Match each disk type on the left with its corresponding description/features on the right. Each disk type may be used once, more than once, or not at all.
Dynamic disks.
Basic Disks
___
Basic disks.Support up to 128 volumes:
Use primary and extended partitions:
Are supported by all operating systems:
Support volumes that use discontinuous disk space:
Store partitioning information in a hidden database on all such disks in the system:
Only support volumes made up of contiguous disk space:
Answers
Dynamic disks can span multiple hard disks as a single volume, allowing for disk mirroring and striping,Basic disks support up to 128 volumes.Dynamic disks: Allow for dynamic volumes, which can be resized without the need for reformatting
Dynamic Disks: Store partitioning information in a database, which is stored on one or more dynamic disks: Support fault tolerance: Can be extended by adding new hard disks to the system: Store partitioning information in a hidden database on all such disks in the system: Support volumes that use discontinuous disk space: Use primary and extended partitions: Basic Disks Are supported by all operating systems: Basic Disks Support volumes that use discontinuous disk space:
To Learn More About Dynamic and Basic Disks: https://brainly.com/question/27960878
#SPJ11
Related Questions
what are the answers for theses question?




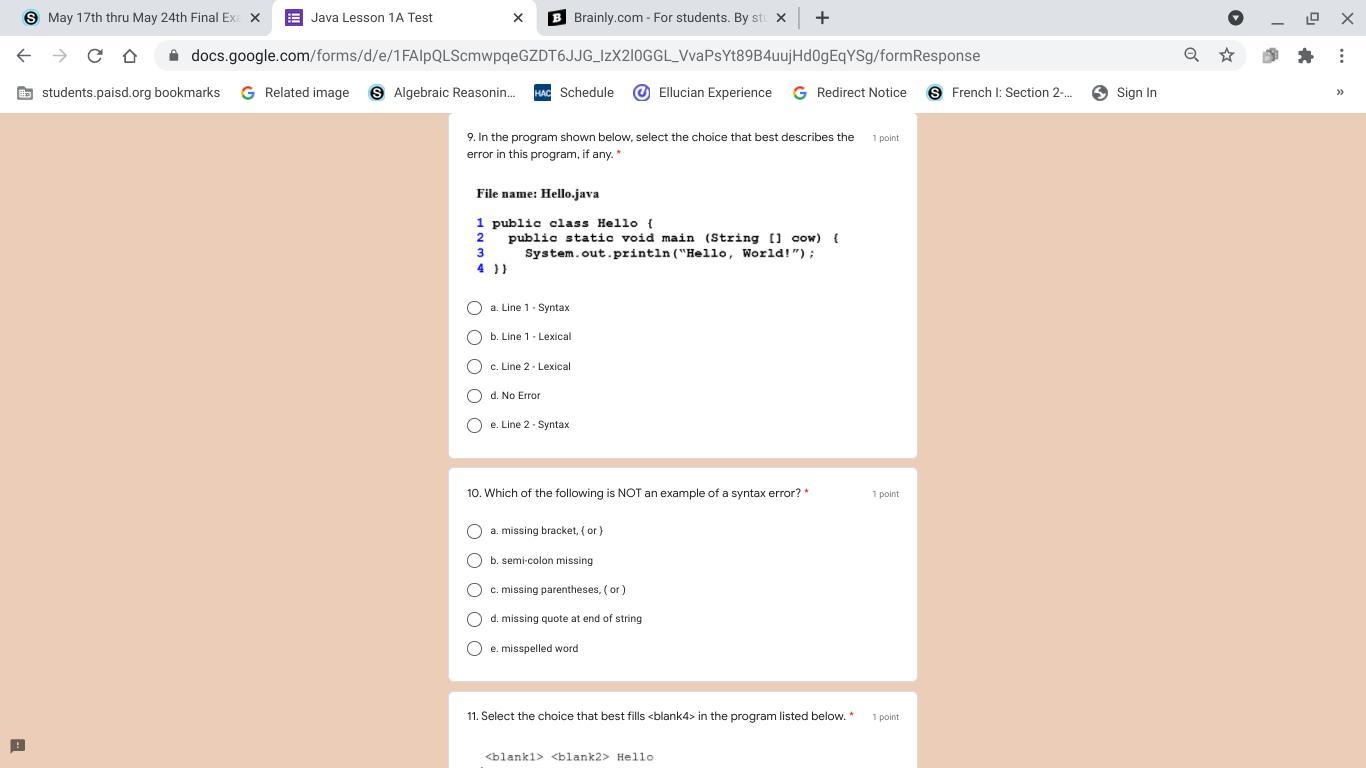
Answers
Answer: me no comprende coding
Explanation:
sorry
When you delete a file or folder in windows what happens to it.
Answers
Answer: When you delete a file, Windows removes the pointer and marks the sectors containing the file's data as available. From the file system's point of view, the file is no longer present on your hard drive and the sectors containing its data are considered free space.
Explanation:
1. Explain your understanding of digital analytics (200
words+)
2. Explain these web analytics terms: Bounce rate, Impression,
Keyword, Organic Search, Page Views, Web Analytics, Load Time,
Crawler/Sp
Answers
Digital analytics refers to the practice of collecting and analyzing data from digital sources to gain insights and make data-driven decisions.
It involves tracking user interactions and behaviors on websites, mobile apps, and other digital platforms. The data collected is used to measure website performance, user engagement, and other key metrics, allowing businesses to optimize their digital strategies and improve overall effectiveness. In web analytics, bounce rate measures the percentage of visitors who leave a website after viewing only one page. A high bounce rate indicates low engagement or lack of relevance for visitors. Impression refers to the number of times an advertisement or piece of content is displayed to users.
Keyword is a specific word or phrase used to optimize content for search engines and improve organic search visibility. Organic search refers to the process of users finding a website through non-paid search engine results. Page views represent the number of times a webpage is viewed by users. Web analytics involves collecting and analyzing data to understand website performance and user behavior. Load time refers to the time it takes for a webpage to fully load. A crawler is a program used by search engines to discover and index webpages.
Learn more about Digital analytics here:
https://brainly.com/question/29734922
#SPJ11.
A mobile phone can be ordered in 2 different sizes (large and small) and 3 different colors (gold, silver and black). Construct a tree diagram to show all possible combinations of mobile phones that can be ordered.
Answers
The tree diagram below illustrates all the possible combinations of mobile phones that can be ordered based on two sizes (large and small) and three colors (gold, silver, and black):
Mobile Phone
|
-------------------------
| |
Large Small
| |
--------------- ---------------
| | | | | |
Gold Silver Black Gold Silver Black
In the diagram, the first level represents the choice of size, with "Large" and "Small" as the options. The second level represents the choice of color, with "Gold," "Silver," and "Black" as the options for each size.
This tree diagram provides a clear visualization of all the possible combinations of sizes and colors for the mobile phones. It helps in understanding the total number of options available and can be used as a reference when making decisions or analyzing different scenarios.
Learn more about probability analysis here:
https://brainly.com/question/32996461
#SPJ11
Choose the correct answer
1. Which of the variable names given below, is invalid?
O Goodluck
O
d2420
O input
O Abcd
Answers
not valid bro so u check again
2 The software needed to send an email is:
+
A presentation software
B web authoring software
C communication software
D graphics software
Answers
Answer:
C communication software
Explanation:
C communication software IS THE ANSWER
What are the disadvantages of using a page description diagram?
A.
They lack flexibility.
B.
Only an experienced designer can create an effective PDD.
C.
They are difficult to understand.
D.
Web developers cannot combine them with wireframes.
Answers
A disadvantage of using a page description diagram is that: B. only an experienced designer can create an effective PDD.
What is PDD?PDD is an acronym for page description diagram and it can be defined as a type of diagram which is used to outline the content and elements on webpages, especially by organizing their elements into low, medium, and high priority.
In Computer technology, a disadvantage of using a page description diagram is that: B. only an experienced designer can create an effective page description diagram (PDD).
Read more on web diagrams here: https://brainly.com/question/16418487
#SPJ1
1. Implement a three layer feedforward artificial neural network (ANN) training by Backpropagation for the MNIST dataset (https://en.wikipedia.org/wiki/MNIST_database). Output the prediction accuracy. The dataset can be downloaded here: https://pypi.org/project/python-mnist/. Or you can download it from other source
upload the solution with step by step in jupyter and screenshots of output and source code.
Thank you
Answers
Implementing a three-layer feedforward artificial neural network (ANN) training by Backpropagation for the MNIST dataset and outputting the prediction accuracy can be achieved by using Jupyter notebook, Python, and the appropriate libraries such as TensorFlow or PyTorch.
How can you implement a three-layer feedforward artificial neural network (ANN) training by Backpropagation for the MNIST dataset and obtain the prediction accuracy?To implement a three-layer feedforward artificial neural network (ANN) training by Backpropagation for the MNIST dataset, follow these steps:
1. Set up the Jupyter notebook environment and import the necessary libraries such as TensorFlow or PyTorch.
2. Load the MNIST dataset using the provided link or any other reliable source.
3. Preprocess the dataset by performing tasks such as data normalization, splitting it into training and testing sets, and converting labels into one-hot encoded vectors.
4. Design the architecture of the three-layer feedforward ANN with appropriate activation functions, number of hidden units, and output layer.
5. Initialize the network parameters (weights and biases) randomly or using predefined methods.
6. Implement the forward propagation algorithm to compute the predicted outputs.
7. Implement the backpropagation algorithm to update the weights and biases based on the calculated errors.
8. Repeat steps 6 and 7 for a specified number of epochs or until convergence.
9. Evaluate the trained model on the testing set and calculate the prediction accuracy.
10. Upload the solution in Jupyter notebook along with the necessary screenshots of the output and the complete source code.
Learn more about Backpropagation
brainly.com/question/32647624
#SPJ11
Facility Layout: Create a fast food or manufacturing plant layout, identify, and draw the particular facility. Describe the nature of your production and the importance of the layout setting. Consider and describe the activities that take place in that facility. Why are things set up as they are? Be creative.
Answers
A facility layout, also known as plant layout, refers to the arrangement of machinery, equipment, workstations, storage areas, offices, and other items that make up a facility.
A well-designed facility layout is critical for both manufacturing plants and fast-food restaurants. This is because the layout sets the tone for the activities that occur in the facility, such as the movement of goods, customer service, and employee interaction.
Fast Food Layout
A fast-food layout comprises several elements that come together to form an efficient and functional system. The layout must provide the best possible service to customers, maintain high levels of efficiency, and ensure that the facility is clean and hygienic. The kitchen layout should include workstations for preparing different types of food. For example, there should be a station for preparing burgers, a station for preparing fries, and a station for preparing drinks.
The layout of the kitchen should also consider the traffic flow and the sequence of operations. For example, the layout should place the refrigerator next to the preparation area for quick access. The layout of the restaurant must provide for a pleasant environment for the customers, and it should enable them to move around quickly.
Manufacturing Plant Layout
A manufacturing plant layout should provide for a smooth flow of work and maximize productivity. The facility should include storage areas, workstations, and other necessary equipment. The layout should also consider the nature of the production process.
For example, a manufacturing plant layout for a car assembly plant will have different features from a manufacturing plant layout for a pharmaceutical plant. The layout of a car assembly plant will focus on the flow of the assembly line, while the layout of a pharmaceutical plant will prioritize safety and cleanliness.
In conclusion, a facility layout is essential in both fast-food restaurants and manufacturing plants. A good layout should provide for efficiency, functionality, and productivity. By creating a facility layout that takes into account the flow of goods, customer service, and employee interaction, businesses can ensure that they achieve optimal performance.
Learn more about workstations :
https://brainly.com/question/13085870
#SPJ11
Which approach is ideal for ensuring that a Webpage is maintained and does not appear neglected to users?
A. Using more images
B. Using a GUI HTML editor
C. Using automated link-checking software
D.Using internal hyperlinks in essential pages
Answers
Answer:
D
Explanation:
I think putting hyperlink in essential pages is a good idea as it may guide a user
In which number system do the digital computer work
Answers
The numbers that are operated on by a digital computer is known as the binary number system; binary digits, or bits. These are 0's and 1's.
suppose you have a long list of digits (0-9) that you want to write to a file. from a storage standpoint, would it be more efficient to use ascii or utf-8 as an encoding? what is the most efficient way to create an even smaller file to store the information?
Answers
Because we only need digits (0-9) in this case, ASCII and UTF-8 will be identical in terms of storage. This is because the first 128 characters in UTF-8 are stored in a single byte, whereas ASCII is simply a subset of UTF-8.
To make a smaller file, we can either store the numbers as their binary equivalents or try to compress the data using Huffman Coding, which is a greedy algorithm used for compressing data without data loss.
What is ASCII?
ASCII, which stands for American Standard Code for Information Interchange, is a standard for assigning letters, numbers, and other characters to the 256 slots available in the 8-bit code.
The ASCII decimal (Dec) number is derived from binary, the universal computer language. The lowercase "h" character (Char) has a decimal value of 104, which is "01101000" in binary, as shown in the table below.
To know more about ASCII, visit: https://brainly.com/question/20361136
#SPJ4
Question 12 (1 point)
Generally, each pixel in an image creates 25 bytes of data.
True
False
Answers
Answer:
This is B: False
Explanation:
Each pixel of an image creates 24 bits, or 3 BYTES of data for color, and 1 byte for black and white.
What do Cc and Bcc stand for?
O Clear Copy and Binary Clear Copy
O Counter Claim and Best Counter Claim
O Crystal Clear and Binary Crystal Clear
O Carbon Copy and Blind Carbon Copy
Answers
Thank You!
write a python program to print the following series 3..10..31..94......n
Pls answer fast..
Answers
I've included my code in the picture below. Best of luck


An apple cake recipe calls for 454 grams of apples and 50 grams of raisins. How many kilograms of fruit are needed to make 12 cakes?
Answers
Answer:
9.08
Explanation:
Because 454 divided by 50 is 9.08
_____________is a computing environment in which a service provider organization owns and manages the hardware, software, networking, and storage devices, with cloud user organizations (called tenants) accessing slices of shared resources via the Internet. Group of answer choices Cloud computing consumerization of IT Software Service Internet of Things
Answers
Answer:
Cloud Computing
Explanation:
Cloud computing is a term that refers to a platform and a sort of service. Servers are constantly provisioned, configured, reconfigured, and deprovisioned as needed by a cloud computing system. Physical or virtual computers can be used as cloud servers. Other computer resources, such as storage area networks (SANs), network equipment, firewalls, and other security equipment, are generally included in advanced clouds. Cloud computing also refers to apps that have been enhanced so that they may be accessed through the Internet. Large data centers and powerful servers are used to host Web applications and Web services in these cloud applications. A cloud application can be accessed by anybody with a good Internet connection and a basic browser.
Which of the following is NOT correct?
A. Computer is capable of processing only
digital signals.
B. Appropriate software is required for
processing the data.
C. Computer is capable of processing digital
as well as analog signals.
D. Computer is capable of analyzing both
quantitative and qualitative data.
Answers
Answer:A
Explanation:
Which of the following is NOT what Web Developers do?
A)Test applications for a website
B)Integrate graphics, audio, and video into the website
C)Work with other designers to pick color combinations
D)Determine the website's layout
E)Write code for the website
Answers
Answer:C Work with other designers to pick color combinations
Explanation:Got it right on 2.02 web design quiz
Web developers assists with the building, managing and maintainance of websites. Therefore, the options which doesn't mark the function of web developers is Work with other designers to pick color combinations.
Web developers are employed to peruse the effectiveness of website applications, website design, layout, arrangement, organization and development.
However, it is not the function of website developers to choose color combinations while working with other designers.
Learn more : https://brainly.com/question/15439630
Computer simulation of the Ising chain Use Program Ising1D to simulate the one-dimensional Ising model. It is convenient to measure the temperature in units such that J/k=1. For example, a temperature of T=2 means that T=2J/k. The "time" is measured in terms of Monte Carlo steps per spin (mcs), where in one Monte Carlo step per spin, N spins are chosen at random for trial changes. (On the average each spin will be chosen equally, but during any finite interval, some spins might be chosen more than others.) Choose H=0. The thermodynamic quantities of interest for the Ising model include the mean energy E, the heat capacity C, and the isothermal susceptibility χ. (a) Determine the heat capacity C and susceptibility χ for different temperatures, and discuss the qualitative temperature dependence of χ and C. Choose N≥200. (b) Why is the mean value of the magnetization of little interest for the onedimensional Ising model? Why does the simulation usually give M
=0 ? (c) Estimate the mean size of the domains at T=1.0 and T=0.5. By how much does the mean size of the domains increase when T is decreased? Compare your estimates with the correlation length given by (5.56). What is the qualitative temperature dependence of the mean domain size? (d) Why does the Metropolis algorithm become inefficient at low temperatures?
Answers
The Metropolis algorithm relies on accepting or rejecting spin flips based on energy differences, and at low temperatures, the energy differences between states become smaller, leading to slower convergence and longer simulation times.
(a) To determine the heat capacity C and susceptibility χ for different temperatures in the Ising model, you can use the Ising1D program to simulate the system. By running the simulation at different temperatures and measuring the corresponding values of energy and magnetization, you can calculate the heat capacity and susceptibility.
The heat capacity (C) represents the system's response to changes in temperature. At low temperatures, the heat capacity is typically low because the system is more ordered, and there is less energy available for fluctuations. As the temperature increases, the heat capacity also increases, indicating that the system becomes more responsive to temperature changes.
The susceptibility (χ) measures the system's response to an applied magnetic field. Similar to the heat capacity, the susceptibility is usually low at low temperatures due to the system's ordered state. As the temperature increases, the susceptibility also increases, indicating that the system becomes more susceptible to magnetic field influence.
The qualitative temperature dependence of χ and C in the Ising model typically shows a peak or maximum at the critical temperature (Tc) of the system. Below Tc, both χ and C increase as the temperature decreases, reaching a maximum at Tc. Above Tc, both χ and C decrease as the temperature increases.
(b) In the one-dimensional Ising model, the mean value of magnetization (M) is of little interest because there is no long-range order or spontaneous magnetization at any finite temperature in one dimension. Due to thermal fluctuations, the average magnetization usually fluctuates around zero, resulting in M≈0 in the simulation.
(c) To estimate the mean size of domains at temperatures T=1.0 and T=0.5, you can analyze the spatial patterns of spins in the simulation. The domains refer to regions where the spins have the same orientation. By measuring the sizes of these regions, you can estimate the mean domain size.
The mean size of domains generally increases as the temperature decreases. At higher temperatures, thermal fluctuations cause frequent spin flips, resulting in smaller domains. As the temperature decreases, the spins become more ordered, and larger domains form.
To compare your estimates with the correlation length given by (5.56), you can calculate the correlation length based on the spatial correlations between spins. The correlation length characterizes the range over which spin orientations are correlated. If your estimates align with the correlation length, it indicates consistency between the simulated system and the theoretical model.
The qualitative temperature dependence of the mean domain size is an increasing trend as the temperature decreases. Smaller domains are observed at higher temperatures, while larger domains are observed at lower temperatures.
(d) The Metropolis algorithm, which is commonly used in simulations of the Ising model, can become inefficient at low temperatures due to the slow exploration of the energy landscape. At low temperatures, the system is trapped in energy minima, making it difficult for the simulation to explore higher-energy states and reach equilibrium. The Metropolis algorithm relies on accepting or rejecting spin flips based on energy differences, and at low temperatures, the energy differences between states become smaller, leading to slower convergence and longer simulation times. Alternative algorithms, such as the Wolff algorithm or cluster algorithms, are often employed to improve efficiency at low temperatures by allowing for more efficient updates of spin configurations.
Learn more about temperatures :https://brainly.com/question/27944554
#SPJ11
How can you benefit from an internship, even if it is unpaid?
college class
i couldnt find it in article
Answers
The ways that a person can benefit from an internship, even if it is unpaid is that Unpaid internships can be a fantastic way to begin developing your professional network, gain skills, and get insightful input from industry experts. They may also be a reliable predictor of your future career satisfaction.
How do you anticipate using this internship to your advantage?Some of the gains from internship are:
Obtain useful professional experience.Consider a career route.Gain a competitive advantage in the job market.Develop and polish your skills.Obtain compensation in money.Build a network with industry experts.Gain self-assurance.Change over to employment.Note that unpaid intern do assist you in putting your knowledge and talents to use at work. You can better comprehend the everyday responsibilities of that role by participating in work experience as part of your study.
Hence it is seen as a wonderful approach to develop and show off abilities like dependability and communication is through unpaid work experience.
Learn more about internship from
https://brainly.com/question/25385643
#SPJ1
Explain how command driven and menu driven user interface is in (a) function
Answers
In terms of function, a command-driven user interface is more efficient for experienced users who are familiar with the system and the available commands, but it can be less accessible for new or inexperienced users.
What is the user interface about?A command-driven user interface and a menu-driven user interface are both used to interact with computer systems, but they differ in their approach to input and interaction.
A command-driven user interface operates using text-based commands entered by the user in a terminal or command prompt. In this type of interface, the user is expected to have a certain level of knowledge about the system and the available commands.
Therefore, one can say that a menu-driven user interface, on the other hand, provides a graphical interface with a series of menus and options to choose from. The user selects options from the menus to interact with the system and initiate actions.
Learn more about user interface at:
https://brainly.com/question/17372400
#SPJ1
What is the definition of a Robot????
Answers
Answer:
Please look below for your answer
Explanation:
A robot simply refers to a machine—especially one programmable by a computer— capable of carrying out a complex series of actions automatically. Robots can be guided by an external control device or the control may be embedded within. Robots may be constructed on the lines of human form, but most robots are machines designed to perform a task with no regard to their aesthetics.
hope I really helped you
Please mark me as brainliest
Submit your 300-word article review on a recent cyber bullying occurrence that lists five key points and offers your suggestions for two things the article should have covered.
Do this for 65 points
please need done by end of dAY
Answers
Article Review: Understanding and Addressing Cyberbullying
Introduction:
The article discusses the prevalence and impact of cyberbullying in today's digital age, highlighting the need for awareness and effective strategies to combat this harmful behavior.
Key Points:
Definition and Forms of Cyberbullying:
The article provides a clear definition of cyberbullying, exploring its various forms such as online harassment, spreading rumors, and social exclusion. It emphasizes the importance of recognizing these behaviors to effectively address the issue.
Impact on Victims:
The article delves into the detrimental effects of cyberbullying on victims' mental and emotional well-being. It discusses the increased risk of anxiety, depression, and social isolation, emphasizing the need for support systems and intervention strategies.
Role of Technology and Social Media:
The article highlights the role of technology and social media platforms in facilitating cyberbullying. It addresses the challenges of monitoring and controlling online behavior, urging individuals, parents, educators, and policymakers to take collective responsibility.
Prevention and Intervention Strategies:
The article offers insights into preventive measures and intervention strategies. It discusses the importance of educating individuals about responsible online behavior, fostering empathy and digital citizenship, and implementing reporting mechanisms and support networks.
Collaborative Efforts:
The article emphasizes the significance of collaborative efforts among schools, families, communities, and online platforms. It promotes the need for policies, guidelines, and awareness campaigns to create a safe and inclusive digital environment.
Suggestions for Additional Coverage:
Legal Framework and Consequences:
The article could include information about legal frameworks and consequences for cyberbullying perpetrators. It could explore how laws differ across jurisdictions and highlight the importance of holding offenders accountable.
Empowering Bystanders:
Addressing the role of bystanders in cyberbullying incidents could be valuable. The article could discuss how empowering bystanders to intervene or report cyberbullying can create a supportive environment and discourage such behavior.
Conclusion:
In conclusion, the article provides a comprehensive overview of cyberbullying, its impact, and potential strategies for prevention and intervention. By addressing the suggested points, the article could enhance its coverage and provide a more comprehensive understanding of the complex issue of cyberbullying.
Answer:
The article discussed an occurrence of cyberbullying that happened in the recent past. It detailed the incident, the people involved, and the impact that it had. It also discussed the social implications of cyberbullying and the strategies and initiatives that various countries are taking to combat it. Evaluation: The article was well-structured and provided an in-depth analysis of the cyberbullying incident. It included relevant statistics and other evidence to support the information mentioned. The author’s opinion was balanced and informed. Key Points: The article highlighted the consequences of cyberbullying, the ways in which it is increasing in prevalence, the different approaches that are being taken to prevent it, and the measures that can be taken to mitigate its effects. Analysis: The article provided an evidence-based argument that cyberbullying is a serious issue that has serious mental health implications for victims. It also argued that more public awareness of how cyberbullying can occur and how to prevent it is needed. Suggestions: The article could have provided more in-depth information on the strategies used to combat cyberbullying in different countries, as well as how government initiatives have worked in practice. It could have also offered more concrete advice to readers on how to prevent cyberbullying and support victims.
Explanation:
1) Summarize the article: 2) Evaluate the content: 3) Discuss key points of the article: 4) Analyze the main arguments or points: 5) Offer suggestions for what the article should have covered
The power of if worksheet
Answers
Which one of these is an example of unnecessary debt?
A. You buy a perfectly good used car instead of an expensive new car
B. You buy your groceries on Friday instead of coupon Monday.
C. You charge clothes you don't really need on a high-interest store card.
D. You save up all year to take a great surfing vacation.
Answers
hope this helps :)
An example of unnecessary debt is when you change your clothes and don't really need on a high-interest score. Thus option C is correct.
What is unnecessary debt?An unnecessary debt can be caused by a variety of issues such as expensive life events, having children, or moving to a new house. It may also be due to poor money management. The debt is due to those things that are not needed and hence are unnecessary.
Find out more information about unnecessary debt.
brainly.com/question/3566270
When reading electronic texts, it is important to _____.
a) set a purpose for research before reading
b) evaluate the reliability of the source
c) only read texts that support your own point of view
d) look for texts that have strong opinions on a subject
Answers
Answer:
b) evaluate the reliability of the source
one common way to deal with spam that makes it to your computer is to use a(n) ____.
Answers
One common way to deal with spam that makes it to your computer is to use a spam filter.
What is a Spam filter?A spam filter is a program that automatically identifies and separates unwanted or unsolicited emails from legitimate ones. It uses a set of rules and algorithms to detect common characteristics of spam, such as suspicious sender addresses, misleading subject lines, and high frequency of emails.
Once detected, the spam filter can move unwanted emails to a separate folder, delete them immediately, or mark them as spam for manual review. Spam filters can be configured to suit individual preferences and can significantly reduce the time and effort needed to manage email inboxes.
Read more about internet spams here:
https://brainly.com/question/29827400
#SPJ1
the ____ trendline is used to smooth out the data, making it easier to spot trends.
Answers
True, the trendline is used to smooth out the data, making it easier to spot trends.
The trendline is a line that is added to a chart to show the general direction in which the data is moving. It is often used to identify patterns or trends in the data that might not be immediately apparent. The trendline can be linear or nonlinear and is based on a mathematical algorithm that fits the line to the data. By smoothing out the data, the trendline makes it easier to see the overall trend and to make predictions about future values. However, it is important to note that trendlines are only as accurate as the data they are based on, and they should not be used as the sole basis for making important decisions.
learn more about data here:
https://brainly.com/question/27211396
#SPJ11
As the security administrator for your organization, you must be aware of all types of attacks that can occur and plan for them. Which type of attack uses more than one computer to attack the victim?
Answers
Answer:
The answer is "DDoS "
Explanation:
The distributed denial of service attack (DDoS) occurs whenever a directed program's wireless data or assets, generally one or even more application servers, were also swamped by various machines. This attack is always the consequence of many affected systems, that fill up the target network with traffic.
This attack is aimed to avoid legal customers of one's website from accessing it. In being effective in a DDoS attack, further demands need to be sent to the hacker than even the victim's server could deal with. One other way to successfully attack is to send fake requests from the attacker.