Using just excel
show the equation in excel please A bank lent a newly graduated engineer $1,000 at i = 10% per year for 4 years. From the bank's perspective (the lender), the investment in this young engineer is expected to produce an equivalent net cash flow of $315.47 for each of 4 years ▪ Compute the amount of the unrecovered investment for each of the 4 years using the rate of return on the unrecovered balance
Answers
The amount of the unrecovered investment for each of the 4 years using the rate of return on the unrecovered balance are: Year 1: $323.28, Year 2: $337.75, Year 3: $ $338.97 and Year 4: $0.00
In order to compute the amount of the unrecovered investment for each of the 4 years using the rate of return on the unrecovered balance using Excel, the following steps should be taken:
1: Open a blank worksheet and list the following variables:
PV = 1000, nper = 4, pmt = -315.47, rate = 10%/yr.
These variables represent the present value, number of periods, periodic payment, and interest rate per period, respectively.
2: Use the formula for rate of return in Excel to calculate the annual interest rate required to recover the investment. The formula for rate of return is "=RATE(nper, pmt, PV)". The output will be 14.97%.
3: Compute the balance remaining on the loan at the end of each year using the formula for present value of an annuity due in Excel. The formula for the present value of an annuity due is "=PV(rate, nper, pmt, type)" where "type" is set to 1 because payments are made at the beginning of each year.
The balance remaining at the end of each year is the present value of the remaining payments plus the present value of the final payment at the end of the loan term. The calculations for each year are shown below:
Year 1: PV = PV(rate, 3, pmt, 1) + PV(rate, 1, pmt + PV(rate, 3, pmt, 1), 0) = $676.72
Year 2: PV = PV(rate, 2, pmt, 1) + PV(rate, 1, pmt + PV(rate, 2, pmt, 1), 0) = $338.97
Year 3: PV = PV(rate, 1, pmt, 1) + PV(rate, 1, pmt + PV(rate, 1, pmt, 1), 0) = $0.00
Year 4: PV = PV(rate, 0, pmt, 1) = $0.00
Therefore, the amount of the unrecovered investment for each of the 4 years using the rate of return on the unrecovered balance are:
Year 1: $1000 - $676.72 = $323.28
Year 2: $676.72 - $338.97 = $337.75
Year 3: $338.97 - $0.00 = $338.97
Year 4: $0.00 - $0.00 = $0.00
Learn more about investment at:
https://brainly.com/question/32733892
#SPJ11
Related Questions
When code is compiled it?
Answers
Answer:
To transform a program written in a high-level programming language from source code into object code. The first step is to pass the source code through a compiler, which translates the high-level language instructionsinto object code.
Answer: Compiled code is a set of files that must be linked together and with one master list of steps in order for it to run as a program.
Explanation: This is opposed to a interpreted code like web scripts, host server scripts and BASIC that are run one line at a time.
Hope this helps! :)
In addition to the format commands that are found in the ribbon, which option is available for more extensive formatting?
A: Fix Cells dialog box
B: Format Cells dialog box
C: Format dialog box
D: Quick Access tool bar
Answers
Answer:
A
Explanation:
________ requires that a user prove his or her identity for each service invoked and, optionally, requires servers to prove their identity to clients. A. FIM B. Kerberos C. X.509 D. PKI
Answers
Option a is correct. Prior to the CA providing a certificate or certificates for an end entity, the end entity must first register or be certified in order to be recognized by the CA.
Authentication is the process of entering a system, while two-factor authentication is the process of entering a token to enter a system. Server identity and trust are established and verified using private keys, digital certificates, and trusted certificate authorities. Public key encryption method is used by SSL for authentication. A public key and a private key are generated for a server when using public key encryption. Unmistakably connected to this certificate is an integer value that is distinct within the CA (Certification Authority) that issued it. Identification of the algorithm that signed the certificate, along with any additional parameters.
Learn more about server here-
https://brainly.com/question/3211240
#SPJ4
what are the answers for theses question?




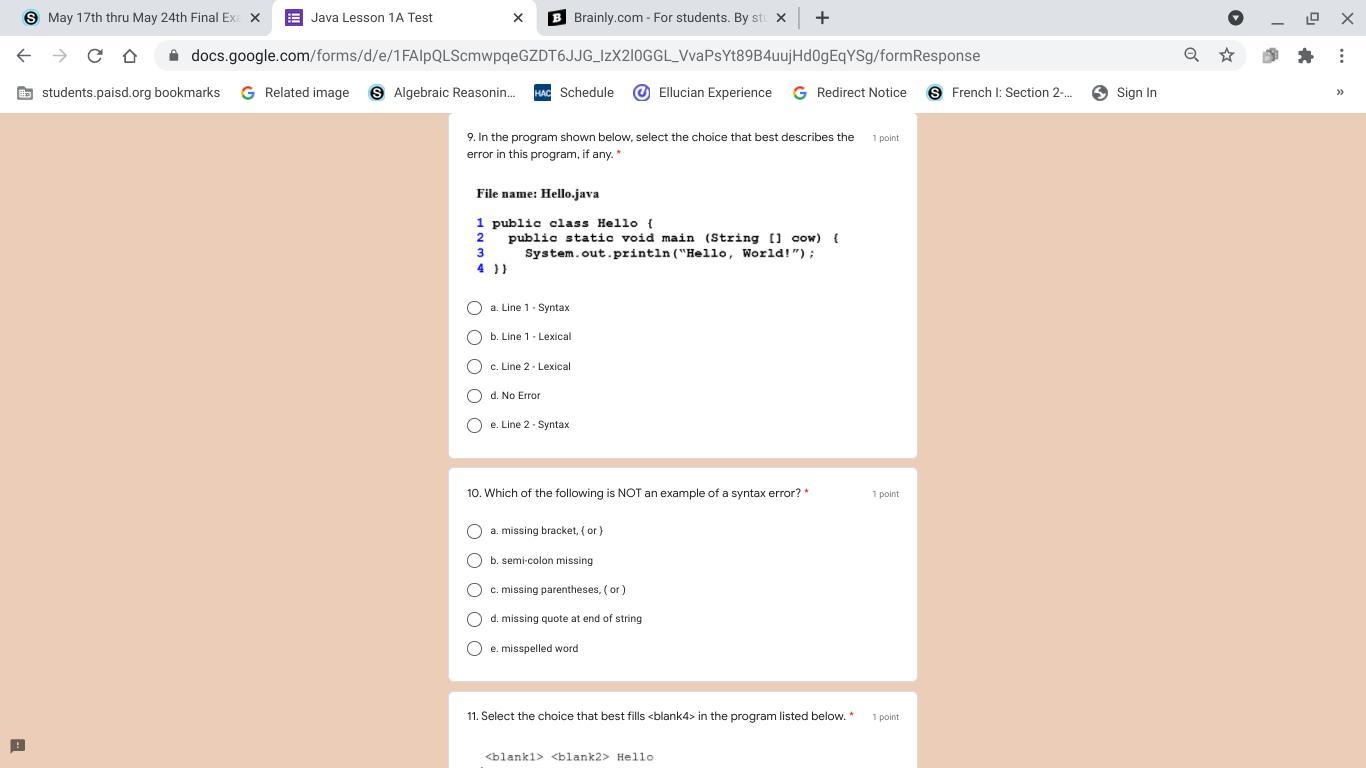
Answers
Answer: me no comprende coding
Explanation:
sorry
Would be easier to divide/fold a rectangular sheet of paper into 22 equal pieces or 24 equal pieces? Explain your answer. Please help !!!!!
Answers
Answer:
24 equal.
Explanation:
What are inserted to show the total number of pages in Word?
Answers
Answer:
Include total number of pages in the page number
Go to Insert > Page Number.
