the httpservletrequestwrapper and httpservletresponsewrapper classes implement a design pattern known as the .
Answers
The HttpServletRequestWrapper and HttpServletResponseWrapper classes implement a design pattern known as the Decorator pattern.
This pattern allows for adding additional functionality to an object dynamically at runtime by wrapping the original object in a new object that has the same interface but with added behavior. In the case of these wrapper classes, they allow for modifying or adding functionality to the HTTP request or response objects that are passed between the client and server in a web application.
The decorator pattern is a design pattern used in object-oriented programming that enables the dynamic addition of behavior to a single object without changing the behavior of other objects belonging to the same class.
Example. A dynamically added responsibility is attached to an object by the decorator. Examples of decorators are the ornaments placed on pine or fir trees. A tree can be decorated with lights, garland, candy canes, glass ornaments, and other holiday accents.
To know more about Decorator pattern, click here:
https://brainly.com/question/22881463
#SPJ11
The HttpServletRequestWrapper and HttpServletResponseWrapper classes implement a design pattern known as the Decorator pattern.
The Decorator pattern is a structural design pattern that allows the addition of behavior to an object dynamically. In this pattern, a decorator class wraps the original class and adds additional functionality without changing the existing code. The HttpServletRequestWrapper and HttpServletResponseWrapper classes are used to enhance the functionality of the HTTP servlet request and response objects respectively. These classes are provided as part of the Java Servlet API to enable developers to modify and extend the behavior of these objects. The HttpServletRequestWrapper and HttpServletResponseWrapper classes are subclasses of the corresponding request and response classes and provide an interface for modifying the request and response objects. These classes are typically used to intercept and modify incoming requests or outgoing responses before they are processed or sent to the client. The Decorator pattern implemented by the HttpServletRequestWrapper and HttpServletResponseWrapper classes allows developers to add functionality to the HTTP servlet request and response objects without modifying the existing code. This pattern enables the creation of flexible and extensible software systems that can adapt to changing requirements and user needs.For such more questions on design pattern
https://brainly.com/question/31477342
#SPJ11
Related Questions
HELP ASAP
Select the correct answer.
When designing an algorithm, what structure can be used to repeat some steps if a condition is met?
OA. iterations
OB. loops
OC. conditional
OD. flowcharts
OE. pseudocode
Answers
Answer:
B. loops
Explanation:
The while loop is used to iterate over a portion of code until a certain condition is fulfilled. Let's imagine we want to know how many times a number may be divided by two before it becomes less than or equal to one.
What are the disadvantages of discovery procedures, and how can they be avoided?
Answers
Discovery procedures are an integral part of the pre-trial discovery process. This procedure allows parties to collect evidence and gain information from each other that is necessary for the resolution of the dispute.
Despite its importance, there are several disadvantages of discovery procedures that must be considered. Here are some of the disadvantages of discovery procedures and how they can be avoided:
1. Cost: One of the main disadvantages of discovery procedures is that it can be expensive. The cost of discovery can be significant, particularly in complex cases where there is a lot of information to be gathered. To avoid the cost of discovery, parties can try to negotiate a settlement before discovery or limit the scope of discovery.
2. Delay: Discovery can cause significant delays in the trial process. The amount of time it takes to complete discovery can vary depending on the complexity of the case, the amount of information to be gathered, and the cooperation of the parties involved. To avoid delay, parties can agree to limit the scope of discovery or use alternative dispute resolution methods, such as mediation or arbitration.
3. Privacy concerns: Discovery can involve the disclosure of sensitive information that parties may not want to be made public. To avoid privacy concerns, parties can request protective orders to limit the disclosure of certain information or agree to keep sensitive information confidential.
4. Abuse: Discovery procedures can be abused by parties who seek to harass or intimidate the other party or cause unnecessary delay. To avoid abuse, courts can impose sanctions on parties who engage in abusive behavior during the discovery process.
In conclusion, although discovery procedures are an essential part of the litigation process, there are several disadvantages that must be considered. Parties can take steps to minimize these disadvantages by negotiating a settlement, limiting the scope of discovery, using alternative dispute resolution methods, requesting protective orders, and avoiding abusive behavior.
Learn more about pre-trial discovery process here:-
https://brainly.com/question/32149735
#SPJ11
Martin is trying to add a new feature to his website. He has created the feature, tested it, and now wants to deploy it on the web server. What precautions should he take before deploying the new feature?
