pls help quick
Question #4. This question is worth 55 points. You may use the exam reference sheet. Write the pseudocode for a procedure, pow2() that displays the nth power of 2 where n is a parameter passed into the procedure. PROCEDURE pow2 ) { }

Answers
Answer:
The procedure is completed as follows:
PROCEDURE pow2(n){
count = 1
power = 1
WHILE count <= n
power = power * 2
count = count + 1
END WHILE
Print power
}
Explanation:
A pseudocode is not a real code and might not be syntactically correct. This is so because it only helps to understand what the code is all about and gives and insight of the code.
Having said that, the pseudocode for the program is as follows:
This line defines the procedure
PROCEDURE pow2(n){
This line initializes count to 1
count = 1
This line initializes power to 1
power = 1
The following iteration iterates from 1 to n
WHILE count <= n
This calculates the nth power of 2
power = power * 2
count = count + 1
The ends the while loop
END WHILE
This prints the calculated power
Print power
The procedure ends here
}
Note that: I'll assume that the 4 lines illustrated do not mean that the pseudocode be written in just 4 lines.
So, more lines would be needed
Related Questions
you manage a windows server. for the d:\reports\finances.xls file you explicitly grant the mary user account the allow modify ntfs permissions. you need to move the file from the existing folder to the d:\confidential folder. you want to keep the existing ntfs permissions on the file. you want to accomplish this with the least amount of effort possible. what should you do?
Answers
This will paste the file from the clipboard to the D:\Confidential folder. The file will be moved to the D:\Confidential folder with the same permissions as in the original location.
You need to simply move the file from the existing folder to the D:\Confidential folder without modifying the existing permissions on it. It is possible to keep the existing ntfs permissions on the file while moving it from the existing folder to the D:\Confidential folder. It is simple to accomplish this with the least amount of effort possible without modifying the existing permissions on the file. What should you do to accomplish this You must perform the following procedure to move the file from the existing folder to the D:\Confidential folder without modifying the existing permissions on it Firstly, locate the file that you want to move, which is D:\Reports\Finances.xls.Secondly, right-click on the file, and select Copy from the context menu. The file will be copied to the clipboard.Thirdly, open the D:\Confidential folder where you want to place the file, and right-click on it. Select the Paste option from the context menu.
learn here about Confidential folder here:
https://brainly.com/question/29588297
#SPJ11
does anyone know how to make a astronaut hop while using loop?
Answers
Answer:
In Java
Explanation:
package application;
import java.util.Scanner;
import entities.Astronaut;
public class Main {
public static void main(String[] args) {
Scanner sc = new Scanner(System.in);
System.out.print("How is the astronaut's energy in a scale of 0 to 100? ");
int energy = sc.nextInt();
Astronaut fakeArmstrong = new Astronaut();
while (energy > 0) {
fakeArmstrong.hop();
energy--;
}
System.out.println("The astronaut is tired eh? Let him rest you psychopato");
sc.close();
}
}
----------------------------------------------------------------------------------------------
package entities;
public class Astronaut {
private int bodyEnergy;
public Astronaut() {
}
public int getBodyEnergy() {
return bodyEnergy;
}
public void hop() {
System.out.println("up and down!");
}
}
why is computer called an information processing device ?
Answers
Since, the computer accepts raw data as input and converts into information by means of data processing, it is called information processing machine (IPM).
Computer is called information processing machine because it gives you meaningful information after processing raw data......
Explain why it is important to use the correct spatial
referencing method, map projection and datum in a GIS project
Answers
Answer:
Using the correct spatial referencing method, map projection, and datum in a Geographic Information System (GIS) project is crucial for several reasons:
Explanation:
Accurate Geospatial Analysis: GIS projects involve analyzing and visualizing spatial data. Choosing the appropriate spatial referencing method ensures that the data aligns accurately with the real-world geographic coordinates. It enables accurate geospatial analysis, such as measuring distances, calculating areas, and performing spatial queries.
Data Integration and Interoperability: GIS projects often involve combining datasets from various sources and integrating them into a common spatial framework. Using consistent map projections and datums ensures that different datasets align properly and can be integrated seamlessly. It facilitates data interoperability, allowing different GIS layers to be overlaid and analyzed together accurately.
