When is it more appropriate to use insertion sort than selection sort?
Answers
When, in the beginning, the array is already mostly sorted Any array can be used because inserting data into a list by insertion sort is always quicker than selecting it.
Why might insertion sort outperform selection sort in some circumstanceThe insertion sort outperforms the selection sort when only a small set of elements are involved or the list has already been partially sorted. Insertion sort is also quick, efficient, and stable.
When is it a good idea to sort an array using the insertion method?When the input list is already mostly sorted, inserting sort is an excellent choice because it has a quick best-case execution time. with regard to longer or more unordered lists.
To know more about insertion sort visit :-
https://brainly.com/question/13326461
#SPJ4
Related Questions
9. What signs of global warming might a person in the Midwest be most concerned about?
Answers
This region will most likely have warmer and wetter winters, wetter springs, and warmer temperatures with longer dry periods.
What is global warming?Global warming is the long-term heating of the Earth's surface observed since the pre-industrial period as a result of human activities, primarily the combustion of fossil fuels.
This increases heat-trapping greenhouse gas levels in the Earth's atmosphere.
Droughts, which are prolonged periods of extremely dry weather, may be of particular concern to residents of the Midwest.
Droughts in the Midwest are expected, which could kill crops and cause wildfires, according to experts.
Temperature rise in the Midwest has accelerated in recent decades, particularly at night and during the winter.
Warmer and wetter winters, wetter springs, and warmer temperatures with longer dry periods are all likely in this region.
Thus, these are some signs of global warming might a person in the Midwest be most concerned about.
For more details regarding global warming, visit:
https://brainly.com/question/12908180
#SPJ1
is a popular blogging tool that allows users to post anything from their browsers, phones, desktops, e-mail programs, and so forth. a. chrome b. mozilla firefox c. wikipedia d. tumblr
Answers
Tumblr is a popular blogging tool that allows users to post anything from their browsers, phones, desktops, e-mail programs, and so forth. Option d is correct.
Tumblr is a free microblogging and social networking site that allows users to post text, pictures, GIFs, videos, live videos, and audio. You can reblog other people's posts and add comments or likes to them. Users can also customize their blog's theme and appearance.
Blogging tools are software or web-based tools that assist bloggers in creating, editing, and publishing blog content. They help bloggers optimize their content, create a blog calendar, design custom graphics, and track their blog's traffic.
Blogging tools have various functionalities that include social sharing, content marketing, email marketing, and analytics. Blogging tools help bloggers save time and stay organized by streamlining their blogging process. Some popular blogging tools include HubSpot, WordPress, and Squarespace.
Learn more about blogging tool https://brainly.com/question/5006962
#SPJ11
which is true regarding how methods work? group of answer choices after a method returns, its local variables keep their values, which serve as their initial values the next time the method is called a method's local variables are discarded upon a method's return; each new call creates new local variables in memory a return address indicates the value returned by the method
Answers
The correct statement for working of method is-
A method's local variables are discarded upon a method's return; Each new call creates new local variables in memory.What is the working of the method?Work methods are indeed the physical actions used to complete a task.
An effective ergonomics program includes several components, one of which is evaluating as well as modifying work methods to avoid discomfort and injury. Ergonomics programs include work method analysis to make sure that safe practices are used for job tasks. Training and work practitioner controls then are implemented to make sure that appropriate methods for reducing employee exposure to intuitive risks are used.Thus, for the given question;
A local variable is a variable that can only be accessed within a specific section of a program.These variables are typically defined in that routine and are considered to be local to that subroutine.Thus, we can conclude that each new call to a method's local variables can result in the creation of new local variables throughout memory.
To know more about the local variables, here
https://brainly.com/question/28274892
#SPJ4
Kernel calls are _____ to manage threads.
a)needed only with KLTs
b)needed only with ULTs
c)always needed
d)never needed
Answers
Kernel calls are always needed to manage threads. A thread is an independent sequence of execution within a process, and it requires the support of the operating system kernel to manage its execution.
