Jackson is working as part of a large animation team and is having a hard time making the characters move realistically because the “bones” and “joints” in the 3D models have some problems. In what step in the animation process were mistakes made?
A.
animation
B.
visual effects
C.
rigging
D.
rendering
Answers
The step in the animation process that involves some mistakes is rendering. Thus, the correct option for this question is D.
What is the Animation process?The animation process may be defined as the methodology of formulating the illusion of movement through the utilization of still images in a two-dimensional space. The process of animation significantly includes characters, storyboards, and backgrounds in the form of vector graphics.
The movement of bones and joints in the 3D models has some problems due to the rendering of actual sense to the viewers. The animation of this part is perfect along with visual effects but the delivery of this includes some confusion which creates problems.
Therefore, the step in the animation process that involves some mistakes is rendering. Thus, the correct option for this question is D.
To learn more about the Animation process, refer to the link:
https://brainly.com/question/28152242
#SPJ1
Related Questions
Question 2 (Show your steps, not only the final results.) According to the PMF table in Question 1, a bag is considered underqualified if it weights less than 47(<47). Randomly select three packages. What is the probability that at least one is underqualified ( 2 points)?
Answers
To calculate the probability of at least one underqualified package out of three randomly selected packages, we need to consider the complement rule. This rule states that the probability of an event occurring is equal to 1 minus the probability of the event not occurring. We will calculate the probability of none of the packages being underqualified and then subtract it from 1 to obtain the desired probability.
To calculate the probability of none of the packages being underqualified, we need to find the probability that each package weighs 47 or more. According to the PMF table in Question 1, the probability of a package weighing 47 or more is 0.67. Since the selection of each package is independent, we can multiply these probabilities together to obtain the probability of none of the packages being underqualified:
P(None underqualified) = 0.67 * 0.67 * 0.67 = 0.300763.
Next, we calculate the probability of at least one package being underqualified by subtracting the probability of none of the packages being underqualified from 1:
P(At least one underqualified) = 1 - P(None underqualified) = 1 - 0.300763 = 0.699237.
Therefore, the probability that at least one package out of three randomly selected packages is underqualified is approximately 0.699 or 69.9%.
Learn more about probability here: https://brainly.com/question/31355126
#SPJ11
Match each code snippet to its appropriate markup language name

Answers
Answer:
Please find the complete solution in the attached file.
Explanation:

You should see the following code in your programming environment:
import simplegui
def draw_handler(canvas):
frame = simplegui.create_frame('Testing', 600, 600)
frame.set_canvas_background("White")
frame.set_draw_handler(draw_handler)
frame.start()
Use the code above to write a program that draws a target. Your program should create an image similar to the one below:
Your image does not need to be exactly the same as the one below, but can have slight modifications (for example, your image can use a different color or different positioning of objects).

Answers
The recommended code for the bove prompt is:
import simplegui
def draw_handler(canvas):
# draw the target circles
canvas.draw_circle((300, 300), 200, 1, "White", "White")
canvas.draw_circle((300, 300), 150, 1, "Blue", "Blue")
canvas.draw_circle((300, 300), 100, 1, "Red", "Red")
canvas.draw_circle((300, 300), 50, 1, "Yellow", "Yellow")
frame = simplegui.create_frame('Target Drawing', 600, 600)
frame.set_canvas_background("White")
frame.set_draw_handler(draw_handler)
frame.start()
What is the explanation for the above response?The above code creates a simple GUI window using the SimpleGUI library and sets the background color of the window to white.
The draw_handler function is then defined to draw the circles of the target with specified colors and sizes. Finally, the GUI window is started using the start() method.
Learn more about code at:
https://brainly.com/question/28848004
#SPJ1
How to move from hardware program management to software product management.
Answers
Answer and Explanation:
I transitioned from semiconductors to software product management many years ago. It is much easier today as many hardware manufacturers are adopting many of the concepts and methodologies now mainstream within software development - namely, Agile and Lean. Where ever possible, ensure that you're adopting as many of these practices in your current industry as possible. Not only will this be better for your current product (IMHO), but it will enable you to build new muscles and demonstrate expertise in transferrable skills.
