What type of gesture is typically used for zooming on a touchscreen?
Answers
The pinch gesture is typically used for zooming on a touchscreen.
What is a pinch gesture?The pinch gesture is a touch gesture used to zoom in and out of an image, webpage, or other material on a touchscreen device. It involves placing two fingers on the screen, such as the thumb and index finger, and bringing them together to zoom out or pulling them apart to zoom in.
When it comes to modern mobile devices, such as smartphones and tablets, this is one of the most prevalent gestures, and it is supported by most touchscreen operating systems.
Learn more about touch screen at:
https://brainly.com/question/28039940
#SPJ11
Related Questions
please help with this question

Answers
Answer:
whats the problem/question?
Explanation:
2. ¿Cuáles de los siguientes Software son lenguajes de Programación?
A) Word, Excel y Powerpoint
B) C# Java y Visual Basic
C) Pseint, Raptor Flowchart
D) Windows, Linux, Mac OS
Answers
B) C# Java y Visual Basic
Create an infographics using the Word Processing Software, informing the audiences about internet safety practices.
Answers
Here is a suggested infographic on internet safety practices using Microsoft Word:
[A Word document shows the following infographic:]
Staying Safe Online
Protect your personal information. Never share your name, address, phone number, passwords, or Social Security Number on social media or public websites.
Be wary of phishing emails and malicious links. Never click links or download attachments from unknown or untrusted sources. Legitimate companies will not ask for sensitive data via email.
Use strong and unique passwords. A strong password contains a minimum of 8 characters, a mix of letters, numbers and symbols, and is not based on personal information. Use different passwords for different online accounts.
Be cautious of what you post. Anything you post online can potentially last forever. Do not post anything that you would not want seen by anyone.
Turn on two-factor authentication whenever possible. This adds an extra layer of security for your accounts like email, social media, and cloud storage services.
Ensure all devices and software are up to date. Install the latest updates to keep security patches current to protect against threats.
Be wary of public Wi-Fi networks. Public networks are not secure and all your online activity and information can be visible to others. Avoid conducting sensitive activities on public Wi-Fi.
Signal for help if anything suspicious happens. If you notice any suspicious activity on your accounts or devices, changing passwords or unauthorized logins, report it immediately to the concerned companies and consider filing a police report.
Online privacy and security is a shared responsibility. Be proactive and spread awareness about internet best practices to help keep everyone safe online. Together, we can make the internet a safer place!
Does this infographic look okay? I tried to highlight some key best practices around protecting personal information, using strong passwords, being cautious of what is posted online, enabling two-factor authentication, keeping software up to date, avoiding public Wi-Fi and knowing how to get help if needed. Please let me know if you would like me to modify anything in the infographic. I can also suggest some other topics or formatting styles if required.
A brief overview of some important internet safety practices that you can include in your infographic using the Word Processing Software is given.
How to explain the informationUse strong passwords: Use a combination of uppercase and lowercase letters, numbers, and symbols in your passwords, and avoid using personal information.
Enable two-factor authentication: Two-factor authentication provides an extra layer of security by requiring a second form of authentication in addition to your password.
Be careful with personal information: Don't share personal information like your full name, address, phone number, or social security number online.
Learn more about Word Processing on
https://brainly.com/question/985406
#SPJ1
Complete the constructors and the sectorArea method of the Circle class.
public class Circle
{
private double radius;
// constructors
// postcondition: the instance variable is initialized
public Circle(double rad)
{
}
// postcondition: the instance variable is initialized
public Circle(int diameter)
{
}
// postcondition: returns the sector area of a circle with radius equal to
// this circle's radius, according to the formula: (deg / 360) * PI * r^2,
// where deg is the angle in degrees passed as the parameter,
// PI is the value of pi (3.1415...), r is the radius of the circle,
// and "^2" means raised to the second power.
// Use the Math class constant to represent the value of pi.
public double sectorArea(double degree)
{
}
// There may be other instance variables, constructors,
// and methods that are not shown.
}
Answers
Answer:
the diameter
Explanation:
is * piI * r^28x 45
What are some ways you deal with stress at school or at home? How could you use those techniques in the workplace?
Answers
Some techniques for managing stress at home and at school that could help in the workplace include active breaks, proper rest, breathing exercises, and yoga.
What is stress?Stress is a term that refers to the way in which an individual's brain interprets a situation or event that represents difficulty for her life.
