_______ once your laptop is in your house, you can relax. your company vpn cannot be stolen from your home.
Answers
The statement "Once your laptop is in your house, you can relax knowing that your company's VPN (Virtual Private Network) cannot be stolen from your home." is true because VPNs use strong encryption methods to protect the data that is being transmitted between your device and the company's network.
As long as you have a secure internet connection and follow proper security protocols, your VPN should remain safe from theft or other security threats. A Virtual Private Network (VPN) is a technology that allows users to create a secure, encrypted connection over a public network, such as the internet. A VPN connection can be used to access resources on a private network, such as a company's internal network, from a remote location, or to encrypt internet traffic to protect it from prying eyes.
When a user connects to a VPN, the user's device establishes a secure connection to a VPN server, which acts as a gateway to the internet. All traffic between the user's device and the VPN server is encrypted, making it difficult for anyone to intercept or spy on the traffic.
Learn more about VPN: https://brainly.com/question/31608093
#SPJ11
Related Questions
In the case study, naldi vs. grunberg, the court ______ the argument for dismissal arguing that the negotiations were only drafted in an email.
Answers
In the case study, Naldi vs. Grunberg, the court rejected the argument for dismissal arguing that the negotiations were only drafted in an email.
What are the characteristics of E-mail?The characteristics of E-mail are as follows:
It involves an instinctive reply to messages.It facilitates the mechanism of auto-forwards and redirection of messages.It involves the facility delivering copies of a message to numerous people. Self-filing and retrieval of messages.According to the question, a formal fallacy may be implemented by the court in order to reject the argument for dismissal. This demonstrates the negotiations that were only drafted in an email format.
Therefore, in the case study, Naldi vs. Grunberg, the court rejected the argument for dismissal arguing that the negotiations were only drafted in an email.
To learn more about Emails, refer to the link:
https://brainly.com/question/25642105
#SPJ1
Describe a feature of a receptionist and explain how she deals with external customers.
Answers
Answer:
A receptionist is a (administrator) who deals with tasks such as, answering a phone call, and giving information to customers. They deal with external customers by letting them talk and not interrupting them..
Alejandro has gone to school startfraction 5 over 7 endfraction of the last 35 days. which expression can be used to determine the number of days alejandro has gone to school?
Answers
The expression that can be used to determine the number of days Alejandro has gone to school is 5/7 x 35.
To find the number of days Alejandro has gone to school, we need to calculate the fraction of days he has attended. Since Alejandro has gone to school for 5/7 of the last 35 days, we can multiply the fraction (5/7) by the total number of days (35). This will give us the number of days he has attended. Therefore, the expression 5/7 x 35 can be used to determine the number of days Alejandro has gone to school.
Know more about fraction here:
https://brainly.com/question/10354322
#SPJ11
Which of these plays an important role in keeping attack traffic off your systems and helps to protect users? check all that apply
Answers
Answer:
Antivirus software
Antimalaware measures
The things which play an important role in keeping attack traffic off your systems and helping to protect users are antimalware measures and Antivirus software. The correct options are a and b.
What are antimalware measures and antivirus software?Antimalware can assist in the prevention of malware assaults by checking all incoming data and preventing malware from being installed and infecting a computer.
When the operating system is unable to communicate with a mouse, the solution is to update the mouse device driver. This is because the mouse driver is frequently and always required to assist the motherboard in interacting with the device.
It is also a software that works between the Operating System and the Mouse because it can effectively and efficiently translate the signals to the motherboard appropriately or ways, which is why Microsoft's generic driver is used.
Therefore, the correct options are a and b.
