which of the following statements about security in the network is true? computers a and d need to communicate with at least two additional computers in the network in order to communicate with each other. computers b and c can communicate with each other without additional computers being aware of the communication.
Answers
The statement b: "computers b and c can communicate with each other without additional computers being aware of the communication" is true.
This is because if computers B and C are directly connected to each other, they can communicate without the need for any other computers to be involved or aware of the communication. On the other hand, the statement "computers A and D need to communicate with at least two additional computers in the network in order to communicate with each other" is not necessarily true. It depends on the network topology and the routing protocols being used. In some cases, it may be possible for computers A and D to communicate directly with each other without the need for additional computers.
Option b is answer.
You can learn more about network at
https://brainly.com/question/30696348
#SPJ11
Related Questions
How the inheritance works in a world of contexts? For example, in space-craft, on earth, and when context changes from one to other?
THIS question is from a course- introduction to artificial intelligence. please answer based on that subject.
Answers
In the context of artificial intelligence, inheritance refers to the mechanism by which a class can inherit properties and behaviors from another class. Inheritance allows for code reuse, modularity, and the creation of hierarchies of classes with shared characteristics.
When considering the concept of inheritance in the context of different worlds or contexts, such as a space-craft and on Earth, it is important to understand that inheritance is primarily a programming concept that allows for code organization and reuse. The actual behavior and characteristics of objects in different contexts would be implemented and determined by the specific logic and rules of the AI system.
In the case of a space-craft and Earth, for example, there might be a base class called "Vehicle" that defines common properties and behaviors shared by both space-craft and Earth vehicles. This could include attributes like speed, capacity, and methods for propulsion. Specific subclasses like "Spacecraft" and "EarthVehicle" could then inherit from the "Vehicle" class and define additional attributes and behaviors that are specific to their respective contexts.
Know more about inheritance here:
https://brainly.com/question/31824780
#SPJ11
if r1 5 11110000111000101010000011111101 and r2 5 00000000111111110000111100001111, what is the value of r3 after executing bic r3,r1,r2?
Answers
BIC instruction is a logical operation that clears bits in a register. This instruction clears the bits specified by the second operand in the first operand. The value of r3 is 0xF05070.
After executing bic r3, r1, r2, the value of r3 can be calculated as follows:The bit-wise not operation is applied to the second operand, r2, as it needs to be used for the AND operation. The result of the bit-wise not operation is 11111111000000001111000011110000.BIT-wise AND is then applied to the first operand, r1, and the result of the bit-wise not operation on the second operand, r2. The result is: 11110000011000001010000011110000.
To know more about operand visit:
https://brainly.com/question/27014457
#SPJ11
Stella has captured this candid photograph of a man who was reunited with his son. She has used facial retouching in each of the images. Which images could she print along with the mans interview?

Answers
Answer: The last picture it looks better.
Explanation: Welcome!
Answer:
4
Explanation:
anyone who like memes? IG= mdkmdk1911
Answers
Answer:
I love them so much, they are the best
Find the maximum number of paths between any two vertices of a
tree.
Answers
The maximum number of paths between any two vertices of a tree can be determined using the formula `n(n-1)/2A tree is a connected graph having no encryption cycles.
In a tree with `n` vertices, the maximum number of paths between any two vertices can be determined using the formula `n(n-1)/2`. This formula is derived as follows: For a given vertex, there are `n-1` vertices that it can be connected to directly (excluding itself).
Therefore, the maximum number of paths from this vertex is `n-1`.Similarly, for each of the `n-1` vertices that are connected to the first vertex, there are `n-2` vertices that they can be connected to (excluding themselves and the first vertex). Therefore, the maximum number of paths from each of these vertices is `n-2`.Continuing this pattern for all `n-1` vertices, we get the following sum:`(n-1) + (n-2) + (n-2) + ... + 1 = (n-1) + ((n-2) + (n-3) + ... + 1) = (n-1) + ((n-2)(n-1)/2) = n(n-1)/2`Therefore, the maximum number of paths between any two vertices of a tree with `n` vertices is `n(n-1)/2`.
To know more about encryption visit:
https://brainly.com/question/30225557
#SPJ11
In the context of gps-enabled location-based services, the ability to see another person's location is an example of ________ service.
Answers
In the context of GPS-enabled location-based services, the ability to see another person's location is an example of a tracking service.
What are GPS-enabled location-based services?GPS-enabled location-based services are smartphone applications that use the device's location information to deliver services, content, or advertising relevant to a user's current location.