One of the main causes of stress is the uncontrolled production and release of hormones that put the individual in an alert attitude that can trigger other symptoms such as:
High blood pressure.Increase in heart rate.Decreased blood sugar levels.How to combat work stress?To combat work stress and avoid these symptoms and health conditions, it is advisable to take work situations calmly and relaxed. Additionally, there are activities that can relieve pressure such as:
Practice yoga.Do breathing exercises.Do not take work home.Take active breaks.Rest properly at night.Learn more about stress in: https://brainly.com/question/1178663
Answer:
take breaks,
Explanation:
You can use the ____ method to search a string to determine whether it contains a specific sequence of characters.
Answers
Answer:
in
Explanation:
Not an explanation, but here's an example:
if "mouth" in "mouthwatering":
print("It is.")
else:
pass
Another example:
if "water" in "mouthwatering":
print("Yes.")
else:
pass
a) the program took a long time to run for larger values of n. explain. b) explain the result for f(47). c) how could we improve the performance of this program (by a lot)? d) rewrite the program to work correctly for somewhat larger values of n (up to 90 or so). hint: what is the largest integer we can represent? what are some issues you might encounter when running this version of the program? e) rewrite the program to run for much larger values of n (over 200). hint: how do we represent numbers larger than the largest integer we can represent? what are some issues you might encounter when running this version of the program?
Answers
The program taking a long time to run for larger values of n can be attributed to the complexity of the algorithm used. If the program has a time complexity.
The number of operations needed to complete the program grows quadratically. This means that for larger values of n, the program will take significantly more time to run compared to smaller values. To explain the result for f(47), we would need to know the specific details of the program.
There are several ways to improve the performance of a program. One way is to optimize the algorithm used. By using a more efficient algorithm with a lower time complexity, the program can run faster even for larger values of n. Additionally, optimizing the code by reducing unnecessary computations and improving memory usage can also lead to performance improvements.
To know more about complexity visit:
https://brainly.com/question/31836111
#SPJ11
Write a program noonsnooze.java that takes an integer command-line argument snooze and prints the time of day (using a 12-hour clock) that is snooze minutes after 12:00pm (noon).
Answers
A program noonsnooze.java that takes an integer command-line argument snooze and prints the time of day (using a 12-hour clock) that is snooze minutes after 12:00pm (noon) is given below:
The Codepublic class NoonSnooze
{
public static void main(String[] args)
{
int snooze = Integer.parseInt(args[0]);
int hour = 12 + (snooze / 60);
int minutes = 00 + snooze % 60;
String ampm;
if(hour%24 < 12) ampm="pm";
else ampm="am";
hour=hour%12;
if (hour==00) hour=12;
String time = hour + ":" + minutes + " " + ampm;
System.out.println(time);
}
}
Read more about programming here:
https://brainly.com/question/23275071
#SPJ1
Which of the following statement is true?
A. An iconic sign need to provide a particularly close replica of its object’s overall appearance.
B. A full-color photograph can duplicate all the features of the appearance of reality.
C. It is very likely that even a rudimentary match between image and reality can trigger the brain to employ its real-world process of visual interpretation.
D. Advertising rely primarily on symbolic property of sign than on indexical and iconic properties of sign to convey the message.
E. Visual communication has a more clear formula than verbal communication to signify analogies, contrasts, causal claims, and other kinds of propositions.
Answers
The true statement among the following statements is that "It is very likely that even a rudimentary match between image and reality can trigger the brain to employ its real-world process of visual interpretation". So, the correct answer is option C.
An iconic sign is a sign that directly represents the thing it denotes, rather than having a symbolic or conventional connection with it. For example, a portrait is an iconic sign that represents the person being portrayed. Another example is a photograph of a dog; it is an iconic sign because it looks exactly like the dog it is representing.
It is not necessary that an iconic sign need to provide a particularly close replica of its object’s overall appearance. While a full-color photograph can duplicate all the features of the appearance of reality, it is not entirely true because photographs are still a representation of reality, not reality itself.
Advertising does not rely primarily on symbolic property of sign than on indexical and iconic properties of sign to convey the message. Rather, it uses a combination of all three properties to convey the message.
Visual communication does not have a more clear formula than verbal communication to signify analogies, contrasts, causal claims, and other kinds of propositions. Each mode of communication has its own unique ways of conveying meaning.