The kernel is the central component of an operating system that manages system resources, including CPU, memory, and I/O devices. Kernel calls are system calls made to the operating system kernel by a user-level thread or a kernel-level thread to request a specific service or operation. In a kernel-level thread (KLT) model, each thread is managed entirely by the kernel, and kernel calls are required to create, manage, and synchronize threads. On the other hand, in a user-level thread (ULT) model, threads are managed entirely by the user-level thread library, and kernel calls are only needed for I/O operations or other system calls that require kernel privileges. In general, kernel calls are essential for managing threads in any operating system model, as they provide the necessary synchronization, communication, and resource management mechanisms needed to ensure that threads can execute efficiently and without conflicts. Therefore, the correct answer to the question is c) always needed.
Learn more about operating system here-
https://brainly.com/question/31551584
#SPJ11
who knows how to cope and paste on (ape.x)
Answers
To copy and paste on Apex, you can use the keyboard shortcuts "Ctrl+C" and "Ctrl+V" or right-click the selected text and choose "Copy" and "Paste."
Without more information about the context and platform you are referring to, it is difficult to provide a helpful response. However, if you are asking how to copy and paste on a computer or mobile device, the process typically involves selecting the text or item you want to copy, pressing "Ctrl + C" on a PC or "Command + C" on a Mac, and then pasting it by pressing "Ctrl + V" or "Command + V". The specific steps may vary depending on the software or device you are using, so it is recommended to consult the instructions or help resources for that specific platform.
Copying and pasting are essential computer skills that allow you to duplicate text or other content from one place and insert it into another. In Apex, you can use these methods to copy and paste information, making it easier to complete tasks efficiently.
To know more about keyboard visit:
https://brainly.com/question/24921064
#SPJ11
What are the two tcp/ip protocols that are used by mail servers for clients accessing incoming mail?
Answers
The two TCP/IP protocols that are used by mail servers for clients accessing incoming mail are POP3 and IMAP4.
These protocols allow the client to access their email by establishing a connection to the mail server.
POP3 (Post Office Protocol version 3) is an email protocol that downloads emails from an email server to a local email client. When you download your email using POP3, your email is deleted from the email server and stored locally on your device.
