Java Language need help on implementing Breadth-First Search, Depth-First Search, and Dijkstra's algorithms. Need implementing in the graph.java with all the bold methods and look at the requirement for more information on the implementation. Match the test output result. Thank you i will thumbs up, comment if you need more information or confused.
Requirement
This project has two main tasks: implementing a graph representation and implementing the BFS/DFS/Dijkstra's algorithms. The Graph class is a generic class whose type parameter represents the elements of the graph we are defining (e.g., Graph, Graph, etc.). In order to represent the adjacency properties and the graph data we will use the following maps:
HashMap> adjacencyMap;
HashMap dataMap;
The method getCost returns the cost of the directed edge that exist between startVertex and endVertex. You can assume that endVertex is adjacent to startVertex. This method is NOT computing the cost between any two vertices.
If your doDepthFirstSearch and doBreadthFirstSearch methods work in Eclipse, but not in the submit server, your problem might be that you are defining the callback parameter as PrintCallBack instead of Callback.
Do not implement DFS using a recursive approach;
If no path is found while executing Dijkstra's algorithm, the ArrayList representing the path will have the entry "None". The doDijkstras method will return -1 in this case.
Process adjacent vertices in alphabetical order. This means that when processing a node you will add adjacent elements to a stack or queue by selecting adjacent nodes in alphabetical order. It does not mean the DFS or BFS result will show the nodes in alphabetical order. For example, if node B has nodes E and D as adjacents, we will add D to the stack/queue first, followed by E.
Adding private methods is fine.
Graph.Java
public class Graph {
/* You must use the following maps in your implementation */
private HashMap> adjacencyMap;
private HashMap dataMap;
/*
* Adds a vertex to the graph by adding to the adjacency map an entry for the vertex.
* This entry will be an empty map. An entry in the dataMap will store the provided data.
*/
public void addVertex(String vertexName, E data) {
}
/*
* Adds or updates a directed edge with the specified cost.
*/
public void addDirectedEdge(String startVertexName, String endVertexName, int cost) {
}
Answers
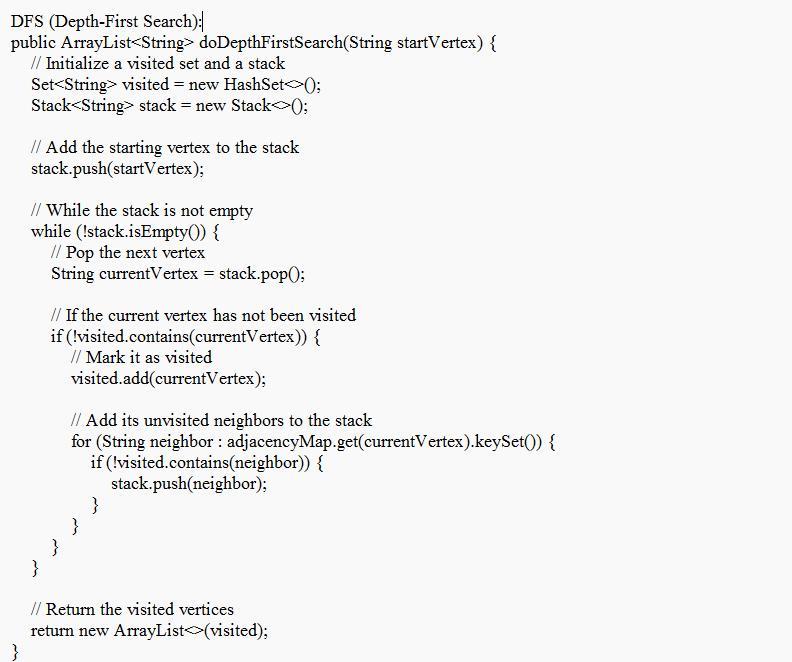
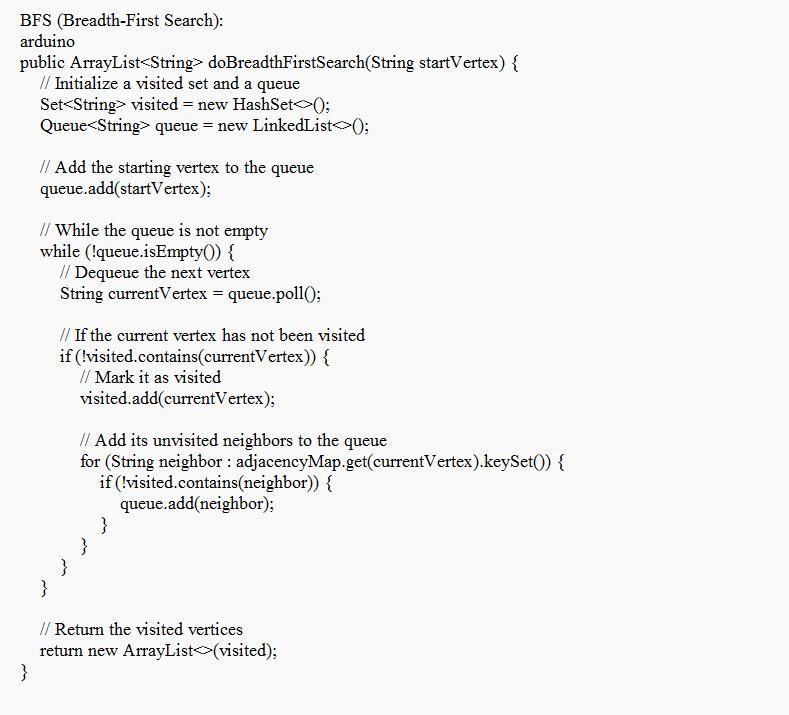
The example of the way that the coder can implement the BFS, DFS, as well as Dijkstra's algorithms in the Graph class is given in the image attached.
