Please help
what is Plug and Play technology. What were some early attempts at auto-configuration of hardware, and discuss how these attempts led to the implementation of Plug and Play today.
What are the more difficult devices to install on Windows / Linux / Mac OS X.
Answers
Answer:
Plug and play make reference to the ability of using a device straight out of the box, without needing any specific configuration or drivers.
Explanation:
The plug and play technology is the attempt to create devices that were capable of being used straight out of the box without the need to install any aditional software or dirvers in the computer to allow the proper use of the device, some of the most popular nowadays are the usbs pendrives, or mouse and keyboards. There was a time when every single piece of hardware that you tried to connect to a computer needed a technitian installing the proper software to be able to use that device.
The most difficult devices to install on the different operative systems vary depeding on what you want to do, but you have to rememeber that the different operative systems work on different basis, and apps won't cross-platform between them.
Related Questions
With suitable example, illustrate the use of #ifdef and #ifndef.
Answers
Partitions are used to divide storage spaces into manageable segments.
Fixed partitions have a predetermined size, and they are used to allocate storage space based on the needs of an application. Fixed partitions are commonly used in mainframe systems, where applications require predictable amounts of storage.
For example, consider an organization that uses a mainframe system to manage its payroll. In this scenario, the organization may use fixed partitions to allocate storage space to the payroll application, ensuring that it has access to a specific amount of storage space at all times.
On the other hand, dynamic partitions allow the operating system to allocate storage space based on the requirements of an application. With dynamic partitions, the size of the partition is not fixed, and it can grow or shrink based on the needs of an application.
For example, consider a personal computer that is used to store and manage different types of data. In this scenario, dynamic partitions are used to allocate storage space to different applications based on their storage requirements.
As new applications are installed, the operating system dynamically allocates storage space to ensure that each application has sufficient storage space to function properly.
To know more about Partitions visit:
brainly.com/question/31672497
#SPJ1
Imagine you have just learned a new and more effective way to complete a task at home or work. Now, you must teach this technique to a friend or coworker, but that person is resistant to learning a new way of doing things. Explain how you would convince them to practice agility and embrace this new, more effective method.
Answers
if a person is resistant to learning a new way of doing things, one can practice agility by
Do Implement the changeMake a dialogue with one's Unconscious. Free you mind to learn.How can a person practice agility?A person can be able to improve in their agility by carrying out some agility tests as well as the act of incorporating any form of specific drills into their workouts.
An example, is the act of cutting drilling, agility ladder drills, and others,
A training that tends to help in the area of agility are any form of exercises such as sideways shuffles, skipping, and others.
Therefore, if a person is resistant to learning a new way of doing things, one can practice agility by
Do Implement the changeMake a dialogue with one's Unconscious. Free you mind to learn.Learn more about agility from
https://brainly.com/question/15762653
#SPJ1
Command-based operating systems include
Answers
Answer:
Cpu is the point of the computer
Explanation:
GOT IT REEEEEEEEEEEEE
Where is the fill handle located
Answers
One strategy to improve your productivity is to ensure your _____ is at the top of every to-do list.
Answers
One strategy to improve your productivity is to ensure your most important task (MIT) is at the top of every to-do list
How to improve productivity?To augment your efficiency, it is essential to make sure that your Most Important Task (MIT) is laid out at the commencement of each daily taskset. Evaluating your MIT necessitates figuring out the single errand with the most noteworthy influence on your 24 hours or aid you attain long-term milestones.
By ranking your MIT as the foremost activity in the morning, you can construct a prolific tone for the rest of your day while also sidestepping getting wholly submerged in trivial endeavors. This may cultivate a feeling of success and encourage consistency in productivity per day.
Read more about productivity here:
https://brainly.com/question/2992817
#SPJ1
Role and responsibility of an IT professional
Answers
Your manager asks you to set up a secure network connection at a remote site to move over some backups which protocol would you use?
a. IP.
b. SSH.
c. SFTP.
d. FTP.
e. DHCP.
Answers
The protocol that should be used for establishing a secure network connection is SSH.