IMAP (Internet Message Access Protocol) is an email protocol that allows email messages to be accessed from an email server through a mail client. IMAP enables you to read your email and synchronize your email messages across different devices. The advantage of using IMAP is that your email messages are stored on the email server, so you can access them from any device.
Learn more about Protocols: https://brainly.com/question/30547558
#SPJ11
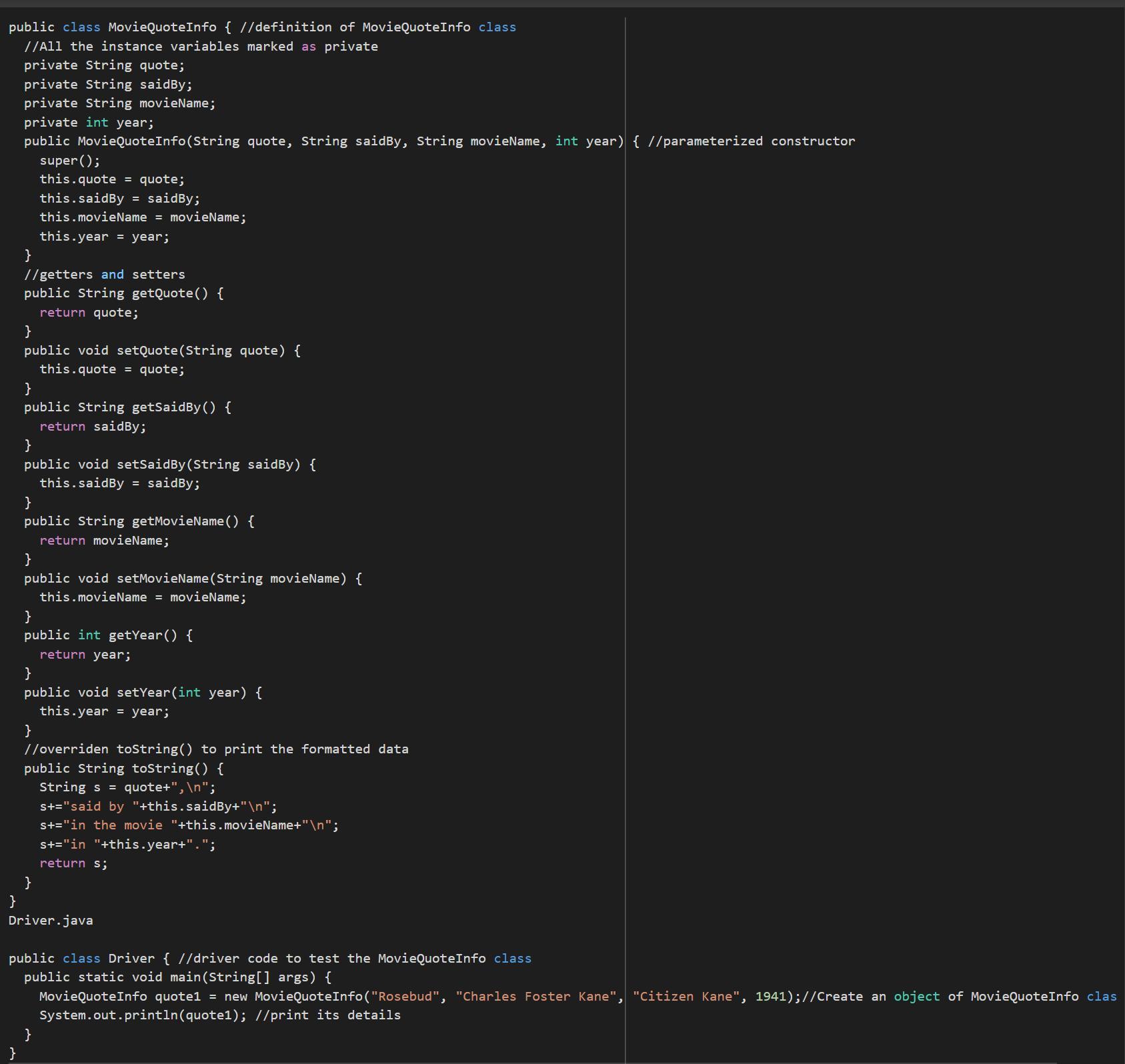
Write, compile, and test the MovieQuoteInfo class so that it displays your favorite movie quote, the movie it comes from, the character who said it, and the year of the movie: I GOT IT DONT WATCH AD.
class MovieQuoteInfo {
public static void main(String[] args) {
System.out.println("Rosebud,");
System.out.println("said by Charles Foster Kane");
System.out.println("in the movie Citizen Kane");
System.out.println("in 1941.");
}
}
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that removes your favorite phrase from the movie. It consists of two classes in which one is driver code to test the MovieQuoteInfo class.
Writing code in JAVA:
public class MovieQuoteInfo { //definition of MovieQuoteInfo class
//All the instance variables marked as private
private String quote;
private String saidBy;
private String movieName;
private int year;
public MovieQuoteInfo(String quote, String saidBy, String movieName, int year) { //parameterized constructor
super();
this.quote = quote;
this.saidBy = saidBy;
this.movieName = movieName;
this.year = year;
}
//getters and setters
public String getQuote() {
return quote;
}
public void setQuote(String quote) {
this.quote = quote;
}
public String getSaidBy() {
return saidBy;
}
public void setSaidBy(String saidBy) {
this.saidBy = saidBy;
}
public String getMovieName() {
return movieName;
}
public void setMovieName(String movieName) {
this.movieName = movieName;
}
public int getYear() {
return year;
}
public void setYear(int year) {
this.year = year;
}
//overriden toString() to print the formatted data
public String toString() {
String s = quote+",\n";
s+="said by "+this.saidBy+"\n";
s+="in the movie "+this.movieName+"\n";
s+="in "+this.year+".";
return s;
}
}
Driver.java
public class Driver { //driver code to test the MovieQuoteInfo class
public static void main(String[] args) {
MovieQuoteInfo quote1 = new MovieQuoteInfo("Rosebud", "Charles Foster Kane", "Citizen Kane", 1941);//Create an object of MovieQuoteInfo class
System.out.println(quote1); //print its details
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1
which of the following statements about user personas is true? 1 point ux designers should avoid creating backstories for personas personas can help identify patterns of behavior in users. personas are modeled after the characteristics of the ux designer. a persona is a real user who provides real reviews on a product.
Answers
The statement "personas can help identify patterns of behavior in users" is true.
What is User personas?User personas are fictional characters created by UX designers to represent different types of users and their behaviors, goals, motivations, and pain points.
By creating user personas, UX designers can better understand their users' needs and design products that meet those needs. Personas are not modeled after the characteristics of the UX designer, and they do not have to be based on real users.
However, user research and feedback can be used to create more accurate and effective personas.
Read more about UX design here:
https://brainly.com/question/30736244
#SPJ1
Opportunity and Spirit, NASA's Mars Exploration Rovers, were the first scientific instruments able to collect samples directly from the surface of Mars. One of the mission's goals was to determine the likelihood that life ever existed on Mars. How were Spirit and Opportunity best able to supply evidence that in the distant past Mars may have had an environment favorable to life?
Answers
Answer:
The rovers sent images of cross beds, centimeter-scale areas in rock layers, that could indicate whether water once flowed on Mars.
Explanation:
What parts construct a Mechanical keyboard and how does it work?
Answers
Answer:
A mechanical keyboard consists of a case, plate, switches, stabilizers, keycaps, and the pcb. The switches are soldered into the pcb, and are help in place by the plate, the plate is held in by the case. People tend to want to make their keyboards sound and feel better. What they do to achieve this is they lube the switches and stabilizers. The most common keyboard switch and stab lubes are krytox 205g0 and tribosis 103. There are different types of switches there are linear switches, tactile switches, and clicky switches. Linear switches go straight down with no feedback, they just bottom out when you type with them. Tactile switches have a little bump around the halfway point of bottom out which gives you feedback that you have pressed that switch. Clicky switches are the same as tactile switches with the bump but have an added “click bar” this generates a small noise when the switches are actuated. Linear switches and tactile switches are mostly used for typing and can be used for gaming, clicky switches are not usually used for typing and are more used for gaming. and how the switches work is when you press down on them, small metal contacts inside make a circuit when the circuit is made it sends information from the switch to the pbc to the computer.
what is the molecular activity of mattern
Answers
Matter is made up of extremely tiny particles called atoms and molecules. Atoms and molecules make up the three common states of matter on Earth—solids, liquids, and gases. The particles of a liquid are attracted to one another, are in motion, and are able to move past one another.
- BRAINLIEST answerer
Which of the below would provide information using data-collection technology?
Buying a new shirt on an e-commerce site
Visiting a local art museum
Attending your friend's baseball game
Taking photos for the school's yearbook
Answers
The statement that would provide the information through the utilization of data-collection technology is as follows:
Buying a new shirt on an e-commerce site.Thus, the correct option for this question is A.
What is meant by Data-collection technology?Data-collection technology may be defined as a type of technology that significantly deals with the process of collecting data for use in business decision-making, strategic planning, research, and other purposes.
According to the context of this question, visiting a local art museum represents the collection of information in real form, while buying a new shirt on an e-commerce site is the collection of data and information in virtual form.
Other options like attending your friend's baseball game and taking photos for the school's yearbook do not involve any sort of technology based on data collection.
Therefore, the correct option for this question is A.
To learn more about Data collection technology, refer to the link:
https://brainly.com/question/25633523
#SPJ1
what is the name for a domain controller on which changes can't be written?
Answers
The name for a domain controller on which changes can't be written is called a Read-Only Domain Controller (RODC).
This type of domain controller is designed to provide security and protection for your network, as it allows users to authenticate and access resources without the ability to make changes to the domain controller's data.
An RODC is a new type of domain controller that hosts read-only partitions of the Active Directory database. Except for account passwords, an RODC holds all the Active Directory objects and attributes that a writable domain controller holds.
Learn more about RODC: https://brainly.com/question/29585813
#SPJ11
What is the best CPU you can put inside a Dell Precision T3500?
And what would be the best graphics card you could put with this CPU?
Answers
Answer:
Whatever fits
Explanation:
If an intel i9 or a Ryzen 9 fits, use that. 3090's are very big, so try adding a 3060-3080.
Hope this helps!
PYTHON CODING LANGUAGE (i am a beginner)
Please write a few lines of code.
Here is a scenario:
In order to find the pay, you need to multiply the rate and hours.
*USE VARIABLES
Answers
Hours = int(input(“enter how many hours were worked”))
Pay_rate = float(input(“Enter the pay rate”))
Pay_amount = Pay_rate * Hours
#calculate the wages
Print (Pay_amount)
#print the final answer
Predict the photography quality if you purchased a 16-megapixel camera with a larger sensor over a 30-megapixel camera with a smaller sensor. Explain your reasoning.
Answers
The photography quality if a person purchased a 16-megapixel camera with a larger sensor is better than a 30-megapixel camera with a smaller sensor because a better sensor tends to detect image that are far and capture them with good quality.
Is 16 megapixels good for photography?Yes. When a person is taking pictures for themselves and their family, a 10-16 MP camera is said to be one that is known to be sufficient to take in a lot of your needs.
Note that Megapixel resolution is one that has an important role in how big you can be able to get or print your pictures.
Hence, The photography quality if a person purchased a 16-megapixel camera with a larger sensor is better than a 30-megapixel camera with a smaller sensor because a better sensor tends to detect image that are far and capture them with good quality.
Learn more about megapixel from
https://brainly.com/question/26515862
#SPJ1
What symbols are used to form a block comment within a SQL program?
Answers
In SQL, block comments are enclosed between the symbols /* and */. Anything written between these two symbols will be considered as a comment and will not be executed by the SQL program.
In SQL, block comments are enclosed between the symbols /* and */, which is a useful feature for developers to add comments within their code for better understanding and maintenance of the program.
For example:
/* This is a block comment
that can span multiple lines
within a SQL program */
Note that some DBMS may not support block comments or may use a different syntax to implement them. It's important to refer to the specific documentation of the DBMS being used for more information.
To learn more about SQL visit : https://brainly.com/question/23475248
#SPJ11
essay on the importance of computer and internet 250 word
Answers
With the significant progress in technology, the importance of the internet has only multiplied with time. The dependence on the internet has been because of multiple advantages that it has to offer – for instance reducing the work stress and changing the face of communication most importantly. By employing the correct usage of the internet, we can find various information about the world. The internet hosts Wikipedia, which is considered to be one of the largest best-composed reference books kept up by a vast community of volunteer scholars and editors from all over the world. Through the internet, one may get answers to all their curiosity. In the education sector too, it plays a major role, especially taking into consideration the pandemic. The Internet during the pandemic provided an easy alternative to replace the traditional education system and offers additional resources for studying, students can take their classes in the comforts of their homes. Through the internet, they can also browse for classes – lectures at no extra cost. The presence of the internet is slowly replacing the use of traditional newspapers. It offers various recreational advantages as well. It can be correctly said that the internet plays a great role in the enhancement of quality of life.
Answer:
Computers and the internet are highly prevalent and crucial in our everyday lives since they are the method by which the current enormous world is linked and becomes one. Computers have altered human life by making things faster and more efficient. Individuals may generate, store, and retain data. Computers and the internet are used by businesses in a variety of areas, including banking, retail, education, and so on. Because of the rising technical capabilities of Internet connectivity, the processing and utilization of information and knowledge is becoming extremely important for society. Since the dawn of the modern era, the Internet has been an outstanding tool for global informatization. It is a fair and accessible source of varied information as well as a mechanism of knowledge dissemination. Computers are incredibly significant today since they are very precise, speedy, and can effortlessly do numerous jobs. Manually doing those activities would take significantly more time. It can perform extremely complex computations in a fraction of a second. Furthermore, it can hold a large quantity of data. One may obtain a variety of knowledge about the globe by using the internet correctly. The internet can provide answers to all of one's questions. It also plays an important part in the education sector since it is an easy alternative to the traditional education system and provides additional learning materials; students may attend their lectures from the comfort of their own homes. They may also search for lessons and lectures on the internet for free.
what is the concept used to verify the identity of the remote host with ssh connections?
Answers
The concept used to verify the identity of the remote host with SSH connections is known as host key verification. SSH (Secure Shell) is a cryptographic protocol that enables secure communication between two computers over an unsecured network.
It employs public-key cryptography to authenticate the remote computer and encrypt the data transmitted between them. When an SSH client connects to an SSH server, the two computers must establish a trust relationship to ensure that they are communicating with the intended partner. The SSH protocol utilizes a public-key cryptography-based system for verifying the identity of the remote host.
The SSH server generates a host key (public/private key pair) when it is first installed, and this key is used to authenticate the server to the client. The host key is used by the client to verify that the server it is connecting to is the intended server.
To know more about identity visit:
https://brainly.com/question/11539896
#SPJ11
2. In the RACI model, which role offers insights or expertise to help others complete project tasks?
Answers
In the RACI model, the role which offers insights or expertise to help others complete project tasks is consulted.
What is a RACI model?
RACI model is also referred to as a RACI chart or RACI matrix and it can be defined as a diagram that is used as a graphical (visual) representation to indicate and identify the fundamental roles and responsibilities of users with respect to major tasks within a project.
In project management, RACI is an acronym for the following:
ResponsibleAccountableConsultedInformedIn the RACI model, the role which offers insights or expertise to help others complete project tasks is consulted because he or she is a subject matter or project topic expert.
Read more on RACI model here: https://brainly.com/question/6177865
A(n) ________ file is usually smaller than the original document, and is easy to send through e-mail.
Answers
A compressed file is usually smaller than the original document, and is easy to send through email.
A compressed file is a file that has been reduced in size using compression algorithms. These algorithms remove redundant or unnecessary data from the file, resulting in a smaller file size. Compressed files are commonly used to make large files more manageable for storage and transmission purposes.
When you compress a file, it is transformed into a compressed format such as ZIP or RAR. These formats use various techniques to reduce the file size, including removing repetitive data and optimizing the storage of information. As a result, a compressed file can be significantly smaller than the original document.
One major advantage of using compressed files is that they are easier to send through email. Email systems often have limitations on the size of attachments that can be sent. By compressing a file, you can reduce its size and stay within these limits. Additionally, compressed files can be easily extracted by the recipient using a compatible decompression tool.
In summary, a compressed file is a smaller version of the original document created through compression algorithms. It is advantageous for email transmission due to its reduced size.
Learn more about compressed file: https://brainly.com/question/30055235
#SPJ11
Which office setup would be difficult to host on a LAN?
hardware.
RAM.
storage.
software.
Answers
The office setup would be difficult to host on a LAN is option C: storage.
What is the office LAN setup like?A local area network (LAN) is a network made up of a number of computers that are connected in a certain area. TCP/IP ethernet or Wi-Fi is used in a LAN to link the computers to one another. A LAN is typically only used by one particular establishment, like a school, office, group, or church.
Therefore, LANs are frequently used in offices to give internal staff members shared access to servers or printers that are linked to the network.
Learn more about LAN from
https://brainly.com/question/8118353
#SPJ1
Which parameter can be used with the ping command to send a constant stream of packets when using a Windows device?A. -fB. -pC. /allD. -gE. -t
Answers
use the "-t" parameter with the ping command on a Windows device.
What is ping command?
On a Windows device, the "ping" command can be used to test network connectivity by sending ICMP packets to a destination host. To send a constant stream of packets using the ping command, you can use the "-t" parameter.
The "-t" parameter in the ping command tells it to send packets continuously until interrupted by the user, as opposed to the default behavior of sending four packets and then stopping.
Here's an example of how to use the "-t" parameter with the ping command on a Windows device:
ping -t <destination IP address or hostname>
This command will continuously send ICMP packets to the specified destination until the user interrupts it by pressing Ctrl+C.
To know more about ping command, visit: https://brainly.com/question/24181922
#SPJ4
8. Given the array String[] words, which already contains 1 or more values, write a block of code which counts and returns the number of words which start with the letter k
Answers
Answer:
Following are the code to this question:
public class Main//defining a class
{
public static void main(String[] arg)//defining main method
{
String[] words={"Key","day", "Know", "kind"};//defining array of String words
int x=0;//defining integer variable for count value
for(int i=0;i<words.length;i++)//defining for loop for count value
{
if(words[i].startsWith("k")||words[i].startsWith("K"))//use if block to check word start from k
x=x+1;//increment the value of x
}
System.out.print("The number of letters which starts from k is: "+ x);//print value with message
}
}
Output:
The number of letters which starts from k is: 3
Explanation:
In this code, inside the main method an array of String "words" is defined that hold a value, and in the next step an integer variable "x" is defined, which is used to count the letters, which starts from k.
For this, a for loop is used that counts the value and in this an, if block is defined that uses the "startsWith" method to check the value and increment the value of x and at the last, it prints its value.
What practice protects your privacy in relation to your digital footprint?
Answers
Reviewing your privacy settings is one of the actions that can assist safeguard your privacy in relation to your digital footprint.
Why should you guard your online presence?However, leaving a digital imprint can also have a number of drawbacks, including unwelcome solicitations, a loss of privacy, and identity theft. Cybercriminals may utilise your digital footprint to launch more precise and successful social engineering attacks against you, such as phishing scams.
Which eight types of privacy exist?With the help of this analysis, we are able to organize different types of privacy into a two-dimensional model that includes the eight fundamental types of privacy (physical, intellectual, spatial, decisional, communicative, associational, proprietary, and behavioural privacy) as well as an additional, overlapping ninth type (informational privacy).
To know more about digital footprint visit:-
https://brainly.com/question/17248896
#SPJ4
The keyDown (code) block is used to write programs where a user can control sprites on
the screen.
O True
O False
Answers
Write an LMC program as follows instructions:
A) User to input a number (n)
B) Already store a number 113
C) Output number 113 in n times such as n=2, show 113
113.
D) add a comment with a details exp
Answers
The LMC program takes an input number (n) from the user, stores the number 113 in memory, and then outputs the number 113 n times.
The LMC program can be written as follows:
sql
Copy code
INP
STA 113
INP
LDA 113
OUT
SUB ONE
BRP LOOP
HLT
ONE DAT 1
Explanation:
A) The "INP" instruction is used to take input from the user and store it in the accumulator.
B) The "STA" instruction is used to store the number 113 in memory location 113.
C) The "INP" instruction is used to take input from the user again.
D) The "LDA" instruction loads the value from memory location 113 into the accumulator.
E) The "OUT" instruction outputs the value in the accumulator.
F) The "SUB" instruction subtracts 1 from the value in the accumulator.
G) The "BRP" instruction branches back to the "LOOP" label if the result of the subtraction is positive or zero.
H) The "HLT" instruction halts the program.
I) The "ONE" instruction defines a data value of 1.
The LMC program takes an input number (n) from the user, stores the number 113 in memory, and then outputs the number 113 n times.
To know more about LMC program visit :
https://brainly.com/question/14532071
#SPJ11
State one technique for overcoming external fragmentation in dynamic partitioning. Why is this technique of overcoming external fragmentation considered inefficient
Answers
Compaction often gives solutions to the issues regarding external fragmentation.
One technique for overcoming external fragmentation in dynamic partitioning is
Compaction.
The reason why this technique of overcoming external fragmentation may be inefficient is because:
External fragmentation may need a lot of compaction and it is an expensive operation. The use of contiguous allocation is often hard to fit processes into memory and also it is so difficult to grow or shrink the amount of memory allocated to a process. Compaction only takes place when relocation is dynamic, and this also is expensive.Compaction often shuffle memory notes or contents and then put or pile them up all in free memory and in one large block.
External fragmentation takes place when free memory is removed into small blocks.
Learn more from
https://brainly.com/question/23636593
An android user recently cracked their screen and had it replaced. If they are in a dark room, the phone works fine. If the user enters a room with normal lights on, then the phone's display is dim and hard to read. What is most likely the problem?
Answers
There are two possibilities for the problem in the given scenario. The first and most probable cause of the problem is that the replaced screen was of low quality or did not meet the device's standards.
Therefore, the screen is not transmitting light properly and is producing dim or blurry images.The second possibility for the problem is that the light sensor of the phone might be affected by the screen replacement. The phone might be adjusting the brightness levels based on the low light environment in the dark room and not adjusting correctly in the normal light environment.
This can result in the phone being too bright or too dim, making it difficult to read the display.However, both of these possibilities can be avoided by purchasing a high-quality replacement screen or seeking professional assistance to fix the problem. In such cases, it is recommended to have an expert inspect the device for any faults and repair it accordingly.Moreover, one can also try to adjust the screen brightness levels manually to make the display more readable in the normal light environment.
To know more about visit:
https://brainly.com/question/32730510
#SPJ11
2. Take notes on all the main ideas from the Recycling Basics page and the Recycle
at Work page, highlighting the ideas you could use to support the implementation of
a workplace recycling program.
a. Be sure to write down any source information that you will need to incorporate
into a works-cited page in MLA format.
Answers
Recycling Basics:
1. Recycling is the process of converting waste materials into reusable materials to conserve resources and reduce waste.
2. The three main steps in recycling are collection, processing, and manufacturing.
3. Recycling can help conserve natural resources, save energy, reduce pollution, and reduce landfill space.
4. Commonly recycled materials include paper, cardboard, glass, metal, and plastic.
5. It is important to sort and separate recyclable materials properly to ensure effective recycling.
6. Recycling programs can be implemented at the household level, community level, and workplace level.
7. Many communities have curbside recycling programs, while others may require residents to drop off recyclables at designated recycling centers.
8. Recycling programs often have guidelines on what materials are accepted and how they should be prepared for recycling.
9. Education and awareness campaigns are crucial for promoting recycling and encouraging participation.
10. Recycling can have economic benefits by creating jobs in the recycling industry and reducing waste management costs.
Recycle at Work:
1. Implementing a workplace recycling program can help reduce waste and contribute to sustainability goals.
2. Start by assessing the current waste generation and identifying opportunities for recycling.
3. Set clear recycling goals and targets for the workplace.
4. Provide easily accessible recycling bins throughout the workplace and ensure they are clearly labeled.
5. Train employees on proper recycling practices and provide ongoing education and reminders.
6. Involve employees in the development and implementation of the recycling program to increase engagement and participation.
7. Monitor and track recycling progress to measure the effectiveness of the program.
8. Consider partnering with recycling service providers or local recycling organizations for support and guidance.
9. Promote and celebrate recycling achievements within the workplace to motivate and engage employees.
10. Regularly review and update the recycling program to adapt to changing needs and ensure continuous improvement.
Source Information:
- Recycling Basics: Environmental Protection Agency (EPA). Retrieved from [insert URL here].
- Recycle at Work: Environmental Protection Agency (EPA). Retrieved from [insert URL here].
for more questions on Recycling
https://brainly.com/question/2055088
#SPJ8