Select the correct answer.
Which option is the correct format of placing HTML tags while coding in HTML?
A.
Answers
The option that is the correct format of placing HTML tags while coding in HTML is <ul><li><li><ul>
What is the HTML tags?HTML tags are the keywords on a location on the world wide web that outline in what way or manner your netting portal must layout and display your location on the world wide web. Almost all tags hold two parts, an gap, and a closing tag. For example, is the gap tag and is the closing tag.
There are two types of HTML tags: double and uneven. Paired tags demand an beginning tag that turns a producing publications with computer software feature on and a closing tag that turns the feature off. Paired tags must enclose the quotation you want formatted accompanying that feature.
Learn more about HTML tags from
https://brainly.com/question/9069928
#SPJ1
See options below
Which option is the correct format of placing HTML tags while coding in HTML?
<ul><li><li><ul>'
(ul><li><li><ul)
<ul><ul>ul><li>
<ul><ui><li><ul>
Related Questions
Which statement is false?Structures are derived data types.Each structure definition must end with a semicolon.A structure can contain an instance of itself.Structures may not be compared using operators == and !=.
Answers
Answer:
A structure can contain an instance of itself
Explanation:
The statement which is known to be false out of the option given is that a structure may comprise or contain an instance of itself. Because to my knowledge, variables of diverse type are always most likely to attributed and contain by a structure.
It is worthy of note that object that aren't similar are utilize in constructing a structure. Another true statement about structure is that a semicolon usually end it's explanation.
some context free languages are undecidable
Answers
how do unblock a school chromebook
Answers
2. go to a website
3. to the left address click the icon you see: Lock, Info, or Dangerous.
4. click Site settings
5. change a permission setting. your changes will automatically save
(ANSWER ASAP!! GIVING BRAINLIEST IF CORRECT :))
Before she applies for an internship with a local engineering company, what type of letter might Zaynab ask one of her teachers to write for her?
A: resignation letter
B: complaint letter
C: thank-you letter
D: recommendation letter
Answers
Answer:
D
Explanation:
She would want a teacher to write a recommendation letter. A recommendation letter vouches for the student and explains why the student would be a good fit for the job.
Answer:
Recommendation letter
Explanation:
A recommendation letter vouches for the student and explains why the student would be a good fit for the job.
A customer calls in and is very upset with recent service she received. You are trying to calm the customer down to come to a resolution but you are not sure how to best do so
Answers
It's crucial to maintain your composure and show empathy while interacting with a frustrated customer. Actively listen to their worries and express your regret for any hardship you may have caused.
Can you describe a moment where you dealt with an angry or upset customer in the past?You can use the STAR approach to share a tale about a time when you had to face an irate client in person. Situation: "A client arrived at my former employment screaming and cursing the workers. She was lamenting because she didn't have her receipt when she tried to return an item.
What are the 5 C's of complaint?The 5Cs approach of formal presentation, where the Cs stand for Principal complaint, Course of sickness.
To know more about customer visit:-
https://brainly.com/question/13472502
#SPJ1
1.Create a function that accepts any number of numerical (int and
float) variables as positional arguments and returns the sum ofthose variables.
2.Modify the above function to accept a keyword argument
'multiplier'. Modify the function to return an additional variable
that is the product of the sum and the multiplier.
3.Modify the above function to accept an additional keyword
argument 'divisor'. Modify the function to return an additional
variable that is the quotient of the sum and the divisor.
Answers
Answer:
This function accepts any number of numerical variables as positional arguments and returns their sum:
python
Copy code
def sum_numbers(*args):
return sum(args)
This function accepts a multiplier keyword argument and returns the product of the sum and the multiplier:
python
Copy code
def sum_numbers(*args, multiplier=1):
total_sum = sum(args)
return total_sum * multiplier
This function accepts an additional divisor keyword argument and returns the quotient of the sum and the divisor:
python
Copy code
def sum_numbers(*args, multiplier=1, divisor=1):
total_sum = sum(args)
return total_sum * multiplier, total_sum / divisor
You can call these functions with any number of numerical arguments and specify the multiplier and divisor keyword arguments as needed. Here are some examples:
python
# Example 1
print(sum_numbers(1, 2, 3)) # Output: 6
# Example 2
print(sum_numbers(1, 2, 3, multiplier=2)) # Output: 12
# Example 3
print(sum_numbers(1, 2, 3, multiplier=2, divisor=4)) # Output: (8, 3.0)
C++ program
Sort only the even elements of an array of integers in ascending order.
