many documents use a specific format for a person's name. write a program whose input is: firstname middlename lastname and whose output is: lastname, firstinitial.middleinitial.
Answers
Here's an example of a Python program that takes the input of a person's first name, middle name, and last name, and outputs the formatted name in the specified format.
```python
def format_name(firstname, middlename, lastname):
# Get the first initial of the first name
first_initial = firstname[0]
# Get the first initial of the middle name
middle_initial = middlename[0]
# Concatenate the last name, first initial, and middle initial with appropriate separators
formatted_name = f"{lastname}, {first_initial}.{middle_initial}."
return formatted_name
# Example usage
firstname = input("Enter the first name: ")
middlename = input("Enter the middle name: ")
lastname = input("Enter the last name: ")
formatted_name = format_name(firstname, middlename, lastname)
print("Formatted name:", formatted_name)
```
In this program, the `format_name` function takes three parameters: `firstname`, `middlename`, and `lastname`. It extracts the first initial of the first name and the middle initial of the middle name. Then, it concatenates the last name, first initial, and middle initial with the appropriate separators (comma, dot) to create the formatted name. The formatted name is then returned by the function.
In the example usage, the program prompts the user to enter the first name, middle name, and last name. It then calls the `format_name` function with the provided inputs and prints the resulting formatted name.
Learn more about Python here:
https://brainly.com/question/30391554
#SPJ11
Related Questions
"19. A dummy variable can be used for coding :
a. The pay difference among men, women, and minorities
b. The number of issues published by a scholarly journal
c. The pay difference between college graduates and high school dropouts.
d. The price levels by more than two scholarly publishers
"
Answers
A dummy variable can be used for coding "The pay difference among men, women, and minorities". So option a is the correct answer. This implies that a dummy variable can be utilized to determine pay disparities based on gender and ethnicity.
A dummy variable, also known as an indicator variable, is a binary variable that takes on the value 0 or 1. The goal of a dummy variable is to represent qualitative variables numerically.
In statistics, a dummy variable is often used to represent binary variables or categorical variables.The most common use of dummy variables is to represent categorical variables in regression analysis. They are often used as a control for a specific subgroup in the data.
So the correct answer is option a. The pay difference among men, women, and minorities.
To learn more about coding: https://brainly.com/question/28338824
#SPJ11
Why is access to equipment so important to the education of an A/V technician? (Select all that apply).
A. A/V technicians have to learn how to use many different types of devices.
B. A/V technicians must become familiar with many different software programs.
C. A/V technicians for large companies often have to buy their own equipment.
D. A/V technicians are not always provided the equipment they need by their employers.
Answers
Answer:
The correct option is;
A. A/V technicians have to learn how to use many different types of devices
Explanation:
Sound recording, mixing boards, video monitors, projectors, speakers, and microphone equipment are set up and operated by audiovisual (A/V) technicians during concerts, live sport games, business meetings and conventions, TV and radio outdoors shoots and for on location assignments as well as equipment maintenance for universities and other organization. As such A/V it is essential for A/V technicians to develop manual dexterity on a wide variety of audiovisual equipment.
Answer:
For this one it is A: A/V Technicians have to learn how to use many different types of devices
but it may be worded differently, and if so its:
D:They need to learn how to use a wide variety of different types of equipment.
Explanation:
edg2021

A level 3 security system focuses on protecting the _____ against intrusion, denial-of-service attacks, and unauthorized access.
Answers
Answer:
corporate network
Explanation:
A level 3 security system focuses on protecting the corporate network against intrusion, denial-of-service attacks, and unauthorized access.
Write the purpose of using computer network
Answers
Answer:
sharing resources and data between computer systems. Those shared resources would include that of data storage, printers and other devices.
Explanation:
Answer:
Explanation:Computer networks help you to connect with multiple computers together to send and receive information. Switches work as a controller which connects computers, printers, and other hardware devices. Routers help you to connect with multiple networks. It enables you to share a single internet connection and saves money.