Martin should make a
of all data on the server, so if the deployment fails, he can restore the website from the backup.
Answers
To restore data from an iCloud backup, select Set Up Manually, then adhere to the on-screen directions.
What is Backup?Follow the onscreen directions after bringing the two devices close together to securely copy most of your settings, preferences, and iCloud Keychain.
The remainder of your data and content can then be restored to your new smartphone from your iCloud backup.
Alternatively, you can wirelessly transfer all of your data from your old device to your new one if both of them run iOS 12.4, iPadOS 13, or a later version.
Therefore, To restore data from an iCloud backup, select Set Up Manually, then adhere to the on-screen directions.
To learn more about Backup, refer to the link:
https://brainly.com/question/29590057
#SPJ1
Answer:backup
Explanation:
Type the correct answer in the box. Spell all words correctly.
Complete the sentence explaining the privileges of being a part of a specific group or organization.
Being a registered member of a
council or organization gives you free access to on-campus facilities.
Reset
Next
Answers
Membership in a council or organization comes with an array of benefits, such as the chance to interact with individuals who share similar interests, privileged admission to exclusive gatherings and assets, and the power to influence the direction and objectives of the collective.
What are the other benefits?Moreover, numerous establishments provide reduced rates or complimentary admission to amenities located on campus, such as fitness centers, libraries, or workspaces, enabling individuals to utilize these resources without bearing extra expenses.
Becoming a member of a group or organization can furnish individuals with useful networking chances and enable them to gain crucial expertise and exposure that can have advantageous impacts in both their personal and professional domains.
Read more about group members here:
https://brainly.com/question/21277404
#SPJ1
To step through a program, what status indicator light needs to be on?
Answers
Answer: It should always stay on normal
Explanation:
Hope this helped :)
What is the name of the final version of software when all design requirements have been met?
Answers
Answer: Alpha Version
Explanation: Yes, definitely you need one apart from SRS.
How do i fix this? ((My computer is on))

Answers
Answer:
the picture is not clear. there could be many reasons of why this is happening. has your computer had any physical damage recently?
Answer:your computer had a Damage by u get it 101 Battery
and if u want to fix it go to laptop shop and tells him to fix this laptop
Explanation:
a coder is assigning a code for an IM injection of a
therapeutic medication. She finds the vode for the injection itself
in the CPT manualbut is unsure how to proceed from there. The coder
should;
Answers
When a coder finds the code for an IM injection of a therapeutic medication in the CPT manual, the next step is to ensure accurate documentation of the specific details related to the injection, such as the medication administered, dosage, and any additional procedures or services performed during the encounter.
Once the coder has located the code for the IM injection in the CPT manual, it is crucial to review the code description and associated guidelines. This helps ensure that the coder understands the specific requirements for reporting the code accurately.
Next, the coder should gather all relevant information from the medical documentation. This includes the name and dosage of the therapeutic medication administered, any additional services or procedures performed during the encounter, and any applicable modifiers required to accurately describe the injection.
By carefully reviewing the code description, following the guidelines, and accurately documenting all pertinent details, the coder can correctly assign the code for the IM injection of the therapeutic medication. This process helps ensure accurate coding and billing for the specific healthcare service provided.
learn more about coder here
https://brainly.com/question/19379706
#SPJ11
Write a Python program in codehs, using post-test while loop, to print the powers of 2 less than one million, starting from 2 to the power of 0.
Hint: Recall from Python Basics Math Operators Unit that ** is the exponentiation operator.
Usage: To find 10 to the power of 5, do 10 ** 5 in Python.
Paste your program in the space provided below, after you test its functionality in codehs.
Answers
This loop will print out the powers of 2 (2^0, 2^1, 2^2, etc.) until it reaches 2^power which is greater than 1 million. The power variable is incremented by 1 each time the loop runs which allows us to keep track of which power of 2 we are at.
What is the variable ?A variable is a named memory location used to store a value that can be changed during the execution of a program. Variables are essential to programming, as they allow programmers to store and manipulate data during the execution of a program. Variables are typically declared with a specific data type, such as an integer or string, and they are assigned a unique name so they can be accessed and manipulated within the program.
