Is malware malicious code?
Answers
Explanation:
Yes, malware is short for malicious software and is a type of code that is designed to cause harm to a computer or network. It can be used to steal sensitive information, destroy data, or gain unauthorized access to a system. Malware is often spread through email attachments, malicious websites, or infected software downloads, and it can take many different forms, including viruses, worms, Trojan horses, ransomware, and spyware.
Related Questions
What was the contribution of John von Neuman in the development of computer?
Answers
Answer:
Explanation: As director of the Electronic Computer Project at Princeton's Institute for Advanced Study (1945-1955), he developed MANIAC (mathematical analyzer, numerical integrator, and computer), which was at the time the fastest computer he was also one of the conceptual inventors of the stored-program digital computer.
John von Neumann's significant contribution to computer development was his invention of the von Neumann architecture, enabling programmable computers.
John von Neumann, the virtuoso polymath hailing from Hungary, emerged as a brilliant luminary who graced the 20th century with his unparalleled contributions to mathematics, physics, and computer science.
Proficient in quantum mechanics, game theory, and nuclear physics, he navigated an intellectual universe as vast as the cosmos itself. Yet, it was the von Neumann architecture, the monument of his ingenuity, that etched his name indelibly in the history of computing.
Like a maestro conducting an orchestra of ideas, von Neumann orchestrated a symphony of innovation, transforming the world with his multifaceted genius and forever inspiring the pursuit of knowledge.
Learn more about John von Neuman here:
https://brainly.com/question/21842436
#SPJ7
Under which accounting method are most income statement accounts translated at the average exchange rate for the period ?
A) current/concurrent method
B) monetary/nonmonetary methode
C)temporal method
D)All of the options
Answers
Under the accounting method where most income statement accounts are translated at the average exchange rate for the period, the correct option is D) All of the options.
The current/concurrent method considers both monetary and nonmonetary balance sheet items and translates income statement accounts at the average exchange rate for the period. This method takes into account the fluctuations in exchange rates throughout the period and provides a more accurate representation of the financial results in the reporting currency.
By using the average exchange rate, the impact of exchange rate fluctuations on income statement accounts is spread out over the period, reducing the impact of currency volatility on reported earnings.
Learn more about accounting method here: brainly.com/question/30512760
#SPJ11
bhhwbuwqdybquyiqyiuydwbuqiwdbyuqwudyb,
Answers
Answer:
The cell state splitter is a membraneless organelle at the apical end of each epithelial cell in a developing embryoThe cell state splitter is a membraneless organelle at the apical end of each epithelial cell in a developing embryoThe cell state splitter is a membraneless organelle at the apical end of each epithelial cell in a developing embryoThe cell state splitter is a membraneless organelle at the apical end of each epithelial cell in a developing embryo
Answer:
butter
Explanation:
Which of the following demonstrates an information system? Tyra is using the computer to create a birthday card for her friend. Ahmad is installing new software to improve the ease of accessing the database. Shania is creating a printed handbook of company policies for new employees. Ian is making updates to the company website to include the latest product information
Answers
Answer:
B. Ahmad is installing new software to improve the ease of accessing the database.
C. Shania is creating a printed handbook of company policies for new employees.
D. Ian is making updates to the company website to include the latest product information
Explanation:
Information Systems is an organized way of assembling, processing, storing, and sharing information. It is used by organizations to run their businesses. A typical information system will feature the people who run or control the process, the tasks they are meant to perform, the procedures which govern the work done, and the technology used to achieve those goals. Information systems incorporate information technology into the running of the business. The examples cited above, illustrate the application of information systems in business affairs. For example,
1. When Ahmad installs new software to improve the ease of accessing the database, the main components of an information system which includes; people (Ahmad), the task (which entails installation of the software), the procedures (that govern software installation), and the technology (apparently a computer system), all have a role to play.
where should the works cited page appear in the document?
