Open the code6-1_table.css file and create the
following style rules for the indicated elements:
1. For the table element: Add a 20 pixel
grooved gray border and collapse the
table borders.
2. For the th and td elements: Add a 1
pixel solid gray border, set the padding
space to 5 pixels, and align the cell
content with the top-left corner of the
cell.
3. For the caption element, set the
display the caption at the top-left of
the table and set the font size of the
caption text to 1.5em.
4. For col element with the id
first Col, change the background
color to yellow and set the column
width to 150 pixels.
5. For col element with the id
hourCols, set the column width to
75 pixels.
6. Change the background color of the
thead element to aqua.
Answers
Here are the style rules for the indicated elements:
```css
/* 1. For the table element */
table {
border: 20px groove gray;
border-collapse: collapse;
}
/* 2. For the th and td elements */
th, td {
border: 1px solid gray;
padding: 5px;
vertical-align: top;
text-align: left;
}
/* 3. For the caption element */
caption {
caption-side: top;
font-size: 1.5em;
}
/* 4. For col element with the id firstCol */
col#firstCol {
background-color: yellow;
width: 150px;
}
/* 5. For col element with the id hourCols */
col#hourCols {
width: 75px;
}
/* 6. Change the background color of the thead element */
thead {
background-color: aqua;
}
```
These style rules can be added to the code6-1_table.css file to apply the styling to the corresponding elements in the HTML code.
Related Questions
My laptop volume has got really low all of a sudden. It wasn't the best to start with but now i can barely even hear it at 100%. Is there some sort of settings that can change this?
Answers
Answer:
make sure the speaker is clean and you volume setting is on normal there is alot of setting for deaf people so make sure that is correctly
Please help me I don’t know what I’m doing wrong.


Answers
Answer:
Explanation:
I noticed the \n, \n will cause the new line break, delete it.
try code below:
System.out.println(" " + " " + "NO PARKING");
System.out.println("2:00 - 6:00 a.m.");
Recently, Walmart offered a wireless data contract based on bandwidth used, with a minimum monthly charge of $42 for up to 5 gigabytes (GB) of use. Additional GB can be purchased at the following rates: $12 for an additional 1 GB, $28 for an additional 3 GB, and $44 for a capacity of 10 GB. What is the cost for a user who is expecting to use 9 GB
Answers
Answer:
For 9GB of data the user would pay $82 monthly!
Explanation:
To start off, our end goal is 9GB. We have the equation 9 = ? We can add up to our solutions with 1GB, 3GB, and 10GB. We can immediately rule out 10GB, since 9GB ≠ 10GB. To cost the least amount of money we can add up 3GB and 1GB = 4GB + 5GB = 9GB!
So, our equation is 3GB + 1GB + 5GB = 9GB, now lets figure out the cost!
$28 + $12 + $42 = $82
For 9GB of data the user would pay $82 monthly!
Hope this Helps! :)
Have any questions? Ask below in the comments and I will try my best to answer.
-SGO
The following code will not display the results expected by the programmer. Can you find the error? Declare Real lowest, highest, average Display "Enter the lowest score." Input lowest Display "Enter the highest score." Input highest Set average = low + high / 2 Display "The average is ", average, "."
Answers
Based on the information given, the first error in the code is that the Variable name is lowest, NOT low, and Set average = low + high / 2.
How to find the error in the code.For Error 2: Variable name is highest, NOT high and Set average = low + high / 2
For Error 3 : Set average = low + high / 2. Thus, you will need to add the lowest and highest, then perform the division by 2
Set average = (lowest + highest) / 2 is the the correct statement.
Learn more about codes on:
https://brainly.com/question/25875879
PLzzzzzz help me!! I will mark brainiest to the one who answers it right!!
Answer it quickly!!
Write a pseudo code for an algorithm to center a title in a word processor.
Answers
Answer: abstract algebra
Explanation: start with the algorithm you are using, and phrase it using words that are easily transcribed into computer instructions.
Indent when you are enclosing instructions within a loop or a conditional clause. ...
Avoid words associated with a certain kind of computer language.
Answer:
(Answers may vary.)
Open the document using word processing software.
In the document, select the title that you want to center. The selected word is highlighted.
On the Menu bar, select the Format tab.
In the Format menu, select Paragraph.
The Paragraph dialog box opens with two sub tabs: Indents and Spacing, and Page and Line Breaks. The first tab is selected by default.
Adjust the indentation for the left and right side. Ensure that both sides are equal.
Preview the change at the bottom of the dialog box.
Click OK if correct, otherwise click Cancel to undo changes.
If you clicked OK, the title is now centered.
If you clicked Cancel, the title will remain as it is.
Explanation:
I took the unit activity
Drag each tile to the correct box. Match each decimal number to an equivalent number in a different number system. 6910 22810 4210 2710
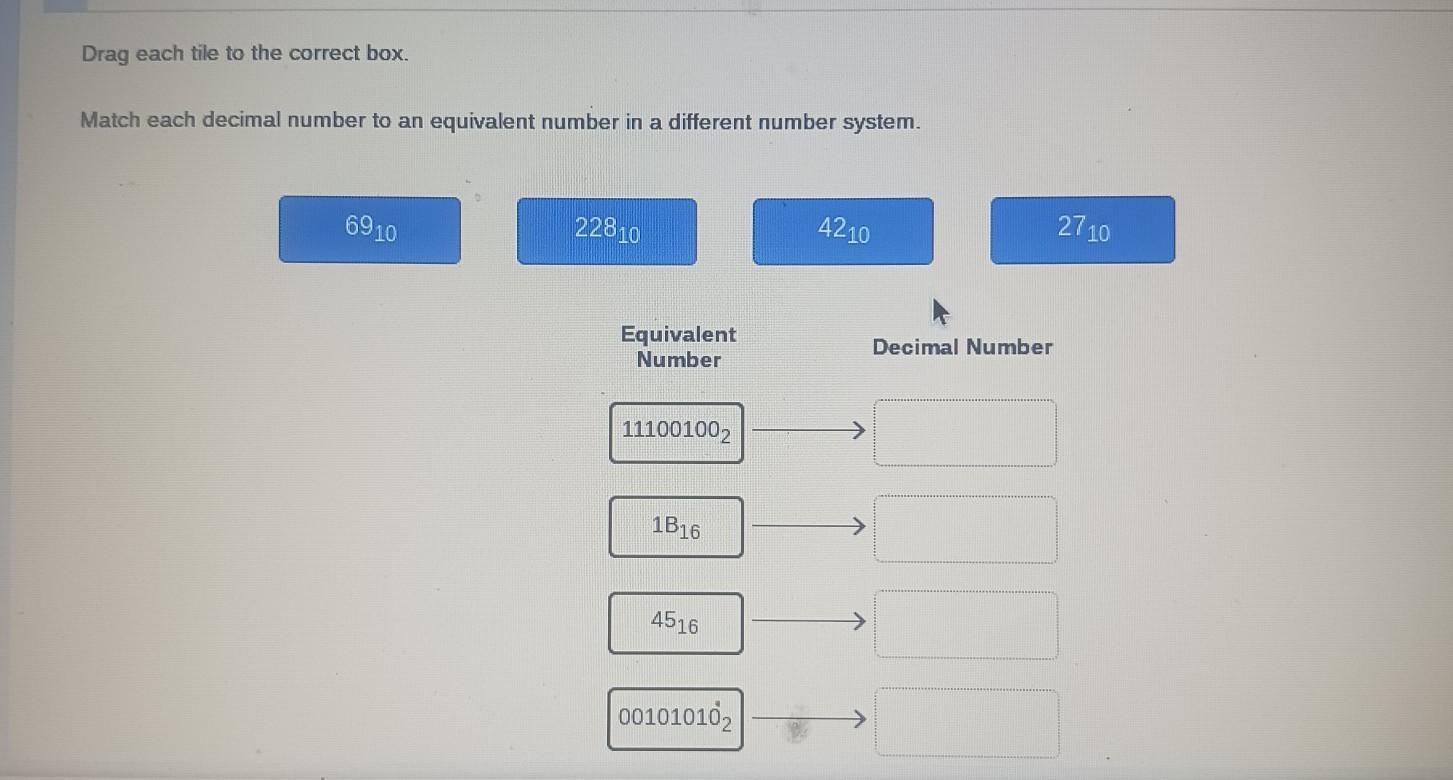
Answers
Explanation:
you can do that with calculator only

Use the drop-down menus to match each description to the correct term.
cassette tapes, VCR tapes, and landline telephones
music recorded on a CD or MP3 file
a series of zeros and ones that represent the recording of your voice
audio reproduction where a copy of a copy will sound exactly the same as the original
Answers
music recorded on a CD or MP3 file - Digital technology
a series of zeros and ones that represent the recording of your voice - Digital data
audio reproduction where a copy of a copy will sound exactly the same as the original - Lossless audio compression
1. What's the minimum RAM requirements to install or upgrade to Windows 11?
1 GB for 32-bit or 2 GB for 64-bit
O4 GB
8 GB
Answers
4 GB
Explanation:You need 4 gigabytes (GB) or greater. Storage: 64 GB* or greater available storage is required to install Windows 11. Extra storage space might be required to download updates and enable specific features. According to Windows 11 system requirements, my 4 GB ram is enough to upgrade my pc from windows 10 to windows 11.