Do one of the following: Select Current Position if you have a header or footer. Select a location if you have no header or footer yet.
Scroll until you see Page X of Y and select a format.
Select Close Header and Footer, or double-click anywhere outside the header or footer area.
Before using an advanced filter, you must first set up a(n) ________.
(Microsoft Excel)
A. Structured Range
B. AutoFilter
C. Slicer
D. Criteria Range
Answers
This option, in Profiles, is used to alert users that the person or company associated with the Profile should be denied access. Routing Restricted Contact Notifications
Answers
The option, in Profiles, that is used to alert users that the person or company associated with the Profile should be denied access is called Restricted.
What is a profile?A profile is a concise representation of a person or an organization. Profiles are used to provide information to others about the person or company. Profiles can be found on social media websites as well as on other websites that enable people to create profiles and share information.
What is Restricted?Restricted is a function available in many online profiles. When a person is placed on your restricted list, they will be unable to see any posts that are set to friends-only or public.
Learn more about information here: https://brainly.com/question/27847789
#SPJ11
To address cybercrime at the global level, _____. Select 2 options.
A. the private sector and law enforcement need to work separately
B. international treaties need to be created and updated
C. standardized processes need to be prevented to promote innovation
D. international treaties need to be less stringent or eliminated
E. there needs to be more investment in cybercrime investigations
Answers
To address cyber crime at the global level:
B. International treaties need to be created and updated.E. There needs to be more investment in cybercrime investigations.What is cyber crime?Cybercrime refers to criminal activities committed using the Internet or other forms of computer networks. Examples include hacking, identity theft, online fraud, cyberstalking, cyberbullying, and the spread of malware or viruses.
Cybercrime can cause harm to individuals, businesses, and even governments, and can have serious consequences for the victims.
Learn more about cyber crime at:
https://brainly.com/question/25157310
#SPJ1
What is the dark, sticky substance that forms when tobacco is burned?
Answers
Answer: Tar.
Explanation:
A chemical substance made when tobacco is burned. Tar contains most of the cancer-causing and other harmful chemicals found in tobacco smoke. When tobacco smoke is inhaled, the tar can form a sticky layer on the inside of the lungs.
Write down the 8th (start from the left hand side) digit and the LAST digit of your student ID as A1 and A0 respectively. Make these two digits into a new number N that has double digits. For example, a student’s student ID is 2012521460204,then the decimal N=44. Then, answer the following SIX questions.
(a) Suppose N is a decimal number, convert (N)10 to its equivalent binary.
(b) Suppose N is a hexdecimal number, convert (N)16 to its equivalent binary.
Answers
Given that, A1 is the 8th digit from the left-hand side and A0 is the last digit of the student ID.So, the student ID is 201526204, then A1 = 5 and A0 = 4 (A) Binary of (N)10 = (110110)2, (B) Binary of (N)16 = (1010100)2.
(A) The given student ID is 201526204
Here, A1 = 5 and A0 = 4N = 54
Binary of (N)10 = (110110)2
Let's write the given number 54 in the powers of 2.64 32 16 8 4 2 1 1 1 0 1 1 0 1 0
So, (N)10 = (110110)2
Binary of (N)16 = (1010100)2
(B) The hexadecimal number is given by 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, A, B, C, D, E, F where A represents 10, B represents 11, C represents 12, D represents 13, E represents 14 and F represents 15.
To convert any hexadecimal to binary, we just need to replace each hexadecimal digit with its corresponding 4-digit binary number.
Hence, the hexadecimal number
(N)16 = 54(decimal) = 36(hexadecimal).
So, (N)16 = (00110110)2 = (1010100)2.
To know more about binary number refer for :
https://brainly.com/question/33282516
#SPJ11
Help please! i don’t know how to do this.