To learn more about antimalware measures, refer to the link:
https://brainly.com/question/27994271
#SPJ2
The question is incomplete. Your most probably complete question is given below:
Antimalware measures
Antivirus software
Digital attack surfaces
cybersecurity
PLEASE HELP 10 POINTS!!!Click this link to view O*NET’s Work Activities section for Human Resources Managers. Note that common activities are listed toward the top, and less common activities are listed toward the bottom. According to O*NET, what are some common work activities performed by Human Resources Managers? Check all that apply.
resolving conflicts and negotiating with others
operating vehicles, mechanized devices, or equipment
handling and moving objects
establishing and maintaining interpersonal relationships
inspecting equipment, structures, or material
communicating with supervisors, peers, or subordinates
Answers
Answer:
developing objectives,assisting and caring for others, establishing and maintaining interpersonal relation ships, teaching and training others
Explanation:
i missed this question because i listened to the other guy
Answer: A D F
Explanation:
Microcomputer other device on the network that requests and utilizes network resources Hub Switch Client Server
Answers
Answer:
Client.
Explanation:
Cloud computing can be defined as a type of computing that requires shared computing resources such as cloud storage (data storage), servers, computer power, and software over the internet rather than local servers and hard drives.
Generally, cloud computing offers individuals and businesses a fast, effective and efficient way of providing services.
Cloud computing comprises of three (3) service models and these are;
1. Platform as a Service (PaaS).
2. Infrastructure as a Service (IaaS).
3. Software as a Service (SaaS).
A client can be defined as a microcomputer or other device on the network that requests and utilizes network resources.
These network resources that are being requested by the client (client computer) are typically made available by a dedicated computer on the network known as a server.
Write a program that accepts the lengths of three sides of a triangle as inputs. the program output should indicate whether or not the triangle is a right triangle. recall from the pythagorean theorem that in a right triangle, the square of one side equals the sum of the squares of the other two sides. use the triangle is a right triangle. and the triangle is not a right triangle. as your final outputs.
Answers
The code will have to obey the Pythagorean theorem that says square of the hypotenuse side is equals to the sum of the squares of the other legs.
How to write a code that check if a triangle is a right angle by using Pythagoras theorem?
The code is written in python.
def right_triangle(x, y, z):
if x**2 + y**2 == z**2 or y**2 + z**2 == x**2 or z**2 + x**2 == y**2:
print("it is a right angle triangle")
else:
print("it is not a right angle triangle")
right_triangle(6, 10, 8)
Code explanationwe defined as function named "right_triangle". x, y and z are argument which are the length of the triangle.Then we check if the sides obeys Pythagoras theorem.If it does we print a positive statement else we print a negative statement.Learn more about python at: https://brainly.com/question/21437082
#SPJ4

What is the best CPU you can put inside a Dell Precision T3500?
And what would be the best graphics card you could put with this CPU?
Answers
Answer:
Whatever fits
Explanation:
If an intel i9 or a Ryzen 9 fits, use that. 3090's are very big, so try adding a 3060-3080.
Hope this helps!
Why is compression important for video
streaming?
Oto increase the number of frames per second
so that motion appears smooth
Oto watch video without waiting for it to
download
O to improve image quality
O to increase file size
DONE✔
Question
Answers
Compression, important for video streaming to watch video without waiting for it to download.
The technique of compressing a video file such that it takes up less space than the original file and is simpler to send across a network or the Internet is known as video compression.
Since compression makes it possible for video data to be transferred over the internet more effectively, it is crucial for video streaming. The video files are often huge, they would take an extended period to download or buffer before playback if they weren't compressed.
Learn more about video, here:
https://brainly.com/question/9940781
#SPJ1
Paths describe the location of folders and files on your computer. If you have saved your work to c:\documents, then your work has been saved to your
A. computer’s hard drive.
B. flash drive
C. student drive
D. OneDrive
Answers
Answer:
la ventana de micros word
implement an algorithm using divide and conquer technique: given two sorted arrays of size m and n respectively, find the element that would be at the kth position in combined sorted array. a. write a pseudocode/describe your strategy for a function kthelement(arr1, arr2, k) that uses the concepts mentioned in the divide and conquer technique. the function would take two sorted arrays arr1, arr2 and position k as input and returns the element at the kth position in the combined sorted array. b. implement the function kthelement(arr1, arr2, k) that was written in part a. name your file kthelement.py examples: arr1
Answers
Pseudocode/Strategy:
Check if k is within the valid range of combined array indices (0 <= k < m + n). If not, return an error or a sentinel value.
If either arr1 or arr2 is empty, return the kth element from the non-empty array. If k is 0, return the minimum element between arr1[0] and arr2[0].
Calculate two indices, i and j, such that i + j = k - 1. Initially, set i = min(k - 1, m - 1) and j = k - 1 - i.
Compare arr1[i] and arr2[j]:
If arr1[i] is greater, discard the right half of arr1 and the left half of arr2. Recur for k - i - 1.
If arr2[j] is greater, discard the right half of arr2 and the left half of arr1. Recur for k - j - 1.
If arr1[i] and arr2[j] are equal, return arr1[i] (or arr2[j]).
Repeat steps 4-5 until the base cases are reached or the desired kth element is found.
b. Implementation in Python:
def kthelement(arr1, arr2, k):
Learn more about Pseudocode here
https://brainly.com/question/24953880
#SPJ11
one of the biggest roadblocks to ecash and ewallet technologies is _____.
Answers
One of the biggest roadblocks to eCash and eWallet technologies is security concerns and user trust.
The adoption of eCash and eWallet technologies has been hindered by concerns surrounding the safety of users' personal and financial information. As digital payment systems become more widespread, the potential for cyber attacks and data breaches also increases. Users may be hesitant to adopt these technologies due to fears that their sensitive information could be compromised, leading to financial loss or identity theft.
In addition, building user trust is essential for the success of eCash and eWallet systems. Many users may be wary of transitioning to digital payment methods, particularly if they have limited experience with technology or are accustomed to traditional payment methods such as cash and checks. To overcome this obstacle, eCash and eWallet providers must invest in education and outreach to demonstrate the benefits and ease of use of their systems.
Furthermore, regulatory compliance and government oversight play a crucial role in the development and adoption of eCash and eWallet technologies. Providers must navigate a complex landscape of laws and regulations to ensure their services are legally compliant, secure, and accessible to users. This can be a time-consuming and costly process, posing another significant roadblock to the widespread adoption of eCash and eWallet solutions.
In summary, security concerns, user trust, and regulatory compliance are among the most significant roadblocks to eCash and eWallet technologies. Overcoming these challenges is crucial for the successful adoption and growth of digital payment systems.
To know more about eCash, click here;
https://brainly.com/question/30196354
#SPJ11
Using MATLAB, write a Newton's algorithm to solve f(x) = 0. Hence your algorithm should have the message:
(1) Please input your function f(x)
(2) Please input your starting point x = a
After solving, your algorithm should give the message:
"Your solution is = "
If your algorithm does not converge (no solution) write the message:
"No solution, please input another starting point".
Test your algorithm using a simple function f(x) that you know the answer
Answers
The following MATLAB algorithm implements Newton's method to solve the equation f(x) = 0. It prompts the user to input the function f(x) and the starting point x = a. After convergence, it displays the solution. If the algorithm does not converge, it displays a message indicating no solution.
% Newton's method algorithm
disp("Please input your function f(x):");
syms x
f = input('');
disp("Please input your starting point x = a:");
a = input('');
% Initialize variables
tolerance = 1e-6; % Convergence tolerance
maxIterations = 100; % Maximum number of iterations
% Evaluate the derivative of f(x)
df = diff(f, x);
% Newton's method iteration
for i = 1:maxIterations
% Evaluate function and derivative at current point
fx = subs(f, x, a);
dfx = subs(df, x, a);
% Check for convergence
if abs(fx) < tolerance
disp("Your solution is = " + num2str(a));
return;
end
% Update the estimate using Newton's method
a = a - fx/dfx;
end
% No convergence, solution not found
disp("No solution, please input another starting point.");
To test the algorithm, you need to provide a function f(x) for which you know the solution. For example, let's solve the equation x^2 - 4 = 0.
When prompted for the function, you should input: x^2 - 4
And when prompted for the starting point, you can input any value, such as 1. The algorithm will converge and display the solution, which should be 2.
Please note that the provided algorithm assumes the input function is valid and converges within the maximum number of iterations. Additional error handling and convergence checks can be implemented to enhance the algorithm's robustness.
Learn more about MATLAB here:
https://brainly.com/question/30763780
#SPJ11
in a network operating system, this computer coordinates all communication between computers.
Answers
Answer:
Explanation:
In a network environment, the network server computer coordinates all communications between the other computers. Smartphones generally include a network operating system. The operating system is often referred to as the software platform.
youve taken up a contract helping to upgrade the existing industral control network for an oil refiner what network typr should you
Answers
When upgrading the existing industrial control network for an oil refinery, a suitable network type to consider is a SCADA (Supervisory Control and Data Acquisition) network.
SCADA networks are commonly used in industrial settings, including oil refineries, to monitor and control various processes and equipment. They provide real-time data acquisition, visualization, and remote control capabilities for industrial systems.
A SCADA network typically consists of the following components:
1 Supervisory Computers: These are the central control systems responsible for monitoring and managing the industrial processes. They gather data from remote field devices and provide control commands.
2 Remote Terminal Units (RTUs) or Programmable Logic Controllers (PLCs): These devices are responsible for collecting data from field devices, such as sensors and actuators, and transmitting it to the supervisory computers. They also receive control commands from the supervisory computers and actuate the field devices accordingly.
3 Communication Infrastructure: SCADA networks rely on robust communication infrastructure to facilitate the exchange of data between the supervisory computers and RTUs/PLCs. This infrastructure may include wired connections (such as Ethernet or serial connections) or wireless technologies (such as Wi-Fi or cellular communication).
4 Security Measures: Given the critical nature of industrial control networks, implementing strong security measures is vital. This includes measures such as access control, data encryption, network segmentation, firewalls, and intrusion detection systems to protect against cyber threats.
When upgrading the industrial control network for an oil refinery, it is crucial to consider the specific requirements and challenges of the environment. Collaborating with network engineers and industrial control system experts can help determine the most appropriate network design, hardware, and security measures to meet the refinery's needs while ensuring the safety, reliability, and efficiency of the control system operations.
learn more about "network ":- https://brainly.com/question/8118353
#SPJ11
which command os used to find a particular word in a document ?
Answers
Answer:
Ctrl+F
EXPLANATION :
Press Ctrl+F, or click Find on the Home tab. Type the text string into the Find What box. Click Find In. On the menu that opens, click Main Document.
hope it helps you please mark me as brainliest
Answer:
press CTRL + F ..........
Analyzing Uses for PDFs
A PDF file would most likely be used for which situation?
O You need to e-mail more than one file to a friend.
O You want someone to make a lot of edits to a file.
You need to send a file to someone who does not have Word.
O You want to save and print several copies of a file.
Answers
Answer:
You need to send a file to someone who does not have Word
Explanation:
In this case the answer is You need to send a file to someone who does not have Word.
But we use PDF to send files without changing its format.
Answer:
You need to send a file to someone who does not have Word
Explanation:
Edhesive 6.5 code practice
Answers
Answer:
import simplegui
def draw_handler(canvas):
canvas.draw_polygon([(300, 400), (550, 400), (550, 550), (300, 550)], 2, "White")
canvas.draw_polygon([(275, 400), (425, 300), (575, 400)], 2, "White")
canvas.draw_polygon([(400, 475), (400, 550), (450, 550), (450, 475)], 2, "White")
canvas.draw_polygon([(325, 450), (325, 500), (375, 500), (375, 450)], 4, "White")
canvas.draw_polygon([(525, 450), (525, 500), (475, 500), (475, 450)], 4, "White")
frame = simplegui.create_frame('House', 600, 600)
frame.set_canvas_background("Black")
frame.set_draw_handler(draw_handler)
frame.start()
Sorry this is kinda late but just copy and paste the code above (i got a 100%)
The program is an illustration of the simple GUI framework in Python
The GUI framework is used to model programs that require a graphic user interface
The program in Python where comments are used to explain each line, is as follows:
#This imports the simplegui module
import simplegui
#This defines the draw_handler function
def draw_handler(canvas):
#The next five lines draws the boundaries of the polygon, in white
canvas.draw_polygon([(300, 400), (550, 400), (550, 550), (300, 550)], 2, "White")
canvas.draw_polygon([(275, 400), (425, 300), (575, 400)], 2, "White")
canvas.draw_polygon([(400, 475), (400, 550), (450, 550), (450, 475)], 2, "White")
canvas.draw_polygon([(325, 450), (325, 500), (375, 500), (375, 450)], 4, "White")
canvas.draw_polygon([(525, 450), (525, 500), (475, 500), (475, 450)], 4, "White")
#The main method begins here
#This creates the frame of the polygon
frame = simplegui.create_frame('House', 600, 600)
#This sets the background as black
frame.set_canvas_background("Black")
#This calls the draw_handler method
frame.set_draw_handler(draw_handler)
#This starts the frame
frame.start()
Read more about similar programs at:
https://brainly.com/question/19910463
which of the following components are the siem's way of letting the it team know that a pre-established parameter is not within the acceptable range?
a. Trends are patterns of activity discovered and reported to the SIEM.
b. Dashboard consists of customizable information screens that show real-time security and network information
c. Alerts are the SIEM's way of letting the IT team know that a pre-established parameter is not within the acceptable range.
d. Sensors are set up at critical endpoints, services, and other vulnerable locations
Answers
According to the question, 0ption (c) Alerts are the SIEM’s way of letting the IT team know that a pre- established parameter is not within the acceptable range.
Why is SIEM so important?Real-time event monitoring, analysis, and logging are provided for compliance and criteria via security information and event management (SIEM), which combines security information management (SIM) with security event management (SEM).
Enterprises could use SIEM, or security information and event production, to discover potential security threats and vulnerabilities before they have a chance to negatively impact business operations. It surfaces customer data anomalies and uses artificial intelligence to automate many of the manual processes involved in threat identification and incident response, making it a cornerstone in modern security operation center (SOCs) for security and compliance management use cases.
What is the future of SIEM?In the future of SIEM, AI will play a bigger role as cognitive skills enhance the system's decision-making capabilities. As the number of endpoints rises, it will also enable systems to expand and adapt. AI holds the promise of a solution that supports additional data types and a comprehensive understanding of the threat landscape as it grows as IoT, cloud, mobile, and other technologies increase the amount of data that a SIEM tool must consume.
The alert or warning aims to catch the attention of the IT professional or professionals who are watching the network. Monitoring at all times is a smart practice in this regard.
To know more about SIEM visit:
https://brainly.com/question/29661858
#SPJ4
What are the most important benefits of using virtual reality in business training?.
Answers
Virtual reality is a synthetic experience that might be similar to or dissimilar to reality. Virtual reality help business to interact more interestingly with the customer.
What is Virtual reality?Virtual reality is a synthetic experience that might be similar to or dissimilar to reality. Virtual reality applications include entertainment, education, and business.
Every company can use virtual reality to rethink how they present to and interact with their consumers. VR, as a marketing and customer service tool, gives up new avenues for exhibiting products and services. Later on, it is likely to become a one-of-a-kind source of information about client behavior.
Hence, Virtual reality help business to interact more interestingly with the customer.
Learn more about Virtual Reality here:
https://brainly.com/question/13269501
#SPJ4
technological progress promotes the advancement of _______ and ___________.
Answers
Technological progress promotes the advancement of society and the economy.
The advancement of society and the economy is a result of technological progress. The advancement of society can be seen through advancements in healthcare, education, communication, transportation, and more. The economy can also benefit from technological progress, which can lead to increased productivity, improved efficiency, and reduced costs.Technological progress has had a significant impact on healthcare. It has led to the development of new medical treatments, procedures, and equipment. Patients can now receive better and more personalized healthcare, leading to a healthier population.
Technological progress has also improved education. Students can now access online courses, which provide a more flexible learning environment. They can also use educational apps, which can help them learn in a fun and engaging way.Technological progress has also improved communication. People can now communicate with each other in real-time, no matter where they are located. Social media platforms have also allowed people to connect with others from all over the world.Technological progress has also improved transportation.
It has led to the development of more fuel-efficient vehicles, which can reduce air pollution and save money on fuel costs.Technological progress has also had a significant impact on the economy. It has led to increased productivity, improved efficiency, and reduced costs. This has resulted in higher profits for businesses and more job opportunities for people.
Learn more about Cost here,https://brainly.com/question/28147009
#SPJ11
technological progress promotes advancements in various fields such as medicine, communication, and transportation.
technological progress plays a crucial role in promoting advancements in various fields. It enables the development and improvement of different aspects of society, including science, medicine, communication, transportation, and more.
In the field of medicine, technological progress has led to the development of advanced medical equipment, improved diagnostic tools, and innovative treatment methods. For example, the invention of MRI (Magnetic Resonance Imaging) machines has revolutionized the way doctors diagnose and treat diseases. Additionally, advancements in surgical techniques, such as minimally invasive procedures, have reduced patient recovery time and improved outcomes.
In the field of communication, technological progress has transformed the way people connect and share information. The invention of smartphones and the internet has made communication faster and more accessible. Social media platforms and instant messaging apps have revolutionized how people interact and stay connected with each other.
Furthermore, technological progress has greatly impacted the field of transportation. The development of electric vehicles and advancements in autonomous driving technology are paving the way for a more sustainable and efficient transportation system. These advancements aim to reduce carbon emissions and improve road safety.
Overall, technological progress drives innovation and facilitates advancements in multiple areas of human life, including science, medicine, communication, and transportation.
Learn more:About technological progress here:
https://brainly.com/question/31271899
#SPJ11
Which of the following gives one reason that explains why computers can solve logic problems? Computers can executes steps repeatedly without error. Computers follow instructions in a random sequence. O Computers evaluate criteria without direction. Computers are a good option for solving all problems.
Answers
Answer:
Computers follow instructions in a specified sequence.
Computers can replace programmers.
Computers evaluate criteria as instructed and take the specified action.
Computers are capable of executing the same steps over and over without error or fatigue.
answer is A, C and D
2
Explanation:
Answer:
Computers can executes steps repeatedly without error.
Explanation:
or A
Can someone help me with Unit 7 of cmu cs academy python. PLSS EMERGENCYY
Answers
Carnegie Mellon University's CMU CS Academy is an online, graphics-based computer science curriculum taught in Python.
Why is Phyton important?Python has become a data science industry standard, allowing data analysts and other professionals to do complicated statistical computations, produce data visualizations, design machine learning algorithms, handle and analyze data, and accomplish other data-related jobs.
Development time is far more essential than computer run time in today's society. Python just cannot be beat in terms of time-to-market. Python is also efficient and dependable, allowing developers to design complex programs with minimal effort.
Learn more about Phyton:
https://brainly.com/question/31768977
#SPJ1
Refer to Table 8-4. Consider the data above (in billions of dollars) for an economy: Gross domestic product (in billions of dollars) for this economy equals
Answers
If one uses the data above (in billions of dollars), the Gross domestic product (in billions of dollars) for this economy equals $1,200.
What is the GDP about?Note that:
GDP (Gross Domestic Product):
Thus it will be :
Consumption + Investment + Government expenditure + (Export - Import)
Which is:
GDP = 800 + 200 + 300 + (100 - 200)
GDP = $1200 billions
See full question below
Consumption expenditures $800
Investment expenditures 200
Government purchases 300
Exports 100
Imports 200
Wages 800
8) Refer to Table above. Consider the data above (in billions of dollars) for an economy: Gross domestic product (in billions of dollars) for this economy equals
A) $2,200.
B) $1,600.
C) $1,400.
D) $1,200.
Learn more about GDP from
https://brainly.com/question/1383956
#SPJ1
Draw a table and then convert it to a work breakdown structure using PERT.
1.) Work Breakdown Structure.
A] Table
Task Number
Task Name
Duration
Predecessor
B] PERT Chart
Task Name
Task ID
Start Day
Finish Day
Duration
Answers
The table and then convert it to a work breakdown structure using PERT.
The TableA] Table
Task Number | Task Name | Duration | Predecessor
1 | Task A | 5 days | None
2 | Task B | 3 days | None
3 | Task C | 4 days | Task A
4 | Task D | 2 days | Task A
5 | Task E | 4 days | Task B
6 | Task F | 3 days | Task C, Task D
7 | Task G | 2 days | Task E, Task F
B] PERT Chart
Task Name | Task ID | Start Day | Finish Day | Duration
Task A | 1 | Day 1 | Day 5 | 5 days
Task B | 2 | Day 1 | Day 3 | 3 days
Task C | 3 | Day 6 | Day 9 | 4 days
Task D | 4 | Day 6 | Day 8 | 2 days
Task E | 5 | Day 4 | Day 7 | 4 days
Task F | 6 | Day 10 | Day 12 | 3 days
Task G | 7 | Day 10 | Day 11 | 2 days
Note: The PERT chart represents the start and finish days for each task based on their duration and predecessor tasks.
Read more about PERT chart here:
https://brainly.com/question/32198932
#SPJ4
Select the correct answers.
Which are the benefits of leveraging web technologies?
processing of large amounts of data
more manpower
better marketing and customer service
increased production costs
difficulty in handling customer complaints

Answers
Answer:
Explanation:
Select the correct answers.
Which are the benefits of leveraging web technologies?
1) Processing of large amounts of data
2) Better marketing and customer service
E-mail messages create a
permanent record than other forms of business communications.
Answers
Answer:
Explanation:
Business correspondence, like oral speech, refers to the verbal form of business communication. However, the message on the printer has a number of absolute advantages over oral speech. In particular, the compiler has the opportunity to put his thoughts in order and, if necessary, correct the message. More precise constructions than oral ones. In addition, the recipient has the opportunity to read the messages at any time.
For the effective conduct of business correspondence, it is necessary to know and be able to apply the norms of official correspondence, the creation, design and organization of work with letters. At the same time, it should be remembered that a business letter, like any other document created in an organization, is an achievement of its image. In order for business communication to be sufficient, it is necessary to know all the components (including, of course, business correspondence), possession covers communicative competence. The material carrier of business correspondence is a business letter.
A business letter is a document used for transmission over a distance between two correspondents, there is a place for both legal entities and individuals. The concept of "business letter" is used for the generalized name of documents of different content, drawn up in accordance with GOST, sent by mail, fax or other means. At the same time, a document is information about a material carrier that has legal force. The specifics of a business letter and its differences from documents such as a contract or an order are described in that it is less strictly regulated, but, as was said, has legal force. Therefore, letters are registered and found in organizations as outgoing and incoming documentation.
The classification of business correspondence matters in terms of significance: the appointment and discovery of documents, their seriousness and urgency, identification in solving problems, identification of the material availability and reliability of registration, etc. For the solution of business correspondence, the application of documents to the system of management documentation and categories of messages that are acceptable over communication networks is essential. The list of grounds, according to the content, the systematization of business correspondence can be applied, is very extensive. We give a classification of business correspondence according to its main basis.
How do I fix the following error occurred attempting to join the domain?
Answers
Click System from the System and Security menu.Click Change settings under Computer name, network, and workgroup settings.Click Change on the Computer Name tab.Click Domain, write the domain name you want this machine to join, and afterwards click OK under Member of.
Why am I unable to connect my machine to the domain?Check your permissions before adding machines to the domain.The Create computer objects permission in Directories must be granted to the user account in order to join a machine to the domain.Make sure the provided user account can log in locally to a client machine as well.
Can a domain be joined without DNS?A DNS server that is set up correctly -Your workstation won't be capable of connecting to a domain if the DNS server is not set correctly.
To know more about domain visit:
https://brainly.com/question/28135761
#SPJ4
100 POINTS!!!! Write in python
10.8

Answers
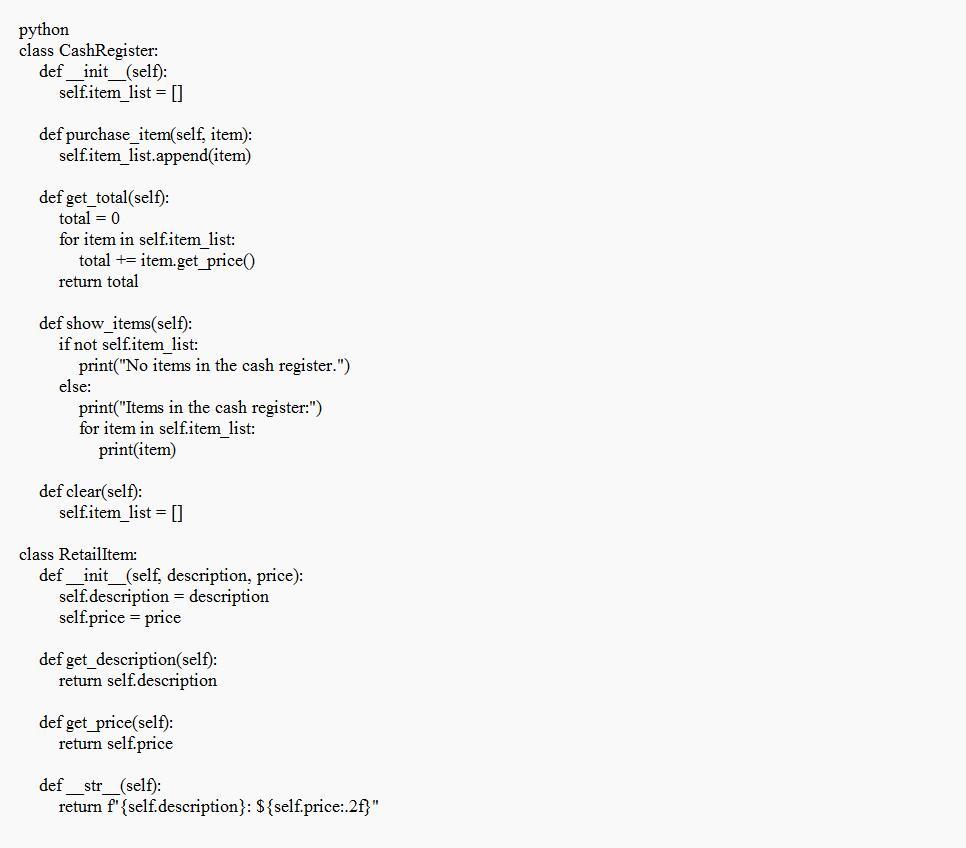
A good example of the implementation of the Cash Register class that is known to have all the methods given in the question is attached below.
What is the Cash Register class?Based on the given program, It initiates three RetailItem instances that signify distinctive products that are available for procurement. The CashRegister object is updated with additional items through the purchase_item function.
The CashRegister's stored items can be viewed through the show_items method, while the get_total method computes and gives back the overall cost. Eventually, the internal list of items within the CashRegister is cleared utilizing the transparent approach.
Learn more about Cash Register class from
https://brainly.com/question/31655783
#SPJ1
See text below
8.
This exercise assumes you have created the RetailItem class for Programming Exer- cise 5. Create a Cash Register class that can be used with the RetailItem class. The Cash Register class should be able to internally keep a list of RetailItem objects. The class should have the following methods:
. A method named purchase_item that accepts a RetailItem object as an argument. Each time the purchase_item method is called, the RetailItem object that is passed as an argument should be added to the list.
. A method named get_total that returns the total price of all the RetailItem objects stored in the Cash Register object's internal list.
⚫ A method named show_items that displays data about the RetailItem objects stored in the Cash Register object's internal list.
⚫ A method named clear that should clear the CashRegister object's internal list.
Demonstrate the Cash Register class in a program that allows the user to select several items for purchase. When the user is ready to check out, the program should display a list of all the items he or she has selected for purchase, as well as the total price.

Type the correct answer in the box. Spell all words correctly.
David has gone to the Niagara Falls with his camera. He wants to click photos of the people around him and also the distant sights. If he can have just one lens with him, which lens would it be?
David can take a lens with him.
Answers
Answer: To zoom in his lens.
Explanation: He can zoom in the lens by turning the lens.