select all of the following scenarios that show interaction between smis components. more than one answer may be correct.
Answers
Information systems (IS) teams at businesses conduct research, A social media specialist at a start-up often scans the news. Users' data is important to social media providers.
A formal, sociotechnical, organizational structure called an information system (IS) is created to gather, process, store, and distribute information. Information systems are made up of four elements from a sociotechnical standpoint: the task, the people, the structure (or roles), and the technology. Information systems are made up of components that work together to gather, store, and analyze data. This data is then utilized to produce digital products that help with decision-making and to offer information. A system that consists of both people and computers and processes or interprets information is known as a computer information system. The phrase is also occasionally used to describe a computer system that has software on it. A second academic field based on systems is called "information systems," which specifically refers to information systems and the complementary networks of computer hardware and software that people and organizations use to gather, filter, analyze, produce, and distribute data. The importance of an information system with a clear border, users, processors, storage, inputs, outputs, and the communication networks stated above is stressed.
Learn more about Information systems here
https://brainly.com/question/14688347
#SPJ4
Related Questions
Can someone give me an example of code of any cartoon character using java applet please help me i need to make my project please☹️
Answers
The Java code for a cartoon character using java applet is
import java.applet.Applet;
import java.awt.*;
public class CartoonCharacter extends Applet implements Runnable {
Thread t;
int x = 0;
int y = 100;
public void init() {
setSize(500, 500);
setBackground(Color.white);
}
public void start() {
if (t == null) {
t = new Thread(this);
t.start();
}
}
public void run() {
while (true) {
x += 10;
repaint();
try {
Thread.sleep(100);
} catch (InterruptedException e) {}
}
}
public void paint(Graphics g) {
g.setColor(Color.red);
g.fillOval(x, y, 50, 50);
}
}
How does the code work?Note that the cartoon character is made like a red circle that navigates accross the screent.
The init() method sets the size of the applet and its background color, while the start( ) method creates a new thread and starts the animation loop in the run() method
Learn more about Java Code at:
https://brainly.com/question/29897053
#SPJ1
Consider a DMA module that is transferring characters (as bytes), one at a time, to main memory from some I/O device connected directly to the DMA device. Suppose that I/O device transfers bit-by-bit at a rate of 19200 bits per second. Suppose the CPU can fetch 1 million instructions per second (with constant use of the system bus and main memory). How much will the processor be slowed down due to the DMA activity
Answers
We have that the Processor speed reducing will be is mathematically given as
S=0.24 %.From the question we are told
Consider a DMA module that is transferring characters (as bytes), one at a time, to main memory from some I/O device connected directly to the DMA device. Suppose that I/O device transfers bit-by-bit at a rate of 19200 bits per second. Suppose the CPU can fetch 1 million instructions per second (with constant use of the system bus and main memory). How much will the processor be slowed down due to the DMA activityProcessorGenerally we have that the processor fetches directions at a charge of 1m guidelines per 2d or 1 MIPS.
The I/O machine switch records at a pace of 19200 bits per seconds.
\(\frac{19200}{8} = 2400\)
Therefore
2400 bytes per sec
Since that CPU is fetching and executing guidelines at an common charge of one million directions per 2nd sluggish down or cycle wasted p.c in DMA switch = ( 2400 / 1000000) * 100
= 0.24%
Hence
The Processor speed reducing down will be
S=0.24 %.
For more information on Processor visit
https://brainly.com/question/16517842
Described the importance of developing strategies to conduct educational research.
Answers
Step 1: Identifying a Problem.
2
Step 2: Reviewing the Literature.
3
Step 3: Specifying a Purpose and Research Questions. Writing purpose statements, research questions, and hypotheses provide critical direction to an educational research study. ...
4
Step 4: Designing a Study.
ecu
Your personal opinion about what a "successful" console in the future will need to include to sell well. How have the changes in technology, gaming culture, and overall society affected the market?
Answers
Answer:
The answer is below
Explanation:
In my personal opinion what a "successful" console in the future will need to include to sell well is "a big library of games." This feature will help a console supports many games that will appeal to all categories of gamers.
The changes in technology, gaming culture, and overall society has affected the game market in many ways such as:
1. In terms of technology: it has made the game manufacturers both the console and third-party game developers to improve their gaming features. For example, the advancement in gaming pads becoming wireless. The gaming console having internet or online features, where gamers can play with each other around the world from their rooms. Also, the gaming character design looking more and more like the real-life personality it represents.