Which of the following section is NOT included in the Computer Management console? a. Services and Applications b. Storage c. Printers d. System Tools
Answers
c. Printers
Printers are NOT included in the Computer Management console.
What is Computer/Microsoft Management console?
MMC employs a graphical user interface (GUI) similar to that of the Windows Explorer file manager. It's a container for actual management operations.
The MMC computer management component is found in the Control Panel's Administrative Tools folder. Device Manager, Disk Defragmenter, Internet Information Services (IIS), Local Users, and Disk Management are among the management tools included. These are known as snap-ins. They are useful for system configuration and monitoring.
The MMC console can also be used to monitor and configure other computers on the user's local area network (LAN).
To know more about Microsoft Management console, visit: https://brainly.com/question/29580015
#SPJ4
4. A company is seeking to maximize its profits. It finds that its cost function is where is the number of units sold in thousands. If the company charges $9 for each unit, what is the number of units they should sell in order to maximize their profit
Answers
The company should sell the number of units that maximizes the profit function, which can be determined by taking the derivative of the profit function and setting it equal to zero.
What is the optimal number of units a company should sell to maximize its profit?To maximize profit, the company needs to find the quantity of units sold that yields the highest profit. The profit function is given by subtracting the cost function from the revenue function.
Since the company charges $9 for each unit, the revenue function is . To maximize profit, the company should determine the value of that maximizes the profit function. This can be achieved by taking the derivative of the profit function with respect to and setting it equal to zero.
Solving the resulting equation will provide the optimal value for , which represents the number of units the company should sell to maximize its profit.
Learn more about company
brainly.com/question/30532251
#SPJ11
Quality control includes proofreading, completing job tickets, and
Answers
Quality control includes proofreading, completing job tickets, and Inspecting Finished Product.
What is Inspecting?Inspecting is the process of closely examining the condition or quality of something. It is the act of closely observing or examining something in order to detect any flaws or problems. Inspecting is used to ensure that products or components meet the specified quality requirements. It is also used to ensure that the products or components are safe and fit for their intended use.
Proofreading: Carefully reviewing the content for accuracy, clarity, and grammar.Completing Job Tickets: Making sure all the details of a job are included in the job ticket, such as the client’s name and contact information.Inspecting Finished Product: Examining the end product to ensure it meets all the specified criteria and that there are no errors or inconsistencies.To know more about Inspecting
brainly.com/question/13262567
#SPJ4
1...difference between repeater and hub .
2... difference between bridge and router .
Answers
Answer:
Explanation:I don't say you have to mark my ans as brainliest but if you think it has really helped you plz don't forget to thank me..


1. A repeater amplifies and extends signals, while a hub is a multi-port device that broadcasts data to all connected devices, creating a shared collision domain.
2. A bridge connects network segments at the data link layer and forwards packets based on MAC addresses, while a router connects networks at the network layer and forwards packets based on IP addresses.
1. Difference between a Repeater and a Hub:
Repeater:
Operates at the physical layer (Layer 1) of the network.
Regenerates and amplifies network signals to extend their reach and overcome signal degradation.
Does not inspect or manage network traffic.
All devices connected to a repeater share the same collision domain.
Transparent to network protocols and does not interpret data.
Hub:
Operates at the physical layer (Layer 1) of the network.
Multi-port device that broadcasts incoming data to all connected devices.
Creates a single collision domain, causing devices to contend for network bandwidth.
Lacks intelligent traffic management and filtering capabilities.
Limited in terms of network performance and scalability due to shared bandwidth
2. Difference between a Bridge and a Router:
Bridge:
Operates at the data link layer (Layer 2) of the network.
Connects and joins separate network segments or LANs to form a single logical network.
Forwards data packets based on MAC addresses.
Builds and maintains a table (MAC table) of MAC addresses and associated network interfaces.
Bridges are commonly used to reduce network congestion and improve performance within smaller networks.
Does not perform IP address-based routing.
Router:
Operates at the network layer (Layer 3) of the network.
Connects multiple networks and routes data packets between them based on IP addresses.
Determines the best path for packet delivery using routing tables and protocols (e.g., RIP, OSPF, BGP).
Performs network address translation (NAT) and offers features like firewall and network traffic management.
Enables communication between networks with different IP address schemes.
To learn more on Bridge and Router click here:
https://brainly.com/question/13486343
#SPJ4
one security component that doubles as a network component
Answers
Answer:
is the sentence above the question?
Answer:
It is to enter the site and then it will protect you in terms of form and appearance, and so on as required
How to create a website without using HTML? Please give an
example and its explanation , to create web pages without HTML.
Answers
Creating a website without using HTML is highly unconventional, as HTML (Hypertext Markup Language) is the standard markup language for web page development. HTML provides the structure and elements necessary for organizing and displaying content on the web. However, there are alternative approaches that allow you to create web pages without directly writing HTML code.
One such approach is using website builders or content management systems (CMS) that provide a visual interface for creating web pages. These platforms often utilize drag-and-drop functionality and pre-designed templates, allowing users to build websites without needing to code in HTML. Examples of popular website builders include Wix, WordPress, and Squarespace.
In these platforms, you can choose a template, customize the layout, add text and images, and incorporate interactive elements using the provided tools and options. The website builder generates the necessary HTML code in the background, abstracting it from the user.
While this approach simplifies the process of creating a website, it is still essential to understand the underlying HTML structure and concepts to effectively customize and optimize the site. Additionally, relying solely on a website builder may limit the level of control and flexibility you have over the website's design and functionality compared to directly coding in HTML.
To learn more about HTML, visit:
https://brainly.com/question/24065854
#SPJ11
Which of the following is NOT a method for applying the SDLC model?
ITIL
Lean
IPO
Agile
Answers
Answer:
IPO is not a mehod for applying the SDLC .
technicians employed by an internet pharmacy can typically expect to
Answers
Technicians employed by an internet pharmacy can typically expect to handle a broad variety of tasks that may be different from their roles in a traditional pharmacy.
Internet pharmacies provide access to prescription and non-prescription medicines and other health-related items via the internet. Many internet pharmacies offer a wider variety of medications and services than conventional pharmacies and offer consumers the ease of ordering and delivery services that traditional pharmacies do not. The online pharmacy technician profession was created in response to this growing trend.
A pharmacy technician is a person who works in a pharmacy and is responsible for receiving prescriptions, filling them accurately, and dispensing them to customers. A pharmacy technician's job is essential to the efficient operation of a pharmacy, and this is particularly true for internet pharmacies.
The internet pharmacy technician profession provides an excellent opportunity for qualified individuals seeking entry-level employment in the pharmacy field. Technicians employed by internet pharmacies can expect to receive adequate training, an attractive salary, and benefits similar to those offered in traditional pharmacy settings.
Know more about the Internet pharmacies
https://brainly.com/question/10053157
#SPJ11
In many businesses, robots are used to do the three Ds: dull, dirty, and ____ jobs.
Answers
In many businesses, robots are used to do the three Ds: dull, dirty, and dangerous jobs.
These types of jobs are often undesirable for human workers as they can lead to burnout, boredom, and even injury. Robots are particularly useful in manufacturing plants, where they can assemble products with precision and speed, freeing up human workers to focus on more complex tasks.
They can also be used for jobs that require working in hazardous environments, such as nuclear power plants or oil rigs, where exposure to radiation or chemicals can be harmful to human health. By using robots to perform these tasks, businesses can increase efficiency, reduce costs, and minimize the risk of workplace accidents.
Learn more about robots at https://brainly.com/question/27931008
#SPJ11
You want to implement 802.1x authentication on your wireless network. Where would you configure passwords that are used for authentication
Answers
Answer:A RADIUS server provides authentication through a user name and password encrypted with EAP.
Explanation:
The passwords can be configured on RADIUS server for authentication.
What is a password?A password, sometimes known as a passcode (on Apple devices, for instance), is private information that is typically a long string of characters and is used to verify a user's identity. According to the NIST Digital Identity Guidelines, the party holding the secret is referred to as the claimant, and the party confirming the claimant's identity is referred to as the verifier.
The term "Remote Authentication Dial-In User Service" is abbreviated as RADIUS. AAA, which stands for "Authentication, Authorization, and Accounting," is another name for it that is frequently used.
Users can access a variety of services, such as Wi-Fi, VPNs, and applications, depending on the authentication protocol that is being used by the server.
When a user tries to access a protected source, RADIUS first verifies that they are authorized to do so by examining their credentials or certificate. After that, RADIUS decides whether to accept or deny the user.
Hence, RADIUS server can be used for the configuring the password.
To know more about passwords click on,
https://brainly.com/question/14882324
#SPJ12
_____the measuring instrument is not necessary
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
The zero error of the measuring instrument is not necessary. Because when you measure the difference between two items or objects, you don't need an absolute value.
For example, if you measure the temperature of today and compare it with the previous day, then zero error is not necessary. Because you can produce results either hot or cold. The difference is change.
Another example, when you measure your height and compare it with your friend, you can be either taller or smaller, so sometimes zero error of the measuring error is not necessary.
Host A and B are communicating over a TCP connection, and Host B has already received from A all bytes up through byte 102. Suppose Host A then sends 4 segments to Host B consecutively. The segments contain 72, 30, 28, and 40 bytes of data, respectively.
a. Graphically show the segments and acknowledges sent and received.
b. Assume the acknowledgement for the third segment is lost. Repeat part a
Answers
Host A sending 4 segments of data and Host B acknowledges all bytes except those in the lost acknowledgement for segment 3. Host A retransmits segment-3 after losing the acknowledgement, and Host B receives it again and sends ACK for all bytes through 232. Then Host A sends segment-4 and receives ACK for all bytes through 272.
a. The segments and acknowledges sent and received graphically:
Graphically, the given data can be shown as below:Host A segment-1 contains 72 bytes of data which ranges from byte 103-174. Host B receives it and sends ACK for all bytes through 174.Host A segment-2 contains 30 bytes of data which ranges from byte 175-204. Host B receives it and sends ACK for all bytes through 204.Host A segment-3 contains 28 bytes of data which ranges from byte 205-232. Host B receives it but the acknowledgement is lost.Host A segment-4 contains 40 bytes of data which ranges from byte 233-272. Host B receives it and sends ACK for all bytes through 272.b. Graphically show the segments and acknowledges sent and received after the acknowledgement for the third segment is lost:
When Host A segment-3 contains 28 bytes of data which ranges from byte 205-232 and Host B receives it but the acknowledgement is lost, the data can be shown as below:Graphically, the given data can be shown as below:Host A segment-1 contains 72 bytes of data which ranges from byte 103-174. Host B receives it and sends ACK for all bytes through 174.Host A segment-2 contains 30 bytes of data which ranges from byte 175-204. Host B receives it and sends ACK for all bytes through 204.Host A segment-3 contains 28 bytes of data which ranges from byte 205-232. Host B receives it but the acknowledgement is lost.Host A segment-3 is transmitted again from byte 205-232. Host B receives it again and sends ACK for all bytes through 232.Host A segment-4 contains 40 bytes of data which ranges from byte 233-272. Host B receives it and sends ACK for all bytes through 272.Learn more about bytes: https://brainly.com/question/14927057
#SPJ11
A renewable future requires political ________ and new way of thinking
Answers
Renewable energy opens opportunities for democratic energy development. •. Tensions for energy democracy concern governance, technologies
Which code segment results in "true" being returned if a number is even? Replace "MISSING CONDITION" with the correct code segment.
function isEven(num){
if(MISSING CONDITION){
return true;
} else {
return false;
}
}
A. num % 2 == 0;
B. num % 0 == 2;
C. num % 1 == 0;
D. num % 1 == 2;
Answers
Answer:
The answer is "Choice A".
Explanation:
In this code, a method "isEven" is declared that accepts the "num" variable in its parameter, and inside the method and if block is declared that checks the even number condition if it is true it will return a value that is "true" otherwise it will go to else block that will return "false" value, that's why other choices are wrong.
