__________ involves moving part or all of a process from main memory to disk.
Answers
paging involves moving part or all of a process from main memory to disk.
Paging is a memory management technique used by computer operating systems. It involves breaking up the main memory into fixed-size blocks called "pages" and moving some or all of a process's pages from main memory to disk. This is done when the system needs more physical memory than is available. Paging allows more processes to be run simultaneously, but it can also cause performance issues if there is a lot of paging activity. When a process needs to access a page that has been paged out, it must be read back into main memory from disk, which can be slow.
learn more about memory here:
https://brainly.com/question/30273393
#SPJ11
Paging involves moving part or all of a process from main memory to disk.
Paging is a memory management technique used by operating systems to free up space in main memory (RAM) by temporarily transferring pages of data to disk.
To optimize the use of memory and allows the system to run more programs simultaneously.
A process requires a page that has been swapped out to disk, the operating system will swap it back into main memory.
The process of moving part or all of a process from main memory to disk is called "paging" or "swapping".
Technique used by the operating system to manage memory resources efficiently.
The system runs out of available physical memory, it can temporarily move some of the less-used portions of the memory to disk to make room for other processes that need more memory.
Portions of memory are needed again; they can be loaded back into main memory from disk.
This process is transparent to the running processes and is handled by the operating system.
"Paging" or "swapping" refers to the process of transferring all or a portion of a process from main memory to disc.
The operating system uses this method to effectively manage memory resources.
In order to make room for other programmed that require more memory when the system's physical memory supply runs out, the system may temporarily shift part of the memory's less-used regions to disc.
They can be read back from disc and put into main memory when they are required once again.
The operating system controls this process, which is invisible to other processes that are already active.
For similar questions on Memory
https://brainly.com/question/28483224
Related Questions
The _______ is used to change the date Auto Fill option.
A. Fill Tag
B. Tag
C. Smart Fill
D. Smart Tag
Answers
A family just changed to a different mobile phone and data service provider. They now need take some time to transfer their content to new phones and learn the features of the new service. This is an example of a:
Answers
The above scenario is an example of switching cost customers incur changing to a new supplier.
What id Switching costs?This is known to be the the costs that a consumer gets or has due to the effect of changing brands, or products.
Note that the above is an example of switching cost customers incur changing to a new supplier as they are said to be psychological, effort-based, and needs time.
Learn more about mobile phone from
https://brainly.com/question/917245
#SPJ1
Match the five traits to their descriptions. word choice Sentences flow naturally from one idea to the next. 슈 conventions The writing is structured in a way appropriate to the topic and purpose. voice Spelling, grammar, and other rules are followed sentence fluency Precise terms enliven the text. organization A sense of the writer's personality comes through. any help

Answers
Answer:
organization goes to "the writing is structured..."
word choice goes to "precise terms..."
voice goes to "a sense of the writer's..."
sentence fluency goes to "sentences flow naturally..."
conventions goes to "spelling, grammar..."
Answer:
yw
Explanation:

Which of the constraints listed below would be considered a physical constraint
-Materials
-Demand for product
-Timeline
-Cost
Answers
materials are the only physical thing
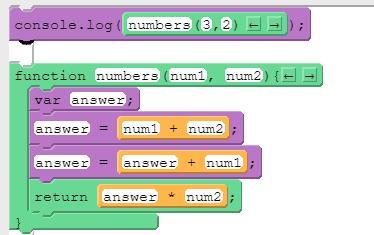
What will print to the console after running this code segment?
A. 15.
B. 16.
C. 18.
D. 21.
Answers
Answer:
16
Explanation:
answer =3+2
answer =5+3
return 8 × 2
16 will print to the console after running this code segment. Therefore, option B is correct.
What do you mean by code segment ?A code segment, also known as a text segment or simply text, is a section of an object file or the program's virtual address space that contains executable instructions.
A character array segment that represents a text fragment. Even though the array is directly accessible, it should be treated as immutable. This allows for quick access to text fragments without the overhead of copying around characters.
In memory, the code segment functions normally as read-only memory and has a fixed size; thus, without the need for loading, it can generally be found in read-only memory (ROM) on embedded systems.
answer = 3+2, answer = 5+3
return 8 × 2
= 16
Thus, option B is correct.
