. suppose that the roundtrip delay between sender and receiver is constant and known to the sender. would a timer still be necessary in protocol rdt 3.0, assuming that packets can be lost? explain.
Answers
Yes, a timer would still be necessary in protocol rdt 3.0 even if the roundtrip delay between sender and receiver is constant and known to the sender.
This is because packets can still be lost in transit due to various reasons such as network congestion, hardware failures, or interference. The purpose of the timer in rdt 3.0 is to ensure that the sender retransmits the packet if it does not receive an acknowledgment (ACK) from the receiver within a certain time period. This helps to ensure that the packet is successfully delivered to the receiver even if it was lost in transit. Even though the roundtrip delay is constant and known, the packet may still be lost in transit due to network congestion or other factors.
In summary, the timer is necessary to ensure that the packet is retransmitted in case of such an event. This helps to improve the reliability of the communication between the sender and receiver, which is a key objective of rdt 3.0.
To learn more about Roundtrip Delay :
https://brainly.com/question/27217941
#SPJ11
Related Questions
___________________ is the act of protecting information and the systems that store and process it.
Answers
Information systems security is the act of protecting information and the systems that store and process it.
What do you mean by information systems?
A formal, sociotechnical, organizational structure called an information system is created to gather, process, store, and distribute information. Four elements make up information systems from a sociotechnical standpoint: task, people, structure, and technology.
In the field of information systems, issues affecting businesses, governments, and society are resolved through the efficient design, delivery, and use of information and communications technology. The four phases of planning, analysis, design and implementation must be completed by all information systems projects.
To learn more about information systems, use the link given
https://brainly.com/question/20367065
#SPJ1
Examples of hardware that computes on a network can share are the operating system and the web browsers
Answers
Answer:
False.
Explanation:
The hardware component of a computer can be defined as the physical parts or peripherals that enables it to work properly. Some examples of hardware components are monitor, speaker, central processing unit, motherboard, hard-drive, joystick, mouse, keyboard, etc.
A software component of a computer comprises of software application or program that are used by the computer to manage or control software application, computer hardware and user processes. Some examples of software components are operating system, registry keys, antivirus, media player, word processor, etc.
In conclusion, the hardware components of a computer are the physical parts that can be seen and touched while the software components cannot be touched but rather are installed as a program.
Hence, examples of software but not hardware that computers on a network can share are the operating system and the web browsers
what is a microphone
Answers
Answer: It is a piece of tech that's used for recording audio
Explanation:
The definition of a "project" is multiple tasks help accomplish an end result many activities connected in series buildings and streets in a city activities in a network none
Answers
The definition of a "project" is multiple tasks help accomplish an end result.
A project can be defined as a temporary endeavor that involves a set of planned and coordinated activities aimed at achieving a specific goal or end result. It typically consists of multiple tasks that are interconnected and contribute to the overall objective. Projects are characterized by their unique nature, defined scope, limited duration, and specific deliverables. The tasks within a project are organized in a logical sequence or series, and their successful completion leads to the achievement of the desired outcome.
To know more about project click here,
https://brainly.com/question/28476409
#SPJ11
the technique of __________ is necessary to refine the structure of a relational database model to optimize its efficiency and maintainability.
Answers
The technique of database normalization is necessary to refine the structure of a relational database model to optimize its efficiency and maintainability.
Database normalization is a process used to eliminate redundancy and improve the organization of data in a relational database. It involves breaking down larger tables into smaller, more focused tables and establishing relationships between them using primary and foreign keys.
By doing so, normalization reduces data duplication, improves data integrity, and allows for efficient querying and updating of the database. It helps to eliminate data anomalies and inconsistencies, making the database easier to maintain and modify over time. Therefore, database normalization is essential for optimizing the efficiency and maintainability of a relational database model.
You can learn more about database normalization at
https://brainly.com/question/30002881
#SPJ11
Individuals connect to the Internet through an __ (1) __ allowing them access to the system. The rules on the Internet for how messages are addressed and passed on are called __ (2) __ .
Answers
Answer:
1. Internet service provider (ISP)
2. Protocols.
Explanation:
Individuals connect to the Internet through an Internet service provider (ISP) allowing them access to the system. An ISP is a telecommunication company that provides internet services for other internet providers i.e they act as a backbone.
The rules on the Internet for how messages are addressed and passed on are called protocols.
A protocol can be defined as a standard set of rules established by the regulatory agencies to determine how data are transmitted from one network device to another.
