods.Write in Qbasic.
Answers
Answer:
Rs. 10,000
Explanation:
10% discount means,
customer bought the things at 100% - 10% = 90%
so if 90% --> 9000
1% --> 100
total price = marked price which is 100%
100% ---> 100*100 = Rs. 10,000
borrowers have the right to inspect the completed closing disclosure (cd) form three business days before closing. group of answer choices true false
Answers
True. Borrowers have the right to inspect the completed Closing Disclosure (CD) form three business days before closing. This is a provision under the Truth in Lending Act (TILA) and the Real Settlement Procedures Act Estate (RESPA) designed to provide borrowers with sufficient time to review the final loan terms and costs before proceeding with the closing of a mortgage loan.
The three-day period allows borrowers to ensure that the loan terms and closing costs align with their expectations and enables them to seek clarifications or address any concerns they may have. The CD form provides a detailed breakdown of the loan terms, interest rate, closing costs, and other important information related to the mortgage transaction. It is important for borrowers to carefully review the CD form to ensure transparency and make informed decisions regarding their mortgage loan.
To know more about mortgage, visit
https://brainly.com/question/31751568
#SPJ11
h. erectus is generally associated with which of the following technologies?
Answers
Homo erectus is generally associated with the Acheulean technology.The Acheulean industry is characterized by the production of bifacial stone tools.
Homo erectus, an extinct species of human ancestors, is commonly associated with the Acheulean technology. The Acheulean industry is characterized by the production of bifacial stone tools, particularly handaxes, which were skillfully crafted and shaped by Homo erectus. These handaxes were symmetrical and had a sharp cutting edge, making them versatile tools for various tasks such as butchering animals and woodworking. The Acheulean technology represents a significant advancement in tool-making compared to earlier technologies and is considered an important milestone in human evolution. It demonstrates Homo erectus's ability to plan, shape materials, and adapt to different environments through the development and use of sophisticated tools.
know more about Acheulean technology :brainly.com/question/33322934
#SPJ11
What is the main purpose of the design of a water hose.
Answers
explain what union means in ms excel in a short easy way
Answers
Answer:
Unions are a way to combine different data into a single table. When you use the union operator in Excel, it combines the data from all the cells that have the same value in them.
Jeremiah needs to see data in two different table views from two regions without creating two tables. Which two features would he use to create this?
Answers
Answer:
Tables & Filter
Explanation:
That correct
Answer:
D. Tables and filter
Explanation:
a(n) ____ policy controls password characteristics for local user accounts.
Answers
The answer is: a(n) password policy.
A password policy is a set of rules and guidelines designed to improve computer security by encouraging users to create strong, secure passwords and use them properly. This policy controls password characteristics for local user accounts by defining various parameters, such as:
1. Minimum password length: This specifies the minimum number of characters required for a password.
2. Password complexity requirements: These rules determine the types of characters (such as uppercase letters, lowercase letters, numbers, and special symbols) that must be included in a password.
3. Password history: This defines how many unique passwords a user must create before they can reuse an old password.
4. Maximum password age: This setting determines the length of time a password can be used before it must be changed.
5. Account lockout policy: This specifies the number of failed login attempts allowed before a user account is locked and the duration of the lockout period.
By implementing a strong password policy, organizations can better protect their local user accounts and overall system security.
Know more about password policy here:
https://brainly.com/question/29392897
#SPJ11