robert smith works for a telephone company. he is interested in determining the satisfaction of customers with the service provided by the company (for landline customers only). he decides to collect data from the customers listed in the company's existing customer directory. in this scenario, the customer directory serves as a(n)
Answers
In this scenario, the customer directory serves as a primary source of information.
A directory service is a group of programs and procedures that keep records of data about your business, subscribers, or both. The Domain Name System, which is made available via DNS servers, is an illustration of a directory service.
The Lightweight Directory Access Protocol, which is based on industry standards, Novell's Novell Directory Services, and Microsoft's Active Directory are the three main directory services now in use.
Thus, it is primary source of information.
For more information about directory service, click here:
https://brainly.com/question/10536810
#SPJ1
Related Questions
Question # 6 Fill in the Blank You designed a program to create a username using the first three letters from the first name and the first four letters of the last name. You are testing your username program again for a user whose name is Paula Mano. The output should be
Answers
Its PuaMano
Explanation:
got it wrong and it shows this answer for edge
what is used when both sets of data are nominal, dichotomous measures, and the data is placed in contigency tables
Answers
When both sets of data are nominal and dichotomous, chi-square test is used for analyzing the data placed in contingency tables.
Chi-square test is a statistical test used to determine if there is a significant difference between the expected frequencies and observed frequencies in one or more categories of a contingency table. In this case, nominal and dichotomous data can be arranged in a contingency table, which is a table that shows the frequency distribution of the data. The test calculates a chi-square statistic and compares it to a critical value, which determines if the null hypothesis can be rejected. If the calculated chi-square value is greater than the critical value, the null hypothesis can be rejected, and it can be concluded that there is a significant difference between the two sets of data.
Learn more about contingency here
brainly.com/question/31679163
#SPJ11
Cuales de estos aparatos son ejemplo de mecanización automatizacion o robotica batidora electrica , grifo de un cuarto de bño publico que se detiene al cabo de un cierto tiempo y maquina fotocopiadora digital
Answers
Answer:
La automatización es el reemplazo del trabajo humano por máquinas o computadoras y programas de computadora. El motivo es económico: la suma de trabajo y consumo de materias primas es menor después de la automatización que antes.
Las formas de automatización se pueden encontrar a nuestro alrededor. Los semáforos son operados por un sistema automatizado. La caja registradora de la tienda que paga los alimentos hace más que sumar el precio de los artículos; también es la base de un sistema de gestión de inventarios. Tan pronto como se vende un artículo, se reserva inmediatamente y se puede pedir un artículo de reemplazo.
buying insurance and investing for the future requires spending less in the present.
Answers
HELP ASAP!!!
What are some potential challenges that society will face given the digital revolution? You may want to think particularly of the news industry.
Answers
!WILL GIVE BRAINLIEST!
Write a Python program that prompts the user for a word. If the word comes between the words apple
and pear alphabetically, print a message that tells the user that the word is valid, otherwise, tell
the user the word is out of range.
Answers
Answer:
word = input()
if word > "apple" and word < "pear":
print("Word is valid.")
else:
print("Word is out of range.")
Which code is easier to learn, Python or C++. And which one is better than the other in your opinion
Answers
Which of the following can be assumed as the simplest form a physical network topology? (1 point)
O the tree topology
O the mesh topology
O the star topology
the bus topology
Answers
This kind of network structure is the most basic. Here, a common medium is used to connect two nodes directly to one another.
What is Topology?The full bandwidth is set aside between the two nodes because there are only two in this network.
Topology is the study of the characteristics of spaces that are unaffected by continuous deformation. Because the objects may be stretched and contracted like rubber sheets yet cannot be broken, it is frequently referred to as "rubber-sheet geometry."
Analysis and general topology are closely connected fields that often take into account local features of spaces. The definition of topological spaces, in which limits of sequences can be taken into consideration, generalizes the idea of continuity.
Therefore, This kind of network structure is the most basic. Here, a common medium is used to connect two nodes directly to one another.
To learn more about Topology, refer to the link:
https://brainly.com/question/10536701
#SPJ1
Harold is working on a science project that includes a spreadsheet containing calculated results based on the data. An obviously incorrect result is being calculated and displayed. The data is correct, but the formula must be flawed. To get the correct information, Harold clicks on the cell containing the incorrect results and adjusts information contained in the:
A. the formula bar.
B. the shortcut toolbar.
C. the calculator pop-up.
D. the column header.
Answers
Answer: When entering a formula into a cell, you begin with an equal sign
Functions and formulas are calculations a spreadsheet program applies to data.