Generally, the standard Internet communications protocols which allow digital computers to transfer (prepare and forward) data over long distances is the TCP/IP suite.
What does it take to get banned from a website like this one? IF moderators could answer that would be awesome. Also what type of things do you have to deal with on a regular basis? (this is for a writing prompt in one of my computer classes and says to cite evidence)
Answers
Answer:
To be banned of this site you would have to do 3 of the following or similar....
1. Ask questions that aren't really questions...(ex. What is 2+2...Do ya'll want free points).
2. Spamm the "ask the question"
3. Answer the question with a half answer.
You only have to deal with question limit which is 15...unless you start answering questions then there is no limit. But make sure you don't loose your answering streak cause then it gives you the answering streak.
Explanation:
In order to link to another page on your web site, you need to know the target page name and:
a
The name of your web server
b
The character encoding of the target page
c
The numeric address of the target location
d
The path to the target page from your current page location
Answers
Answer:
I belive it would be D or C
Explanation:
Thats the only 2 answeres that would logically make since
how to create an e mail account
Answers
Answer:
Go into setting; go to accounts; look for create account or add account; it will then come up with a tab asking what you want to create the for ( choose Email) it will ask who you want to create it for (yourself or Bussiness), you choose whichever you want and then fill in your information.
Hope this helps....
Explanation:
when changing the code to the generic array list implementation, all indexed-based array accesses needed to be modified. why? check all that apply group of answer choices
Answers
The options that apply are: The array changed its name and Indexed-based array code dereferences a void pointer in this implementation, which is NOT allowed
When changing the code to a generic array list implementation, the array may have changed its name, requiring updating all references to the array in the code. Additionally, if the new implementation uses a different data structure or approach, indexed-based array accesses may no longer be valid and could result in dereferencing a void pointer, which is not allowed in many programming languages. In such cases, the indexed-based array accesses would need to be modified to comply with the new implementation.
However, the other options listed do not necessarily apply. It is not clear that writing more complicated code is always better, and it is possible that the changes were needed for other reasons. Similarly, it is not clear that the array was out of bounds or that no changes were really needed - it depends on the specific details of the code and the new implementation.
Learn more about the generic array list implementation here: https://brainly.com/question/20313495
#SPJ4
Your question is incomplete; the full question is:
When changing the code to the generic array list implementation, all indexed-based array accesses needed to be modified. Why? Check all that apply