Avoiding Distortions and Errors: Different map projections introduce distortions in representing the curved Earth surface on a flat map. Each map projection has its own strengths and limitations, and choosing the appropriate one for a specific project minimizes distortions and errors. Using an unsuitable map projection can lead to inaccuracies, such as misshapen features, distorted distances, or incorrect spatial relationships.
Coordinate Transformation and Data Sharing: GIS projects often require sharing data with others or integrating data from different regions or coordinate systems. By using the correct datum and coordinate transformation techniques, data can be accurately converted between different spatial referencing systems, ensuring seamless data sharing and integration. It facilitates collaboration among different stakeholders and allows for the proper analysis of data across different geographic areas.
Standardization and Consistency: Following established spatial referencing methods, map projection standards, and datums ensures consistency across GIS projects and promotes interoperability with existing geospatial datasets and systems. It enables data sharing, comparison, and analysis between different projects and organizations, fostering a standardized and compatible geospatial data environment.
What nomenclature will I use to denote the mass of a component in a given stream? Note: the T
2
symbol in the text editing options allows you to write a superscript. It has a down arrow to the right, click this and then select T
2
for subscript.
Answers
The mass of a component in a given stream is commonly represented as m[sub]2[/sub].
In the field of process engineering, it is common to use specific notations to represent different variables and parameters. When referring to the mass of a component in a given stream, the standard notation is to use the symbol m[sub]2[/sub]. The subscript "2" denotes the specific component being referred to within the stream.
This notation helps to distinguish and identify the mass of individual components in a system where multiple substances may be present. By utilizing this convention, engineers and researchers can accurately represent and analyze the mass flow rates and compositions of various components in a stream.
Learn more about m[sub]2[/sub]
brainly.com/question/33181571
#SPJ11
based on the landauer limit, what is the minimum energy consumption of an exascale computer that operates at room temperature?
Answers
The Landauer Limit is a theoretical minimum energy requirement for digital computing operations.
It states that for every bit of information that is erased in a computational process, a minimum amount of energy is required, which is equal to kT ln(2), where k is the Boltzmann constant, T is the temperature in Kelvin, and ln(2) is the natural logarithm of 2. Assuming that an exascale computer operates at room temperature, which is around 300 Kelvin, the minimum energy consumption per bit of information erased would be approximately 2.9 x 10⁻²¹ Joules.
Therefore, the minimum energy consumption of an exascale computer that operates at room temperature would depend on the number of bits erased during computational processes, which can vary widely depending on the nature and complexity of the calculations being performed.
You can learn more about energy consumption at: brainly.com/question/16025398
#SPJ11
Placing parenthesis around a word, in a search, provides an exact match to that word
in the results.
True
False
Answers
Answer:
Explanation:
Placing parenthesis around a word, in a search, provides an exact match to that word in the results.
True
(Laplace transformation) Find the inverse of the following F(s) function using MATLAB: S-2 s² - 4s+5
Answers
To find the inverse Laplace transform of F(s) = (s - 2)/(s² - 4s + 5) using MATLAB, you can use the ilaplace function.
Here is the MATLAB code:
The Matlab Codesyms s t
F = \((s - 2)/(s^2 - 4*s + 5);\)
f = ilaplace(F, s, t);
The inverse Laplace transform of F(s) is represented by the variable f.
To find the inverse Laplace transform of F(s) = (s - 2)/(s² - 4s + 5) in MATLAB, use the ilaplace function.
This function takes the Laplace transform expression, the Laplace variable, and the time variable, returning the inverse transform expression.
Read more about MATLAB here:
https://brainly.com/question/13715760
#SPJ4
Each of the following three declarations and program segments has errors. Locate as many as you can use the text area below to list the errors. A: class Circle: { private double centerx; double centery; double radius; setCenter (double, double); setRadius (double); } B: Class Moon; { Private; double earthweight; double moonweight; Public; moonweight (double ew); // Constructor { earthweight = ew; moonweight = earthweight / 6; } double getMoonweight(); { return moonweight; } double earth; cout >> "What is your weight? "; cin << earth; Moon lunar (earth); cout << "on the moon you would weigh <
Answers
A: The method signatures for setCenter and setRadius are missing the return type.
