Match the desription with the role of Internal Audit Help executive team understand and use the COCO ERM framework through periodic education over time. Using the ERM framework to help develop audit plans helps facilitate this understanding. Can play a major role in coordinating risk assessments in the organization and help formulate risk responses. The formulation of risk responses aids in the consultive role of Internal Audit. The CAE can be a proponent of a common language. Help ensure a consistent deploymtnt of ERM across the enterprise. Assist with the reporting of exposures and audit results on an aggregate enterprise basis and with the collection, analysis and synthesis of risk-related data. Use the 5 components of ERM framework to assess the effectiveness of risk management (Possibly report to the Board)
Answers
The role of Internal Audit in relation to the COCO ERM (Committee of Sponsoring Organizations of the Treadway Commission Enterprise Risk Management) framework involves helping the executive team understand and utilize the framework, coordinating risk assessments, formulating risk responses, ensuring consistent deployment of ERM, assisting with reporting and data analysis, and assessing the effectiveness of risk management.
Internal Audit plays a crucial role in helping the executive team understand and use the COCO ERM framework by providing periodic education and facilitating the development of audit plans aligned with the framework. This helps the organization in better understanding and applying ERM principles.
Internal Audit can also play a major role in coordinating risk assessments throughout the organization and helping formulate appropriate risk responses. By collaborating with key stakeholders, Internal Audit ensures that risk assessments are comprehensive and risk responses are tailored to mitigate identified risks effectively. This contributes to the consultative aspect of Internal Audit's role.
Furthermore, the Chief Audit Executive (CAE) can advocate for the establishment of a common language related to ERM within the organization. This helps in promoting a shared understanding of risk concepts and terminology, facilitating communication and collaboration across different departments.
Internal Audit also assists in ensuring the consistent deployment of ERM across the enterprise. By providing guidance, monitoring ERM implementation, and promoting best practices, Internal Audit helps in achieving a standardized and integrated approach to risk management.
Another important aspect of Internal Audit's role is assisting with the reporting of exposures and audit results on an aggregate enterprise basis. This involves collecting, analyzing, and synthesizing risk-related data to provide comprehensive reports to management and possibly the Board of Directors. Internal Audit uses the five components of the ERM framework (internal environment, objective setting, event identification, risk assessment, and risk response) to assess the effectiveness of risk management practices within the organization.
Learn more about framework here:
https://brainly.com/question/14661976
#SPJ11
Related Questions
a _____ is a square or rectangle on the start menu that is used to launch an app or application. select one: a. widget b. dialog box c. tile d. button
Answers
A Option C. tile is a square or rectangle on the start menu that is used to launch an app or application.
1. The purpose of a tile is to enable quick and convenient access to apps. By clicking or tapping on a tile, users can launch the associated app or application without the need to navigate through menus or search for it manually. This streamlined approach enhances the user experience by reducing the time and effort required to open apps.
2. Tiles offer several advantages over traditional methods of app launching. Firstly, they provide a visually appealing and organized layout on the Start menu, making it easy for users to locate and identify apps based on their icons or logos. Additionally, tiles can display live information or notifications, such as recent updates or dynamic content, giving users a glimpse of app activity at a glance.
3. Furthermore, tiles can be customized and arranged according to the user's preferences. Users can resize tiles, group them into categories, and organize them in a way that suits their workflow. This level of personalization allows for a personalized and efficient app launching experience.
Therefore, Option C. Tile is the correct option.
To know more about tile visit :
https://brainly.com/question/32397581
#SPJ11
to make sure that parameter values aren't displayed in the url when a servlet is requested, you should use the method in the form tag.
Answers
To make sure that parameter values aren't displayed in the URL when a servlet is requested, you should use the "POST" method in the form tag. When a form is submitted using the "POST" method, the parameter values are sent in the body of the HTTP request instead of being appended to the URL.
This helps to keep the URL clean and prevents sensitive information from being displayed in the address bar. In contrast, when the "GET" method is used, the parameter values are appended to the URL, which can make them visible to users and potentially expose sensitive data. Therefore, to maintain security and privacy, it is recommended to use the "POST" method when handling forms in a servlet.
When a form is submitted using the "POST" method, the parameter values are sent in the body of the HTTP request instead of being appended to the URL.when the "GET" method is used, the parameter values are appended to the URL, which can make them visible to users and potentially expose sensitive data. Therefore, to maintain security and privacy, it is recommended to use the "POST" method when handling forms in a servlet.
To know more about URL Visit:
https://brainly.com/question/29888289
#SPJ11
A feature that allows you to quickly apply the contents of one cell to another cell or range of cells selected.
O auto fill
O auto sum
O fill down
O fill right
Answers
Answer:
Auto fill
Explanation:
I took the test!
Which sentence in the passage shows an effective way to protect your document from misuse? Claire has saved her research paper on her hard disk. She sets an access password while saving the file. Evan is another researcher who saves his file in a special folder by his name. He finds it tedious to remember passwords. Kayla saves her research paper on her desktop for easy access.
Answers
Answer: She sets an access password while saving the file. hope this helps!!!!
Explanation:
You secure a team who’s wants to help you develop, source, test, and launch the product. You spend the next 2 years getting to launch by spending $35,000 in your first year and $40,000 in year 2 prior to launch. Your forecasted sales: Year 1(post launch): 50units Year 2: 150 Year 3: 200 Year 4: 250 Year 5: 250 Your price point is $700 direct to Consumer, Amazon takes 16% of the Gross sale as a fee leaving you with a Net Sale of $588 per unit Your on-going cost to run the business starting in the launch year is the following: Year 1: 35% of Net Revenue, Year 2 through 5: 30% of Net Revenue. What COGS, and therefore net profit%, (to the nearest 10thof a $ and %)do you need to make this a positive NPV at 8% Cost of Capital (interest rate)?
Please show your work in excel. Thank you!
Answers
To make this a positive NPV at 8% cost of capital, the COGS needs to be $350.40 and the net profit percentage needs to be 40.5%.
To calculate the COGS and net profit percentage needed to make this a positive NPV at 8% cost of capital, we need to first calculate the net revenue for each year. The net revenue is calculated by subtracting the Amazon fee and the ongoing cost to run the business from the gross sale price.
Net revenue for Year 1: $588 x 50 units = $29,400
Net revenue for Year 2: $588 x 150 units = $88,200
Net revenue for Year 3: $588 x 200 units = $117,600
Net revenue for Year 4: $588 x 250 units = $147,000
Net revenue for Year 5: $588 x 250 units = $147,000
Next, we need to calculate the ongoing cost to run the business for each year:
Ongoing cost for Year 1: 35% x $29,400 = $10,290
Ongoing cost for Year 2: 30% x $88,200 = $26,460
Ongoing cost for Year 3: 30% x $117,600 = $35,280
Ongoing cost for Year 4: 30% x $147,000 = $44,100
Ongoing cost for Year 5: 30% x $147,000 = $44,100
To calculate the COGS, we need to subtract the net profit percentage from 100% and then divide the ongoing cost by the result. We can use the NPV formula in Excel to calculate the NPV of the cash flows.
Using Excel, we can calculate the COGS and net profit percentage needed to make this a positive NPV at 8% cost of capital. The COGS is $350.40 and the net profit percentage is 40.5%.
Therefore, to make this a positive NPV at 8% cost of capital, the COGS needs to be $350.40 and the net profit percentage needs to be 40.5%.
learn more about excel here:
https://brainly.com/question/3441128
#SPJ11
HELP ASAP!!!
What are some potential challenges that society will face given the digital revolution? You may want to think particularly of the news industry.
Answers
Write a program that reads some integers between 1 and 100 and counts the occurrences of each. Note that if a number occurs more than one time, the plural word "times" is used in the output. Note the integers are entered in one line separated by a space.
Sample Run
Enter integers between 1 an 100, inclusive: 2 5 6 5 4 3 23 43 2
2 occurs 2 times
3 occurs 1 time
4 occurs 1 time
5 occurs 2 times
6 occurs 1 time
23 occurs 1 time
43 occurs 1 time
Answers
A program that reads integers between 1 and 100 and counts the occurrences of each integer. Here is the explanation and code for the problem.
The program starts by asking the user to enter integers between 1 and 100, inclusive. The input is split into a list of integers using the `split()` method and the `map()` function.
2. Next, a dictionary called `counts` is created to hold the counts of each number.
3. The program loops through the list of numbers, checking if each number is already in the `counts` dictionary. If it is, the count is incremented. If it's not, the number is added to the dictionary with a count of 1.
4. Finally, the program loops through the `counts` dictionary and prints out each number and its count, with the correct pluralization. If the count is 1, the word "time" is used. If the count is greater than 1, the word "times" is used.
Take input as a list of integers separated by a space, Use a dictionary to store each integer as the key and its count as the value. Iterate through the list and update the dictionary counts, Print the integers and their occurrence in the output.
To know more about code visit:
https://brainly.com/question/31228987
#SPJ11
Your computer uses 4 bits to represent decimal numbers (0, 1, 2, 3 and so on) in binary. What is the SMALLEST number for which an overflow error occur?
A. 14
B. 15
C. 16
D. 17
Answers
Answer:d
Explanation:
Using numeric representations in computers, it is found that the smallest number for which an overflow errors occurs is 16, option c.
----------------------
In an unsigned n-bit arithmetic in a computer, the numbers represented are in the following range: From 0 to \(2^{n} - 1\). If a value is greater than \(2^{n} - 1\), an overflow error occurs, as there are not enough bits to represent the number.----------------------
In this question, the computer uses 4 bits, thus \(n = 4\).The largest number that is represented without causing overflow is \(2^n-1 = 2^4 - 1 = 16 - 1 = 15\)Thus, the smallest number which causes overflow is 16, option c.A similar question is found at https://brainly.com/question/18379853
write short note on social and emotional interaction
Answers
Social and emotional interaction refers to the way individuals interact with others and their ability to manage their own emotions in social situations. This involves skills such as communication, empathy, and understanding social cues.
Social and emotional interaction skills are critical for individuals to navigate social situations successfully and form strong relationships. Effective communication, empathizing with others, and understanding social cues can enhance one's ability to connect with others and foster positive interactions. Being able to regulate one's emotions in social situations is also crucial for managing stress, building resilience, and maintaining mental health. These skills can be improved through practice, such as engaging in social activities, seeking feedback, and learning from experience. Education and therapy can also provide valuable tools and strategies for developing social and emotional interaction skills and promoting healthy relationships and emotional wellbeing.
Learn more about mental health here;
https://brainly.com/question/31708532
#SPJ11
Which of the following is an example of a compressed file format?
A. MP3
B. WAV
C. AIFF
D. CD Quality
E. MP%
Answers
WAV is an example of a compressed file format.
What is Compressed File Format?Compressed file format refer to file which is the reduced version of the original size and may contain two or more files and also directory. smaller than its original size and could contain on Compressed files can be downloaded easily and transmit more faster than other files.
What is WAV?Waveform Audio(WAV) File Format refer to an audio form of file format which was created by Microsoft and IBM for the purpose storing audios on personal computer.
Therefore, Waveform Audio(WAV) file format is an example of a compressed file format.
Learn more on Compressed file format from the link below.
https://brainly.com/question/4478177
There are numerous data storage companies in existence today, each with their own plans to store data for different purpose and size. Let's consider a scenario where you have recently been employed by a such company called "StorageSolutions" which specializes in storing huge amount of data. Now, you have been assigned the task to store a number in a variable. The number is 51,147,483,647,321. You have different data types like Integer, Float, Char, and Double. Which data type will you use from the given data types to store the given number and why? Justify your answer with logical reasoning
Answers
Storage Solutions is one of the many data storage companies with different data storage purposes and sizes. In this scenario, you have to store a number 51,147,483,647,321 in a variable.
There are several data types available, including Integer, Float, Char, and Double. Based on the requirements, we will select the appropriate data type to store the value. Since the value is relatively large, we can rule out the Char and Integer data types.
Double data types provide greater precision than float data types and are ideal for high-precision calculations. Since the value we need to store is 51,147,483,647,321, we need a data type that can hold a larger number of digits than the Float data type can. In this situation, Double is the best data type choice for storing large numbers. Hence, we can use the Double data type to store the value.
To know more about Storage visit:
https://brainly.com/question/86807
#SPJ11
Write a statement that declares a prototype for a function named add which has two int parameters and returns an int.
Answers
Answer:
int add(int a, int b);
Explanation:
The prototype has a return type of int.
We call it add and give it two parameters a and b relatively.
If a change is made to the active
cell, what type of cell will also
change?
Precedents
Dependents
Answers
Answer:
precedents
Explanation:
Which of the following opens when the Labels icon is clicked?
Answers
The option that opens when the labels icon is clicked is: "Envelopes & Labels dialog box & the Labels tab" (Option D)
What is the explanation for the above response?The function of the Envelopes & Labels dialog box & the Labels tab is to allow the user to create and print labels for various purposes.
The Labels tab provides options for selecting the label manufacturer and product number, as well as specifying the layout and content of the labels. Users can choose from a variety of preset label sizes or create their own custom size.
The dialog box also allows users to add text, images, and barcodes to the labels. Once the labels are created, they can be previewed and printed, making it a useful tool for creating address labels, product labels, and more.
Learn more about labels icon at:
https://brainly.com/question/20713933
#SPJ1
Full Question:
Although part of your question is missing, you might be referring to this full question:
Which of the following opens when the Labels icon is clicked?
Envelopes menu
Labels menu
Envelopes & Labels dialog box 7 the Envelopes tab
Envelopes & Labels dialog box & the Labels tab
What is the difference between the complete scan and the resident shield?
Answers
A complete scan and resident shield are two types of antivirus scans. The main difference between them is that a complete scan checks all files and folders on your computer, while a resident shield scans only files as they are accessed or modified.
A complete scan is a thorough antivirus scan that checks all files and folders on your computer's hard drive. This scan examines all of your system's files to detect viruses, malware, and other threats that may be present. A complete scan is time-consuming and can take several hours to complete, depending on the size of your hard drive.
As you work on your computer and open or modify files, the resident shield scans the files for malicious code and alerts you if any are found. This type of scan is very useful because it provides immediate protection against threats that may try to infect your computer while you're working on it.
To know more about antivirus visit:
https://brainly.com/question/29356216
#SPJ11
Which of the following is a definition of conventions?
A: the ideas readers absorb while reading a text
B: rules that help readers understand the meaning of texts
C: the meaning of texts understood through symbols
D: questions you ask to understand a texts meaning
Answers
Answer: B: rules that help readers understand the meaning of texts
Explanation:
The statement that represents a definition of conventions is ruled that help readers understand the meaning of texts. Thus, the correct option for this question is B.
What is Convention?A convention may be defined as an assembly of persons that intentionally met for a common purpose in order to facilitate a common work and methodology. It is generally an assembly or conference of a set of people.
In this assembly or conference, the motive is to understand the actual meaning of the texts with respect to rules and regulations. It represents a way through which something is accomplished or done.
In literature, conventions are the defining characteristics, or must-haves, of a given genre. Any aspiring gumshoe worth their weight in magnifying glasses will convey to you that detectives, suspects, and a hearty dose of all conventions of the mystery genre.
Therefore, the statement that represents a definition of conventions is ruled that helps readers understand the meaning of texts. Thus, the correct option for this question is B.
To learn more about Conventions, refer to the link:
https://brainly.com/question/24147773
#SPJ2
Define the term Project brief? why is it important to do planning?
Answers
Answer: the project brief is a document that provides an overview of the project.
Explanation: It says exactly what the designer, architect, and contractor needs to do to exceed your expectations and to keep the project on track with your goals and your budget.
PLS HURRY!!
Look at the image below

Answers
Answer:
1. A function can use variables as parameters.
2. A function can have more than one parameter.
3. The definition of a function must come before where the function is used.
Explanation:
The definition of a function can come before or after it is used - I am pretty sure it cannot be placed after the function is being used. It should always come before it is used, so this statement is false.
A function can use variables as parameters - this is true, variables are just labels to hold data.
A function can have more than one parameter - this is true.
A function must have a return value - functions do not always have to return values. It could simply print, so this statement is false.
The definition of a function must come before where the function is used - As said earlier, the definition of functions must come before it is used/called. This statement is true.
Hope this helps :)
Given an array of numbers, write a function that prints in the console another array which contains all the even numbers in the original array, which also have even indexes only. Test 1: getOnlyEvens([1, 2, 3, 6, 4, 8]) prints [ 4] Test 2: getOnlyEvens([0, 1, 2, 3, 4]) prints [0, 2, 4]
Answers
In Test case 1 Output: [4] and in Test case 2 Output: [0, 2, 4].
Here's an example implementation of the `getOnlyEvens` function in JavaScript that achieves the desired behavior:
```javascript
function getOnlyEvens(arr) {
const result = [];
for (let i = 0; i < arr.length; i += 2) {
if (arr[i] % 2 === 0) {
result.push(arr[i]);
}
}
return result;
}
// Test case 1
console.log(getOnlyEvens([1, 2, 3, 6, 4, 8])); // Output: [4]
// Test case 2
console.log(getOnlyEvens([0, 1, 2, 3, 4])); // Output: [0, 2, 4]
```
In the `getOnlyEvens` function, we iterate over the original array starting from index 0 and incrementing `i` by 2 in each iteration. This ensures that we only consider elements with even indexes.
For each element at an even index, we check if it is an even number (`arr[i] % 2 === 0`). If it is, we add it to the `result` array using the `push` method.
Finally, we return the `result` array, which contains all the even numbers from the original array that have even indexes.
Know more about array:
https://brainly.com/question/31605219
#SPJ12
What is logical operator in a basic? Mention its types and explain one of them with its truth table?
Answer this for 20 points pls
Answers
Answer:
This indicates an or operation in a logical expression.
Types: And, or and not.
A favorably adjudicated background investigation is required for access to classified information
a. True
b. False
Answers
A favorably adjudicated background investigation is required for access to classified information: A. True.
What is a classified source material?In Computer technology, a classified source material is sometimes referred to as classified information and it can be defined as an information source that comprises very important, restricted, and sensitive information that must only be shared and disseminated secretly with authorized persons.
What is an adjudicative process?In Computer technology, an adjudicative process can be defined as a strategic process which typically involves an examination and background investigation of a sufficient period of the life of a person, in order to make an affirmative determination that he or she is eligible for a security clearance and access to a classified source material or classified information.
Read more on classified source material here: brainly.com/question/15346759
#SPJ1
Complete the procedure for forwarding a message by selecting the correct term from each drop-down menu.
1. ___ or open a message.
2. Click the Forward button.
3. In the To field, enter the names of intended recipients.
4. Click the ___ button.
Answers
Answer:
Preview; send.
Explanation:
Communication can be defined as a process which typically involves the transfer of information from one person (sender) to another (recipient), through the use of semiotics, symbols and signs that are mutually understood by both parties. One of the most widely used communication channel or medium is an e-mail (electronic mail).
An e-mail is an acronym for electronic mail and it is a software application or program designed to let users send texts and multimedia messages over the internet.
The procedure for forwarding a message to a recipient include;
1. Preview or open a message. This is to ensure that the appropriate or specific message is selected.
2. Click the Forward button. This button opens the dialog box to allow the sender input various details about the message and the recipient.
3. In the To field, enter the names of intended recipients.
4. Click the send button. This button automatically forwards the message to the intended recipient(s).
an array that can be sized and bound at runtime is a question 20 options: a) static array b) fixed stack-dynamic array c) stack-dynamic array d) fixed heap-dynamic array e) none of the above
Answers
An array that can be sized and bound at runtime is a stack-dynamic array. The correct answer is option c.
A stack-dynamic array, also known as a dynamic stack or a resizable stack, is a type of data structure that provides a stack interface while using a dynamic array as its underlying storage.
A stack is a linear data structure that follows the Last-In-First-Out (LIFO) principle, meaning that the last element added to the stack will be the first one removed. A dynamic array, on the other hand, is a type of array that can be resized during runtime, allowing for more efficient memory usage and flexible data storage. By combining these two concepts, a stack-dynamic array can grow or shrink dynamically as elements are pushed onto or popped off of the stack. This allows for efficient memory usage and avoids the need to pre allocate a fixed amount of memory for the stack, which can lead to wasteful memory usage if the stack does not reach its maximum capacity.
Learn more about stack-dynamic array here: https://brainly.com/question/29216876
#SPJ11
Give two types of peripheral storage media that the tablet computer could use.
Answers
1. MicroSD Cards: Tablet computers often have a built-in microSD card slot that allows users to expand the storage capacity of the device. MicroSD cards are small, portable, and can store various amounts of data depending on their capacity. They are commonly used for storing photos, videos, documents, and other files.
2. USB Flash Drives: Tablets with USB ports or support for USB On-The-Go (OTG) can utilize USB flash drives as peripheral storage media. USB flash drives are compact, lightweight, and offer varying storage capacities. They can be easily connected to a tablet via a USB cable or adapter, allowing for convenient data transfer and storage.
How would you rate this answer on a scale of 1 to 5 stars?
how does digital and hybrid computers differ in portability
Answers
Answer:
Digital computers perform functions like mathimatical,compex calculations. while hybrid computers work with the duo combinations like analog and tempature.
Explanation:
I passed the class A+
yourwelcome :)
thank me if it was correct for you too.
Can you solve this challenging activity?

Answers
Answer:
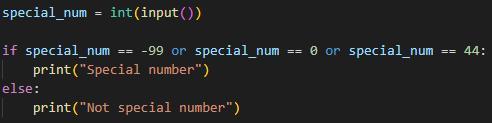
special_num = int(input())
if special_num == -99 or special_num == 0 or special_num == 44:
print("Special number")
else:
print("Not special number")
Explanation:
Suzanne has inserted an image into her document and would like to adjust the color and contrast of the image.
Where can Suzanne find these options?
O Design tab, Picture Tools group
o Contextual tab Picture Tools > Format in the Picture Tools group
O Contextual tab Picture Tools > Format in the Adjust group
o Contextual tab Picture Tools > Format in the Align group
Answers
Answer:
C.) O Contextual tab Picture Tools > Format in the Adjust group
Explanation:
Computer simulation of the Ising chain Use Program Ising1D to simulate the one-dimensional Ising model. It is convenient to measure the temperature in units such that J/k=1. For example, a temperature of T=2 means that T=2J/k. The "time" is measured in terms of Monte Carlo steps per spin (mcs), where in one Monte Carlo step per spin, N spins are chosen at random for trial changes. (On the average each spin will be chosen equally, but during any finite interval, some spins might be chosen more than others.) Choose H=0. The thermodynamic quantities of interest for the Ising model include the mean energy E, the heat capacity C, and the isothermal susceptibility χ. (a) Determine the heat capacity C and susceptibility χ for different temperatures, and discuss the qualitative temperature dependence of χ and C. Choose N≥200. (b) Why is the mean value of the magnetization of little interest for the onedimensional Ising model? Why does the simulation usually give M
=0 ? (c) Estimate the mean size of the domains at T=1.0 and T=0.5. By how much does the mean size of the domains increase when T is decreased? Compare your estimates with the correlation length given by (5.56). What is the qualitative temperature dependence of the mean domain size? (d) Why does the Metropolis algorithm become inefficient at low temperatures?
Answers
The Metropolis algorithm relies on accepting or rejecting spin flips based on energy differences, and at low temperatures, the energy differences between states become smaller, leading to slower convergence and longer simulation times.
(a) To determine the heat capacity C and susceptibility χ for different temperatures in the Ising model, you can use the Ising1D program to simulate the system. By running the simulation at different temperatures and measuring the corresponding values of energy and magnetization, you can calculate the heat capacity and susceptibility.
The heat capacity (C) represents the system's response to changes in temperature. At low temperatures, the heat capacity is typically low because the system is more ordered, and there is less energy available for fluctuations. As the temperature increases, the heat capacity also increases, indicating that the system becomes more responsive to temperature changes.
The susceptibility (χ) measures the system's response to an applied magnetic field. Similar to the heat capacity, the susceptibility is usually low at low temperatures due to the system's ordered state. As the temperature increases, the susceptibility also increases, indicating that the system becomes more susceptible to magnetic field influence.
The qualitative temperature dependence of χ and C in the Ising model typically shows a peak or maximum at the critical temperature (Tc) of the system. Below Tc, both χ and C increase as the temperature decreases, reaching a maximum at Tc. Above Tc, both χ and C decrease as the temperature increases.
(b) In the one-dimensional Ising model, the mean value of magnetization (M) is of little interest because there is no long-range order or spontaneous magnetization at any finite temperature in one dimension. Due to thermal fluctuations, the average magnetization usually fluctuates around zero, resulting in M≈0 in the simulation.
(c) To estimate the mean size of domains at temperatures T=1.0 and T=0.5, you can analyze the spatial patterns of spins in the simulation. The domains refer to regions where the spins have the same orientation. By measuring the sizes of these regions, you can estimate the mean domain size.
The mean size of domains generally increases as the temperature decreases. At higher temperatures, thermal fluctuations cause frequent spin flips, resulting in smaller domains. As the temperature decreases, the spins become more ordered, and larger domains form.
To compare your estimates with the correlation length given by (5.56), you can calculate the correlation length based on the spatial correlations between spins. The correlation length characterizes the range over which spin orientations are correlated. If your estimates align with the correlation length, it indicates consistency between the simulated system and the theoretical model.
The qualitative temperature dependence of the mean domain size is an increasing trend as the temperature decreases. Smaller domains are observed at higher temperatures, while larger domains are observed at lower temperatures.
(d) The Metropolis algorithm, which is commonly used in simulations of the Ising model, can become inefficient at low temperatures due to the slow exploration of the energy landscape. At low temperatures, the system is trapped in energy minima, making it difficult for the simulation to explore higher-energy states and reach equilibrium. The Metropolis algorithm relies on accepting or rejecting spin flips based on energy differences, and at low temperatures, the energy differences between states become smaller, leading to slower convergence and longer simulation times. Alternative algorithms, such as the Wolff algorithm or cluster algorithms, are often employed to improve efficiency at low temperatures by allowing for more efficient updates of spin configurations.
Learn more about temperatures :https://brainly.com/question/27944554
#SPJ11
What are the parts of an if-else statement in Java?
O condition, first action, second action
condition, operator, first action
O first action, second action, third action
first action, condition, second action
Answers
An if-else statement in Java is a control flow statement that allows the programmer to specify different actions based on a certain condition. The basic structure of an if-else statement in Java consists of three parts: the condition, the first action, and the second action.
The condition is a boolean expression that is evaluated to determine whether it is true or false. If the condition is true, the first action is executed. If the condition is false, the second action is executed. The condition, first action, and second action are specified as follows:
if (condition) {
first action;
} else {
second action;
}
In this syntax, the condition is specified in parentheses after the keyword "if". The first action is specified within the curly braces that follow the "if" keyword. The second action is specified within the curly braces that follow the "else" keyword.
It's important to note that the first action and second action can be any valid Java statement, including simple statements such as assignment statements, method calls, or more complex statements such as nested if-else statements or loops. The if-else statement allows the programmer to choose between two alternative actions based on the evaluation of a condition.
To know more about Java: https://brainly.com/question/30354647
#SPJ4
What action(s) from the CRUD method should be used to describe the required data usage in the case of the function name is "Take delivery of a new goods" for the entity types: GOODS and DELIVERY?
Answers
The CREATE and UPDATE actions from the CRUD method should be used to describe the required data usage in the case of the function name "Take delivery of new goods" for the entity types GOODS and DELIVERY.
This is because CREATE is the action used for generating and inserting data into the database, whereas UPDATE is used for changing the existing data. A CRUD (Create, Read, Update, and Delete) is an acronym for database operations to enable the storage and management of data.
It is a standard and widely recognized method of performing database operations. The CREATE action involves adding a new item to the database, which is what happens when a new delivery of goods arrives. This operation stores new data in the database to allow the records to be retrieved when required. Similarly, the UPDATE operation allows the records in the database to be updated if new information becomes available or data errors occur. Therefore, the CREATE and UPDATE actions from the CRUD method should be used to describe the required data usage in the case of the function name "Take delivery of new goods" for the entity types GOODS and DELIVERY.
To know more about data visit:
https://brainly.com/question/28285882
#SPJ11