Which type of network allows backups and network security to be centrally located?
A. Client-to-peer
B. Client/server
C. Peer-to-peer
D. VPN
Answers
Answer:
B
Explanation:
B is the answer.
A client-server network is a type of computer network that uses a dedicated computer to store data, manage/provide resources, and govern user access. The correct option is B.
What is a Client/Server Network?A client-server network is a type of computer network that uses a dedicated computer to store data, manage/provide resources, and govern user access (server). The server acts as the network's hub, connecting all other computers. A client computer is one that interfaces to the server.
A computer network is a group of computers that exchange resources on or delivered by network nodes. To communicate with each other, the computers use common communication protocols over digital links.
When the data from all of these nodes is saved on a single or mainframe computer, the network is referred to as a Client-server Network.
As a result, the Client/Server Network is the sort of network that allows backups and network security to be centralized.
Learn more about Client/Server Network here:
https://brainly.com/question/13346485
#SPJ2
Related Questions
if the modulus n used for rsa is 1024 bits long, the primes p and q will each be approximately bits long
Answers
In RSA encryption, if the modulus (n) is 1024 bits long, then the prime numbers p and q used to generate the modulus will each be approximately 512 bits long.
RSA encryption works by multiplying two large prime numbers (p and q) together to form a modulus (n) for both the public and private keys. The bit length of n directly impacts the security of the RSA system, and is essentially twice the size of p or q. Therefore, for a 1024-bit n, p and q would each be approximately 512 bits in length. However, the exact length can vary slightly due to the precise values of the primes chosen. The larger the values of p and q, the more secure the RSA system, but also the slower the encryption and decryption processes.
Learn more about RSA encryption here:
https://brainly.com/question/31329259
#SPJ11
Under Conversions, in the Goals Overview report with a Custom Segment for sessions in which users visited a page with "Android" in the title, how many Goal Completions occurred?
Answers
Under Conversions, in the Goals Overview report with a Custom Segment for sessions in which users visited a page with "Android" in the title, 4,355 Goal Completions occurred. The correct option is b.
Goal Completions, in the context of web analytics tools, refer to the number of times users have successfully completed predefined goals on a website.
A goal represents a specific action or conversion that you want your website visitors to take.
It could be a purchase, a form submission, a download, or any other meaningful interaction that aligns with your business objectives. When a user performs the desired action, it is counted as a Goal Completion.
4,355 Goal Completions were recorded under Conversions in the Goals Overview report with a Custom Segment for sessions in which users accessed a page with "Android" in the title.
Thus, the best choice is b.
For more details regarding goal completions, visit:
https://brainly.com/question/29840321
#SPJ1
Your question seems incomplete, the probable complete question is:
Let's practice Segments by going to the Merchandise Store account with a date range of Feb 1, 2016 - Feb 29, 2016 to answer the following questions:
2.
Under Conversions, in the Goals Overview report with a Custom Segment for sessions in which users visited a page with "Android" in the title, how many Goal Completions occurred?
a. 330
b. 4,355
c. 9,852
d. 10,865
What is a commerce platform?
Answers
Answer:
In basic terms, a commerce platform simply refers to technology that enables a transaction (the commerce bit). The platform part allows you to overlay that technology across various channels such as online and in-store.
Answer:
Explanation:
a commerce platform simply refers to technology that enables a transaction (the commerce bit). The platform part allows you to overlay that technology across various channels such as online and in-store.20 Feb 2017
What is the purpose of the Revisions pane in a presentation?
to make suggestions for improvement
to organize and rename groups of slides
to leave comments on slides for other users
to delete all the slides in a presentation at once
Answers
Sorry if I’m wrong
Answer:
to make suggestions for improvement
What does CAD stand for?
Communicating Assisted Design
Counting All Dimensions
Computer Aided Design
Computer Assisted Development
helppp pless....!
Answers
Computer Aided Design is the correct answer
Answer:
C. Computer Aided Development
Explanation:
CAD stand for Computer Aided Development
I hope it helps! Have a great day!
Lilac~
Walt has selected data in a worksheet and inserted a chart. However, the chart is inserted right on top of the data set, and he cannot see the data. How should Walt most efficiently fix this situation?
A) Cut and paste the chart to a different worksheet or to a different part of the current worksheet.
B) Delete the current chart and first select a blank sheet or space before inserting the chart again.
C) Right-click the chart and select Move Below Data Table from the menu list.
D) Click View and zoom into the worksheet so the chart is easily visible.
Answers
Answer:
Answer Should be C but I cant say for sure
Explanation:
Answer:
C
Explanation:
Edge 2020
_____ merges each of the rows in the selected range across the columns in the range.
Answers
Answer:
Merge and Center
Explanation:
It is correct trust me
which memory can be removed from motherboard? RAM OR ROM?
Answers
Answer:
RAM is random-access memory and it can be removed from the motherboard.
Feel free to mark as brainliest :D
Type the correct answer in the box. Spell all words correctly.
Complete the sentence to highlight an area of application of procedural languages.
“what” is an open source operating system that programmers developed based on a procedural language.
Answers
It is to be noted that Linux is an open-source operating system that programmers developed based on a procedural language.
What are procedural languages?FORTRAN, COBOL, ALGOL, BASIC, C, and Pascal are examples of procedural languages. Non-Procedural Language: In non-procedural languages, the user specifies just "what to do" rather than "how to do." It's sometimes referred to as an applicative or functional language.
Linux was created in C, assembly languages, and other programming languages. Linux is an open-source operating system comprised of the kernel, the OS's core component, and the tools, programs, and services that come with it.
Learn more about Linux:
https://brainly.com/question/15122141
#SPJ1
Pro and Cons of Artificial Intelligence in Art
You must have 3 statements in each
Answers
Answer:
The answer is below
Explanation:
Aritifiaicla intelligence in art is an artwork created by the application of artificial intelligence software.
Some of the pros of artificial intelligence in the art are:
1. It creates a new and improved interface, specifically in graphic design such as virtual reality and 3D printing
2. It creates and mixes the artistic ideas properly, such as mixing of different instruments in music to creates a new sound
3. It establishes graphical and visual display with no blemishes o,r error when applied accordingly, such as AUTOCAD
The cons of artificial intelligence in art are:
1. Artificial Intelligence lacks emotional sense. Hence it is challenging to display artistic elements that portray genuine emotions
2. It lacks creativity. Unlike humans, artificial intelligence is not as creative as humans when it comes to words or sentence constructions in an artistic sense.
3. It doesn't apply experience to its productions. Arts can be improved with more understanding of what is happening in the society or environment; artificial intelligence cannot translate its experience into arts formation.
____ is the type of direct connection most commonly used with smartphones and tablets to keep them connected to the internet via a cellular network.
Answers
The type of direct connection most commonly used with smartphones and tablets to keep them connected to the internet via a cellular network is known as cellular data. This technology allows users to connect to the internet using their cellular network provider, giving them access to the web from anywhere they can get a signal.
Cellular data is an essential feature for mobile devices, as it enables users to stay connected and access online services on the go. It is especially important for people who travel frequently, as they can use cellular data to access maps, email, social media, and other online services without relying on Wi-Fi networks. In recent years, cellular data technology has advanced significantly, with faster data transfer speeds and more reliable connections. This has enabled users to stream video, play games, and use other data-intensive services on their mobile devices without experiencing lag or buffering.
Overall, cellular data is a crucial feature for modern smartphones and tablets, allowing users to stay connected to the internet and access online services wherever they go. As mobile technology continues to evolve, we can expect cellular data to play an increasingly important role in how we stay connected and interact with the online world.
Learn more about Wi-Fi networks here-
https://brainly.com/question/31844027
#SPJ11
Why does a computer needs RAM
Answers
Answer:
The more RAM your CPU has access to, the easier its job becomes, which enables a faster computer. If you do not have a sufficient amount of RAM than your CPU has to work much, much harder to transfer data, which severally damages the computer's performance. Random access memory also helps your system support software.
Answer:
The more RAM your CPU has access to, the easier its job becomes, which enables a faster computer. If you do not have a sufficient amount of RAM than your CPU has to work much, much harder to transfer data, which severally damages the computer's performance. Random access memory also helps your system support software
which two features could be added to a game using an "if () then " block
Answers
The two features could be added to a game using an "if () then " block are:
Using nested If Then blocks.Checks the specific Bid quantity for the instrument. What does the If Then block mean?The If Then block is known to be the outputs one of a given two values, that is as a result of the value of a Boolean input.
Note that the input value is very important and as such, The two features could be added to a game using an "if () then " block are:
Using nested If Then blocks.Checks the specific Bid quantity for the instrument.Learn more about game from
https://brainly.com/question/1786465
#SPJ1
The four main parts of a computer system are the Input, output, processor, and:
O A core.
OB. hardware.
OC. software.
OD. storage.
Answers
Answer:D) Storage
Explanation:
what is bit and byte in computer
Answers
Hope this helps
Gian wants to add audio to his presentation. which audio type is not supported? midi file mp3 audio file windows media audio file tiff file
Answers
The information provided in the inquiry indicates that TIFF data file is not supported.
Describe a TIFF file.Computer files called TIFFs, which stand for Tag Image Format, are employed to store raster images and image data. If you want to minimize lossy file formats, TIFFs, which are a favorite among shooters, are a useful option to keep high-quality photographs before editing.
Is TIFF superior to JPEG?When modifying an image, think about storing it in a TIFF file rather than a JPEG. Although TIFF files were larger, they retain their quality and clarity even after being altered and saved numerous times. JPEGs, in contrast hand, will somewhat lose clarity and quality with each saving.
To know more about TIFF file visit:
https://brainly.com/question/20293277
#SPJ4
Read through the following scenario, and then decide which computer is the best fit.

Answers
Answer:
gaming pc?
Explanation:
i dont know why you have this question kinda weird but entertainment pc or gaming pc sounds right
Answer:
B. Gaming or media production computer
Explanation:
Gaming or media production computer is the best computer you'll need because if you don't have the best computer it probably won't work on you. But if you the gaming or media production computer it will work on you.
I hope this helps.<3
Have a nice day.<3
6.3 code practice edhisive
You should see the following code in your programming environment:
Import simplegui
Def draw_handler(canvas):
# your code goes here
Frame = simplegui.creat_frame(‘Testing’ , 600, 600)
Frame.set_canvas_background(“Black”)
Frame.set_draw_handler(draw_handler)
Frame.start()
Use the code above to write a program that, when run, draws 1000 points at random locations on a frame as it runs. For an added challenge, have the 1000 points be in different, random colors.
Answers
Answer:
import simplegui
import random
def draw_handler(canvas):
for x in range(1000):
colorList = ["Yellow", "Red", "Purple", "White", "Green", "Blue", "Pink", "Orange"]
c = random.choice(colorList)
x = random.randint(1,600)
y = random.randint(1,600)
canvas.draw_point([x, y], c)
frame = simplegui.create_frame('Testing', 600, 600)
frame.set_canvas_background("Black")
frame.set_draw_handler(draw_handler)
frame.start()
Explanation:
I used a for loop, setting my range to 1000 which is how you create exactly 1000 points. Next, I defined my color array, my x randint value, and my y randint value. I set both the x and y randint values to 1 - 600 since the frame is 600x600. The rest is pretty self explanatory.
keisha is a network administrator. she wants a cloud-based service that will allow her to load operating systems on virtual machines and manage them as if they were local servers. what service is keisha looking for?
Answers
The service is keisha looking for is cloud computing. Cloud computing depends on resource sharing to accomplish coherence.
In order to provide quicker innovation, adaptable resources, and scale economies, cloud computing, in its simplest form, is the supply of computing services via the Internet ("the cloud"), encompassing servers, storage, databases, networking, software, analytics, and intelligence.
The on-demand availability of computer system resources, in particular data storage (cloud storage) and processing power, without direct active supervision by the user, is known as cloud computing. Functions in large clouds are frequently dispersed over several sites, each of which is a data center. Cloud computing often uses a "pay as you go" model, which can help reduce capital expenses but may also result in unanticipated running expenses for users. Cloud computing depends on resource sharing to accomplish coherence.
To know more about cloud computing click here:
https://brainly.com/question/11973901
#SPJ4
Repeat this for circuits 4-6, 7-9, and 10-11. you should have a total of 4 screenshots with your fnt submission.
Answers
To repeat the process for circuits 4-6, 7-9, and 10-11, you need to follow the same steps as before. Here's a step-by-step guide:
1. Open the circuit diagram for circuit 4.
2. Analyze the components and connections in the circuit.
3. Calculate the values of any resistors, capacitors, or other components in the circuit.
4. Determine the voltage across each component and the current flowing through them, using Ohm's Law and Kirchhoff's laws.
5. Take a screenshot of the circuit diagram and label it as "Circuit 4."
6. Repeat steps 1-5 for circuits 5 and 6, taking screenshots and labeling them accordingly.
7. Move on to circuits 7-9 and repeat steps 1-5 for each circuit, taking screenshots and labeling them appropriately.
8. Finally, proceed to circuits 10 and 11, and repeat the same steps to analyze and capture screenshots for these circuits.
By following these steps, you will have a total of 4 screenshots with your final submission, labeled as Circuit 4, Circuit 5, Circuit 6, and Circuits 7-9 combined.
To know more about Kirchhoff's laws :
brainly.com/question/6417513
#SPJ11
log the 'age' property of the 'person' object
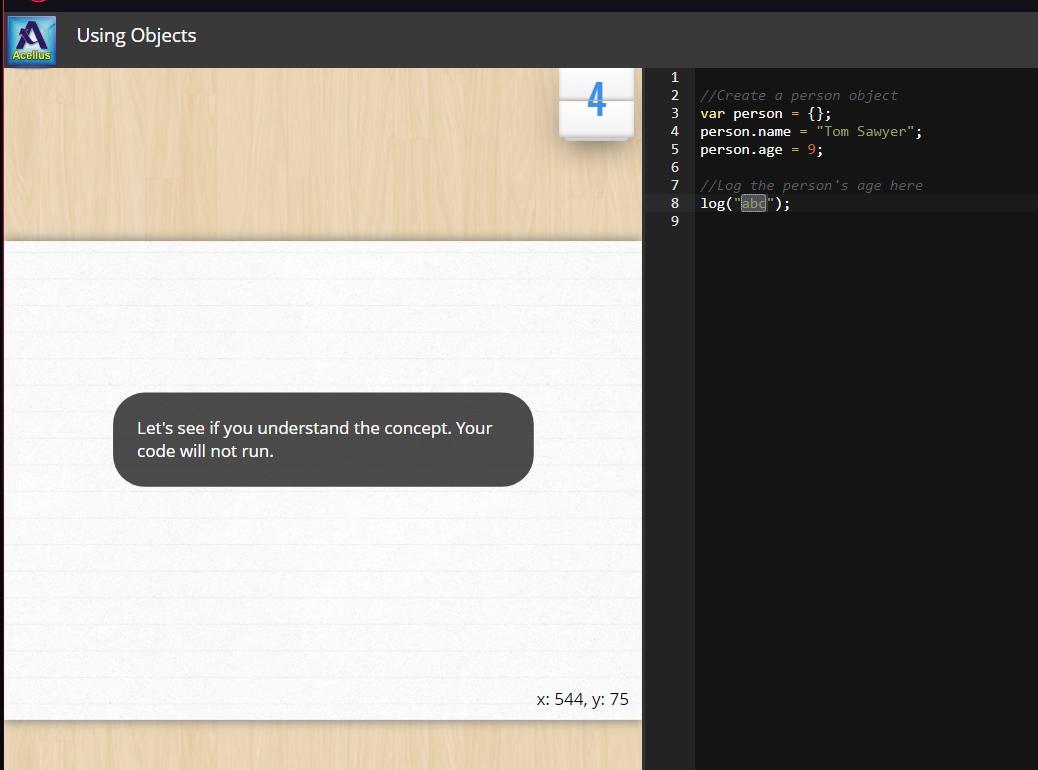
Answers
Answer:
vauwnwkwiauauwiajhwbwbw
How might you use what you learned about
creating a vision board in the future?
Answers
The question above pls answer quickly

Answers
Answer:
B
Explanation:
In cell J6, using a lookup function, enter a formula to determine the projected room classification based on the projected quarterly revenue after renovations in Cell I6, use the named range RoomClassification when entering this formula.
Answers
Assuming that cell I6 holds the anticipated quarterly revenue following renovations and that the designated range Room Classification comprises a table with two columns. =VLOOKUP(I6,RoomClassification,2,TRUE).
When performing a VLOOKUP, What does col index num mean?The related column number in the list is Col index num (Column index number). The column number in the table has nothing to do with where it is located in Excel.
What does the VLOOKUP function's Lookup value represent?Lookup value: Decide which cell will get the search values. Table array: The table range, which consists of every table cell. Col index num: The data being searched for.
To know more about columns visit:-
https://brainly.com/question/13602816
#SPJ1
What is Fill handle?
Answers
Answer: I copied and pasted my answer if you need the website to cite information let me know
Explanation:
Fill Handle is a feature in Excel that enables you to auto-complete a list in a row/column by simply dragging it using your mouse. A basic understanding of fill handle in Excel could save you some time and make you more productive.
4.2 Code Practice: Question 2
Instructions
Write a loop that continually asks the user what pets the user has until the user enters rock, in which case the loop ends. It should acknowledge the user in the following format. For the first pet, it should say You have a dog with a total of 1 pet(s) if they enter dog, and so on.
Sample Run
What pet do you have? lemur
What pet do you have? parrot
What pet do you have? cat
What pet do you have? rock
------------
Sample Output
You have a lemur with a total of 1 pet(s)
You have a parrot with a total of 2 pet(s)
You have a cat with a total of 3 pet(s)
Answers
Answer:
total = 0
while True:
pet = input("What pet do you have? ")
if pet == "rock":
break
total += 1
print("You have a {} with a total of {} pet(s)".format(pet, total))
Hope this helps!
Brainliest and a like is much appreciated!
When you insert a Quick table, you cannot format it true or false
Answers
Answer:
True
Explanation:
Format the table the way you want — e.g. borders, shading, row height, alignment, emphasis, font size, etc. for the heading row and the table rows. You can use manual formatting, or one of the built-in table designs
Katrina wants to get a random number and assign it to a variable called force. Which line of code should be used?
orce = random.randint(1,10)
force = random(1,10)
force = randint(1,10)
force == random.randint(1,10)
Answers
Since Katrina wants to get a random number and assign it to a variable called force the code to be used is
force = random.randint(1, 10)
How will the above code work?This line uses the randint function from the random module to generate a random integer between 1 and 10 (inclusive) and assigns it to the variable force
Computer code is a set of instructions or a set of rules written in a specific programming language (i.e., the source code) in computer programming.
Learn more about code at:
https://brainly.com/question/26134656
#SPJ1
a program p reads in 500 integers in the range [0..100] exepresenting the scores of 500 students. it then prints the frequency of each score above 50. what would be the best way for p to store the frequencies?
Answers
An array of size 50 will be best option to store number of students for each score.
frequencies of scores above 50 need to be stored. The scores below 50 and to index scores above 50 can be ignored, and 50 can be subtracted from score value. Thus -
Creating an array of integers with size=101, we will store frequency of numbers against the indexes of the array.
main()
[
int arr[101], i, temp;
for(i=0; i<101; i++)
arr[i]=0;
for(i=0; i<500; i++)
[
scanf("%d",& temp);
arr[temp]++;
]
for(i=0; i<102; i++)
if(arr[i] > 50)
printf(" frequency of %d is %d", i,arr[i]);
]
Thus, arr[i] will store frequency of number i.
learn more about index scores at
https://brainly.com/question/13873632
#SPJ4
Which explanation best explains the importance of using encryption?
Answers
Encryption is important because it protects sensitive information from unauthorized access. Encryption makes it difficult for hackers to steal personal and financial data, which can be used for identity theft, fraud, and other cyber crimes.
Step by step Explanation:
1. Encryption is a method of converting information into a code that only authorized individuals can read. The code is created using an encryption algorithm, which is a complex mathematical formula.
2. The importance of using encryption lies in its ability to protect sensitive information from unauthorized access. This includes personal and financial data, such as credit card numbers, social security numbers, and passwords.
3. Hackers and cyber criminals are always looking for ways to steal this type of information. If they are successful, they can use it for identity theft, fraud, and other crimes. Encryption makes it more difficult for them to do so.
4. Encryption is particularly important when data is transmitted over the internet. This includes online banking, e-commerce transactions, and email communication. Without encryption, this information can be intercepted and read by anyone with access to the internet.
5. Encryption also helps to protect information stored on electronic devices, such as laptops and smartphones. If these devices are lost or stolen, encryption can prevent unauthorized access to the data they contain.
6. In summary, encryption is important because it protects sensitive information from unauthorized access. It is a vital tool in the fight against cybercrime and is essential for ensuring the security and privacy of personal and financial data.
Know more about the encryption click here:
https://brainly.com/question/29572224
#SPJ11