To learn more about the code segment, follow the link;
https://brainly.com/question/20063766
#SPJ2
Windows 1.0 was not considered to be a "true" operating system but rather an operating environment because _____.
it crashed a lot
it could only run one application at a time
it didn't use a pointing device
it provided a shell for MS-DOS
Answers
Answer:
it providrd a shell for MS-DOS
Explanation:
It basically was a shell to make MS-DOS different. MS-DOS was still the underlying operating system.
make a clan using 5S of the current state of your workstation now in the computer laboratory room how are you going to manage smooth workplace
Answers
Answer:
Explanation:
Using your toilet as a trash can. ...
Taking baths and long showers. ...
Conventional showerheadsYou should consider switching to a low-flow showerhead, which uses about 2 gallons of water per minute. ...
Leaky pipes. ...
Laundry loads that are only half full. ...
Running a dishwasher that's not completely full.
how does selection sort work to sort an array? selection sort swaps the first value of an array with the last index of an array, then swaps the second value in an array with the second to last value, until all values have swapped places. selection sort iterates through each index and swaps the current index with the minimum value that exists in the indices greater than the current index. selection sort sets the first index as sorted, and shifts each minimum value into the correct position by finding the lowest value on the sorted side of the array at indices lower than the current index. selection sort finds the lowest value in an array and shifts all elements to the right of that value.
Answers
Selection sort is an algorithm that works by iteratively selecting the smallest element from the unsorted part of an array and swapping it with the element at the beginning of the unsorted section. This process is repeated for each index, with the sorted section growing by one element each time.
1)Initially, the whole array is considered unsorted. The algorithm starts at the first index, searches for the minimum value among the unsorted elements, and then swaps that minimum value with the value at the first index. Now, the first element is sorted, and the unsorted section starts from the second index.
2)The algorithm continues by finding the minimum value in the remaining unsorted section, starting from the second index. Once found, this minimum value is swapped with the value at the second index. Now, the first two elements are sorted, and the unsorted section starts from the third index.
3)This process is repeated for each index until the entire array is sorted. By iteratively selecting the smallest element from the unsorted part and swapping it with the current index, selection sort efficiently sorts the array in ascending order.
4)In summary, selection sort works by dividing the array into a sorted and an unsorted section. It iteratively finds the smallest element in the unsorted section and swaps it with the first unsorted element, effectively expanding the sorted section and reducing the unsorted section until the whole array is sorted.
For more such question on algorithm
https://brainly.com/question/13902805
#SPJ11
Tipos de estructuras A. Expresiones y de variables B. Selectivas y de control C. Instrucciones y parámetros
Answers
Responder:
B. Selectivas y de control
Explicación:
Las estructuras pueden incluir las estructuras selectivas y de control que podrían explicarse como guías de instrucción que dan instrucciones sobre qué elegir y hacer en función de un conjunto de valores de parámetros dados. Por lo tanto, es posible que tengamos una estructura secuencial que solo proporcione una reacción diferente simple en lugar de una guía condicional utilizando GOTO y la declaración NULL.
Las estructuras de control, por otro lado, pueden verse como controles de bucle tales como los bucles FOR, IF y WHILE, por lo que la dirección tomada depende de que se cumpla cierta condición que se especifica en el bloque de programa.
in comparison with a flat file system, _____ in a database.
Answers
Storage space in a database is less than it is in a flat file system.
What distinguishes databases from flat file systems?The following list of differences between databases and flat files: Databases offer greater flexibility, whereas flat files offer less. Data consistency is provided by database systems, however it is not possible with flat files. A database is safer than flat files.
What distinguishes a relational database from a flat-file database?A relational database is made up of several tables of data that are connected to one another by unique key fields. Relational databases, which have more flexibility than flat file databases, which only have one table of data, are more difficult to design and maintain.
To know more about database visit:-
https://brainly.com/question/6447559
#SPJ4
How do I give an answer brainliest?
Answers
Answer:
when two people answer there would be a white crown at the bottom right corner (of the answer) when you click on it it turns yellow/gold which means that you have marked that answer brainliest.
Pick the better answer (in your opinion) and then mark it brainliest.
Windows 7 search could search for files and folders on the local system as well as on the network shares. True or False
Answers
Answer:
True
Explanation:
Computer that us part of a workgroup can access the network
1. P_OP_EW_RE
2.H_R_W_R_
3._ON_E_TI_IT_
4.P_OC_D_RE
5._O_TW_R_
Answers
Answer:
poopaewr4vh23rbu2rfbu2rfu
Explanation:
Ask the user for five-coordinate pairs. Store each pair as a tuple, and store all the pairs in a list. Print the slope between adjacent coordinate pairs. So, if you end up with a list of coordinate pairs like this:
[(1, 2), (2, 3), (-3, 3), (0, 0), (2, 6)]
… then your program should print the following slopes:
Slope between (1, 2) and (2, 3): 1.0
Slope between (2, 3) and (-3, 3): 0.0
Slope between (-3, 3) and (0, 0): -1.0
Slope between (0, 0) and (2, 6): 3.0
You’ll need to pack the two values you retrieve from the user into a tuple.
As you go through your pairs of tuples, you can also unpack the variables in them into x1, y1, x2, and y2. That way, computing the slope is as simple as:
slope = (y2 - y1) / (x2 - x1)

Answers
Answer:
Python code print("**** Please enter 5 coordiante pairs ****") lst1 = [] # initialise two empy lists lst2 = [] for i in range(5) : # 5 iterations to ...
What would be considered a generous amount of storage capacity,
in GB, for a network that must allow access to 322 users? What is a
generous amount of bandwidth, in MBPS, for those 322 users?
Answers
A generous amount of bandwidth for 322 users could be considered as 100 Mbps or more. This would provide enough bandwidth for most activities and allow for smooth operation even during peak usage periods.
The amount of storage capacity and bandwidth required for a network depends on several factors, such as the size of the files being stored and transferred, the number of users accessing the network simultaneously, and the type of applications or services running on the network.
Assuming an average storage requirement of 1 GB per user, 322 users would require at least 322 GB of storage capacity. However, to ensure that there is enough space for future growth and to accommodate larger files, a generous amount of storage capacity could be considered as 500 GB or more.
As for the bandwidth requirements, it also depends on the type of activities the users are performing on the network. For example, if the users are mostly browsing the internet and sending emails, then a bandwidth of 10-20 Mbps could be sufficient. However, if the network is used for streaming videos or downloading large files, then a higher bandwidth would be required.
Assuming a moderate usage scenario, a generous amount of bandwidth for 322 users could be considered as 100 Mbps or more. This would provide enough bandwidth for most activities and allow for smooth operation even during peak usage periods.
Learn more about bandwidth here
https://brainly.com/question/13440200
#SPJ11
Write a loop that sets newScores to oldScores shifted once left, with element 0 copied to the end. Ex: If oldScores = {10, 20, 30, 40}, then newScores = {20, 30, 40, 10}.Note: These activities may test code with different test values. This activity will perform two tests, both with a 4-element array (int oldScores[4]). See "How to Use zyBooks".
If the submitted code tries to access an invalid array element, such as newScores[9] for a 4-element array, the test may generate strange results. Or the test may crash and report "Program end never reached".
#include
using namespace std;
int main() {
const int SCORES_SIZE = 4;
int oldScores[SCORES_SIZE];
int newScores[SCORES_SIZE];
int i;
for (i = 0; i < SCORES_SIZE; ++i) {
cin >> oldScores[i];
}
/* Your solution goes here */
for (i = 0; i < SCORES_SIZE; ++i) {
cout << newScores[i] << " ";
}
cout << endl;
return 0;
}
Answers
Below is a possible solution using a loop to shift the elements of oldScores and store them in newScores:
css
for (i = 0; i < SCORES_SIZE; ++i) {
newScores[(i + SCORES_SIZE - 1) % SCORES_SIZE] = oldScores[i];
}
newScores[SCORES_SIZE - 1] = oldScores[0];
What is the loop about?Below is the solution that sets newScores to oldScores shifted once left, with element 0 copied to the end:
cpp
for (i = 0; i < SCORES_SIZE - 1; ++i) {
newScores[i] = oldScores[i+1];
}
newScores[SCORES_SIZE-1] = oldScores[0];
This loop iterates through oldScores, copying each element to the next index in newScores (i+1). Finally, it copies the first element of oldScores (index 0) to the last index in newScores.
Here's the updated main() function with the loop and output:
cpp
int main() {
const int SCORES_SIZE = 4;
int oldScores[SCORES_SIZE];
int newScores[SCORES_SIZE];
int i;
for (i = 0; i < SCORES_SIZE; ++i) {
cin >> oldScores[i];
}
for (i = 0; i < SCORES_SIZE - 1; ++i) {
newScores[i] = oldScores[i+1];
}
newScores[SCORES_SIZE-1] = oldScores[0];
for (i = 0; i < SCORES_SIZE; ++i) {
cout << newScores[i] << " ";
}
cout << endl;
return 0;
}
Read more about loop here:
https://brainly.com/question/26568485
#SPJ1
please help will give brainliest

Answers
Answer:
waterfall- google search
Explanation:
how academic skills for teachers help students at the university
Answers
Academic skills for teachers has help students at the university because with its use, students are able to have test-taking strategies and understands their courses more better.
Why are academic skills vital for university?The use of Academic skills is one that act to encourage students so they can be able to be more efficient and better learners.
Conclusively, It is one that give students the power or confidence to be involved fully in any courses that are useful for them outside of the classroom.
Learn more about skills from
https://brainly.com/question/1233807
You want to add a picture of a potential new office layout to the title page of a proposal. How can you adjust the size of the image without changing its proportions?
Answers
Answer:
You can adjust the size of an image without changing its proportion by holding down the shift key while adjusting one of the edges.
A user logs onto their computer system and notices that several of their files are missing and some are renamed. what should you do? group of answer choices
Answers
Restore the files from a backup. If a user notices that several of their files are missing or renamed, it is likely that their system has been compromised by malware.
In such a situation, it is important to take immediate action to mitigate the damage. The first step should be to disconnect the machine from the internet to prevent further infection. Then, the malware removal process should be initiated to identify and eliminate the threat. However, restoring the missing or renamed files from a backup should also be considered as a way to ensure data recovery. In some cases, restoring from the last Restore Point may also be an option, but it depends on the severity of the infection and the availability of a reliable Restore Point.
Learn more about cybersecurity here: brainly.com/question/27560386
#SPJ4
what is the mpls standard, and why is it often used by isps to move traffic from one customer site to another?
Answers
MPLS stands for Multi Protocol Label Switching.
What is MPLS and why is it used?
The IP packet routing method known as Multi Protocol Label Switching (MPLS) uses labels to direct IP packets along paths rather than relying on routers' intricate routing tables. This function aids in speeding up IP packet delivery.
The networks that are passed are built to give users more control over packet-switched networks.
The best routing systems are these. These systems have various traits and distinct priorities. These priorities are determined by operators and data flow.
Multiprotocol Label Switching, or MPLS as it is more often known, enables businesses and services to build the next-generation network. They enhance the existing offerings by integrating advanced services and value.
Better technologies exist with MPLS. The application has been integrated with MPLS.
To know more about MPLS refer:
https://brainly.com/question/29582349
#SPJ4
he specialty chips are designed to improve specific computing operationsT/F
Answers
True. Specialty chips are specifically designed to enhance and optimize specific computing operations. Specialty chips are purpose-built to enhance and optimize specific computing operations, providing improved performance, efficiency, and capabilities for targeted tasks or applications.
Specialty chips, also known as application-specific integrated circuits (ASICs), are designed to improve the performance and efficiency of specific computing operations. Unlike general-purpose processors, which are designed to handle a wide range of tasks, specialty chips are tailored to excel in specific domains or applications. Specialty chips are created by focusing on the specific requirements and characteristics of a particular computing task or problem. By customizing the chip's architecture and circuitry, designers can optimize its performance for the targeted operation. This specialization allows for significant improvements in speed, power efficiency, and overall performance compared to using general-purpose processors for the same task. Examples of specialty chips include graphics processing units (GPUs) designed for accelerating graphics rendering and machine learning tasks, digital signal processors (DSPs) optimized for signal processing applications, and application-specific integrated circuits (ASICs) developed for specific functions like encryption, networking, or artificial intelligence.
Learn more about graphics processing units here:
https://brainly.com/question/14393815
#SPJ11
can someone tell me why it says that and how i can fix it pls


Answers
View the image below for the answer.

In table design view, enter Value must be <=5000 as the validation text property for the bonus amount field. -click the bonus amount field-in the field properties field click the validation text property-type Value must be <=5000 in the field-press enter
Answers
To enter "Value must be <=5000" as the validation text property for the bonus amount field in table design view, you'll need to follow these steps:
1. Open the table in design view by right-clicking on the table name in the navigation pane and selecting "Design View."
2. Click on the bonus amount field to select it.
3. In the field properties pane, scroll down to the Validation Rule property and type "<=5000" (without the quotes).
4. Press Enter to save the validation rule.
5. Scroll down to the Validation Text property and type "Value must be <=5000" (again, without the quotes).
6. Press Enter to save the validation text.
Once you've completed these steps, users will see the validation text "Value must be <=5000" if they try to enter a value greater than 5000 in the bonus amount field. This will help prevent data entry errors and ensure that the data in your table is accurate and consistent.
For such more question on validation
https://brainly.com/question/29976983
#SPJ11
Sketches in your answers are to be neat two-dimensional plan or elevation views showing
adequate details clearly and neatly labelled.
1. Sketch, show and label the framing arrangement used on your vessel:
a. Forward – to include
i. Side frames
ii. Web frames
iii. Stringers plates
iv. Stem
b. Transom stern – to include
i. Side frames
ii. Transom floor
iii. Stern post
Answers
The main components of a steam power plant include a boiler, turbine, condenser, and generator.
What are the main components of a steam power plant?a. Forward:
- Side frames: These are vertical structural members located on the sides of the vessel. They provide strength and support to the hull.
- Web frames: These are horizontal or diagonal structural members that connect the side frames, adding rigidity to the hull structure.
- Stringer plates: These are longitudinal plates attached to the side frames and web frames, running along the length of the vessel. They help distribute loads and strengthen the hull.
- Stem: The stem is the vertical or inclined post at the forward end of the vessel. It provides structural support and helps to shape the bow.
b. Transom stern:
- Side frames: Similar to the forward section, these vertical structural members are located on the sides of the vessel's stern.
- Transom floor: This is the horizontal plate that connects the side frames at the transom stern, providing strength and rigidity.
- Stern post: The stern post is the vertical structural member at the aft end of the vessel. It supports the transom and provides structural integrity to the stern.
Learn more about components
brainly.com/question/30324922
#SPJ11
katia wants to listen to online radio on her home computer while she works. what is the best option she should use to get connected to the internet? a. broadband b. dial-up c. mobile app d. a landline connection
Answers
a. broadband
Which one of the following descriptions of an IP address is most accurate?A machine on the web or a regional network can be identified by its IP address, which is a special address.The rules defining the data format delivered over the internet or a local network are known as "Internet Protocol," or IP.
Which media conglomerate has AT&T just acquired and is currently expanding?The $43 billion merger between AT&T and Discovery, which resulted in the creation of Warner Bros. Discovery, was finalized on Friday.With the deal's completion, the largest pure entertainment brand—which includes two international streamers and far too many cable and broadcast channels to count—is officially launched on the market.
To know more about broadband visit:
https://brainly.com/question/15860110
#SPJ4
Do you know how to change your grades on a printer???????????
Answers
Answer:
To change ur grade make sure to do it on the website first by right clicking your mouse and clicking inspect element and once done changing x out and it will save
Explanation:
Question 7 of 10
What term is used to refer to the requesting of information from a database?
O A. Inquiring
O B. Asking
O C. Querying
O D. Looking
Answers
which of these describe raw data?check all of the boxes that apply A) what a person buys B) where a person lives C) data that has been analyzed D) data that has not been analyzed
Answers
Which three elements are required to have a Trade Secret?
Answers
The three elements that are required to have a trade secret are as follows:
It bestows a competitive lead on its owner.It is subject to sensible endeavor to control its secrecy.It is confidential in nature. What do you mean by Trade secret?A Trade secret may be defined as a type of intellectual property that significantly consists of secret information that might be sold or licensed specifically in order to main its secrecy.
Trade secrets can take many forms such as formulas, plans, designs, patterns, supplier lists, customer lists, financial data, personnel information, physical devices, processes, computer software, etc. These secrets must not be generally known by or readily ascertainable to competitors.
Therefore, the three elements that are required to have a trade secret are well mentioned above.
To learn more about Trade secrets, refer to the link:
https://brainly.com/question/27034334
#SPJ1