The following information is to be considered:
SFTP is secure also it is a protocol for file transferring that applied SSH.IP, FTP, and DHCP should not be for safety purposes as they are not secure.SSH is a secured connection for the remote sites so here the SSH protocol should be used.
Therefore we can conclude that The protocol that should be used for establishing a secure network connection is SSH.
Learn more about the protocol here: brainly.com/question/16985821
Without proper synchronization, which is possible, a deadlock, corrupted data, neither or both? Give reasons for your answer.
need answer pls
Answers
Without proper synchronization, corrupted data is possible due to the fact that a shared datum can be accessible by multiple processes.
Data synchronization simply means the idea of keeping multiple copies of dataset in coherence with one another in order to maintain data integrity. It's the process of having the same data in two or more locations.
Without proper synchronization, corrupted data is possible because a shared datum could be accessed by multiple processes without mutual exclusive access.
Read related link on:
https://brainly.com/question/25640052
In this exercise, we examine how pipelining affects the clock cycle time of the processor. Problems in this exercise assume that individual stages of the datapath have the following latencies:
IF ID EX MEM WB
250ps 350ps 150ps 300ps 200ps
Also, assume that instructions executed by the processor are broken down as follows:
alu beq sw sw
45% 20% 20% 15%
1. What is the clock cycle time in a pipelined and non-pipelined processor?
2. What is the total latency of an LW instruction in a pipelined and non-pipelined processor?
3. If we can split one stage of the pipelined datapath into two new stages, each with half the latency of the original stage, which stage would you split and what is the new clock cycle time of the processor?
4. Assuming there was are no stalls or hazards, what is the utilization of the data memory?
5. Assuming there are no stalls or hazards, what is the utilization of the write-register port of the "Registers" unit?
6. Instead of a single-cycle organization, we can use a multi-cycle organization where each instruction takes multiple cycles but one instruction finishes before another is fetched. In this organization, an instruction only goes through stages it actually needs (e.g., ST only takes 4 cycles because it does not need the WB stage). Compare clock cycle times and execution times with single-cycle, multi-cycle, and pipelined organization
Answers
The clock cycle time in a pipelined and non-pipelined processor will be 350ps and 1250ps respectively.
1. The clock cycle time in a pipelined processor will be the slowest instruction decode which is 350ps. The clock cycle time in a non-pipelined processor will be:
= 250 + 350 + 150 + 300 + 200
= 1250ps
2. The total latency of an LW instruction in a pipelined processor will be:
= 5 × 350 = 1750ps.
The total latency of an LW instruction in a non-pipelined processor will be:
= 250 + 350 + 150 + 300 + 200
= 1250ps
3. Based on the information asked, the stage to be split will be the cycle time. Now, the new cycle time will be based on the longest stage which will be 300ps.
4. It should be noted that the store and load instruction is used for the utilization of memory. The load instruction is 20% of the time while the store instruction is 15% of the time. Therefore, the utilization of data memory will be:
= 20% + 15% = 35%
5. The utilization of the write-register port of the "Registers" unit will be:
= 20% + 45% = 65%
6. The multi cycle execution time will be:
= (5 × 20%) + [4 × (45% + 20% + 15%)]
= (5 × 0.2) + (4 × 0.8)
= 1 + 3.2
= 4.2
The single cycle execution time will be:
= Cycle time non-pipeline / Cycle time pipeline
= 1250/350
= 3.5
Read related link on:
https://brainly.com/question/25231696
In Digital certificate authentication, which key does the supplicant use to encrypt the challenge message before sending it to the verifier?
Answers
Answer:
Supplicant's Private Key
Explanation:
The supplicant uses its PRIVATE KEY to encrypt the challenge message before sending it to the verifier.
This is evident in that in a Digital Certificate Authentication, concerning challenge-response, when the verifier sends a challenge message to the supplicant, the supplicant would encrypt the challenge message with its PRIVATE KEY and send the response message back to the verifier. In return, the verifier would decrypt the response message with the true party’s public key.
What happens when you add an extra line of text to SmartArt using the Text pane?
Answers
Shapes are automatically added to or removed from your SmartArt design as needed.