Answers
Answer:
The Works Cited Page should be the last page of the documents (and it should be a separate page on its own, not just at the bottom of the essay).
how and why Steve Jobs left Apple Computer.
Answers
Answer:
Jobs was forced out of Apple in 1985 after a long power struggle with the company's board and its then-CEO John Sculley. ... He was largely responsible for helping revive Apple, which had been on the verge of bankruptcy.
Explanation:
Programs which were typically reserved for college-level classes such as computer animation and CAD programs are now being applied in high school classrooms across the country as part of the_______________________.
A. STEM engineering initiative
B. STEM education issues
C. STEM education initiatives
D. all of the responses
Please help
Answers
Step by step explanation:
Programs which were typically reserved for college-level classes such as computer animation and CAD programs are now being applied in high school classrooms across the country as part of the STEM education initiatives. Thus, option C is correct.
What is Transformative graduate education programs?Transformative graduate education programs (TGP) is applications with a countrywide scope known as transformative graduate schooling programmes (TGP) are supposed to have an effect at the reformation of graduate training inside the united states.
On the way to start comparing the impact of TGPs on the wide variety of doctoral tiers provided, a essential outcome for such programmes and a pinnacle academic precedence in many nations, we use records from national resources and change the unit of evaluation from the man or woman doctoral pupil to the doctoral organization as a whole.
We look at whether or not TGPs improve the awarding of Ph.D. degrees to ladies and minorities, and if they do, whether or not they accomplish that at STEM-orientated universities, which are often the least welcoming of all environments for these organizations.
Thus, option C is correct.
To learn more about Transformative graduate education programs (TGP) refer the link:
brainly.com/question/28091427
#SPJ3
(10 points) For EM algorithm for GMM, please show how to use Bayes rule to drive \( \tau_{k}^{i} \) in closed-form expression.
Answers
The closed-form expression for \( \tau_{k}^{i} \) in the EM algorithm for GMM is derived using Bayes rule, representing the probability that observation \( x_{i} \) belongs to the kth component. By dividing the likelihood and prior by the sum of all such terms, we arrive at the desired expression.
In EM algorithm for GMM, Bayes rule can be used to derive the closed-form expression for \( \tau_{k}^{i} \).
The expression is as follows:$$\tau_{k}^{i} = \frac{p_{k}(x_{i}|\theta_{k})\pi_{k}}{\sum_{j=1}^{K}p_{j}(x_{i}|\theta_{j})\pi_{j}}$$where, \(x_{i}\) is the ith observation, \(\theta_{k}\) represents the parameters of the kth component, \(p_{k}(x_{i}|\theta_{k})\) represents the probability of \(x_{i}\) belonging to the kth component, and \(\pi_{k}\) is the mixing proportion of the kth component.
To derive this expression using Bayes rule, we can use the following steps:1. Using Bayes rule, we can write the posterior probability of the kth component as:$$p_{k}(\theta_{k}|x_{i}) = \frac{p_{k}(x_{i}|\theta_{k})\pi_{k}}{\sum_{j=1}^{K}p_{j}(x_{i}|\theta_{j})\pi_{j}}$$2.
Since we are interested in the probability that the ith observation belongs to the kth component, we can simplify the above expression as:$$p_{k}(x_{i}|\theta_{k})\pi_{k} = \tau_{k}^{i}p_{k}(\theta_{k}|x_{i})\sum_{j=1}^{K}\tau_{j}^{i}p_{j}(x_{i}|\theta_{j})$$3. Dividing both sides of the above equation by \(p_{i}(x_{i})\), we get:$$\tau_{k}^{i} = \frac{p_{k}(x_{i}|\theta_{k})\pi_{k}}{\sum_{j=1}^{K}p_{j}(x_{i}|\theta_{j})\pi_{j}}$$This is the closed-form expression for \( \tau_{k}^{i} \) that we were looking for.
For more such questions algorithm,Click on
https://brainly.com/question/13902805
#SPJ8
A project to develop a new-generation of integrated circuit is an example of a(an) ________________
Group of answer choices
a. Unique project
b. Technology project
c. Routine project
d. Administrative project
Answers
A project to develop a new-generation integrated circuit would be classified as a technology project (option b). It involves the application of specialized knowledge and technical expertise to create an innovative product.
The development of a new-generation integrated circuit requires advanced technical skills and specialized knowledge in the field of electronics and semiconductor technology. It involves designing and manufacturing a highly complex electronic component that integrates multiple functions into a single chip. This type of project typically involves research, experimentation, and innovation to achieve advancements in performance, functionality, or miniaturization.
Technology projects are characterized by their focus on creating or improving technological products, processes, or systems. They often require a high degree of technical expertise, collaboration with experts, and the use of specialized tools and equipment. The development of new integrated circuits falls into this category as it involves pushing the boundaries of existing technology to develop cutting-edge solutions.
Unlike routine projects that involve repetitive tasks or administrative projects that focus on organizational processes, technology projects are unique and often have a significant impact on the industry or market. They require creativity, problem-solving skills, and the ability to adapt to rapidly evolving technological advancements. The development of a new-generation integrated circuit aligns with the characteristics of a technology project due to its innovative nature and the specialized knowledge and skills required for its successful execution.
Learn more about integrated circuit here:
https://brainly.com/question/33512970
#SPJ11
What is the purpose of the CC option in an email?
A.
Create a carbon copy of the message.
B.
Save the message as a template for future use.
C.
Send a copy of the message to one or more people.
D.
Forward a message to multiple recipients.
( Edmentum MSE )
Answers
Answer:
c
Explanation:
send a copy of the messege
true or false if a file with the specified name already exists when the file is opened, and the file is opened in 'w' mode, then the existing file will be overwriten
Answers
True. If a file with the specified name already exists when the file is opened, and the file is opened in 'w' mode, then the existing file will be overwritten.
About 'w' modeIf a file with the specified name already exists when the file is opened, and the file is opened in 'w' mode, then the existing file will be overwritten.
This is because 'w' mode is used to write to a file, and if the file already exists, it will be overwritten with the new content. If you want to append to an existing file instead of overwriting it, you can use 'a' mode.
Here is an example:
# Open a file in 'w' mode file = open('example.txt', 'w')
# Write some content to the file file.write('This is some content.')
# Close the file file.close()
# Open the file again in 'w' mode file = open('example.txt', 'w')
# Write some more content to the file file.write('This is some new content.')
# Close the file file.close() ``` In this example, the file 'example.txt' will be overwritten with the new content, and the original content will be lost.
Learn more about w mode at
https://brainly.com/question/29835433
#SPJ11
WILL GIVE BRAINLIEST!!!!!!!!

Answers
Answer:
camera
Explanation:
they used a camaera so technology inspired
What types of customizations have you or would you make to your operating system, and why?
Answers
Answer:
Explanation:
I have made a couple of customizations to my OS, which is Windows 10. The first being that I activated dark mode, this feature turns the entire OS into a dark-themed color, including apps and menus. This makes using the computer for extended hours much easier on the eyes. The other very important customization I added was a hover taskbar. This allows me to add many important shortcuts to the taskbar which all appear when I hover over the taskbar. It makes my desktop much cleaner and I have quick and easy access to my most important applications.
A recursive method that computes the number of groups of k out of n things has the precondition that ______. n is a positive number and k is a nonnegative number n is a nonnegative number and k is a positive number n and k are nonnegative numbers n and k are positive numbers
Answers
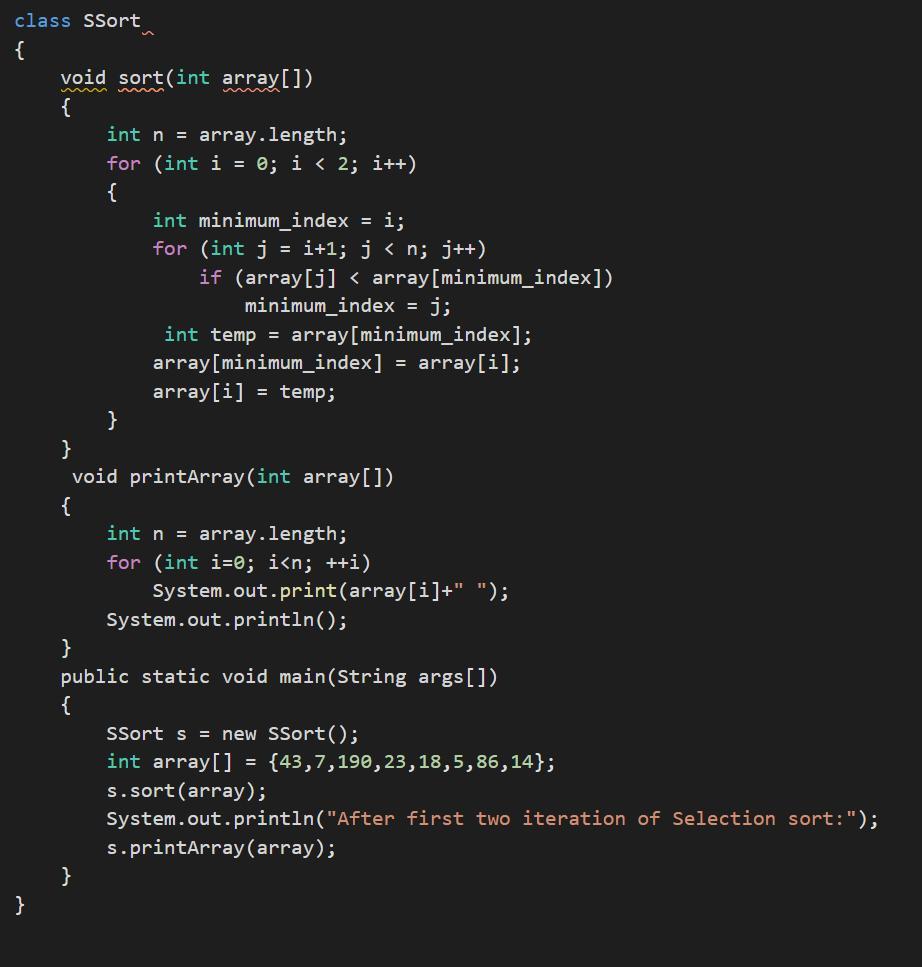
Show the contents of the array {43, 7, 190,23,18, 5,86,14} (sort in ascending order) after the first two iterations of Selection Sort. How many comparisons would be needed to sort an array containing 10 elements using Bubble sort in the worst case
Answers
Using the knowledge in computational language in JAVA it is possible to write a code that organizes the values in larger and smaller in arguments.
Writing the code in JAVA we have:class SSort
{
void sort(int array[])
{
int n = array.length;
for (int i = 0; i < 2; i++)
{
int minimum_index = i;
for (int j = i+1; j < n; j++)
if (array[j] < array[minimum_index])
minimum_index = j;
int temp = array[minimum_index];
array[minimum_index] = array[i];
array[i] = temp;
}
}
void printArray(int array[])
{
int n = array.length;
for (int i=0; i<n; ++i)
System.out.print(array[i]+" ");
System.out.println();
}
public static void main(String args[])
{
SSort s = new SSort();
int array[] = {43,7,190,23,18,5,86,14};
s.sort(array);
System.out.println("After first two iteration of Selection sort:");
s.printArray(array);
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

Ups developed software called ____ to enable u.s. customs and border protection agents to inspect packages that pass through the worldport international hub in louisville.
Answers
Ups developed software called target search to enable u.s. customs and border protection agents to inspect packages that pass through the worldport international hub in louisville.
An American international shipping, receiving, and supply chain management corporation, United Parcel Service, was established in 1907. The American Messenger Firm, which first specialized in telegraphs, evolved into UPS, one of the biggest shipping couriers in the world and a Fortune 500 company.
Today, UPS is most well-known for its ground delivery services and the UPS Store, a retail network that helps UPS packages and offers equipment for small businesses.
Learn more about UPS https://brainly.com/question/27583268
#SPJ4
Which of the following characters are wildcards in Excel? (Check all that apply.) A. # B. * C. ? D. $.
Answers
The asterisk (*) and the question mark (?) are wildcards in Excel.
The asterisk represents any number of characters, while the question mark represents a single character. The pound sign (#) is not a wildcard, but is used to represent numbers in certain formats. The dollar sign ($) is not a wildcard either, but is often used in cell references to indicate an absolute reference. This explanation provides detail on each of the options and clarifies which are and are not wildcards in Excel.
In Excel, wildcards are special characters that represent other characters in certain functions and formulas.
Represents any sequence of characters or a string of any length (including zero length). For example, "A*" would match any text starting with the letter "A."
To know more about Excel visit:-
https://brainly.com/question/28643466
#SPJ11
d What sales methods do you think would work best for selling this product? TIP: Would you sell the product online, over the phone, in a store, etc.? (1-5 sentences. 2.0 points)
e. Describe the methods you would use to pay and motivate sales people to sell this product. Would you use sales quotas or a particular type of commission structure? Why or why not? (1-5 sentences. 2.0 points)
f. What price do you think the company should charge for this product? Explain what factors you considered in deciding what price to charge. (1-6 sentences. 4.0 points)
Answers
Assuming that the chosen product is a smartphone, the sales method that would work to improve to sell this product would be the exposure in a specialized store where the potential customer could try out the device's features and obtain personalized service to solve their doubts.
Sales methodsThese are techniques used for the company to achieve the best performance in its sales, it must be aligned with organizational values and objectives to be effective. Some examples are:
Sales commandConsultative sellingCustomer-centric sellingThe methods used by the cell phone company management to pay and motivate sales personnel to sell this product would be to establish a commission structure focused on specific sales targets.
This strategy would motivate employees to sell more devices focused on increasing their benefits, increasing their productivity and service quality to better serve customers.
The price that the company should charge for the product must be compatible with the market, being the factors for determining the final price, the design, the physical components, the benefits and the value of the brand for the consumers.
Find out more information about sales methods here:
https://brainly.com/question/18957404
this device can be used to type documents,send email,browse the internet,handle spreadsheets,do presentations,play games,and more.
Answers
Calculate the Branch-CPI-Penalty for a system like the one in Lesson 14, Slide 21, whose buffer hit rate = 0.88 and whose prediction accuracy for entries in the buffer = 0.91. Assume the probability of a branch not in BTB being taken = 0.59. Round your answer to three decimal places.
Answers
Based on the information, the Branch-CPI-Penalty for the given system is approximately 0.5716.
How to calculate the valueGiven the prediction accuracy for entries in the buffer (P1 = 0.91), we can calculate the branch misprediction penalty using the formula:
Branch-Misprediction-Penalty = 1 - P1
Branch-Misprediction-Penalty = 1 - 0.91
= 0.09
Given the buffer hit rate (P2 = 0.88) and the probability of a branch not in BTB being taken (P3 = 0.59), we can calculate the BTB miss penalty using the formula:
BTB-Miss-Penalty = 1 - (P2 * P3)
BTB-Miss-Penalty = 1 - (0.88 * 0.59)
= 1 - 0.5184
= 0.4816
Branch-CPI-Penalty = Branch-Misprediction-Penalty + BTB-Miss-Penalty
= 0.09 + 0.4816
= 0.5716
Therefore, the Branch-CPI-Penalty for the given system is approximately 0.5716.
Learn more about system on
https://brainly.com/question/28561733
#SPJ4
2. Read the following scenarios about how three different programmera approach
programming a computer game. Identify which type of programming design
approach each represents (3 points):
a) Yolanda first breaks down the whole game she needs to program into modules.
She then breaks these modules into smaller modules until the individual parts are
manageable for programming. She writes the smallest modules, and then
recombines them into larger parts.
b) Isabella takes the game process and groups together sets of related data involved
in the process. She then identifies the messages the data should respond to. After
writing the code for each set of data, Isabella then combines, tests, and refines the
subsets until the software runs properly
Answers
a.) Structured programming
b.) Object-oriented programming
c.) Top-down programming
The programming design approach represented in this scenario is modular programming. The programming design approach represented in this scenario is object-oriented programming.
What is programming?The process of creating a set of instructions that tells a computer how to perform a task is known as programming.
Computer programming languages such as JavaScript, Python, and C++ can be used to create programs.
Modular programming is the programming design approach represented in this scenario.
Yolanda divides the entire game into modules, which are then subdivided further into smaller modules until the individual parts are manageable for programming.
Object-oriented programming is the programming design approach represented in this scenario. Isabella organizes sets of related data and determines which messages the data should respond to.
Thus, this method entails representing data and functions as objects and employing inheritance and polymorphism to generate flexible and reusable code.
For more details regarding programming, visit:
https://brainly.com/question/11023419
#SPJ2
the object oriented element that allows us to build more complex objects out of simpler objects is.
Answers
In object-oriented programming, the composition approach divides a big class into smaller classes or objects. It is a technique for combining smaller classes or objects to produce more complex ones.
Which object-oriented component does has-a relationship define?Association is a relationship of the "has-a" variety. Through the use of their objects, associations create the relationship between two classes. One-to-one, one-to-many, many-to-one, and many-to-many associations are all possible.
What two fundamental building blocks of an object do you see in object-oriented programming?State: Fields, or member variables in classes, are where an object stores its state. Specified behaviours - A method is how an item communicates its behaviour (functions in some programming languages).
To know more about programming visit:-
https://brainly.com/question/11023419
#SPJ1
Best available control technology (bact) is the same as maximum achievable control technology (mact).
a. true
b. false
Answers
Answer:
false
Explanation:
best available control technology (bact) refers to the methods that are best for the control of pollution, bacterial infections etc etc
whereas,
maximum achievable control technology (mact) are the standards introduced in 1990s for clean air and environment.
configure and apply a numbered standard acl on router0 which denies traffic from all hosts in the subnet to router 1.
Answers
To configure and apply a numbered standard ACL on router0 to deny traffic from a subnet to router1, you need to create a numbered standard ACL, specify the deny statement for the desired source address and wildcard mask, apply the ACL to the inbound interface of router0, and save the configuration.
How can you configure and apply a numbered standard ACL on router0 to deny traffic from a subnet to router1?How you can configure and apply a numbered standard ACL on router0 to deny traffic from all hosts in the subnet to router1:
Create a numbered standard ACL by typing "access-list [number] deny [source-address] [wildcard-mask]" command. For example, you can type "access-list 10 deny 192.168.1.0 0.0.0.255" to deny traffic from all hosts in the 192.168.1.0/24 subnet.
Apply the ACL to the inbound interface of router0 by typing "interface [interface-name]" and then "ip access-group [acl-number] in" command. For example, if the interface connecting router0 to the subnet is "FastEthernet0/0", you can type "interface FastEthernet0/0" followed by "ip access-group 10 in" to apply the ACL.
Save the configuration by typing "write memory" or "copy running-config startup-config" to ensure that the configuration is saved and will persist after a reboot.
That's it! With this configuration, all traffic from the specified subnet will be denied when it tries to reach router1.
Learn more about numbered standard ACL
brainly.com/question/32140320
#SPJ11
Which one?..........

Answers
Answer:
d. Clock
Explanation:
A flip flop is an circuit, an electrical circuit precisely that is used as a means to story data or information. This type of data or information stored in a flip flop is binary data or information. A flip flop has a high stable state and a low stable state.
A flip flop is a circuit that is very essential and must be present when building systems like the computer or communication system.
A flip flop must have a CLOCK signal or indicator because this helps control the triggering(i.e the change from one state to another) that occurs in a flip flop.
WILL GIVE BRAINLIEST!!!!!!
People do look at transportation options when considering neighborhoods to which to move.
True
False
Answers
True is the answer youre looking for
an attacker managed to associate his/her mac address with the ip address of the default gateway. in result, a targeted host is sending network traffic to the attacker's ip address instead of the ip address of the default gateway. based on the given info, which type of attack is taking place in this scenario?
Answers
Based on the given information, the type of attack that is taking place in this scenario is ARP Spoofing.
The main purpose of ARP Spoofing is to link the MAC address of the attacker's device with the IP address of the default gateway so that the targeted host sends network traffic to the attacker's IP address rather than the IP address of the default gateway. ARP Spoofing is a form of network attack in which the attacker sends fake Address Resolution Protocol (ARP) messages on a local area network (LAN). ARP Spoofing is also known as ARP Poisoning, ARP Poison Routing (APR), or ARP Cache Poisoning.
ARP Spoofing attacks are successful because of the way the Address Resolution Protocol works. ARP is a low-level network protocol that resolves IP addresses to physical addresses, such as MAC addresses, on a local area network (LAN). The attacker can cause network traffic to flow through the attacker's computer by associating his or her MAC address with the IP address of the default gateway. The attacker may then intercept or alter network traffic to achieve their goals, such as stealing data or spreading malware.
Learn more about ARP Spoofing:https://brainly.com/question/2864303
#SPJ11
A forensics analyst is attempting a live acquisition of the contents of the memory of a running Linux device. In order to copy the blocked /dev/mem file with memdump or dd, the analyst must install a kernel driver. Recommend a framework that will enable the analyst to install a kernel driver.
Answers
Linux requires a small amount of RAM compared to other modern operating systems. You should have at least 8 MB, even though having at least 16 MB is highly recommended.
What memory of a running Linux device?To find out how much memory the computer has, run the Linux command cat /proc/meminfo. This command makes the data contained in the /proc directory's meminfo file available for viewing.
Therefore, MemTotal, which is given in the sample in bold, denotes the total amount of memory that will be exposed. The more RAM you have, the faster the system will work.
Learn more about Linux device here:
https://brainly.com/question/28502677
#SPJ1
Along with chaining together blocks of data using hashes, what two other features help blockchain remain secure?.
Answers
Along with chaining together blocks of data using hashes, the two other features that help blockchain remain secure is decentralization and consensus.
What other two characteristics aid in keeping blockchain secure?Data structures created by blockchain technology include built-in security features. It is founded on cryptographic, decentralized, and consensus concepts that guarantee the integrity of transactions.
Note that the two types of cryptographic keys are private key and public key. Both of these keys are held by each person or node, and they are used to generate digital signatures. The most significant feature of blockchain technology is this digital signature, which serves as a specific and secure reference for a digital identity.
Learn more about decentralization from
https://brainly.com/question/25661114
#SPJ1
A company can provision a new EC2 instance at the click of a button, which reduces the time to make those resources available to their development team from weeks to just minutes. Which benefit of cloud computing does this demonstrate?
Answers
The benefit of cloud computing that this scenario demonstrate is an increase in speed and agility.
What is cloud computing?Cloud computing can be defined as a type of computing that requires the use of shared computing resources over the Internet rather than the use of local servers and hard drives.
The features of cloud computing.In Computer technology, the features of cloud computing include the following:
ElasticityOn-Demand self-service.MultitenancyPooled resourcesIn this scenario, the benefit of a cloud computing that reduces the time to make resources available to EC2's development team from weeks to just minutes is increased speed and agility.
Read more on cloud computing here: https://brainly.com/question/19057393