Answers
Answer: Here is one way you could write a C++ program to sort only the even elements of an array of integers in ascending order:
Explanation: Copy this Code
#include <iostream>
#include <algorithm>
using namespace std;
// Function to sort only the even elements of an array in ascending order
void sortEvenElements(int arr[], int n)
{
// create an auxiliary array to store only the even elements
int aux[n];
int j = 0;
// copy only the even elements from the original array to the auxiliary array
for (int i = 0; i < n; i++)
if (arr[i] % 2 == 0)
aux[j++] = arr[i];
// sort the auxiliary array using the STL sort function
sort(aux, aux + j);
// copy the sorted even elements back to the original array
j = 0;
for (int i = 0; i < n; i++)
if (arr[i] % 2 == 0)
arr[i] = aux[j++];
}
int main()
{
// test the sortEvenElements function
int arr[] = {5, 3, 2, 8, 1, 4};
int n = sizeof(arr) / sizeof(arr[0]);
sortEvenElements(arr, n);
// print the sorted array
for (int i = 0; i < n; i++)
cout << arr[i] << " ";
return 0;
}
A Quicksort (or Partition Exchange Sort) divides the data into 2 partitions separated by a pivot. The first partition contains all the items which are smaller than the pivot. The remaining items are in the other partition. You will write four versions of Quicksort:
• Select the first item of the partition as the pivot. Treat partitions of size one and two as stopping cases.
• Same pivot selection. For a partition of size 100 or less, use an insertion sort to finish.
• Same pivot selection. For a partition of size 50 or less, use an insertion sort to finish.
• Select the median-of-three as the pivot. Treat partitions of size one and two as stopping cases.
As time permits consider examining additional, alternate methods of selecting the pivot for Quicksort.
Merge Sort is a useful sort to know if you are doing External Sorting. The need for this will increase as data sizes increase. The traditional Merge Sort requires double space. To eliminate this issue, you are to implement Natural Merge using a linked implementation. In your analysis be sure to compare to the effect of using a straight Merge Sort instead.
Create input files of four sizes: 50, 1000, 2000, 5000 and 10000 integers. For each size file make 3 versions. On the first use a randomly ordered data set. On the second use the integers in reverse order. On the third use the
integers in normal ascending order. (You may use a random number generator to create the randomly ordered file, but it is important to limit the duplicates to <1%. Alternatively, you may write a shuffle function to randomize one of your ordered files.) This means you have an input set of 15 files plus whatever you deem necessary and reasonable. Files are available in the Blackboard shell, if you want to copy them. Your data should be formatted so that each number is on a separate line with no leading blanks. There should be no blank lines in the file. Even though you are limiting the occurrence of duplicates, your sorts must be able to handle duplicate data.
Each sort must be run against all the input files. With five sorts and 15 input sets, you will have 75 required runs.
The size 50 files are for the purpose of showing the sorting is correct. Your code needs to print out the comparisons and exchanges (see below) and the sorted values. You must submit the input and output files for all orders of size 50, for all sorts. There should be 15 output files here.
The larger sizes of input are used to demonstrate the asymptotic cost. To demonstrate the asymptotic cost you will need to count comparisons and exchanges for each sort. For these files at the end of each run you need to print the number of comparisons and the number of exchanges but not the sorted data. It is to your advantage to add larger files or additional random files to the input - perhaps with 15-20% duplicates. You may find it interesting to time the runs, but this should be in addition to counting comparisons and exchanges.
Turn in an analysis comparing the two sorts and their performance. Be sure to comment on the relative numbers of exchanges and comparison in the various runs, the effect of the order of the data, the effect of different size files, the effect of different partition sizes and pivot selection methods for Quicksort, and the effect of using a Natural Merge Sort. Which factor has the most effect on the efficiency? Be sure to consider both time and space efficiency. Be sure to justify your data structures. Your analysis must include a table of the comparisons and exchanges observed and a graph of the asymptotic costs that you observed compared to the theoretical cost. Be sure to justify your choice of iteration versus recursion. Consider how your code would have differed if you had made the other choice.
Answers
The necessary conditions and procedures needed to accomplish this assignment is given below. Quicksort is an algorithm used to sort data in a fast and efficient manner.