2. In terms of gaming culture: modern games are no longer for teenagers alone. It is now appealing to adults as well. This is evident in football players and coaches playing the games and talking about it. Even some players tend to influence their ratings in the game by mentioning how good they are in the press in comparison to the rating game developers are giving them.
3. Overall society has now seen gaming consoles as part of everyday life. The parents, researchers, and even feminist groups are now well aware of the gaming industry. And each of the stakeholders involved is influenced by how the game consoles manufacturers market their games through media, sports personalities, celebrities, etc.
A large population of Aloha users manages to generate 50 requests/sec, including both originals and retransmissions. Time is slotted in units of 40 msec.a. What is the chance of success on the first attempt at a given station?b. What is the probability of exactly k collisions (for k = 1, 2,...,10) followed by a success?c. What is the expected number of transmission attempts needed?
Answers
Answer:
a) 0.1353
b) attached below
c) 7.4
Explanation:
Frame transmission rate = 40 msec
Total load requests = 50 requests /sec
hence
Total arrival rate G in Frames ( G ) / x secs
= 50 request/sec * X sec
= 50 * ( 40*10^-3 )
= 2 requests/ x sec
a) Determine chance of success on first attempt
0.1353
b) Determine the probability of exactly K collisions followed by a success
attached below
c) what is the expected number of transmission attempts needed
7.4

which windows and network location enables network discovery and allows files and printers to be easily shared
Answers