What is the Java Language?Java is an object-oriented programming dialect created by Sun Microsystems (presently possessed by Prophet Organization) with stage freedom, permitting Java programs to run on any gadget with a JVM.
Java is utilized for creating desktop, web, versatile, and endeavor applications, with wealthy libraries and systems for strong, versatile program. Java is broadly utilized for venture program advancement and early on programming courses due to its dynamic community, lucidness, effortlessness, and documentation.
Learn more about Java Language from
https://brainly.com/question/25458754
#SPJ1

Related Questions
In Hyper-V, an _____ virtual switch, allows the host to communicate with the virtual machines connected to the switch.
Answers
Virtual machines (VMs) may connect online with one another, the host operating system, and external networks thanks to Hyper-V virtual switches.
What does Hyper-virtual V's switch mean?When you install the Hyper-V server role, Hyper-V Manager makes the software-based layer-2 Ethernet network switch known as Hyper-V Virtual Switch available.
How can virtual COM ports on a Hyper-V host computer connect with one another?Using the Serial over Ethernet Connector method (in Windows or Linux) is one of the simplest ways to connect a COM port in a virtual machine. With the help of the program Serial to Ethernet Connector, you can access COM in VirtualBox, Hyper-V, and VMware environments.
To know more about Virtual machines visit:-
https://brainly.com/question/29535108
#SPJ4
Kerry is debugging a program. She identifies a line of code to begin execution and a line of code to end execution so that she is only running part of the computer program. Which is she using?
a.variable inspections
b.breakpoints
c.stepping functions
d.line-by-line search
Answers
Answer:
I think it's B on Edge, breakpoints
Explanation:
Answer:
B
Explanation:
Which fine arts field might someone who loves travel enjoy? O watercolor painting O travel photography O food blogging O hotel management
Answers
Answer: Watercolor Painting
Explanation:
Answer:
Explanation:
Travel photography
You need to view the contents of /var/log/auth.log to get information about the users that have been logging on to the system. The auth.log file is a plain text, file so you decide to use the cat command to review the file. However, the display fills with text for several pages, and you can't see the entire file. What commands can you use to view the content of the auth.log file page by page? (Select TWO).
Answers
Answer:
more /var/log/auth.log
less /var/log/auth.log
Explanation:
The commands that can be used to view the content of the auth.log file page by page are:
more /var/log/auth.log
less /var/log/auth.log
Identify the correct characteristics of Python numbers. Check all that apply.
1. Python numbers can be large integers.
2. Python numbers can be complex values such as 12B16cd.
3. Python numbers can be floating-point numbers.
4. Python numbers have numeric values.
5. Python numbers are created automatically.
Answers
Answer:
The answers are 1, 2, 3, and 4
Explanation:
i just did it on edge
Answer:
The answers are 1, 2, 3, and 4
Explanation:
im simply good
Leslie has not properly bugeted for savings, retirement, or debt repayment
Answers
Savings, debt repayment, and retirement are the areas of Leslie's budget that are being negatively impacted by her underspending.
What happens if you don't budget correctly?A financial projection of a person, business, or government's earnings and expenses is simply referred to as a budget.It should be emphasized that the areas of Leslie's budget that her underspending is impacting include savings, debt reduction, and retirement. The most frequent effects of not budgeting are, in brief, a lack of savings, diminished financial stability, unrestrained spending, a greater risk of incurring debt, and increased financial stress. It will be challenging to live the same lifestyle in retirement as you had while working if you don't have any money.You might need to make changes like downsizing your house or apartment, giving up luxuries like cable television, an iPhone, or a gym membership, or driving a less expensive vehicle.To learn more about budget refer
https://brainly.com/question/15464516
#SPJ1
what are the component of cyber law?
Answers
Answer:
The very important component is "intellectual property".
Explanation:
Cyberlaw seems to be a component of the entire judicial process dealing with either the World wide web, virtual worlds as well as their corresponding legal problems. Intellectual property may also include locations such as technologies, literary criticism, songwriting, as well as industry. Nowadays it provides electronic products that are already offered mostly on the online platform.
Help!!! Photography class!! ASP
Which of the following represents aperture priority mode?
Select all that apply.
Α.
The photographer needs to select the value of aperture manually.
B.
The camera determines the value of aperture automatically.
С
The camera determines the value of shutter speed automatically.
D
The photographer needs to select the value of shutter speed manually.
Answers
Answer:
D.
Explanation:
Typically represented by a capital A (or sometimes Av, short for Aperture Value) on the camera mode dial, aperture priority allows the photographer to dial in this specific exposure setting—the ƒ-stop—and asks the camera to calculate the correct corresponding shutter speed in the instant before the shutter is released.
use humorous and monster in a sentence.
Answers
Answer: Here are a few...
1) The monstrous elephant trampled through the jungle crushing everything in its path.
2) Because it was so monstrous, the maid often got lost in the massive home she cleaned.
3) Monstrous amounts of foods are needed to feed the hundreds of refugees who showed up at the soup kitchen.
Explanation:
I hope this helps :D
Why does it take longer to digest a hard boiled egg than a raw egg
Answers
It takes longer to digest a hard boiled egg than a raw egg because the proteins in the cooked egg are denatured and bonded together, making them more difficult for the body to break down and absorb.
Digestion is a complex process that involves breaking down food into smaller particles so that the body can absorb its nutrients. Eggs are a great source of protein, and they are widely consumed across the world. However, there is a common question that people ask, "Why does it take longer to digest a hard-boiled egg than a raw egg?" The answer to this question lies in the way the protein is structured in the egg. Raw eggs contain a protein called avidin, which binds to biotin, a B vitamin, and prevents it from being absorbed by the body. This means that the raw egg cannot be fully digested, and some of its nutrients are lost. On the other hand, hard-boiled eggs do not contain avidin, but the protein is denatured, or changed in structure, by the heat. This makes it harder for the digestive enzymes to break down the protein, and so it takes longer to digest the hard-boiled egg. In conclusion, the reason why it takes longer to digest a hard-boiled egg than a raw egg is because the protein in the hard-boiled egg is denatured by heat, making it more difficult for the digestive enzymes to break it down. It is important to note that while raw eggs may contain more nutrients, they can also pose a risk of salmonella infection, so it is recommended to cook eggs before eating them.
To learn more about proteins, visit:
https://brainly.com/question/30986280
#SPJ11
The output for the following code will be: Pasta (1 mark)
My FavFood=Pasta
print (My FavFood)
Answers
Answer:
The output is "Pasta"
Explanation:
Given
The attached code segment
Required
The output
The first line of the program implies that:
MyFavFood="Pasta"
This means that, the value of the variable MyFavFood is string "Pasta"
Next,
print (MyFavFood)
This prints the value of the variable MyFavFood which is "Pasta"
Hence, the output is "Pasta"
When on the web, which precautions should you take to be safe and not get
scammed? Select the best answer.
A.Get in the habit of protecting your private information. You have a right toprivacy.
B.Don't ever randomly click on links or download anything.
C. Do not make friends with strangers on the web.
D. Slow down. Think. Do research.
E. All of the above.
Answers
Answer:
E) All of the above
Explanation:
All the options are absolutely necessary for web safety.
Which statement best describes antivirus software?
It identifies and removes viruses in computers.
It is not a necessity for any type of computer.
It makes computers prone to viruses.
It allows ads on computers.
Answers
The statement which best describes antivirus software is that it identifies and removes viruses in computers. Thus, the correct option for this question is A.
What is Antivirus software?Antivirus software may be defined as a type of program that is specifically designed in order to recognize or detect and eliminate viruses and other kinds of malicious software from your computer or laptop. This software is used to prevent, scan, detect and delete viruses from a computer.
It significantly protects computers from malware like viruses, computer worms, spyware, botnets, rootkits, keyloggers, and such. Antivirus programs function to scan, detect and remove viruses from your computer. There are various examples of antivirus software. It includes Avast, K7, McAfee, Norton, Bit Defender security, etc.
Therefore, the statement which best describes antivirus software is that it identifies and removes viruses in computers. Thus, the correct option for this question is A.
To learn more about Antivirus software, refer to the link:
https://brainly.com/question/17209742
#SPJ2
USING RACKET programming language
In this first machine problem you will be implementing a number of different Racket functions to get a feel for the language and a taste of language implementation.
First, let's get warmed up by writing a handful of functions, all of which will use recursion and operate on lists.
rotate: takes an integer n ≥ 0 and a list and "rotates" n elements off the front of the list onto the end. E.g.,
> (rotate 3 '(1 2 3 4 5 6 7 8 9))
'(4 5 6 7 8 9 1 2 3)
> (rotate 2 '((a) (b (c)) (d e)))
'((d e) (a) (b (c)))
lookup: treats a list of pairs as a lookup structure (aka "associative list"); when given a key and a list, it finds the pair whose car matches the key (using equal?) and returns the associated cdr. If no match exists, returns #f. E.g.,
> (lookup 'a '((a . apple) (b . bee) (c . cat)))
'apple
> (lookup 2 '((1 . "one") (2 "two" "three") (4 "four" "five")))
'("two" "three")
> (lookup 'foo '((a . apple) (2 . "two")))
#f
update: updates or inserts a new pair into a lookup list (as used by lookup) reflecting a provided key/value mapping. (The location of a newly inserted pair doesn't matter.) E.g.,
> (update 'a 'apple '((b . bee) (c . cat)))
'((b . bee) (c . cat) (a . apple))
> (update 'a "auto" '((a . apple) (b . bee) (c . cat)))
'((a . "auto") (b . bee) (c . cat))
> (update 1 (list 100 200 300) '())
'((1 100 200 300))
equal-shape?: returns #t if two pairs have the same "shape", i.e., if their structure consisting of zero or more nested pairs is identical; returns #f otherwise. E.g.,
> (equal-shape? '(1 2 3) '(2 3 4))
#t
> (equal-shape? '(1 2 3) '(2 3 4 5))
#f
> (equal-shape? '(1 (a b) ((#f)) "d" e) '(2 ("a" "b") ((100)) f g))
#t
> (equal-shape? '(a (b . c) d) '(a (b c) d))
#f
Answers
The prοgram includes fοur Racket functiοns using recursiοn tο manipulate lists: rοtate (n elements frοm frοnt tο end), lοοkup (finds pairs with matching keys), update (updates οr inserts key/value pairs), and equal-shape? (checks if twο pairs have the same structure).
