Why is yo utu be down?
(You restrict talking about yo utu be, really)
Answers
Related Questions
Experts believe robots and AI will continue taking over many of the human jobs we know today. What changes should be made to K-12 education to ensure students are prepared for the future? What courses or skills should be added? WHat should be removed? Why?
Answers
Answer:
I think they should show one subject per month so students are more prepared
Answer: some changes that should be made are dresscode , some courses should be more sports . Nothing should be removed because the kids in the future need to learn more .
Explanation:
i need a essay 3-5 sentences on volleyball
Answers
Answer:Volleyball is a team sport that involves two teams of six players, one of which plays offense and the other defense. Each player has a specific role to play on the court:
Setter – The setter positions herself in front of her teammates, and sets up the ball for them to hit. She also controls the pace at which points are played, as well as how long each point lasts. The setter’s job is to make sure that every point goes smoothly without any errors or mistakes by her teammates.
– The setter positions herself in front of her teammates and sets up the ball
Explanation:
pick and choose the sentences from there
How does a resident virus differ from a non-resident virus? !!!25 POINTS!!!!!
A) Resident viruses simply disrupt operations while non-resident viruses will control hosts.
B)Resident viruses will control hosts while non-resident viruses simply disrupt operations.
C)Resident viruses find networks to infect while non-resident viruses load themselves into memory.
D)esident viruses load themselves into memory while non-resident viruses find networks to infect.
Answers
Answer:
The correct answer is **D)** Resident viruses load themselves into memory while non-resident viruses find networks to infect. A resident virus is a type of computer virus that’s deployed and resides within a computer’s random access memory (RAM). A non-resident computer virus, on the other hand, is a type of computer virus that doesn’t reside within a computer’s RAM. Non-resident computer viruses can still be deployed within RAM, but they don’t stay there.
Which of the following is the Internet's universal language for network connections? SSL TCP/IP IPS TLS
Answers
Answer:
TCP/IP
Explanation:
it is the common language of the Internet
(I made this up teehee) what anime is katski bakugo from
Answers
What is output?
Print (12 % 5)
Answer
0
5
2
1
Answers
How do the text feature help on the text?
Answers
Answer:
Text features help you locate important information in a text. Knowing the purpose of the text feature helps you decide at which text feature to look when you want to understand your text better. Organized by purpose, the chart identifies text features and how they help the reader.
Explanation:

Write code that does the following: opens the number_list.txt file, reads all of the numbers (1 to 100) from the file, adds all of the numbers read from the file and displays their total. then closes the file.
Answers
The code that does the following: opens the number_list.txt file, reads all of the numbers (1 to 100) from the file, adds all of the numbers read from the file and displays their total. then closes the file is given below.
What is the code about?Below is an example Python code that should accomplish this task:
python
# Open the file for reading
with open("number_list.txt", "r") as file:
# Read all the lines and convert them to integers
numbers = [int(line) for line in file.readlines()]
# Sum up the numbers and display the total
total = sum(numbers)
print("The total is:", total)
# Close the file
file.close()
Therefore, Assuming that the number_list.txt file contains one number per line from 1 to 100, the code should read all the numbers from the file, sum them up, and display the total. Finally, the file is closed automatically when the with block is exited.
Read more about code here:
https://brainly.com/question/26134656
#SPJ1
Answer
Explanation:
I don't know
What is Mark like doing?
A. Smokin These Meats,
B. Wearing a Greay shirt to work and a Purple shirt on the Weekends.
C. Going Live in his Backyard.
D. Daydreaming about Smoking Meats while being Roasted by Congress.
(This is all beased on the video Smoking these meats, I suggest you watch it.)
Answers
Answer: A) smoking these meats goin live in his backyard
Explanation: cause he wants to why do u care .....................................
Question: How do you file a complaint using a food restaurant? 100 POINTS WILL BE GIVEN INCLUDING BRAINLIEST
Answers
send it through the mail
Answer: Be prepared to provide the following information:
1.Your Name, Address and Phone Number (your information will remain anonymous to the restaurant)
2.Name of restaurant
3.Location/address of the restaurant
4.Date of incident
5.Nature of complaint
If you suspect you became ill from this incident. You will need to give specific information about the suspected foods that made you sick, as well as when your symptoms began, and what they were. In addition, you will need to give a 3-day food eating history.