#Start
power = 0
while 2**power < 1000000:
print(2**power)
power += 1
#End
To learn more about variable
https://brainly.com/question/29360094
#SPJ1
independence day in school long passage plss
Answers
Answer:
Independence Day Celebration in My School
Fifteen August, is a red letter day in the history of India. On this day in 1947, our country become free form the long imprisonment of the British rule. Since 1947, fifteenth August is celebrated every year with great joy and pride. It reminds us for the great struggle of our freedom from the British rule. The great sacrifice for our freedom fighters is remembered, which serves as a beacon light for the development of this great country. The main function is held at Red Fort in Delhi where the Prime Minister unfurls the National flag. It is an occasion of celebration for every Indian and the whole nation celebrate a holiday from all work and take a pledge to work whole heatedly for the development of this country and preservation of Independence. All those who have stood out exclusively in their respective field of work are honored in public meetings. The whole nation pays homage to the security forces who have laid down their lives for the honor and security of the country.
We also celebrated the Independence day in our school compound, with great pump and show. The school building and the ground were cleaned and decorated for the occasion. A flag pole was put up at the top of the school building. The seating arrangement was made on the platform. Markings were made on the ground with white lines. The flower pots were kept all along the path.
There was great enthusiasm among students. The school band of students took its position half an hour before the actual function was to began. The members of the band were wearing a beautiful uniform. They began to play sweet tunes. The students had taken their places well before the time. They were all in school uniform, the white paint and white shirt.
The function began exactly at 8 a.m. all who were present stood in attention. The principal unfurled the flag. The petals of rose fell on us. Five boys sang a song in honor of the national flag. It was “Vijayee Vishwa Trianga Payara”. Them by the school band. The principal look the salute. He made an impressive speech and invited the Education Minster to impressive speech and invited the Education Minster to address us. In his address he asked us to take pledge to safeguard the freedom of nation. He also reminded us of great sons of India, Mahatma Gandhi, Pt. Nehru, Subhash Chandra Bose, Lala Lajpat Roy and Chander Shekar Azad and their sacrifices to the nation. After that different groups of students presented a programme of mass drill and pyramid formation. Ever one liked the programme.
In the end, all stood in attention. All the students, teachers and guardians sang the National Anthem in chorus. With this the function was over. Today the memories of this function are as alive to me, as it was on that day.
A for construct is a loop construct that processes a specified list of objects. As a result, it is executed as long as there are remaining objects to process. True or false?
Answers
The for loop will always execute as long as there are remaining objects to process. It's a true statement.
What is a for loop?A for loop is used to do something repeatedly.
The for loop iterate over an items.
In a simpler term, the for loop is used to repeat a section of code known number of times.
Therefore, a for construct is a loop construct that processes a specified list of objects.
As a result, it is executed as long as there are remaining objects to process is a true statement.
learn more on for loop here: https://brainly.com/question/2374898
#SPJ2
You are configuring a switch that has three hosts attached to FastEthernet 0/2 through 0/4. All three hosts are part of a public kiosk display that allows guests to access the internet. You would like to implement port security to prevent guests from removing Ethernet cables from the hosts and connecting them to the Ethernet ports on their personal laptops. If guests attempt to connect through their personal laptops, you would like the switch to drop the frames.
Complete the following tasks:
. Configure FastEthernet 0/2 through 0/4 as access ports.
. On the FastEthernet 0/2 through 0/4, configure port security to learn and retain the MAC addresses of the connected hosts.
. Configure the port security violation as protect on each applicable interface.
. Save your changes to the startup-config file.
Answers
To prevent guests from connecting their personal laptops to the public kiosk display, you can configure port security on the switch. Follow these steps:
1. Configure FastEthernet 0/2 through 0/4 as access ports:
```
interface FastEthernet 0/2
switchport mode access
interface FastEthernet 0/3
switchport mode access
interface FastEthernet 0/4
switchport mode access
```
2. Enable port security and configure it to learn and retain MAC addresses:
```
interface FastEthernet 0/2
switchport port-security
switchport port-security mac-address sticky
interface FastEthernet 0/3
switchport port-security
switchport port-security mac-address sticky
interface FastEthernet 0/4
switchport port-security
switchport port-security mac-address sticky
```
3. Configure the port security violation mode as "protect" on each applicable interface:
```
interface FastEthernet 0/2
switchport port-security violation protect
interface FastEthernet 0/3
switchport port-security violation protect
interface FastEthernet 0/4
switchport port-security violation protect
```
Remember to save your changes to the startup-config file to make them persistent:
```
copy running-config startup-config
```
In summary, by configuring the FastEthernet interfaces as access ports, enabling port security to learn and retain MAC addresses, and setting the port security violation mode to "protect," you can prevent guests from connecting their personal laptops to the public kiosk display. This ensures that only the authorized MAC addresses are allowed to communicate through the switch ports. Any attempts to connect unauthorized devices will result in the switch dropping the frames, effectively restricting network access.