The array changed its name
No changes were really needed - it was just an exercise to show how to access array elements differently
The array was out of bounds
Indexed-based array code dereferences a void pointer in this implementation, which is NOT allowed
It is better to write more complicated code
5. Why is adaptability important in the workplace?
Answers
Answer:
because u can adapt a job
Explanation: hmmhmhmmhmhmhmmhhm
THIS HELPS RIGHT??????
Helppppp meeeeee eee
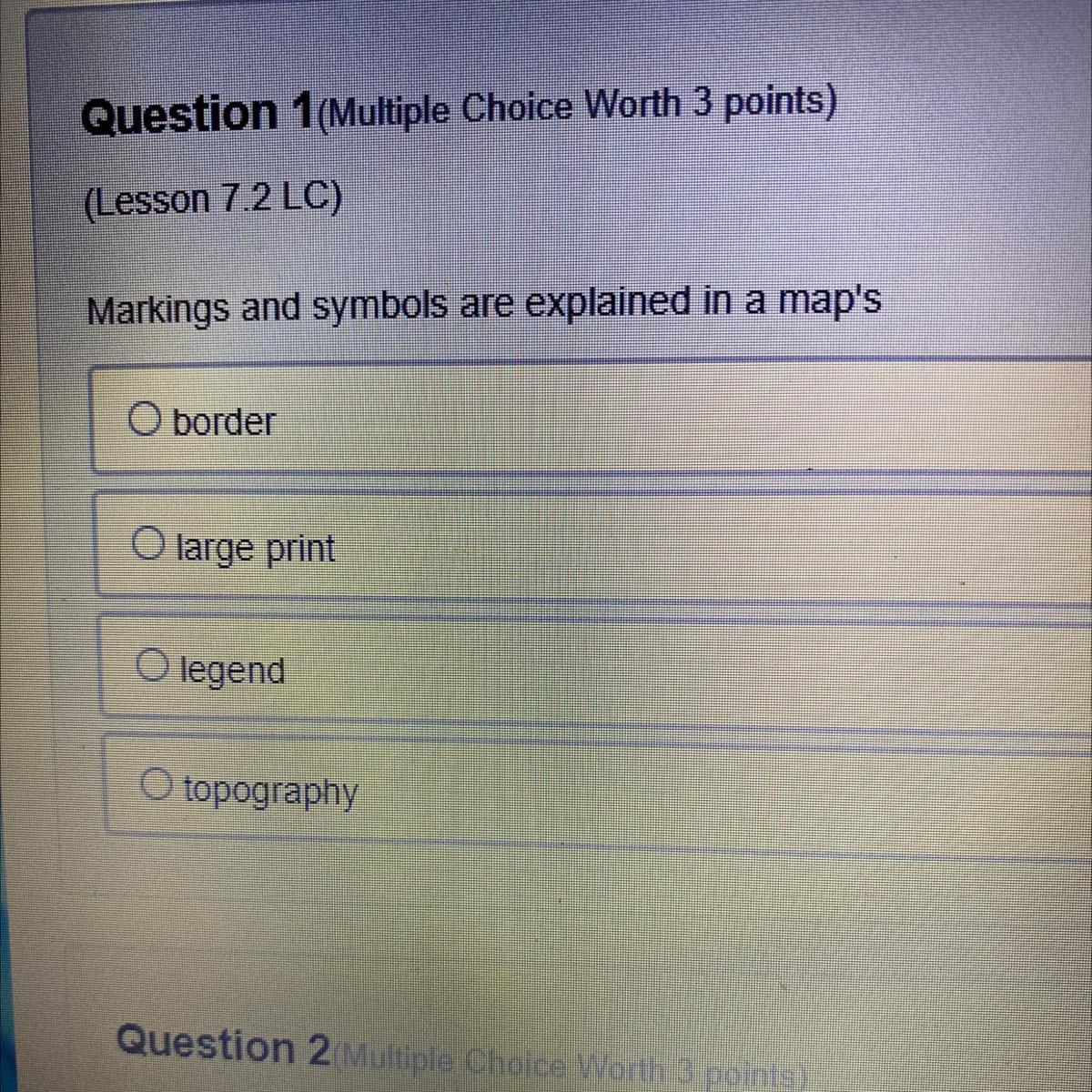
Answers
Answer:
Option C is correct
Explanation:
A map legend or key is a visual explanation of the symbols used on the map. It typically includes a sample of each symbol (point, line, or area), and a short description of what the symbol means.
You manage the information systems for a large manufacturing firm. Supervisory control and data acquisition (SCADA) devices are used on the manufacturing floor to manage your organization's automated factory equipment. The SCADA devices use embedded smart technology, allowing them to be managed using a mobile device app over an internet connection. You are concerned about the security of these devices. What can you do to increase their security posture? (Select two.)
Answers
Answer: Install the latest firmware updates from the device manufacturer.
Verify that your network's existing security infrastructure is working properly
Explanation:
Since the person is concerned about the security of these devices, in order to increase their security posture, the latest firmware updates should be installed fom the device manufacturer.
The firmware is the software program or set of instructions which is programmed on a hardware device. Installing the latest update is necessary in order to prevent third party use or hacking. Also, it's vital to check the network's existing security infrastructure in order to check if it's working properly.
What is the drawback of the linear model?
A.
communication is only in one direction
B.
too much noise is created
C.
no feedback is sent on receiving the message
D.
long travel between the sender and the receiver
Answers
Answer:
long travel between the sender and the receiver
Explanation:
The drawback of linear model is long travel between the sender and the receiver. The correct option is D.
What is linear model?Depending on the context, the phrase "linear model" is used differently in statistics.
The word is frequently used interchangeably with a linear regression model since it occurs most frequently in relation to regression models.
The phrase has a different connotation when employed in time series analysis, though.
Something that is linear is related to a line. A line is built using all of the linear equations. A non-linear equation is one that cannot be represented by a straight line. It has a variable slope value and resembles a graphed curve.
The linear model's disadvantage is the distance between the transmitter and the receiver.
Thus, the correct option is D.
For more details regarding linear model, visit:
https://brainly.com/question/29757372
#SPJ2
write an if/else statement that compares age with 18, adds 1 to adults if age is greater than or equal to 18 , and adds 1 to minors otherwise.