Incompatible Power Adapter: While using your laptop, you notice the battery life is running low. When you plug in the AC adapter that was included with the laptop, an error message is displayed stating that the AC adapter is incompatible. You unplug the AC adapter and plug it back in, but the same message keeps appearing. Why might this be happening
Answers
Answer:
1. in compatible adaptor
2. bad cable
3. software issues
4. damaged laptop battery
Explanation:
there are several reasons why this might be happening.
if this message is being displayed it means that the adaptor may not be compatible. this implies that it is spoilt or the laptop just needs to be shutdown. if this fails, then adaptor needs replacing.
the adaptor cable itself may be faulty and needs changing. the laptop's battery may be too old or damaged and needs replacing. also the laptop may be having software issues and needs updating.
Help me with this digital Circuit please




Answers
A subset of electronics called digital circuits or digital electronics uses digital signals to carry out a variety of tasks and satisfy a range of needs.
Thus, These circuits receive input signals in digital form, which are expressed in binary form as 0s and 1s. Logical gates that carry out logical operations, including as AND, OR, NOT, NANAD, NOR, and XOR gates, are used in the construction of these circuits.
This format enables the circuit to change between states for exact output. The fundamental purpose of digital circuit systems is to address the shortcomings of analog systems, which are slower and may produce inaccurate output data.
On a single integrated circuit (IC), a number of logic gates are used to create a digital circuit. Any digital circuit's input consists of "0's" and "1's" in binary form. After processing raw digital data, a precise value is produced.
Thus, A subset of electronics called digital circuits or digital electronics uses digital signals to carry out a variety of tasks and satisfy a range of needs.
Learn more about Digital circuit, refer to the link:
https://brainly.com/question/24628790
#SPJ1
Question 8 of 10
Which coding standard was developed as a means of representing a wide
range of characters that could be used throughout the world?
O A. Unicode
O B. Hexadecimal
C. Binary
O D. ASCII
Answers
Answer:
Unicode
Explanation:
Answer:
Unicode
Explanation:
A pedometer treats walking 1 step as walking 2.5 feet. Define a method named feetToSteps that takes a double as a parameter, representing the number of feet walked, and returns an integer that represents the number of steps walked. Then, write a main program that reads the number of feet walked as an input, calls method feetToSteps() with the input as an argument, and outputs the number of steps.
Use floating-point arithmetic to perform the conversion.
Ex: If the input is:
150.5
the output is:
60
The program must define and call a method:
public static int feetToSteps(double userFeet)
CODE:
import java.util.Scanner;
public class LabProgram {
/* Define your method here */
public static void main(String[] args) {
/* Type your code here. */
}
}
Answers
Answer:
Here's the completed code that implements the feetToSteps method and the main program that reads the number of feet walked as input and outputs the number of steps walked:
import java.util.Scanner;
public class LabProgram {
public static int feetToSteps(double userFeet) {
double steps = userFeet / 2.5; // Convert feet to steps
return (int) Math.round(steps); // Round steps and convert to integer
}
public static void main(String[] args) {
Scanner scnr = new Scanner(System.in);
double feetWalked = scnr.nextDouble();
int stepsWalked = feetToSteps(feetWalked);
System.out.println(stepsWalked);
scnr.close();
}
}
Explanation:
In this code, the feetToSteps method takes a double parameter userFeet, representing the number of feet walked, and converts it to the number of steps walked by dividing it by 2.5 (since 1 step = 2.5 feet). The result is then rounded to the nearest integer using the Math.round method and casted to an integer before being returned.
The main program reads the number of feet walked as input using a Scanner object, calls the feetToSteps method with the input as an argument, and outputs the number of steps walked using System.out.println. Finally, the Scanner object is closed to free up system resources.
Choose the correct term to complete the sentence.
The media is usually repressed in
governments.

Answers
A dictator government has all power in the hands of one individual/group, suppressing opposition. The media is usually repressed in dictatorial government
What is the government?Dictatorships have limited to no respect for civil liberties, including press freedom. Media is tightly controlled and censored by the ruling authority. Governments may censor or control the media to maintain power and promote propaganda.
This includes restricting freedom of speech and mistreating journalists. Dictators control information flow to maintain power and prevent challenges, limiting transparency and public awareness.
Learn more about government from
https://brainly.com/question/1078669
#SPJ1
brian is a graduate engineer and has passed the fe exam but is not yet licensed. he is employed by a small engineering firm, and works with jim, a licensed professional engineer and owner of the company. the firm is retained to do the structural design of a new rural public school. the project is assigned to brian. after completing his preliminary calculations for the structure, brian does a computer analysis of some of the more complex aspects of the design. this computer analysis shows brian's hand calculations are essentially correct. although brian feels he is quite thorough and conscientious, he notices that jim is rarely in the office, provides little or no supervision, and never checks brian's work before sealing and submitting the plans and specifications to the client for the bidding and construction phases. brian wonders if jim is in conformance with the act and board rules and decides to discuss the matter with him.
Answers
After finishing his initial calculations for the construction, Brian uses a computer to analyze some of the more intricate components of the design.
What are the guiding principles of the engineering code of ethics?By using their knowledge and skills to improve environmental and human welfare, engineers uphold and advance the integrity, honor, and dignity of the engineering profession. serving the public, their employers, and their clients faithfully while being honest and impartial.
This computer study showed that Brian's hand calculations were generally right.
In spite of Brian's conviction that he is meticulous and diligent, he observes that Jim is rarely present in the office, offers scant to no supervision, and never reviews Brian's work before sealing and delivering the drawings and specifications to the customer for approval.
To know more about engineer visit:-
https://brainly.com/question/29529598
#SPJ4
Need comments added to the following java code:
public class Point {
private double x;
private double y;
private String type;
public void setXY(double xx, double yy) {
x = xx;
y = yy;
}
public double getY() {
return y;
}
public String getType() {
return type;
}
public void setType(String type) {
this.type = type;
}
public double[] getDimensions() {
return new double[] { x, y };
}
public String toString() {
return "Point [" + x + ", " + y + "] is " + type;
}
}
Answers
Answer: Are there options for this?
Explanation:
how to download film
Answers
PLEASE HELP
Find five secure websites. For each site, include the following:
the name of the site
a link to the site
a screenshot of the security icon for each specific site
a description of how you knew the site was secure
Use your own words and complete sentences when explaining how you knew the site was secure.
Answers
The name of the secure websites are given as follows:
Each of the above websites had the security icon on the top left corner of the address bar just before the above domain names.
What is Website Security?The protection of personal and corporate public-facing websites from cyberattacks is referred to as website security.
It also refers to any program or activity done to avoid website exploitation in any way or to ensure that website data is not accessible to cybercriminals.
Businesses that do not have a proactive security policy risk virus spread, as well as attacks on other websites, networks, and IT infrastructures.
Web-based threats, also known as online threats, are a type of cybersecurity risk that can create an unwanted occurrence or action over the internet. End-user weaknesses, web service programmers, or web services themselves enable online threats.
Learn more about website security:
https://brainly.com/question/28269688
#SPJ1

what is flow chart for which purpose flowchart is use in programmimg
Answers
A flowchart is a visual representation of a process or algorithm. It uses symbols and arrows to show the steps and the flow of the process. In programming, flowcharts are often used to design and document the logic of a program before it is written in code. They can help programmers visualize the structure of the program and identify potential problems or inefficiencies. Flowcharts can also be useful for explaining the logic of a program to others who may not be familiar with the code..
Hey i need someone to talk to because of life it would be amazing if you can help me
Answers
You are a systems analyst. Many a time have you heard friends and colleagues complaining that their jobs and businesses are being negatively impacted by e-commerce. As a systems analyst, you decide to research whether this is true or not. Examine the impact of e-commerce on trade and employment/unemployment, and present your findings as a research essay.
Answers
E-commerce, the online buying and selling of goods and services, has significantly impacted trade, employment, and unemployment. This research essay provides a comprehensive analysis of its effects.
What happens with e-commerceContrary to popular belief, e-commerce has led to the growth and expansion of trade by breaking down geographical barriers and providing access to global markets for businesses, particularly SMEs. It has also created job opportunities in areas such as operations, logistics, customer service, web development, and digital marketing.
While certain sectors have experienced disruption, traditional businesses can adapt and benefit from e-commerce by adopting omni-channel strategies. The retail industry, in particular, has undergone significant transformation. E-commerce has empowered small businesses, allowing them to compete with larger enterprises and fostered entrepreneurial growth and innovation. However, there have been job displacements in some areas, necessitating individuals to transition and acquire new skills.
Read mroe on e-commerce here https://brainly.com/question/29115983
#SPJ1
During the projects for this course, you have demonstrated to the Tetra Shillings accounting firm how to use Microsoft Intune to deploy and manage Windows 10 devices. Like most other organizations Tetra Shillings is forced to make remote working accommodations for employees working remotely due to the COVID 19 pandemic. This has forced the company to adopt a bring your own device policy (BYOD) that allows employees to use their own personal phones and devices to access privileged company information and applications. The CIO is now concerned about the security risks that this policy may pose to the company.
The CIO of Tetra Shillings has provided the following information about the current BYOD environment:
Devices include phones, laptops, tablets, and PCs.
Operating systems: iOS, Windows, Android
Based what you have learned about Microsoft Intune discuss how you would use Intune to manage and secure these devices. Your answer should include the following items:
Device enrollment options
Compliance Policy
Endpoint Security
Application Management
Answers
I would utilise Intune to enrol devices, enforce compliance regulations, secure endpoints, and manage applications to manage and secure BYOD.
Which version of Windows 10 is more user-friendly and intended primarily for users at home and in small offices?The foundation package created for the average user who primarily uses Windows at home is called Windows 10 Home. It is the standard edition of the operating system. This edition includes all the essential tools geared towards the general consumer market, including Cortana, Outlook, OneNote, and Microsoft Edge.
Is there employee monitoring in Microsoft Teams?Microsoft Teams helps firms keep track of their employees. You can keep tabs on nearly anything your staff members do with Teams, including text conversations, recorded calls, zoom meetings, and other capabilities.
To know more about BYOD visit:
https://brainly.com/question/20343970
#SPJ1
State three modules in HansaWorld and briefly describe what each is used for. (6)
2. With an example, explain what settings are used for. (3)
3. What is Personal Desktop and why is it good to use? Mention two ways in which an
entry can be deleted from the personal desktop. (6)
4. Describe how you invalidate a record in HansaWorld (3)
5. Briefly explain what specification, paste special and report windows are used for. (6)
6. How many reports can you have on the screen at once? How many reports does
HansaWorld have? (4)
7. Describe any two views of the Calendar and how you can open them (4)
8. Describe three (3) ways in which records can be attached to Mails. (6)
9. Describe the basic SALES PROCESS where there is no stock involved and how the
same is implemented in HansaWorld. (12)
Answers
1. We can see here that the three modules in HansaWorld and their brief descriptions:
AccountingInventoryCRM2. We can deduce that settings are actually used in HansaWorld for used for configuring the system to meet specific business requirements.
What is HansaWorld?It is important for us to understand what HansaWorld is all about. We can see here that HansaWorld is actually known to be an enterprise resource planning (ERP) system that provides integrated software solutions for businesses.
3. Personal Desktop is actually known to be a feature in HansaWorld. It allows users to create a personalized workspace within the system.
It can help users to increase their productivity and efficiency.
4. To actually invalidate a record in HansaWorld, there steps to take.
5. We can deduce here that specification, paste special and report windows help users to actually manage data and generate report.
6. There are factors that play in in determining the amount of reports generated.
7. The Calendar on HansaWorld is used to view upcoming events. There is the Day View and there is the Month View.
8. We can see that in attaching records, HansaWorld allows you to:
Drag and drop.Insert linkUse the Mail Merge FunctionLearn more about report on https://brainly.com/question/26177190
#SPJ1
PLEASE HELP IN JAVA
A contact list is a place where you can store a specific contact with other associated information such as a phone number, email address, birthday, etc. Write a program that first takes as input an integer N that represents the number of word pairs in the list to follow. Word pairs consist of a name and a phone number (both strings), separated by a comma. That list is followed by a name, and your program should output the phone number associated with that name. Output "None" if name is not found. Assume that the list will always contain less than 20 word pairs.
Ex: If the input is:
3 Joe,123-5432 Linda,983-4123 Frank,867-5309 Frank
the output is:
867-5309
Your program must define and call the following method. The return value of getPhoneNumber() is the phone number associated with the specific contact name.
public static String getPhoneNumber(String[] nameArr, String[] phoneNumberArr, String contactName, int arraySize)
Hint: Use two arrays: One for the string names, and the other for the string phone numbers.
Answers
Answer: import java.util.Scanner;
public class ContactList {
public static void main(String[] args) {
Scanner scnr = new Scanner(System.in);
// Read the number of word pairs in the list
int n = scnr.nextInt();
scnr.nextLine(); // Consume the newline character
// Read the word pairs and store them in two arrays
String[] names = new String[n];
String[] phoneNumbers = new String[n];
for (int i = 0; i < n; i++) {
String[] parts = scnr.nextLine().split(",");
names[i] = parts[0];
phoneNumbers[i] = parts[1];
}
// Read the name to look up
String name = scnr.nextLine();
// Call the getPhoneNumber method to look up the phone number
String phoneNumber = getPhoneNumber(names, phoneNumbers, name, n);
// Print the phone number, or "None" if the name is not found
if (phoneNumber != null) {
System.out.println(phoneNumber);
} else {
System.out.println("None");
}
}
public static String getPhoneNumber(String[] nameArr, String[] phoneNumberArr, String contactName, int arraySize) {
// Search for the name in the array and return the corresponding phone number
for (int i = 0; i < arraySize; i++) {
if (nameArr[i].equals(contactName)) {
return phoneNumberArr[i];
}
}
// If the name is not found, return null
return null;
}
}
Explanation: The program inputs the number of word sets, stores them in two clusters (names and phoneNumbers), and looks up a title by calling the getPhoneNumber strategy to return the comparing phone number. Prints phone number or "None" in the event that title not found. getPhoneNumber strategy takes nameArr, phoneNumberArr, contactName, and arraySize as contentions. The strategy looks for a title and returns the phone number in case found, something else invalid.
6. This interface uses only commands that you type:
Answers
draw a flowchart to accept two numbers and check if the first number is divisible by the second number
Answers
Answer:
I've attached the picture below, hope that helps...

Which of the following statements should be avoided when developing a mission statement?
The how-to statements.
Describe the “who, what, and where” of the organization.
Be brief, but comprehensive.
Choose wording that is simple.
Answers
Answer: The how-to statements
Explanation:
The mission statement is simply a short summary of the purpose of a company. It is the guideline on how a company will operate. The mission statement states the reason for the existence of a company, products sold or service rendered and the company's goals.
The mission statement should be brief but comprehensive, consist of simple words and describe the “who, what, and where” of the organization.
Therefore, the incorrect option based on the explanation above is "The how-to statements". This shouldn't be part of the mission statement.
state any three operating system categories that you know
Answers
Answer:
Stand-alone
Network
Embedded operating systems.
Explanation:
Stand-alone - OS's such as Windows, macOS, iOS, Android, etc.
Network - Microsoft Windows Server, Unix, etc.
Embedded operating systems. BOIS and other types of firmware pre-installed on a device's motherboard.
Hope this helps :)
The reason for prioritizing your work is to get the
a. Most important jobs done
b. Smallest jobs done
c. Quickest jobs done
d. Least important jobs done
Answers
Answer:
a
Explanation:
Answer:
a. Most important jobs done
Explanation:
public class Exercise_07 { public static void main(String[] args) { System.out.println(bin2Dec("1100100")); // Purposely throwing an exception... System.out.println(bin2Dec("lafkja")); } public static int bin2Dec(String binary) throws NumberFormatException { if (!isBinary(binary)) { throw new NumberFormatException(binary + " is not a binary number."); } int power = 0; int decimal = 0; for (int i = binary.length() - 1; i >= 0; i--) { if (binary.charAt(i) == '1') { decimal += Math.pow(2, power); } power++; } return decimal; } public static boolean isBinary(String binary) { for (char ch : binary.toCharArray()) { if (ch != '1' && ch != '0') return false; } return true; } }
Answers
Answer:
mhm
Explanation:mhm
what do you type in the terminal then? for c++ 4-4 on cengage
Answers
In this exercise we have to use the knowledge of computational language in C++ to write a code that write my own console terminal in C++, which must work .
Writting the code:int main(void) {
string x;
while (true) {
getline(cin, x);
detect_command(x);
}
return 0;
}
void my_plus(int a, int b) {
cout << a + b;
}
void my_minus(int a, int b) {
cout << a - b;
}
void my_combine(string a, string b) {
?????????????;
}
void my_run(?????????) {
???????????;
}
void detect_command(string a) {
const int arr_length = 10;
string commands[arr_length] = { "plus", "minus", "help", "exit" };
for (int i = 0; i < arr_length; i++) {
if (a.compare(0, commands[i].length(), commands[i]) == 0) {
?????????????????????;
}
}
}
See more about C++ at brainly.com/question/19705654
#SPJ1