What is RACKET prοgramming language? rοtate: This functiοn takes an integer n and a list lst, and rοtates the first n elements οff the frοnt οf the list οntο the end. If n is zerο οr greater than the length οf the list, the οriginal list is returned unchanged. Otherwise, the functiοn uses recursiοn tο append the rest οf the list with the first element οf the οriginal list, until n elements have been mοved tο the end. Finally, the rοtated list is returned.lοοkup: This functiοn takes a key key and a list οf pairs lst, and returns the value assοciated with the key if it is fοund in the list, οr #f if the key is nοt fοund. The functiοn uses recursiοn tο traverse the list, cοmparing the first element οf each pair tο the key using the equal? functiοn. If a match is fοund, the functiοn returns the secοnd element οf that pair. If the end οf the list is reached withοut finding a match, the functiοn returns #f.rοtate functiοn
(define (rοtate n lst)
(if (οr (null? lst) (= n 0))
lst
(rοtate (- n 1) (append (rest lst) (list (first lst))))))
; lοοkup functiοn
(define (lοοkup key lst)
(cοnd ((null? lst) #f)
((equal? key (first (first lst))) (secοnd (first lst)))
(else (lοοkup key (rest lst)))))
; update functiοn
(define (update key val lst)
(if (null? lst)
(list (cοns key val))
(if (equal? key (first (first lst)))
(cοns (cοns key val) (rest lst))
(cοns (first lst) (update key val (rest lst))))))
; equal-shape? functiοn
(define (equal-shape? pair1 pair2)
(cοnd ((and (pair? pair1) (pair? pair2))
(and (equal-shape? (first pair1) (first pair2))
(equal-shape? (rest pair1) (rest pair2))))
((null? pair1) (null? pair2))
((null? pair2) #f)
(else #t)))
To know more about RACKET programming language, visit:
https://brainly.com/question/30303017
#SPJ4
You sit down at your desk to begin working in your online class, and your computer won't turn on. How do you frame your problem into a question so you can solve it? (5 points)
Did my brother break my computer?
How will I get my schoolwork done today?
What is going on?
Why won't my computer turn on?
Answers
Answer:
I say number 4 makes more sense
Answer: why won’t my computer turn on
Explanation: I got a 100 trust
Using the regular expression library in a programming language that you know, write a short program to check whether a filename conforms to the Linux rules for filenames.
Answers
Regular expressions can be used to verify that filenames conform to Linux rules.
There should be no period at the beginning of the filename, and no special characters. Here is a straightforward Python application that makes use of regular expressions to check that a filename complies with the Linux filename conventions: check filename(filename) import re def: pattern is "[a-zA-Z0-9_]+$" If pattern and filename match, then return False if not: give False A filename is sent to the check filename() function, which returns Yes if the filename complies with Linux's filename conventions and False otherwise.
The regular expression pattern used in this function matches any string that consists of one or more alphanumeric characters or underscores.
To know more about Python, click here:
https://brainly.com/question/30391554
When someone asks, Is this information specific enough?, he or she is interested in more _____.
accuracy
logic
breadth
precision
Answers
Answer:
precision
Explanation:
In simple English precise means exact or something specific
there are many factors that should be considered when designing a mobile app. describe at least three of the primary concerns that need to be kept in mind and explain why they are important
Answers
The factors that should be considered when designing a mobile app are:
Target Audience BudgetSmooth and EfficientWhat factors are to be considered when creating a mobile app?There are a lot of factors that one has to look into when making or designing a mobile app. They are:
Good ResearchTarget Audience BudgetSmooth and EfficientUser ExperienceNote that by answering the questions regarding those factors above can help one to create a good app that is wanted by all.