Answers
Here is an example if/else statement in Python that compares age with 18, adds 1 to the variable "adults" if age is greater than or equal to 18, and adds 1 to the variable "minors" otherwise:
if age >= 18: adults += 1else: minors += 1In computer programming, an if/else statement is a control structure that allows the program to make a decision based on a condition. The condition is evaluated as either True or False and depending on the result, the program executes one of two code blocks: the if block or the else block.In this code snippet, the variable "age" represents the age of the person being checked, while the variables "adults" and "minors" represent the number of adults and minors, respectively. The "+=" operator is used to increment the value of these variables by 1.Learn more about the if/else statement:https://brainly.com/question/18736215
#SPJ11
In 3–5 sentences, describe how technology helps business professionals to be more efficient.
Answers
Answer:
Technology helps business professionals, keep more organized, communicate better, and effectively keeps businesses secure. Technology helps keep employee information and business paper work more organized using computers and software; while making it easier to communicate with employee's using e-mail and memo's.
Explanation:
/\ correct
Write a program in Python which prints your name, surname and class.
Answers
Answer:
print(name + "\n" + surname + "\n" + class)
Explanation:
not enough information is given but this will print those three variables with a newline between each.
A soldier white line down the center of a two lane road indicates
Answers
Answer:
This indicates that you may carefully switch lanes.
Explanation:
If dotted line, then yes.
Hope wants to add a third use at the end of her nitrogen list.
What should Hope do first?
What is Hope’s next step?
Answers
Answer:the first answer is put it at the end of 2b
the second answer is press enter
Explanation:
Answer:
1, put it at the end of 2b 2, press enter key
Explanation:
write sql commands to the following:-
1. display the average price of each type of vehicle having quantity more that 20.
2. count the type of vehicle manufactured by each company
3. display the total price of all the types of vehicles
plssss answerrr...

Answers
Answer:
I can't seem to add SQL to the answer, so let's try this:
For the first one, you need to build a select that uses the avg function on the price column.
For the second one, you need to use the count function. Select that and the company, and group by company.
For the third, it's slightly unclear. Do they mean to mean to display the total price of all vehicles or the total price of each type of vehicle. The former would just be done by selecting a sum of the price. The latter by selecting that and the type column, grouping by type. I'm not sure if type is a keyword, so you might need backtick quotes wrapped around it.
See below for the SQL command of each category
How to write the SQL commands?To do this, we make use of the following clauses:
SELECTAVERAGEWHERECOUNTUsing the above highlight, we have:
Average price of each vehicle having quantity more than 20.The table name is given as: Vehicles
To display the average, we use the following query:
SELECT
Type, avg(Price)
FROM Vehicle
GROUP BY Type
HAVING QTY >20;
Count type of vehicle by each companyTo count each type of vehicle, we use the following query:
SELECT
company, COUNT(DISINCT Type)
FROM VEHICLE
GROUP BY Company;
Display the total price of allThe total price is calculated using:
Total = Price * Quantity
So, we have the following query:
SELECT
Type, SUM(Price* Qty)
FROM VEHICLE
GROUP BY Type;
Read more about SQL at:
https://brainly.com/question/25694408
#SPJ2
Which of the following functions would you use to retrieve data from a previous row in a result set?
a. PERCENT_RANK
b. LEAD
c. CUME_DIST
d. LAG
SQL
Answers
The function that you would use to retrieve data from a previous row in a result set is the LAG function. This function allows you to access the value of a column from the previous row in the result set. It can be useful for calculating differences or changes between rows. The syntax for using the d. LAG function in SQL is.
LAG(column_name, offset, default_value) OVER (ORDER BY column_name) The column_name parameter specifies the column you want to retrieve the previous value from, the offset parameter specifies how many rows back you want to look, and the default_ value parameter specifies what value to return if there is no previous row (e.g. for the first row in the result set). This is a but I hope it helps clarify the use of the LAG function in SQL.
To retrieve data from a previous row in a result set, you would use the "LAG" function in SQL.
The LAG function in SQL is used to retrieve data from a previous row in a result set.
To know more about retrieve data visit:-
https://brainly.com/question/27703563
#SPJ11
A technician is working on a laptop and GPS is not functioning. What is a possible solution for this situation
Answers
A possible solution to a laptop whose global positioning system (GPS) is not functioning is to: verify that airplane mode is not activated on the laptop.
A laptop can be defined as a small, portable computer that is embedded with a keyboard and monitor, which is light enough in terms of weight, to be placed on the user's lap while working.
Assuming, the technician has verified that all the wireless settings on the laptop are correct.
Hence, the most likely problem for the laptop's global positioning system (GPS) not to function is that it is in airplane mode.