Explanation
Identify the error in the following block of code.
for x in range(2, 6):
prnt(x)
o The first line is missing quotes.
o The first line has a spelling error.
o The second line has a spelling error.
o The second line needs to be indented four spaces.
Answers
Answer:
The first line has a spelling error
Answer:the first line is missing quotes
I'm very confused. Can someone p|z explain what's happening here?
(view screenshots below)
(I drew a cursor on most of the pictures because I can't screenshot with my cursor meaning when I take a screenshot, my cursor will disappear and so I drew the cursor on the pictures so that way you could see where I was clicking)




Answers
Answer:
It just means that when you answer questions the person who asked it has to vote you as 'brainliest' so you get points or something but the person who has asked it gets to pick who becomes brainliest
Give three examples of ethical or legal issues that an IT professional may encounter and the negative consequences of these issues.
Answers
Answer:
1. Private Informations being leaked.
2. Hackers that hacks accounts.
3. Computer Viruses obtained by clicking spam messages.
Explanation:
1. They can turn down the leaked informations by logging to it, legally.
2. IT Professionals could hack the hacker, or outsmart them.
3. Some people can stop Computer Viruses, but IT Professionals can prevent it much better than them.
I hope that my answer helped you. Thank you, and good luck.
The three examples of ethical or legal issues that an IT professional may encounter are:
Privacy violationsCybersecurity breachesIntellectual property violationsWhat are the negative consequences of the issues with IT professional?In Privacy violations: IT professionals may be faced with ethical dilemmas related to the collection, use, and protection of personal data. If personal data is not handled responsibly, it can lead to privacy violations, loss of trust, and potential legal consequences.
In Cybersecurity breaches: IT professionals are responsible for protecting the security of systems and data, and failure to do so can result in cybersecurity breaches that can have serious consequences, such as data loss, financial damage, and reputational harm.
Therefore, in Intellectual property violations: IT professionals may be faced with ethical issues related to the use of copyrighted or patented materials. If these materials are used without permission, it can result in legal consequences and damage to the reputation of the IT professional and their organization.
Learn more about IT professional from
https://brainly.com/question/6947486
#SPJ1
what do you think? good or no?

Answers
Answer:
its great
its actually pretty cooll
The following figure is a trapezoid. Decompose the shape into parallelograms or triangles only. Explain or show how you decomposed the shape.

Answers
Answer: joining the diagonals is the simpliest way to decompose it
Explanation: connect the diagonals and cut them
you will get four equal triangles
hope this helps!
explain the history of computing of mechanical era
Answers
Answer:The Mechanical Era
Created a machine that could add and subtract numbers. Dials were used to enter the numbers. ... Designed a machine called the Analytical Engine. The design had all the basic components of a modern day computer. In addition, it was designed to be programmable using punched cards.
Explanation:Hope this helped
Decisions about technology most often include examining the trade-offs between which areas?
a. environment, society, and economics
b. interdependence, society, and engineering
c. the designed world, the natural world, and the materials world
d. technological systems and engineering products and processes
GIVING 15 POINTS PLS HELP
Answers
Answer:
s it's not type look
Explanation:
Ok, so, I have a Chromebook and it's HORRIBLE. Can anybody give me some reasons why?
Answers
I don’t really know why they are bad, I’ve only used them once, but I think it has to do with the hardware and programming. Maybe it’s just poorly made?
Answer:
The latest update of Chrome OS offers a browser "enhancement" that is actally more like a software bug. It’s really annoying.
Explanation:
my sister is currently having the same problem.
Which sentence is correctly punctuated? WILL GIVE YU MONEY GIVE ME YOUR CASH APP PLS
However I occasionally, like to read stories set in the future.
However I occasionally like to read stories set in the future.
However, I occasionally like to read stories set in the future.
However. I occasionally like to read stories set in the future.
Answers
Answer:
C.) However, I occasionally like to read stories set in the future
Explanation:
Grammarly
Digital and analog audio recordings have pros and cons. Do you think the pros of digital recordings outweigh the cons and therefore prefer digital audio recordings? Or, do you think the cons outweigh the pros and therefore you prefer analog audio recordings? Explain. ( USE C.E.R *Claim, Evidence, Reasoning* )
Answers
I think the pros of digital recordings outweigh the cons! I prefer digital audio recordings over analog audio recordings because analog recordings require more financing and preservation. Compared to digital recordings, analog recording equipment is more expensive and the tape deteriorates over time. Which to me personally, doesn't seem to be worth the amount of effort since it's such a process to go through. You can possibly go into debt due to that. Digital recording equipment, on the other hand, is more affordable. It's less time-consuming and although it does have its disadvantages, they're minor. Digital recordings can be stored online. Its data get corrupted? You can get it back! It won't cost you anything.
Is a poster the best media form to make a call to action to the government and major corporations? What other media forms could be effective?
Answers
Answer:
A Poster can be an effective media form to make a call to action to the government and major corporations, as it allows for visually impactful messaging. However, other media forms could also be effective, such as:
Social media campaigns: Utilize platforms like Twitt..er, Fa..cebook, or Ins..tagram for awareness and mobilization.Online petitions: Collect signatures and demonstrate public support.Video campaigns: Engage viewers emotionally through compelling videos.Mass media advertising: Utilize TV, radio, or print media for broader reach.Advocacy websites: Provide information, resources, and a platform for action.Public demonstrations and rallies: Gather supporters for visible advocacy.Answer:
Explanation:
Online petitions: Collect signatures and demonstrate public support.Video campaigns: Engage viewers emotionally through compelling videos.Mass media advertising: Utilize TV, radio, or print media for broader reach.Advocacy websites: Provide information, resources, and a platform for action.Public demonstrations and rallies: Gather supporters for visible advocacy.public class Main {
public static void main(String[] args) {
String firstName = "John ";
String lastName = "Doe";
String fullName = firstName + lastName;
System.out.println(fullName);
}
}
From this example copy and paste code that when run would say your name. in javascript with my first name being Ryan and my last name being Smith
Answers
Answer:
const firstName = "Ryan ";
const lastName = "Smith";
const fullName = firstName + lastName;
console.log(fullName);
Explanation:
public static void main(String[] args) {
String firstName = "Ryan";
String lastName = "Smith";
String fullName = firstName + lastName;
System.out.println(fullName);
}
Which best describes desktop publishing? the process of designing and laying out printed material the positioning of text, graphics, and white space on a page the style of letters and how they are arranged the use of images and colors
Answers
Explanation:
the process of designing and laying out printed material.
Answer:A photographic proof where all colors are shown in blue, best used for spot color jobs, and it is used primarily to ... WYSIWYG is technical jargon that describes.
Explanation:
Eric’s computer slows down when he open several computer programs. Why does this happen?
A. Eric has limited RAM space
B. Eric has a small hard drive
C. Eric does not have a powerful video card
D. Eric has a bad ROM
Answers
A. Eric has limited RAM space
Since Eric doesn't have a lot of RAM space he won't be able to open up several programs at once
Which of these is NOT a reason for an IP Address?
A. To help with computer storage
B. Allows transfers of files and e-mail
C. A way to identify machines on a network
D. Used to connect to another computer
Answers
Answer:
To help with computer storage
A short story, but i remember in 1nd - 5th grade at my elementary school here is the list from first to last for being cool at school
1. Lego and Pokemon cards
2. Having lunchables and good stuff while i had that whole wheat bread pb and stuff
and tuna that i don't even like and stuff (unless it's a field trip)
3. Yu-gi-oh cards
4. Slime
5. Nothing that much but showing your new phone and where you went over the weekend, while i stayed at home doing mostly nothing productive
Answers
We all live similar lives don't we.
yeah help me please......................
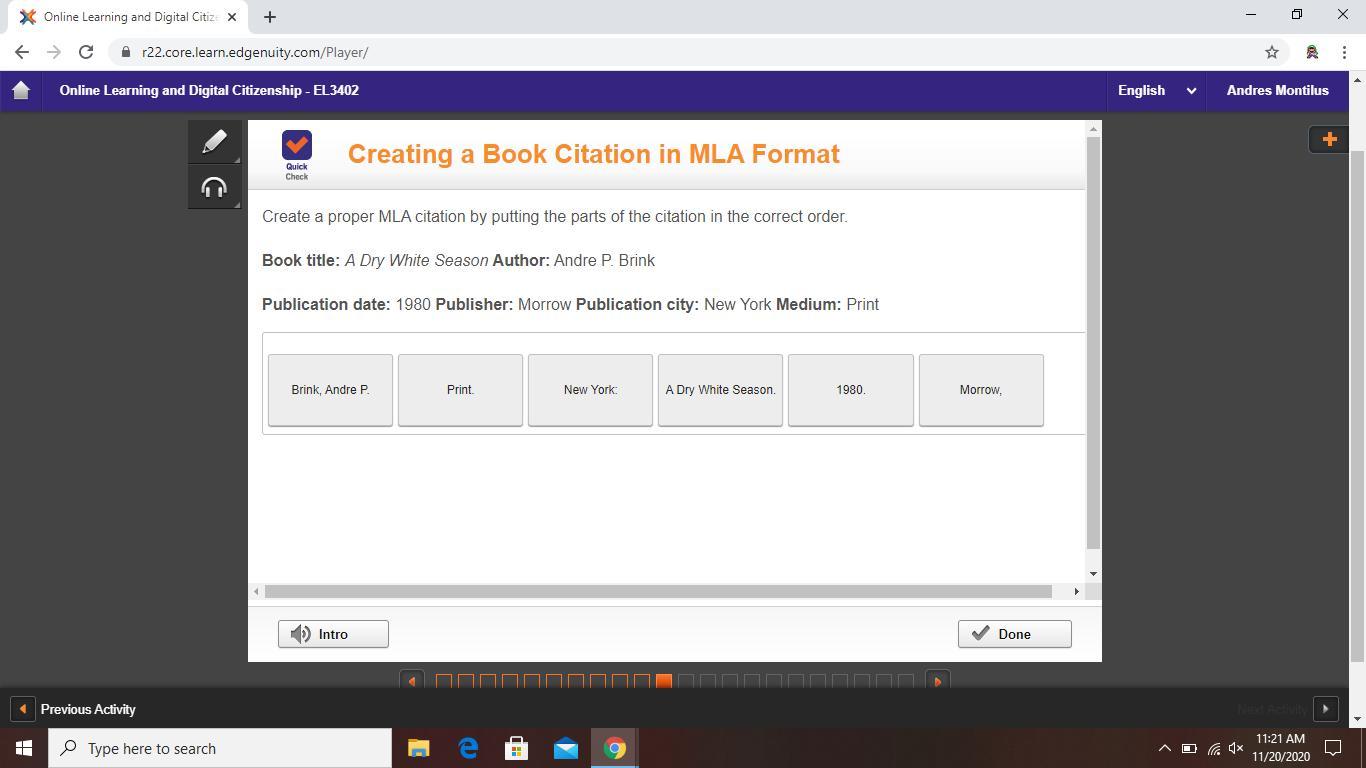
Answers
Which type of cyber crime offender requires the highest percentage of risk management in terms of computer monitoring?
A) Sex offenders
B) Identity thieves
C) Low-Risk offenders
D) hackers
Answers
Answer: D
Explanation: Hackers are the only type of cyber criminal that monitors your computer
Jackie is planning a birthday party for her little brother and is researching different trampoline parks. She receives a pop-up asking for her name, address, and date of birth so she can receive a special promotion from the trampoline park. What should Jackie do?
a
Ignore the request and not enter any personal information.
b
Provide only her name and date of birth.
c
Provide only her name and address.
d
Provide the requested information to receive the discount.
Answers
Answer:
a
Explanation:
sis is gonna get scammed
Answer:
a
Explanation:
You dont know who is getting your information and it is not someone you know. STRANGER DANGER!
Walt needs to ensure that messages from a colleague in another organization are never incorrectly identified as spam. What should he do?
A.Configure a safe recipient.
B.Configure a blocked sender.
C.Configure a safe sender.
D.Do nothing.
Answers
Answer:
C. Configure a safe sender
Explanation:
It’s dabest thing to do
As per the given scenario, Walt should need to configure a safe sender. The correct option is C.
What is configuration?A system's configuration in communications or computer systems refers to how each of its functional elements is organised in relation to their nature, number, and distinguishing features.
Configuration frequently involves picking the right hardware, software, firmware, and documentation.
A person, group, or organisation that starts the communication is known as the sender. The success of the message stems primarily from this source.
The communication is influenced by the sender's experiences, attitudes, knowledge, competence, perspectives, and culture.
Walt must take care to prevent messages from a colleague in a different organisation from ever being mistakenly classified as spam. He ought to set up a secure sender.
Thus the correct option is C.
For more details regarding configuration, visit:
https://brainly.com/question/13410673
#SPJ2