Therefore, the correct answer is option C.
To learn more about rudimentary: https://brainly.com/question/11378924
#SPJ11
What is the value of the variable “I” just before the program exits the whole loop?
I=1;
While(I<5)
{I++;}
I =I +2;
A)1
B)4
C)5
D)6
E)7
Answers
Answer:
For PLATO, the answer is NOT 4.
Explanation:

The value of the variable “I” just before the program exits the whole loop is 7. The correct option is E.
What are the variables in the program?A variable in programming is a value that can change based on external factors or data that has been supplied to the program. A program typically consists of data that it uses while running and instructions that tell the machine what to execute.
In a computer program, information is stored in variables so that it may be accessed and changed.
They also give us the means to give data a name that is descriptive, making it easier for us and the reader to understand our programs. It can be useful to conceive of variables as data storage units.
I=1;
While(I<5)
{I++;}
I =I +2; 7
Therefore, the correct option is E) 7.
To learn more about variables, refer to the link:
https://brainly.com/question/15776744
#SPJ2
I need some help with this project. The picture of the assignment is above

Answers
Answer:
sorry
Explanation:
you need to do this on your own Wahhabi
but if you sub to my you-tube channel at chris got ha,x i will help you out
Which of the following is a trademark automatically received by an organization when a symbol is being consistently used in the normal course of business?
Answers
Complete Question:
Which of the following is a trademark automatically received by an organization when a symbol is being consistently used in the normal course of business?
Group of answer choices
A. Open source trademark.
B. Common law trademark.
C. Registered trademark.
D. Open source trademark.
Answer:
B. Common law trademark.
Explanation:
A common law trademark can be defined as a protection or enforceable mark for a product name, logo, symbol or brand name used to distinguish goods and services prior to its registration with the state or federal government. Common law trademark is a trademark which is automatically received by an organization when a symbol is being consistently used in the normal course of business.
This ultimately implies that, common law trademarks are not governed by any statute and as such are only limited to the geographical location where they are used.
For instance, if a tomato paste is being sold to consumers with the product name "Ginoo" in Florida, the company's trademark applies to Florida only. Thus, another company can use the product name without any trademark infringement in other states of the country such as New York, Washington DC, California etc. except in Florida due to a common law trademark.
Denise earned a C in Language Arts. Daniel earned a C as well but took Language Arts Honors. Which of the following is true?
Answers
Daniel also had a C, but he enrolled in Language Arts Honors. this is true statement.
What is C language?The programming language C is all-purpose for computers. Dennis Ritchie came up with it back in the '70s, and it's still heavily utilized and important today. The features of C, by design, accurately mirror the capabilities of the CPUs it is intended to run on. At Bell Laboratories in 1972, Dennis Ritchie developed the general-purpose computer language C. Despite being ancient, it is a relatively common language. Due to its development for the UNIX operating system, C has a close connection to UNIX. High-level, all-purpose programming languages like the C language are available. For those who program systems, it offers a simple, reliable, and effective interface. As a result, system software, application software, and embedded systems are all frequently developed using the C language. Languages like C and C++ are object-oriented, whereas C is a procedural language.To learn more about C language refer to:
https://brainly.com/question/26535599
#SPJ1
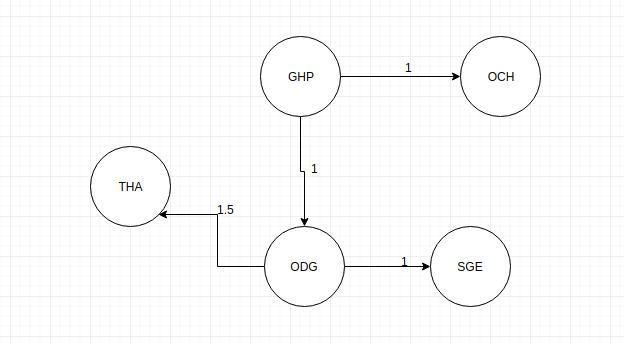
use prim's algorithm to find a minimal spanning tree for the times whose vertices are the hotels given in the distance chart. what is the total time for this spanning tree?
Answers
The greedy approach is the foundation of the Prim's algorithm. We choose the edge with the least weight at each step, assuming that the final node hasn't been reached yet.
The spanning tree would appear like this. All the names are written in shorthand. Kindly corelate.
What is spanning tree?