Functions are preset calculations within spreadsheet software.
Formulas are user-entered calculations that may contain cell references, numerical values, and preset calculations.
Which of the following steps of an incident response plan includes the act of limiting the damage by the team, where affected systems or areas are isolated, and response staff are called in as required by the situation?1. Remediation2. Recovery3. Reveiw4. Containment
Answers
The step of an incident response plan includes the act of limiting the damage by the team, where affected systems or areas are isolated, and response staff are called in as required by the situation is: 4. containment.
What is incident management?Incident management can be defined as a strategic process through which a business organization (company or firm) identifies, analyzes, and correct hazards and potential problems, in order to ensure that normal service operation is restored as quickly as possible to its end users after a disruption, as well as to prevent or limit a re-occurrence of these hazards and mistakes in the future.
What are the steps of an incident response plan?Generally speaking, there are different steps involved in an incident response plan and these include the following;
RemediationRecovery ReviewContainmentIn conclusion, containment is a step of an incident response plan that helps to limit the damage caused during an incident.
Read more on incident management here: brainly.com/question/11595883
#SPJ1
Write a program that takes a date as input and outputs the date's season in the northern hemisphere. The input is a string to represent the month and an int to represent the day. Note: End with a newline.
Answers
A program that takes a date as input and outputs the date's season in the northern hemisphere will bear this order
cout << "Winter"
cout << "Spring"
cout << "Summer"
cout << "Autumn"
Complete Code below.
A program that takes a date as input and outputs the date's season in the northern hemisphereGenerally, The dates for each season in the northern hemisphere are:
Spring: March 20 - June 20Summer: June 21 - September 21Autumn: September 22 - December 20Winter: December 21 - March 19And are to be taken into consideration whilst writing the code
Hence
int main() {
string mth;
int dy;
cin >> mth >> dy;
if ((mth == "January" && dy >= 1 && dy <= 31) || (mth == "February" && dy >= 1 && dy <= 29) || (mth == "March" && dy >= 1 && dy <= 19) || (mth == "December" && dy >= 21 && dy <= 30))
cout << "Winter" ;
else if ((mth == "April" && dy >= 1 && dy <= 30) || (mth == "May" && dy >= 1 && dy <= 30) || (mth == "March" && dy >= 20 && dy <= 31) || (mth == "June" && dy >= 1 && dy <= 20))
cout << "Spring" ;
else if ((mth == "July" && dy >= 1 && dy <= 31) || (mth == "August" && dy >= 1 && dy <= 31) || (mth == "June" && dy >= 21 && dy <= 30) || (mth == "September" && dy >= 1 && dy <= 21))
cout << "Summer" ;
else if ((mth == "October" && dy >= 1 && dy <= 31) || (mth == "November" && dy >= 1 && dy <= 30) || (mth == "September" && dy >= 22 && dy <= 30) || (mth == "December" && dy >= 0 && dy <= 20))
cout << "Autumn" ;
else
cout << "Invalid" ;
return 0;
}
For more information on Programming
https://brainly.com/question/13940523
When would you use an omnidirectional microphone?
when there are three or more actors in a scene
when it is a windy day and you want to reduce the sound of the wind in the recording
when you want to get outdoor sounds that relate to an outdoor scene in a film
when you want to record in surround sound
Answers
Answer:
when it is a windy day and you want to reduce the sound of the wind in the recording
Orders algorithms from best to worst efficiency
Answers
algorithms are essential and have numerous uses. Algorithms are widely utilized in a variety of fields.
Thus, Algorithms are the building blocks of computer programming and are used to tackle issues ranging from straightforward sorting and searching to more complicated ones like artificial intelligence and machine learning.
Algorithms are used in mathematics to solve issues like determining the shortest path in a graph or the best answer to a set of linear equations.
Operations Research: Algorithms are used to decide and optimize in areas like resource allocation, logistics, and transportation.
Thus, algorithms are essential and have numerous uses. Algorithms are widely utilized in a variety of fields.
Learn more about Algorithm, refer to the link:
https://brainly.com/question/21172316
#SPJ1
Why is computer called a fast machine
Answers
Answer:
it does work faster and better than humans
Noah is creating a startup. He uses the website Upwork to hire freelancers in India and in the Ukraine to work for him. This is an example of:
1.industrialization.
2.automation.
3.outsourcing.
4.Moore’s Law.
Answers
Answer:
outsourcing
Explanation:
Which type of attack involves an adversary attempting to gather information about a network to identify vulnerabilities?
Answers
The type of attack involves an adversary attempting to gather information about a network to identify vulnerabilities is called option B: reconnaissance.
What is reconnaissance in cyber attack?The primary goal of reconnaissance attacks is information collection. These initiatives are the result of some digital study as well as physical scouting. This information collection may involve anything from physical surveillance to social engineering to network probing.
Therefore, one can say that information-gathering phase of ethical hacking is known as reconnaissance, during which you gather information about the intended system. Anything from network architecture to employee contact information might be included in this data. Hence the option selected is correct.
Learn more about reconnaissance attack from
https://brainly.com/question/28529674
#SPJ1
See full question below
Which type of attack involves an adversary attempting to gather information about a network to identify vulnerabilities?
DoS
reconnaissance
dictionary
man-in-the-middle
A workspace that an employee accesses using a Web browser fits the definition of a _____.
•mobile device
•Wifi-enabled device
•collaborative environment
•virtual workspace
Answers
Answer:
virtual workspace
Explanation:
I hope I've helped
The following selected accounts appear in the adjusted trial balance for Deane Company. Indicate the financial statement on which each account would be reported. Account (a) Accumulated Depreciation.(b) Depreciation Expense. (c) Retained Earnings (beginning). (d) Dividends.(e) Service Revenue. (f) Supplies. (g) Accounts Payable.
Answers
(a) Accumulated Depreciation: Reported on the balance sheet.
(b) Depreciation Expense: Reported on the income statement.
(c) Retained Earnings (beginning): Reported on the statement of retained earnings.
(d) Dividends: Reported on the statement of retained earnings.
(e) Service Revenue: Reported on the income statement.
(f) Supplies: Reported on the balance sheet.
(g) Accounts Payable: Reported on the balance sheet.
(a) Accumulated Depreciation is an account that represents the total amount of depreciation expense recorded on the company's assets over time. It is a contra-asset account and is reported on the balance sheet to reduce the carrying value of the related assets.
(b) Depreciation Expense is the amount charged against earnings to reflect the gradual lo
Learn more about statement here:
https://brainly.com/question/17238106
#SPJ11
Suppose we are using a three-message mutual authentication protocol, andAlice initiates contact with Bob. Suppose we wish Bob to be a stateless server, and thereforeit is inconvenient to require him to remember the challenge he sent to Alice. Lets modify theexchange so that Alice sends the challenge back to Bob, along with the encrypted challenge. So the protocol is:Step 1: Alice send a message [I’m Alice] to Bob. Step 2: Bob sends a random number, R. Step 3: Alice sends a message [R,KAlice−Bob{R}]. Is this protocol secure?
Answers
No, this protocol is not secure. A secure mutual authentication protocol must, among other things, support mutual authentication, which allows both parties to confirm the identities of one another.
Due to the fact that Bob cannot recall the challenge he gave to Alice, he is unable to confirm Alice's identity using this protocol. As a result, an attacker can read Alice and Bob's messages and then pretend to be Alice to Bob by simply playing back the message that Alice originally sent.
This problem can be resolved by changing the protocol so that Bob sends a challenge along with the random number R, and Alice must respond with the challenge as well. This way, Bob can verify Alice's identity by checking if the challenge in Alice's response matches the one he sent earlier.
For such more question on protocol:
https://brainly.com/question/8156649
#SPJ11
Data analytics tools and methods fall into the following categories—descriptive, predictive, prescriptive, and.
Answers
Data analytics tools and methods fall into the following categories: Descriptive, Predictive, and Prescriptive, according to experts. However, a few other approaches, such as diagnostic analytics, can be used. The following is a detailed explanation of the various types of data analytics.
Descriptive Analytics
Descriptive analytics aids in the collection and description of vast amounts of data from various sources. The goal is to improve the accuracy and completeness of data in the data warehouse. This method aids in the transformation of raw data into actionable information for business decision-making.
Predictive Analytics
This method assists businesses in forecasting and identifying trends in their current dataset. Predictive analytics relies heavily on data modeling, algorithms, and statistical models to produce forecasts based on data sets. It involves identifying the primary drivers behind a trend and forecasting how it will impact the business.
Prescriptive Analytics
Prescriptive analytics leverages machine learning to help businesses optimize their decision-making. It entails a combination of human expertise and machine learning. Prescriptive analytics aims to identify the best action or outcome from a set of possible scenarios, allowing businesses to make data-driven decisions.
Diagnostic Analytics
Diagnostic analytics identifies why something has happened. It's all about determining the root cause of a problem, allowing businesses to solve problems more efficiently. It works by analyzing historical data to determine what factors influenced a particular outcome.
To know more about data visit:
https://brainly.com/question/30051017
#SPJ11
To determine the network ID of an IP address, computers use a logical AND operation between the IP address and the subnet mask. True or False.
Answers
The given statement "To determine the network ID of an IP address, computers use a logical AND operation between the IP address and the subnet mask." is true becasue when a computer receives an IP address and a subnet mask, it can determine the network ID by performing a logical AND operation between the two values.
The subnet mask is a binary value that has a 1 in each bit position corresponding to the network bits in the IP address and a 0 in each bit position corresponding to the host bits. By performing a logical AND operation between the IP address and subnet mask, the computer effectively "masks out" the host bits and only retains the network bits, which results in the network ID. This information is essential for routing data between networks in a TCP/IP-based network.
You can learn more about logical AND operation at
https://brainly.com/question/13524798
#SPJ11
Choose the term so achieve the output shown.
>>>import math
>>>math. ___ (36)
6.0
•Sqr
•Root
•sqrt
Answers
Answer:
sqrt
Explanation:
Answer:
sqrt
Explanation:
sqrt= square root
sqrt of 36 is 6
Define the term Project brief? why is it important to do planning?
Answers
Answer: the project brief is a document that provides an overview of the project.
Explanation: It says exactly what the designer, architect, and contractor needs to do to exceed your expectations and to keep the project on track with your goals and your budget.
What is the output of the following code fragment? int i = 1; int sum = 0; while (i <= 11) { sum = sum + i; i++; } System.out.println("The value of sum is " + sum); The value of sum is 65. The value of sum is 66. The value of sum is 55. The value of sum is 56.
Answers
Answer:
The value of sum is 66
Explanation:
i = 1
sum = 0
while (i <= 11) {
sum = sum + i;
i++;
}
i = 1
sum = sum + isum = 0 + 1sum = 1i = 2
sum = sum + isum = 1 + 2sum = 3i = 3
sum = sum + isum = 3 + 3sum = 6i = 4
sum = sum + isum = 6 + 4sum = 10i = 5
sum = sum + isum = 10 + 5sum = 15i = 6
sum = sum + isum = 15 + 6sum = 21i = 7
sum = sum + isum = 21 + 7sum = 28i = 8
sum = sum + isum = 28 + 8sum = 36i = 9
sum = sum + isum = 36 + 9sum = 45i = 10
sum = sum + isum = 45 + 10sum = 55i = 11
sum = sum + isum = 55 + 11sum = 66i = 12 --> does not comply with the condition "i < = 11", the while loop is over
The rules and guidelines for appropriate computer mediated communication are called ________. A. Social norms b. Etiquette c. Netiquette d. Manners Please select the best answer from the choices provided A B C D.
Answers
The rules and guidelines for appropriate computer mediated communication are called Netiquette.
What is Netiquette?
Netiquette, which is a blend of “net” and “etiquette,” refers to the polite and appropriate behavior when communicating with others online.
These rules are important as they help to improve communication skills, prevent misconceptions, and encourage only socially acceptable behavior when working or collaborating online.
Some of the DOs of Netiquette among others includes:
Being mindful of your toneUse of emoticons Use of good grammarSome of the DONTs among others includes:
Overuse of abbreviationsUnnecessary rants/FlamingOverusing capsIn conclusion Netiquette involves not doing what you would not do in person.
Learn more about Netiquette here:https://brainly.com/question/998689
Answer:
c
Explanation:
edg
Activity
You have learned about the graphical elements that you can add in a spreadsheet. Create your own spreadsheet using these elements.
Question 1
Create a chart using the sample data in the table below. Recollect the steps on how to create a chart, and explain the necessary steps based on
the data in the table. Mention what the x- and the y-axes state and your interpretation of the data represented in the chart.
Year Percentage Increase in Expenses
2005
25.3
2007
30
2009
35
2011
35.8
2014
40
please help

Answers
Answer:
its a
Explanation:
the answer is a i am right
Answer:
Here are the steps I followed to create the chart on the Microsoft Excel spreadsheet.
I clicked the Insert option from the top toolbar.
I clicked the Chart option.
I clicked Chart Type, and selected the type of chart I wanted. The table above provides data on the increase in percentage of expenses over the years. I chose the Column chart to display this data graphically. The column chart is the best form of chart that can show variation between items.
I selected the Data Range. I specified the start and end values of the data set that I wanted to plot in the chart.
Under Chart Elements, I specified the title and legend for the chart. A legend makes it easy for a viewer to understand a titled graph.
The x-axis represents the year in my column chart, and the y-axis shows the percentage increase in expenses per year. With the help of this chart, I could see that every year the percentage in expenses has increased steadily, and reached the highest value in 2014.
Explanation:
This is really close to the sample answer, so I would be careful...
plz help me to do 4 number

Answers
Answer:
A is an abbaccus. B is Blaze Pascal. C is The Jacquard Loom. D is Charles Babbage. E is The Manchester Baby.
Explanation:
1
TIME REMAINING
01:51:06
Zubair needs to change some of the data in a table that he has created. How should he go about selecting a row in
the table?
Moun the mourn nointor in a noint hefore the text in a cell
Answers
log the 'age' property of the 'person' object
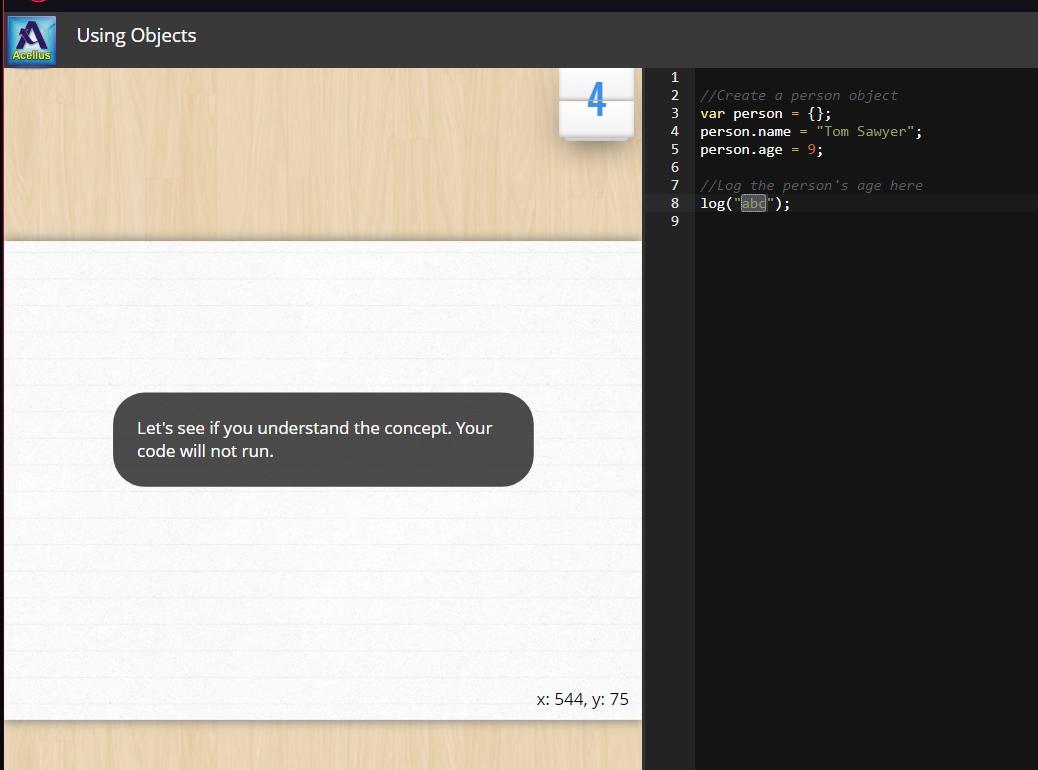
Answers
Answer:
vauwnwkwiauauwiajhwbwbw
what is your favorite coler and what do you like to do and
Answers
Answer:
Orange
Explanation:
I like orange because its vibrant.