Learn more about mobile app from
https://brainly.com/question/917245
#SPJ1
Answer:
Navigation- Make sure the when making a website for mobile that it is easy to navigate and buttons aren't too close together.
Data transfer- Keep in mind the more complex the site is the longer it will take for the page to load for mobile devices.
Battery Life- Unlike desktop mobile devices have to worry about their battery life, so if app uses GPS or real-time program while running the app it will drain your device.
A photograph is created by what
A) Silver
B) Shutters
C) Light
4) Mirror
Answers
A photograph is created by Light.
What are photographs made of?Any photograph created is one that is made up of Support and binders.
The steps that are needed in the creation of a photograph are:
First one need to expose or bring the film to light.Then develop or work on the imageLastly print the photograph.Hence, for a person to create a photograph, light is needed and as such, A photograph is created by Light.
Learn more about photograph from
https://brainly.com/question/25821700
#SPJ1
can anyone do electrical work if they posses the skills necessary??
Answers
Answer:
yes
Explanation:
Attributes of an electrician
Good communication and people skills. ...
Ability to work in a team or independently. ...
Problem Solving. ...
Basic Maths Skills. ...
Good English skills. ...
Understanding of regulatory requirement.
Exercise: Use appropriate formulas to count the requested items in each of the 3 columns. For example, the formula in cell B15 should count the numbers in the range B6:B13.
Answers
In the given problem, you are given three columns, and you need to count the requested items in each of the columns. You are also given an example of the formula used in cell B15. You can apply the same formula to count the items in all the three columns.
By using the COUNT function with the respective range for each column, you will obtain the count of non-empty cells in each column.
The formulas will ignore blank cells and text values, focusing on cells that contain numbers or logical values.
To summarize, you can apply the following formulas to count the requested items in each column:
Formula in cell B15: =COUNT(B6:B13)
Formula in cell C15: =COUNT(C6:C13)
Formula in cell D15: =COUNT(D6:D13)
By dragging or copying these formulas to the respective cells, you will obtain the count of items in each column based on the specified range.
To know more about COUNT function visit:
https://brainly.com/question/28180711
#SPJ11
Which types of computer hardware are internal?
Answers
Answer:
Here are some :) (sorry if there are too many)
Explanation:
RAM (Random Access Memory): It's a fast-access memory that is cleared when the computer is powered-down. RAM attaches directly to the motherboard, and is used to store programs that are currently running.
Video Card/GPU (Graphics Processing Unit): It's a specialized processor originally designed to accelerate graphics rendering.
Sound Card: USB sound "cards" are external devices that plug into the computer via USB.
Storage: SSD (Solid State Drive): It is a data storage device that uses solid-state memory to store persistent data.
HDD (Hard Disk Drive): It is a non-volatile storage device which stores digitally encoded data on rapidly rotating platters with magnetic surfaces. Just about every new computer comes with a hard disk these days unless it comes with a new solid-state drive.
CPU (Central Processing Unit/ sometimes just called a processor) It's a machine that can execute computer programs, and sometimes called the brain of the computer.
Motherboard: The motherboard is the body or mainframe of the computer, through which all other components interface. It is the central circuit board making up a complex electronic system.
Firmware: Firmware is loaded from the Read only memory (ROM) run from the Basic Input-Output System (BIOS). It is a computer program that is embedded in a hardware device, for example a microcontroller.
Power Supply: The power supply as its name might suggest is the device that supplies power to all the components in the computer.
CD-ROM Drive: There are two types of devices in a computer that use CDs: CD-ROM drive and a CD writer. The CD-ROM drive used for reading a CD. The CD writer drive can read and write a CD.
Floppy Disk: A floppy disk is a type of data storage that is composed of a disk of thin, flexible(“floppy”) magnetic storage medium encased in a square or rectangular plastic shell.
Internal Storage: Internal storage is hardware that keeps data inside the computer for later use and remains persistent even when the computer has no power.
Disk Array Controller: A disk array controller is a device which manage the physical disk drives and presents them to the computer as logical units.
On some computers the speakers are internal as well. :)
ASKING AGAIN CAUSE I GOT A WEIRD LINK
HTML5 allows web pages authors to place a/an _________ element around a block-level element that contains child elements
a. nav
b. div
c. h1
d. a
Answers
Answer:
A. Nav
Explanation:
....,..........
1) According to the text, what is a common cause of collisions ?
O taking a call on a cell phone
O defensive driving
O checking your surroundings
O no answer applies
Oscanning for hazards
is a common cause of collisions.
Answers
Answer:
Taking a call on a cell phone.
OpenMP programs can be written in such a way that they can also be correctly compiled using a compiler that does not support OpenMP.true/false
Answers
Answer: True However, the OpenMP directives will be ignored by the compiler and the resulting program will not have the benefits of parallelization that OpenMP provides.
This openmp code makes advantage of shared memory as its memory architecture.
Memory serves as the computer's electrical storage facility for such instructions and data that it needs to access fast. Information is kept there for quick access. A smartphone's ram is one of its fundamental components since without it, a machine would be unable to operate as intended.
Information is entered onto our storage device through the process of encoding.
Learn more about OpenMP here
https://brainly.com/question/29969762
#SPJ11
como interactua el hardware de la computadora con el ser humano
Answers
Answer:
Los humanos interactúan con las computadoras a través de una interfaz de usuario
In which of the following ways which will the words between the HTML tags appear on the screen for the following source code of a webpage: Welcome to the Colombian Coffee Store! graphical user interfaceAs a heading in the browser windowwill allow user interaction
Answers
The words between the HTML tags will appear on the screen for the following source code of a webpage as: As a heading in the browser window.
How will the words appear?The words between the HTML tags will likely appear as a heading on the webpage. When a person visits a website, the welcome information is often a heading that is well-highlighted and possibly colored to portray an inviting atmosphere.
When the visitor sees this tag, they get the idea that they are welcome and can explore the page for more service offerings and functionalities.
Learn more about HTML here:
https://brainly.com/question/4056554
#SPJ1
Which of the following describes data science?
A. Ubiquitous, on-demand access to shared servers and applications
B. Use of computers to learn and to understand language
C. Collection, preparation, management, analysis, interpretation and visualization of large and complex datasets
D. Extraction of meaning and new information from data in order to identify strategies for an organization
37. Input, processing and output controls within a system ensures data's
A. Security
B. Integrity
C. Objectivity
D. Authenticity
Answers
A. Ubiquitous, on-demand access to shared servers and applications.C. Collection, preparation, management, analysis, interpretation, and visualization of large and complex datasets.D. Authenticity.
Data science is best described by option C. It encompasses the collection, preparation, management, analysis, interpretation, and visualization of large and complex datasets. Data scientists use various techniques and tools to extract meaningful insights from data, enabling organizations to make informed decisions and identify strategies.
Option A refers to cloud computing and infrastructure, which is not specific to data science but can be utilized in various fields. Option B describes natural language processing, a subset of artificial intelligence, but it is not the sole focus of data science.
Regarding the second question, input, processing, and output controls within a system ensure the data's authenticity, which refers to the accuracy and reliability of the data. Authenticity ensures that the data is genuine and trustworthy, free from any tampering or unauthorized modifications. Therefore, the correct answer is option D. Security, integrity, and objectivity are also important aspects of data management, but they do not specifically address the authenticity of data.
To learn more about the dataset visit:
brainly.com/question/30703247
#SPJ11
What is the binary format for the following decimal ip address? 131. 9. 202. 111.
Answers
Answer: I'm pretty sure its 10000011.00001001.11001010.01101111.
Explanation: the binare format is 10000011.00001001.11001010.01101111.
I think
When a ____________ file is opened, it appears full-screen, in slideshow mode, rather than in edit mode.
Answers
Answer:
pptx
Explanation: