the search steps through an array, comparing each value to the search value. question 9 options: binary selection sequential iterative
Answers
The search steps through an array, comparing each item with the search value is sequential search.
What is sequential search?Sort or search in array can be performed by many methods including binary, selection, sequential, iterative.
Binary search will use algorithm to divide array to two part repeatedly to search value.
Selection sort will find the value and move them to their final position make it this method is very efficient for sorting.
Sequential search or linear will comparing each value one by one to search value. Sequential is adequate for small array.
Iterative sort will find the smallest value and swap them with the first value in array index.
Learn more about iterative here:
brainly.com/question/16929607
#SPJ4
Related Questions
PLEASE HURRY!!!!
Rowan bought a new laptop. What will protect the computer from viruses A.application software
B.up to date hardware
C. A new camera
D. System software
Answers
Answer:
D
Explanation:
Use Norton Sercrity link below
https://us.norton.com
Answer:
D
Explanation:
John tells you that a certain algorithm runs in time (3 + 200), and Bill tells you that the same algorithm runs in time Ω(3). Can both John and Bill be correct? Why?
Answers
According to the question, the statements made by both John and Bill are correct. This is because both express the value of algorithms with respect to their requirement and identification.
What is an Algorithm?An algorithm may be characterized as a type of procedure that is widely used for solving a problem or performing a computation. They act as an exact list of instructions that conduct specified actions step by step in either hardware- or software-based routines.
As per John, the worst-case run time requires the setting of the algorithm to (3+200), but on contrary, as per Bill, the running time of the same algorithm requires Ω(3). The concept of both people is correct but they are understanding the algorithm with respect to their facts and requirements.
Therefore, the statements made by both John and Bill are correct. This is because both express the value of algorithms with respect to their requirement and identification.
To learn more about Algorithm, refer to the link:
https://brainly.com/question/24953880
#SPJ9
A letter of application should be written on:
•Lined tablet paper
•Fancy or decorative stationary
•Neon paper
•Plain white or pale-colored paper
Answers
You want to draw a rectangle over the moon you added to your slide and then move it behind the moon. You want it to look like a frame.
What ribbon tab would you click to find the tool to add the rectangle?
Animations
Insert
Design
Home
Answers
A _____ address directs the frame to the next device along the network.
Answers
Answer:
When sending a frame to another device on a remote network, the device sending the frame will use the MAC address of the local router interface, which is the default gateway.
An unicast address directs the frame to the next device along the network.
What is network?
A computer network is a group of computers that share resources on or provided by network nodes. To communicate with one another, the computers use standard communication protocols across digital linkages. These linkages are made up of telecommunication network technologies that are based on physically wired, optical, and wireless radio-frequency means and can be configured in a number of network topologies.
The term "unicast" refers to communication in which a piece of information is transferred from one point to another. In this situation, there is only one sender and one receiver.
To learn more about network
https://brainly.com/question/28041042
#SPJ13
Which of the following parts apply when delivering an indirect bad news message? Select all that apply.
Question 2 options:
Opening with a buffer statement
Being direct with news
Explaining the situation
Inserting stories and important anecdotes
Keeping details to a minimum
Providing alternatives
Answers
The parts that apply when delivering an indirect bad news message are:
Opening with a buffer statement
Explaining the situation
Keeping details to a minimum
Providing alternatives.
When delivering an indirect bad news message, the following parts apply:
Opening with a buffer statement: Start the message with a neutral or positive statement that prepares the recipient for the upcoming news. This helps soften the impact and reduces defensiveness.Explaining the situation: Provide a clear and concise explanation of the circumstances or reasons behind the bad news. This helps the recipient understand the context and rationale.Keeping details to a minimum: While it is important to provide necessary information, it is also crucial to avoid overwhelming the recipient with excessive details. Focus on the key points to maintain clarity and avoid confusion.Providing alternatives: Offer alternative solutions or options to mitigate the impact of the bad news. This shows empathy and provides the recipient with potential avenues for resolution or improvement.The parts that do not apply in delivering an indirect bad news message are:
Being direct with news: Indirect bad news messages typically involve delivering the news subtly rather than being direct.Inserting stories and important anecdotes: Including stories or anecdotes may not be suitable for an indirect bad news message as it can distract from the main message and dilute its impact.Therefore, the applicable parts for delivering an indirect bad news message are opening with a buffer statement, explaining the situation, keeping details to a minimum, and providing alternatives.
For more such question on bad news message
https://brainly.com/question/22473511
#SPJ8
Data about the details of a tin of beans stored on the tin using a?
Answers
Answer:
copper
Explanation:
hope it will be helpful
Write a simple JavaScript function named makeFullName with two parameters named givenName and familyName. The function should return a string that contains the family name, a comma, and the given name. For example, if the function were called like this: var fn = makeFullName("Theodore", "Roosevelt");
Answers
Answer:
Explanation:
Ji
A JavaScript function exists as a block of code created to accomplish a certain task.
What is a JavaScript function?In JavaScript, functions can also be described as expressions. A JavaScript function exists as a block of code created to accomplish a certain task.
Full Name with two parameters named given Name and family Name
#Program starts here
#Prompt User for Input "given Name and family Name "
given Name = input("Enter Your given Name: ")
family Name = input("Enter Your family Name: ")
#Define Function
def last F(given Name, Family Name):
given Name = given Name[0]+"."
print(Last Name+", "+Family Name);
last F(given Name, Family Name) #Call Function
#End of Program
To learn more about JavaScript function
https://brainly.com/question/27936993
#SPJ2
What new details are you able to see on the slide when the magnification is increased to 10x that you could not see at 4x? What about 40x?
Answers
Answer:
x=10
Explanation:
just need points because i can scan questions anymore
A user attempts to send an email to an external domain and quickly receives a bounce-back message. The user then contacts the help desk stating the message is important and needs to be delivered immediately. While digging through the email logs, a systems administrator finds the email and bounce-back details: Your email has been rejected because It appears to contain SSN Information. Sending SSN information via email external recipients violates company policy. Which of the following technologies successfully stopped the email from being sent?
a. DLP
b. UTM
c. WAF
d. DEP
Answers
Answer:
1. DLP (Data Loss Prevention)
Explanation:
DLP tools are meant to protect sensitive information of an organization, by monitoring data transmissions and enforcing previously set policies
UTM means Unified Threat Management. It is a suite of security programs, usually including antivirus, antispam, firewall and others.
WAF stands for Web Application Firewall. It is a specific firewall used to protect web servers by monitoring HTTP traffic.
DEP or Data execution Prevention is a security feature in some operating systems that blocks applications trying to access restricted memory areas.
How many times would the code in this loop repeat? ____________ for ( j = 0; j < 10; j++ ) { appendItem (myList, aNumber); }
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
The for-loop given in the question is:
for ( j = 0; j < 10; j++ )
{
appendItem (myList, aNumber); //this loop append a number to a list myList
}
This loop starts from J variable's value zero and when J's value is less than 10, the loop iterate through its body until J's value becomes greater or equal to 10. As J's value exceed nine, the loop will get terminated.
So this loop repeats 10 times its loop body, at the 11th time, the condition becomes false and the loop will get terminated.
Jazmyn cannot find the paper that she wrote last night. She is in a panic and you want to help her. What advice would you give
her?
A. Go to the Start menu or Dock to see if the operating
system saved it there.
C. Use the search tool to locate the file by file name,
content, or date.
B. Retype the paper and save it in a new folder.
D. Restart the computer and wait for the document to
open automatically.
Answers
Answer:
C
Explanation:
Answer: maybe C it might not be right i hope you got it right
the value 'blackstone' specified cannot be used as it conflicts with the value 'generic' for asin 'b09mr1ph1b' in the amazon catalog. if this is asin 'b09mr1ph1b', update the value to match the asin data. if this is a different product, update identifying information (upc/ean/part number/etc.).
Answers
Change the value to reflect the ASIN data if this is ASIN "asin name". Update the identifying details if this is a new product.
Explain about the invalid ASIN mean on Amazon?This mistake shows that your Amazon feed lacks the necessary information, according to this error. Example: A product ID doesn't match an existing ASIN or a crucial value is invalid. There is a different inventory file template for each Amazon product category.
The ASIN number is specific to a product rather than a seller. In this case, if someone else is currently selling your product on Amazon, you can utilise their ASIN. Amazon maintains the order of its catalogue by allowing each product a single ASIN.
Despite the fact that SKUs and ASINs are both used to identify Amazon products, they each function differently. SKUs aid in inventory control while ASINs identify each distinct product on Amazon.
To learn more about generic for asin refer to:
https://brainly.com/question/12904434
#SPJ4
You are working with a database table that contains data about music. The table includes columns for track_id, track_name, composer, and milliseconds (duration of the music track). You are only interested in data about the classical musician Johann Sebastian Bach. You want to know the duration of each Bach track in seconds. You decide to divide milliseconds by 1000 to get the duration in seconds, and use the AS command to store the result in a new column called secs. Add a statement to your SQL query that calculates the duration in seconds for each track and stores it in a new column as secs. NOTE: The three dots (...) indicate where to add the statement.
SELECT
track_id,
track_name,
composer,
...
FROM
track
WHERE
composer = "Johann Sebastian Bach"
Answers
To calculate duration in seconds for each Bach track in a database table, the SQL query selects the track_id, track_name, composer, and divides the milliseconds column by 1000 to create a new column called "secs".
To calculate the duration in seconds for each track by dividing the milliseconds by 1000 and store it in a new column called "secs", the following statement should be added to the SQL query:
SELECT track_id, track_name, composer, milliseconds/1000 AS secs
FROM track
WHERE composer = "Johann Sebastian Bach"
This will return a result set with the track_id, track_name, composer, and duration in seconds as secs, only for tracks composed by Johann Sebastian Bach.
The given SQL query selects the track_id, track_name, and composer from the track table where the composer is "Johann Sebastian Bach". To get the duration in seconds for each track, the milliseconds column is divided by 1000 and the result is stored in a new column called "secs" using the AS command. The resulting query calculates the duration in seconds for each Bach track and includes it in the output.
Learn more about command here:
https://brainly.com/question/30401660
#SPJ4
Which type of virus includes protective code that prevents outside examination of critical elements?
Answers
Answer:
Armoured viruses
Explanation:
Armoured viruses are computer viruses that have been found to be very dangerous, Armoured viruses ar designed to protect itself against any attempt to detect or trace Its activities. They have different ways through which they bypass antivirus software applications in a computer system, making it very difficult to eliminate from an infected system.
Drag each tile to the correct box. Match each decimal number to an equivalent number in a different number system. 6910 22810 4210 2710
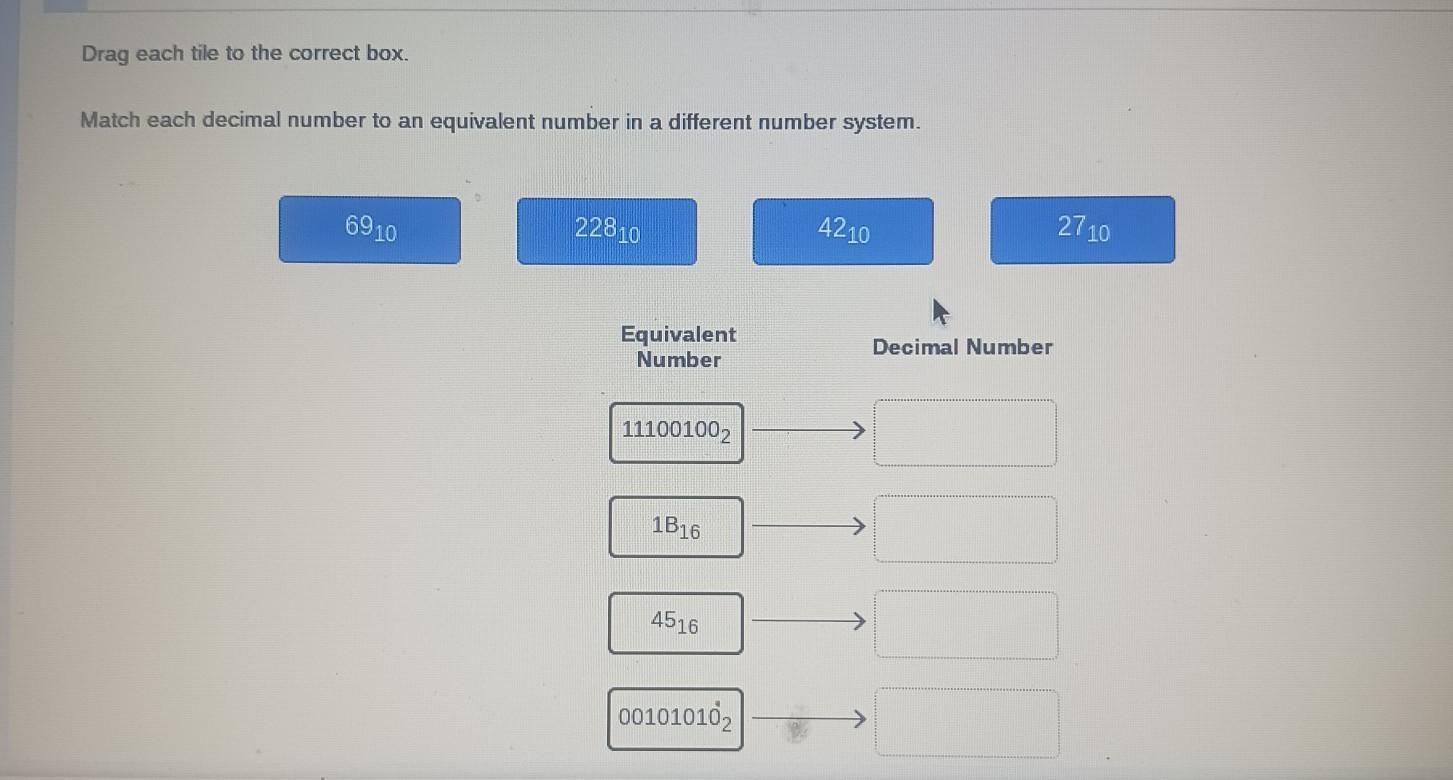
Answers
Explanation:
you can do that with calculator only

How is opera diffrerent from blues,gospel,and country music?

Answers
Answer: Opera has its roots in Europe; the other styles are American
Explanation:
https://www.celonis.com/solutions/celonis-snap
Using this link
To do this alternative assignment in lieu of Case 2, Part 2, answer the 20 questions below. You
will see on the left side of the screen a menu for Process Analytics. Select no. 5, which is Order
to Cash and click on the USD version. This file is very similar to the one that is used for the BWF
transactions in Case 2, Part 2.
Once you are viewing the process analysis for Order to Cash, answer the following questions:
1. What is the number of overall cases?
2. What is the net order value?
Next, in the file, go to the bottom middle where you see Variants and hit the + and see what it
does to the right under the detail of variants. Keep hitting the + until you see where more than a
majority of the variants (deviations) are explained or where there is a big drop off from the last
variant to the next that explains the deviations.
3. What is the number of variants you selected?
4. What percentage of the deviations are explained at that number of variants, and why did you
pick that number of variants?
5. What are the specific variants you selected? Hint: As you expand the variants, you will see on
the flowchart/graph details on the variants.
6. For each variant, specify what is the percentage of cases and number of cases covered by that
variant? For example: If you selected two variants, you should show the information for each
variant separately. If two were your choice, then the two added together should add up to the
percentage you provided in question 4 and the number you provided in question 3.
7. For each variant, how does that change the duration? For example for the cases impacted by
variant 1, should show a duration in days, then a separate duration in days for cases impacted
by variant 2.
At the bottom of the screen, you see tabs such as Process, Overview, Automation, Rework, Benchmark,
Details, Conformance, Process AI, Social Graph, and Social PI. On the Overview tab, answer the
following questions:
8. In what month was the largest number of sales/highest dollar volume?
9. What was the number of sales items and the dollar volume?
10. Which distribution channel has the highest sales and what is the amount of sales?
11. Which distribution channel has the second highest sales and what is the amount of sales?
Next move to the Automation tab and answer the following questions:
12. What is the second highest month of sales order?
13. What is the automation rate for that month?
Nest move to the Details tab and answer the following questions:
14. What is the net order for Skin Care, V1, Plant W24?
15. What is the net order for Fruits, VV2, Plant WW10?
Next move to the Process AI tab and answer the following questions:
16. What is the number of the most Common Path’s KPI?
17. What is the average days of the most Common Path’s KPI?
18. What other information can you get off this tab?
Next move to the Social Graph and answer the following questions:
19. Whose name do you see appear on the graph first?
20. What are the number of cases routed to him at the Process Start?
Answers
1. The number of overall cases are 53,761 cases.
2. The net order value of USD 1,390,121,425.00.
3. The number of variants selected is 7.4.
4. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. Seven variants explain 87.3% of the total variance, including order, delivery, credit limit, material availability, order release, goods issue, and invoice verification.
10. January recorded the highest sales volume, with 256,384 items sold for USD 6,607,088.00. Wholesale emerged as the top distribution channel, followed by Retail.
12. December stood out as the second-highest sales month,
13. with an automation rate of 99.9%.
14. Notable orders include Skin Care, V1, Plant W24 (USD 45,000.00) and
15. Fruits, VV2, Plant WW10 (USD 43,935.00).
17. The most common path had a KPI of 4, averaging 1.8 days.
18. This data enables process analysis and improvement, including process discovery, conformance, and enhancement.
19. The Social Graph shows Bob as the first name,
20. receiving 11,106 cases at the Process Start.
1. The total number of cases is 53,761.2. The net order value is USD 1,390,121,425.00.3. The number of variants selected is 7.4. The percentage of the total variance explained at 7 is 87.3%. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. The seven specific variants that were selected are: Order, Delivery and Invoice, Check credit limit, Check material availability, Order release, Goods issue, and Invoice verification.6. Below is a table showing the percentage of cases and number of cases covered by each variant:VariantPercentage of casesNumber of casesOrder57.2%30,775Delivery and Invoice23.4%12,591Check credit limit5.1%2,757
Check material availability4.2%2,240Order release4.0%2,126Goods issue2.4%1,276Invoice verification1.7%9047. The duration of each variant is as follows:VariantDuration in daysOrder24Delivery and Invoice3Check credit limit2Check material availability1Order release2Goods issue4Invoice verification1
8. The largest number of sales/highest dollar volume was in January.9. The number of sales items was 256,384, and the dollar volume was USD 6,607,088.00.10. The distribution channel with the highest sales is Wholesale and the amount of sales is USD 3,819,864.00.
11. The distribution channel with the second-highest sales is Retail and the amount of sales is USD 2,167,992.00.12. The second-highest month of sales order is December.13. The automation rate for that month is 99.9%.14. The net order for Skin Care, V1, Plant W24 is USD 45,000.00.15.
The net order for Fruits, VV2, Plant WW10 is USD 43,935.00.16. The number of the most common path’s KPI is 4.17. The average days of the most common path’s KPI is 1.8 days.18. Additional information that can be obtained from this tab includes process discovery, process conformance, and process enhancement.
19. The first name that appears on the Social Graph is Bob.20. The number of cases routed to Bob at the Process Start is 11,106.
For more such questions deviations,Click on
https://brainly.com/question/24251046
#SPJ8
You have an Azure subscription that contains the following fully peered virtual networks: VNet1, located in the West US region. 5 virtual machines are connected to VNet1. VNet2, located in the West US region. 7 virtual machines are connected to VNet2. VNet3, located in the East US region, 10 virtual machines are connected to VNet3. VNet4, located in the East US region, 4 virtual machines are connected to VNet4. You plan to protect all of the connected virtual machines by using Azure Bastion. What is the minimum number of Azure Bastion hosts that you must deploy? Select only one answer. 1 2 3 4
Answers
Answer:
To protect all the connected virtual machines with Azure Bastion, the minimum number of Azure Bastion hosts that you must deploy is 2.
Explanation:
Azure Bastion provides secure and seamless RDP and SSH access to virtual machines directly through the Azure portal, eliminating the need to expose them to the public internet. Each Azure Bastion host provides connectivity to virtual machines within a single virtual network.
In this scenario, you have four virtual networks (VNet1, VNet2, VNet3, and VNet4) located in two different regions (West US and East US). Since VNet1 and VNet2 are in the same region (West US), you can deploy one Azure Bastion host in that region to provide access to the 12 virtual machines (5 in VNet1 and 7 in VNet2).
For VNet3 and VNet4, which are located in the East US region, you would need another Azure Bastion host to provide access to the 14 virtual machines (10 in VNet3 and 4 in VNet4).
Therefore, the minimum number of Azure Bastion hosts required is 2, with one host deployed in the West US region and another host deployed in the East US region.
You are a systems analyst. Many a time have you heard friends and colleagues complaining that their jobs and businesses are being negatively impacted by e-commerce. As a systems analyst, you decide to research whether this is true or not. Examine the impact of e-commerce on trade and employment/unemployment, and present your findings as a research essay.
Answers
E-commerce, the online buying and selling of goods and services, has significantly impacted trade, employment, and unemployment. This research essay provides a comprehensive analysis of its effects.
What happens with e-commerceContrary to popular belief, e-commerce has led to the growth and expansion of trade by breaking down geographical barriers and providing access to global markets for businesses, particularly SMEs. It has also created job opportunities in areas such as operations, logistics, customer service, web development, and digital marketing.
While certain sectors have experienced disruption, traditional businesses can adapt and benefit from e-commerce by adopting omni-channel strategies. The retail industry, in particular, has undergone significant transformation. E-commerce has empowered small businesses, allowing them to compete with larger enterprises and fostered entrepreneurial growth and innovation. However, there have been job displacements in some areas, necessitating individuals to transition and acquire new skills.
Read mroe on e-commerce here https://brainly.com/question/29115983
#SPJ1
Question 1 of 4
OSHA requires which of the following trenches to have a protective system installed?
Select the best option.
O
A trench 1 foot deep.
A trench 3 feet deep.
A trench 14 feet deep.
Answers
Answer:
These are all wrong. OSHA requires a trench to have a protective system starting at 5 feet.
Explanation:
OSHA's own rules state this, unless it is in stable rock. If it is under 5 feet, it isn't required and can be decided by someone qualified.
In c++, make the output exactly as shown in the example.

Answers
Answer:
Here's a C++ program that takes a positive integer as input, and outputs a string of 1's and 0's representing the integer in reverse binary:
#include <iostream>
#include <string>
std::string reverse_binary(int x) {
std::string result = "";
while (x > 0) {
result += std::to_string(x % 2);
x /= 2;
}
return result;
}
int main() {
int x;
std::cin >> x;
std::cout << reverse_binary(x) << std::endl;
return 0;
}
The reverse_binary function takes an integer x as input, and returns a string of 1's and 0's representing x in reverse binary. The function uses a while loop to repeatedly divide x by 2 and append the remainder (either 0 or 1) to the result string. Once x is zero, the function returns the result string.
In the main function, we simply read in an integer from std::cin, call reverse_binary to get the reverse binary representation as a string, and then output the string to std::cout.
For example, if the user inputs 6, the output will be "011".
Hope this helps!
How do a write 19/19 as a whole number
Answers
Answer:
1.0
Explanation:
You divide 19 by 19 and get 1
3
Drag each label to the correct location on the image.
An organization has decided to initiate a business project. The project management team needs to prepare the project proposal and business
justification documents. Help the management team match the purpose and content of the documents.
contains high-level details
of the proposed project
contains a preliminary timeline
of the project
helps to determine the project type,
scope, time, cost, and classification
helps to determine whether the
project needs meets business
needs
contains cost estimates,
project requirements, and risks
helps to determine the stakeholders
relevant to the project
Project proposal
Business justification
Answers
Here's the correct match for the purpose and content of the documents:
The Correct Matching of the documentsProject proposal: contains high-level details of the proposed project, contains a preliminary timeline of the project, helps to determine the project type, scope, time, cost, and classification, helps to determine the stakeholders relevant to the project.
Business justification: helps to determine whether the project needs meet business needs, contains cost estimates, project requirements, and risks.
Please note that the purpose and content of these documents may vary depending on the organization and specific project. However, this is a general guideline for matching the labels to the documents.
Read more about Project proposal here:
https://brainly.com/question/29307495
#SPJ1
Chris is concerned about deploying an application to a cloud service provider and being locked in technologically so that his organization would have to stay with that cloud service provider in order to run that application. Which of the following could he possibly use that should allow for an easier migration from one cloud service provider to another?
a. Virtual machines.
b. Containerization.
c. Orchestration.
d. Serverless computing.
Answers
Answer:
d. Serverless computing.
Explanation:
Chris is concerned about deploying an application to a cloud service provider and being locked in technologically so that his organization would have to stay with that cloud service provider in order to run that application.
Therefore, the use of Serverless computing should allow for an easier migration from one cloud service provider to another.
This is because, serverless computing has to do with a cloud computing model which gives the machine resources tasks to take care of servers on behalf of clients.
Which of the following is the best example of a purpose of e-mail?
rapidly create and track project schedules of employees in different locations
easily provide printed documents to multiple people in one location
quickly share information with multiple recipients in several locations
O privately communicate with select participants at a single, common location
Answers
Answer:
The best example of a purpose of email among the options provided is: quickly share information with multiple recipients in several locations.
While each option serves a specific purpose, the ability to quickly share information with multiple recipients in different locations is one of the primary and most commonly used functions of email. Email allows for efficient communication, ensuring that information can be disseminated to multiple individuals simultaneously, regardless of their physical location. It eliminates the need for physical copies or face-to-face interactions, making it an effective tool for communication across distances.
Explanation:
A number is a palindrome if its reversal is the same as itself. Write a program ReverseNumber.java to do the following:
1. Define a method call reverse, which takes a 4-digit integer and returns an integer in reverse. For example, reverse(1234) should return 4321. (Hint: use / and % operator to separate the digits, not String functions)
2. In the main, take user input of a series of numbers, call reverse method each time and then determine if the number is a palindrome number, for example, 1221 is a palindrome number, but 1234 is not.
3. Enhance reverse method to work with any number, not just 4-digit number.
Answers
The reverse method takes an integer as input and reverses it by extracting the last digit using the modulus operator % and adding it to the reversed number after multiplying it by 10.
The Programimport java.util.Scanner;
public class ReverseNumber {
public static int reverse(int number) {
int reversedNumber = 0;
while (number != 0) {
int digit = number % 10;
reversedNumber = reversedNumber * 10 + digit;
number /= 10;
}
return reversedNumber;
}
public static boolean isPalindrome(int number) {
return number == reverse(number);
}
public static void main(String[] args) {
Scanner scanner = new Scanner(System.in);
System.out.print("Enter a number: ");
int number = scanner.nextInt();
if (isPalindrome(number)) {
System.out.println(number + " is a palindrome number.");
} else {
System.out.println(number + " is not a palindrome number.");
}
}
}
Read more about Java program here:
https://brainly.com/question/26789430
#SPJ1
is it true guyz!
if its true
mag handa na tayo pag totoo
kasi nabasa ko din sa bible

Answers
Answer:
wdbqdduwdhqacwuihdqwuihdowu
Explanation:
wddwddaascaca
list different power options of computer
Answers
Answer:
1. System Standby
2. System Hibernation
3. System shutdown
4. System restart
6. In terms of a career, the word benefits refers to how much vacation and salary bonuses a person gets. True False
Answers
It is false that in terms of a career, the word benefits refers to how much vacation and salary bonuses a person gets.
The term "benefits" in the context of a profession comprises a wider range of offerings supplied by a company to an employee, even if vacation and pay bonuses might be included in the benefits package.
Benefits frequently involve additional remuneration and benefits in addition to vacation time and salary increases.
Health insurance, retirement plans, paid time off, flexible work schedules, tuition reimbursement, employee assistance programmes, wellness programmes, and other benefits are a few examples of these.
The benefits package is intended to draw in new hires, keep them on board, improve job satisfaction, and support workers' health and work-life balance. Therefore, vacation time and incentive pay are just a portion of the total benefits that an employer provides.
Thus, the given statement is false.
For more details regarding career, visit:
https://brainly.com/question/8825832
#SPJ1