What is SmartArt design ?SmartArt design is defined as a graphic depiction of your ideas and facts. Using SmartArt, you can transform plain text into something more aesthetically pleasing. It aids in highlighting crucial information or simplifies its interpretation and comprehension.
Click Add Shape After to add a box to the same level as the selected box but after it. Click Add Shape Before to add a box that is at the same level as the selected box but comes before it. Click Add Shape Above to add a box one level above the currently chosen box.
Thus, shapes are automatically added to or removed from your SmartArt design as needed.
To learn more about SmartArt design, refer to the link below:
https://brainly.com/question/28210906
#SPJ1
The Establishment Clause of the First Amendment forbids the government from passing any legislation "respecting an establishment of religion."
What is SmartArt?This section opposes the establishment of an official religion by the government and also forbids government activities that unjustly favor one religion over another. Additionally, it forbids the government from unreasonably favoring either religion or non-religion.
Although some religiously-motivated government activity is acceptable—and perhaps inevitable it is unclear how much the Establishment Clause permits.
The Supreme Court has previously approved the use of public funds for private religious school transportation and textbooks as well as university monies for the printing and dissemination of publications produced by student religious organizations.
Therefore, Government legislation "respecting an institution of religion" is prohibited by the Establishment Clause of the First Amendment.
To learn more about smart art, refer to the link:
https://brainly.com/question/1980413
#SPJ1
How have advancements in technology and social media impacted communication and relationships in our society?
Answers
Answer:The advancement of technology has changed how people communicate, giving us brand-new options such as text messaging, email, and chat rooms,
Explanation:
Answer: the answer will be they allow faster and more efficient communication and can help build relationships.
Explanation:
Directions Interview your parent or any member of your family. Identity
v. Performance Tasks
sources of your family income. Classify the types of your family
income if it is Money Income, Real Oncome or Psychic income

Answers
Answer:
Total family income is first classified by it's four major source, earings of a male head , earings of a wife or female head , earings of a family members , and property or transfer income.
Write a BASH script to create a user account. The script should process two positional parameters: o First positional parameter is supposed to be a string with user name (e.g., user_name) o Second positional parameter is supposed to be a string with user password (e.g., user_password) The script should be able to process one option (use getopts command): o Option -f arg_to_opt_f that will make your script direct all its output messages to file -arg_to_opt_f
Answers
#!/bin/bash
usage() {
echo "Usage: $0 [ -f outfile ] name password" 1>&2
exit 1
}
while getopts "f:" o; do
case "${o}" in
f)
filename=${OPTARG}
;;
*)
usage
;;
esac
done
shift $((OPTIND-1))
name=$1
password=$2
if [ -z "$password" ] ; then
usage
fi
set -x
if [ -z "$filename" ] ; then
useradd -p `crypt $password` $name
else
useradd -p `crypt $password` $name > $filename
fi
How do I give brainliest (I’m new) .Actually answer my question!
Answers
Answer: I’m sorry, but what is your question? Then, I may be able to help you. Also, add a link (image)!
Explanation: Thank You!
Answer:
Hi! There has to be two answers to your question. That is the only way you are able to give a brainliest. You can give a brainliest if you believe a person who wrote an answer to your question fully detailed and organized. It has to answer your question.
Hope this helps! :D
How did the case Cubby v. CompuServe affect hosted digital content and the contracts that surround it?
Answers
Although CompuServe did post libellous content on its forums, the court determined that CompuServe was just a distributor of the content and not its publisher. As a distributor, CompuServe could only be held accountable for defamation if it had actual knowledge of the content's offensive character.
What is CompuServe ?As the first significant commercial online service provider and "the oldest of the Big Three information services," CompuServe was an American company. It dominated the industry in the 1980s and continued to exert significant impact into the mid-1990s.
CompuServe serves a crucial function as a member of the AOL Web Properties group by offering Internet connections to budget-conscious customers looking for both a dependable connection to the Internet and all the features and capabilities of an online service.
Thus, CompuServe could only be held accountable for defamation if it had actual knowledge of the content's offensive character.
To learn more about CompuServe, follow the link;
https://brainly.com/question/12096912
#SPJ1
Design a software system for a bookstore that keeps an inventory of two types of books: Traditional books and books on CD. Books on CD may also contain music. The bookstore purchases books from publishers and sets a price for each book. Customers can purchase books from the bookstore, using either cash or a credit. The bookstore keeps track of which books it has in its inventory, and the books purchased by each customer
a. What are the objects in your object- oriented Solution?
b. What are the interactions between objects in your solution?
c. Which objects "have" other objects?
d. Which Objects "Use" other objects?
e. Which objects are other objects?
Answers
Answer:
Explanation:
a. In this scenario, the best solution would have an Object of Traditional Books, CD, Music, Bookstore and Customer.
b. All five objects would be able to be called by the main program loop and the Customer Object would call upon and use either the Books or CD object, While the Bookstore object would call upon all of the other objects.
c. Both the Bookstore object and Customer object will "have" other objects as the Bookstore needs to hold information on every Book or CD in the Inventory. While the Customer object would call upon the Book and CD object that they are purchasing.
d. The Music Object will extend the CD object and use information on the CD object as its parent class.
e. Since the Music Object extends the CD object it is also considered a CD since it is in CD format like the Books on CD and therefore is both objects.
someone help me
Write a C++ program that display a checkerboard pattern made of stars and blanks, as shown below. A checkerboard is eight squares by eight squares. This will be easier if you first declare two named string constants representing the two different row patterns. Be sure to include appropriate comment in your code, choose meaningful identifiers, and use indentation as do the programs.
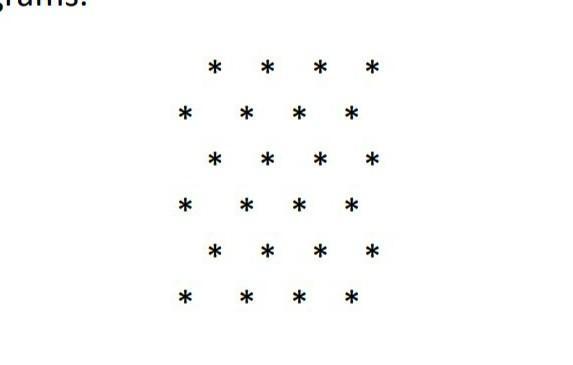
Answers
The program is an illustration of loops.
Loops are used to perform repetitive and iterative operations.
The program in C++ where comments are used to explain each line is as follows:
#include <iostream>
using namespace std;
int main(){
//This declares and initializes all variables
string star = "*", blank = " ", temp;
//The following iteration is repeated 8 times
for (int i = 1; i <= 8; i++) {
//The following iteration is repeated 8 times
for (int j = 1; j <= 8; j++) {
//This prints stars
if (j % 2 != 0) {
cout << star;
}
//This prints blanks
else if (j % 2 == 0) {
cout << blank;
}
}
//This swaps the stars and the blanks
temp = star;
star = blank;
blank = temp;
//This prints a new line
cout << endl;
}
}
Read more about similar programs at:
https://brainly.com/question/16240864
5. What are Excel cell references by default?
Relative references
Absolute references
Mixed references
Cell references must be assigned
Answers
Answer: relative references
Explanation:
By default, all cell references are RELATIVE REFERENCES. When copied across multiple cells, they change based on the relative position of rows and columns. For example, if you copy the formula =A1+B1 from row 1 to row 2, the formula will become =A2+B2.
The most reliable way to store important files without having to worry about backups or media failure is ____________.
A) cloud storage
B) on a USB flash drive
C) on a hard disk drive
D) on an optical disc
Answers
The ideal approach to save data for a longer time is cloud storage. Data security and storage reliability are two advantages of cloud storage that can't be matched. In addition, end-to-end encryption ensures the safety of all transmitted data.
What sum will amounts to Rs 1227 in 9 months at 6%
e emple Interest 2.
Answers
Answer:
given us,
principal (p)= Rs 1227
Time(t)= 9
Rate(r)= 6./.
Here,
simple interest= P×T×R/100
= 1227×9×6/100
= 66258/100
= 662.58
Explanation:
by using simple interest formula
The principal investment required to get a total amount, principal plus interest, of Rs 227.00 from simple interest at a rate of 6% per year for 0.75 years (9 months) is $1,174.16
Given Data
Final Amount A = Rs 1227
Time = 9 months
Rate = 6%
Principal = ?
Equation:P = A / (1 + rt)
Calculation:First, converting R percent to r a decimal
r = R/100 = 6%/100 = 0.06 per year.
Putting time into years for simplicity,
9 months / 12 months/year = 0.75 years
Solving our equation:
P = 1227 / ( 1 + (0.06 × 0.75)) = 1174.1626794258
P = $1,174.16
Learn more about simple interest here:
https://brainly.com/question/2294792
Match the advantage, disadvantage, and similarity of digital libraries and traditional libraries.
must have a computer and Internet access
information immediately available for download
access to many different types of information
:: disadvantage of digital libraries :: advantage of digital libraries :: similarity with traditional libraries
Answers
The matchup are:
Advantage of digital libraries: Information immediately available for download.Disadvantage of digital libraries: Must have a computer and internet access.Similarity with traditional libraries: Access to many different types of information.What is digital libraries?Digital libraries are collections of digital information, such as books, journals, images, videos, and other media, that are stored and managed electronically. They provide access to a vast array of information in a convenient, easily searchable format and can be accessed from anywhere with an internet connection.
Therefore, Digital libraries offer many advantages over traditional libraries, such as faster searching, immediate availability of information, and the ability to access information from anywhere in the world.
Learn more about digital libraries from
https://brainly.com/question/2645741
#SPJ1
System testing – During this stage, the software design is realized as a set of programs units. Unit testing involves verifying that each unit meets its specificatio
Answers
System testing is a crucial stage where the software design is implemented as a collection of program units.
What is Unit testing?Unit testing plays a vital role during this phase as it focuses on validating each unit's compliance with its specifications. Unit testing entails testing individual units or components of the software to ensure their functionality, reliability, and correctness.
It involves executing test cases, evaluating inputs and outputs, and verifying if the units perform as expected. By conducting unit testing, developers can identify and rectify any defects or issues within individual units before integrating them into the larger system, promoting overall software quality.
Read more about System testing here:
https://brainly.com/question/29511803
#SPJ1
A local firewall adds protection to a hardware firewall by protecting a device _______. Select all that apply. WILL GIVE BRAINLIST ONLY IF RIGHT. Please help asap
A. When device is not connected to internet
B. Not connected through hardware firewall
C. cellular traffic that a hardware firewall prevents
D. For traffic that get past a hardware firewall
Answers
A local firewall adds protection to a hardware firewall by protecting a device not connected through the hardware firewall
How to determine the true statement?Basically, there are two types of firewall protection
Local firewallNetwork firewallBoth types of firewall connect the computer from cyberattacks.
However, the local firewall is active when the computer is not connected through the hardware firewall
Hence, the true statement is (b)
Read more about firewalls at:
https://brainly.com/question/25798879
#SPJ9
Gigantic Life Insurance has 4000 users spread over five locations in North America. They have called you as a consultant to discuss different options for deploying Windows 10 to the desktops in their organization. They are concerned that users will be bringing their own mobile devices such as tablets and laptops to connect to their work data. This will improve productivity, but they are concerned with what control they have over the users' access to corporate data. How will Windows 10 help the company manage users who bring their own devices?
Answers
in python Simple geometry can compute the height of an object from the object's shadow length and shadow angle using the formula: tan(angleElevation) = treeHeight / shadowLength. Given the shadow length and angle of elevation, compute the tree height.
Sample output with inputs: 0.4 17.5
Tree height: 7.398881327917831
Answers
Answer:
import math
angle = float(input('Enter Angle: '))
shadowLength = float5(input('Enter Shadow Length: '))
tree_height = math.tan(angle)*shadowLength
print('Tree Height = {}'.format(tree_height))
Explanation:
From the equation given, the first step is to derive the equation for calculating the Tree Height.
In order to calculate the tangent of an angle, the math module has to be imported. math module allows the program to perform advanced math operations.
The program then prompts the user to input values for angle and shadow length.
The inputted values are converted to floats and used in the equation that was derived for Tree height.
Three height is evaluated and the result is printed to the screen

Write an application that combines several classes and interfaces.
Answers
Answer:
Explanation:
The following program is written in Java and it combines several classes and an interface in order to save different pet objects and their needed methods and specifications.
import java.util.Scanner;
interface Animal {
void animalSound(String sound);
void sleep(int time);
}
public class PetInformation {
public static void main(String[] args) {
Scanner scnr = new Scanner(System.in);
String petName, dogName;
String dogBreed = "null";
int petAge, dogAge;
Pet myPet = new Pet();
System.out.println("Enter Pet Name:");
petName = scnr.nextLine();
System.out.println("Enter Pet Age:");
petAge = scnr.nextInt();
Dog myDog = new Dog();
System.out.println("Enter Dog Name:");
dogName = scnr.next();
System.out.println("Enter Dog Age:");
dogAge = scnr.nextInt();
scnr.nextLine();
System.out.println("Enter Dog Breed:");
dogBreed = scnr.nextLine();
System.out.println(" ");
myPet.setName(petName);
myPet.setAge(petAge);
myPet.printInfo();
myDog.setName(dogName);
myDog.setAge(dogAge);
myDog.setBreed(dogBreed);
myDog.printInfo();
System.out.println(" Breed: " + myDog.getBreed());
}
}
class Pet implements Animal{
protected String petName;
protected int petAge;
public void setName(String userName) {
petName = userName;
}
public String getName() {
return petName;
}
public void setAge(int userAge) {
petAge = userAge;
}
public int getAge() {
return petAge;
}
public void printInfo() {
System.out.println("Pet Information: ");
System.out.println(" Name: " + petName);
System.out.println(" Age: " + petAge);
}
//The at (email symbol) goes before the Override keyword, Brainly detects it as a swearword and wont allow it
Override
public void animalSound(String sound) {
System.out.println(this.petName + " says: " + sound);
}
//The at (email symbol) goes before the Override keyword, Brainly detects it as a swearword and wont allow it
Override
public void sleep(int time) {
System.out.println(this.petName + " sleeps for " + time + "minutes");
}
}
class Dog extends Pet {
private String dogBreed;
public void setBreed(String userBreed) {
dogBreed = userBreed;
}
public String getBreed() {
return dogBreed;
}
}

Which of the following statements adds 21 days to the date in the dueDate variable below? var dueDate = new Date();?
a. dueDate = dueDate + 21;
b. dueDate = dueDate.getDate() + 21;
c. dueDate.setDate(21);
d. dueDate.setDate( dueDate.getDate() + 21 );
Answers
Answer:
dueDate.setDate(dueDate.getDate() + 21);
Explanation:
Given
The following declaration (in JavaScript):
var dueDate = new Date();
Required
Add 21 days to dueDate
Assume the date object is [mydate], the syntax to add [n] number of days to [mydate] in JavaScript is:
[mydate].setDate([mydate].getDate() + n);
In this question:
The variable is dueDate and the number of days is 21
Going by:
[mydate].setDate([mydate].getDate() + n);
The correct option is:
dueDate.setDate(dueDate.getDate() + 21);
Do you use commas or periods in Terms Of Conditions?
For example,
in the following terms of conditions should be a comma or a period?
- Professionalism is required, (or period)
- You may not breach this document, (or period)
Furthermore, if a period is used, is the rest of the contract useless?
Answers
Answer:
yes u should use a period
Explanation:
Joseph learned in his physics class that centimeter is a smaller unit of length and a hundred centimeters group to form a larger unit of length called a meter. Joseph recollected that in computer science, a bit is the smallest unit of data storage and a group of eight bits forms a larger unit. Which term refers to a group of eight binary digits? A. bit B. byte O C. kilobyte D. megabyte
Answers
Answer:
byte
Explanation:
A byte is made up of eight binary digits