Generally, when an airplane mode is activated (turned on) on a laptop, all the software programs that uses wireless technology would not function, until it is disabled (turned off)
In conclusion, a possible solution to a laptop whose global positioning system (GPS) is not functioning is to verify that airplane mode is not activated (turned on) on the laptop.
Read more: https://brainly.com/question/20347476
In cell K2 enter a formula using the IF and OR functions, as well as structured references, to determine if Adam Moriarty can be a group leader. a. The IF function should first determine if the staff member’s Service Years is greater than 3 OR if the staff member’s college graduate status is "Yes". Remember to use a structured reference to the Service Years and the College Graduate columns.
Answers
Solution :
The value of the K2 cell is filled by IF and OR functions with structured references as :
\(K2=IF(OR([CBF\ \text{Staff[ Service years]} > 3, \text{CBF Staff[College graduate]}="Yes"),"Yes","No")\)
Now if the syntax of the formula is not provided, then we can use :
\($K2=IF(OR([[\text{Service Years}]]>3,[[\text{College Graduate}]]="Yes"),"Yes","No")$\)
The staff member are required to satisfy one of the two or both the conditions so as to become a group leader. The conditions are :
--- staff member should served for more than 3 years
--- staff members should be college graduate


Some organizations and individuals, such as patent trolls, abuse intellectual property laws .
computer science
Answers
Answer:
False.
Explanation:
Patent can be defined as the exclusive or sole right granted to an inventor by a sovereign authority such as a government, which enables him or her to manufacture, use, or sell an invention for a specific period of time.
Generally, patents are used on innovation for products that are manufactured through the application of various technologies.
Basically, the three (3) main ways to protect an intellectual property is to employ the use of
I. Trademarks.
II. Patents.
III. Copyright.
Copyright law can be defined as a set of formal rules granted by a government to protect an intellectual property by giving the owner an exclusive right to use while preventing any unauthorized access, use or duplication by others.
Patent trolls buy up patents in order to collect royalties and sue other companies. This ultimately implies that, patent trolls are individuals or companies that are mainly focused on enforcing patent infringement claims against accused or potential infringers in order to win litigations for profits or competitive advantage.
Hence, some organizations and individuals, such as patent trolls, do not abuse intellectual property laws.
Answer:
the answer is intentionally
Explanation:
i took the test
Cloud resource service models include Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
Match each service model listed on the left with the appropriate description on the right. (Each service model may be used once, more than once, or not at all.)
1. Provider delivers everything a developer needs to build an application.
2. Providers deliver processing, storage, networks, and virtualized environment services.
3. Clients deploy and run software without purchasing servers, data center space, or network equipment.
4. Provider delivers applications to the client either over the internet or on a local area network.
5. Client avoids the cost and complexity of buying and managing the underlying hardware and software layers.
Answers
The appropriate matching of cloud resource service models with their descriptions are as follows:
1. Provider delivers everything a developer needs to build an application - Platform as a Service (PaaS)
2. Providers deliver processing, storage, networks, and virtualized environment services - Infrastructure as a Service (IaaS)
3. Clients deploy and run software without purchasing servers, data center space, or network equipment - Software as a Service (SaaS)
4. Provider delivers applications to the client either over the internet or on a local area network - Software as a Service (SaaS)
5. Client avoids the cost and complexity of buying and managing the underlying hardware and software layers - Infrastructure as a Service (IaaS)
1. Platform as a Service (PaaS): This service model provides developers with a complete platform to build, develop, and deploy applications without worrying about the underlying infrastructure. The provider delivers tools, frameworks, libraries, and development environments required to build applications.
2. Infrastructure as a Service (IaaS): This service model offers virtualized computing resources, such as processing power, storage, networks, and virtualized environments. Clients can use these resources to deploy and manage their own applications or software platforms.
3. Software as a Service (SaaS): With this service model, clients can access and use software applications hosted by a provider over the internet. Clients do not need to invest in or maintain servers, data centers, or network equipment. They can simply use the software through a web browser or other client applications.
4. Software as a Service (SaaS): In this case, the provider delivers applications directly to the client, either over the internet or on a local area network. The client can access and use these applications without the need for installation or local hosting.
5. Infrastructure as a Service (IaaS): With this service model, clients can avoid the costs and complexities associated with buying and managing the underlying hardware and software layers. The provider takes care of the infrastructure, including servers, storage, networking, and virtualization, allowing clients to focus on their applications or services.