A spanning tree is a sub-graph of an undirected connected graph that contains all of the graph's vertices and the fewest number of edges possible between them. It is not a spanning tree if a vertex is missed. Weights may or may not be applied to the edges.
What is minimum spanning tree?
A minimum spanning tree is one in which the weight of the edges added together is as small as it can be.
To know more about spanning tree, check out:
https://brainly.com/question/13148966
#SPJ1
describe at least five ways in which Information Technology can help students studying subject other than computing
Answers
Answer:
‘Computer Science’ and ‘information technology’ are completely different subjects. Information Technology (IT) is-
(i) the study,
(ii) design,
(iii) development,
(iv) implementation, and
(v) support or management
of computer-based information systems, particularly software applications and computer hardware.
Information Technology (IT) deals with the use of electronic computers and computer software to-
(i) convert,
(ii) store,
(iii) protect,
(iv) process,
(v) transmit, and
(vi) securely retrieve information.
Shortly, information technology (IT) itself means learning to use technology in business or in studies of some subject matter using technology.
Hence, IT could help students studying subjects other than computing with the above mentioned points considered.
The following is a mock-up of a Battleship game board. The square with a X marks the position of a battleship.
Where is the ship?
1 2 3 4
A
B X
C
D
Row ___
Column ___
Row: D, C, A, or B?
Column: 4, 3, 1, or 2?
Answers
Answer:
Row B column 2
Explanation:
X is directly underneath column 2 and the row is B
Answer:
its actually B3
Explanation:
1. What pricing strategy is used by local electric
distributors/retailers in charging us monthly electric bills?
Answers
Local electric distributors/retailers are the ones that distribute and sell electricity to the consumers.
They need to have a pricing strategy to charge the consumers a fair price for their services. There are different pricing strategies used by these companies to charge the monthly electric bills.One of the most common pricing strategies used by local electric distributors/retailers is the Cost-plus pricing strategy. This strategy involves adding a markup to the total cost of providing the service. The markup is added to cover the expenses and generate a profit for the company. This pricing strategy is commonly used by regulated utilities as the markup is reviewed and approved by the regulatory commission.
The second pricing strategy is the value-based pricing strategy. This strategy involves charging the customers based on the value they receive from the service. For example, a customer who consumes more electricity will be charged more. This pricing strategy is common in competitive markets where different electric distributors/retailers are competing to win customers.The third pricing strategy is the demand-based pricing strategy. This strategy involves charging the customers based on the demand for electricity.
During peak hours, when the demand is high, the price of electricity is high. During off-peak hours, when the demand is low, the price of electricity is low. This pricing strategy is used to encourage the customers to use electricity during off-peak hours and reduce the load during peak hours.In conclusion, local electric distributors/retailers use different pricing strategies to charge the consumers monthly electric bills. The choice of pricing strategy depends on various factors such as the regulatory environment, market competition, and customer demand.
Learn more about customer :
https://brainly.com/question/13472502
#SPJ11
Solid-state storage uses___ to store data

Answers
Answer: Capacitors
Explanation: Soild-State drives use conductors to work.
Many 3PLs are using the technology area to distinguish themselves from
A. warehouse firms.
B. transport firms.
C. 4PLs.
D. competitors.
Answers
Many 3PLs (third-party logistics providers) are using technology as a way to distinguish themselves from warehouse and transport firms.
Technology has become increasingly important in the logistics industry, with the rise of e-commerce and the need for faster and more efficient supply chain operations. 3PLs that invest in and leverage technology can offer their customers a range of benefits, such as real-time tracking of shipments, visibility into inventory levels and order status, and the ability to quickly adapt to changes in demand or supply chain disruptions. By offering these value-added services, 3PLs can differentiate themselves from traditional warehouse and transport firms, which may not have the same level of technological capabilities or resources.
Learn more about Many 3PLs here: brainly.com/question/14327713
#SPJ11
(a) Willow has created a hangman program that uses a file to store the words the program can select from. A sample of this data is shown in Fig. 3.
Fig. 3
crime, bait, fright, victory, nymph, loose.
Show the stages of a bubble sort when applied to data shown in Fig. 3.
(b) A second sample of data is shown in Fig. 4.
Fig. 4.
amber, house, kick, moose, orange, range, tent, wind, zebra.
Show the stages of a binary search to find the word "zebra" when applied to the data shown in Fig. 4.
Answers
(a) A bubble sort applied to the data in Fig. 3 produces these stages:
Loose, crime, bait, fright, victory, nymph
Crime, loose, bait, fright, victory, nymph
Bait, crime, loose, fright, victory, nymph
Fright, bait, crime, loose, victory, nymph
Victory, fright, bait, crime, loose, nymph
Nymph, victory, fright, bait, crime, loose.
(b) When a binary search is conducted in order to find the word "zebra" in the data in Fig. 4, the following yield occurs:
The search begins by looking at the list's middle item, which is "orange".
Hope to explain the bubble sortSince "zebra" comes after "orange" alphabetically, the search continues amongst the second half of the list.
The centermost item on this narrowed down list proves to be "tent", from there, it is deduced that "zebra" must go after "tent" alphanumerically.
Likewise, the process is repeated for the reminder of the sequence.
Moving forward, the search encounters "wind" in its midst, again concluding that zebra has to appear subsequently.
Finally, when observing the midpoint of the remainder, "zebra" is pinpointed as the desired result.
Learn more about bubble sort on
https://brainly.com/question/30395481
#SPJ1
I do not understand what the are asking in csys 1. 3. 6
And I would really prefer someone explaining it so I will understand the next one
Answers
Without further context, it is difficult to provide a specific answer to what is being asked in csys 1.3.6. However, it is possible that this is a reference to a specific command or function within a particular system or software.
To better understand what is being asked in csys 1.3.6, you may need to provide more information about the system or software you are working with. This could include the context in which the command is being used, any error messages or prompts that appear when you enter the command, and any documentation or resources that may provide additional information about the command.Alternatively, if you are encountering difficulty with a specific task or problem within the system or software, you may want to seek assistance from a support team or online community. They may be able to provide guidance and help you better understand the specific command or function within the system or software.
To learn more about command click the link below:
brainly.com/question/30585049
#SPJ4
what is the main purpose of the circulatory system
Answers
The network of blood vessels and the heart that carries blood throughout the body. This system helps tissues get the right amount of nutrients, oxygen, and waste disposal.
The most important component of the circulatory system?The primary function of the circulatory system is to carry oxygen, nutrients, and hormones to the muscles, tissues, and organs throughout the body. Another role of the circulatory system is to remove waste from cells and organs so that your body can eliminate it.
What is the primary goal of this quiz about the circulatory system?The circulatory system's job is to provide nutrients and oxygen to body cells while returning carbon dioxide and oxygen-poor blood to the heart and lungs.
To know more about circulatory system visit:-
https://brainly.com/question/29259710
#SPJ4
while t >= 1 for i 2:length(t) =
T_ppc (i) (T water T cork (i- = - 1)) (exp (cst_1*t)) + T cork (i-1);
T cork (i) (T_ppc (i) - T pet (i- = 1)) (exp (cst_2*t)) + T_pet (i-1);
T_pet (i) (T cork (i)
=
T_air) (exp (cst_3*t)) + T_air;
end
T final ppc = T_ppc (t);
disp (newline + "The temperature of the water at + num2str(t) + "seconds is:" + newline + T_final_ppc + " Kelvin" + newline + "or" + newline +num2str(T_final_ppc-273) + degrees Celsius" + newline newline);
ansl = input (prompt, 's');
switch ansl case 'Yes', 'yes'} Z = input (IntroText); continue case {'No', 'no'} break otherwise error ('Please type "Yes" or "No"')
end
end
Answers
The given code describes a temperature change model that predicts the final temperature of water based on various input parameters such as the temperatures of cork, pet, and air.
It appears that you are providing a code snippet written in MATLAB or a similar programming language. The code seems to involve a temperature calculation involving variables such as T_ppc, T_water, T_cork, T_pet, and T_air. The calculations involve exponential functions and iterative updates based on previous values.
The model uses a set of equations to calculate the temperature changes for each component.
The equations used in the model are as follows:
T_ppc(i) = (T_water – T_cork(i-1)) * (exp(cst_1 * t)) + T_cork(i-1)T_cork(i) = (T_ppc(i) – T_pet(i-1)) * (exp(cst_2 * t)) + T_pet(i-1)T_pet(i) = (T_cork(i) – T_air) * (exp(cst_3 * t)) + T_airThese equations are implemented within a for loop, where the input variables t, T_water, T_cork, T_pet, cst_1, cst_2, cst_3 are provided, and the output variable T_final_ppc represents the final temperature of the water after the temperature change.
Additionally, the code includes a prompt that allows the user to enter "Yes" or "No." Choosing "Yes" continues the execution of the code, while selecting "No" stops the code.
Overall, the code simulates and predicts the temperature changes of water based on the given inputs and equations, and offers the option to continue or terminate the execution based on user input.
Learn more about MATLAB: https://brainly.com/question/13715760
#SPJ11
Write a program that gets a list of integers from input, and outputs non-negative integers in ascending order (lowest to highest). Ex: If the input is: 10 -7 4 39 -6 12 2 the output is: 2 4 10 12 39
Answers
Answer:
Following are the code to this question:
#include <iostream>//defining header file
using namespace std;
int main()//defining main method
{
int a[]={10,-7,4,39,-6,12,2};//defining single deminition array and assign value
int i,x,j,t; //defining integer variable
cout<<"Before sorting value: ";
for(i=0;i<7;i++) //using loop to print value
{
cout<<a[i]<<" ";//print value
}
cout<<endl <<"After sorting value: ";
for(i=0;i<7;i++)//defining loop to sort value
{
for(j=i+1;j<7;j++)//count array value
{
if(a[i]>a[j]) //defining condition to inter change value
{
//performing swapping
t=a[i]; //integer variable t assign array value
a[i]=a[j];//swapp value
a[j]=t;//assign value in array
}
}
}
for(i=0;i<7;i++) //defining loop to print value
{
if(a[i]>=0) //defining condition to check positive value
{
cout<<a[i]<<" ";//print value
}
}
return 0;
}
Output:
Before sorting value: 10 -7 4 39 -6 12 2
After sorting value: 2 4 10 12 39
Explanation:
Following are the description to the above code:
In the above program code, Inside the main method, an array a[] is declared that assign some value, and another integer variable "i, j, x, and t" is declared, in which variable "i and j" are used in the loop, and "x, t" is used to sort value.In the next step, three main for loop is declared, in which the first loop is used to print array value.In the second loop, inside another loop is used that sorts array values.In the last loop, a condition is defined, that check the positive value in the array and print its values.Answer:
integers=[]
while True:
number=int(input())
if number<0:
break
integers.append(number)
print("",min(integers))
print("",max(integers))
Explanation:
if you are using the tor browser to visit a commercial website, which of the following statement are true? a. no tor node will know your source ip address b. no tor node will know your destination ip address c. no tor node will know your source and destination ip addresses at the same time d. the commercial website will not know your source ip address
Answers
If you are using the Tor browser to visit a commercial website, the statement that is true include the following: D. the commercial website will not know your source IP address.
What is an IP address?In Computer technology, an IP address is an abbreviation for Internet protocol address and it can be defined as a unique set of numbers that are assigned to a network device such as a computer, website or other network devices such as routers, switches, etc., in order to successfully differentiate them from one another in an active network system.
In Computer networking, the internet protocol (IP) address comprises two (2) main versions and these include;
Internet protocol version 4 (IPv4).Internet protocol version 6 (IPv6).In conclusion, a Tor browser is a special web browser that is designed and developed to mask the source IP address of any commercial website.
Read more on IP address here: brainly.com/question/13590517
#SPJ1
in conducting a computer abuse investigation you become aware that the suspect of the investigation is using abc company as his internet service provider (isp). you contact isp and request that they provide you assistance with your investigation. what assistance can the isp provide?
Answers
ISPs can provide assistance in a computer abuse investigation by disclosing user information, providing connection logs, email records, internet usage data, network logs, and complying with legal processes.
What assistance can the ISP provide?When we contact an internet service provider for help in a case of computer abuse investigation, they can help us through;
1. User Information: Using ISP, it can help to expose the information of the subscriber that is connected to the suspect's account. This can help track the suspect.
2. Connection Logs: This can help to keep records of internet connections which includes the IP addresses, timestamps and the duration of the sessions.
3. Email and Communication Records: It can also help to provide the content of the suspect email record and the timestamps between each message.
4. Internet Usage Data: It also help to track down the internet usage of the suspect such as browsing details, bandwidth usage etc.
5. Network Logs and Monitoring: In some cases, ISPs may have network monitoring systems in place that can capture traffic data, including packet captures, to help investigate network-related abuses or attacks. They can provide relevant logs or assist in analyzing network traffic.
6. Compliance with Legal Processes: ISPs must comply with lawful requests for assistance in investigations.
Learn more on ISP here;
https://brainly.com/question/19561587
#SPJ4
How do you manage your online presence? What kind of sites are you most active on, and what steps can you take to manage your image on these sites better?
Answers
Answer:
1. optimize your website to increase your online visibility and other search engines.
2. make your company information clear and prominent.
Though obvious, it's surprising how many businesses neglect to do make it easy to locate their business information. You should show:
company name
location, including city and state
contact information
overview of products and services
operating hours
3. provide useful content in your page
data warehouses that store large amounts of information about business transactions allow companies to use _______ to exploit the information they contain.
Answers
Data warehouses that store vast amounts of information about business transactions allow companies to utilize business intelligence tools and analytics to exploit the information they contain.
Data warehouses serve as centralized repositories that store large volumes of structured and organized data from various sources, including business transactions. These repositories provide a foundation for companies to analyze and exploit the information they contain in a meaningful way.
By leveraging business intelligence tools and analytics, companies can extract valuable insights, trends, and patterns from the data stored in the data warehouse. These tools enable businesses to perform complex queries, generate reports, and conduct advanced analytics to gain a deeper understanding of their operations, customer behavior, market trends, and more.
The exploitation of information in data warehouses empowers companies to make informed decisions, optimize processes, identify growth opportunities, and enhance overall business performance. By analyzing historical and real-time data, companies can gain valuable insights that drive strategic decision-making, operational efficiency, and competitive advantage.
In summary, data warehouses store vast amounts of information about business transactions, and companies can use business intelligence tools and analytics to exploit this information. Through data analysis and interpretation, companies can gain actionable insights that support decision-making, performance improvement, and strategic planning.
Learn more about Data warehouses here :
https://brainly.com/question/18567555
#SPJ11
The four main parts of a computer system are the Input, output, processor, and:
O A core.
OB. hardware.
OC. software.
OD. storage.
Answers
Answer:D) Storage
Explanation:
Write a half page summary on how to clean a Gaming PC properly.
Answers
Answer:
As a responsible PC gaming enthusiast, you simply cannot wait for spring to do a little routine cleaning on your PC. Regardless of whether you casually play or professionally game, all gaming computers are susceptible to dirt, dust, and other contaminants that can severely impact performance. Dust buildup can cause PC components to retain heat, making it difficult for internal fans to keep the system cool. As a result, the system can become less efficient and unusually slow. However, there are steps you can take to keep your gaming computer in great condition. In this article, we explain how to clean the inside of your gaming computer, so you can keep on fighting the good fight in digital worlds.Assemble the Right ToolsGaming desktops are very complex pieces of technology. Be smart by assembling the necessary tools and supplies before you begin the deep-clean process. Most of the products you need might already be sitting around the house, including compressed air cans, rubbing alcohol, white vinegar, distilled water, microfiber cloths, ear swabs, and tape.How to Clean a Gaming PCFollow these 10 steps to get back on good terms with your gaming rig.1. Disconnect the power cable, USB peripherals, as well as any audio equipment attached to your computer and safely discharge the remaining power.2. Take the computer case outside, so the dust doesn’t settle in the same room that your gaming setup is located.3. Wipe the exterior and interior of the computer case.4. Detach the dust filters and wipe away any accumulated dust. We recommend using compressed air for full coverage. If you have foam filters, gently rinse with water and leave them to dry.5. Wipe down the inside of the case by hand after disconnecting the graphics cards and RAM modules.6. If possible, remove the heatsink entirely to scrub away any gunk or debris.7. Clean off any dust hidden between the cracks of the graphics cards, so you can easily clean the motherboard.8. Remove any big clumps of dust by using a cloth dampened with rubbing alcohol.9. Use the compressed air can to clean nooks, crannies, and the motherboard. For stubborn dust spots, just dampen an ear swab with rubbing alcohol or use a gentle toothbrush to clean.10. Once the case interior is completely clean and free of dust, you can put each component back where it belongs.Routine cleaning and maintenance are important to the health of your gaming PC. We recommend using compressed air every three to six months to prevent dust buildup from impacting your PC components. You should also make an effort to clean your mouse, headphones, keyboard, and monitor to keep your gaming setup looking like new.
Explanation: