The upgraded system uses a directory containing additional information not supplied by the customer. The directory is used to help direct calls effectively. Which of the following is LEAST likely to be included in the directory?
answer choices
A list of common issues and whether each issue requires a human representative
A list of common keywords or phrases and a corresponding issue for each keyword or phrase
A list of computers the company owns and the computers’ corresponding IP addresses
A list of human representatives and the corresponding department for each representative
Answers
The least likely to be included in the directory for aiding in effective call re-routing is a list of the computers the company possesses and the machines' matching IP addresses.
What do the lines connecting the computers in this graphic denote?The computers can communicate with one another by sending messages. A collection of connected computers that can send and receive data is known as a computer network.
Which of the following describes a network of interconnected and interrelated computing devices that may transfer data?The Internet of Things (IoT) is a network of interconnected computing devices, mechanical and digital machinery, items, animals, and people who have access to data transmission capabilities and unique identities.
To know more about IP addresses visit:-
https://brainly.com/question/16011753
#SPJ1
Related Questions
Put the steps in order to produce the output shown below. Assume the indenting will be correct in the program.
5 3
9 3
5 7
9 7
Answers
Answer:
I took a screenshot of the test withe that question
Explanation:

Print the two-dimensional list mult_table by row and column. Hint: Use nested loops.
Sample output with input: '1 2 3,2 4 6,3 6 9':
1 | 2 | 3
2 | 4 | 6
3 | 6 | 9
Must be in Python
Answers
Answer:
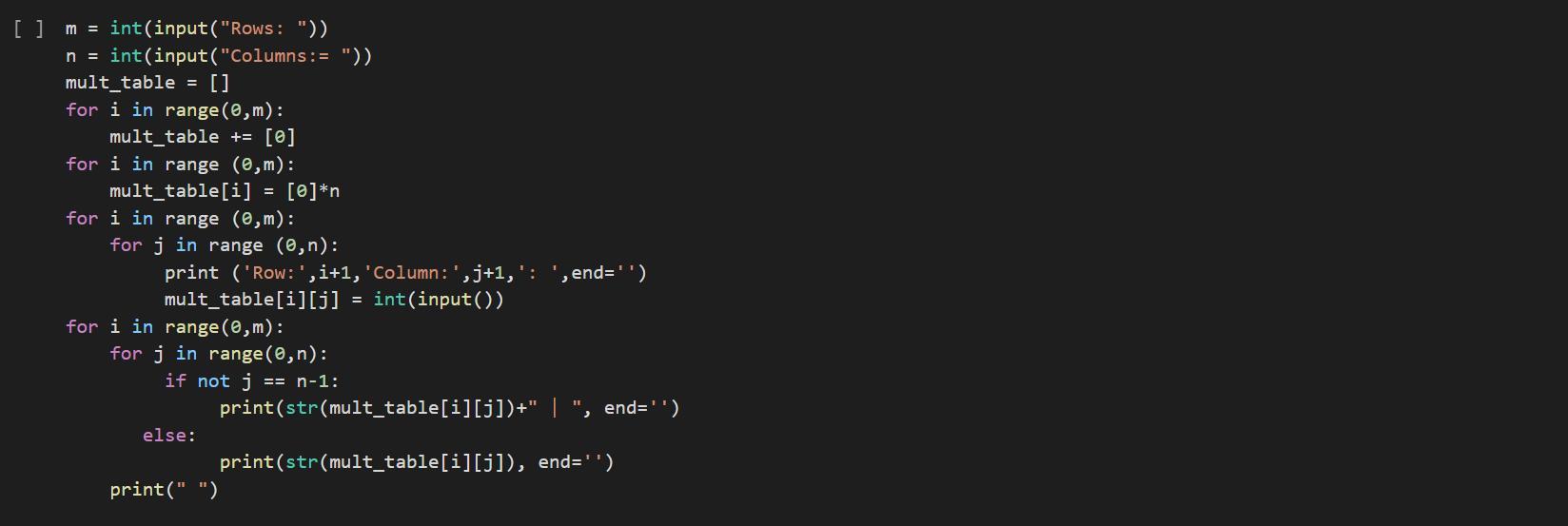
m = int(input("Rows: "))
n = int(input("Columns:= "))
mult_table = []
for i in range(0,m):
mult_table += [0]
for i in range (0,m):
mult_table[i] = [0]*n
for i in range (0,m):
for j in range (0,n):
print ('Row:',i+1,'Column:',j+1,': ',end='')
mult_table[i][j] = int(input())
for i in range(0,m):
for j in range(0,n):
if not j == n-1:
print(str(mult_table[i][j])+" | ", end='')
else:
print(str(mult_table[i][j]), end='')
print(" ")
Explanation:
The next two lines prompt for rows and columns
m = int(input("Rows: "))
n = int(input("Columns:= "))
This line declares an empty list
mult_table = []
The following two iterations initializes the list
for i in range(0,m):
mult_table += [0]
for i in range (0,m):
mult_table[i] = [0]*n
The next iteration prompts and gets user inputs for rows and columns
for i in range (0,m):
for j in range (0,n):
print ('Row:',i+1,'Column:',j+1,': ',end='')
mult_table[i][j] = int(input())
The following iteration prints the list row by row
for i in range(0,m):
for j in range(0,n):
if not j == n-1:
print(str(mult_table[i][j])+" | ", end='')
else:
print(str(mult_table[i][j]), end='')
print(" ")
In this exercise we have to use the knowledge of computational language in python to describe a code, like this:
The code can be found in the attached image.
To make it easier the code can be found below as:
m = int(input("Rows: "))
n = int(input("Columns:= "))
mult_table = []
for i in range(0,m):
mult_table += [0]
for i in range (0,m):
mult_table[i] = [0]*n
for i in range (0,m):
for j in range (0,n):
print ('Row:',i+1,'Column:',j+1,': ',end='')
mult_table[i][j] = int(input())
for i in range(0,m):
for j in range(0,n):
if not j == n-1:
print(str(mult_table[i][j])+" | ", end='')
else:
print(str(mult_table[i][j]), end='')
print(" ")
See more about python at brainly.com/question/26104476
The market is in
until the price of goods reflects equal supply and demand.
Answers
Which is the first step in the process of reading materials critically
Answers
Answer:
SQRRR or SQ3R is a reading comprehension method named for its five steps: survey, question, read, recite, and review. The method was introduced by Francis P. Robinson, an American education philosopher in his 1946 book Effective Study. The method offers a more efficient and active approach to reading textbook material
Billie downloads an email attachment from a co-worker. The attachment contains a virus. Within minutes of downloading the file, Billie's computer shuts down and will not turn back on. The company uses an intranet network. How did a virus most likely get into the original file sent to Billie? Explain your answer.
Answers
Answers:
You suspect that you have accidentally downloaded a virus.Turn off his computer and reboot from a clean system disk.She has no reason to expect a file from this person.Lisa has received a file attachment from a co-worker, James.The attachment contains a virus.The virus most likely get into the original file sent to Billie through a corrupt file that was sent and it automatically pitch itself to the file.
How do viruses get into files?A lot of Computer Viruses are known to often spread to other disk drives or computers mostly wen an infected files are gotten through downloads that are gotten from websites, email attachments, etc.
Note that the issue is that virus most likely get into the original file sent to Billie through a corrupt file that was sent and it automatically pitch itself to the file.
Learn more about email attachment from
https://brainly.com/question/17506968
#SPJ2
LANGUAGE IS PYTHON PLEASE HELP.
Write a while loop that repeats while user_num ≥ 1. In each loop iteration, divide user_num by 2, then print user_num.
Sample output with input: 20
10.0
5.0
2.5
1.25
0.625
Answers
Identify four problems endemic to the traditional file environment
Answers
Explanation:
The four problems endemic to the traditional file environment are
Repetition in data: data discrepancy occurs because of duplicate data in the various files.Programs are data-dependent means changes in any programs require data changes also.Security is poor and lack of data availability.lack of compliance and data sharing and also unofficial access is not regulated.which three statements are true about purchase orders in qbo
Answers
Regarding QBO , three claims are accurate: You can only shut individual lines on a buy order you establish, and Quickbooks Online closes purchase orders even when payment is not yet received in full. Purchase orders can only be created for inventory.
Why would you utilize QuickBooks purchase orders?Make it simpler to track orders: An essential component of record keeping is the purchase order. You can quickly track your orders by generating a purchase order. Also, it's simple to verify that you got the right things when your order is delivered.
What exactly is a buy order and how do you utilize one?Purchase orders are written instructions given by a buyer to a seller. They act as legally binding documentation of the goods/services and serve as a key tool for buyers by formalizing specifications and pricing.
To know more about QBO visit:-
https://brainly.com/question/30591322
#SPJ1
Question:-
Which 3 statements are true about purchase orders in QuickBooks Online?(Select all that apply)
.You can only create purchase orders for inventory
.You can close individual lines on a purchase order
.You can add purchase orders to any type of purchase transaction
.QuickBooks Online closes purchase orders, even when not fully received
.You can add multiple purchase orders to one purchase transaction
In which year did Patricia Schwirian
develop her model?
Answers
1986
Patricia Schwirian- Proposed a model intended to stimulate and guide systematic research in nursing informatics in 1986.Model and framework that enables identifications of significant information needs, that can foster research (some are similar to Maslow's Heirarchy of needs)
How does a fully integrated Data and Analytics Platform enable organizations to
convert data into consumable information and insight?
Answers
A fully integrated Data and Analytics Platform enable organizations to convert data into consumable information and insight by:
How does a fully integrated Data and Analytics Platform enable convert data?This is done by putting together or the archiving of all the captured data and also the act of getting them back if and when needed for business purpose.
Note that it is also done by making analytics reports and creating Machine Learning models to refine the data.
Learn more about Analytics Platform from
https://brainly.com/question/27379289
#SPJ1
What statement is accurate in regards to
sharing workbooks?
Select an answer:
It is a legacy feature that is no longer a feature in Excel.
You must add the feature to the Quick Access Toolbar.
You can share and unshare from the Review option on the
ribbon.
You cannot track the changes of each user.

Answers
The statement that is accurate in regards to sharing workbooks is that You must add the feature to the Quick Access Toolbar
What does a shared workbook implies?The term connote the act of sharing an Excel file. Here, a person can give other users any form of access to the same document.
Sharing workbook is one that allow people to make any kinds of edits at the same time, which saves a person the trouble of keeping track of different versions.
Learn more about workbooks from
https://brainly.com/question/5450162
What is the output of the following code segment?
String[] cs = "Bill Gates and Paul Allen founded Microsoft on April 4, 1975.".split(" ");
System.out.println(cs[6].charAt(5));
Answers
Answer:
o
Explanation:
why is this not working for my plus membership
Answers
Answer:
The overwhelming main cause for PlayStation Plus subscriptions not being recognised is because of PlayStation server maintenance which prevents your PS4 from communicating with Sony and discovering that you are a paid up PS Plus subscriber.
1. Ang tawag sa hanay ng mga cells sa worksheet ng spreadsheet na nakahanay ng pahalang. Ito ay may numero kaliwang bahagi nito.
Answers
hope it helps
#carry on learning
UK UKI
Different
DIFFERENTIATE BETWEEN FORMULA & A FUNCTION GNING EXAMPLE
Answers
Explanation:
A Formula is an equation designed by a user in Excel, while a Function is a predefined calculation in the spreadsheet application. Excel enables users to perform simple calculations such as finding totals for a row or column of numbers. Formulas and functions can be useful in more complex situations, including calculating mortgage payments, solving engineering or math problems, and creating financial models.
industrial advantages of using a waterfall model for library system
Answers
Answer:
It allows for departmentalization and managerial control. Simple and easy to understand and use. Easy to manage due to the rigidity of the model – each phase has specific deliverables and a review process. Phases are processed and completed one at a time.
Explanation:
Code to be written in R language:
The Fibonacci numbers is a sequence of numbers {Fn} defined by the following recursive relationship:
Fn= Fn−1 + Fn−2, n > 3
with F1 = F2 = 1.
Write the code to determine the smallest n such
that Fn is larger than 5,000,000 (five million). Report the value of that Fn.
Answers
Here is the R code to determine the smallest n such that the Fibonacci number is larger than 5,000,000:
fib <- function(n) {
if (n <= 2) {
return(1)
} else {
return(fib(n - 1) + fib(n - 2))
}
}
n <- 3
while (fib(n) <= 5000000) {
n <- n + 1
}
fib_n <- fib(n)
cat("The smallest n such that Fibonacci number is larger than 5,000,000 is", n, "and the value of that Fibonacci number is", fib_n, "\n")
The output of this code will be:
The smallest n such that Fibonacci number is larger than 5,000,000 is 35 and the value of that Fibonacci number is 9227465.
Learn more about R language here: https://brainly.com/question/14522662
#SPJ1
What additional uses of technology can u see in the workplace
Answers
Answer:
Here are some additional uses of technology in the workplace:
Virtual reality (VR) and augmented reality (AR) can be used for training, simulation, and collaboration. For example, VR can be used to train employees on how to operate machinery or to simulate a customer service interaction. AR can be used to provide employees with real-time information or to collaborate with colleagues on a project.Artificial intelligence (AI) can be used for a variety of tasks, such as customer service, data analysis, and fraud detection. For example, AI can be used to answer customer questions, identify trends in data, or detect fraudulent activity.Machine learning can be used to improve the accuracy of predictions and decisions. For example, machine learning can be used to predict customer churn, optimize marketing campaigns, or improve product recommendations.Blockchain can be used to create secure and transparent records of transactions. For example, blockchain can be used to track the provenance of goods, to manage supply chains, or to record financial transactions.The Internet of Things (IoT) can be used to connect devices and collect data. For example, IoT can be used to monitor equipment, track assets, or collect data about customer behavior.These are just a few of the many ways that technology can be used in the workplace. As technology continues to evolve, we can expect to see even more innovative and creative uses of technology in the workplace.
script code written in many languages of the best known: ( C#_PHP_HTML)
Answers
Answer:
PHP
Explanation:
The best way to answer this question is to interpret it as, which of the three is a scripting language.
Analyzing each of the languages
1. C#
C# is not a scripting language, but instead it is an object-oriented programming language. Also, c# is a compiled language and one of the features of scripting language is that, they are interpreted.
2. PHP
Basically, PHP are used for server side scripting language because it uses scripts and its programs are not for general purpose runtime environment (but instead for special runtime environments).
3. HTML
HTML is neither a programming language, nor a scripting language because its design pattern does not follow that or programming and scripting languages, and it can not perform what an actual programming and scripting language do.
how many answer can you get daily
Answers
Answer:
2 - 6.Explanation:
If you have way to many questions you don't know, then your answer is about 12 - 16.
Anna bought a box of blueberries for £7. She used 700 grams for a cheesecake and she has 450 grams left. How much did the blueberries cost per 100 grams?
Answers
0.61 (rounded up)
Explanation:
You add both 700 and 450 which will give you 1150g
You then divide 1150 by 100 which gives you 11.5
Then divide 7 by 11.5 which will give you 0.61 as cost of every 100 grams
The Internet began when a large company wanted to sell products online.
True
or
False
Answers
Answer:
True
Explanation:
Answer:
It would be true
Explanation:
Consider all of the ways that you interact with the internet during a normal month in your life: websites, banking, apps, etc. Of all of those interactions, explain which one you think is LEAST secure and describe how much “risk” you experience using it. Then explain which interaction you feel is MOST secure?
Answers
Answer:
Website, are probably the least secure because depending on what site you click on it can be an add for a different website. You can risk ending up on a site you didn't want to. I think that banking apps are the most secure, because its mostly through your bank so it would have to be secure.
Explanation:
anyone know how to fix black screen of death on computer
Answers
Answer:
you asked a question so you must have fixed it
Explanation:
logic
Write a recursive function called DrawTriangle() that outputs lines of '*' to form a right side up isosceles triangle. Function DrawTriangle() has one parameter, an integer representing the base length of the triangle. Assume the base length is always odd and less than 20. Output 9 spaces before the first '*' on the first line for correct formatting.
Answers
Answer:
Code:-
# function to print the pattern
def draw_triangle(n, num):
# base case
if (n == 0):
return;
print_space(n - 1);
print_asterisk(num - n + 1);
print("");
# recursively calling pattern()
pattern(n - 1, num);
# function to print spaces
def print_space(space):
# base case
if (space == 0):
return;
print(" ", end = "");
# recursively calling print_space()
print_space(space - 1);
# function to print asterisks
def print_asterisk(asterisk):
# base case
if(asterisk == 0):
return;
print("* ", end = "");
# recursively calling asterisk()
print_asterisk(asterisk - 1);
# Driver Code
n = 19;
draw_triangle(n, n);
Output:-
# Driver Code n = 19;| draw_triangle(n, n);

(5) Add the following two binary numbers together. Take that result, and XOR it with the shown binary number. Then take those results, and NOR it together with the last binary number. (40 pts.) please show the steps
Step 1: 1001101 + 1010
Step 2: XOR 1011001
Step 3: NOR 110110
Answers
Answer:
Here are the steps to solve the problem:
Step 1: 1001101 + 1010 To add these two binary numbers together, we need to align them by their least significant bit (rightmost bit) and then add them column by column:
1001101
+ 1010
--------
1011001
Copy
So the result of step 1 is 1011001.
Step 2: XOR 1011001 To XOR two binary numbers, we compare their bits column by column. If the bits are the same (both 0 or both 1), the result is 0. If the bits are different (one is 0 and the other is 1), the result is 1:
1011001
^ 1011001
--------
0000000
Copy
So the result of step 2 is 0000000.
Step 3: NOR 110110 To NOR two binary numbers, we first OR them and then NOT the result. To OR two binary numbers, we compare their bits column by column. If at least one of the bits is 1, the result is 1. If both bits are 0, the result is 0. To NOT a binary number, we flip all its bits (0 becomes 1 and vice versa):
OR:
0000000
| 110110
--------
110110
NOT:
~110110
--------
001001
So, the final result of step 3 is 001001.
The address for the website you want to visit is called the browser internet URL World Wide Web
Answers
URL would be your answer to this question.
you can take care of the computer in the following ways except _____
a. connecting it to a stabilizer before use b. using it always
Answers
You can take care of the computer in the following ways except by using it always (Option B).
How can the computer be cared for?To care for a computer and guarantee its ideal execution and life span, here are a few suggested ones:
Keep the computer clean: Frequently clean the outside of the computer, counting the console, screen, and ports, utilizing fitting cleaning devices and arrangements. Ensure against tidy and flotsam and jetsam: Clean flotsam and jetsam can collect the interior of the computer, driving to overheating and execution issues. Utilize compressed discuss or a computer-specific vacuum cleaner to tenderly expel tidiness from the vents and inner components. Guarantee legitimate ventilation: Satisfactory wind stream is basic to anticipate overheating. Put the computer in a well-ventilated zone and guarantee that the vents are not blocked by objects. Consider employing a portable workstation cooling cushion or desktop fan in case vital.Utilize surge defenders: Interface your computer and peripherals to surge defenders or uninterruptible control supply (UPS) gadgets to defend against control surges and electrical vacillations that can harm the computer's components.Learn more about computers in https://brainly.com/question/19169045
#SPJ1
How can you compute, the depth value Z(x,y) in
z-buffer algorithm. Using incremental calculations
find out the depth value Z(x+1, y) and Z (x, y+1).
(2)
Answers
The Depth-buffer approach, usually referred to as Z-buffer, is one of the methods frequently used to find buried surfaces. It is a method in image space and pixel.
Thus, The pixel to be drawn in 2D is the foundation of image space approaches and Z buffer. The running time complexity for these approaches equals the product of the number of objects and pixels.
Additionally, because two arrays of pixels are needed—one for the frame buffer and the other for the depth buffer—the space complexity is twice the amount of pixels.
Surface depths are compared using the Z-buffer approach at each pixel location on the projection plane.
Thus, The Depth-buffer approach, usually referred to as Z-buffer, is one of the methods frequently used to find buried surfaces. It is a method in image space and pixel.
Learn more about Z buffer, refer to the link:
https://brainly.com/question/12972628
#SPJ1
Discuss at least 1 Microsoft Windows security features that could protect data?
Answers
Answer:
Virus & threat protection.
Explanation:
Monitor threats to your device, run scans, and get updates to help detect the latest threats.
One Microsoft Windows security feature that can help protect data is BitLocker Drive Encryption.
BitLocker is a full-disk encryption feature available in certain editions of Microsoft Windows, such as Windows 10 Pro and Enterprise. It provides protection for data stored on the system's hard drives or other storage devices.
By encrypting the entire drive, BitLocker helps safeguard the data against unauthorized access or theft, even if the physical drive is removed from the device. It uses strong encryption algorithms to convert the data into an unreadable format, ensuring that only authorized users with the appropriate encryption key or password can access and decrypt the data.
BitLocker also provides additional security features, such as pre-boot authentication, which requires users to enter a password or use a USB key to unlock the drive before the operating system loads. This prevents unauthorized users from accessing the encrypted data, even if they have physical access to the device.
Overall, BitLocker Drive Encryption is a powerful security feature in Microsoft Windows that can effectively protect data by encrypting entire drives and adding layers of authentication and protection against unauthorized access.
Learn more about Security here:
https://brainly.com/question/13105042
#SPJ6