The language a person speaks is one example of ________________.
a.
stereotypes
b.
communication codes
c.
nonverbal communication
d.
being ‘other’ oriented
Please select the best answer from the choices provided
Answers
Answer: b. Códigos de comunicación/ comunication codes
Explanation:
Answer:
it is b
Explanation:
this is because you are communicating with each other
Related Questions
What two types of devices have a keyboard integrated into the screen?
Question 1 options:
laptops and smartphones
tablets and electric typewriters
typographers and tablets
tablets and smartphones
Answers
Answer:
tablets and smartphones
Explanation:
Have a good day!
what plugs into this?
Answers
What will be the value of number after this code is finished executing?
for i in range(100):
number = 0
A.
100
B.
0
C.
1
D.
i
Answers
The value of number given after this code is finished executing for i in range(100) will be B. 0.
What is coding?Computer code, or a set of instructions or a system of rules defined in a specific programming language, is a term used in computer programming.
Code, often known as source code, refers to text that a computer programmer has created in a programming language. Programming languages like C, C#, C++, Java, Perl, and PHP are examples. Another less formal term for text produced in markup or style languages, such as HTML and CSS, is code.
In this case, after execution for i in range(100), it will be 0 which is the number given to perform the execution.
Learn more about code on:
https://brainly.com/question/26134656
#SPJ1
The value of number given after this code is finished executing for i in range(100) will be B. 0.
What is coding?
Computer code, or a set of instructions or a system of rules defined in a specific programming language, is a term used in computer programming.
Code, often known as source code, refers to text that a computer programmer has created in a programming language. Programming languages like C, C#, C++, Java, Perl, and PHP are examples. Another less formal term for text produced in markup or style languages, such as HTML and CSS, is code.
In this case, after execution for i in range(100), it will be 0 which is the number given to perform the execution.
what is the answer i need them now pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls

Answers
Answer: Insert ribbon > table drop down menu
Explanation:
Answer:Insert ribbon > table drop down menu
Explanation:
What does this mean?

Answers
Answer:
Maybe no phones with-in the vicinity of 6 inches?
Explanation:
What do you believe about money? Do you believe that it’s hard to come by?
Answers
please describe the role of games in modern society!
Answers
In a minimum of 250 words, discuss the technological problems that can occur when consumers emphasize on speed over security.
Answers
1. Vulnerabilities and Breaches: Emphasizing speed often means sacrificing robust security measures. This can lead to vulnerabilities in software, applications, or systems that attackers can exploit. Without adequate security measures, data breaches become more likely, exposing sensitive information such as personal data, financial records, or trade secrets. The aftermath of a breach can be detrimental, including reputational damage, legal consequences, and financial losses.
2. Malware and Phishing Attacks: When speed takes precedence, consumers may overlook potential malware or phishing attacks. By rushing through security checks or bypassing cautionary measures, they inadvertently expose themselves to malicious software or fraudulent schemes. These attacks can compromise personal information, hijack devices, or gain unauthorized access to networks, resulting in financial losses and privacy violations.
3. Inadequate Authentication and Authorization: Speed-centric approaches might lead to weak or simplified authentication and authorization mechanisms. For instance, consumers may choose easy-to-guess passwords or reuse them across multiple platforms, making it easier for attackers to gain unauthorized access. Additionally, authorization processes may be rushed, granting excessive privileges or overlooking necessary access controls, creating opportunities for unauthorized users to exploit system vulnerabilities.
4. Neglected Updates and Patches: Prioritizing speed often means neglecting regular updates and patches for software and systems. By delaying or avoiding updates, consumers miss out on critical security fixes and vulnerability patches. Hackers actively exploit known vulnerabilities, and without timely updates, devices and systems remain exposed to these threats, making them easy targets.
5. Lack of Secure Development Practices: When speed becomes the primary concern, secure development practices might take a backseat. Security testing, code reviews, and quality assurance measures may be rushed or ignored, leading to the inclusion of vulnerabilities in the software or application itself. These vulnerabilities can be exploited by attackers to gain unauthorized access or execute malicious activities.
To mitigate these problems, it is essential to strike a balance between speed and security. Consumers should prioritize security measures such as using strong passwords, enabling multi-factor authentication, regularly updating software, and being cautious of suspicious links or emails. Service providers and developers must also prioritize security in their products and services by implementing secure coding practices, conducting thorough security assessments, and promptly addressing vulnerabilities. Ultimately, a comprehensive approach that values both speed and security is crucial for maintaining a safe and efficient technological ecosystem.
Explanation:
--> used brainly simplify :D
Consumers prioritizing speed over security can lead to several technological problems. This includes vulnerabilities and breaches where attackers can exploit weaknesses in software or systems. Malware and phishing attacks become more likely when security measures are overlooked. Weak or simplified authentication and authorization methods can make it easier for unauthorized users to gain access. Neglecting updates and patches leaves devices and systems vulnerable to known threats. Lastly, rushing through secure development practices may result in the inclusion of vulnerabilities in the software itself. To address these issues, consumers should use strong passwords, update their software regularly, and be cautious of suspicious links or emails. Service providers and developers should prioritize security by conducting thorough security assessments and promptly addressing vulnerabilities. Striking a balance between speed and security is crucial for a safe and efficient technological environment.
Question 8 of 10 Which of these is an example of your external influences?
a Peers
b Values
c Emotions
d Thoughts
Answers
Answer:
peers
Explanation:
values emotions and thoughts are all internal influences
What makes the Columbus
Research Laboratory
different from Earth Labs?
Answers
Answer:
The Columbus laboratory is ESA’s largest single contribution to the International Space Station. It was also the first permanent European research facility in space.
Explanation: that is something I know i don’t know if it will help you with your answer
The first person gets the brainiest!!!
Match the areas seen on the presentation program’s interface with their uses.
A. Placeholder
B. Speaker Note
C. Slide Master
D. Theme
1. default template for any new presentation
2. predefined appearance of a slide
3.used to insert the choice of items on a slide
4. guidelines that assist in delivering the presentation
Where is my Plato/ Edmentum at???
Answers
Answer:
1A
2D
3C
4B
Explanation:
:)
2 is D
3 is C
and
4 is B
Why is it important for iOS developers who have learned to program in Swift to also know Objective-C?
A. Objective C is a user interface framework for building software using iOS.
B. Objective C is the integrated development environment best suited for iOS app development.
C. Objective C is the language in which older iOS apps were written, which developers may want to upgrade.
D. Objective C is the newest programming language for building iOS apps.
Answers
How can you assess a website for currency?
a. by checking the the sites that appear at the top of the search because they're always the most current
b. by finding out how much it costs by looking at the page with pricing
c. by checking the page for dates showing when it was posted and when it was last revised
d. by looking at the “About” page to see who authored the page
Answers
Answer:
By checking the page for dates showing when it was posted and when it was last revised
Hope this helps :)
-ilovejiminssi♡
Question: How do you file a complaint using a food restaurant? 100 POINTS WILL BE GIVEN INCLUDING BRAINLIEST
Answers
send it through the mail
Answer: Be prepared to provide the following information:
1.Your Name, Address and Phone Number (your information will remain anonymous to the restaurant)
2.Name of restaurant
3.Location/address of the restaurant
4.Date of incident
5.Nature of complaint
If you suspect you became ill from this incident. You will need to give specific information about the suspected foods that made you sick, as well as when your symptoms began, and what they were. In addition, you will need to give a 3-day food eating history.
Explanation
Hello can you please help with this if you want to thank you!

Answers
REAL ANSWERS ONLY!!! BRAINLLIEST AND 50 POINTS FOR BEST ANSWER

Answers
2-Photographs allow people to see visual evidence of events, view nature in artistic ways, and tell stories with little to no words.
3-Successful photojournalists need to understand that the point of photography is to tell a story in an interesting way that will entertain and draw viewers in.
4-Photography connects people all around the world. A large group of people could view the same photo, and evaluate it in a number of different ways. These people can converse and tell each other about what they can take from the photo, and how their perspectives change the meaning of the photo.
The two that I didn't answer were up to your own opinion, so I'll let you try to figure them out yourself with the information that I gave you. :)
Walt needs to ensure that messages from a colleague in another organization are never incorrectly identified as spam. What should he do?
A.Configure a safe recipient.
B.Configure a blocked sender.
C.Configure a safe sender.
D.Do nothing.
Answers
Answer:
C. Configure a safe sender
Explanation:
It’s dabest thing to do
As per the given scenario, Walt should need to configure a safe sender. The correct option is C.
What is configuration?A system's configuration in communications or computer systems refers to how each of its functional elements is organised in relation to their nature, number, and distinguishing features.
Configuration frequently involves picking the right hardware, software, firmware, and documentation.
A person, group, or organisation that starts the communication is known as the sender. The success of the message stems primarily from this source.
The communication is influenced by the sender's experiences, attitudes, knowledge, competence, perspectives, and culture.
Walt must take care to prevent messages from a colleague in a different organisation from ever being mistakenly classified as spam. He ought to set up a secure sender.
Thus the correct option is C.
For more details regarding configuration, visit:
https://brainly.com/question/13410673
#SPJ2
Which type of cyber crime offender requires the highest percentage of risk management in terms of computer monitoring?
A) Sex offenders
B) Identity thieves
C) Low-Risk offenders
D) hackers
Answers
Answer: D
Explanation: Hackers are the only type of cyber criminal that monitors your computer
How do I mark brainlyist
Answers
Bloxburg Build can anyone help me
Answers
Why isn't my brainly post being answered?
Answers
Try deleting then reposting, it may not always pop up in new questions, I will have a look at the question anyway.
Hope this helps!
one word instructions are also known as
Answers
Online note-taking tools can help students by providing a way to study for tests. showing them how to take notes. explaining how to do homework. providing the answers to tests.
(in my logic I'd say it's "providing a way to study for tests, but I want to double check.)
Answers
Answer:
Yeah, it makes sense, but try and replace the second "providing" to avoid repetition.
Explanation:
I'd also add "familiarises them with writing on a digital support, as well as makes it easier for them to have a clear image about the lesson, creating a smooth background (on paper there are many factors that might make notes look awful)".
What happens when you try mixing colors (color3, Vector3) in tech? What happens
A. It fades with the color
B. It prints an error in output and chooses a random color
C. It reverts itself
D. It layers with a random color
E. None of the above
Answers
Answer:
A
Explanation:
When the prompt function is used in JavaScript, _____ appears.
A.
an error message
B.
a pop-up box
C.
a data warning
D.
a password request
Answers
Answer:
B
Explanation:
instructs the browser to display a dialog with an optional message prompting the user to input some text, and to wait until the user either submits the text or cancels the dialog
Hello. My Samsung tablet glitches and now its just a black screen. I've tried turning it on and off and holding down the power button but it just won't come on! Please help!
Answers
Answer:
press the volume up and down button while holding the power button, hold all three buttons til it turn on.
Explanation:
so this kinda gives the device like a reset/restart and or like it's refreshing itself!
Answer:
I tryed the 1st answer and it worked so give him brainliest.
Explanation:
Marco is writing a program in which the users will be told that they cannot enter the castle if they do not have 50 armor points. Which of the following lines of code would do that?
A.
if armor > 50:
print(“You cannot enter the castle!”)
B.
if armor = 50:
print(“You cannot enter the castle!”)
C.
if armor == armor:
print(“You cannot enter the castle!”)
D.
if armor < 50:
print(“You cannot enter the castle!”)
Answers
Answer:
D
Explanation:
the sign “<“ means the mouth would eat the bigger one. When you put it in it will allow you to go in the castle if you have MORE then 50
I hope it correct and it helps!
Answer:
d
Explanation:
the sign “<“ means the item on the left side is smaller than the item on the right.
Everything that you see on a computer screen is a representation of which of the following?
A.
floats
B.
0s and 1s
C.
database messages
D.
flowchart input
Answers
Answer:
B
Explanation:
coding and programming for the computer to something on command (pressing keys etc)
Answer:B
Explanation:
Part 1: Compare the Websites
You are conducting research for a project about elephant sanctuaries. Compare the two websites using the 5 W’s criteria for reliability and validity. For each website, complete the 5 W’s Checklist.
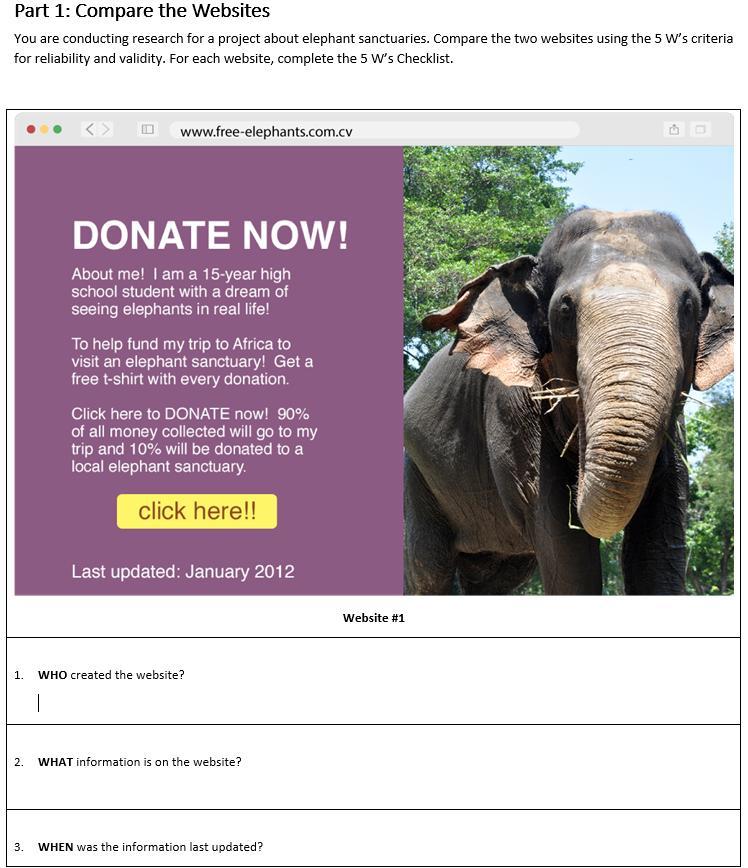




Answers
Answer:
WHO: a 15-year old high school student
WHAT: information about donating to a local elephant sanctuary and a trip
WHEN: January 2012
WHERE: www.free-elephants.com.cv
WHY: To help fund the student's trip to Africa to visit an elephant sanctuary
who: a 15-year-old high school student
what: information about donating to a local elephant sanctuary and a trip
when: January 2012
where: www.free-elephants.com.cv
why: To help fund the student's trip to Africa to visit an elephant sanctuary
What are the different types of software? Give one example