Users can receive information on restaurants, shops, events, and other points of interest within their current location, as well as reviews, ratings, and recommendations for these locations.
Learn more about GPS at:
https://brainly.com/question/14897262
#SPJ11
programs designed to boost adherence to exercise are somewhat successful but an alternative to such program is
Answers
While programs designed to boost adherence to exercise have shown some success, an alternative approach to promoting exercise adherence is to focus on creating an environment that naturally supports and encourages physical activity.
This alternative approach shifts the emphasis from relying solely on individual motivation and self-discipline to designing environments that make exercise more accessible, convenient, and enjoyable for individuals.
Creating an environment that supports exercise adherence involves making physical activity opportunities readily available and integrating them into everyday life. This can be achieved by establishing walking or cycling paths, promoting active transportation options, providing exercise facilities in workplaces or residential areas, and incorporating physical activity into the design of urban spaces. Additionally, community-wide initiatives, such as organizing sports events, fitness classes, or recreational activities, can help foster a culture of exercise and provide social support.
By focusing on environmental changes, the alternative approach aims to remove barriers and create opportunities for exercise without solely relying on individuals' willpower or motivation. This approach recognizes that human behavior is influenced by the context in which it occurs and that modifying the environment can have a profound impact on promoting long-term exercise adherence. It shifts the responsibility from solely relying on individuals to proactively seek out exercise opportunities to creating an environment that naturally supports and encourages physical activity, making it easier for individuals to incorporate exercise into their daily lives.
To learn more about self-discipline, click here:
brainly.com/question/2666700
#SPJ11
hammock activities are simply: a. another name for dependencies b. an activity sequencing ladder c. the shortest activity path through a network d. a means for disaggregating the project network into logical summaries
Answers
Hammock activities are simply a means for disaggregating the project network into logical summaries. Therefore option d is correct
To explain further, hammock activities in project management are used to summarize group-related activities within a project network. They do not represent specific tasks but rather serve as placeholders for a set of related activities. Hammock activities are typically used to simplify the representation of complex project networks by providing a way to summarize and organize dependencies. They help in creating logical summaries and allow for easier management and analysis of project schedules. Therefore, option d, "a means for disaggregating the project network into logical summaries," best describes hammock activities.
To learn more about Hammock activities: https://brainly.com/question/7899423
#SPJ11
You have created a new storage space using a single 500 GB external USB 3.0 drive. The drive is becoming full, so you add another external 1 TB USB 2.0 drive to the storage pool. Now that you have two drives, you would like to create a volume with storage space resiliency set to two-way mirror. You create the new volume with two-way resiliency and a size limit of 1 TB. As you are copying files from the C: drive to this new volume, you receive a warning that you are running out of space. Only a few hundred megabytes have been copied; why might you be receiving the warning so quickly? What can you do about it?
Answers
Answer:
In the clarification section following, the definition including its query is mentioned.
Explanation:
I believe we possess 2 other discs except for the major memory card-a USB 500 GB USB 3.0 drive, just one TB USB 2.0 drive. So we're making a two-array mirrored storage space resilience kit. We get a warning when we duplicate files from either the C: drive towards this second adaptation that you should be running out of places. That was because these need to have a backup process around each other discs throughout the situation of a two-way mirror.This serves to protect the organization from disc failure and enhances the overall efficiency of the device. Thus, even when copying, even though only several 100 MB has also been cut and pasted to something like the disc, the disc intercepts that the information collected from either the 500 GB drive as well as the major disc must be stored there. And that is how the alert arrives that throughout the new trip, we're running out of space. So this is how they so easily get the alarm.
Edhesive 6.7 code practice

Answers
May I ask, when you accidently drop your laptop into a pool,...(water) . Will the Data and Many other information... inside the laptop gone?
Answers
Answer:
no
Explanation:
when its being repaired you will get all your information back. Unless you drop it in fire or your hard disk get crushed or formatted
HELPPPPPPPPPPPPPPPPPPPPPPPPPPPPPPP!!!
Express the diagram in the form of a logic statement. [2]
P = ________________________
3. (a) Complete the truth table below for the logic circuit which is made up of NAND gates only.
