True or False: You can apply transitions to titles to fade them up or move them on or off the screen.
Answers
The statement "You can apply transitions to titles to fade them up or move them on or off the screen." is true because titles in Adobe Premiere Pro can have transitions applied to them.
Transitions in video editing refer to the visual effects that occur between two adjacent clips. They can be used to indicate the passage of time or to provide a smooth flow between two different shots. Adobe Premiere Pro allows users to apply a wide range of transitions, such as crossfades, wipes, and dissolves, to their video projects. Additionally, users can customize the duration, direction, and other settings of these transitions to create unique visual effects that enhance the overall quality of their videos.
You can learn more about Adobe Premiere Pro at
https://brainly.com/question/31319258
#SPJ11
Related Questions
What does search engine optimization (SEO) do?
A.
helps in tracking changes in progress
B.
tries to improve the ranking in user searches
C.
tries setting quality benchmarks
D.
makes navigation easier for the visitor
Answers
Answer:
B. tries to improve the ranking in user searches
Explanation:
Search engine optimization (SEO) can be defined as a strategic process which typically involves improving and maximizing the quantity and quality of the number of visitors (website traffics) to a particular website by making it appear topmost among the list of results from a search engine such as Goo-gle, Bing, Yah-oo etc.
This ultimately implies that, search engine optimization (SEO) helps individuals and business firms to maximize the amount of traffic generated by their website i.e strategically placing their website at the top of the results returned by a search engine through the use of algorithms, keywords and phrases, hierarchy, website updates etc.
Hence, search engine optimization (SEO) tries to improve the ranking in user searches by simply increasing the probability (chances) of a specific website emerging at the top of a web search.
How can you make the drawing tools contextual tab appear
Answers
Answer:
C. place the insertion point in any text in the text box.
Typically, the Ribbon contains the Draw tab. Here's how to add it, though, if you can't see it on yours. Customize the ribbon by selecting it with the right mouse click. Click OK after selecting the checkbox next to draw. Thus, option C is correct.
What make the drawing tools contextual tab appear?If your Draw Tools are hidden, you can reveal them by bringing up the View menu, selecting Toolbars, and then selecting Drawing. Look at the Draw Tools' features for a bit.
When you click outside these objects, the tools in the contextual tabs are put away, giving you the options and resources you need to deal with them.
Clicking on the item causes the tab to reappear, and you can get them back. Your workspace remains uncluttered as a result.
Therefore, place the insertion point in any text in the text box.
Learn more contextual tab about here:
https://brainly.com/question/14139335
#SPJ2
the e site may not require codon recognition. why?
Answers
The E site (Exit site) in the ribosome does not require codon recognition as its primary function is to release the tRNA after the amino acids have been added to the growing polypeptide chain.
The E site may not require codon recognition is because once the tRNA has delivered its amino acid to the protein chain, its role is complete and it can be released from the ribosome. The E site simply serves as a docking station for the tRNA molecule before it is released back into the cytoplasm to be recharged with another amino acid.
The A site (Aminoacyl-tRNA site), the P site (Peptidyl-tRNA site), and the E site (Exit site). The A site is responsible for codon recognition and binding the incoming aminoacyl-tRNA. The P site is where the peptide bond forms between the amino acids.
To k now more about Codon visit:-
https://brainly.com/question/31118854
#SPJ11
PLZZZZZZZZZZZZZZZ HELP ME OUT!!!!! I SICK AND TIRED OF PEOPLE SKIPING MY QUESTION WHICH IS DUE TODAY!!!!
Directions
Read the dilemma below and then complete the Feelings & Options steps.
"Missing Out"
Text:
For months, Aida and her three closest friends had been waiting for a new movie to come out. The movie was based on one of their favorite books, and they promised they would see it all together and then go out for pizza. On the movie's opening weekend, Aida had a last-minute emergency and wasn't able to go. The others decided to go anyway because they had really been looking forward to it. That night they posted constantly about their fun and new inside jokes. Aida wanted to keep connected, but seeing the constant posts bummed her out. She felt like no one even cared that she had missed out on their plans.
Identify: Who are the different people involved in the scenario? What dilemma or challenge are they facing?