If you are early in your career, then the route Allan Hui promotes is a valid one. However, I would argue that we're living in an age of more doing than learning. Good product managers are extremely hard to find. If you're smart, a quick learner, and if you can demonstrate the core abilities to an experienced team that can appreciate your background, you can make the move relatively quickly.
A key book to read: Inspired, by Marty Cagan. This book is built upon the foundation of software product management.
Which genre of art is specific to digital media?
A. Graphic design
B. Photography
C. Animation
D. Video Games
Answers
compare and discuss between electromechanical and electronic era of computer
Answers
Answer:
The difference between electromechanical and electronic era of computer is that electomaechanical era was between the date of 1840 and 1940.These are the beginnings of telecommunication.While electronic era of computer was The electronic age is wha we currently live in. It can be defined as the time between 1940 and right now. The ENIAC was the first high-speed, digital computer capable of being reprogrammed to solve a full range of computing problems.
Which of the following cloud features is represented by leveraging remote monitoring and system tuning services?
Reliability
Performance
Utilization
Maintenance
Answers
Answer:
Reliability
Explanation:
8.If constant values are needed in several methods, declare them together with the instance fields of a class and tag them as _____ and _____ and give them public access.
Answers
You should declare the constant values together with the instance fields of a class and tag them as static and final while giving them public access.
What is a constant?A constant can be defined as any variable whose value can't be changed under any circumstance, once it has been assigned.
The types of variable modifiers.In Computer programming, there are two main types of variable modifiers that are used for creating a constant and these include:
Static modifierFinal modifierIn this scenario, you should declare the constant values together with the instance fields of a class and tag them as static and final while giving them public access, in order to make them accessible to all end users.
Read more on constant variable here: brainly.com/question/20264183
A local company has hired you to build a program that helps them manage their menu items. The program should allow the staff to add new menu items, remove existing ones, and search for items based on their name, category, or price. The program should also provide a way to sort the menu items based on name or price.
Using the data structures and algorithms that you have learnt, build a menu management program in Python
Answers
Here is a Python program that manages menu items by using data structures and algorithms that are implemented to help the staff of a local company.
This program allows the staff to add new menu items, remove existing ones, search for items based on their name, category, or price, and sort the menu items based on name or price:
```class Menu Item:
def __init__(self, name, category, price):
self.name = name
self.category = category
self.price = priceclass
Menu:
def __init__(self):
self.menu_items = [] def add_item(self, item):
self.menu_items.append(item)
def remove_item(self, item):
self.menu_items.remove(item)
def search_by_name(self, name):
Menu Item class represents a single item in the menu. It has three attributes - name, category, and price. Menu class represents the whole menu. It has several methods for adding, removing, searching, and sorting menu items. The main() function is responsible for running the program and interacting with the user.
To know more about Python visit:
https://brainly.com/question/30391554
#SPJ11
Josef wants to read more about Justice Jackson. Josef would find most of the information?

Answers
Answer: the answer is d
Explanation:
TRUST ME !!!
the introduction of the minicomputer a. allowed computers to be customized to the specific needs of departments or business units. b. enabled decentralized computing. c. offered new, powerful machines at lower prices than mainframes. d. all of the above.
Answers
The invention of the minicomputer made it possible to tailor computers to the unique requirements of departments or business units, enabling decentralised computing, and provided brand-new, potent machines for less money than mainframes. all the given option is correct.
What is minicomputer?
A minicomputer, often known as a mini, is a category of smaller general-purpose computers that were created in the middle of the 1960s and were marketed for significantly less money than mainframe and semi computers from IBM and its main rivals. The New York Times proposed a consensus definition of the a minicomputer in a 1970 survey as a device with an input-output device, such as a teleprinter, and at least four thousand words of memory that can execute program in a higher level language, including such Fortran or BASIC, and that costs less than US$25,000. The class comprised a unique group with its own operating systems and software architectures. As opposed to calculation and record keeping, minis were made towards control, instrumentation, human contact, and communication switching.
To learn more about minicomputer
https://brainly.com/question/28004913
#SPJ4
After you have solved the Tower of Hanoi at least three times, write an algorithm with clear, numbered steps that would guide another player through the steps of solving the puzzle.
Answers
Answer:
def tower_of_hanoi(n , source, auxiliary, destination):
if n==1:
print("Move disk 1 from source",source,"to destination",destination )
else:
tower_of_hanoi(n-1, source, destination, auxiliary)
print("Move disk",n,"from source",source,"to destination",destination )
tower_of_hanoi(n-1, auxiliary, source, destination)
n = 3
tower_of_hanoi(n,'A','B','C')
Explanation:
The python function "tower_of_hanoi" is a recursive function. It uses the formula n - 1 of the n variable of recursively move the disk from the source rod to the destination rod.
Finally, the three disks are mounted properly on the destination rod using the if-else statement in the recursive function.
Answer:
C. 127
Explanation: edge 2022
Choose the term so achieve the output shown.
>>>import math
>>>math. ___ (36)
6.0
•Sqr
•Root
•sqrt
Answers
Answer:
sqrt
Explanation:
Answer:
sqrt
Explanation:
sqrt= square root
sqrt of 36 is 6
An installation is:
please help asap
Answers
Answer: an installation is the act of putting something in, a device that stays in one place, a military base, or an art piece that often involves building and different types of materials.
Explanation:
Getting your new air conditioner put in is an example of an installation.
What are software applications?
lines of code that were written by developers
devices that you insert into the computer
files that are stored on the computer
Answers
Answer:
the person above is correct if i were you id take notes!
Explanation:
Answer:
Only A (Top answer)
Explanation:
Files do not create any software alltogether and devices pluged in are not considered software.
Some one help pls will mark brainless !!!!!
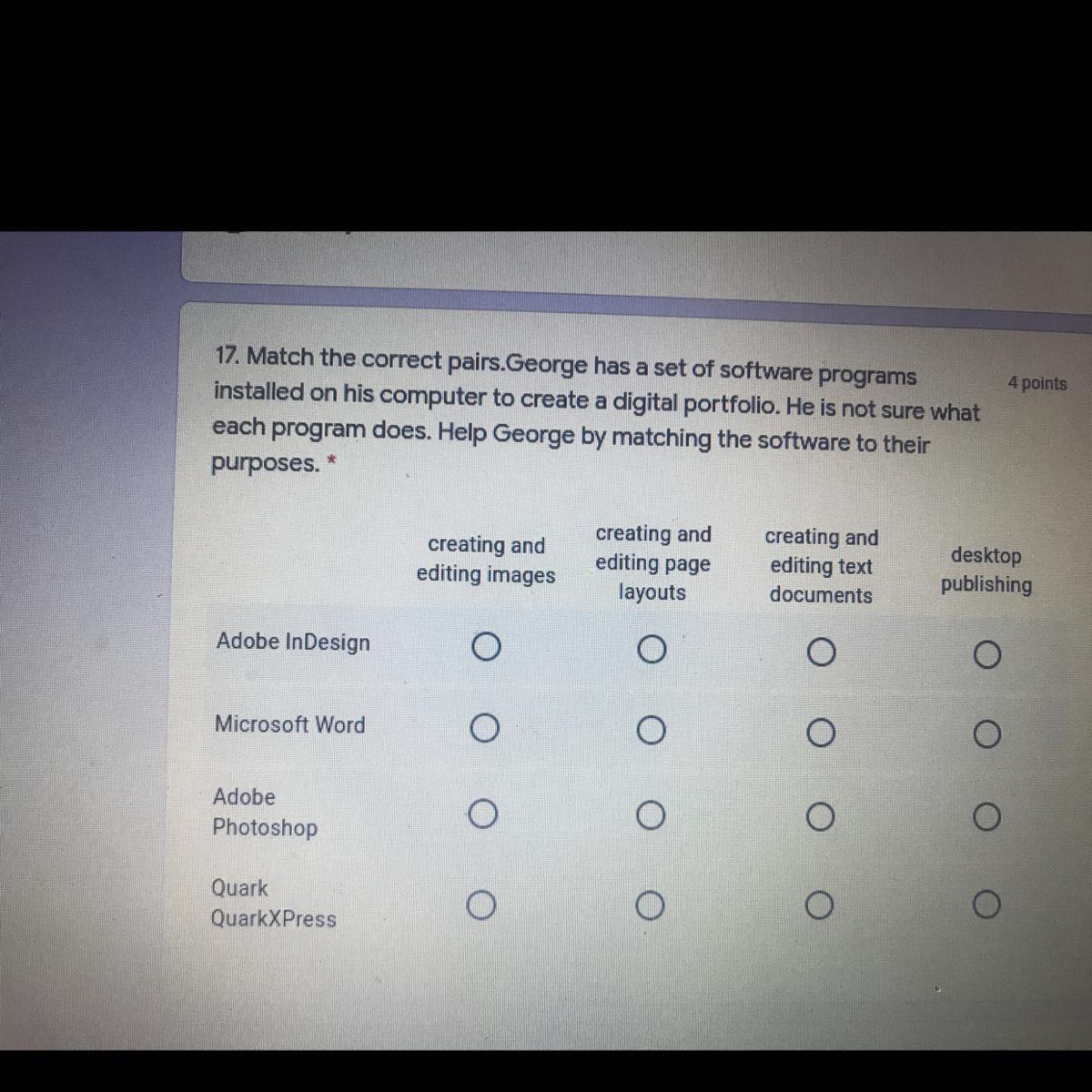
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
store id on the stores table is the primary key and defined as a number. if store id is a foreign key on the employee info table it and requires a .
Answers
Store id is a foreign key on the employee info table. It seems like the end of the sentence got cut off, but based on the information provided, I can make an assumption about what the missing part might be.
If the Store ID is a foreign key on the Employee Info table, then it would also need to be defined as a number, in order for it to reference the Store ID primary key on the Stores table. The foreign key constraint ensures that the Store ID values on the Employee Info table correspond to valid Store ID values on the Stores table. In database design, a foreign key is a column or set of columns in a table that refers to the primary key of another table. The purpose of a foreign key is to ensure referential integrity between the two tables.
Learn more about primary key: https://brainly.com/question/12001524
#SPJ11
I'm not sure how to do these. By the way, it has to be python.

Answers
Task 1:
float75 = float(75)
string75 = "75"
# you cannot add together a number and a string because a string has no inherent numerical value like a number does.
Task 2:
num = float(input("Enter a number"))
print(num**2)
Task 3:
num = int(input("Enter an integer: "))
print("When you divide "+str(num)+" by 7, the quotient is "+str(num//7)+" and the remainder is "+str(num%7)+".")
Task 4:
gigs = int(input("How many gigabytes does your flashdrive hold? "))
print("A flashdrive with "+str(gigs)+ " gigabyte(s) holds "+str(gigs*8589934592)+" bit(s).")
For task 4, you might have to change the number 8589934592 to something else. I'm not entirely sure how many bits are in a gigabyte. I hope this helps though.
Mention five(5) businesses that needs computer to apperate.
Answers
Answer:
1. Accounting
2. software developing
3. Website designing
4. Online transaction
5. Advertising
what is the primary protocol used by cisco ise to exchange policy information with other network components?
Answers
The primary protocol used by Cisco ISE to exchange policy information with other network components is pxGrid .
What is pxGrid?Cisco Platform Exchange Grid (pxGrid) enables multivendor, cross-platform network system collaboration between components of the IT infrastructure like security monitoring and detection systems, network policy platforms, asset and configuration management, identity and access management platforms, and practically any other...
Therefore, The pxGrid is considered a protocol and it is a protocol framework of high level mechanisms called pxGrid can be used with any kind of transport protocol. It doesn't bind to any transport.
Learn more about network components from
https://brainly.com/question/24133891
#SPJ1
Motor controllers are typically which
of the following?
A. Installed on motor housings
B. Installed in enclosures
C. Installed under floors by motors
D. Installed exposed in manufacturing plants
Answers
Answer:
The enclosure of the must protect the windings, bearings, and other mechanical parts from moisture, chemicals, mechanical damage and abrasion from grit. NEMA standards MG1-1.25 through 1.27 define more than 20 types of enclosures under the categories of open machines, totally enclosed machines, and machines with encapsulated or sealed windings.
how will search engines deal with a poor site structure? The search engines will rearrange the poor site structure into a better structure,
The search engines will not recommend the site to other users.
The search engines will dig deeper until they understand the site structure.
The search engines will continue coming back to the site in the event the site structure is fixed.
Answers
Search engines play a crucial role in determining whether your site is accessible to users, and they have specific criteria for ranking websites.
Poor site structure impacts search engines by making it difficult to navigate and search engine spiders to crawl and index the website. Search engines respond to poor site structure in several ways.
They are as follows:
1. The search engines will not recommend the site to other users.
If the site structure is terrible, search engines will not suggest it to users searching for related content.
This means that the website will have less traffic and may result in a loss of revenue.
2. The search engines will dig deeper until they understand the site structure.
Poor site structure makes it difficult for search engines to understand how the pages on the site relate to one another.
Search engines will try to crawl the website, but it may take them longer to find the content they're looking for.
3. The search engines will rearrange the poor site structure into a better structure.
Search engines are always looking for ways to enhance the user experience, and they will alter the site structure if it improves the user's experience.
4. The search engines will continue coming back to the site in the event the site structure is fixed. Once search engines have crawled your site, they will continue to return and update their index if changes are made to the site structure.
This means that if you improve your site structure, your website's search engine ranking may improve, resulting in increased traffic and revenue.
Know more about Search engines here:
https://brainly.com/question/512733
#SPJ11
What is my Sac State?
Answers
Your secure portal to manage your university account and utilize the technological services offered by the university is called My Sac State.
Sacramento, California's California State Institution, Sacramento (CSUS, Sacramento State, or just Sac State) is a public university. Founded in 1947 as Sacramento State College, it is the eleventh oldest institution in the California State University system. Since 1947, Sacramento State has been educating students and providing services to the capital area of California. Located six miles from the state Capitol and a vibrant urban core, the University and the community it serves are intertwined. Sacramento State provides a world-class education in the heart of California's capital. The University is home to some of the top programs, centers, scholars, and students in the country.
Learn more about technological here-
https://brainly.com/question/20414679
#SPJ4
Construct The Dupont Identify For 5tholis Goit. Mote: Do Not Round Intermeciate Calculations And Round Your Answers To 2 Decinal Places, E.G. 32.16, Finter The Profit Margin And Return On Equity As A Percent.Homework Assignment (0: Ch.2 \& 3 (Exam 1) (1) Wack Hire Frint A Tefurencest Construct The DuPont Identity For Smolira Golf Note: Do Not Round
Answers
To construct the DuPont identity for Smolira Golf, we need to calculate three key financial ratios: profit margin, total asset turnover, and equity multiplier. These ratios will help us analyze the company's profitability, efficiency in utilizing assets, and financial leverage. The DuPont identity formula combines these ratios to provide a comprehensive understanding of the company's return on equity (ROE).
1. Profit Margin: Calculate the profit margin by dividing net income by total revenue and expressing it as a percentage. It measures the company's ability to generate profits from its sales.
2. Total Asset Turnover: Calculate the total asset turnover by dividing total revenue by average total assets. It indicates how efficiently the company utilizes its assets to generate revenue.
3. Equity Multiplier: Calculate the equity multiplier by dividing average total assets by average shareholders' equity. It measures the financial leverage or debt-to-equity ratio of the company.
Once these ratios are calculated, we can use the DuPont identity formula: ROE = Profit Margin × Total Asset Turnover × Equity Multiplier. This formula helps us understand the overall return on equity, which represents the company's profitability in relation to its shareholders' equity.
Remember to perform the necessary calculations using the financial data of Smolira Golf, and round the final answers to two decimal places, expressing the profit margin and ROE as percentages.
Learn more about equity here:
https://brainly.com/question/33585348
#SPJ11
The programs that run on a computer are called:
Answers
a hacker has discovered a system vulnerability and proceeds to exploit it to gain access to the system. the vulnerability is not yet known to the developer so no fix is available. what type of attack is this?
Answers
Vulnerability - This is an example of a zero-day attack.
What is vulnerability?
Vulnerabilities are weaknesses in a computer system that reduce its overall security. Vulnerabilities might be flaws in the hardware itself or the software that uses it. A malicious actors, such as an attacker, can use vulnerabilities to breach privilege restrictions and carry out illegal actions on a computer system. An attacker needs at least one tool or technique that really can connect to a system flaw in order to exploit a vulnerability. In this context, the attack surface is another name for vulnerabilities. Discover all assets, prioritise assets, assess or do a full vulnerability scan, report on results, fix vulnerabilities, confirm remediation, and repeat are all frequent steps in the cyclical practise of vulnerability management.
To learn more about vulnerability
https://brainly.com/question/25633298
#SPJ4
A computer system consists uses usernames with 6 symbols, where the allowable symbols are capital letters (A, B, . . ., Z) and digits (0, 1, . . . , 9). Don’t multiply out. Leave your answers in a form like 7! × 53 × 2.
(a) How many usernames are possible if repetition is not allowed?
(b) How many usernames allow repetition and use only letters?
(c) How many usernames are possible if the first three symbols must be different capital letters (i.e., no repeats), the last symbol must be a nonzero digit, and there are no other restrictions on the symbols?
Answers
The possible usernames if repetition is not allowed is 36⁶.
The usernames that allow repetition is 26⁶
The usernames possible if the first three symbols must be different is 15,600.
How to find possibilities?(a) There are 36 possible symbols for each of the 6 symbols, so there are 36⁶ possible usernames.
(b) There are 26 possible letters for each of the 6 symbols, so there are 26⁶ possible usernames.
(c) There are 26 possible letters for the first symbol, 25 possible letters for the second symbol, and 24 possible letters for the third symbol. There are 10 possible digits for the last symbol. So there are 26 × 25 × 24 × 10 = 15,600 possible usernames.
The first three symbols must be different capital letters. There are 26 possible capital letters for the first symbol, 25 possible capital letters for the second symbol, and 24 possible capital letters for the third symbol. So there are 26 × 25 × 24 possible combinations for the first three symbols.
The last symbol must be a nonzero digit. There are 10 possible digits for the last symbol. So there are 26 × 25 × 24 × 10 possible usernames.
Find out more on computer system here: https://brainly.com/question/30146762
#SPJ4
the processing is done in the
Answers
Answer:
CPU Central Processing Unit
Answer:
CPU.... I'm not sure but it might be right or can u put the full question because it sorta don't make any sense
An operating system is an interface between human operators and application software
Answers
It is true that an operating system is an interface between human operators and application software.
What is a software?Software is a collection of instructions, data, or computer programmes that are used to run machines and carry out particular activities.
Hardware, on the other hand, refers to a computer's external components. Applications, scripts, and programmes that operate on a device are collectively referred to as "software."
An operating system is a piece of software that serves as a conduit between the user and the hardware of a computer and manages the execution of all different kinds of programmes.
An operating system (OS) is system software that manages computer hardware, software resources, and provides common services for computer programs.
Thus, the given statement is true.
For more details regarding software, visit:
https://brainly.com/question/985406
#SPJ9
defina constant and explain its type
Answers
A constant can be defined as the a thing whose value constant across duration. A constant is a statistic that applies to all computations equally and does not change. There are four types of constant.
What is constant?Constant refers to a set point that cannot be altered while a running program is running. A numeric, symbol, or sequence of characters is referred to as a constants in the Program code. Or any type of data may be used. Lambda expressions are another name for integers.
Constants are classified into four types:
integer, string, hexadecimal string, bit.Learn more about constant , here:
https://brainly.com/question/1597456
#SPJ1