The Private network location is the windows and network location enables network discovery and allows files and printers to be easily shared
How to determine the windowIn Windows, the organized area that empowers organize disclosure and permits simple sharing of records and printers is the Private network location.
After you set your arrange association to the Private network location, it empowers different arrange highlights, counting organize revelation, record sharing, and printer sharing.
By default, Windows categorizes arrange associations into three sorts:
PublicPrivateDomainThe Private network location is the foremost prohibitive, constraining organize disclosure and impairing record and printer sharing for security reasons.
Learn more about windows at: https://brainly.com/question/27764853
#SPJ1
9.6 code practice edhesive
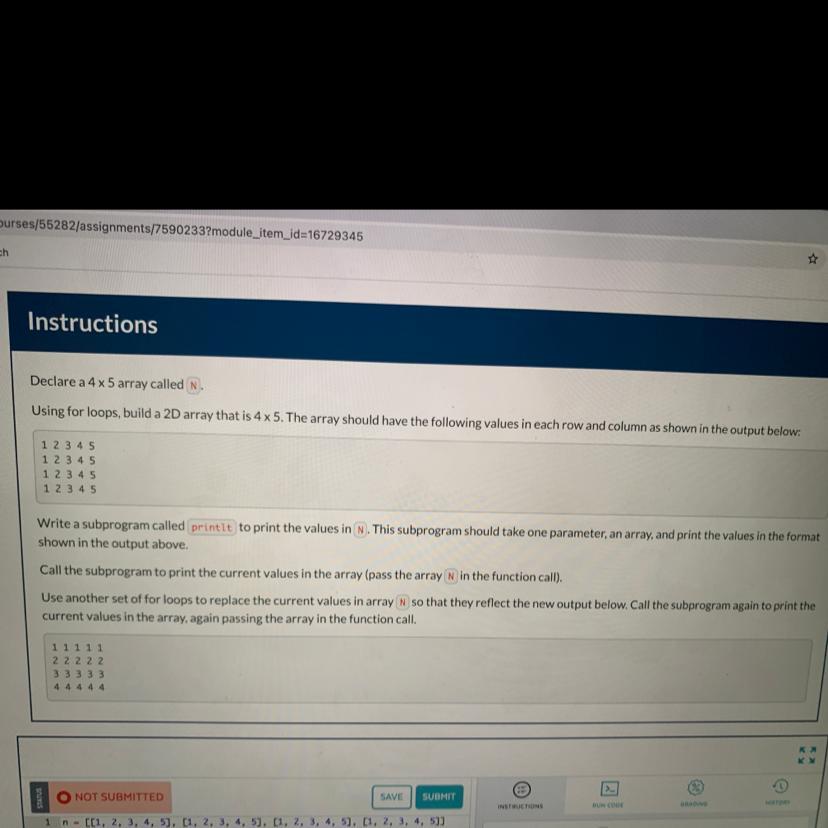
Answers
Answer: i got 50% for this I don’t know what to fix
Explanation:
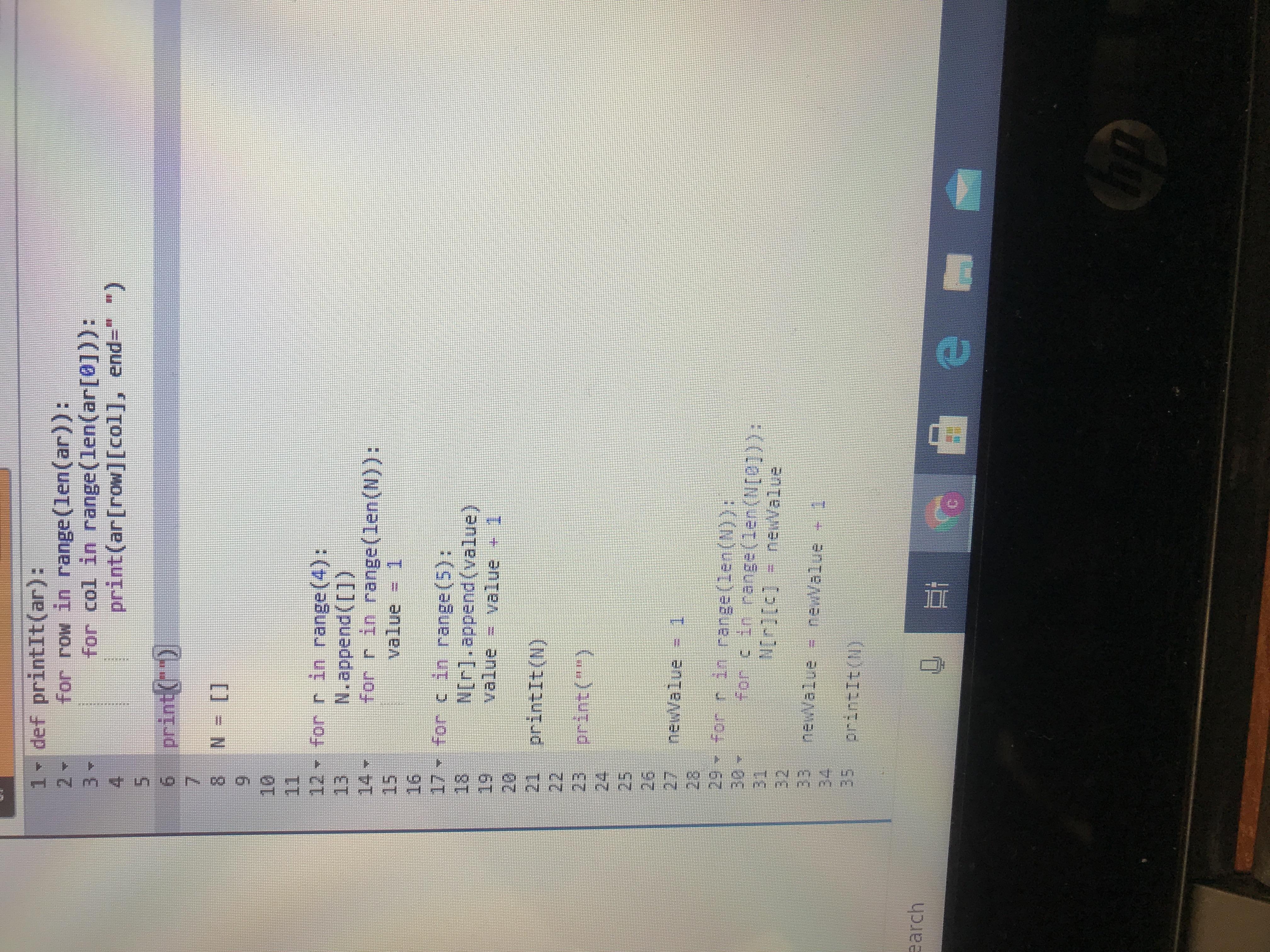
Answer:
def printIt(ar):
for row in range(len(ar)):
for col in range(len(ar[0])):
print(ar[row][col], end=" ")
print("")
N= []
for r in range(4):
N.append([])
for r in range(len(N)):
value = 1
for c in range(5):
N[r].append(value)
value = value +1
printIt(N)
print("")
newValue = 1
for r in range(len(N)):
for c in range(len(N[0])):
N[r][c] = newValue
newValue = newValue + 1
printIt(N)
Explanation: Ez clap
In PyCharm, write a program that prompts the user for their name and age. Your program
should then tell the user the year they were born. Here is a sample execution of the program
with the user input in bold:
What is your name? Amanda
How old are you? 21
Hello Amanda! You were born in 2001.