![HELPPPPPPPPPPPPPPPPPPPPPPPPPPPPPPP!!!Express the diagram in the form of a logic statement. [2] P = ________________________3.](https://i5t5.c14.e2-1.dev/h-images-qa/contents/attachments/NoE1DnieovxjZViB66UnB8fBINlICMCx.jpeg)
Answers
Answer:
different or difference between Dot-matrix and Daisy-wheel printer
You are designing a simple calculator program for young children to use. Right now, if they do something that the program didn’t expect, a message appears that reads, “User input deemed invalid.” What changes could you make so that the message would be more suitable for this audience?
Answers
The change you could make to make the message more suitable for this audience would be to identify a suitable message so that the children understand that they made a mistake using the program. For example: You made a mistake, try again.
What is a user input?A user input is a term that refers to the action performed by a user of a digital system or a specific program. This message has been standardized to indicate to the user that he has made a mistake in pressing buttons or in handling a program.
How to modify the message?To modify the message we must edit the base font of the program so that the message that we want to appear on the screen is different. On the other hand, we must identify a message that is simple and direct so that the children understand that they made a mistake when using the program.
What message can we put for the children?The right message for children should clearly communicate to them what has happened without discouraging them. So a suitable example of a message would be:
You've made a mistake, try again.Learn more about user input in: https://brainly.com/question/8789964
#SPJ1
linux even though being posix compliant, was originally unsuitable for hard real time systems because it
Answers
The statement is true. Linux, despite being POSIX compliant, was initially unsuitable for hard real-time systems due to certain limitations.
Linux is a widely used open-source operating system that adheres to the POSIX (Portable Operating System Interface) standards, which define a set of APIs and interfaces for compatibility between operating systems. However, Linux was originally not suitable for hard real-time systems. Real-time systems require precise and deterministic timing behavior to meet strict deadlines, which was not adequately supported by the early versions of the Linux kernel.
The Linux kernel, being designed primarily for general-purpose computing, had certain limitations that made it unsuitable for hard real-time applications. One of the main issues was the lack of sufficient mechanisms for providing strict real-time guarantees, such as bounded interrupt latencies and predictable scheduling. The scheduling algorithms and interrupt handling in the early Linux kernels were optimized for throughput and fairness rather than deterministic timing.
To address these limitations, specialized real-time variants of Linux, such as the PREEMPT-RT patchset, were developed. These variants introduced enhancements to the kernel, including a real-time scheduler, improved interrupt handling, and other optimizations to provide better real-time capabilities. With these modifications, Linux has become more suitable for hard real-time systems, although it may still have limitations compared to dedicated real-time operating systems.
Learn more about Linux here: https://brainly.com/question/32173761
#SPJ11
Who monitors the remaining work of the Sprint Backlog?
Answers
The Development Team monitors the remaining work of the Sprint Backlog. They update the progress during the Daily Scrum to ensure they are on track to meet the Sprint Goal.
During the Daily Scrum, the Development Team discusses their progress towards completing the Sprint Backlog items. They update the remaining work estimates and make any adjustments to the plan as necessary. The Development Team is responsible for monitoring their own progress and ensuring that they are on track to complete the work within the Sprint timebox. If they identify any obstacles or risks, they raise them during the Daily Scrum so that the team can work together to address them. Ultimately, the Development Team is accountable for delivering a potentially releasable increment of the product at the end of the Sprint, and monitoring the remaining work of the Sprint Backlog is an important part of achieving this goal.
learn more about Sprint here:
https://brainly.com/question/31230662
#SPJ11
HELP!!
A delivery of information from one person—or a small team of people—to an audience is called a ____________.
Question 8 options:
Presentation
Template
Speaker Notes
Slide Show Toolbar
Answers
Answer:
Presentation
Explanation:
Information is being presented to an audience (this makes sense).
A template can be used to organize the information that is to be given to the audience.
Speaker notes only help the speaker give the information to the audience.
Slide how toolbar is only for creating the slideshow that can be used to help the audience understand what the speaker is saying.
by default, where is the print queue stored within windows server 2012/r2?
Answers
In Windows Server 2012/R2, the print queue is stored by default in the spooler folder located at C:\Windows\System32\spool\PRINTERS.
This folder holds all pending print jobs until they are processed and sent to the printer.
The print queue is managed by the print spooler service, which runs in the background and controls the flow of print jobs to the printer. The spooler folder can be accessed by administrators to manage and troubleshoot print jobs, including deleting or pausing jobs if necessary.
It is important to ensure that this folder is periodically checked and cleared to prevent any build-up of old or unnecessary print jobs.
Learn more about print queue at https://brainly.com/question/32149805
#SPJ11
what is role can ICT play in helping school take part in social responsibility
Answers
Answer:
The answer is below
Explanation:
Given that Social responsibility deals with ideas that individuals or groups of people are expected or bound to work in alliance with other individuals or groups of people in favor of the generality of society.
Hence, some of the role ICT can play in helping school take part in social responsibility are:
1. Helps students to have independent access to knowledge
2. It assists the students with special needs
3. It helps the teachers to teach outside the comfort of the classroom only.
4. It exposes teacher and students to more knowledge and opportunities
5. The school governing body can access people and the community's opinions about ways to improve the school better.
6. It exposes the school to more ideas and opportunities.
7. It can be used to assist the school in improving the quality of education, both for the teachers and students side.
True or false? A virtual IP is a means by which two appliances can be put in a fault tolerant configuration to respond to requests for the same IP address?
Answers
True. A virtual IP (VIP) is an IP address that is not associated with a particular physical interface on a network device. It can be used to provide a fault-tolerant configuration in which multiple devices share a common IP address.
In a fault-tolerant configuration, if one device fails, another device takes over the virtual IP address to ensure that network services remain available. This is often accomplished using a technique called virtual IP failover, where a backup device takes over the virtual IP address if the primary device fails.
So, in summary, a virtual IP is a means by which two or more devices can share the same IP address and provide fault tolerance for network services.
To know more about virtual IP click this link -
brainly.com/question/31674088
#SPJ11
true or false: the ride-sharing company uber is an example of technological convergence.
Answers
True. The ride-sharing company Uber is definitely an example of technological convergence.
Technological convergence is the process by which different types of technology merge together to create a new, more advanced technology. In the case of Uber, it involves the convergence of smartphones, GPS technology, and payment systems. Uber's app uses GPS to track the location of the rider and driver, smartphones to connect them, and payment systems to process the payment for the ride. The combination of these technologies has made it possible for Uber to create a new and innovative service that is changing the way people think about transportation. In addition, Uber's use of big data and algorithms to optimize its service is also an example of technological convergence, as it combines the fields of computer science, data analytics, and transportation. Overall, Uber is a prime example of how technological convergence can lead to disruptive innovation and transform entire industries.
Learn more about technological convergence here:
https://brainly.com/question/30538435
#SPJ11.
Please! I need help matching this.
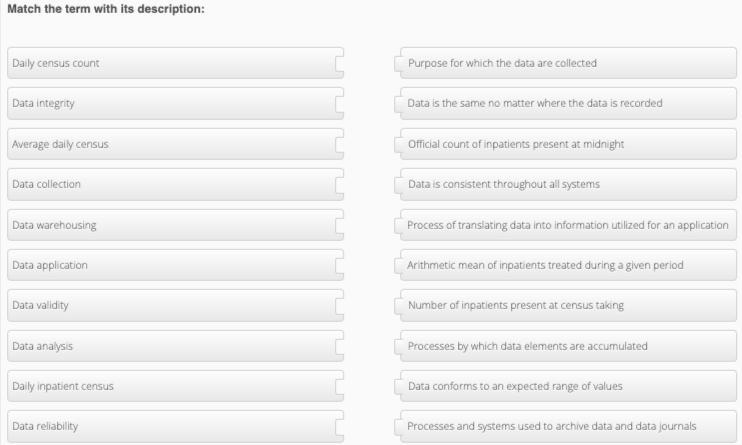
Answers
We can see here that matching the term with its description, we have:
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1
As an ________ ________ __________ , the mobile and multimedia Internet is altering our quality of life, our quality of health, the way we interact socially and more.
Answers
As an agent of change, the mobile and multimedia Internet is altering our quality of life, our quality of health, the way we interact socially and more.
Describe the five steps of the process of assessing personal strengths and weaknesses
Answers
•Revisit past feedback. ...
•“Hire” yourself. ...
•Revisit your strength list.
quick I need help ASAP
Question 1 (1 point)
Why in the world would you need a spreadsheet?
Question 2 (1 point)
What are spreadsheets used for?
Question 3 (1 point)
What does this unit cover
this is a k12 test
Answers
Answer:
1. Spreadsheets are an essential business and accounting tool. They can vary in complexity and can be used for various reasons, but their primary purpose is to organize and categorize data into a logical format. Once this data is entered into the spreadsheet, you can use it to help organize and grow your business.
2. A spreadsheet is a tool that is used to store, manipulate and analyze data. Data in a spreadsheet is organized in a series of rows and columns and can be searched, sorted, calculated and used in a variety of charts and graphs.
3. ?
GOOD LUCK!
Answer:
DO NOT INCLUDE (1=) AND DO NOT FORGET TO INCLUDE THE PUNCTUATION.
Explanation:
1 = Spreadsheets are helpful when trying to manage large amounts of numerical data.
2= You might keep a spreadsheet if you keep track of your checkbook balance, the mileage on your car, your grades, or your workout results at the gym.
3= This unit covers the basics of spreadsheets—how to create them; what can be done using formulas and calculations; and how to format them.
Consider the following program running on the MIPS Pipelined processor studied in class. Does it has hazards? add $s0, $t0, $t1 sub $s1, $t2, $t3 and $s2, $s0, $s1 or $s3, $t4, $t5 slt $s4, $s2, $s3
Group of answer choices
True False
Answers
True. The given MIPS program has hazards.
The first instruction, "add $s0, $t0, $t1", writes the result to register $s0. The second instruction, "sub $s1, $t2, $t3", reads the value from register $t2, which is also needed as an input for the first instruction. This creates a data hazard known as a RAW (Read After Write) hazard, where the second instruction reads a register before the first instruction writes to it.
Similarly, the third instruction, "and $s2, $s0, $s1", reads the value from register $s0, which is also needed as an input for the first instruction. This creates another data hazard, where the third instruction reads a register before the first instruction writes to it.
Finally, the fourth instruction, "or $s3, $t4, $t5", reads the value from register $t5, which is also needed as an input for the fifth instruction. This creates a data hazard, where the fourth instruction reads a register before the fifth instruction writes to it.
Therefore, the given MIPS program has data hazards.
Learn more about MIPS here:
https://brainly.com/question/30543677
#SPJ11
Express 42 as a product of its prime factor
Answers
of primes.
Except to change the order of the factors is
2 × 3 × 7. We call 2 × 3 × 7 the prime factorization of 42.
1. Which is not a cold sandwich?
a. Pinwheel sandwich
b. Tea sandwich
c. Wrap sandwich
d. Grilled sandwich
Answers
Answer:
D. Grilled sandwich
Explanation:
Grilled sandwich is a kind of hot sandwich.




How did transistors revolutionize the world of computers?
Answers
Answer:
Transistors transformed the world of electronics and had a huge impact on computer design. Transistors made of semiconductors replaced tubes in the construction of computers. By replacing bulky and unreliable vacuum tubes with transistors, computers could now perform the same functions, using less power and space.
Once you turn 18, if you choose one of the 4 options for accessing credit, how will you be sure you use that credit responsibly?
The 4 options are below
GET A CO-SIGNER CHIP AWAY AT STUDENT LOANS
For those aged 18-21 years, Paying off the interest on an unsubsidized
a parent can act as a co-signer, student loan while you're in school can
so you can open a credit card also bump your score up.
account.
GET A SECURED CREDIT CARD TAG ONTO ANOTHER CREDIT CARD
Most providers can offer a secured Ask to be added as an authorized user
credit card if a cash deposit is put for you parent's credit card account.
up as collateral exchange.
Answers
Answer:
hm not sure man
Explanation:
sorry, give me crown and 5 stars tho
Answer: (A) Jason bought a used car and got a loan from his credit union.
(B) The Overtons bought a new home and mortgaged it for 30 years.
(D) Tammy borrowed $40,000 in school loans to be paid back in 5 years.
Explanation:
edge its right
in what network topology are devices daisy-chained together in a single line
Answers
In a network topology, devices daisy-chained together in a single line is a linear bus topology. A bus topology is a network configuration in which all devices are attached to a central cable called a bus or backbone.
What is network topology?
Network topology is a way to organize the devices that are connected to a network. Network topology can be categorized into six basic categories. These six categories are:
Mesh topology
Star topology
Bus topology
Ring topology
Hybrid topology
Tree topology.
What is daisy-chained network topology?
A daisy-chained network topology is a type of topology in which devices are connected together in series. Each device in the network connects to two other devices. The first device connects to the second, the second device connects to the third, and so on until the last device in the chain is reached. This type of topology is also referred to as a linear topology or a bus topology.
What is a single line network topology?
A single line network topology is a type of topology in which all devices are connected to a single cable. This cable is used to transmit data between the devices. All devices in a single line network topology are connected in series. This means that data must pass through each device before it reaches its final destination.
Learn more about network topology at https://brainly.com/question/17036446
#SPJ11