Learn more about port security.
brainly.com/question/32221403
#SPJ11
1. For loop is used for repeating over a sequence, that is either a ___________ or _________________
Answers
Answer:
For loop is used for repeating over a sequence, that is either a list, tuple, dictionary, or a set.
8.4.11 code hs help me please
Answers
Code HS is an online platform that provides resources for learning how to code and developing computer science skills. It offers courses and exercises in a variety of programming languages, including Java, Python, and JavaScript.
To better assist you with your question, could you please provide more information about what specifically you need help with related to 8.4.11 code HS. To complete CodeHS 8.4.11, you need to write a program that reads a list of integers, stores them in an ArrayList, and then prints the sum of the integers.
Here is a step-by-step explanation to solve this problem.
1. Import the required libraries:
java
import java.util.ArrayList;
import java.util.Scanner;
2. Create a Scanner object to read the input:
java
Scanner scanner = new Scanner(System.in);
3. Create an ArrayList to store the integers:
java
ArrayList numbers = new ArrayList<>();
To know more about programming visit:
https://brainly.com/question/11023419
#SPJ11
Information is defined as being data organized in a meaningful way that is useful to the user.
a. true
b. false
Answers
Answer:
The statement is true
Explanation:
The given statement exists true. Data is defined as being information organized in a meaningful way that is useful to the user.
What is meant by data?Data is a collection of discrete values that convey information, such as quantity, quality, fact, statistics, or other basic units of meaning, or simply sequences of symbols that can be interpreted further in the pursuit of knowledge. A datum is a single state within a data set.
Data is information that has been efficiently converted into a form suitable for movement or processing. In the context of today's computers and transmission media, data is information that has been converted into binary digital form. It is fine to use data as a singular or plural subject.
Data is defined as information that has been organized in a meaningful way for the user to use. A value chain is the cost of carrying out various activities within a business. Predictive value, feedback value, and timeliness are all characteristics of relevant information.
To learn more about data refer to:
https://brainly.com/question/26711803
#SPJ4
A technician is checking a customer's wireless network performance and has determined it was using 802.11g. The technician's recommendation is for the customer to upgrade to 802.11ac. Which of the following is the BEST reason to upgrade?
Answers
Answer:
Spped
Explanation:
How does the rhythm of "The Raven" compare to "Casey at the Bat?"
Answers
Answer:
Casey at the Bat: A Ballad of the Republic Sung in 1888' is the full title of an American poem written by Ernest Lawrence Thayer. The poem tells the story of the final half-inning of a baseball game. ... Not only is it a love song to the dramatic sport of baseball, but it is a ballad to 'the Republic in 1888'.
Which HTML tag is formatted correctly?