1. Write the program. Format your code using best practices. You can refer to the zyBooks
style guide, if needed, to use proper naming conventions for variables and methods. Use the
most appropriate statements with minimal extraneous elements, steps, or procedures.
2. Run the program.
3. Debug the program. Be sure your code produces the correct results.
4. Save and submit your file.
Answers
Program to prompt user for name and age and then tell them the year they were born
prompt user for name
name = input("What is your name? ")
prompt user for age
age = input("How old are you? ")
calculate year of birth
year_of_birth = 2022 - int(age)
print message to user
print("Hello " + name + "! You were born in " + str(year_of_birth) + ".")
Which device is not considered a computer?
a smartphone
an analog controller
Answers
Answer:
An analog controller is not considered a computer because you just move around the controls. You don't stare at a screen like a smartphone, so it is not a computer.
Explanation:
If you were to sort the Title field in tblBooks in a Descending order, in ms access which author would be at the top of the list? A. Linda Rode B. Robert Howard C.Isaac Asimov D. Roger D. Abrahams
Answers
If the Title field in the tblBooks table is sorted in descending order in MS Access, the author at the top of the list would be Linda Rode. So, the correct option is A.
Sorting the Title field in descending order means arranging the titles in reverse alphabetical order.
Out of the given authors, Linda Rode would be at the top of the list because her last name, "Rode," comes first alphabetically when compared to the other authors' last names. The other authors' last names are Howard, Asimov, and Abrahams.When sorting in descending order, the records are listed from Z to A or highest to lowest, depending on the sorting field. In this case, since we are sorting the Title field, which is a text field, the sorting would be in reverse alphabetical order.Therefore, Linda Rode, with her last name starting with "R," would appear at the top of the list. So, the correct choice is option A.
For more questions on author
https://brainly.com/question/32116759
#SPJ8
I really need help with this what are 4 things that show you this email is a scam

Answers
Answer:
1. Grammar errors and misspelled words.
Example: if no action is "taking" we will be "force"
Correct words are supposed to be taken and forced.
2. Name of sender "Email_Service" The underscore brings a little suspicion and it doesn't match the name of the email its being sent from.
3. Urgency. In other words this is an "ACT NOW, ACTION REQUIRED" email, which normally come from scams.
4. Threats – LAST WARNING, IF NO ACTION IS TAKEN YOUR EMAIL WILL BE BLACKLISTED.
Explanation:
In C language / Please don't use (sprint) function. Write a function fact_calc that takes a string output argument and an integer input argument n and returns a string showing the calculation of n!. For example, if the value supplied for n were 6, the string returned would be 6! 5 6 3 5 3 4 3 3 3 2 3 1 5 720 Write a program that repeatedly prompts the user for an integer between 0 and 9, calls fact_calc and outputs the resulting string. If the user inputs an invalid value, the program should display an error message and re-prompt for valid input. Input of the sentinel -1 should cause the input loop to exit.
Note: Don't print factorial of -1, or any number that is not between 0 and 9.