H2 should be:
-Blue
-Times New Roman or Arial
-Align to the right
2. Strong should be:
-Teal
-32pt
-Boldness of 700
3. P should be:
-All in uppercase
-Overlined
-Word space of 10em

Answers
Answer:
Make sure to create and link a css file with the following:
<link rel="stylesheet" href="./styles.css">
In your css file, enter these styles:
h2 {
color: blue;
font-family: 'Times New Roman', Times, serif;
text-align: right;
}
strong {
color: teal;
font-size: 32pt;
font-weight: 700;
}
p {
text-transform: uppercase;
text-decoration: overline;
word-spacing: 10em;
}
Explanation:
In order for the html file to know where your styles are located, you have to link it to the css file with the code given above. In this file, you will enter some css to change the styles of the elements you have created in your html file.
To alter the style of an element, you first have to enter the name of the element itself, its class or its id. In this case, we have used the element itself, meaning that all the same elements in the html file will have the same style. The styles you wish to use are entered in between the curly brackets.
In your specific problem, we are trying to change the h2, strong and p elements, so that is what we have done. For the h2, you wanted it blue, therefore we use the color property to change the color. For the font, we use the font-family and finally we use text-align to align it to the right. The same pretty much applies for the other two elements. Your strong element needs to be teal,32pt and 700 bold. Therefore we use the color, font-size and font-weight properties respectively. And finally for the p element, we will use the text-transform, text-decoration and word-spacing properties respectively.
When you dont know the name of the property you want to change, I suggest googling it. You will definitely find the property name you are looking for. W3schools.com is a good source to use.
your organization has decided to use dhcp for ipv6. you want all windows 10 systems using ipv6 to get all of their tcp/ip information through dhcp. how would you set up the network?
Answers
your organization has decided to use dhcp for ipv6. you want all windows 10 systems using ipv6 to get all of their tcp/ip information through dhcp. By setting up a Stateful network would you set up the network .
Why is DHCP utilized and what does it do?
Network devices are set up to communicate on an IP network using the Dynamic Host Configuration Protocol (DHCP).
A DHCP client utilizes the DHCP protocol to request configuration data from a DHCP server, including an IP address, a default route, and one or more DNS server addresses.
What are DHCP and DNS?
It is possible to translate domain names (like its.umich.edu) into IP addresses using the Domain Name System (DNS) on the Internet.
In order to automatically assign IP addresses and other parameters to devices when they connect to a network, there is a mechanism called Dynamic Host Configuration Protocol (DHCP).
Learn more about DHCP Server .
brainly.com/question/29432103
#SPJ4
I Have a Kodak pixpro camera and I put my memory card in (sandisk) but it keeps on saying "card is not formatted" then it gives me the option of "format" "doing so will clear all data" "yes or no" but i barely bought the memory card and the camera , so What do i do ? I never used the camera or the memory card . (PLEASE HELP )
Answers
If you've never used the camera, and you're fairly certain there aren't any pictures on the memory device, then it's safe to format the disk so that you set up the table of contents properly. That way the computer can read the data in the right sectors and so on. I would choose the option "yes" and follow the instructions on the screen. It should lead you to a blank disk so you can then fill it up with future pictures down the road.
If you think there are pictures on the card and you want to retrieve them, then try putting the card into a different memory reader and see if the same message pops up. Chances are there are slightly different formats that aren't being compatible in some way if this is the case.
2. Xamarin.Forms is a UI toolkit to develop the application. A. TRUE B. FALSE C. Can be true or false D. Can not say
Answers
The statement "Xamarin.Forms is a UI toolkit to develop the application" is true because Xamarin.Forms is indeed a UI toolkit used for developing applications. Option a is correct.
Xamarin.Forms is a cross-platform UI toolkit provided by Microsoft that allows developers to create user interfaces for mobile, desktop, and web applications using a single codebase. It provides a set of controls and layouts that can be used to create visually appealing and responsive user interfaces across different platforms, including iOS, Android, and Windows.
With Xamarin.Forms, developers can write their UI code once and deploy it to multiple platforms, reducing the effort and time required to develop and maintain applications for different operating systems.
Option a is correct.
Learn more about developers https://brainly.com/question/19837091
#SPJ11
Why is quantum computing potentially a better fit for weather forecasting than classical computers?.
Answers
The reason why quantum computing is potentially a better fit for weather forecasting than classical computers is that It can perform advanced simulations more efficiently.
What is quantum computing?Quantum computing is known to be a kind of technologies that is known to be futurists in nature.
Quantum computers is one that is seen to have the power to quickly process a lot of high numbers of quantities of weather data and carry out analysis that are said to be too complex for classical computers.
Hence, The reason why quantum computing is potentially a better fit for weather forecasting than classical computers is that It can perform advanced simulations more efficiently.
See full question below
Why is quantum computing potentially a better fit for weather forecasting than classical computers?
It can perform advanced simulations more efficiently.
It can be easily installed at locations around the globe.
It can function efficiently when stored at high temperatures.
It can store extensive data for better pattern recognition.
Learn more about quantum computing from
https://brainly.com/question/25513082
#SPJ1
ReadWorks.org
Assignments
Johnny's First Job
Answers
Answer:
reading and the gathered up to be in a Philippine language pilipino and see what they said it will send it s dark blue in a Philippine area is not what pic and I are going well with your grade now just need help now need help
Liam noticed someone had accessed his social media account and made several posts without his knowledge. Which of the following practices will keep unauthorized users from gaining access to his online accounts?
Answers
Answer:
Liam could, Change the password,
Explanation:
change the password, so the password would be difficult to guess.
Avoid logging onto social media on public computers or WiFi connections.
Don't giving out account information to friends and avoid opening suspicious links and emails.
DON:T opening suspicious links or emails could allow malware to infect your computer the moment you open them.
HOpe this HelPed
which of the following are acceptable in java, and doesn't cause a compile error?
group of answer choices
int[1][2] nums = {{1}, {1, 2}};
int[][] nums = new int[3][1];
int[1][2] nums = new int[][];
int[][] nums = new int[3][];
int[][] nums = {{1}, {1, 2}};
Answers
The number itself serves as the number's basis integer and is located before the exponent. The smaller number printed above and to the right of the base is the exponent.
The Java phrase "a[a.length] = 10;" is incorrect because, in many programming languages, including Java, array indexing starts at 0 and ends at (length-1). Therefore, an ArrayIndexOutOfBoundsException is thrown during runtime if an attempt is made to get the element that already exists at index a.length but that is outside the scope of this array.
1. int[][] nums = new int[3][1];
2. int[][] nums = new int[3][];
3. int[][] nums = {{1}, {1, 2}};
Therefore, it is crucial to use the correct syntax: "a[a.length-1] = 10;" to assign the value integer 10 to the closing/terminal entity a within the array. By subtracting 1 from the length of the given array overall, the user would be able to access the last item in the array and find where it is located using this method.
The base value is multiplied by itself that many times when the exponent is positive. Based on the given options, the following are acceptable in Java and don't cause a compile error:
Learn more about integer here
https://brainly.com/question/31640857
#SPJ11
what would you do if you got exposed on social media and (depression) who feels like that sometimes ?
Answers
Answer:
Sadness
Explanation:
Because i sad or mad
Answer:
nothing
Explanation:
i wouldn't get the app
Companies such as ORACLE, Amazon Web Services, and Microsoft offer courses to learn about their technologies.
Answers
Answer:
True?
Explanation:
Outline the dangers arising as a result of using computers
Answers
Answer:
Visual impairment
Physical Health problem
Explanation:
The benefits of computers are so numerous a d has been an essential business and educational tool every organization must possess for one purpose or the other. Such is how immense its importance is. However, the computer also comes with it's own risk, which may include :
Visual impairment is a major problem most computer users face or will likely encounter in the future due to prolonged exposure of the eyes to the light emanating from the screen. This visual challenge is populary called the. Computer Vision Syndrome.
Similarly, related health related issues affecting the physical body such as the back, hip, neck pains which result from postural position when using the computer.
PLS IM GOOFY HELPPPP:
Antony is working and going to school, plus he spends a lot of time commuting on the train in between the two. What would be the BEST type of equipment for him to use for typing?
Question 8 options:
A an electric typewriter
B a laptop
C a desktop computer
D a manual typewriter
Answers
B. Laptop
have a great day!! hope this helps
the ____ is a temporary storage area that holds items copied from any office program.
Answers
Answer:
Clipboard
Explanation:
PLEASE HELP
Which option is the correct format of placing HTML tags while coding in HTML?
A.
B.
C.
D.
Answers
Answer:
the 3rd one you put
Explanation:
the volume of two similar solids are 1080cm and 1715cm .if the curved surface area of the smaller cone is 840cm .fond the curved surface area of the larger cone
Answers
Answer:
\(A_{big} = 1143.33cm^2\)
Explanation:
The given parameters are:
\(V_{small} = 1080\)
\(V_{big} = 1715\)
\(C_{small} = 840\)
Required
Determine the curved surface area of the big cone
The volume of a cone is:
\(V = \frac{1}{3}\pi r^2h\)
For the big cone:
\(V_{big} = \frac{1}{3}\pi R^2H\)
Where
R = radius of the big cone and H = height of the big cone
For the small cone:
\(V_{small} = \frac{1}{3}\pi r^2h\)
Where
r = radius of the small cone and H = height of the small cone
Because both cones are similar, then:
\(\frac{H}{h} = \frac{R}{r}\)
and
\(\frac{V_{big}}{V_{small}} = \frac{\frac{1}{3}\pi R^2H}{\frac{1}{3}\pi r^2h}\)
\(\frac{V_{big}}{V_{small}} = \frac{R^2H}{r^2h}\)
Substitute values for Vbig and Vsmall
\(\frac{1715}{1080} = \frac{R^2H}{r^2h}\)
Recall that:\(\frac{H}{h} = \frac{R}{r}\)
So, we have:
\(\frac{1715}{1080} = \frac{R^2*R}{r^2*r}\)
\(\frac{1715}{1080} = \frac{R^3}{r^3}\)
Take cube roots of both sides
\(\sqrt[3]{\frac{1715}{1080}} = \frac{R}{r}\)
Factorize
\(\sqrt[3]{\frac{343*5}{216*5}} = \frac{R}{r}\)
\(\sqrt[3]{\frac{343}{216}} = \frac{R}{r}\)
\(\frac{7}{6} = \frac{R}{r}\)
The curved surface area is calculated as:
\(Area = \pi rl\)
Where
\(l = slant\ height\)
For the big cone:
\(A_{big} = \pi RL\)
For the small cone
\(A_{small} = \pi rl\)
Because both cones are similar, then:
\(\frac{L}{l} = \frac{R}{r}\)
and
\(\frac{A_{big}}{A_{small}} = \frac{\pi RL}{\pi rl}\)
\(\frac{A_{big}}{A_{small}} = \frac{RL}{rl}\)
This gives:
\(\frac{A_{big}}{A_{small}} = \frac{R}{r} * \frac{L}{l}\)
Recall that:
\(\frac{L}{l} = \frac{R}{r}\)
So, we have:
\(\frac{A_{big}}{A_{small}} = \frac{R}{r} * \frac{R}{r}\)
\(\frac{A_{big}}{A_{small}} = (\frac{R}{r})^2\)
Make \(A_{big}\) the subject
\(A_{big} = (\frac{R}{r})^2 * A_{small}\)
Substitute values for \(\frac{R}{r}\) and \(A_{small}\)
\(A_{big} = (\frac{7}{6})^2 * 840\)
\(A_{big} = \frac{49}{36} * 840\)
\(A_{big} = \frac{49* 840}{36}\)
\(A_{big} = 1143.33cm^2\)
Hence, the curved surface area of the big cone is 1143.33cm^2
Review the items below to make sure that your Python project file is complete. After you have finished reviewing your turtle_says_hello.py assignment, upload it to your instructor.
1. Make sure your turtle_says_hello.py program does these things, in this order:
Shows correct syntax in the drawL() function definition. The first 20 lines of the program should match the example code.
Answers
Code defines the drawL() function with the correct syntax and includes the required documentation string. The function takes a turtle object 't' as an argument, and draws an L shape using turtle graphics.
Define the term syntax.
In computer programming, syntax refers to the set of rules that dictate the correct structure and format of code written in a particular programming language. These rules define how instructions and expressions must be written in order to be recognized and executed by the computer.
Syntax encompasses a wide range of elements, including keywords, operators, punctuation, identifiers, and data types, among others. It specifies how these elements can be combined to form valid statements and expressions, and how they must be separated and formatted within the code.
To ensure that your turtle_says_hello.py program meets the requirement of having correct syntax in the drawL() function definition, you can use the following code as an example:
import turtle
def drawL(t):
"""
Draws an L shape using turtle graphics.
t: Turtle object
"""
t.forward(100)
t.left(90)
t.forward(50)
t.right(90)
t.forward(100)
To ensure that your turtle_says_hello.py program is complete and correct.
1. Make sure that your program runs without errors. You can do this by running your program and verifying that it executes as expected.
2. Check that your program follows the instructions provided in the assignment. Your program should start by importing the turtle module, creating a turtle object, and define the drawL() function.
3. Verify that your drawL() function works as expected. The function should draw an "L" shape using turtle graphics. You can test this by calling the function and verifying that it draws the expected shape.
4. Ensure that your program ends by calling the turtle.done() function. This will keep the turtle window open until you manually close it.
5. Make sure that your code is properly formatted and indented. This will make it easier for others to read and understand your code.
6. Finally, ensure that your program meets any other requirements specified in the assignment. This might include things like adding comments or following a specific naming convention.
Therefore, Once you have verified that your program meets all of these requirements, you can upload it to your instructor for review.
To learn more about syntax click here
https://brainly.com/question/18362095
#SPJ1
A way for developers to avoid bias in their computational artifacts is to
identify solutions to bias in software
increase universal access to bias
refine their computational artifacts
use the various forms of bias and inequity
test their software for inequity and bi
Select 3 option
Answers
The computational techniques are discussed with an emphasis on real-world flow control simulations for flying vehicles.
Thus, The unstable Reynolds-averaged Navier-Stokes formulation is used in one approach, and the lattice Boltzmann method is used in the vehicles. The modeling of a number of flow-control strategies and the creation of new actuation systems both make use of special boundary techniques.
The findings of research projects that used computer simulations to address a wide range of aerodynamic and propulsion flow issues are given.
In order to accomplish a goal, the flow-control techniques are utilized to manipulate vortical flow structures and control flow separation. As a result, commercial and military flow-control implementations for airplanes and rotorcraft have been made.
Thus, The computational techniques are discussed with an emphasis on real-world flow control simulations for flying vehicles.
Learn more about Computer, refer to the link:
https://brainly.com/question/31727140
#SPJ1
Which example best illustrates a way that abstraction has made computers easier to use? a: you plan which clothes and other items you want to pack for an trip. b: you call your doctor office and scheduled an appointment for an exam. c: you wake up in the morning, eat breakfast, and then brushed your teeth. d: you watch an funny video on tomtom and then share it with an friend. answer: d
Answers
The example that best illustrates a way that abstraction has made computers easier to use is option d: watching a funny video on TomTom and then sharing it with a friend. Abstraction in this case refers to the simplification of complex processes and hiding unnecessary details, allowing users to easily navigate and interact with computer systems.
What is a user data?
Answers
Answer: Any data the user creates or owns.
Explanation:
the user being the one on the otherside of the computer, usually a human.
but examples of user data are intalled programs, uploads, word documents created by user (computer user)