Answers
Answer:
One friend being nice and the other being rude, thats a dillema.
Explanation:
Because its logical
Which term describes a protocol to manage a network, able to configure a network, monitor activity, and control devices?
Post Office Protocol version 3 (POP 3)
Simple Mail Transfer Protocol (SMTP)
Internet Message Access Protocol (IMAP)
Simple Network Management Protocol (SNMP)
Answers
Answer:
Simple Network Management Protocol (SNMP)
Explanation:
Answer:
SNMP
Explanation:
vote brainliest please.
hy does payments constitute such a large fraction of the FinTech industry? (b) Many FinTech firms have succeeded by providing financial services with superior user interfaces than the software provided by incumbents. Why has this strategy worked so well? (c) What factors would you consider when determining whether an area of FinTech is likely to tend towards uncompetitive market structures, such as monopoly or oligopoly?
Answers
(a) lengthy and complex processes for making payments (b) legacy systems and complex interfaces (c) regulatory requirements and substantial initial investment, can limit competition
(a) Payments constitute a significant portion of the FinTech industry due to several factors. First, traditional banking systems often involve lengthy and complex processes for making payments, leading to inefficiencies and higher costs. FinTech firms leverage technology and innovative solutions to streamline payment processes, providing faster, more secure, and convenient payment options to individuals and businesses. Additionally, the rise of e-commerce and digital transactions has increased the demand for digital payment solutions, creating a fertile ground for FinTech companies to cater to this growing market. The ability to offer competitive pricing, improved accessibility, and enhanced user experience has further fueled the growth of FinTech payment solutions.
(b) FinTech firms have succeeded by providing financial services with superior user interfaces compared to incumbents for several reasons. Firstly, traditional financial institutions often have legacy systems and complex interfaces that can be challenging for users to navigate. FinTech companies capitalize on this opportunity by designing user-friendly interfaces that are intuitive, visually appealing, and provide a seamless user experience. By prioritizing simplicity, convenience, and accessibility, FinTech firms attract and retain customers who value efficiency and ease of use. Moreover, FinTech companies leverage technological advancements such as mobile applications and digital platforms, allowing users to access financial services anytime, anywhere, further enhancing the user experience.
(c) Several factors contribute to the likelihood of an area of FinTech tending towards uncompetitive market structures such as monopoly or oligopoly. Firstly, high barriers to entry, including regulatory requirements and substantial initial investment, can limit competition, allowing a few dominant players to establish market control. Additionally, network effects play a significant role, where the value of a FinTech service increases as more users adopt it, creating a competitive advantage for early entrants and making it challenging for new players to gain traction. Moreover, data access and control can also contribute to market concentration, as companies with vast amounts of user data can leverage it to improve their services and create barriers for potential competitors. Lastly, the presence of strong brand recognition and customer loyalty towards established FinTech firms can further solidify their market position, making it difficult for new entrants to gain market share.
To learn more about technology click here: brainly.com/question/9171028
#SPJ11
How will an older browser display a blue box which has been made semi-transparent using CSS 3 opacity?
Answers
An older browser will display the blue box with full opacity, ignoring the CSS3 opacity property.
Cascading Style Sheets Level 3 (CSS3) is the iteration of the CSS standard used in the styling and formatting of Web pages. CSS3 incorporates the CSS2 standard with some changes and improvements.
The opacity property sets the opacity level for an element. CSS 3 opacity property is not supported by older browsers. When opacity is set to a value less than 1, modern browsers apply alpha blending to create a semi-transparent effect.
However, older browsers do not understand this property and treat it as if it doesn't exist. Consequently, the blue box will be displayed at full opacity, without any transparency effect.
When using CSS 3 opacity on an older browser, the blue box will not appear semi-transparent but will be fully opaque, as the opacity property is not recognized by older browser versions. It is important to consider browser compatibility when using CSS properties to ensure consistent rendering across different platforms and versions.
Learn more about CSS3 here:
brainly.com/question/32156289
#SPJ11
you manage a windows server. for the d:\reports\finances.xls file you explicitly grant the mary user account the allow modify ntfs permissions. you need to move the file from the existing folder to the d:\confidential folder. you want to keep the existing ntfs permissions on the file. you want to accomplish this with the least amount of effort possible. what should you do?
Answers
This will paste the file from the clipboard to the D:\Confidential folder. The file will be moved to the D:\Confidential folder with the same permissions as in the original location.
You need to simply move the file from the existing folder to the D:\Confidential folder without modifying the existing permissions on it. It is possible to keep the existing ntfs permissions on the file while moving it from the existing folder to the D:\Confidential folder. It is simple to accomplish this with the least amount of effort possible without modifying the existing permissions on the file. What should you do to accomplish this You must perform the following procedure to move the file from the existing folder to the D:\Confidential folder without modifying the existing permissions on it Firstly, locate the file that you want to move, which is D:\Reports\Finances.xls.Secondly, right-click on the file, and select Copy from the context menu. The file will be copied to the clipboard.Thirdly, open the D:\Confidential folder where you want to place the file, and right-click on it. Select the Paste option from the context menu.
learn here about Confidential folder here:
https://brainly.com/question/29588297
#SPJ11
The type value ____ for the input element may cause modern browsers to validate entries to ensure that they are valid web addresses.
Answers
Answer:
url
Explanation:
A cpu converts the data entered through the keyboard into output displayed on the monitor. True or false?.
Answers
A CPU converts the data entered through the keyboard into output displayed on the monitor. True.
What is a computer?A computer can be defined as an electronic device that is designed and developed to receive data in its raw form as an input and processes these data through the central processing unit (CPU) into an output (information) that could be used by an end user.
What is a CPU?CPU is an abbreviation for central processing unit and it can be defined as the main components of a computer because it acts as the “brain” of a computer and does all the processing, calculations, and logical control.
This ultimately implies that, the central processing unit (CPU) performs most of the calculations, which enables a computer to function and is sometimes referred to as the “brain” of the computer.
Read more on CPU here: brainly.com/question/5430107
#SPJ1
is an impact printer makes contact with the paper.
Answers
Answer:
Yes
Explanation:
because the name impact
GoPro is a company that makes high-definition waterproof cameras. Their primarycommunication strategy is letting users provide some of the content and dominatediscussions. In this case, sharing media means GoPro is _____________.
Answers
In this case, sharing media means GoPro is engaging in user-generated content (UGC).
User-generated content (UGC) is media content generated by users. As compared to mainstream media, the UGC includes photographs, videos, and written material that are created by users on social media platforms.What is the marketing strategy of GoPro?GoPro is a camera manufacturer that sells sports cameras, drones, and other accessories. The primary marketing strategy of GoPro is centered on user-generated content (UGC). GoPro is well-known for its extreme sports and adventure-themed footage. They use user-generated content to promote their brand by providing incentives for users to upload and share their images and videos through their website, social media, and other platforms.
Learn more about GoPro: https://brainly.com/question/5880614
#SPJ11
Fill in the blanks to output "I love
Python".
Answers
Answer:
print("I love Python")
Explanation:
Elementary, my dear Watson.
Which of the variables have the value 50 after executing the code segment?
see the image below for reference
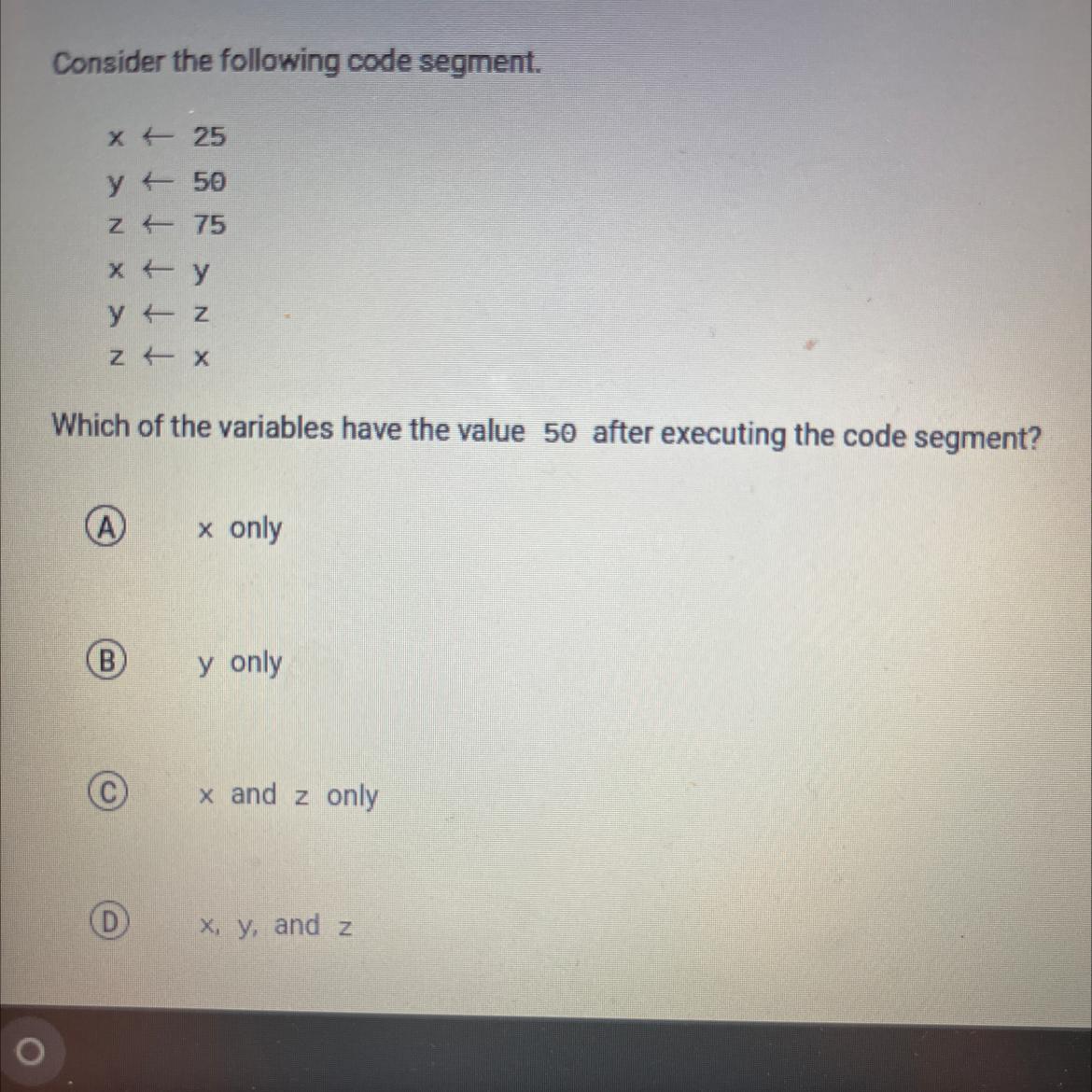
Answers
The segment of code that will have the value of 50 after executing the code segment is this:
C. X and Z only
What is the segment?A segment is a section of code that instructs the computer to take certain actions. In the above code, we can see that the y value is set to return the value of 50.
Also, in the fourth instruction, the x value is instructed to return the value of y. So, the segment of code that is meant to execute and return the number, 50 is option c which contains x and z.
Learn more about coding here:
https://brainly.com/question/22654163
#SPJ1
Why do cooler substances have a tendency to sink?
Answers
Answer:
Explanation:
the molecules to slow down and they get closer to together.
:)
Convection happens in fluids (liquids & gases). The heat energy moves through the material as the particles in the material move through the material.
Hot liquids and gases rise because when they are heated they expand and become less dense. The less dense warm liquid or gas then floats up through the more dense cold liquids and gases.
Cold liquids and gases sink because when cooled they contract and become more dense. The more dense cold liquids and gases sink down through the less dense warm liquids and gases.
These changes in density cause the convection currents in the liquid or gas.

those services undertaken to prepare the organization or the csirt constituents to protect and secure systems in anticipation of problems, attacks, or other events are called ____.
Answers
The services undertaken to prepare an organization or CSIRT constituents to protect and secure systems in anticipation of problems, attacks, or other events are called proactive security measures.
Proactive security measures encompass a range of activities aimed at preventing and mitigating potential security threats before they occur. These services involve strategic planning, risk assessment, and the implementation of various preventive measures.
To begin with, proactive security measures involve conducting comprehensive risk assessments to identify vulnerabilities and potential threats to the organization's systems. This assessment helps in understanding the current security posture and assists in developing a robust security strategy. Based on the identified risks, organizations can implement measures such as regular system patching and updates, network segmentation, and strong access controls to proactively strengthen their security.
Furthermore, organizations can engage in security awareness training programs to educate employees about potential risks and best practices for maintaining a secure environment. This includes training on identifying phishing attempts, practicing good password hygiene, and adhering to security policies and procedures.
Additionally, implementing intrusion detection and prevention systems, conducting vulnerability assessments, and establishing incident response plans are essential proactive security measures. These measures enable organizations to detect and respond to security incidents swiftly, minimizing potential damage and ensuring business continuity.
In summary, proactive security measures involve strategic planning, risk assessment, and the implementation of preventive measures to prepare organizations or CSIRT constituents for potential problems, attacks, or events. By taking a proactive approach, organizations can enhance their overall security posture and better protect their systems from potential threats.
Learn more about security here:
https://brainly.com/question/32350573
#SPJ11
Which combination of options is the keyboard shortcut to access the find dialog box and search a worksheet for particular values? ctrl h ctrl r ctrl f ctrl e
Answers
A hot key is a key or group of keys on a computer keyboard that, when pressed simultaneously, carry out a task (such launching an application) more quickly than a mouse or other input device.
What is the uses of shortcut keys ?The Find and Replace dialog box, which enables you to look for a specific value in your worksheet and replace it with another value, is opened by pressing the keyboard shortcut Ctrl + F. Additionally, formatting can be found and changed with this shortcut.The function keys and keyboard shortcuts in Word for Windows are discussed in this article.
The Find tab appears in place of the Replace tab when using the CTRL+H keyboard shortcut or the Replace button on the ribbon to open the Find and Replace dialog box.Pressing Ctrl + R will refresh (reload) the current web page in all popular Internet browsers, including Chrome, Edge, Firefox, and Opera.To choose the search box, use Ctrl + E.
To learn more about shortcut key refer to :
https://brainly.in/question/135577
#SPJ4
The ____ file is typically saved with a prefix of inc_.
a. insert
b. include
c. nested
d. increment
Answers
The include file is typically saved with a prefix of inc_.
What is include file?The include (or require ) statement is known to be one that often takes the total text/code/markup that is seen in the specified file and it is one that copies it into a given file that uses what we call the include statement.
A file is known to be any form of documents and it is one that can be in any format such as pdf, doc and others.
Hence, in the case above, The include file is typically saved with a prefix of inc_ as that is the way to save it.
Learn more about file from
https://brainly.com/question/26125959
#SPJ1
If you want to create programs with more detailed images, maybe even characters that you could interact with, what pieces of information do you need in your code
Answers
The pieces of information needed in the code to create a more detailed program are the sprite objects
What are sprites?Sprites are program objects that are used in a program to add more features such as detailed images, characters and animations in the program.
The sprite objects are dragged and dropped on the program
Hence, the pieces of information needed are the sprite objects
Read more about object-oriented program at:
https://brainly.com/question/25649719
URGENT! I know it has to be one of these answers, but I cannot tell the difference between them for the life of me. Help.

Answers
I don't see a difference. Otherwise, they both are correct.
Suppose you derived/extended your class from a library class, and have worked with this class satisfactorily for a while. You then write a new method for your class but inadvertently use the same name and parameters as those of a public method of that library class. What will happen?
Answers
If you inadvertently use the same name and parameters as a public method of the library class, your method will override the library method.
When you derive or extend your class from a library class and inadvertently use the same name and parameters as a public method of that library class, you are essentially creating a method with the same signature. In object-oriented programming, this is known as method overriding. The new method you wrote in your class will replace the library method, and any calls to that method will now invoke your implementation instead.
This can have unintended consequences if the library method was relied upon by other parts of your code or by external code. If the functionality of the library method was important and you inadvertently change or modify it in your implementation, it may cause errors or unexpected behavior in the overall system.
To avoid such conflicts, it is good practice to choose method names and signatures that are unique to your class and do not clash with existing methods in the library class. If you do need to extend or modify the functionality of a library method, consider using a different name or parameter list to avoid overriding the original behavior.
Learn more about programming
brainly.com/question/14368396
#SPJ11
Consider the chemical formula for calcium chlorate: Ca(ClO3)2
How many of each of these atoms is in a molecule of calcium chlorate?
Ca:
Cl:
O:
Answers
A molecule of calcium chlorate contains one calcium atom, two chlorine atoms, and six oxygen atoms.
What are the chemical properties of calcium chlorate?Calcium chlorate is a chemical compound with the formula Ca(ClO3)2. It is a white crystalline powder that is highly soluble in water and is commonly used as an oxidizing agent in various industrial processes. The chemical properties of calcium chlorate are primarily related to its ability to release oxygen gas and promote oxidation reactions. This compound is highly reactive and can decompose explosively when exposed to heat or shock. It is also hygroscopic, meaning it can absorb moisture from the air, which can affect its stability and reactivity. When heated, calcium chlorate can decompose into calcium chloride and oxygen gas. Due to its potential hazards, calcium chlorate should be handled and stored with care, and appropriate safety measures should be taken when working with this compound. Despite its hazards, calcium chlorate has important applications in the manufacture of other chemicals and materials and is an important component in certain industrial processes.
To learn more about calcium chlorate, visit:
https://brainly.com/question/5923839
#SPJ1
What is the main characteristic of a Peer-to-Peer (P2P) network? HELP
A.) it helps computers to connect to the Internet
B.) both server hardware and software are not required
C.) a network operating system (NOS) routes all data between peers
D.) it enables connections between two or more different networks
Answers
The main characteristic of a Peer-to-Peer (P2P) network is it helps computers to connect to the Internet. The correct option is A.
What is a Peer-to-Peer (P2P) network?Peer-to-peer (p2p) networks offer a fault-tolerant and scalable method of placing nodes anywhere on a network without having to keep a lot of routing state.
This makes a wide range of applications possible, such as multicast systems, anonymous communications systems, and web caches, in addition to simple file sharing.
Therefore, the correct option is A. it helps computers to connect to the Internet.
To learn more about the Peer-to-Peer (P2P) network, refer to the link:
https://brainly.com/question/9315259
#SPJ1
PLSS HELP I WILL GIVE BRAINLIEST!!

Answers
Answer:
1.1000 megabyte
Explanation:
what is graphical symbols
Answers
Explanation:
A graphical symbol is a visually perceptible figure with a particular meaning used to transmit information independently of language.
if this helps you please mark me brainliest
have a nice day :)
Maxie created a presentation about cats, and she would like her teacher to critique her. Which critique item will help her know if the audience could hear her well?
Group of answer choices
Are you speaking loud and clear?
Are you using facial expressions?
Are you focusing on your topic?
Are you speaking at a good pace?
Answers
Answer:
Are you speaking loud and clear?
Explanation:
If she is speaking loud and clear that probably mean they can hear her.
Question 7 of 10
What term is used to refer to the requesting of information from a database?
O A. Inquiring
O B. Asking
O C. Querying
O D. Looking
Answers
who plays oblox .............................
Answers
Answer:
Me
Explanation:
1) The four main ways marketers divide potential customers is by:
A) occupation, income, age, and interests.
B) demographics, psychographics, behavior, and geography.
C) location, race, educational background, and wealth.
D) political affiliation, musical interests, wealth, and location.
Answers
The four main ways marketers divide potential customers is by occupation, income, age, and interests.
What are potential customers?
A company’s potential customer is usually referred to as a prospect. It is a person who has the potential to be interested in the services and products that are offered by the company but has not yet purchased.
In that sense, he’s not a customer. The term potential customer is extremely vague, it can very well define a person who knows the company and who wants to buy one of their products.
For example, it could refer to a person who could potentially be interested, as they have a common characteristic with the majority of the company’s clients, for example, the practice of the same profession.
Therefore, The four main ways marketers divide potential customers is by occupation, income, age, and interests.
To learn more about potential customers, refer to the link:
https://brainly.com/question/988073
#SPJ6
how was the background for the revolution of 2007 prepared
Answers
Answer:
Answer is in the attachment.
Hope this helps..