Learn more about network here:
https://brainly.com/question/29350844
#SPJ11
Understanding the logic and processes computers use to solve problems and run programs is known as:_________
Answers
Answer:
Computational Thinking
Explanation:
3. What does a production sound mixer do? Which responsibility of a production sound mixer do you think sounds most difficult and why? A production sound mixer has many duties, he has to announce each take that is being films, he also is responsible for recording voice-overs/wild lines. In my opinion the most difficult is recording the wild lines because the dialogues and all the film lines are in your hands, it's a lot of responsibility and you need to be very organized to keep track of all the lines you need to record and make sure that everything sounds right.
Answers
Answer:
The production sound mixer has various jobs around the studio, such as slating, wild lines, voice-overs, and background sound effects. Their hardest is likely slating, which requires a bit more precision than their other jobs.
Explanation:
"What does a production sound mixer do? Which responsibility of a production sound mixer do you think sounds most difficult and why?"
Straight from the lesson related to this question:
In getting sound right for a film, equipment is only part of the story. People are also needed to best use that equipment... On smaller-budget films, the filmmaker may select a production sound mixer who has his or her own equipment as this choice can save the filmmaker a considerable amount of money in sound equipment rental, and the mixer is likely to be skilled in using his or her own equipment.
In short, the production sound mixer is a person hired to mix sounds together in a film production. They have several responsibilities, such as those included in the passage below:
The responsibilities of the production sound mixer position can vary, again depending on the film's budget, needs, and size of crew. However, the production sound mixer does perform certain functions for almost every film. For example, s/he announces each take that is filmed and is responsible for slating. Slating is the use of the film slate, also called a clapboard, which shows specific information about each take, such as the date, director, production, scene number, and take number.
The production sound mixer can also be responsible for recording voice-overs, which are actors' lines that are not spoken by the actors within the scene... The sound mixer also records what are called "wild lines," which are lines that the actors repeat because the originals were not spoken or recorded clearly enough for the film's needs. He or she may not necessarily be responsible for creating the sound effects, but he or she may be responsible for recording the sound effects that someone else creates.
The production sound mixer has various jobs around the studio, such as slating, wild lines, voice-overs, and background sound effects. Their hardest is likely slating, which requires a bit more precision than their other jobs.
Quotes from FLVS.
Compare the printout on the SDV screen (Brain) with the list you created and coded. Why didn’t the Brain have 1s and 0s on it? Can you identify how the code creates what you saw on the Brain?
Answers
The printout on the SDV screen (Brain) and the list I created and coded, are different because the code creates a representation of the data on the Brain, rather than displaying the data itself in the form of 1s and 0s.
The code is used to create the visualization on the Brain by interpreting the data and displaying it in a way that is understandable for humans. This visualization can include various elements such as text, images, and graphics. The code is responsible for creating the layout, design, and functionality of the visualization, as well as for processing and displaying the data.What is the code about?It is likely that the code uses various programming libraries and frameworks to create the visualization on the Brain, and these libraries and frameworks have their own methods for handling and displaying data.
The code may also use algorithms and data structures to process and organize the data before it is displayed on the Brain.
In all, the printout on the SDV screen (Brain) and the list I created and coded are different because the code creates a representation of the data on the Brain rather than displaying the data itself in the form of 1s and 0s. The code uses various programming libraries, frameworks, algorithms and data structures to process and display the data in a way that is understandable for humans.
Learn more about coding from
https://brainly.com/question/27639923
#SPJ1
Which statement describes one of the responsibilities of a computer programmer?
A.
providing remote technical support to users
B.
installing, configuring, and monitoring network systems
C.
using computer-generated software to create special effects
D.
using coding languages to create software for retrieving data
E.
designing and implementing databases
Answers
Answer:
d i think
Explanation:
If multiple GPOs are linked to the same site, domain, or OU, they will be applied in a random order. a. True b. False
Answers
False. The order of Group Policy Object (GPO) processing is determined by the inheritance and precedence rules.
What is the purpose of a firewall in network security?When multiple GPOs are linked to the same site, domain, or Organizational Unit (OU), the processing order follows a specific sequence.
The GPOs are processed in the following order:
Local, Site, Domain, and OU. Within each level, the GPOs are processed in the order of their link precedence, with the GPO having the highest link order applied last, effectively overwriting any conflicting settings from previous GPOs.
Learn more about (GPO) processing
brainly.com/question/31919196
#SPJ11