What was the computer invented by Attanasoff and Clifford?
Answers
The Atanasoff Berry Computer was the brainchild of Clifford Berry and John Vincent Atanasoff (ABC). It was an electronic digital computer that carried out calculations using binary numbers (bits).
What is the name of the computer invented by Dr. Atanasoff?Atanasoff was declared to be the computer's inventor in the Sperry Rand litigation. His specialised device became known as the Atanasoff-Berry Computer.
What was the purpose of the Atanasoff Berry computer?The ABC was created specifically to address systems of concurrent linear equations. It was capable of handling systems with up to 29 equations, which was a challenging issue at the time. These kinds of issues were starting to crop up often in the physics department, where John Atanasoff worked.
To know more about Computer visit:-
https://brainly.com/question/30917291
#SPJ9
Related Questions
Please answer.
For this Code Practice, use the following initializer list, terms:
terms = ["Bandwidth", "Hierarchy", "IPv6", "Software", "Firewall", "Cybersecurity", "Lists", "Program", "Logic", "Reliability"]
Write a sort program to alphabetize the list of computer terms, much like the preceding question. However, this time, define and use a function named swap as part of your solution. The swap function should not be a sort function, but should instead implement the swap functionality used in sorting. This function should swap the elements in the array at each of the indexes by comparing two elements to one another, and swapping them if they need to be in a different alphabetical order.
Your function should take three parameters: the first is the array name, and the second and third are the indexes to swap. Print the terms array before and after it is sorted.
Expected Output
['Bandwidth', 'Hierarchy', 'IPv6', 'Software', 'Firewall', 'Cybersecurity', 'Lists', 'Program', 'Logic', 'Reliability']
['Bandwidth', 'Cybersecurity', 'Firewall', 'Hierarchy', 'IPv6', 'Lists', 'Logic', 'Program', 'Reliability', 'Software']
Answers
Answer:
def swap (ar, a, b):
temp = ar[a]
ar[a] = ar[b]
ar[b] = temp
terms = ["Bandwidth", "Hierarchy", "IPv6", "Software", "Firewall", "Cybersecurity", "Lists", "Program", "Logic", "Reliability"]
print(terms)
for i in range(len(terms)):
for j in (range(i, len(terms))):
if(terms[i] > terms[j]):
swap(terms, j, i)
print(terms)
Explanation:
I got 100% on edhesive.
The code practice requires the uses of loops and conditional statements.
Loops are used for repetition of operations, while conditional statements are used for making decisions.
The sort program in Python, where comments are used to explain each line is as follows:
#This defines the swap function
def swap (terms, a, b):
#This creates a temporary variable
temp = terms[a]
#The next two lines swap the elements
terms[a] = terms[b]
terms[b] = temp
#This initializes the list
terms = ["Bandwidth", "Hierarchy", "IPv6", "Software", "Firewall", "Cybersecurity", "Lists", "Program", "Logic", "Reliability"]
#This prints the list before sorting
print(terms)
#This calculates the length of the list
n = len(terms)
#This iterates through the list
for i in range(n):
#This iterates through every other element of the list
for j in (range(i, n)):
#This swaps the elements
if(terms[i] > terms[j]):
swap(terms, j, i)
#This prints the list after sorting
print(terms)
Read more about sort programs at:
https://brainly.com/question/15263760
What is the name of the provision of services based around hardware virtualization?
Answers
Explanation:
Hardware virtualization refers to the creation of virtual (as opposed to concrete) versions of computers and operating systems. ... Hardware virtualization has many advantages because controlling virtual machines is much easier than controlling a physical server.
The name of the provision of services based around hardware visualization is called cloud computing
The cloud hypervisor is the software that is made use of during hardware visualization. The hypervisor does the function of managing hardware resources involving the customer and the service provider.
The work of hypervisor is that it manages the physical hardware resource which is shared between the customer and the provider.
Read more on https://brainly.com/question/13088836?referrer=searchResults
Which concept is central both to the Declaration of Independence and to Social Contract Theory?
Answers
Rousseau wrote about "the laws being solely the authentic acts of the general will" in 1762. In 1776, Thomas Jefferson wrote that the authority of the government should be derived from the consent of the governed in the Declaration of Independence. Both men argue that sovereignty (the power to make the laws) should be in the hands of the people.
Order the steps to successfully create a data table.
Answer: Write the formula used to create table values
Select the range
Select the Data tab and What-If Analysis
Select Data Table
Select the values for row/column input.
Answers
Here are the steps to successfully create a data table:
Select the range.Select the Data tab and What-If Analysis.Select Data Table.Write the formula used to create table values.Select the values for row/column input.How to create the data tableFor achieving the desired outcome of generating a data table, it is suggested to adhere to the following measures:
Choose the cells group in which you intend to generate the data table. Include both the cells for input and presentation of results in the specified range.
Provide the equation that you intend to apply for computing the figures enlisted in the data chart. This equation must refer to the designated cells and yield the intended outcome.
Access the What-If Analysis feature by navigating to the Data tab within your spreadsheet program. To access the menu, simply click on it.
Choose the Data Table option from the What-If Analysis menu. This action will trigger the appearance of a dialog box or prompt that will require you to input the required details.
Determine the desired input values for either the row or the column in the data table dialogue box. The table's outcomes will be computed based on these values.
By adhering to these guidelines, you can produce a chart of data that exhibits computed figures derived from various input situations, aiding you in scrutinizing and comprehending the ramifications of different factors on your data.
Read more about data tables here:
https://brainly.com/question/32534586
#SPJ1
Direction: Read each item carefully and choose the letter of the correct answer. Write your answers on a separate sheet of paper or in your notebook. 1. What program is used to create spreadsheets which can later be used to analyze statistical tool? A. MS Excel B. MS Word C. MS Publisher D. MS OneNote 2. What MS Excel function adds a range of cells? A. ADD B. PLUS C. SUM D. TOTAL 3. Which of the following objects can be inserted in your document? 3
Answers
Answer: good
Explanation: good
PLS HELP!! TAKINT TEST
A _____ is a network geographically confined to one building.
A) VPN
B) MAN
C) LAN
D) WAN
Answers
What is the best way to delete a program that you downloaded that says that its open but its not opened in your screen? I will give Brainliest to whoever gets it right. Or whoever gets 10 votes and 5 thanks.
Answers
Answer:
Ctrl+Alt+Del and open Task Manager. Right-click and select End Process. Proceed with uninstalling the program as normal, now that the program has been closed.
Explanation:
please help me plss! PLS
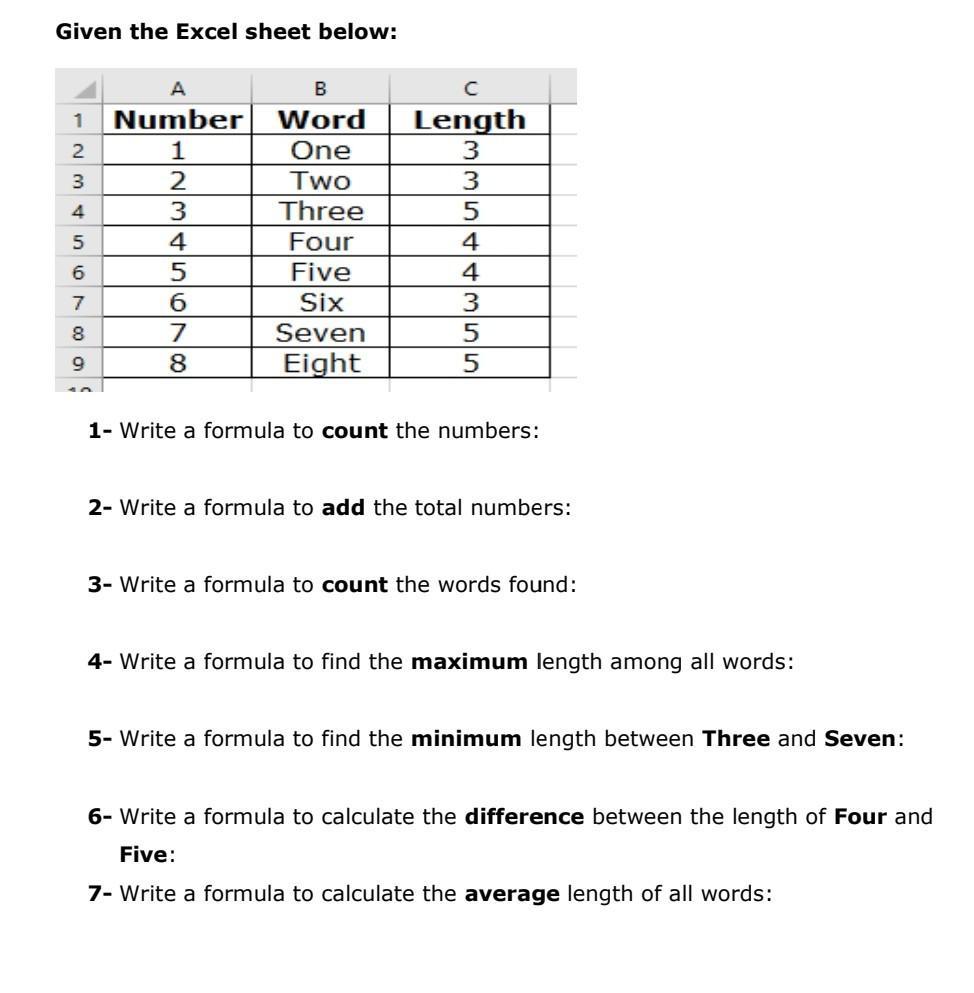
Answers
Explanation:
OKAY, you got your asnswer.. sorry I could not help.
A customer uses an app to order pizza for delivery. Which component includes
aspects of the customer's interaction with an enterprise platform?
Answers
~frestoripongetosarangeou
A consumer orders pizza for delivery via an app. The element of the data component covers how a customer interacts with an enterprise platform
What is the data component?A data component is a tool that provides information on the activities taking place on a certain enterprise platform. This application also aids in keeping track of the available inventory.
In this approach, customers place their orders through a smartphone app.
Therefore, while ordering pizza the consumer uses the data component.
To know more about the Data component, visit the link below:
https://brainly.com/question/27976243
#SPJ2
11. Stationary Expenditure
A stationery store sells pencils at $1.20 each, erasers at $2 each, and compasses at $5 each. Write a program that asks the user for the number of each of these items purchased, calculates the total expenditure made by the user, and then displays the result on the screen.
Answers
Answer:
What type of program python?
9. Describe each line of code in the pseudocode version of the generalized getInteger(…) function.
Answers
Note that the following is an example pseudocode version of a generalized getInteger() function:
function getInteger(prompt):
loop:
display prompt
input_string = get_input()
if is_valid_integer(input_string):
return convert_to_integer(input_string)
else:
display error_message
continue
What is the explanation for the above response?Here's a description of each line of code in this pseudocode:
function getInteger(prompt):: This line declares the start of the getInteger() function, which takes a prompt string as a parameter.
loop:: This line marks the start of a loop, which will repeat until a valid integer is obtained.
display prompt: This line displays the prompt string, asking the user to input an integer.
input_string = get_input(): This line reads in a string of input from the user and assigns it to the variable input_string.
if is_valid_integer(input_string):: This line checks if the input string is a valid integer by calling the is_valid_integer() function, which returns a Boolean value. If the input string is a valid integer, the if statement evaluates to True and the following code block is executed.
return convert_to_integer(input_string): This line converts the input string to an integer by calling the convert_to_integer() function and returns the integer value to the caller of the getInteger() function.
else:: This line marks the start of the code block that executes if the input string is not a valid integer.
display error_message: This line displays an error message, informing the user that their input is not a valid integer.
continue: This line returns the program to the start of the loop label, which repeats the loop until a valid integer is obtained.
Learn more about pseudocode at:
https://brainly.com/question/13208346
#SPJ1
I really need help with coderZ does anyone kno?
Answers
Answer:
Easy-to-use virtual robotics and STEM platform tailored to serve every student at every level!
CoderZ is a powerful, award-winning online platform.
Explanation:
CoderZ is a powerful, award-winning online platform through which students learn valuable STEM skills such as coding, robotics, and physical computing. CoderZ is highly flexible and designed for use in the classroom or through a wide range of remote learning environments. Computers and technology are everywhere. Studying science, technology, engineering and math gives kids valuable skills for the future and develop life-skills like computational thinking, critical thinking and problem-solving as well.
STEM and CS education focuses on how to approach complex problems, break down the challenges into small pieces and approach resolving them in a logical manner – critical skills for any career path.
program a macro on excel with the values: c=0 is equivalent to A=0 but if b is different from C , A takes these values
Answers
The followng program is capable or configuring a macro in excel
Sub MacroExample()
Dim A As Integer
Dim B As Integer
Dim C As Integer
' Set initial values
C = 0
A = 0
' Check if B is different from C
If B <> C Then
' Assign values to A
A = B
End If
' Display the values of A and C in the immediate window
Debug.Print "A = " & A
Debug.Print "C = " & C
End Sub
How does this work ?In this macro, we declare three integer variables: A, B, and C. We set the initial value of C to 0 and A to 0.Then, we check if B is different from C using the <> operator.
If B is indeed different from C, we assign the value of B to A. Finally, the values of A and C are displayed in the immediate window using the Debug.Print statements.
Learn more about Excel:
https://brainly.com/question/24749457
#SPJ1
Data and text mining is a promising application of AaaS. What additional capabilities can AaaS bring to the analytic world
Answers
Answer:
It can bring useful capabilities such as
1. large-scale optimization
2. solution to very complex multi-criteria decision problems,
3. Distributed simulation models
Explanation:
The AaaS is the Analytics as a service (AaaS) it is the provision of analytics applications or programs and operations via the usage of web-delivered technologies. Aaas gives organizations an alternative to performing business analytics.
Apart from data and text mining, it also has the following capabilities
1. large-scale optimization
2. solution to very complex multi-criteria decision problems,
3. distributed simulation models.
The above prescriptive analytics would need highly capable systems which can only be realized when we use collaborative systems that are service based that can make use of large-scale computational resources.
history of computer from difference engine
Answers
Answer:
Charles Babbage (1791-1871), computer pioneer, designed two classes of engine, Difference Engines, and Analytical Engines. Difference engines are so called because of the mathematical principle on which they are based, namely, the method of finite differences.
Explanation:
Difference Engine, an early calculating machine, verging on being the first computer, designed and partially built during the 1820s and '30s by Charles Babbage.
Which line of code in this program is most likely to result in an error?

Answers
Line 2 is most likely to result in an error because it's trying to print out the word hello but words need to be surrounded with quotation marks.
Uncontrolled railroad crossing warning signs include _____
A. round black-on-yellow warning signs.
B. red flashing lights.
C. crossing gates.
D. none of the above
Answers
Answer:
letter D
Explanation:
The controlled railroad crossings have red lights and warning signs with railway gates. But if none of those items are present, then it is an uncontrolled railroad crossing.
Uncontrolled railroad crossing warning signs include; D; None of the above
There are two main types of railroad crossings namely;
Controlled railroad crossing warning signs.Uncontrolled railroad crossing warning signs.A Controlled railroad crossing has signs such as warning signs, red lights and railway gates.
However, in uncontrolled railroad crossing, the signs don't include any of the ones listed for controlled railroad crossing signs but instead will have no signs, no signals and no gates.
Looking at the options, A, B and C represent controlled railroad crossing signs and so the correct answer in none represents uncontrolled railroad crossing signs.
Read more about railroad crossings at; https://brainly.com/question/4360017
Help me with this digital Circuit please




Answers
A subset of electronics called digital circuits or digital electronics uses digital signals to carry out a variety of tasks and satisfy a range of needs.
Thus, These circuits receive input signals in digital form, which are expressed in binary form as 0s and 1s. Logical gates that carry out logical operations, including as AND, OR, NOT, NANAD, NOR, and XOR gates, are used in the construction of these circuits.
This format enables the circuit to change between states for exact output. The fundamental purpose of digital circuit systems is to address the shortcomings of analog systems, which are slower and may produce inaccurate output data.
On a single integrated circuit (IC), a number of logic gates are used to create a digital circuit. Any digital circuit's input consists of "0's" and "1's" in binary form. After processing raw digital data, a precise value is produced.
Thus, A subset of electronics called digital circuits or digital electronics uses digital signals to carry out a variety of tasks and satisfy a range of needs.
Learn more about Digital circuit, refer to the link:
https://brainly.com/question/24628790
#SPJ1
Database systems are exposed to many attacks, including dictionary attack, show with implantation how dictionary attack is launched?(Java or Python) ?
Answers
A type of brute-force attack in which an intruder uses a "dictionary list" of common words and phrases used by businesses and individuals to attempt to crack password-protected databases.
What is a dictionary attack?
A Dictionary Attack is an attack vector used by an attacker to break into a password-protected system by using every word in a dictionary as a password for that system. This type of attack vector is a Brute Force Attack.
The dictionary can contain words from an English dictionary as well as a leaked list of commonly used passwords, which, when combined with common character replacement with numbers, can be very effective and fast at times.
To know more about the dictionary attack, visit: https://brainly.com/question/14313052
#SPJ1
2. Write a C program that generates following outputs. Each of the
outputs are nothing but 2-dimensional arrays, where ‘*’ represents
any random number. For all the problems below, you must use for
loops to initialize, insert and print the array elements as and where
needed. Hard-coded initialization/printing of arrays will receive a 0
grade. (5 + 5 + 5 = 15 Points)
i)
* 0 0 0
* * 0 0
* * * 0
* * * *
ii)
* * * *
0 * * *
0 0 * *
0 0 0 *
iii)
* 0 0 0
0 * 0 0
0 0 * 0
0 0 0 *

Answers
Answer:
#include <stdio.h>
int main(void)
{
int arr1[4][4];
int a;
printf("Enter a number:\n");
scanf("%d", &a);
for (int i=0; i<4; i++)
{
for(int j=0; j<4; j++)
{
if(j<=i)
{
arr1[i][j]=a;
}
else
{
arr1[i][j]=0;
}
}
}
for(int i=0; i<4; i++)
{
for(int j=0; j<4; j++)
{
printf("%d", arr1[i][j]);
}
printf("\n");
}
printf("\n");
int arr2[4][4];
int b;
printf("Enter a number:\n");
scanf("%d", &b);
for (int i=0; i<4; i++)
{
for(int j=0; j<4; j++)
{
if(j>=i)
{
arr1[i][j]=b;
}
else
{
arr1[i][j]=0;
}
}
}
for(int i=0; i<4; i++)
{
for(int j=0; j<4; j++)
{
printf("%d", arr1[i][j]);
}
printf("\n");
}
printf("\n");
int arr3[4][4];
int c;
printf("Enter a number:\n");
scanf("%d", &c);
for (int i=0; i<4; i++)
{
for(int j=0; j<4; j++)
{
if(j!=i)
{
arr1[i][j]=c;
}
else
{
arr1[i][j]=0;
}
}
}
for(int i=0; i<4; i++)
{
for(int j=0; j<4; j++)
{
printf("%d", arr1[i][j]);
}
printf("\n");
}
printf("\n");
return 0;
}
Explanation:
arr1[][] is for i
arr2[][] is for ii
arr3[][] is for iii


What do those codes do???

Answers
Explanation:
Essentially,
<label for="fname"> First Name: </label>
Creates a label under "fname". The text that will be displayed is First Name.
<input type="text" id="fname" name="fname"
The input type is searching for text, which will be the user's entered name. After collecting the name, it then stores it into "fname".
Example:
First Name:
[enter name]
The same concept goes towards the botton email section as well.
Hope this helps! ^-^
-Isa
Transmissions in wireless networks do not allow for collision detection but try to avoid collision. Briefly describe this process and explain why it is termed as unreliable.
Answers
Transmissions in wireless networks do not allow for collision detection but try to avoid collision and also It is especially crucial for wireless networks since wireless transmitters desensing (turning off) their receivers during packet transmission prevents the option of collision detection using CSMA/CD.
What are the different types of wireless transmission?Wireless transceivers are unable to send and receive on the same channel simultaneously, hence they are unable to identify collisions. This is because the send power (which is typically around 100mw) and the receive sensitivity have such a huge disparity (commonly around 0.01 to 0.0001mw).
Therefore, Infrared, broadcast radio, cellular radio, microwaves, as well as communications satellites are examples of wireless transmission media that are used in communications. Infrared (IR), which is a wireless transmission medium that uses infrared light waves to transmit signals, was covered previously in the chapter.
Learn more about collision detection from
https://brainly.com/question/14775265
#SPJ1
Homework state ten difference between electronic and non electronic means of communication
Answers
Here are the ten differences between electronic and non-electronic means of communication:
The Differences between electronic and non-electronic means of communication:Method
Speed
Distance
Cost
Accessibility
Record-keeping
Media
Security
Collaboration
Environmental impact
The swiftness of communication sets apart electronic means from their non-electronic counterparts as the second distinguishing factor. Electronic communication enables fast delivery and receipt of messages, facilitating instantaneous communication over vast geographic areas.
By simply pressing a few buttons or tapping on a screen, data can be transmitted and obtained within seconds. Conversely, traditional methods such as sending tangible letters or having in-person discussions may result in message delivery setbacks. Electronic methods of communication are faster than traditional letter delivery or physical presence, since the latter can impede the efficiency of communication.
Read more about communication here:
https://brainly.com/question/28153246
#SPJ1
Complete the sentence.
If you wanted the best performance for a game that requires a powerful graphics processor and lots of memory, you
would run it on a
tablet
desktop
smartphone
Answers
A Quicksort (or Partition Exchange Sort) divides the data into 2 partitions separated by a pivot. The first partition contains all the items which are smaller than the pivot. The remaining items are in the other partition. You will write four versions of Quicksort:
• Select the first item of the partition as the pivot. Treat partitions of size one and two as stopping cases.
• Same pivot selection. For a partition of size 100 or less, use an insertion sort to finish.
• Same pivot selection. For a partition of size 50 or less, use an insertion sort to finish.
• Select the median-of-three as the pivot. Treat partitions of size one and two as stopping cases.
As time permits consider examining additional, alternate methods of selecting the pivot for Quicksort.
Merge Sort is a useful sort to know if you are doing External Sorting. The need for this will increase as data sizes increase. The traditional Merge Sort requires double space. To eliminate this issue, you are to implement Natural Merge using a linked implementation. In your analysis be sure to compare to the effect of using a straight Merge Sort instead.
Create input files of four sizes: 50, 1000, 2000, 5000 and 10000 integers. For each size file make 3 versions. On the first use a randomly ordered data set. On the second use the integers in reverse order. On the third use the
integers in normal ascending order. (You may use a random number generator to create the randomly ordered file, but it is important to limit the duplicates to <1%. Alternatively, you may write a shuffle function to randomize one of your ordered files.) This means you have an input set of 15 files plus whatever you deem necessary and reasonable. Files are available in the Blackboard shell, if you want to copy them. Your data should be formatted so that each number is on a separate line with no leading blanks. There should be no blank lines in the file. Even though you are limiting the occurrence of duplicates, your sorts must be able to handle duplicate data.
Each sort must be run against all the input files. With five sorts and 15 input sets, you will have 75 required runs.
The size 50 files are for the purpose of showing the sorting is correct. Your code needs to print out the comparisons and exchanges (see below) and the sorted values. You must submit the input and output files for all orders of size 50, for all sorts. There should be 15 output files here.
The larger sizes of input are used to demonstrate the asymptotic cost. To demonstrate the asymptotic cost you will need to count comparisons and exchanges for each sort. For these files at the end of each run you need to print the number of comparisons and the number of exchanges but not the sorted data. It is to your advantage to add larger files or additional random files to the input - perhaps with 15-20% duplicates. You may find it interesting to time the runs, but this should be in addition to counting comparisons and exchanges.
Turn in an analysis comparing the two sorts and their performance. Be sure to comment on the relative numbers of exchanges and comparison in the various runs, the effect of the order of the data, the effect of different size files, the effect of different partition sizes and pivot selection methods for Quicksort, and the effect of using a Natural Merge Sort. Which factor has the most effect on the efficiency? Be sure to consider both time and space efficiency. Be sure to justify your data structures. Your analysis must include a table of the comparisons and exchanges observed and a graph of the asymptotic costs that you observed compared to the theoretical cost. Be sure to justify your choice of iteration versus recursion. Consider how your code would have differed if you had made the other choice.
Answers
The necessary conditions and procedures needed to accomplish this assignment is given below. Quicksort is an algorithm used to sort data in a fast and efficient manner.
What is the Quicksort?Some rules to follow in the above work are:
A)Choose the initial element of the partition as the pivot.
b) Utilize the same method to select the pivot, but switch to insertion sort as the concluding step for partitions that contain 100 or fewer elements.
Lastly, Utilize the same method of pivot selection, but choose insertion sort for partitions that are of a size equal to or lesser than 50 in order to accomplish the task.
Learn more about Quicksort from
https://brainly.com/question/29981648
#SPJ1
HELP PLEASE ASAP! I don't know what is wrong with my code, it's suppose to output the same given output. C++ program.
#include //Input/Output Library
#include //Srand
#include //Time to set random number seed
#include //Math Library
#include //Format Library
using namespace std;
//User Libraries
//Global Constants, no Global Variables are allowed
//Math/Physics/Conversions/Higher Dimensions - i.e. PI, e, etc...
//Function Prototypes
void init(int [],int);//Initialize the array
void print(int [],int,int);//Print the array
void revrse(int [],int);;//Reverse the array
//Execution Begins Here!
int main(int argc, char** argv) {
//Set the random number seed
srand(static_cast (time(0)));
//Declare Variables
const int SIZE=50;
int test[SIZE];
//Initialize or input i.e. set variable values
init(test,SIZE);
//Display the outputs
print(test,SIZE,10);
//Reverse the Values
revrse(test,SIZE);
//Display the outputs
print(test,SIZE,10);
//Exit stage right or left!
return 0;
}
void init (int test[],const int x) {
for (int i=0; i >test[i];
}
}
void revrse(int test[],int SIZE){//Reverse the array
int test1[SIZE];
for(int i=0; i
test1[i] = test[SIZE-i-1];
}
for(int i=0; i
test[i]=test1[i];
}
}
void print (int test[] , int SIZE, int perlin) {
for(int i=0; i
cout<
if(i%perlin==(perlin-1))
cout<
}
}


Answers
The code that is written above is one that lacks the "iomanip" statement for inclusion. Incorporating it is good in using the setw function for arranging the output.
Once you have rectified the print function, make sure to include the statement cout << endl; after completing the loop so that a fresh line is printed after every line of output.
What is the code about?The loop condition within the init function should be modified to i < x instead of i > test[i]. To start the array elements, the loop needs to iterate starting from 0 and lastly at x-1.
Note that you neglected to return the inverted elements to their initial arrangement in the source test array. To double the data, place test[i] = test1[i]; within the loop.
Learn more about code from
https://brainly.com/question/26134656
#SPJ1


Write a Boolean function named isPrime which takes an integer as an argument and returns true if the argument is a prime number, or false otherwise. Use the function in a program that prompts the user to enter a number then displays a message indicating whether the number is prime.
Answers
Answer:
public static lotsof verbosekrap(String args[]) {
int num;
printf("Enter this nonsense BF: ");
scanf("%d", &num);
isPrime(num);
}
public boolean isPrime(int num) {
if (num == prime) {
returns true;
} else {
returns "your mom sucks and fails";
}
Explanation:
this is a mix of C and Java, I don't care
Integers numPizzas and dollars are read from input. A pizza costs 5 dollars.
If numPizzas is less than 5, output "numPizzas requires at least 5 to purchase."
If numPizzas is greater than or equal to 5, then declare and initialize int variable totalCost with the product of numPizzas and 5.
If totalCost is less than or equal to dollars, output "Successful purchase!"
Otherwise, output "Not all pizzas purchased."
If numPizzas is greater than 26, output "Now out of stock." Otherwise, output "Item still in stock."
End with a newline.
Ex: If the input is 8 67, then the output is:
Successful purchase!
Item still in stock.
Answers
The program based on the information given is depicted below.
How to write the program#include <iostream>
using namespace std;
int main() {
int numPizzas, dollars;
cin >> numPizzas >> dollars;
if (numPizzas < 5) {
cout << "numPizzas requires at least 5 to purchase." << endl;
}
else {
int totalCost = numPizzas * 5;
if (totalCost <= dollars) {
cout << "Successful purchase!" << endl;
if (numPizzas > 26) {
cout << "Now out of stock." << endl;
}
else {
cout << "Item still in stock." << endl;
}
}
else {
cout << "Not all pizzas purchased." << endl;
}
}
return 0;
}
Note: The endl is used to output a newline character at the end of each output message.
Learn more about program on:
https://brainly.com/question/26642771
#SPJ1
TRUE/FALSE 75POINTS
1 Newspapers are forms of digital media
True
False
2 Moore's Law says that every two years the speed of computers doubles.
True
False
3 Web 2.0 is place where digital media is not just received but both created and shared.
True
False
4 click farms are interactive games for web2.0 users
true
false
5 Careers in digital media have drastically declined in recent years.
True
False
Answers
Newspapers are forms of digital media is a false statement.
Moore's Law says that every two years the speed of computers doubles is a true statementWeb 2.0 is place where digital media is not just received but both created and shared is a true statement.The click farms are interactive games for web2.0 users is a false statement.Careers in digital media have drastically declined in recent years is a false statement.What are the types of newspaper media?A newspaper is known to be a kind of a Print Media. Note that it is said to be the oldest media forms and they are known to be newspapers, magazines, journals and others.
Also, Moore's Law is said to be one that states that the amount of transistors on a processor chip will become a double portion every 18 month
Therefore, Newspapers are forms of digital media is a false statement.
Moore's Law says that every two years the speed of computers doubles is a true statementWeb 2.0 is place where digital media is not just received but both created and shared is a true statement.The click farms are interactive games for web2.0 users is a false statement.Careers in digital media have drastically declined in recent years is a false statement.Learn more about Newspapers from
https://brainly.com/question/26027924
#SPJ1
The original creators of Android were ____________.
Answers
Answer:
I got this from online
Explanation:
Rich Miner, Nick Sears, Chris White, and Andy Rubin.