SAMPLE RUN #4: ./Fact
Interactive Session
Hide Invisibles
Highlight:
None
Show Highlighted Only
Enter·an·integer·between·0·and·9·or·-1·to·quit:5↵
5!·=·5·x·4·x·3·x·2·x·1·x··=·120↵
Enter·an·integer·between·0·and·9·or·-1·to·quit:6↵
6!·=·6·x·5·x·4·x·3·x·2·x·1·x··=·720↵
Enter·an·integer·between·0·and·9·or·-1·to·quit:20↵
Invalid·Input↵
Enter·an·integer·between·0·and·9·or·-1·to·quit:8↵
8!·=·8·x·7·x·6·x·5·x·4·x·3·x·2·x·1·x··=·40320↵
Enter·an·integer·between·0·and·9·or·-1·to·quit:0↵
0!·=··=·1↵
Enter·an·integer·between·0·and·9·or·-1·to·quit:-1↵

Answers
Here's an implementation of the fact_calc function in C language:
#include <stdio.h>
void fact_calc(char* output, int n) {
if (n < 0 || n > 9) {
output[0] = '\0';
return;
}
int result = 1;
sprintf(output, "%d!", n);
while (n > 1) {
sprintf(output + strlen(output), " %d", n);
result *= n--;
}
sprintf(output + strlen(output), " 1 %d", result);
}
int main() {
int n;
char output[100];
while (1) {
printf("Enter an integer between 0 and 9 (or -1 to exit): ");
scanf("%d", &n);
if (n == -1) {
break;
} else if (n < 0 || n > 9) {
printf("Invalid input. Please enter an integer between 0 and 9.\n");
continue;
}
fact_calc(output, n);
printf("%s\n", output);
}
return 0;
}
How does the above code work?The fact_calc function takes two arguments: a string output and an integer n.The function first checks if n is less than 0 or greater than 9. If so, it sets the output string to an empty string and returns.If n is a valid input, the function initializes result to 1 and starts building the output string by appending n! to it.Then, the function loops from n down to 2, appending each number to the output string and multiplying it with result.Finally, the function appends 1 and the value of result to the output string, effectively showing the calculation of n!.In the main function, we repeatedly prompt the user for an integer between 0 and 9 (or -1 to exit) using a while loop.We check if the input is valid and call the fact_calc function with the input and a buffer to store the output string.We then print the resulting output string using printf.If the user inputs an invalid value, we display an error message and continue the loop.If the user enters -1, we exit the loop and end the program.
Learn more about C Language:
https://brainly.com/question/30101710
#SPJ1
Match the features of integrated development environments (IDEs) and website builders to the appropriate location on the chart.

Answers
Answer:
website builder
complex coding techniques and advanced programming languages.
What kind of variable is measured using 2 different values
Answers
A variable that is measured using two different values can be classified as a categorical variable or a binary variable.
Depending on the nature of the values, a variable can be classified as:
1)Categorical Variable: If the two different values represent distinct categories or groups, the variable is considered categorical. In this case, the variable can take on only one of two possible values.
Examples include gender (male/female), presence/absence of a certain trait, yes/no responses, or any other classification with mutually exclusive categories.
2)Binary Variable: If the two different values represent two distinct outcomes or states, the variable can be classified as a binary variable. Binary variables are often used in statistics, machine learning, and hypothesis testing.
Examples include success/failure, true/false, 1/0, or positive/negative results.
It's important to note that the distinction between categorical and binary variables lies in the nature of the values and the underlying meaning they convey.
Categorical variables can have more than two categories, while binary variables specifically refer to variables with only two possible values.
For more questions on variable
https://brainly.com/question/28248724
#SPJ8
Consider the following language:
L={ |M is a Turing Machine and M accepts at least one palindrome,
and rejects at least one palindrome}
a. Is L a decidable language? Prove your answer.
b. Is L a recognizable language? Prove your answer.
Answers
L is a decidable language because the Turing machine accepts it.
L is a recognizable language if TM M recognizes it.
How do you know if a language is decidable?A language is said to be decidable only when there seems to exists a Turing machine that is said to accepts it,
Here, it tends to halts on all inputs, and then it answers "Yes" on words that is seen in the language and says "No" on words that are not found in the language. The same scenario applies to recognizable language.
So, L is a decidable language because the Turing machine accepts it.
L is a recognizable language if TM M recognizes it.
Learn more about programming language from
https://brainly.com/question/16936315
#SPJ1
This type of hosting model provides space, utilities, but you must provide your own server equipment.
Answers
Colocation hosting is a type of hosting model provides space, utilities, but you must provide your own server equipment.
What does the term colocation hosting mean?Colocation, often known as colocation hosting, is the practice of renting out equipment, servers, space, and bandwidth to companies in a highly secure data center facility. Companies can rent space in colocation facilities, which provide stronger security and uptime guarantees, to host their servers.
An actual building known as a colocation data center provides space with the right power, cooling, and security to house servers and computing technology for enterprises. Anything from cabinets to cages to private apartments are included in this capacity.
Therefore, A data center that provides colocation hosting is a type of service that involves renting out space and housing servers. The servers are owned by the clients, who also assert complete control over the hardware and software.
Learn more about hosting from
https://brainly.com/question/14302227
#SPJ1
Joseline is trying out a new piece of photography equipment that she recently purchased that helps to steady a camera with one single leg instead of three. What type of equipment is Joseline trying out?
A. multi-pod
B. tripod
C. semi-pod
D. monopod
Answers
Joseline trying out tripod .A camera-supporting three-legged stand is known as a tripod. For stability, cameras are fixed on tripods, sometimes known as "sticks." In tripods, the fluid head is used. The camera may now tilt up and down in addition to pan left and right.
What tools are employed in photography?You will need a camera with manual settings and the ability to change lenses, a tripod, a camera case, and a good SD card if you're a newbie photographer who wants to control the visual impacts of photography. The affordable photography gear listed below will help you get started in 2021.A monopod, which is a one-legged camera support system for precise and stable shooting, is also known as a unipod.A camera-supporting three-legged stand is known as a tripod. For stability, cameras are fixed on tripods, sometimes known as "sticks." In tripods, the fluid head is used. The camera may now tilt up and down in addition to pan left and right.To learn more about tripod refer to:
https://brainly.com/question/27526669
#SPJ1
Answer:
monopod
Explanation:
This feature in Word Online allows you to view your document to see what it will look like when printed.
Open
Print Preview
Save
Sneak Preview
Answers
Answer:
Print preview allows you to view your document before printing
Answer: they are correct, the answer is print preview! (i did the quiz)
Explanation:
you can give them brianliest now!
What are the basic characteristics of object-oriented analysis and design (OOAD)? How does OOAD compare to structured analysis and design (SAD)?
Answers
Answer:
Basic characteristics of OOAD and compression with SAD can be defined as follows:
Explanation:
The Object-oriented analysis is described as a design and analysis system like an application, that uses Oops programming. It is the measurement model, that is the presentation, which became a part of the object-based review.
The features of OOAD can be defined as follows.
The complex issues are simply solved. The operation of very fast recovery. The stability in condition changes. Its conceptual method for resolving its extremely complex problems.The difference in OOAD and SAD can be defined as follows:
The OOAD mainly focuses upon the design of objects, it can be used in highly complex logical systems, whereas the SAD focuses on data analysis systems and processes. The OOAD uses the framework to target data, but the SAD is process-oriented. It uses class and UML diagrams, but SSAD uses DFDs to extract the element, it has many limited steps to prepare and execute, but OOAD relies mostly on initial growth. This method is being developed in the course of the process.how do I write a proper python dictionary for my rooms in my text-based adventure game? I have the entrance, the gallery (wizard hat), the cellar (wizard robe), the bedroom (the potion), dining room (spell book), dungeon (wizard orb), the living room (wizard staff) and the potion room (the wizard). (The items that go with the rooms are in parenthesis behind the rooms)
Answers
Python may be used to create text adventure games that the player enters text into, which causes the tale to change.
How to Create a Text Based Adventure Game in Python?If you're learning how to program, creating a text adventure game is a fun project to try. Python can be used to create text adventure games that the player enters text into, which causes the story to change.The Python script will go over a number of fundamental programming ideas. Print commands, if clauses, and functions are included in this.Using a common text file with the.py extension, you can write a script. If you are unfamiliar with Python syntax, check at some fundamental Python examples to help you learn it more quickly. You may also take a look at some practical Python one-liners to carry out specific tasks.Set up your story and welcome message in the main function of the Python code."AdventureGame.py" should be created as a new file.Include the primary starting function in the file. A brief introductory tale will be included in the feature to welcome the player to the adventure game. After that, it will call introScene, another function.To Learn more About Python refer To:
https://brainly.com/question/26497128
#SPJ4

You work at a help desk tecthnician in a mid-sized business. As your organization has been growing, there has been an increase of issues dealing with malware, viruses, and other threats to the systems. There hasn't been a consistent means of securing the various data assets, PCs and network. Your IT Manager would like you to create a proposal in order to implement measures to combat malware, viruses, and other threats to the organizational data assets. The proposal should also address security concepts and mitigation strategies to keep the PCs and networks secure.
The organization has all of its workers in a single building but has multiple floors split up based on departments. All of the users are on Windows PCs with a mix of Windows 10, Windows 7 and Windows 8.1. The servers consist of a database server, file server, email server, web application servers as well as other business application servers. Due to the fact that the organization has multiple floors, most users currently use a wireless connection. Throughout the project, you will be building on your proposal document. Your proposal should address the following scenarios using the resources provided:
• Some users in your sales department have been noticing their browsers being "taken over". When they go on a particular site, they get directed to another site. This has only started happening when they were exploring some new products and have navigated to sites that may have installed malware on their browsers. Provide details of solutions that can be implemented to combat malware.
• In the HR department, they have been sharing files sent from recruiting agencies. One of the agencies has reached out as they noticed that one of the files they had sent to our HR department had a virus. Provide ways of implementing measures to combat these viruses.
• There have been an increased number of other issues in the organization in which the users need training on. In particular, the areas of phishing emails, personal mobile devices at work, removal media, and poor passwords have been problematic. Provide ways of implementing measures to deal with other issues such as phishing, mobile devices, removal media, and poor passwords.
In addition, in order to create consistency in terms of security concepts, your proposal should also address the following points:
• Apply the mitigation strategies to manage the PC issues listed above.
• Apply the security concepts to ensure the security of networks for wired and wireless networks.
Answers
Answer:
Most people don't have time to read this question
Q Search Based on the diagram, host A sends a packet to server B. The two serial links use HDLC, while the rest are Ethernet. How many times does a router re-encapsulate the original IP packet into a new data link frame? O O 5 4 3 6 R2 R1 A $1/0 $1/0 R3 99+ S1/1 S1/0 R4 R5 D ENG IN A
Answers
Based on the diagram,there are three routers between host A and server B (R1, R3, R4). Each router will re-encapsulate the original IP packet into a new data link frame as the packet traverses the network. Therefore, the answer is 3 times. (Option C)
How is this so?In the given network diagram, the packet sent from host A to server B passes through three routers (R1, R3, R4).
As the packet travels through each router, it is re-encapsulated into a new data link frame specific to the respective link type (HDLC or Ethernet). This process occurs three times in total.
Learn more about network at:
https://brainly.com/question/1326000
#SPJ1
Question 2: Fill in the blanks i. In MS Excel, keyboard shortcut keys to create a new workbook is ii. The extension of a Microsoft Excel file is xx iii. The intersection of a column and a row in a worksheet is called ell dri+x iv. To return frequent value of the cell in a given range, mode function is used. v. Applying a formatting without any criteria is called_normal formatting [5]
Answers
It is to be noted tht the words used to fill in the blanks for the MS Excel prompt above are:
i. Ctrl + N
ii. .xlsx
iii. cell
iv. mode
v. default formatting.
What are the completed sentences?
The completed sentences are
i. In MS Excel, keyboard shortcut keys to create a new workbook is "Ctrl + N".
ii. The extension of aMicrosoft Excel file is ".xlsx".
iii. The intersection of a column and a row in a worksheet is called a "cell".
iv. To return the most frequent value of a cell in a given range, the mode function is used.
v. Applying formatting without any criteria is called "default formatting".
Learn more about MS Excel at:
https://brainly.com/question/24749457
#SPJ1
What will be the different if the syringes and tube are filled with air instead of water?Explain your answer
Answers
Answer:
If the syringes and tubes are filled with air instead of water, the difference would be mainly due to the difference in the properties of air and water. Air is a compressible gas, while water is an incompressible liquid. This would result in a different behavior of the fluid when being pushed through the system.
When the syringe plunger is pushed to force air through the tube, the air molecules will begin to compress, decreasing the distance between them. This will cause an increase in pressure within the tube that can be measured using the pressure gauge. However, this pressure will not remain constant as the air continues to compress, making the measured pressure unreliable.
On the other hand, when the syringe plunger is pushed to force water through the tube, the water molecules will not compress. Therefore, the increase in pressure within the tube will be directly proportional to the force applied to the syringe plunger, resulting in an accurate measurement of pressure.
In summary, if the syringes and tube are filled with air instead of water, the difference would be that the measured pressure would not be reliable due to the compressibility of air.
(TCO C) When a remote user attempts to dial in to the network, the network access server (NAS) queries the TACACS+ server. If the message sent to the server is REJECT, this means _____.
Answers
Answer:
The correct answer to the following question will be "The user is prompted to retry".
Explanation:
NAS seems to be a category of server system a broader open internet as well as web through in-house and perhaps remotely associated user groups.
It handles as well as provides linked consumers the opportunity to provide a collection of network-enabled applications collectively, thereby integrated into a single base station but rather portal to infrastructure.Unless the text or response sent to the server seems to be REJECT, this implies that the authentication process continued to fail and therefore should be retried.given 2,4,3,-1 as input, what is the output for the following program:total_product = 1 user_value = int(input()) while user_value > 0: total_product = total_product * user_value user_value = int(input()) print('Product:', total_product, end='')
Answers
The python program for any of the given values is as written below.
How to run a Program in Python?We are told to use input for the python program as;
2, 4, 3, -1
Now, the python program using 2 as user value and 1 as total product gives us the program as;
total_product = 1
user_value = (input(1)) #while user_value > 0:
total_product = total_product * user_value
user_value = (input(2))
print('Product:2', total_product, end='2')
Read more about Python Program at; https://brainly.com/question/26497128
#SPJ1
Luke is setting up a wireless network at home and is adding several devices to the network. During the setup of his printer, which uses 802. 11g standard, he finds that he can't connect to the network. While troubleshooting the problem, he discovers that his printer is not compatible with the current wireless security protocol because it is an older version of hardware.
What wireless network security protocol will allow Luke to use the printer on his wireless network?
a. WPA
b. WEP
c. WPA2
d. WPA-PSK+WPA2-PSK
Answers
The wireless network security protocol that will allow Luke to use the printer on his wireless network is WEP. The correct answer is option b.
WEP (Wired Equivalent Privacy) is a security protocol that is used to secure wireless networks. It was introduced in 1999 and was widely used in the early days of wireless networking. However, it is an older version of hardware and is considered less secure than newer protocols such as WPA (Wi-Fi Protected Access) and WPA2 (Wi-Fi Protected Access 2).
Since Luke's printer is an older version of hardware, it is not compatible with the current wireless security protocol. Therefore, using WEP will allow Luke to use the printer on his wireless network.
Learn more about wireless network security:
brainly.com/question/30087160
#SPJ11
What is output by following code?
C=c+2

Answers
The output of the C++ code is 21.
What is C++?
C++ has changed significantly over time, and modern C++ has object-oriented, generic, and functional features, as well as low-level memory manipulation capabilities. It is always implemented as a compiled language, and various manufacturers, including the Free Software Foundation, LLVM, Microsoft, Intel, Embarcadero, Oracle, and IBM, provide C++ compilers, allowing it to be used on a wide range of systems.
Let first write the question
C=1
sum = 0
while(C<10):
C=C+3
sum=sum + C
print(sum)
Now Focus on
while(C<10):
C=C+3
sum=sum + C
The value of C is initially 1
C=1+3
Sum= 0+4
In second loop the value of C will become 4
c=4+3
sum=4+7
In third loop the value of C will be 7
c=7+3
sum=11+10
so the answer is 11+10=21
To learn more about C ++
https://brainly.com/question/28185875
#SPJ13
PLEASE HELP IN C++
Integer numElements is read from input. Given the integer vector yearlySalary with the size of numElements, write a for loop to initialize yearlySalary with the remaining integers read from input, in reverse order.
Ex: If the input is
4
102 107 126 138
then the output is:
138 126 107 102
Answers
Code:
numElements = int(input()) # Read the number of elements from input
yearlySalary = [] # Initialize an empty list
# Read the remaining integers from input and append them to yearlySalary in reverse order
for _ in range(numElements):
yearlySalary.append(int(input()))
# Reverse the list to obtain the desired order
yearlySalary = yearlySalary[::-1]
# Print the elements in yearlySalary
for salary in yearlySalary:
print(salary, end=' ')
in this solution, we first read the value of numElements from the input. Then, we initialize an empty list yearlySalary. Next, we use a for loop to read the remaining integers from the input and append them to the yearlySalary list. Finally, we reverse the list using slicing (yearlySalary[::-1]) and print the elements in the desired order.
Feel free giving brainliest!
Limiting a field's entry to a certain number of characters is an example of
phishing
code injection
data validation
Answers
Answer:
data validation
Explanation:
Validation type How it works
Length check Checks the data isn't too short or too long