There is a semicolon after the class declaration, which should be removed
Corrected code:
class Circle {
private:
double centerx;
double centery;
double radius;
public:
void setCenter(double x, double y);
void setRadius(double r);
};
void Circle::setCenter(double x, double y) {
centerx = x;
centery = y;
}
void Circle::setRadius(double r) {
radius = r;
}
B: There is a semicolon after the class declaration, which should be removed
There should not be a semicolon after "Private" in the class declaration
The function definition for moonweight is missing a return type
The input operator (>>) and output operator (<<) in the main program are reversed
Corrected code:
class Moon {
private:
double earthweight;
double moonweight;
public:
Moon(double ew); // Constructor
double getMoonweight();
};
Moon::Moon(double ew) {
earthweight = ew;
moonweight = earthweight / 6;
}
double Moon::getMoonweight() {
return moonweight;
}
int main() {
double earth;
cout << "What is your weight? ";
cin >> earth;
Moon lunar(earth);
cout << "On the moon you would weigh " << lunar.getMoonweight() << endl;
}
Learn more about setRadius here:
https://brainly.com/question/32164582
#SPJ11
What are the Attitude Control System Errors
that impacted the TIMED NASA mission?
Answers
The Attitude Control System (ACS) is a system that governs the spacecraft's position and orientation in space. When it comes to the TIMED mission, the Attitude Control System (ACS) had two major issues, which are elaborated below:1. A pitch rate gyro drift: It was discovered that one of the pitch rate gyros was affected by a constant drift, which was most likely caused by radiation exposure.
This resulted in attitude estimation errors, which meant that the spacecraft was pointed in the wrong direction.2. An ACS magnetic sensor failure: A sudden voltage spike caused a magnetic sensor's permanent failure, which then resulted in large attitude errors. The ACS magnetic sensor is an important component of the ACS since it determines the spacecraft's orientation in space.
The sensor in question was unable to estimate the correct magnetic field vector and, as a result, could not calculate the spacecraft's orientation correctly. Both the pitch rate gyro drift and the magnetic sensor failure led to the spacecraft's inability to maintain its orientation in space.
To know more about orientation visit:-
https://brainly.com/question/31034695
#SPJ11
You want to connect an external hard drive for backups. Which is the fastest connection used by current external hard drives
Answers
Answer:
thunderbold proly
Explanation:
How many voltage values can be represented with a 10-bit binary code?
A. 128
B. 256
C. 512
D. 1024
Answers
8 bits is enough to represent 256 different numbers. 9 bits is enough to represent 512 numbers. 10 bits can represent 1024 numbers.
1024 voltage values can be represented with a 10-bit binary code. Thus, option D is correct.
What is binary code?A binary code uses a two-symbol method to describe text, central processing unit instruction, and any other material. The signed binary system's "0" and "1" are frequently employed as the two signals in this system. The symbol, command, etc. is given a set of binary digits, often referred to this as bits, by the binary code.
These methods incorporate this program to comprehend operational directives and user actions and provide the user with a pertinent output. 256 distinct numerals can be represented using only 8 bits. 512 numbers can be represented with 9 bits. 1024 values can be represented by 10 bits.
Therefore, option D is the correct option.
Learn more about binary code, here:
https://brainly.com/question/28222245
#SPJ2
1. you have 10 different user ids and passwords for different accounts and have a hard time remembering them all. the best thing to do is:
Answers
The best thing to do if you have multiple user IDs and passwords for different accounts is to create a unique and strong password for each account.
Use a combination of upper and lower-case letters, numbers, and symbols in order to make it difficult for someone to guess your password. You can also use a password manager like LastPass or Password to help you remember all of your passwords, as these services will securely store all of your passwords in one place. Additionally, consider setting up two-factor authentication for each account to add an extra layer of protection.
Learn more about passwords :
https://brainly.com/question/29836274
#SPJ4
Which student is demonstrating the most effective time-management skills?
Answers
Answer:
Carlo sticks to a regular study schedule.
Explanation:
I did this already.
Which class requires campers to work in teams to create a
project?
Answers
Answer:
Summer camp?
Explanation:
write a declaration for these variables: salesquarter1, salesquarter2, salesquarter3, and salesquarter4, all of type money (a structured type with two int fields, dollars and cents) and initialize these variables to $350,249.22, $381,100.00, $291,527.06, and $142,447.38 respectively.
Answers
class Example
{
public static void main ( String[] args )
{
salesquarter1 = "$350,249.22";
salesquarter2 = "$381,100.00" ;
salesquarter3 = "$291,527.06" ;
salesquarter4 = "$142,447.38" ;
System.out.println("salesquarter1 : " + salesquarter1);
System.out.println("salesquarter1 : " + salesquarter2 );
System.out.println("salesquarter1 : " + salesquarter3 );
System.out.println("salesquarter1 : " + salesquarter4 );
}
}
Declaration variable :
In a computer programming language, a variable's declaration is a statement that identifies the variable's name and data type. Declarative code informs the compiler of the existence and location of an entity in the programme. You should initialise a variable as soon as you declare it. Although enumerations and type definitions can be be used as entities, declarations are most frequently used for functions, variables, constants, and classes. Data types or type signature types may also include dimensions, as in the case of arrays, and are normally specified in declarations. A declaration is used in forward declaration to inform the compiler of the existence of the entity; this is significant in strongly typed languages that demand that functions, variables, and constants, together with their types, be declared with a declaration before usage. Declarations are particularly prominent in languages in the ALGOL tradition, including the BCPL family, most prominently C and C++, and also Pascal. Java uses the term "declaration", though Java does not require separate declarations and definitions.
To learn more about declaration variables refer :
https://brainly.com/question/14325424
#SPJ4
Class Example
Public static void main ( String args )
salesquarter1 = "$350,249.22";
salesquarter2 = "$381,100.00" ;
salesquarter3 = "$291,527.06" ;
salesquarter4 = "$142,447.38" ;
System.out.println("salesquarter1 : " + salesquarter1);
System.out.println("salesquarter1 : " + salesquarter2 );
System.out.println("salesquarter1 : " + salesquarter3 );
System.out.println("salesquarter1 : " + salesquarter4 );
Declaration variable :
In a computer programming language, a variable's declaration is a statement that identifies the variable's name and data type. Declarative code informs the compiler of the existence and location of an entity in the programme. You should initialise a variable as soon as you declare it. Although enumerations and type definitions can be be used as entities, declarations are most frequently used for functions, variables, constants, and classes. Data types or type signature types may also include dimensions, as in the case of arrays, and are normally specified in declarations. A declaration is used in forward declaration to inform the compiler of the existence of the entity; this is significant in strongly typed languages that demand that functions, variables, and constants, together with their types, be declared with a declaration before usage. Declarations are particularly prominent in languages in the ALGOL tradition, including the BCPL family, most prominently C and C++, and also Pascal. Java uses the term "declaration", though Java does not require separate declarations and definitions.To learn more about declaration variables refer :
brainly.com/question/14325424
#SPJ4
Relani is a new Internet search engine. The site focuses on displaying the most popular, frequently accessed sites worldwide first in any search, encouraging users to explore the most optimal options. In this case, Relani avoids:_______.
a. Attribute determinance.
b. Peripheral-route processing.
c. Information overload.
d. Central-route processing.
e. Problem recognition
Answers
Relani is a new Internet search engine. The site focuses on displaying the most popular, frequently accessed sites worldwide first in any search, encouraging users to explore the most optimal options. In this case, Relani avoids Information overload. Therefore the correct answer is Option C.
Relani's emphasis on prioritizing the most well-known, regularly visited websites across the globe in any search helps to reduce the number of possibilities displayed to the user and prevent them from being overloaded with information, which is a common issue with other search engines.
Using this strategy, consumers' search processes will be made simpler and the likelihood of information overload would be decreased.
For such more question on Information overload:
https://brainly.com/question/3738775
#SPJ11
_____ is where the OS must prevent independent processes from interfering with each other's memory, both data and instructions. A) Support of modular programming b) Process isolation c) Automatic allocation and management d) Protection and access control
Answers
Support of modular programming is where the OS must prevent independent processes from interfering with each other's memory, both data and instructions. Thus, option A is correct.
What is five principal storage management?The OS has five principal storage management responsibilities: process isolation, automatic allocation and management, support of modular programming, protection and access control, and long term storage.
A long-term storage will ensure your data can be found, understood, accessed and used in the future.The OS, or other system software, acts as a bridge between the user and the hardware, allowing users to complete the tasks that require hardware support.
Therefore, Support of modular programming is where the OS must prevent independent processes from interfering with each other's memory, both data and instructions. Thus, option A is correct.
Learn more about modular programming on:
https://brainly.com/question/11797076
#SPJ1
A computer would do a better job than a human at solving lengthy, complex math problems. True False
Answers
Answer:
I would say true
Explanation:
Humans, by contrast, can master many things, from tying our shoes to cooking an omelet to solving complex math equations. The best AI hardly comes close to the incredible creativity and design of any human, and it’s an open question whether AI can ever become what its prophets claim. Second, when we make AI, we are basically copying our Creator.
Answer:
Its true and give the man brainlyest! or me. that would be nice too!
Explanation:
the truth value of an array with more than one element is ambiguous.
Answers
An array is a collection of elements that are of the same data type, and each of them has a unique identifier. In computing, it is used to organize data and for easy access. The truth value of an array with more than one element is ambiguous because a single condition cannot fully determine the truth or falsity of the entire array.
Consider an array with two or more elements. If we were to test the condition of the array to determine its truth value, we would have to test each element in the array. This is because a single element can be true or false, but the entire array cannot be true or false as a single entity. To overcome this problem, we can use a loop to iterate through each element in the array and test the condition.
If the condition is true for all elements in the array, then the entire array is considered true. However, if the condition is false for at least one element, then the entire array is considered false. In conclusion, the truth value of an array with more than one element is ambiguous, and we must test each element to determine its truth or falsity.
To know more about elements visit:
https://brainly.com/question/31950312
#SPJ11
Which of the following is the fastest computer processing speed?
Group of answer choices
bytes
megahertz
megabytes
gigahertz
Answers
Explanation: One megahertz is equal to one million cycles per second, while one gigahertz equals one billion cycles per second.
This means a 1.8 GHz processor has twice the clock speed of a 900 MHz processor.
Count( *) tallies only those rows that contain a value, while count counts all rows. true false
Answers
False. The statement is incorrect. Both `COUNT(*)` and `COUNT(column_name)` count all rows, including those with NULL values.
The `COUNT(*)` function in SQL counts all rows in a table or a result set, regardless of the presence or absence of values. It considers each row as a separate entity and includes NULL values in the count. This function is useful when you want to obtain the total number of rows, regardless of specific column values.
Similarly, the `COUNT(column_name)` function also counts all rows in a table or result set, but it only considers the non-NULL values in the specified column. It excludes NULL values from the count. This function allows you to determine the number of rows where a particular column has non-NULL values, which can be helpful for data analysis and filtering purposes.
In summary, both `COUNT(*)` and `COUNT(column_name)` count all rows, but `COUNT(*)` includes NULL values while `COUNT(column_name)` counts only non-NULL values in the specified column.
Learn more about NULL values here:
https://brainly.com/question/30462492
#SPJ11
Computer coding is unnecessary for aspiring multimedia designers to learn. True or False? HURRY!!!
Answers
Answer:
True
Explanation:
Consider a partial output from a cost minimization problem that has been solved to optimality. name Final value shadow price constraint R.H side allowable increase allowable desrease
labor time 700 -6 700 100 200
The Labor Time constraint is a resource availability constraint. What will happen to the dual value (shadow price) if the right-hand-side for this constraint increases to 750 ?
a. It will be zero. b. It will be positive. c. It will remain at −6. d. It will be more negative. e. It will be less negative.
Answers
Option(e) is correct. The Labor Time constraint is a resource availability constraint. If the right-hand side for this constraint increases to 750, the dual value (shadow price) will be less negative.
Resource availability constraints imply a scarcity of resources. The limiting factor is that these constraints limit the production or output of an organization. Constraints of resource availability are represented as linear equations in optimization problems, which must be fulfilled. These constraints specify the maximum number of resources that can be used in production, the minimum amount of production that must be achieved, and the availability of specific resources within the plant, among other things.The allowable increase and decrease in the right-hand side of the constraint of labor time are 100 and 200, respectively.The allowable increase is 50. Therefore, the shadow price will be less negative. As a result, the correct option is (e) It will be less negative.To learn more about resource availability constraints please visit:
https://brainly.com/question/14977242
#SPJ11
Which of the following is NOT an important factor when choosing an insurance company?
Licensing
Price
Financial solidity
Location
Answers
Answer:
financial solidity
Explanation:
it will be always be ready while sound or not
A factor which isn't important when choosing an insurance company is: D. location.
What is an insurance company?An insurance company is a business firm that is establish to collect premium from all of their customers (insured) for losses which may or may not occur, so they can easily use this cash to compensate or indemnify for losses incurred by those having high risk.
Generally, it is important to consider the following factors when choosing an insurance company:
LicensingPriceFinancial solidityHowever, location is a factor which isn't important when choosing an insurance company.
Read more on insurance here: https://brainly.com/question/16789837
b
Simeiry: Wit Cenfirm orapticiy that the ecuation is anticentiv
Answers
The equation is not inherently anticentive.
Anticentive refers to a situation where individuals or entities are disincentivized from taking certain actions or pursuing certain outcomes.To determine if the equation is anticentive, we need to assess the incentives or disincentives it creates for different actors or scenarios.The equation itself does not possess a built-in disincentive; it is a neutral mathematical expression.The determination of whether an equation becomes anticentive depends on the context in which it is applied, the associated costs or benefits, and the preferences of the actors involved.If the equation is used in a specific scenario where the resulting outcomes or costs create disincentives, it can be considered anticentive in that particular context.However, it is important to note that the equation itself is not inherently anticentive but rather its application or the consequences it implies can lead to such effects.The equation itself is not anticentive, as it is a neutral mathematical expression. The anticentive nature of the equation arises from its application in specific contexts and the resulting costs or outcomes. Assessing the incentives or disincentives requires a thorough analysis of the associated context and the preferences of the actors involved.
Learn more about Equation :
https://brainly.com/question/29797709
#SPJ11
What Tradeoffs Do Buffer Trees Pose As Compared To LSM Trees?
Answers
Buffer trees and Log-structured merge-tree are both data structures in computer science, and there are several tradeoffs between them.
As compared to LSM trees, buffer trees pose the following tradeoffs:
Buffer trees store data in a balanced binary tree, whereas LSM trees combine the best of both worlds: a memory component for fast operations and a disk component for durability.
Buffer trees are mainly used in-memory database management systems (DBMS), while LSM trees are used in several storage engines. Buffer trees are more efficient when dealing with small datasets, while LSM trees work best when handling large amounts of data.Buffer trees provide faster operations when the dataset fits into memory.
LSM trees are better suited to larger datasets, even those that do not fit into memory. However, buffer trees are less efficient when dealing with large datasets, and they can cause more I/O because they are not optimized for the disk layout
Learn more about binary trees at
https://brainly.com/question/31838009
#SPJ11
Consider the following code: x = 9 y = -2 z = 2 print (x + y * z) What is output? 9 13 14 5
Answers
Answer:
5
Explanation:
x = 9
y -2
x = 2
expression = (x + y * z)
Apply BODMAS rule.
= 9 + (-2 * 2)
= 9 + (-4)
= 9 - 4
= 5
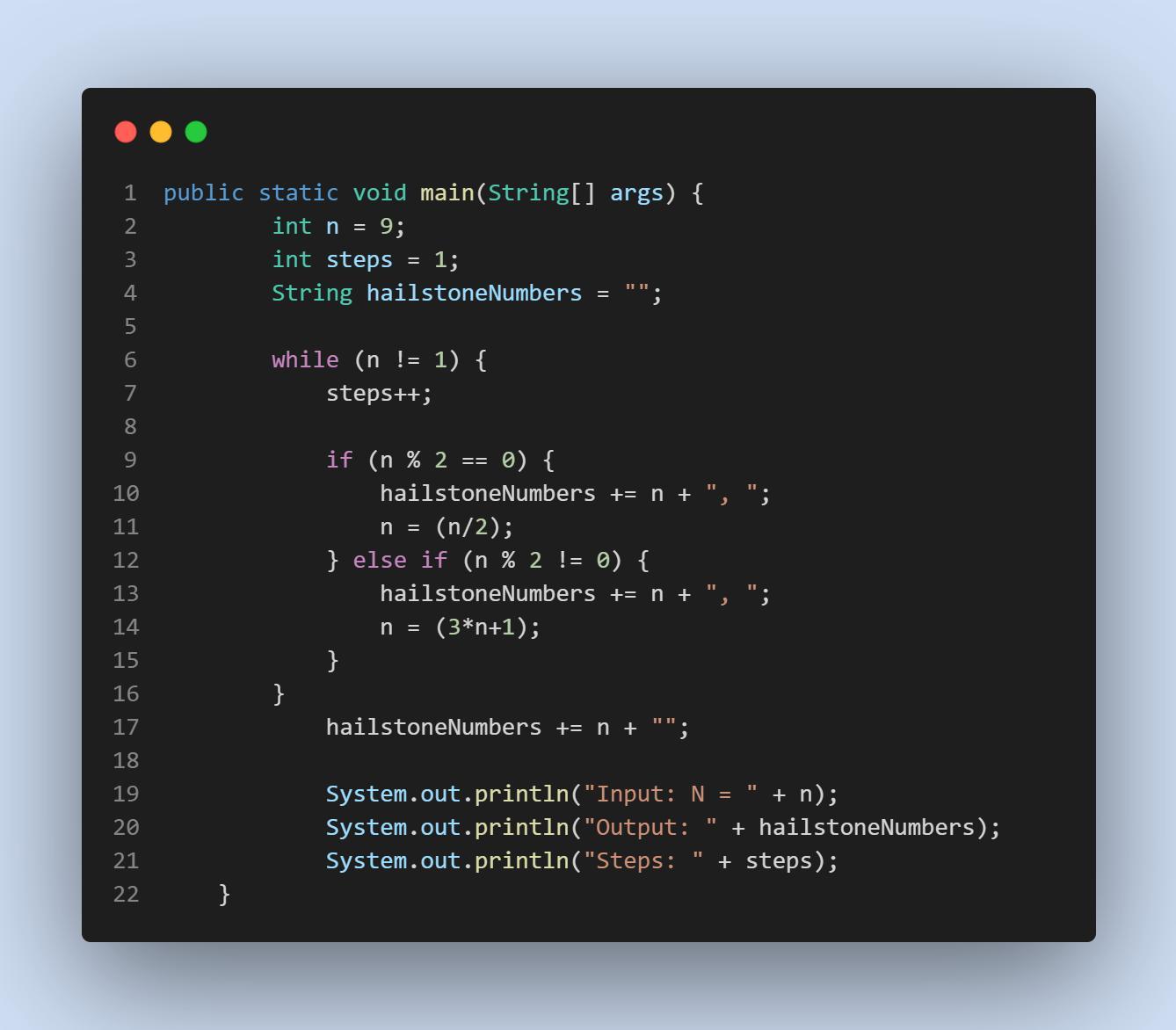
PLEASE HELP! THIS IS FROM A BEGINNERS COMPUTER SCIENCE CLASS:
Write a program that generates the "Hailstone series" for any number from 1 to 1000. The Hailstone series is an interesting sequence of numbers, and can be calculated like this:
If the current value of n is even, the next number in the sequence will be n/2 (use integer division)
If the current value of n is odd, the next number in the sequence will be 3*n + 1
This process is repeated until you reach a value of 1. It is theorized that every integer will eventually end at 1. At the time of writing, this has been tested to be true for numbers up to ~1048, but it has never been proven!
Your program should print the Hailstone series for a particular number and the number of steps it took to reach 1.
Answers
Answer:
This is an iterative approach to the problem; you could also have done a recursive approach. This version is easier to think about in my opinion.
write the importance of Data and software Security
Answers
Answer:
Data security is when protective measures are put in place to keep unauthorized access out of computers, websites, and databases. This process also provides a mechanism for protecting data from loss or corruption.
Explanation:
please make me brainiest if it helps you