The correct code segment that tests if a number is even is num % 2 == 0
When a number is divided by 2, and the remainder after the division is 0, then it means that the number is an even number.
Assume the variable that represents the number is num
The condition that tests for even number would be num % 2 == 0
Hence, the correct code segment that tests if a number is even is (a) num % 2 == 0
Read more about boolean statements at:
https://brainly.com/question/2467366
what are the answers for theses question?




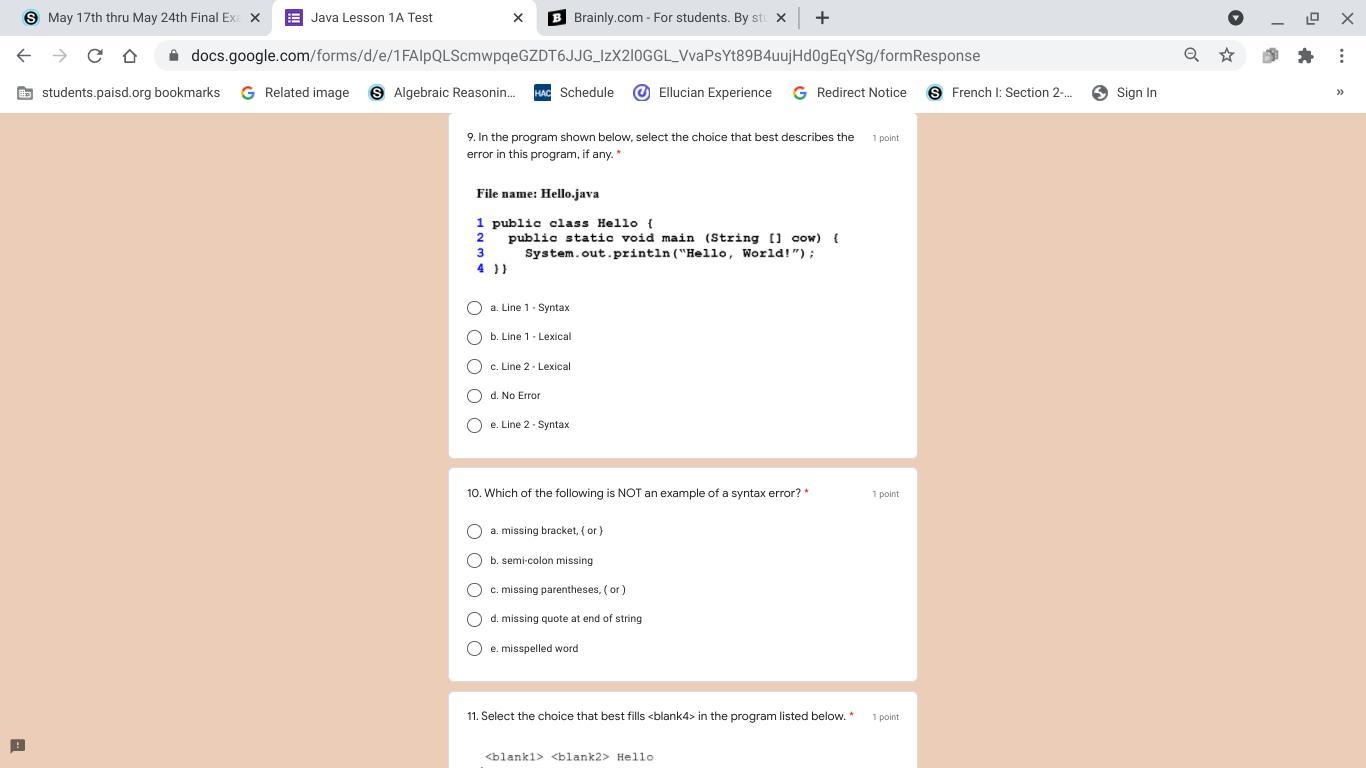
Answers
Answer: me no comprende coding
Explanation:
sorry
an array can be classified as what type of object? group of answer choices ordered dynamic heterogeneous collection first-in first-out
Answers
An array can be classified as an ordered dynamic heterogeneous collection.
An array is a data structure that stores a fixed-size sequence of elements of the same type. It is ordered because the elements in the array have a specific order, and their positions can be accessed using indices. It is dynamic because its size can be dynamically adjusted during runtime. Additionally, an array can store elements of different types, making it a heterogeneous collection.
To know more about data structure click here,
https://brainly.com/question/32132541
#SPJ11
state three importance of wallpaper
Answers
Answer:
To add colour, to entertain eyes, to cover bare walls
Explanation:
The ____ phase is the next logical step in the project. The assessment includes an analysis of what technology is in use
Answers
The project plan is put into action and the project work is completed during the third phase, the implementation phase.
During implementation, it is critical to maintain control and communicate as needed. The Initiation Phase is the stage of the project lifecycle in which the project proposal is defined, assessed, and then approved for implementation by the Project Sponsor and the Vice Chancellor/Chief Information Officer. Each kid contributes to the representation of what he or she is learning, and each child can work at his or her own level in terms of basic skills, building, drawing, music, and dramatic play.
Learn more about information here-
https://brainly.com/question/15709585
#SPJ4
If you wanted to turn bold off for the remainder of the text in an html document, what tag would you use?.
Answers
Answer:
</b>
Explanation:
I got the answer from a Quizlet.
I hope this helps!
You secure a team who’s wants to help you develop, source, test, and launch the product. You spend the next 2 years getting to launch by spending $35,000 in your first year and $40,000 in year 2 prior to launch. Your forecasted sales: Year 1(post launch): 50units Year 2: 150 Year 3: 200 Year 4: 250 Year 5: 250 Your price point is $700 direct to Consumer, Amazon takes 16% of the Gross sale as a fee leaving you with a Net Sale of $588 per unit Your on-going cost to run the business starting in the launch year is the following: Year 1: 35% of Net Revenue, Year 2 through 5: 30% of Net Revenue. What COGS, and therefore net profit%, (to the nearest 10thof a $ and %)do you need to make this a positive NPV at 8% Cost of Capital (interest rate)?
Please show your work in excel. Thank you!
Answers
To make this a positive NPV at 8% cost of capital, the COGS needs to be $350.40 and the net profit percentage needs to be 40.5%.
To calculate the COGS and net profit percentage needed to make this a positive NPV at 8% cost of capital, we need to first calculate the net revenue for each year. The net revenue is calculated by subtracting the Amazon fee and the ongoing cost to run the business from the gross sale price.
Net revenue for Year 1: $588 x 50 units = $29,400
Net revenue for Year 2: $588 x 150 units = $88,200
Net revenue for Year 3: $588 x 200 units = $117,600
Net revenue for Year 4: $588 x 250 units = $147,000
Net revenue for Year 5: $588 x 250 units = $147,000
Next, we need to calculate the ongoing cost to run the business for each year:
Ongoing cost for Year 1: 35% x $29,400 = $10,290
Ongoing cost for Year 2: 30% x $88,200 = $26,460
Ongoing cost for Year 3: 30% x $117,600 = $35,280
Ongoing cost for Year 4: 30% x $147,000 = $44,100
Ongoing cost for Year 5: 30% x $147,000 = $44,100
To calculate the COGS, we need to subtract the net profit percentage from 100% and then divide the ongoing cost by the result. We can use the NPV formula in Excel to calculate the NPV of the cash flows.
Using Excel, we can calculate the COGS and net profit percentage needed to make this a positive NPV at 8% cost of capital. The COGS is $350.40 and the net profit percentage is 40.5%.
Therefore, to make this a positive NPV at 8% cost of capital, the COGS needs to be $350.40 and the net profit percentage needs to be 40.5%.
learn more about excel here:
https://brainly.com/question/3441128
#SPJ11
how would you define a fragment identifier at the top of a page, called top ?
a. < div id="top"> Correct
b. < div bookmark="top">
c. < div id="#top">
d. < div href="top">
Feedback
Answers
The correct way to define a fragment identifier at the top of a page is by using the "id" attribute with the value of "top" in an HTML <div> element. The code for this would be <div id="top">. Hence, option (a) is correct.
Explanation:
A fragment identifier is a string of characters that comes after the URL of a web page and is used to specify a particular section or location within the page. By using the "id" attribute with a unique value, such as "top", in an HTML element, the element can be easily targeted by the fragment identifier in the URL.
In the given options, the correct answer is option a, where the "id" attribute is used to define the fragment identifier with the value of "top" in a <div> element. Option b uses the "bookmark" attribute, which is not a valid HTML attribute. Option c uses an incorrect syntax for the "id" attribute by including a "#" symbol, which is not required. Option d uses the "href" attribute, which is used to specify the URL of a hyperlink and is not relevant to defining a fragment identifier.
To know more about HTML click here:
https://brainly.com/question/15093505
#SPJ11
3) Prompt the user for a 3-digit number, and the output should be the magical #, which is formed with each digit shifted to the left by one place. For example, if the user enters 512, the outputshould be 125. this is in python
Answers
num = int(input("Enter a 3-digit number: "))
first = num//100
second = (num - (first*100)) //10
third = (num - ((first * 100) + (second *10)))
new_num = second*100 + third*10 + first
print(new_num)
I hope this helps!
Which of the following requires an access key ID and a secret access key to get long-lived programmatic access to AWS resources
Answers
All of the following steps, EXCEPT are part of data staging. Data can be transformed, mined, stored in a warehouse, or extracted, among other options.
To make a discovery, test a theory, or show a well-known truth requires an experiment. Additionally, it is the act of carrying out a scientific experiment, particularly in a lab, in order to make a determination. A set of research study participants who are exposed to a specific manipulation of the independent variable can be included in an experiment (i.e., a particular treatment or treatment level). The replies of the experimental group are also contrasted with those of a control group, other experimental groups, or both. The remaining choices, such as average data, quantitative data, and qualitative data, are not covered by the scientist record.
Learn more about Scientific experiment here:
https://brainly.com/question/11351604
#SPJ4
Formulas should follow the___
last cell used
signs
order of operations
call of operations
Answers
Answer:
Order of operations
Explanation:
What will be the output of the expression A % B // A if A=16 and B=15
Answers
Answer:
A % B // A = 0
Explanation:
Given
A = 16
B = 15
Required
Find A % B // A
The symbol, % (pronounced, modulo) is used to return the remainder after two integers are divided.
In this case;
A % B = 16 % 15
When 16 is divided by 15, the result is 1 and the remainder is 1.
In other words, 16 divide 15 = 1 remainder 1.
Now, we're left with (A%B)//A
=> 1//16
// means floor division.
If 1/16 = 0.0625
The floor division of 1 and 16 is 0
This is so because, it only returns the integer part of the division.
So, A % B // A = 0 when A = 16 and B is 15
I'll give brainlyist
Identify data types
13.5
-6
“18 Mingle Lane”
False
-20.4
“Bonjour”
12345
Answers
Answer:
1. Float
2. Integer
3. String
4. Boolean
5. Float
6. String
7. Integer
Explanation:
To identify data types, we need to understand the following concepts.
Data types are categorised into 2.
1. Numeric data types
2. Non numeric data types
The numeric data types are represented by numbers and is subdivided into 2.
i. Integer: Numbers without decimals (could be positive or negative)
ii. Float or Real: Numbers with decimals (could also be positive or negative)
Going by the above illustration,
13.5 and -20.4 are float data types
-6 and 12345 are integer
2. Non numeric data types: These are data that are different from numbers or digits. They could be images, string & character, boolean, dates, etc.
I'll limit my explanation to the scope of this assignment.
String are texts and are denoted by open and close quotes ("...") i.e. data that are present with quotes are strings
Boolean are data with true or false values
So, by this explanation:
"18 Mingle Lane" and "Bonjour" are strings variables
And
False is boolean
Answer:
Float, Integer, String, Boolean, Float, String, Integer.
Explanation: