what are key characteristics of the introduction stage? (choose every correct answer.)
Answers
The introduction stage of a product is characterized by high marketing expenses, little competition, product development focus, small market size, low sales volume, refining of product quality and design, targeting early adopters, establishing brand reputation, higher product prices, limited quantities, developing distribution channels, extensive advertising, and market research activities.
The key characteristics of the introduction stage are as follows:High marketing and advertising expenses, little to no competition, focus on developing the product, small market size, and low sales volume during this stage are all key characteristics.
The product's quality and design are still being refined by the manufacturer. Customers who are interested in new products and willing to pay a premium for them are the target audience for companies in the introduction stage.
Competition is often non-existent or limited, allowing companies to establish their brands and reputations. The price of the product is often higher during the introductory phase because the company has yet to realize the economies of scale that come with mass production.
As a result, the product is often sold in limited quantities at a high price to recoup the company's development expenses and to maximize profit margins.
In the introduction stage, a company must develop its distribution channels and educate its target audience about the benefits of its new product. As a result, advertising and other promotional activities are typically more prevalent during this stage.
Companies will also engage in market research to gain a better understanding of their target audience and to fine-tune their marketing messages. As a result, high marketing and advertising expenses are a key characteristic of the introduction stage.
Learn more about stage of a product: brainly.com/question/25754149
#SPJ11
Related Questions
What is an easy and accurate way that a graphic designer can increase the size of a digital shape while keeping the ratio of height to width the same?
First make the height taller, and then drag the width by using one’s eyes to try to make sure the proportions stay the same.
Hold the key, such as Shift, that the program uses to make sure all dimensions are adjusted while dragging just one side.
Open the shape’s properties window, and type the height value multiplied by 2 and the width value multiplied by 3.
First convert the shape into a photo file, and then digitally manipulate it in a program such as Adobe Photoshop.
Answers
Answer:
Open the shape’s properties window, and type the height value multiplied by 2 and the width value multiplied by 3.
Explanation:
Answer: A resolution independent, vector graphics and illustration application used to create logos, icons, drawings, typography and complex illustrations for any medium.
explanation:
because it is what it is
Which of the following are relational operators? (Select all that apply)
(4 Points)
?=
=
!=
<
>=
==
Answers
The relational operators are used to compare two values are <, >=, !=
The following are the relational operators:
- "<" (less than)
- ">=" (greater than or equal to)
- "!=" (not equal to)
- "?=" (equal to)
The "=" operator is not a relational operator, but rather an assignment operator used to assign a value to a variable. The "?=" operator is not a standard relational operator in most programming languages, but rather a compound assignment operator used to perform a specific operation (such as addition or bitwise operations) on a variable and a constant, and then store the result back in the variable.
So, the correct answers are "<" (less than), ">=" (greater than or equal to), and "!=" (not equal to).
Answer: <, >=, !=
Learn more about relational operators here:https://brainly.com/question/28039937
#SPJ11
if an if else statement is true, it will include which kind of results?
A. different
B. the same
C. longer
D. shorter
Answers
Answer:
different because statement is false
Amber, a network administrator, is conducting VoIP training for other IT team members. Melanie, a new team member, is confused about the difference between latency and jitter. What is the BEST way to explain the difference
Answers
The best way to explain the difference is option A: Jitter is the up and down variation in latency.
What are VoIP services?Voice over Internet Protocol (VoIP), is known to be a form of a technology that gives one room to be able to make voice calls via the use of a broadband Internet connection.
In the case above, The best way to explain the difference is option A: Jitter is the up and down variation in latency as it is the only best option.
See options below
Jitter is the up and down variation in latency.
Latency is the up and down variation in jitter.
Jitter is caused by an inadequate codec.
Latency is caused by sampling; jitter is not.
Learn more about latency from
https://brainly.com/question/27013190
#SPJ1
If wearing protective gloves, there's no need to wash your hands after exposure to blood.
Answers
Answer:
No, still wash hands
Explanation:
Answer: wash hands
Explanation: if you don't then you could probably get hurt by the chemicals.
QUESTION 4 of 10: What term refers to the basic characteristics of a population segment, such as gender, age, and income?
Answers
What value is displayed as a result of executing the code segment?

Answers
Answer:
A: 3
Explanation:
The MOD operator is used to calculate the remainder of dividing two numbers, so by the end of this operation, we are adding the MODs of each integer in this list, because this program ends once each integer in list has gone through the steps, and the result of calculating the MOD of each integer is then added back because of the third step. So it should look like this: (4 MOD 2) + (2 MOD 2)...(1 MOD 2) and the result of adding these values should then result in 3.
The value which is displayed as a result of executing the code segment is equal to: A. 3.
What is MOD?MOD is an abbreviation for modulo operation and it can be defined as a mathematical technique that is used in computer science to determine the remainder of an arithmetic operation such as the division of two numbers.
Based on the code segment, the value which is displayed as a result of executing the modulo operation would be equal to 3 at the end of the iteration or operation.
Read more on computer codes here: brainly.com/question/25619349
What term is defined as software that allows users to use and adapt it for any purpose, often allowing the public to participate in further development? open well open well open use open use open pit open pit open source
Answers
A terminology which is defined as software that allows users to use and adapt it for any purpose, often allowing the public to participate in further development is: open source.
The types of software license.In Computer technology, there are four (4) main types of software programs based on usage rights and these include the following:
Freeware softwarePurchased licenseShareware softwareOpen source softwareWhat is an open source software?In Computer technology, an open source software can be defined as a terminology which is used to describe a type of software that all end users can use and adapt it for any purpose or modify it for free without paying any license fee (money).
Read more on software here: brainly.com/question/25703767
#SPJ1
which utility is used to prepare computers for imaging by removing specific information, such as the computer name and computer sid?
Answers
The utility that is used to prepare computers for imaging by removing specific information, such as the computer name and computer sid, is known as Sysprep.
Microsoft Windows operating systems come with an utility called Sysprep that is used to get a system ready for imaging or cloning.
The computer name, the security identification (SID), and other system-specific data are all removed from the system when Sysprep is executed on the machine. This eliminates conflicts and issues and enables the system to be imaged or cloned and distributed to other computers.
System administrators and other IT experts frequently utilize Sysprep to get systems ready for deployment in a big environment. When setting up a new network or adding new systems to an existing one, it can be used to create a standard image that can be quickly deployed to numerous computers, which can save time and effort.
To know more about Imaging kindly visit
https://brainly.com/question/29347554
#SPJ4
The ______ interprets and carries out the basic instructions that operate a computer.
Answers
The processor interprets and carries out the basic instructions that operate a computer.
What is Processor?
An integrated electronic circuit called a processor is what does the calculations for a computer. A processor executes basic instructions given from an operating system, including mathematical, logical, input/output (I/O), and other operations (OS). The majority of other processes rely on the actions of a processor.
What is Operating System?
An operating system (OS) is a piece of software that controls all other application programs in a computer after being originally loaded by a boot program. Through a specified application program interface, the application programs use the operating system by requesting services (API).
CPUs will perform most basic arithmetic, logic and I/O operations, as well as allocate commands for other chips and components running in a computer. The term processor is used interchangeably with the term central processing unit (CPU), although strictly speaking, the CPU is not the only processor in a computer.
Learn more about processor click on this:
https://brainly.com/question/474553
#SPJ4
Role of memory in a computer system
Answers
Answer/Explanation:
The role of memory in a computer system is to remember the date you have searched on it or websites you've visited or photos you've taken. This is called the memory drive. Memory drives are very important imagine spending your whole life on this video game and you finally finished your game! Well without the memory drive you'd have to start that game all over again.
Because of the memory drive we can save our data in our devices. Memory drive is used in every device that we use in modern day. Memory drives are important for computers to work properly. Did you know the reason we have fans or holes in the bottom of our computer is to cool the drives down in our computer?
It's because they get overheated cause they work on your computer constantly. Computers are very complex and high tech so it helps to make things into small drives. Memory is important for the survival of tech, computers. We use memory every day in different ways wether its our computers or our devices or our heads.
~ LadyBrain
T/F : because of the weaknesses of wep, it is possible for an attacker to identify two packets derived from the same iv.
Answers
The correct answer is True.Because of the weaknesses of WEP (Wired Equivalent Privacy), it is possible for an attacker to identify two packets derived from the same initialization vector (IV).
WEP is an outdated wireless security protocol that was commonly used in early Wi-Fi networks. It has several known vulnerabilities, including weak encryption mechanisms and predictable IVs. The IV is a component used in the encryption process of WEP to introduce randomness.One of the weaknesses of WEP is that it reuses IVs, which leads to the same encryption key being used for multiple packets. This repetition allows an attacker to capture enough packets and analyze their patterns to identify when two packets share the same IV. Once an attacker identifies packets with the same IV, they can employ statistical analysis techniques to potentially deduce the key used for encryption.
To know more about vector click the link below:
brainly.com/question/32077106
#SPJ11
Precisez la nature de l'information logique ou analogique pour chaque exaple ci dessous
Answers
Answer:
Bonjour pourriez vous m'aider svp ?
Précisez la nature de l'information (logique ou analogique pour chaque exemple ci dessous:
a) poids
b) conformité d'une pièce de monnaie
c) niveau d'eau dans une bouteille
d)porte ouverte ou fermée
e) force de pression
f) présence d'une personne dans une pièce
g)position angulaire
h) température inférieur ou supérieur à 15°C
i) vitesse du vent
j) présence de matériaux métallique à proximité
Enterprise database applications tend to have some flexibility for customization,
a. True b. False
Answers
a. True Enterprise database applications generally provide a certain degree of flexibility for customization.
These applications are designed to meet the diverse needs of various businesses and industries. They often include features and functionalities that can be tailored to specific requirements. Customization options may include modifying data structures, creating user-defined fields, defining business rules and workflows, integrating with other systems, and implementing personalized user interfaces. This flexibility allows organizations to adapt the database application to their unique processes, workflows, and data models, enhancing efficiency and supporting their specific business needs. Customization capabilities are crucial for enterprise applications to provide a scalable and adaptable solution that can cater to the evolving requirements of different organizations.
Learn more about features here: brainly.com/question/31541704
#SPJ11
Why must game development team prioritize which bugs must be fixed and which bugs are minor and can remain in the game?
Answers
Answer:
Game development teams prioritize which bugs must be fixed and which bugs are minor and can remain in the game because of several reasons:
Limited Resources: Game development teams have limited resources, including time, budget, and staff. Prioritizing which bugs to fix helps them to allocate their resources more effectively.
Severity of Bugs: Some bugs can cause the game to crash or become unplayable, while others are minor and do not affect gameplay. Prioritizing the most severe bugs helps to ensure that players can enjoy the game without major issues.
Impact on User Experience: Bugs that affect the core gameplay mechanics or prevent players from progressing in the game can have a significant impact on the user experience. Prioritizing these bugs helps to ensure that players can enjoy the game as intended.
Development Cycle: Game development teams often work on tight schedules and deadlines. Prioritizing which bugs to fix helps to ensure that the most critical issues are resolved before the game is released, while less critical issues can be addressed in future updates or patches.
Overall, prioritizing which bugs to fix is an essential part of game development, as it helps to ensure that the game is as enjoyable and functional as possible, given the resources and time available to the development team.
Choose the term that makes the sentence true.
When you enlarge a raster image, the painting program uses ___
to add the needed pixels.
Answers
When you enlarge a raster image, the painting program uses interpolation to add the needed pixels.
What is Interpolation?Interpolation is a technique used by painting programs to add pixels to an image when it is enlarged, by estimating the color values of the new pixels based on the color values of existing pixels.
Hence, it can be seen that when making an image edit and you want to make an enlargement of a raster image, there is the use of interpolation to add the needed pixelation.
Read more about interpolation here:
https://brainly.com/question/18768845
#SPJ1
True or False: selecting the range before you enter data saves time because it confines the movement of the active cell to the selected range.
Answers
True. Selecting the range before you enter data saves time because it confines the movement of the active cell to the selected range.
What is active cell?An active cell, also known as a cell pointer, current cell, or selected cell, is a rectangular box that highlights a cell in a spreadsheet. An active cell makes it clear which cell is being worked on and where data entry will take place.
A spreadsheet cell that has been clicked on becomes the active cell. When a cell is selected, you can type values or a function into it. Most spreadsheet programmes will show the value of the active cell both within the cell itself and within a lengthy text field in the spreadsheet toolbar. The text field is useful for viewing or editing functions as well as for editing lengthy text strings that don't fit in the active cell.
Learn more about active cell
https://brainly.com/question/30511246
#SPJ4
how many megapixels is in a macbook air 2017 camera
Answers
Answer:
.7
Explanation:
Python converts your code into bytecode when you run your program. This process is an intermediate step in a process called.
Answers
Python first compiles your source code (. py file) into a format known as byte code . Compilation is simply a translation step and byte code is a lower level and platform-independent representation of your source code
Python converts your code into bytecode when you run your program. This process is an intermediate step in a process called Compilation.
The line of code returns the ASCII code.
ASCII, has the full form American Standard Code for Information Interchange. It consists of a 7-bit code in which every single bit represents a unique alphabet.
Python is a high-level computer programming language. It is dynamically used.
First, it does a compilation for a file with the extension `.pyc`
Python converts your code into bytecode when you run your program. This process is an intermediate step in a process called Compilation.
Learn more about Python code here:
https://brainly.com/question/34746850.
#SPJ3
a proxy server can be configured to do which of the following? answer restrict users on the inside of a network from getting out to the internet. allow all content except for the content you have identified as restricted. act as a unified threat security device or web security gateway. block all content except for the content you have identified as permissible.
Answers
A proxy server can be configured to act as a unified threat security device or web security gateway.
A proxy server can be used to filter and monitor traffic between a network and the internet, providing an additional layer of security to protect the network from external threats.
This can include blocking access to malicious websites, scanning incoming and outgoing emails for viruses, and enforcing security policies to ensure that users are accessing the internet safely and responsibly.
While a proxy server can be used to restrict users on the inside of a network from accessing certain websites or content, it is not limited to this functionality.
Similarly, a proxy server can be used to block all content except for the content you have identified as permissible, but this is not its primary purpose. The primary function of a proxy server is to act as a security gateway, providing protection against external threats and enforcing security policies to ensure the safety and integrity of the network.
Learn more about proxy server here:
https://brainly.com/question/28075045
#SPJ11
A proxy server can be configured in various ways to provide security to a network. These configurations may include restricting users on the inside of a network from getting out to the internet, allowing all content except for restricted, acting as a unified security device, and blocking all content except permissible inputs.
Explanation:A proxy server is a server that acts as an intermediary for requests from clients seeking resources from other servers, providing a layer of security and improved performance. The functionalities mentioned in your question can indeed be performed by a proxy server. Particularly, a proxy server can indeed be configured to:
Restrict users on the inside of a network from accessing the internet. This is done as part of a network's security strategy.Allow all content except for the content that has been identified as restricted. This is useful in workplaces and schools to prevent access to certain websites.Act as a unified threat security device or web security gateway. In this case, it protects the network from threats on the internet.Block all content except for the content you have identified as permissible. Again, this contributes to the overall network security.Learn more about Proxy Server here:https://brainly.com/question/36416771
YOOO CAN ANYONE SOLVE THIS IN JAVA??
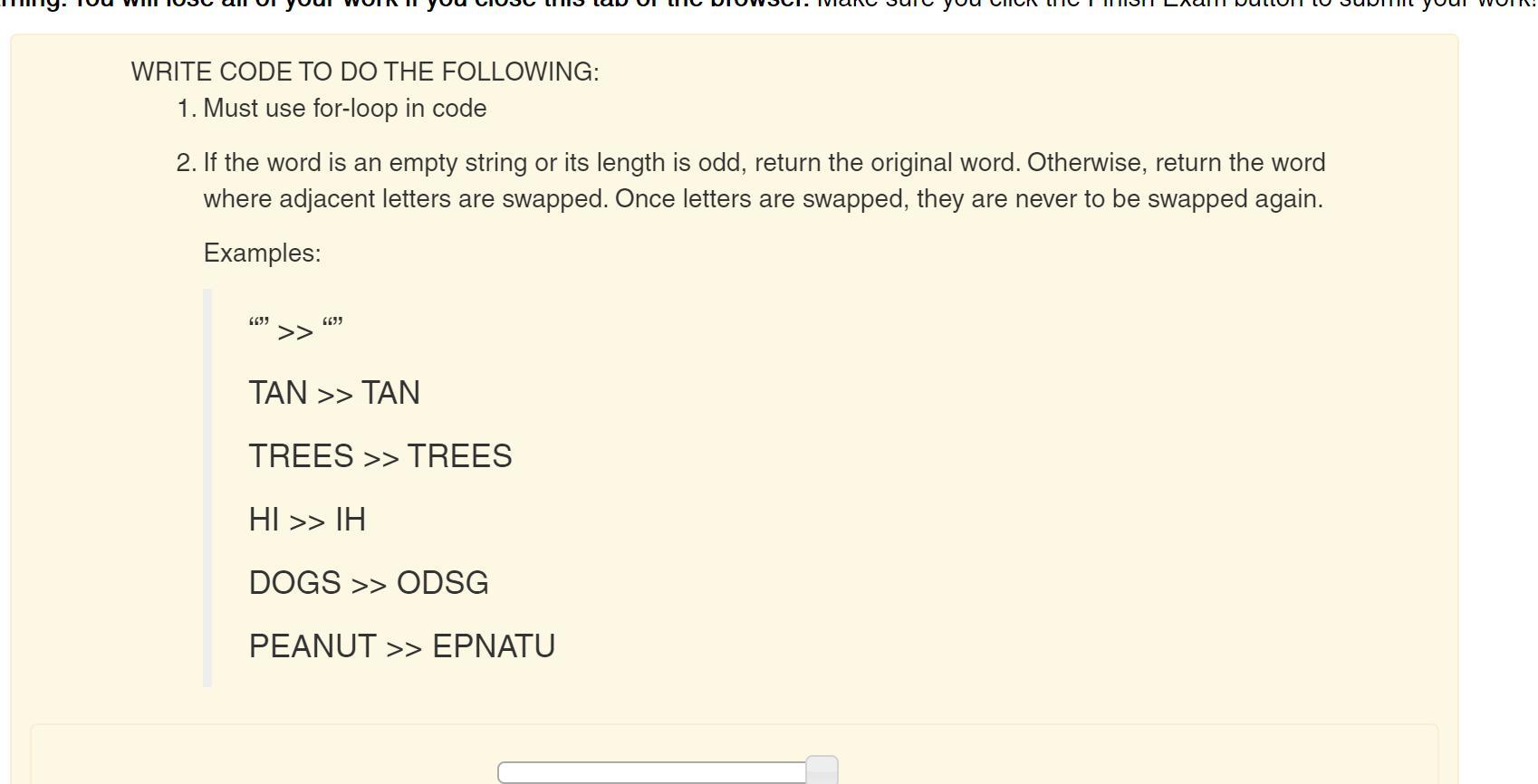
Answers
public class JavaApplication80 {
public static String swapLetters(String word){
char prevC = '_';
String newWord = "";
int count = 0;
if (word.length() % 2 == 1 || word.isBlank()){
return word;
}
else{
for (int i = 0; i<word.length(); i++){
char c = word.charAt(i);
if(count % 2 == 1){
newWord += (c +""+ prevC);
}
prevC = c;
count+=1;
}
}
return newWord;
}
public static void main(String[] args) {
System.out.println(swapLetters("peanut"));
}
}
This works for me. Best of luck.
Answer:
I do not know
Explanation:
Which function would you use to find the oldest date in a range?
a. Min
b. Max
c. Oldest
d. Median
Answers
A range's oldest date is determined via the MIN function. Dates can be expressed as numbers, therefore you can use the MIN function to represent the oldest date and the MAX function to represent the most recent date.
What is meant by MIN function?The MIN function in Excel is a built-in function that locates the lowest integer among a range. Text-filled cells are disregarded by the function. Only cells with numbers will function. Note: The MAX function does the exact opposite of MIN by locating the highest number inside a range. The MIN function examines your data range and delivers the smallest value found there. Let's say we need to get the minimum values and we have data from A2 to B6. We can utilise Excel's MIN function in this situation. The least value within the A2 to B6 cell range may be obtained in this example by applying the MIN function formula =MIN(A2:B6).Therefore,
The earliest date is determined using the formula
=MIN(IF(A2:A26=D2,B2:B26)) in cell E2.
For the most recent date, enter
=MAX(IF(A2:A26=D2,B2:B26)) in cell F2.
To learn more about MIN function, refer to:
https://brainly.com/question/30607138
Here is one way to reduce hazards to human health.Use fewer harmful chemicals,or use chemicals in a more responsible way.
Answers
Answer:
The answer is below
Explanation:
A hazard is an agent that can cause severe damage to the health of people. property or the environment at large when being exposed to the hazard.
Here are some ways in which hazard can be prevented:
Make sure that the required personal protective equipment are worn at all times.Chemicals should be used and disposed in a safe manner.There should be barriers between people and barriers such as radiation.Machines should be used to lift heavy equipment.Which of the following critical-section problem's requirements ensures programs will cooperatively determine what process will next enter its critical section?
Select one:
a. none of the other answers
b. progress
c. bounded waiting
d. mutual exclusion
Answers
The requirement that ensures programs will cooperatively determine what process will next enter its critical section is progress. Therefore option (B) is correct answer.
The progress requirement in the critical-section problem ensures that if no process is currently executing in its critical section and some processes are waiting to enter the critical section, then the selection of the next process to enter the critical section should be made in a fair and orderly manner.
This requirement ensures that all processes have a fair chance of accessing the critical section, preventing any process from being indefinitely delayed or prevented from executing its critical section code. Hence option (B) is correct answer.
Learn more about critical-section problem https://brainly.com/question/33328991
#SPJ11
Does anyone know 7.1.3: Firework karel?
Answers
Answer:
Yess its from freelancer
you have been tasked with running a penetration test on a server. you have been given knowledge about the inner workings of the server. what kind of test will you be performing?
Answers
During the penetration testing process, the target system is actively analyzed for any potential weaknesses that may arise from incorrect or bad system configuration, known and undiscovered hardware or software defects, operational gaps in process, or technical countermeasures.
What constitutes a successful penetration test?During the penetration testing process, the target system is actively analyzed for any potential weaknesses that may arise from incorrect or bad system configuration, known and undiscovered hardware or software defects, operational gaps in process, or technical countermeasures.The appropriate response to the question is all of the aforementioned. The process of assessing a computer program, system, and web service to find defects that could be used for malicious activities is known as penetration testing.The three forms of testing that make up the methodology of penetration testing are called black-box assessment, white-box assessment, and gray-box assessment.To learn more about Penetration testing process refer to:
https://brainly.com/question/13068620
#SPJ4
What are the important points
concerning critical thinking?
(Select all that apply.)
You need to practice the right skills.
You can learn it quickly.
You should use your feelings.
You must evaluate information.
You need to be unbiased and unemotiona
You need to use logic and reason.
You need to be well-spoken.
Answers
The important points to note concerning critical thinking are:
You must evaluate information.You need to be unbiased and unemotional.You need to use logic and reason.You need to be well-spoken.What value do critical thinking abilities have?People that use critical thinking are more able to understand their own objectives, motives, as well as self.
You can alter your circumstances, foster personal development, as well as increase your level of general satisfaction when you can derive knowledge to identify the most crucial components and apply those to your life.
Therefore, based on the above, one can say that the options d, e, f, and g selected are correct.
Learn more about critical thinking from
https://brainly.com/question/25434379
#SPJ1
which regulator publishes hmda data on its website?
Answers
The regulatory agency that publishes HMDA data on its website is the Consumer Financial Protection Bureau (CFPB). HMDA, or the Home Mortgage Disclosure Act, requires certain financial institutions to report data on mortgage applications and loans.
The CFPB collects this data and publishes it annually on their website, making it publicly available for consumers, researchers, and industry professionals to analyze and use for various purposes. In addition to publishing HMDA data, the CFPB also provides tools and resources to help consumers understand and navigate the mortgage lending process. For example, they offer a mortgage glossary, a mortgage calculator, and information on how to file a complaint if a consumer believes they have been treated unfairly by a mortgage lender. The CFPB plays an important role in ensuring that mortgage lending practices are fair and transparent. By publishing HMDA data and providing educational resources, they empower consumers to make informed decisions about their home buying journey and hold lenders accountable for their actions.For such more questions on HMDA
https://brainly.com/question/27941728
#SPJ11
which output will be displayed by the following program?
print(Grade List)
print(100)
print(93)
print(82)
print(Total)
print(100+93+82)
Answers
Answer:SyntaxError: unexpected data type
Explanation:I just took the test and i tried the code in python
:) good luck on the test!!
The output for the given program will be SyntaxError: invalid syntax.
What is invalid syntax?Invalid syntax simply implies that the code one wrote cannot be interpreted as valid Python instructions. "Syntax" called to the rules and structures of a language, both spoken a s well as written.
Python creates syntax errors when it transforms source code to byte code. They usually implies that something is wrong with the program's syntax.
For illustration: The message is redundant when the colon at the end of a def statement is removed. SyntaxError: insufficient syntax.
Here are some examples of Python syntax errors: x, y = myfunction Otherwise, return x + y: print("Hello!") if mark is greater than 50 print("You succeeded!") If you arrive, print("Hi!") print("Bye!") else If flag is set, print("Flag is set!")
Thus, as per the given program, it is not showing proper format of the language so it will be showing SyntaxError.
For more details regarding programming, visit:
https://brainly.com/question/11023419
#SPJ5
The universal serial bus (usb) standard specifies that type b connectors can be attached to?
Answers
The universal serial bus (USB) standard specifies that Type B connectors can be attached to peripheral devices. These peripheral devices include printers, scanners, and external hard drives, among others.
Type B connectors are usually squarish in shape with beveled corners, and they are usually used to connect to larger devices. Type B connectors are typically found on peripheral devices such as printers, scanners, and external hard drives.
They have a square shape with beveled corners and are designed to connect to larger devices. USB cables are used to connect devices to a computer or to other devices, and they are available in several types, including Type A, Type B, Type C, and Mini USB.
To know more about universal serial bus visit :-
https://brainly.com/question/33232346
#SPJ11