Which type of computer is best for download the sims 4 game?
Answers
Answer:
LOL I DON'T EVEN KNOW
Explanation:
Related Questions
Creating a company culture for security design document
Answers
Use strict access control methods: Limit access to cardholder data to those who "need to know." Identify and authenticate system access. Limit physical access to cardholder information.
Networks should be monitored and tested on a regular basis. Maintain a policy for information security.
What is a healthy security culture?Security culture refers to a set of practises employed by activists, most notably contemporary anarchists, to avoid or mitigate the effects of police surveillance and harassment, as well as state control.
Your security policies, as well as how your security team communicates, enables, and enforces those policies, are frequently the most important drivers of your security culture. You will have a strong security culture if you have relatively simple, common sense policies communicated by an engaging and supportive security team.
What topics can be discussed, in what context, and with whom is governed by security culture. It forbids speaking with law enforcement, and certain media and locations are identified as security risks; the Internet, telephone and mail, people's homes and vehicles, and community meeting places are all assumed to have covert listening devices.
To learn more about security culture refer :
https://brainly.com/question/14293154
#SPJ1
what does the government payers or insurance carriers perform when an unusual billing pattern has been observed
Answers
Answer:
Whenever there is an unusual billing government payers or insurance carriers perform routine audits.
Examples of unusual billing patterns include but are not to:
the serial reoccurrence of the same diagnostic code after every visit;the repeated billing of the same procedure.These audits are performed using, in most cases, computer software applications which are capable of screening transactions to uncover such patterns.
Cheers!
Create a Python program that prints all the numbers from 0 to 4 except two distinct numbers entered by the user.
Note : Use 'continue' statement.
Answers
Here is a Python program that prints all numbers from 0 to 4, excluding two distinct numbers entered by the user, using the 'continue' statement:
```python
numbers_to_exclude = []
# Get two distinct numbers from the user
for i in range(2):
num = int(input("Enter a number to exclude: "))
numbers_to_exclude.append(num)
# Print numbers from 0 to 4, excluding the user-entered numbers
for i in range(5):
if i in numbers_to_exclude:
continue
print(i)
```
The program first initializes an empty list called `numbers_to_exclude` to store the two distinct numbers entered by the user.
Next, a loop is used to prompt the user to enter two distinct numbers. These numbers are appended to the `numbers_to_exclude` list.
Then, another loop is used to iterate through the numbers from 0 to 4. Inside the loop, an 'if' condition is used to check if the current number is in the `numbers_to_exclude` list. If it is, the 'continue' statement is executed, which skips the current iteration and proceeds to the next iteration of the loop.
If the current number is not in the `numbers_to_exclude` list, the 'print' statement is executed, and the number is printed.
This program ensures that the two distinct numbers entered by the user are excluded from the output, while all other numbers from 0 to 4 are printed.
For more such answers on Python
https://brainly.com/question/26497128
#SPJ8
What is the best way to deal with a spam
Answers
Simply ignoring and deleting spam is the best course of action. Avoid responding to or engaging with the spam communication because doing so can let the sender know that your contact information is still live and invite additional spam in the future. Additionally, it's critical to mark the email as spam using your email program or by reporting it to the relevant authorities. Make careful to report the spam to the proper authorities for investigation if it appears to be a phishing scheme or contains hazardous content.
Is unity a good game engine?
Answers
Answer:
Yes, though it can be pretty basic, because it is not needed to use coding
Explanation:
why are images important in research assignments? A. Because they allow your work to be cited by others B. Because they can illustrate an argument C. Because they are required before having your item published in the library database D. Because they take up more space than words in a document.
Answers
Answer:
C
Explanation:
Everything else does not make sense
There are 12 inches in a foot and 3 feet in a yard. Create a class named InchConversion. Its main() method accepts a value in inches from a user at the keyboard, and in turn passes the entered value to two methods. One converts the value from inches to feet, and the other converts the same value from inches to yards. Each method displays the results with appropriate explanation.
Answers
Answer:
import java.util.Scanner;
public class InchConversion
{
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
System.out.print("Enter inches: ");
double inches = input.nextDouble();
inchesToFeet(inches);
inchesToYards(inches);
}
public static void inchesToFeet(double inches){
double feet = inches / 12;
System.out.println(inches + " inches = " + feet + " feet");
}
public static void inchesToYards(double inches){
double yards = inches / 36;
System.out.println(inches + " inches = " + yards + " yards");
}
}
Explanation:
In the inchesToFeet() method that takes one parameter, inches:
Convert the inches to feet using the conversion rate, divide inches by 12
Print the feet
In the inchesToYards() method that takes one parameter, inches:
Convert the inches to yards using the conversion rate, divide inches by 36
Print the yards
In the main:
Ask the user to enter the inches
Call the inchesToFeet() and inchesToYards() methods passing the inches as parameter for each method
How to use the screen mirroring Samsung TV app
Answers
If you want to show what's on your phone or computer screen on a Samsung TV, you can do it by these steps:
Make sure both your Samsung TV and the thing you want to copy are using the same Wi-Fi.
What is screen mirroringThe step also includes: To get to the main menu on your Samsung TV, just press the "Home" button on your remote.
The screen mirroring is Copying or making a duplicate of something. They are repeating each other's words to try to fix the problem between them. This is the way to show what is on your computer or phone screen on another screen by using wireless connection.
Learn more about screen mirroring from
https://brainly.com/question/31663009
#SPJ1
Which of the following best describes an insider attack on a network?
OA. an attack by someone who uses fake emails to gather information related to user credentials
OB. an attack by someone who becomes an intermediary between two communication devices in an organizatio
OC. an attack by a current or former employee who misuses access to an organization's network
O D. an attack by an employee who tricks coworkers into divulging critical information to compromise a network
Answers
An attack by a current or former employee who misuses access to an organization's network ca be an insider attack on a network. The correct option is C.
An insider attack on a network refers to an attack carried out by a person who has authorized access to an organization's network infrastructure, either as a current or former employee.
This individual intentionally misuses their access privileges to compromise the network's security or to cause harm to the organization.
Option C best describes an insider attack as it specifically mentions the misuse of network access by a current or former employee.
The other options mentioned (A, B, and D) describe different types of attacks, but they do not specifically involve an insider with authorized access to the network.
Thus, the correct option is C.
For more details regarding network, visit:
https://brainly.com/question/29350844
#SPJ1
Which copy of the speech did Lincoln sign?
Answers
Which of the following would a dialogue editor most likely do if an actor makes a lip smacking sound during a dialogue sequence?
A)Use an ADR
B)Review raw footage to layer over the dialogue
C)Use voice over narration
D)Remove it and replace it with another sound
Answers
Answer:
c
Explanation:
Assume you have a data definition class called Account. You wish to create a specific type of account, called MoneyMarketAccount. Write the first line of code that will declare the MoneyMarketAccount class.
Answers
Answer:
It depends on the code that has to be used, but in general C++ and python are shown below.
Explanation:
for a .cpp code we have:
class MoneyMarketAccount: public Account
in a .py code in the console, the following part has to be added
class MoneyMarketAccount(Account)
problem description IT
Answers
In IT, a problem description refers to a clear and concise explanation of an issue or challenge that needs to be resolved within a technology system or application.
How is this so?It involves providing relevant details about the symptoms, impact, and context of the problem.
A well-written problem description outlines the specific errors, failures, or undesired behavior observed and provides enough information for IT professionals to analyze and identify potential solutions.
A comprehensive problem description is crucial for effective troubleshooting and problem-solving in the IT field.
Learn more about Problem Description at:
https://brainly.com/question/25923602
#SPJ1
which of the following is not the correct definition of an operating system
A.
it controls all other execution in a computer
B.
interface between hardware and application programs
C.
its a platform for ensuring that other executions has taken place
D.
maintains consistency of data loss during execution
Answers
The correct answer is C. An operating system is not a platform for ensuring that other executions have taken place. An operating system is a software program that manages the hardware and software resources of a computer and provides common services for computer programs. It acts as an interface between the hardware and application programs and controls all other execution in a computer. It also maintains consistency of data during execution.
Users are unable to open files that are not relevant to their jobs. Users can open and view files but are unable to edit them. Users can open, view, and edit files. The bullet points above describe _____. Responses access privileges firewalls network topologies modems
Answers
Answer:
Explanation:
them
>>> phrase = "abcdefgh"
>>> phrase[3:6]
Answers
Answer:
Following are the correct code to this question:
phrase = "abcdefgh"#defining a variable phrase that holds a string value
print(phrase[3:6])#use print method for slicing and print its value
Output:
def
Explanation:
In the above code, a variable "phrase" is defined that holds a string value, and use a print method, inside the method, the variable is used as a list and use slicing.
It is a characteristic that enables you to access the series parts like strings, tuples, and lists. It also uses for modifying or removing objects in series, in the above slicing it starts from 3 and ends when it equal to the 6th letter, that's why it will print "def".
Imagine you're an Event Expert at SeatGeek. How would you respond to this customer?
* Hi SeatGeek, I went to go see a concert last night with my family, and the lead singer made several inappropriate comments throughout the show. There was no warning on your website that this show would not be child friendly, and I was FORCED to leave the show early because of the lead singer's behavior. I demand a refund in full, or else you can expect to hear from my attorney.
Best, Blake
Answers
By Imagining myself as an Event Expert at SeatGeek.I would respond to the customer by following below.
Dear Ronikha,
Thank you for reaching out to SeatGeek regarding your recent concert experience. We apologize for any inconvenience caused and understand your concerns regarding the lead singer's inappropriate comments during the show.
We strive to provide accurate and comprehensive event information to our customers, and we regret any oversight in this case.
SeatGeek acts as a ticket marketplace, facilitating the purchase of tickets from various sellers. While we make every effort to provide accurate event details, including any warnings or disclaimers provided by the event organizers, it is ultimately the responsibility of the event organizers to communicate the nature and content of their shows.
We recommend reaching out directly to the event organizers or the venue where the concert took place to express your concerns and seek a resolution.
They would be in the best position to address your experience and provide any applicable remedies.
Should you require any assistance in contacting the event organizers or obtaining their contact information, please let us know, and we will be happy to assist you further.
We appreciate your understanding and value your feedback as it helps us improve our services.
Best regards,
Vicky
Event Expert, SeatGeek
For more such questions Event,click on
https://brainly.com/question/30562157
#SPJ8
a democratic government has to respect some rules after winning the elections. Which of these points is not a part of those rules
Answers
After coming to power, a democratic administration is bound to follow certainrules and regulations. And Office-bearers are not accountable is not a part of those rules.
How is this so?In a democratic administration,office-bearers are indeed accountable as they are bound by rules and regulations.
The accountability ensures transparency,ethical conduct, and adherence to the principles of democracy.
Office-bearers are expected to uphold the laws and serve the interests of the people they represent.
Learn more about democratic administration at:
https://brainly.com/question/31766921
#SPJ1
Compare and contrast predictive analytics with prescriptive and descriptive analytics. Use examples.
Answers
Explanation:
Predictive, prescriptive, and descriptive analytics are three key approaches to data analysis that help organizations make data-driven decisions. Each serves a different purpose in transforming raw data into actionable insights.
1. Descriptive Analytics:
Descriptive analytics aims to summarize and interpret historical data to understand past events, trends, or behaviors. It involves the use of basic data aggregation and mining techniques like mean, median, mode, frequency distribution, and data visualization tools such as pie charts, bar graphs, and heatmaps. The primary goal is to condense large datasets into comprehensible information.
Example: A retail company analyzing its sales data from the previous year to identify seasonal trends, top-selling products, and customer preferences. This analysis helps them understand the past performance of the business and guide future planning.
2. Predictive Analytics:
Predictive analytics focuses on using historical data to forecast future events, trends, or outcomes. It leverages machine learning algorithms, statistical modeling, and data mining techniques to identify patterns and correlations that might not be evident to humans. The objective is to estimate the probability of future occurrences based on past data.
Example: A bank using predictive analytics to assess the creditworthiness of customers applying for loans. It evaluates the applicants' past financial data, such as credit history, income, and debt-to-income ratio, to predict the likelihood of loan repayment or default.
3. Prescriptive Analytics:
Prescriptive analytics goes a step further by suggesting optimal actions or decisions to address the potential future events identified by predictive analytics. It integrates optimization techniques, simulation models, and decision theory to help organizations make better decisions in complex situations.
Example: A logistics company using prescriptive analytics to optimize route planning for its delivery truck fleet. Based on factors such as traffic patterns, weather conditions, and delivery deadlines, the algorithm recommends the best routes to minimize fuel consumption, time, and cost.
In summary, descriptive analytics helps organizations understand past events, predictive analytics forecasts the likelihood of future events, and prescriptive analytics suggests optimal actions to take based on these predictions. While descriptive analytics forms the foundation for understanding data, predictive and prescriptive analytics enable organizations to make proactive, data-driven decisions to optimize their operations and reach their goals.
An array called numbers contains 35 valid integer numbers. Determine and display how many of these values are greater than the average value of all the values of the elements. Hint: Calculate the average before counting the number of values higher than the average
Answers
python
Answer:
# put the numbers array here
average=sum(numbers)/35 # find average
count=0 #declare count
for i in numbers: #loop through list for each value
if i > average: #if the list number is greater than average
count+=1 #increment the count
print(count) #print count
Calculate how much disk space (in sectors, tracks, and surfaces) will be required to
store 300,000 120-byte logical records if the disk is fixed sector with 512 bytes/
sector, with 96 sectors/track, 110 tracks per surface, and 8 usable surfaces. Ignore
any file header record(s) and track indexes, and assume that records cannot span
two sectors.
It will be great if you could explain the answer to me. :)
Answers
Answer:
see your answer in image
mark me brainlist


The amount of disk space in sectors that would be required to store 300,000 records is equal to 75,000 sectors.
Given the following data:
Number of records = 300,000.Size of each logical record = 120 byte.Number of bytes (sector) = 512.Number of sectors per track = 96.Number of tracks per surface = 110.How to calculate the required disk space?First of all, we would determine the number of logical records that can be held by each sector as follows:
Number of logical records per sector = 512/120
Number of logical records per sector = 4.3 ≈ 4.0.
Now, we can calculate the required disk space to store 300,000 records:
Disk space = 300,000/4
Disk space = 75,000 sectors.
For the tracks, we have:
Disk space in tracks = 75,000/96
Disk space in tracks = 781.25 ≈ 782.
Disk space in tracks = 782 tracks.
For the surfaces, we have:
Disk space in surfaces = 782/110
Disk space in surfaces = 7.10 ≈ 8.
Disk space in surfaces = 8 surfaces.
Read more on disk space here: https://brainly.com/question/26382243
WHICH PROGRAMMING LANGUAGES ARE THE BEST FOR PROGRAMMING?
Answers
Answer:
python is probably the best is you are a begginer
java and C++ are good too
Plz help, will guve brainliest to best answer (if i can)

Answers
Answer:
Online text:1,3,4
not online text:2,5
What is a search engine
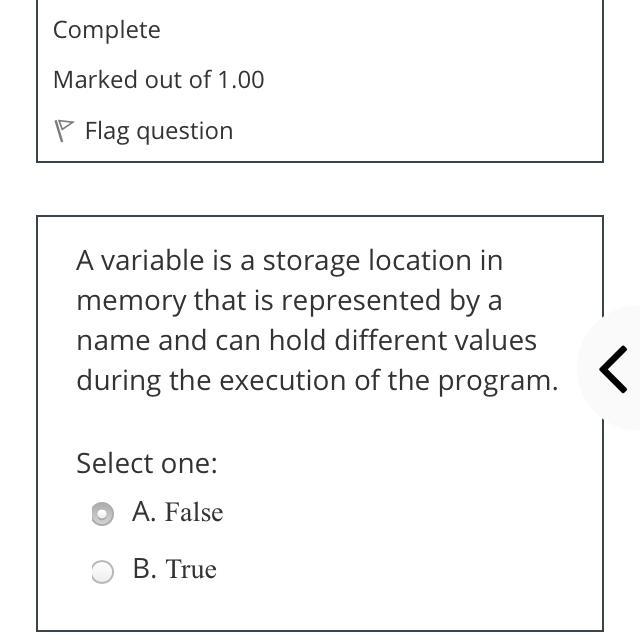
Answers
Answer:
dababy
Explanation:

Code to be written in R language:
The Fibonacci numbers is a sequence of numbers {Fn} defined by the following recursive relationship:
Fn= Fn−1 + Fn−2, n > 3
with F1 = F2 = 1.
Write the code to determine the smallest n such
that Fn is larger than 5,000,000 (five million). Report the value of that Fn.
Answers
Here is the R code to determine the smallest n such that the Fibonacci number is larger than 5,000,000:
fib <- function(n) {
if (n <= 2) {
return(1)
} else {
return(fib(n - 1) + fib(n - 2))
}
}
n <- 3
while (fib(n) <= 5000000) {
n <- n + 1
}
fib_n <- fib(n)
cat("The smallest n such that Fibonacci number is larger than 5,000,000 is", n, "and the value of that Fibonacci number is", fib_n, "\n")
The output of this code will be:
The smallest n such that Fibonacci number is larger than 5,000,000 is 35 and the value of that Fibonacci number is 9227465.
Learn more about R language here: https://brainly.com/question/14522662
#SPJ1
What is the purpose of the property, transition-timing-function?
It sets how many times a transition will play.
It delays the start of a transition by a set number of seconds.
It changes the speed at different stages of the transition.
It adds a pause between steps in an animation.
Answers
Answer:
It changes the speed at different stages of the transition.
Explanation:
HTML is an acronym for hypertext markup language and it is a standard programming language which is used for designing, developing and creating web pages.
Generally, all HTML documents are divided into two (2) main parts; body and head. The head contains information such as version of HTML, title of a page, metadata, link to custom favicons and CSS etc. The body of the HTML document contains the contents or informations that a web page displays.
Basically, the purpose of the property, transition-timing-function is that It changes the speed at different stages of the transition. Thus, it states the values between the beginning and ending of a transition are calculated over its duration.
The Chief Information Officer (CIO) has determined the company’s new PKI will not use OCSP. The purpose of OCSP still needs to be addressed. Which of the following should be implanted?A. Build an online intermediate CA.B. Implement a key escrow.C. Implement stapling.D. Install a CRL.
Answers
Answer:
B. Implement a key escrow.
Explanation:
A key escrow can be defined as a data security method of storing very essential cryptographic keys.
Simply stated, key escrow involves a user entrusting his or her cryptographic key to a third party for storage.
As a standard, each cryptographic key stored or kept in an escrow system are directly linked to the respective users and are encrypted in order to prevent breach, theft or unauthorized access.
Hence, the cryptographic keys kept in an escrow system are protected and would not be released to anyone other than the original user (owner).
In this scenario, the Chief Information Officer (CIO) has determined the company's new public key infrastructure (PKI) will not use online certificate status protocol (OCSP). However, the purpose of online certificate status protocol (OCSP) still needs to be addressed. Thus, what should be implemented is a key escrow because the online certificate status protocol (OCSP) is an internet protocol used for maintaining the security of a server and obtaining a digital certificate that has been revoked.
Olivia is excited about with the golf clubs Justin gave her for her birthday, so she smiles broadly and jumps up and down. Olivia’s use of nonverbal communication is an example of which principle of nonverbal communication?
Group of answer choices
Nonverbal communication is more ambiguous than verbal
Nonverbal communication is more credible
Nonverbal messages structure conversation
Nonverbal communication conveys emotional messages
Answers
Olivia's use of nonverbal communication in this situation is an example of the principle that nonverbal communication conveys emotional messages.
What is communication?Olivia's broad smile and jumping up and down indicate her excitement and happiness about the gift she received. Nonverbal cues such as facial expressions, tone of voice, and body language often convey emotions more accurately and powerfully than words alone.
Therefore, Nonverbal communication refers to any form of communication that does not involve the use of words, such as facial expressions, body language, gestures, and tone of voice. It is an important aspect of human communication because it can convey a range of messages and emotions that cannot be expressed through words alone.
Read more about communication here:
https://brainly.com/question/28153246
#SPJ1
What is the correct command to shuffle the following list? import random people= ["Peter", "Paul", "Mary', 'Jane'] O shuffle (people) Opeople.shuffle() random.shuffle (people) random.shufflelist(people)
Answers
Answer:
import random
people = ["Peter", "Paul", "Mary", "Jane"]
random.shuffle(people)
Explanation:
EVALUATING A HUMAN RIGHTS CAMPAIGN • Identify an organization (name) and the human right that they are campaigning for. (1+2=3) • Describe (their) FOUR possible objectives of the campaign (4x2=8) • Discuss THREE actions that you may take to get involved in a campaign (3x2=6) Evaluate the success of the campaign (indicate their successes, challenges, failures) (3x2=6) [44] 4. RECOMMENDATIONS Recommend, at least TWO practical ways by which the campaign could be assisted to ensure its successes. (2x2=4) 5. CONCLUSION In your conclusion, summarize the significance of key findings made out of your evaluation and suggest about what could be done about the findings (1x3=3)
Answers
With regards to the human rights campaign, Amnesty International's campaign for freedom of expression plays a vital role, with successes, challenges, and room for improvement through collaboration and engagement.
The explanation1. The Organization is Amnesty International
Human Right is Freedom of Expression
2. Objectives is Raise awareness, advocate for release of imprisoned individuals, lobby for protective laws, mobilize public support.
3. Actions is Join as member/volunteer, sign petitions, attend protests.
4. Evaluation is Successes include increased awareness and releases, challenges faced from governments and limited resources, failures in changing repressive laws.
5. Recommendations is Collaborate with organizations, engage influencers to amplify impact.
Conclusion - Amnesty International's campaign for freedom of expression plays a vital role, with successes, challenges, and room for improvement through collaboration and engagement.
Learn more about Human rights campaign at:
https://brainly.com/question/31728557
#SPJ1