NEED ANSWER ASAP PLZ HELP ME IDONT UNDERETAND IT
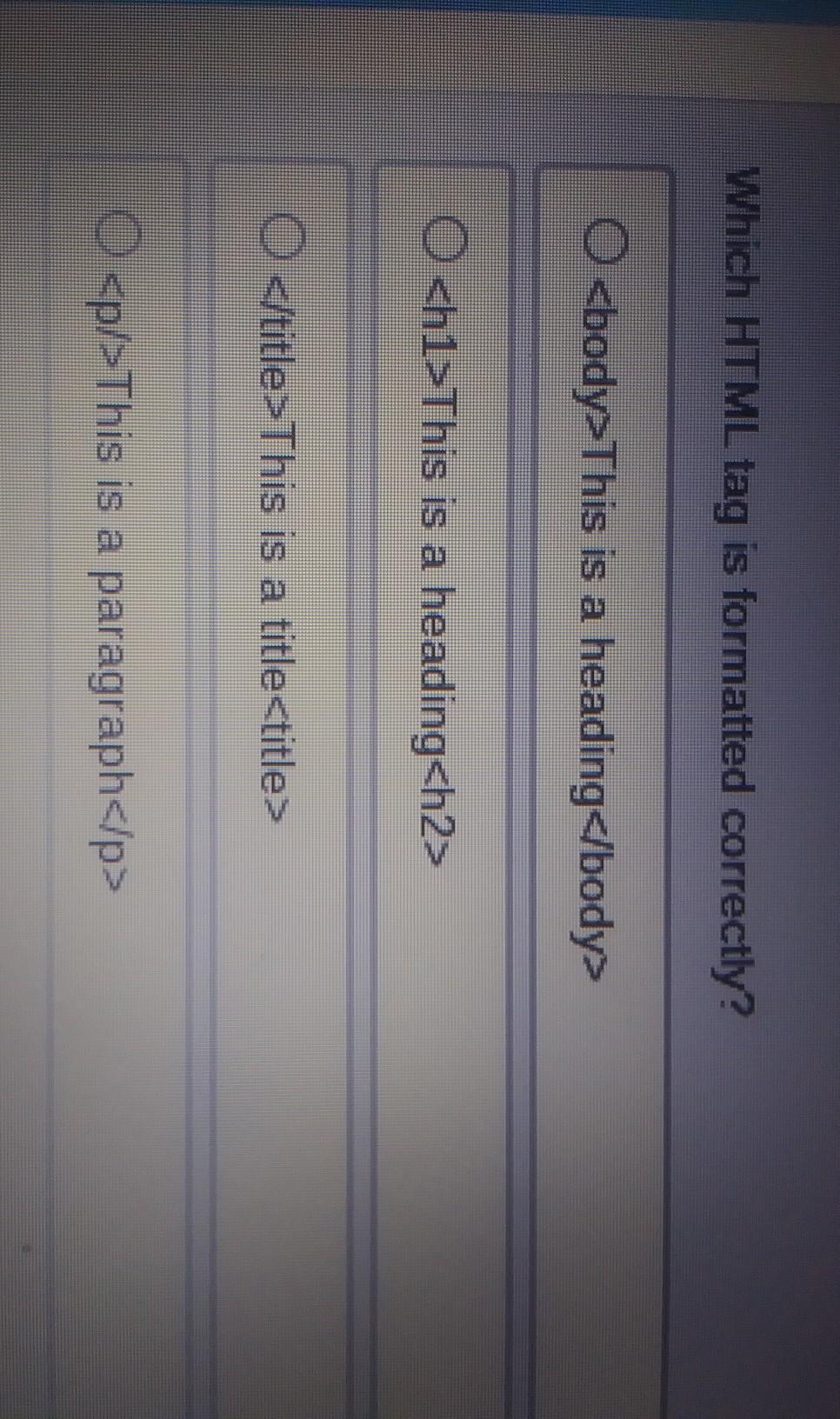
Answers
I think the last one is the correct one
Answer:
D
Explanation:
All others don't work
9. Alice Builds a Cache Complete the blanks in the following question with the appropriate answer. Alice P. Hacker has two types of memory that she's using to build his system in which to store her objects. The first type, type A, is extremely fast, but it's expensive and she doesn't have much of it. She has 10GB of type A memory that can being used to store A objects, and reading an object from this memory takes 1ms. The second type of memory, type Z, is a lot slower, but it's cheap, and so Alice bought a lot of it. She has 1TB of the second type of memory that she can use to store objects, and reading an object from this memory takes 100ms. Alice decides she's going to build a system where she keeps all of her objects in the second type of memory, and then also keeps copies of some of those objects in the first type so that she can do some of her reads more quickly. Alice has 2048 objects, all of the same size, which use up all of her second type of memory storage. Alice decides to analyze different ways to pick and choose what she keeps in her type A memory, and how they affect her expected object read performance. Please round all answers to 3 decimal places If Alice is naive and decides to randomly fill her type A memory with objects and never change it, what is her expected time to read 10 randomly selected objects out of the 2048 (in ms)? ms Alice now runs a workload where she reads 20 objects per minute. 50% of the objects she reads are objects she's seen in the past 30 seconds, and the other 50% of the objects are randomly chosen from the full 2048. Using the same naive strategy as before, what is her expected average read time for an object with this workload? ms Alice tries to improve her performance. She decides that every time she reads an object, if it is not in her type A memory, she will put it there. When she needs to remove something, she will remove the thing that she read least recently. What is Alice's average read time per object in the best case scenario? ms What is Alice's average read time per object in the worst case scenario? ms
Answers
If Alice is naïve and decides to randomly fill her type A memory with objects and never change it, her expected time to read 10 randomly selected objects out of the 2048 would be 50ms.
What is the Cache about?With the workload of reading 20 objects per minute, where 50% of the objects are objects she's seen in the past 30 seconds, and the other 50% are randomly chosen from the full 2048, her expected average read time for an object with this naive strategy would be 75ms.
If Alice decides to improve her performance by putting an object in her type A memory every time she reads it and removing the least recently read object when she needs to remove something, in the best case scenario, her average read time per object would be 1ms.
Therefore, In the worst case scenario, her average read time per object would be 50.5ms.
Learn more about Cache from
https://brainly.com/question/6284947
#SPJ1
Binary is represented by two digits, write out each and describe what each means:
Answers
Answer:
binary is represented by 1 and 0
Explanation:
the binary of 1 means it has value, and the binary of 0 means it has no value. with a combination of 1s and 0s, you can get a complex program to run, like this platform :) what it basicly does is a true or false kinda think. just think of it that way: true or false, value or no value, and yes or no. the 1 is a positive value and the 0 is a negative value that has no value.
I hope this helps you :D
In binary, the 0s and 1s signify OFF and ON, respectively.
What do the binary numbers 1 and 0 represent?In binary, the 0s and 1s signify OFF and ON, respectively. A "0" in a transistor indicates that no electricity is flowing, while a "1" indicates that electricity is flowing.
Numbers are physically represented inside the computing equipment in this fashion, allowing calculations.
Learn more about binary numbers here:
https://brainly.com/question/13371877
#SPJ4
briefly explain the emerging trends in micro computer technology according to size
Answers
Answer:
Emerging trends in IT include big data analytics, virtual and augmented reality, 5G, and the internet of things. Computer science workers can learn about computer science current events and new technologies by joining a professional organization.Mar 3, 2022
Why won't my brainly account level up?
Answers
Well, you need to have 5 brainiest answers plus 500 points. So, in order to level up in brainly you need 500 plus 5 brainiest.
What is brainly?Brainly is a Polish company with headquarters in New York City. It is a social learning platform where millions of students and teachers work together to solve academic problems. The mission of Brainly is to encourage students to share and explore knowledge in a collaborative environment.
It can also be used to ask and answer homework questions by students, parents, and teachers. The platform includes n elements such as points and ranks. It encourages users to participate in the online community by answering questions posted by other users. Brainly reported 350 million monthly users as of November 2020, making it the most popular education app in the world.
Learn more about level up
https://brainly.com/question/7853380
#SPJ1
Answer:
This is because to level up, you need a certain number of points and brainliest answers! To get this you can always keep answering questions to get your points up and whenever you complete an answer which is superior than any other, the user may choose to give you brainliest!
Hope this helps, have a lovely day! :)
PHOTOGRAPHY: In 200 words or more explain the difference between deep and shallow depth field and when would you use either technique when taking a photograph?
Answers
The differences are:
A shallow depth of field is said to be a small area in view and its background is always blurred but a A deep depth of field is known to be one that captures a bigger area in view and its image are said to be sharp and clear.What is the difference between deep and shallow focus?The Images gotten in shallow focus is one that needs little or shallow depths of field, and its lenses also needs long focal lengths, and big apertures. But Deep focus images needs small focal lengths and long depths of field.
In the case above i recommend deep depth field and therefore, The differences are:
A shallow depth of field is said to be a small area in view and its background is always blurred but a A deep depth of field is known to be one that captures a bigger area in view and its image are said to be sharp and clear.Learn more about photograph from
https://brainly.com/question/13600227
#SPJ1
If a spreadsheet user wants Calc to add a range of cells, what built-in function should he or she use?
A) the ADD function
B) the OPR function
C) the SUM function
D) the WIZARD function
Answers
Answer: Its C
Explanation:
If you were creating your own website, what would you include to make sure your website was reliable and
valid?
Answers
Answer:
I would make sure to include all the sources i used? IT depends on what the website is about.
Explanation:
Hey there!
These are the best things to do to your website if you want to make sure it's reliable and valid:
Include research Do NOT include any biased opinionsHope this helps!
Have a great day! :)
T/F the msba tool can quickly identify missing patches and misconfigurations.
Answers
True, the Microsoft Baseline Security Analyzer tool can quickly identify missing patches and misconfigurations. This tool helps users maintain a secure and up-to-date system.
This article in our series on Microsoft’s free security tools is focused on a tool called the Microsoft Baseline Security Analyzer (MBSA). Many years ago before Windows Update was available, servicing software was much more painful than it is today. Microsoft released security updates weekly, and there were few deployment technologies available to help determine which systems needed which updates. For those IT administrators that lived through those days, the MBSA was a godsend. Today, 10 years later, the MBSA is still a free security tool that many, many IT Professionals use to help manage the security of their environments.
The MBSA is an easy-to-use tool designed for IT professionals and helps small and medium-sized businesses determine their security state in accordance with Microsoft security recommendations and offers specific remediation guidance. It is a standalone security and vulnerability scanner designed to provide a streamlined method for identifying common security misconfigurations and missing security updates. MBSA is used by many leading third-party security vendors and security auditors and, on average, scans over 3 million computers each week.
learn more about Microsoft Baseline Security Analyzer here:
https://brainly.com/question/17267870
#SPJ11
After evidence is discovered in logs or alerts, how long does it typically take for someone in a firm to discover there is a security compromise in a system
Answers
After evidence is discovered in logs or alerts, it typically takes 197 days for someone in a firm to discover there is a security compromise in a system. According to the 2020 IBM Cost of a Data Breach report, it takes an average of 197 days for a company to recognize and identify a data breach.
A step-by-step explanation of this is as follows:
Companies must first identify potential compromises within their networks and systems. Alerts or logs will often reveal evidence that something is wrong within the system.
Investigations must then be carried out to determine the root cause of the warning. This can take some time since many factors, such as the system's complexity and the magnitude of the breach, may affect the amount of time it takes for the investigation to be completed.
Once the investigation is complete, the company may decide to alert the appropriate authorities, assess damages, and take remedial action to mitigate future breaches. The whole process can take weeks or even months, depending on the nature of the breach, the time and resources available, and the procedures in place to ensure proper response to data breaches.
Know more about the networks and systems click here:
https://brainly.com/question/30650307
#SPJ11
What is the HP Pavilion laptop?
Answers
Consumer-focused laptops and desktops are part of HP Inc.'s Pavilion series. In 1995, Hewlett-Packard released it. Both laptops and desktops go by this designation.
Why do laptops wear out so quickly?Performance-wise, a better gaming laptop should last five years or so. Choose a laptop that performs as well as or better than a console. The GPU has the biggest impact on a gaming laptop's lifespan. Spend your cash where it counts the most because the majority of gaming laptops hardware isn't upgradeable.
What distinguishes a gaming laptop from a standard laptop?A video card, a computer component designed to improve the quality of visuals displayed on a screen, is a feature of gaming PCs. A conventional PC typically uses an inbuilt graphics processor and fans in place of separate RAM, a Gpus, and just a cooling system.
To know more about laptop visit:
https://brainly.com/question/271859
#SPJ1
Select the correct text in the passage.
Select the sentence that is not the correct use of technology in parenting.
Technology has helped parents to access a vast information resource due to the presence of the internet. They can show a range of education
material like nursery rhymes, stories, scientific concepts, and so on conveniently on their smartphones. Teachers can coordinate with the
parents about the child's progress due to smartphones and various applications on it. Some parents have replaced the customary practice of
reading a bedtime story to children with a television show of the child's choice.
Reset
Next
Answers
Answer:
some parents have replaced the customary practice of reading a bedtime story to childern with a television show of the child's choice
Explanation:
Drive
0101
0102
0103
0104
0105
0106
0107
0108
0109
0110
0111
0112
0113
0114
0115
0166
Sorting Minute
True
102
162
165
91
103
127
112
137
102
147
163
109
91
107
93
100
An Excel table can help
you organize your data in
preparation for using it
with charts and other
analysis tools.
Copyright © 2003-2022 International Academy of Science. All Rights Reserved.
False
Answers
Answer:
What
Explanation:
True