What is the Quicksort?Some rules to follow in the above work are:
A)Choose the initial element of the partition as the pivot.
b) Utilize the same method to select the pivot, but switch to insertion sort as the concluding step for partitions that contain 100 or fewer elements.
Lastly, Utilize the same method of pivot selection, but choose insertion sort for partitions that are of a size equal to or lesser than 50 in order to accomplish the task.
Learn more about Quicksort from
https://brainly.com/question/29981648
#SPJ1
You have an Azure subscription that contains the following fully peered virtual networks: VNet1, located in the West US region. 5 virtual machines are connected to VNet1. VNet2, located in the West US region. 7 virtual machines are connected to VNet2. VNet3, located in the East US region, 10 virtual machines are connected to VNet3. VNet4, located in the East US region, 4 virtual machines are connected to VNet4. You plan to protect all of the connected virtual machines by using Azure Bastion. What is the minimum number of Azure Bastion hosts that you must deploy? Select only one answer. 1 2 3 4
Answers
Answer:
To protect all the connected virtual machines with Azure Bastion, the minimum number of Azure Bastion hosts that you must deploy is 2.
Explanation:
Azure Bastion provides secure and seamless RDP and SSH access to virtual machines directly through the Azure portal, eliminating the need to expose them to the public internet. Each Azure Bastion host provides connectivity to virtual machines within a single virtual network.
In this scenario, you have four virtual networks (VNet1, VNet2, VNet3, and VNet4) located in two different regions (West US and East US). Since VNet1 and VNet2 are in the same region (West US), you can deploy one Azure Bastion host in that region to provide access to the 12 virtual machines (5 in VNet1 and 7 in VNet2).
For VNet3 and VNet4, which are located in the East US region, you would need another Azure Bastion host to provide access to the 14 virtual machines (10 in VNet3 and 4 in VNet4).
Therefore, the minimum number of Azure Bastion hosts required is 2, with one host deployed in the West US region and another host deployed in the East US region.
You are given a string of n characters s[1 : : : n], which you believe to be a corrupted text document in which all punctuation has vanished (so that it looks something like itwasthebestoftimes...). You wish to reconstruct the document using a dictionary, which is available in the form of a Boolean function dict(): for any string w, dict(w) = true if w is a valid word false otherwise . (a) Give a dynamic programming algorithm that determines whether the string s[] can be reconstituted as a sequence of valid words. The running time should be at most O(n2), assuming calls to dict take unit time. (b) In the event that the string is valid, make your algorithm output the corresponding sequence of words.
Answers
Answer: provided in the explanation section
Explanation:
Given that:
Assume D(k) =║ true it is [1 : : : k] is valid sequence words or false otherwise
To determine D(n)now the sub problem s[1 : : : k] is a valid sequence of words IFF s[1 : : : 1] is a valid sequence of words and s[ 1 + 1 : : : k] is valid word.
So, from here we have that D(k) is given by the following recorance relation:
D(k) = ║ false maximum (d[l]∧DICT(s[1 + 1 : : : k]) otherwise
Algorithm:
Valid sentence (s,k)
D [1 : : : k] ∦ array of boolean variable.
for a ← 1 to m
do ;
d(0) ← false
for b ← 0 to a - j
for b ← 0 to a - j
do;
if D[b] ∧ DICT s([b + 1 : : : a])
d (a) ← True
(b). Algorithm Output
if D[k] = = True
stack = temp stack ∦stack is used to print the strings in order
c = k
while C > 0
stack push (s [w(c)] : : : C] // w(p) is the position in s[1 : : : k] of the valid world at // position c
P = W (p) - 1
output stack
= 0 =
cheers i hope this helps !!!
Across the breadth of decision domains,
O The greater use of intuition over analytics results in stronger organizational
performance
The greater use of analytics over intuition results in stronger organizational
performance
O The use of analytics over intuition results in improved performance in about 75 percent
of the decision domains
O The use of analytics over intuition results in improved performance in about 50 percent
of the decision domains
Answers
Answer: C. The use of analytics over intuition results in improved performance in about 50 percent of decision domains.
Explanation: This suggests that while analytics can be a powerful tool for decision-making, there are still many situations in which intuition plays an important role. It is important for organizations to strike a balance between using analytics and intuition to make decisions that lead to improved performance.
9. Computer 1 on network A, with IP address of 10.1.1.10, wants to send a packet to Computer 2, with IP address of
172.16.1.64. Which of the following has the correct IP datagram information for the fields: Version, minimum
Header Length, Source IP, and Destination IP?
Answers
Answer:
Based on the given information, the IP datagram information for the fields would be as follows:
Version: IPv4 (IP version 4)
Minimum Header Length: 20 bytes (Since there are no additional options)
Source IP: 10.1.1.10 (IP address of Computer 1 on network A)
Destination IP: 172.16.1.64 (IP address of Computer 2)
So the correct IP datagram information would be:
Version: IPv4
Minimum Header Length: 20 bytes
Source IP: 10.1.1.10
Destination IP: 172.16.1.64
In this network, devices are connected directly to each other without any additional
networking devices between them. Individual users are responsible for their own
resources and can decide which data and devices to share.
Explain this type of network with its advantages and disadvantages
Answers
The network described in the prompt is a Peer-to-Peer (P2P) network, also known as a "workgroup."
Advantages of a P2P networkCost-effective: P2P networks are relatively inexpensive to set up and maintain since they don't require any additional networking equipment or servers.
Flexibility: In a P2P network, devices can be added or removed easily without affecting the rest of the network.
Decentralized: Since there is no central server or device controlling the network, it is more resistant to failure and can continue to function even if some devices are offline.
Security: P2P networks can be more secure since there is no central point of attack or failure, and individual users have more control over their own resources and security settings.
Disadvantages:Limited scalability: P2P networks are not designed to handle large numbers of devices or users, and as the network grows, it can become difficult to manage and maintain.
Reliability: Since each device is responsible for its own resources, the network can be less reliable if individual devices fail or are offline.
Security: While P2P networks can be more secure in some ways, they can also be vulnerable to malware and other security threats if individual devices are not properly secured and maintained.
Learn more about Peer-to-Peer at:
https://brainly.com/question/10571780
#SPJ1
Which of the following situations is least likely fair use
Answers
Answer:
Is there more to the question or is that it?
Where are the situations??
Which of the following is an example of an open-ended question?
O What are your thoughts about this?
O Should I repeat what I just said?
Do you agree?
Do you understand?
Answers
Answer:
What are your thoughts about this?
Explanation:
A question that can be answered with yes or no is a closed question.
Which of the following describes the phishing
of it up information security crime
Answers
Pretending to be someone else when asking for information
What is phishing?A method wherein the criminal poses as a reliable person or respectable company in order to solicit sensitive information, such as bank account details, through email or website fraud.
Attackers create phony emails that contain harmful links. Once the victim clicks the link and enters their credentials, the attacker can use those credentials to gain illegal access. Consequently, the victim is phished.
Phishing is a dishonest method of obtaining sensitive information by posing as a reliable organization. Similar to any other form of fraud, the offender can do a great deal of harm, especially if the threat continues for a long time.
To learn more about phishing refer to:
https://brainly.com/question/23021587
#SPJ9
A two-dimensional list is suitable for storing tabular data. True False 2 A two-dimensional list is really a one-dimensional list of one-dimensional lists. True False 3 The smallest index of any dimension of a two-dimensional list is 1. True False 4 The maximum indexes of a two-dimensional list with 6 rows and 10 columns are 5 and 9, respectively. True False 5 How many elements can be stored in a two-dimensional list with 5 rows and 10 columns
Answers
Answer:
1.) True
2.) True
3.) False
4.) True
5.) 50
Explanation:
A.) Two dimensional list reperesents arrays arranges in rows and column pattern ; forming a Table design. 1 dimension represents rows whe the other stands for the column.
B.) When a 1-dimensional list is embedded in another 1 - dimensional list, we have a 2 - D list.
C.) The smallest index of any dimension of a 2-D list is 0
.D.) Given a 2-D list with 6 rows and 10 columns
Maximum dimension:
(6 - 1) = 5 and (10 - 1) = 9
Dimension = (5, 9)
E.) maximum number of elements :
5 rows by 10 columns
5 * 10 = 50 elements.
Imagine you have just learned a new and more effective way to complete a task at home or work. Now, you must teach this technique to a friend or coworker, but that person is resistant to learning a new way of doing things. Explain how you would convince them to practice agility and embrace this new, more effective method.
Answers
if a person is resistant to learning a new way of doing things, one can practice agility by
Do Implement the changeMake a dialogue with one's Unconscious. Free you mind to learn.How can a person practice agility?A person can be able to improve in their agility by carrying out some agility tests as well as the act of incorporating any form of specific drills into their workouts.
An example, is the act of cutting drilling, agility ladder drills, and others,
A training that tends to help in the area of agility are any form of exercises such as sideways shuffles, skipping, and others.
Therefore, if a person is resistant to learning a new way of doing things, one can practice agility by
Do Implement the changeMake a dialogue with one's Unconscious. Free you mind to learn.Learn more about agility from
https://brainly.com/question/15762653
#SPJ1
Which function deletes the first occurence of 3 in a list named listB ?
listB.clear(3)
listB(3)
listB delete(3)
listB.remove(3)
Answers
Answer:
\(listB.remove(3)\)
Explanation:
Given
Options A to D
Required
Which deletes the first occurrence of 3
The options show that the question is to be answered using the knowledge of Python.
So, we analyze each of the options using Python syntax
(a) listB.clear(3)
In python, clear() is used to delete all elements of a list, and it does not take any argument i.e. nothing will be written in the bracket.
Hence, (a) is incorrect
(b) listB(3)
The above instruction has no meaning in Python
(c) listB delete(3)
The above instruction as written is an invalid syntax because of the space between listB and delete.
Also, it is an invalid syntax because lists in Python do not have the delete attribute
\((d)\ listB.remove(3)\)
This removes the first occurrence of 3
Answer: listB delete(3)
Explanation: got it right on edgen
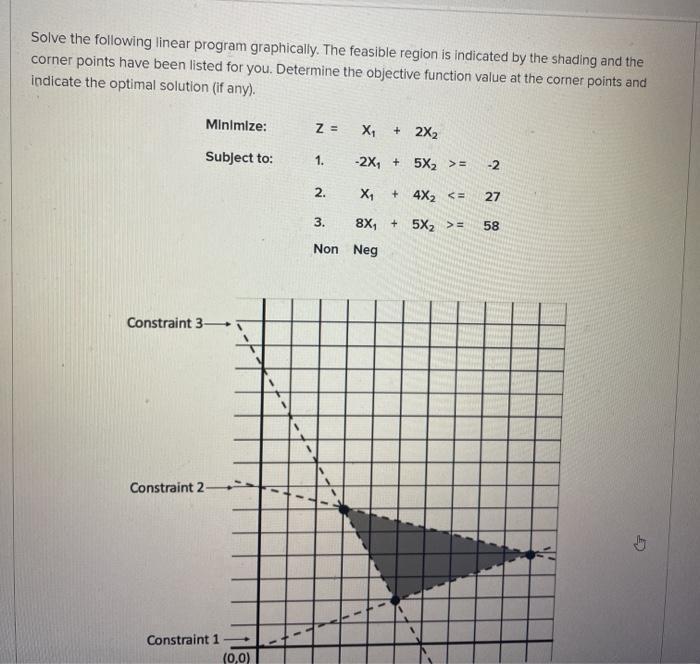
Solve the following linear program graphically (each line represents one unit). The feasible region is indicated by the shading and the corner points have been listed for you. Determine the objective function value at the corner points and indicate the optimal solution (if any). Minimize: Z
Answers
Answer:
(a): The value of the objective function at the corner points
\(Z = 10\)
\(Z = 19\)
\(Z = 15\)
(b) The optimal solution is \((6,2)\)
Explanation:
Given
\(Min\ Z = X_1 + 2X_2\)
Subject to:
\(-2X_1 + 5X_2 \ge -2\) ---- 1
\(X_1 + 4X_2 \le 27\) ---- 2
\(8X_1 + 5X_2 \ge 58\) --- 3
Solving (a): The value of the at the corner points
From the graph, the corner points are:
\((6,2)\ \ \ \ \ \ (11,4)\ \ \ \ \ \ \ \ (3,6)\)
So, we have:
\((6,2)\) ------- Corner point 1
\(Min\ Z = X_1 + 2X_2\)
\(Z = 6 + 2 * 2\)
\(Z = 6 + 4\)
\(Z = 10\)
\((11,4)\) ------ Corner point 2
\(Min\ Z = X_1 + 2X_2\)
\(Z = 11 + 2 * 4\)
\(Z = 11 + 8\)
\(Z = 19\)
\((3,6)\) --- Corner point 3
\(Min\ Z = X_1 + 2X_2\)
\(Z = 3 + 2 * 6\)
\(Z = 3 + 12\)
\(Z = 15\)
Solving (b): The optimal solution
Since we are to minimize Z, the optimal solution is at the corner point that gives the least value
In (a), the least value of Z is: \(Z = 10\)
So, the optimal solution is at: corner point 1
\((6,2)\)
which country did poker originate from?
Answers
Poque, a game that dates back to 1441 and that was supposedly invented in Strasbourg, seems to be the first early evidence of the French origin of the game. Poque in particular used a 52-card deck
France/French
Consider the following code:
a = 3
b = 2
print (a ** b)
What is output?
A.9
B.8
C.1
D.6

Answers
Answer:
C
Explanation:
*i'm really bad at explaining* the letters is going up like- a b c d e f g and the numbers are going down like- 3 2 1 0
Answer:
A. 9
Explanation:
the symbol (**) means to put to the exponent to. So in this case, 3**2 is the same as 3^2 or 3 squared, 3x3=9. So that is the answer.
What are two examples of ways an electronic record may be distributed to others
Answers
Explanation:
Two ways an electronic record may be distributed are e-mail or printing and publishing to others.
What is lossy compression
A. It is a technique that results in the loss of all files on a computer.
B. It is a technique that reduces the file size by permanently removing some data
C. It is a method of combining the memories of the ram and the rom
D. It is a method that stores data dynamically requiring more power
Answers
Answer:
B. It is a technique that reduces the file size by permanently removing some data
Answer:
B. It is a technique that reduces the file size by permanently removing some data
Explanation:
You have a spreadsheet with population counts for major cities in the United States. Population counts are given in different columns to show breakdown by age groups and gender. The names of cities are listed in rows. You need the population count in column 45 for the city in row 30. What tool could you use to navigate to the cell quickly?
filter
sort
locate
replace
Answers
Answer:
The answer is C. Locate
Explanation: Got it right on edg please mark brainliest
QUESTION 5 OF 30
Burnout can happen quickly when
working with multiple sysadmins
working overtime
working as the sole sysadmin
Answers
Answer:
Burnout can happen quickly when working with multiple sysadmins, working overtime, or working as the sole sysadmin.
Explanation:
Give two ways that a sound file can be compressed
Answers
Answer:
Compress Audio Files With Monkey's Audio for Windows.Compress MP3 Files With iTunes or Apple Music.https://www.celonis.com/solutions/celonis-snap
Using this link
To do this alternative assignment in lieu of Case 2, Part 2, answer the 20 questions below. You
will see on the left side of the screen a menu for Process Analytics. Select no. 5, which is Order
to Cash and click on the USD version. This file is very similar to the one that is used for the BWF
transactions in Case 2, Part 2.
Once you are viewing the process analysis for Order to Cash, answer the following questions:
1. What is the number of overall cases?
2. What is the net order value?
Next, in the file, go to the bottom middle where you see Variants and hit the + and see what it
does to the right under the detail of variants. Keep hitting the + until you see where more than a
majority of the variants (deviations) are explained or where there is a big drop off from the last
variant to the next that explains the deviations.
3. What is the number of variants you selected?
4. What percentage of the deviations are explained at that number of variants, and why did you
pick that number of variants?
5. What are the specific variants you selected? Hint: As you expand the variants, you will see on
the flowchart/graph details on the variants.
6. For each variant, specify what is the percentage of cases and number of cases covered by that
variant? For example: If you selected two variants, you should show the information for each
variant separately. If two were your choice, then the two added together should add up to the
percentage you provided in question 4 and the number you provided in question 3.
7. For each variant, how does that change the duration? For example for the cases impacted by
variant 1, should show a duration in days, then a separate duration in days for cases impacted
by variant 2.
At the bottom of the screen, you see tabs such as Process, Overview, Automation, Rework, Benchmark,
Details, Conformance, Process AI, Social Graph, and Social PI. On the Overview tab, answer the
following questions:
8. In what month was the largest number of sales/highest dollar volume?
9. What was the number of sales items and the dollar volume?
10. Which distribution channel has the highest sales and what is the amount of sales?
11. Which distribution channel has the second highest sales and what is the amount of sales?
Next move to the Automation tab and answer the following questions:
12. What is the second highest month of sales order?
13. What is the automation rate for that month?
Nest move to the Details tab and answer the following questions:
14. What is the net order for Skin Care, V1, Plant W24?
15. What is the net order for Fruits, VV2, Plant WW10?
Next move to the Process AI tab and answer the following questions:
16. What is the number of the most Common Path’s KPI?
17. What is the average days of the most Common Path’s KPI?
18. What other information can you get off this tab?
Next move to the Social Graph and answer the following questions:
19. Whose name do you see appear on the graph first?
20. What are the number of cases routed to him at the Process Start?
Answers
1. The number of overall cases are 53,761 cases.
2. The net order value of USD 1,390,121,425.00.
3. The number of variants selected is 7.4.
4. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. Seven variants explain 87.3% of the total variance, including order, delivery, credit limit, material availability, order release, goods issue, and invoice verification.
10. January recorded the highest sales volume, with 256,384 items sold for USD 6,607,088.00. Wholesale emerged as the top distribution channel, followed by Retail.
12. December stood out as the second-highest sales month,
13. with an automation rate of 99.9%.
14. Notable orders include Skin Care, V1, Plant W24 (USD 45,000.00) and
15. Fruits, VV2, Plant WW10 (USD 43,935.00).
17. The most common path had a KPI of 4, averaging 1.8 days.
18. This data enables process analysis and improvement, including process discovery, conformance, and enhancement.
19. The Social Graph shows Bob as the first name,
20. receiving 11,106 cases at the Process Start.
1. The total number of cases is 53,761.2. The net order value is USD 1,390,121,425.00.3. The number of variants selected is 7.4. The percentage of the total variance explained at 7 is 87.3%. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. The seven specific variants that were selected are: Order, Delivery and Invoice, Check credit limit, Check material availability, Order release, Goods issue, and Invoice verification.6. Below is a table showing the percentage of cases and number of cases covered by each variant:VariantPercentage of casesNumber of casesOrder57.2%30,775Delivery and Invoice23.4%12,591Check credit limit5.1%2,757
Check material availability4.2%2,240Order release4.0%2,126Goods issue2.4%1,276Invoice verification1.7%9047. The duration of each variant is as follows:VariantDuration in daysOrder24Delivery and Invoice3Check credit limit2Check material availability1Order release2Goods issue4Invoice verification1
8. The largest number of sales/highest dollar volume was in January.9. The number of sales items was 256,384, and the dollar volume was USD 6,607,088.00.10. The distribution channel with the highest sales is Wholesale and the amount of sales is USD 3,819,864.00.
11. The distribution channel with the second-highest sales is Retail and the amount of sales is USD 2,167,992.00.12. The second-highest month of sales order is December.13. The automation rate for that month is 99.9%.14. The net order for Skin Care, V1, Plant W24 is USD 45,000.00.15.
The net order for Fruits, VV2, Plant WW10 is USD 43,935.00.16. The number of the most common path’s KPI is 4.17. The average days of the most common path’s KPI is 1.8 days.18. Additional information that can be obtained from this tab includes process discovery, process conformance, and process enhancement.
19. The first name that appears on the Social Graph is Bob.20. The number of cases routed to Bob at the Process Start is 11,106.
For more such questions deviations,Click on
https://brainly.com/question/24251046
#SPJ8
Identify the types of networks described.
A home network is a ______.
The network in a state is a _______.
The internet is a _______.
options for all three:
Wi-Fi Hotspot
Local Area Network (LAN)
Wide Area Network (WAN)
Answers
Answer:
wi-fi hotspot, local area network, wide area network
Explanation:
think about it. how are you on this site? you might be at home. you are using a wifi hotspot to connect to brainly. at home.
or maybe at school
the state network is LAN and even wider than that is the internet which is a WAN
According to ACM and IEEE What are the most popular programming languages used in industry today
Answers
Python remains on top but is closely followed by C. Indeed, the combined popularity of C and the big C-like languages—C++ and C#—would outrank Python by some margin.
What is a programming language?A method of notation for creating computer programs is known as a programming language. The majority of formal programming languages are text-based, though they can also be graphical. They are a sort of programming language.
Large enterprises all across the world employ client-server applications, and Java is the programming language most often associated with their creation.
Learn more about programming language here:
https://brainly.com/question/16936315
#SPJ1